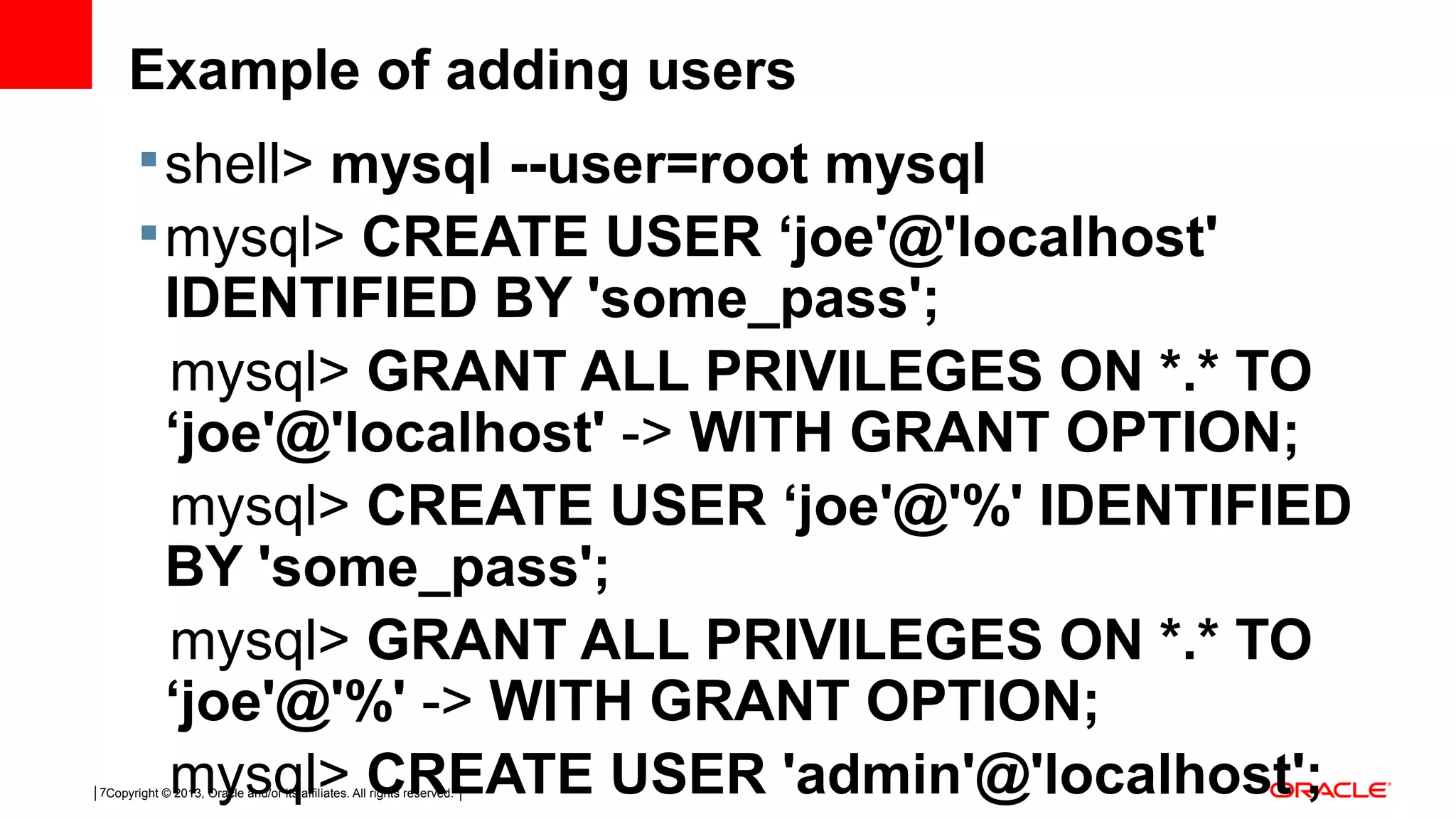
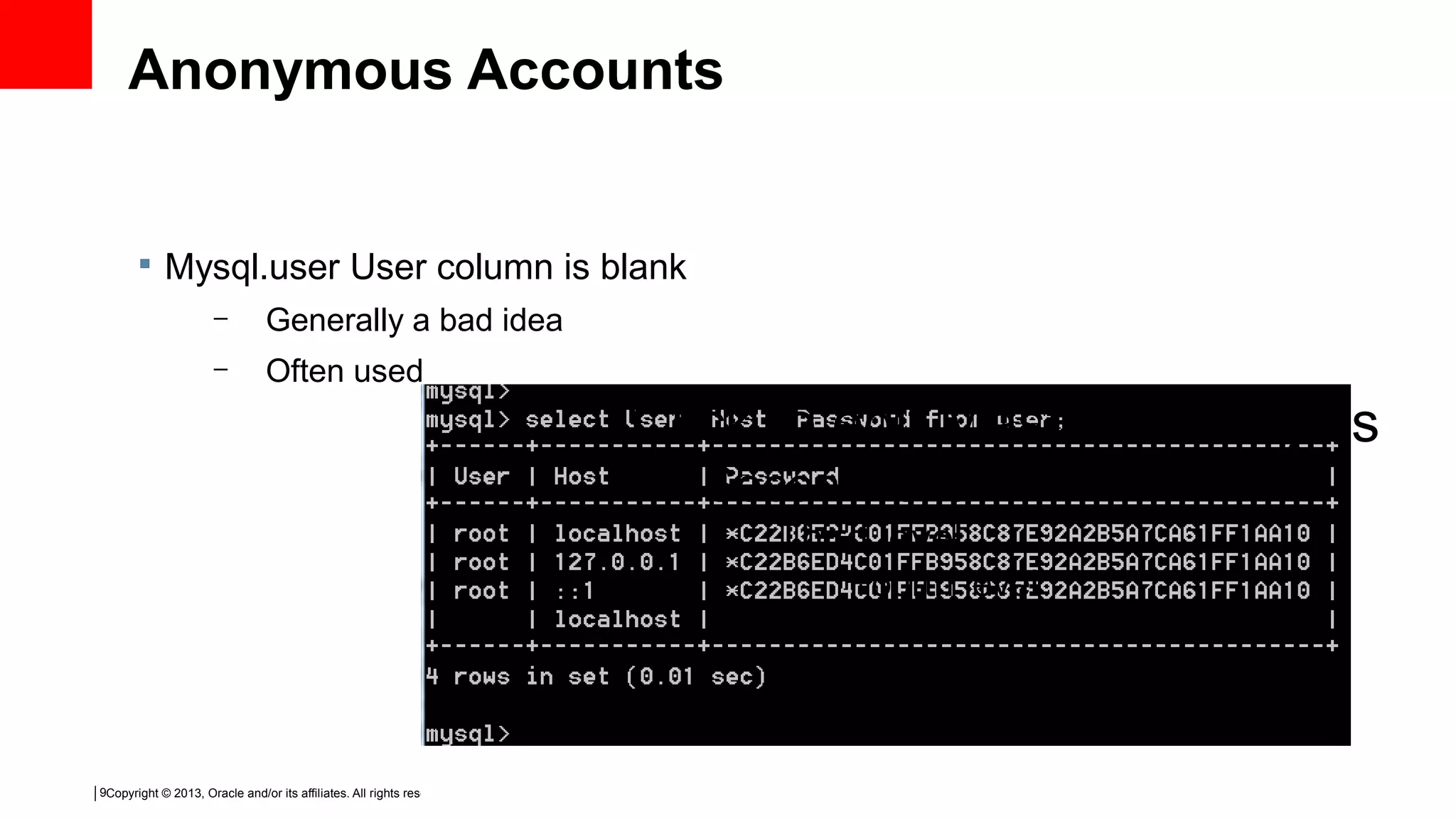
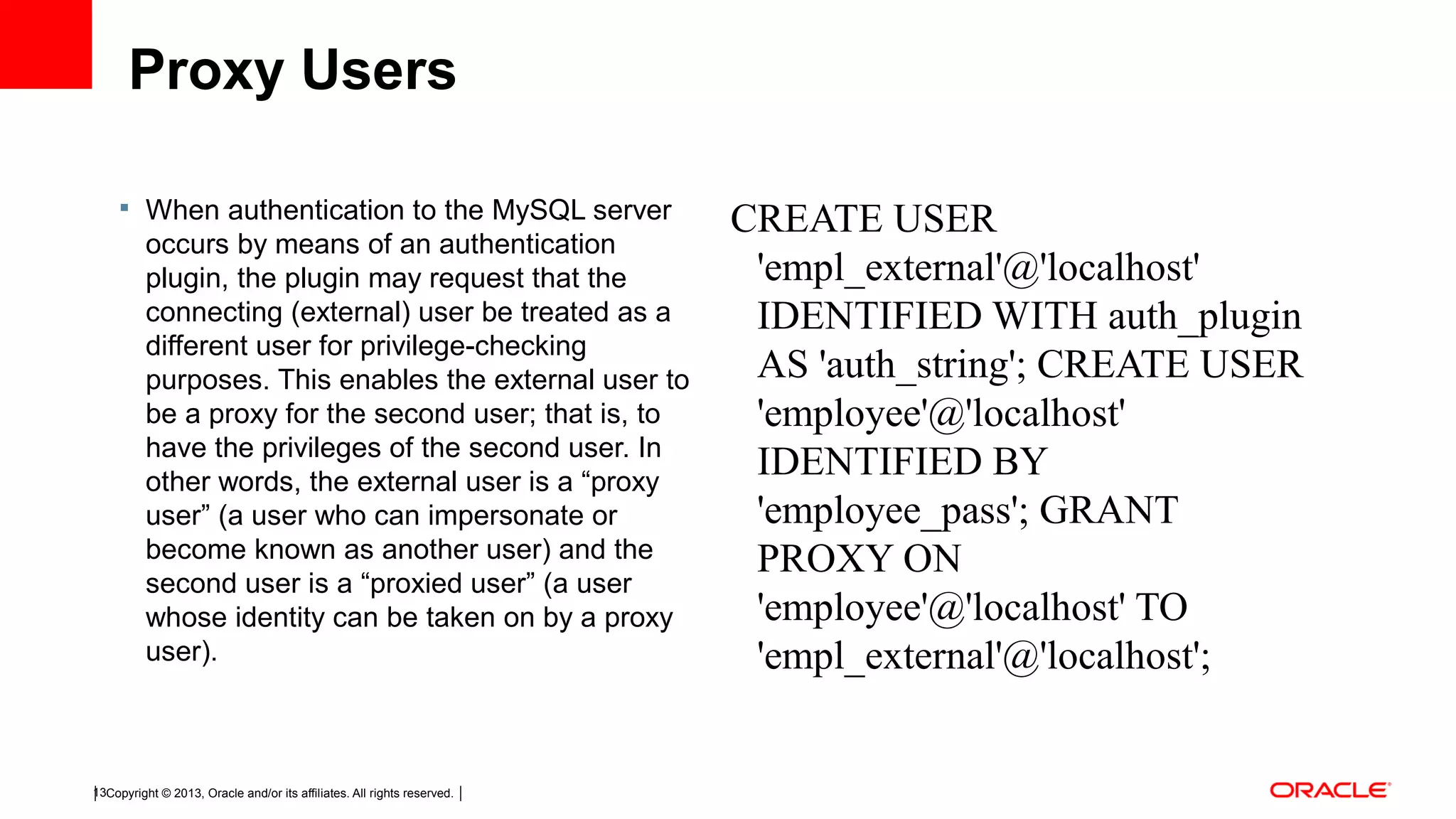
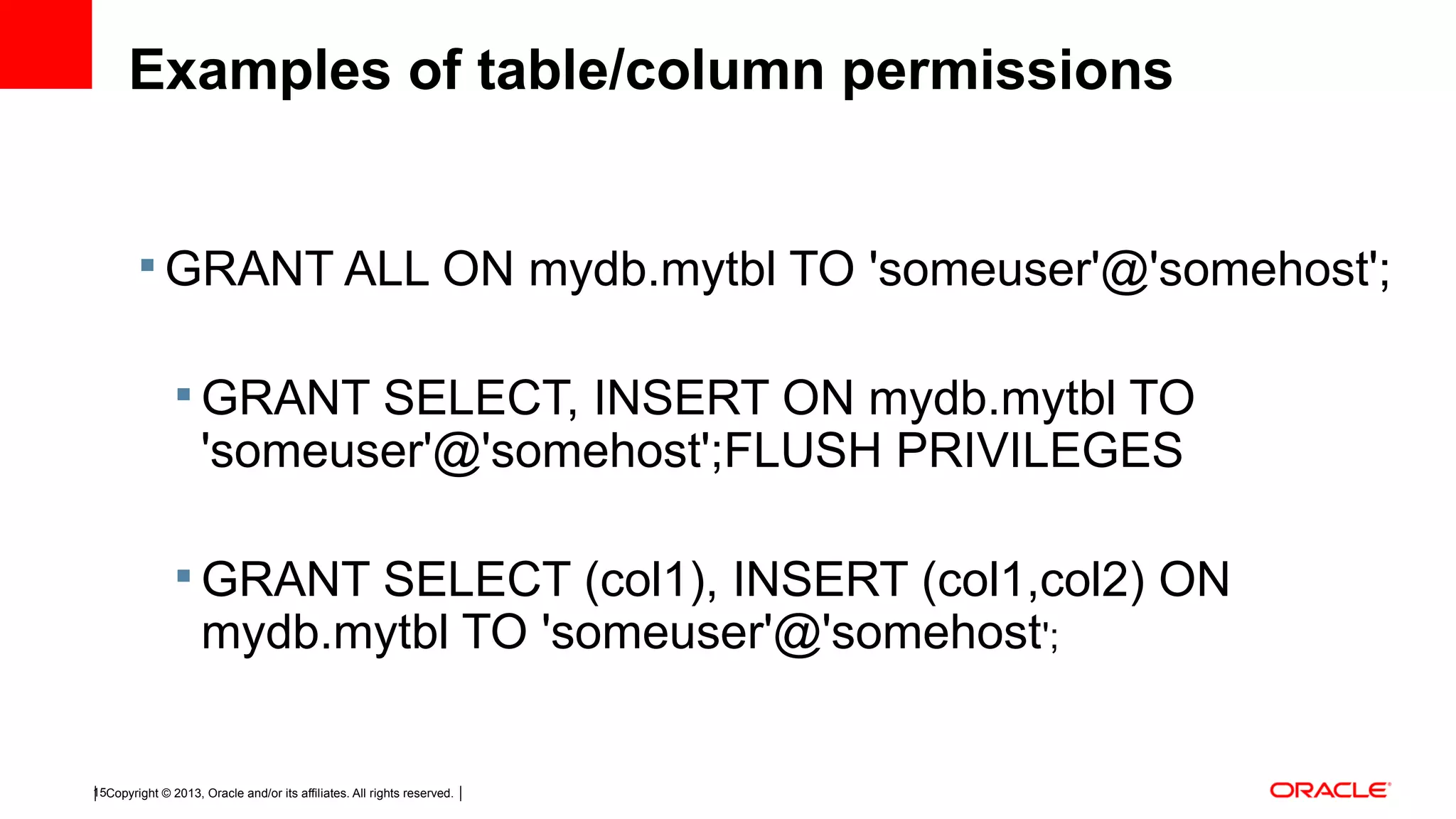
This document discusses tips and tricks for MySQL user administration. It covers how MySQL stores user accounts and passwords, and two main ways to create accounts using SQL statements or manipulating grant tables directly. It also discusses user privileges, plugins for authentication, proxy users, and best practices like being stingy with privileges and auditing privileges regularly.