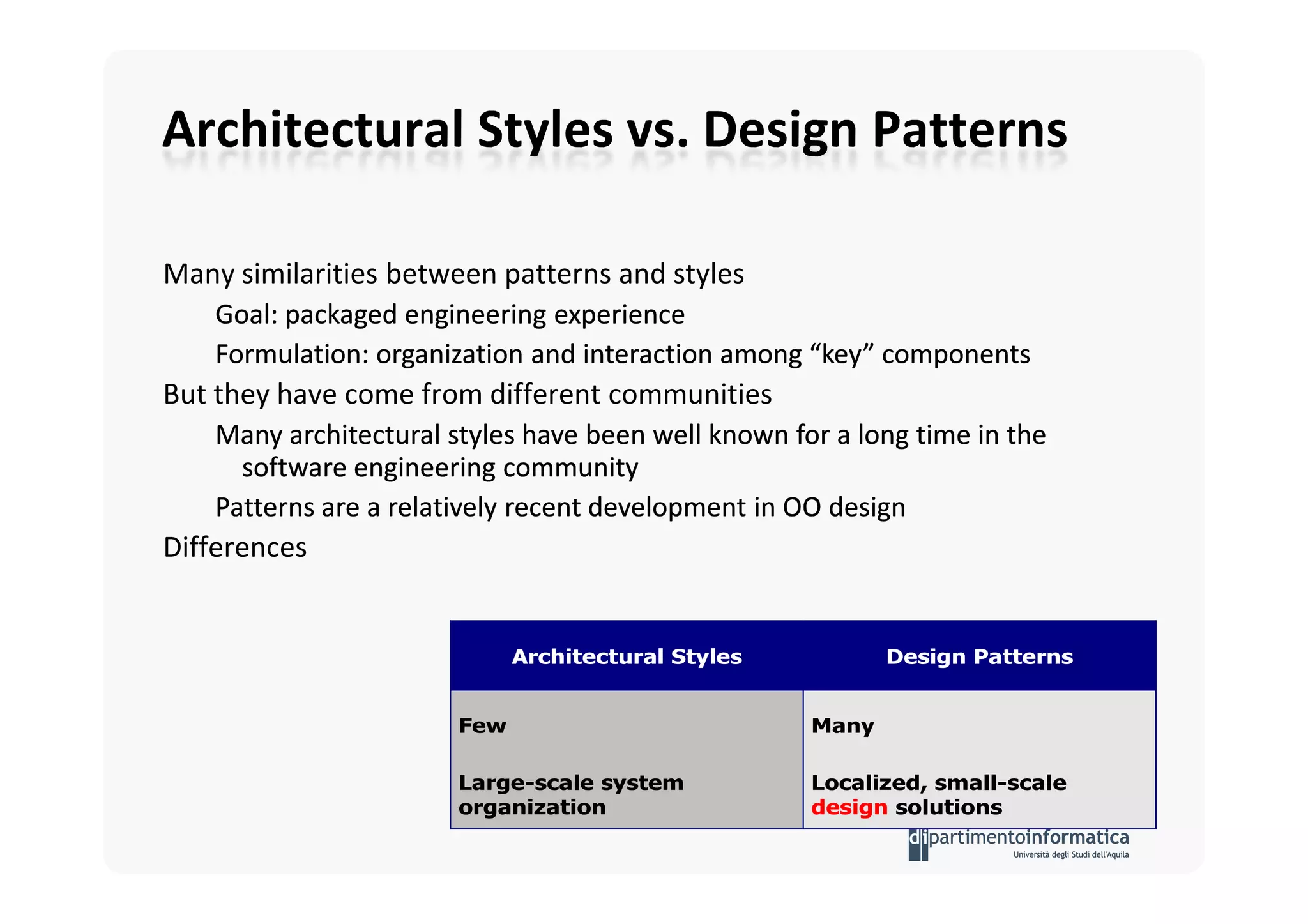
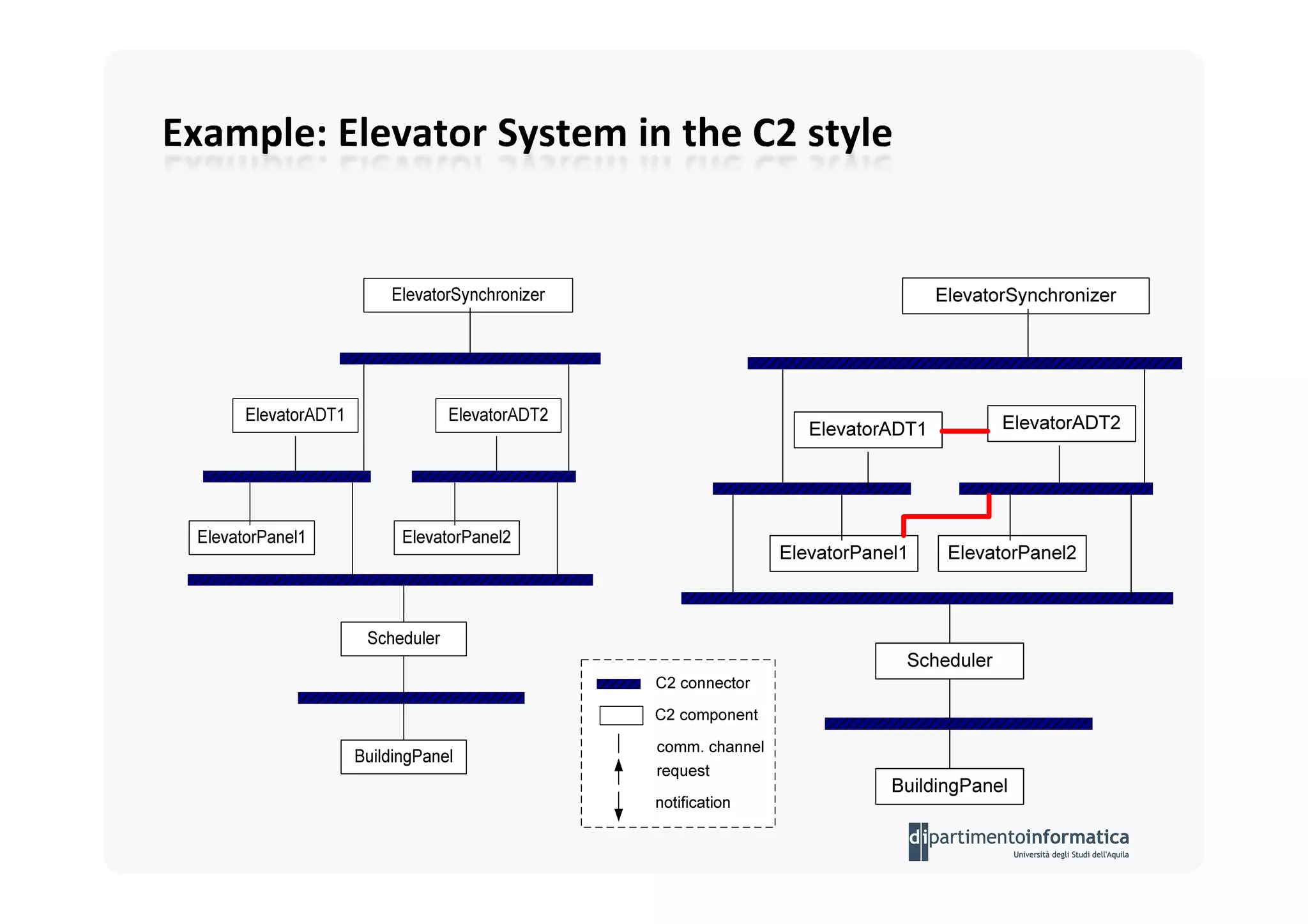
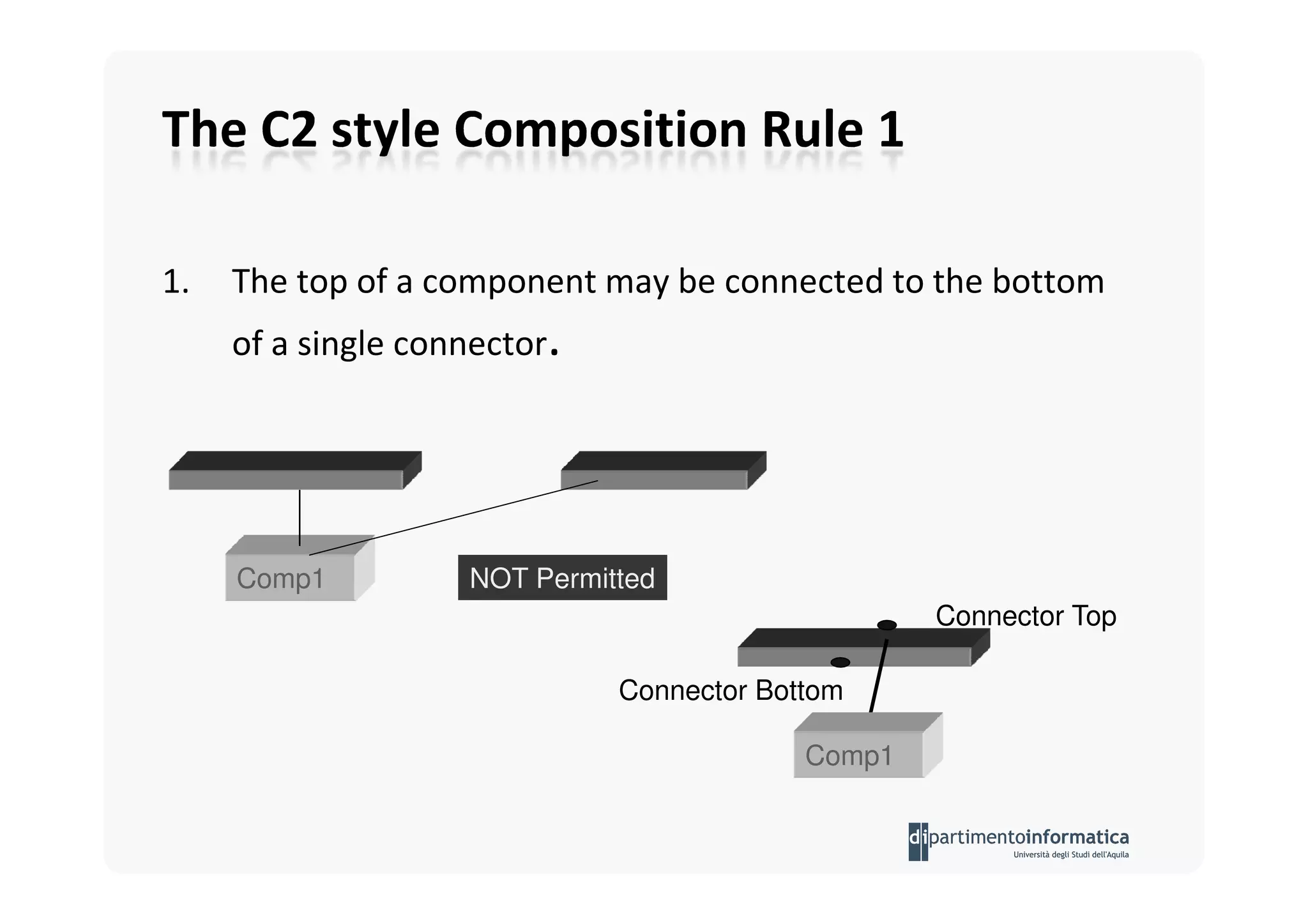
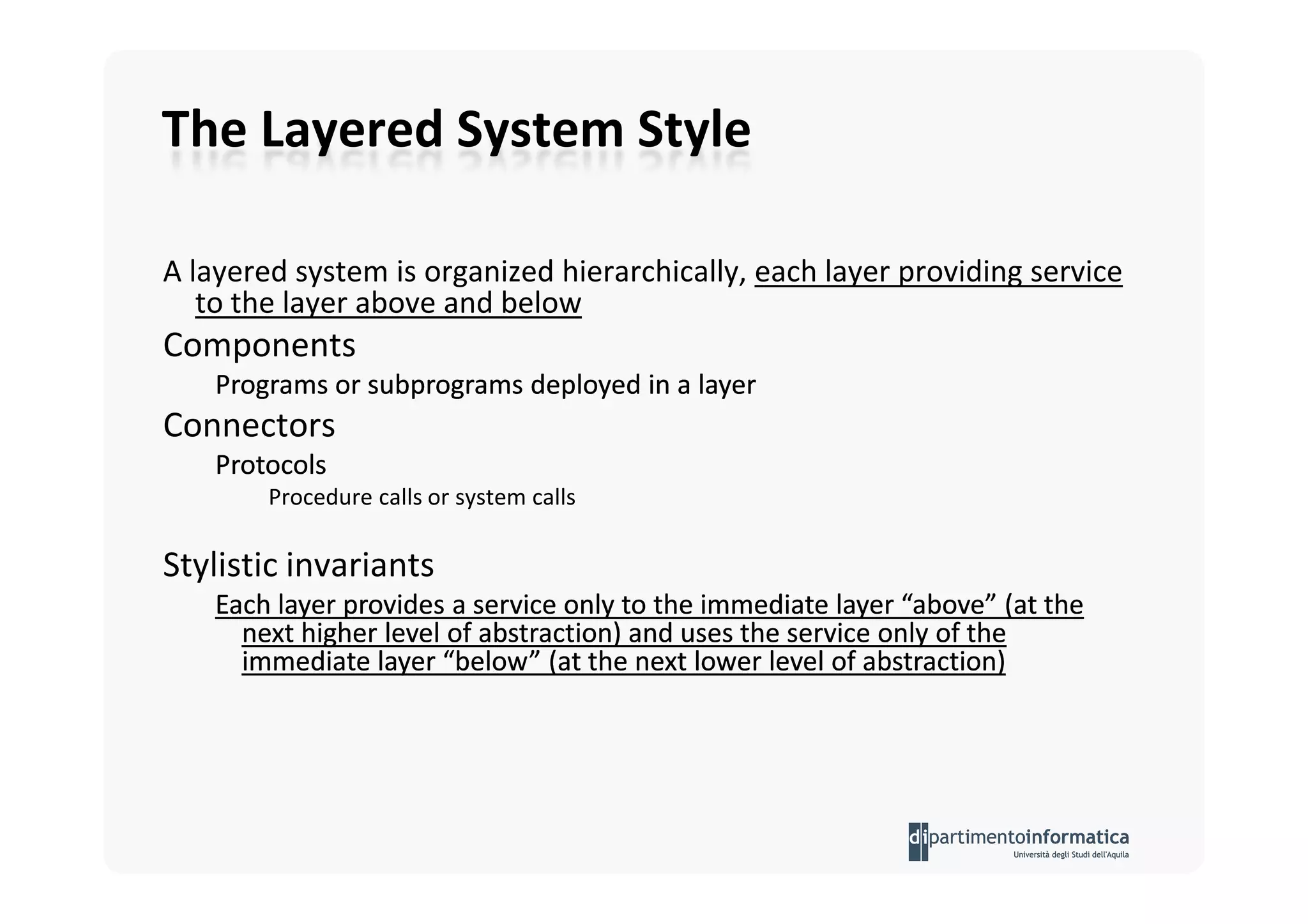
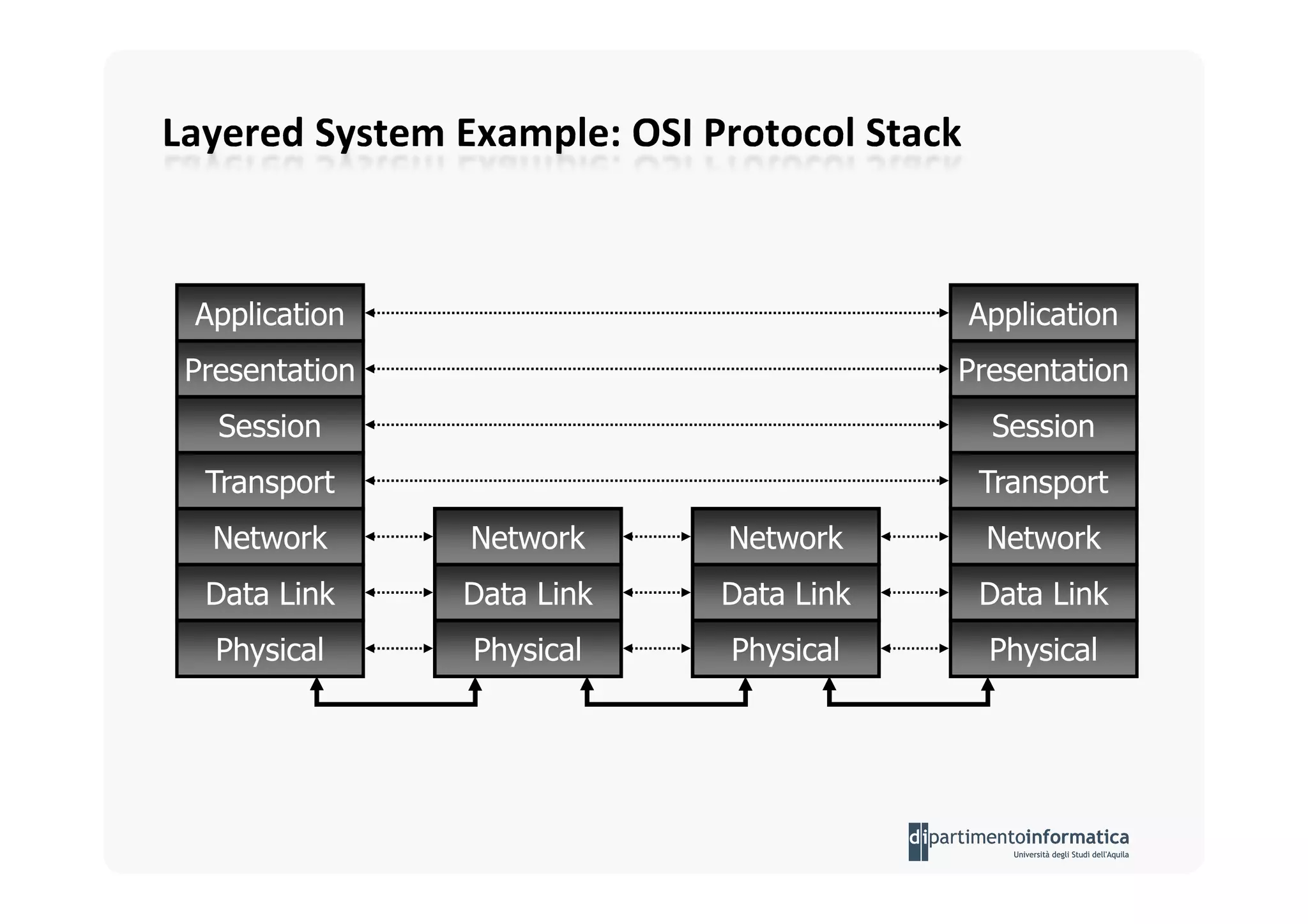
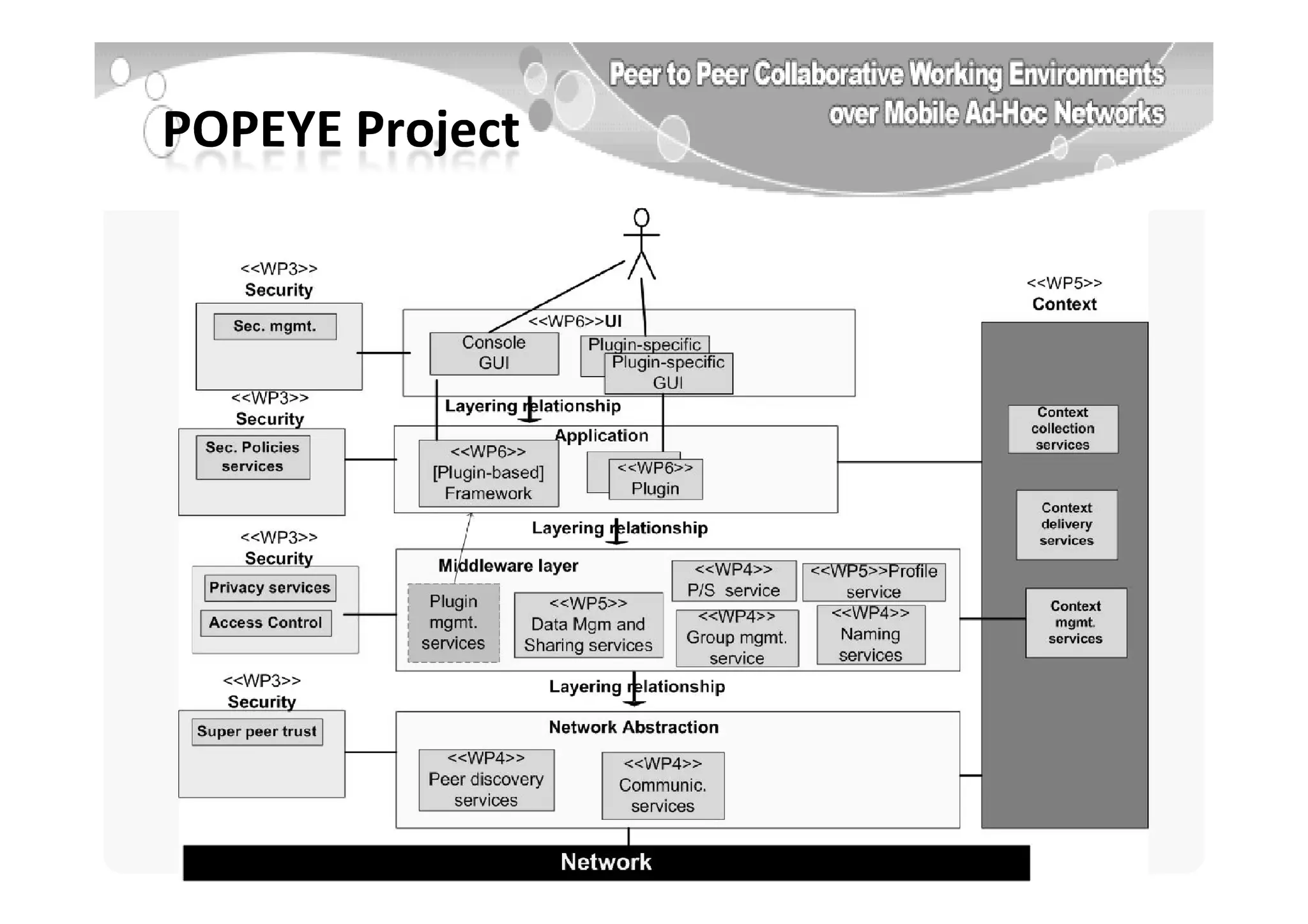
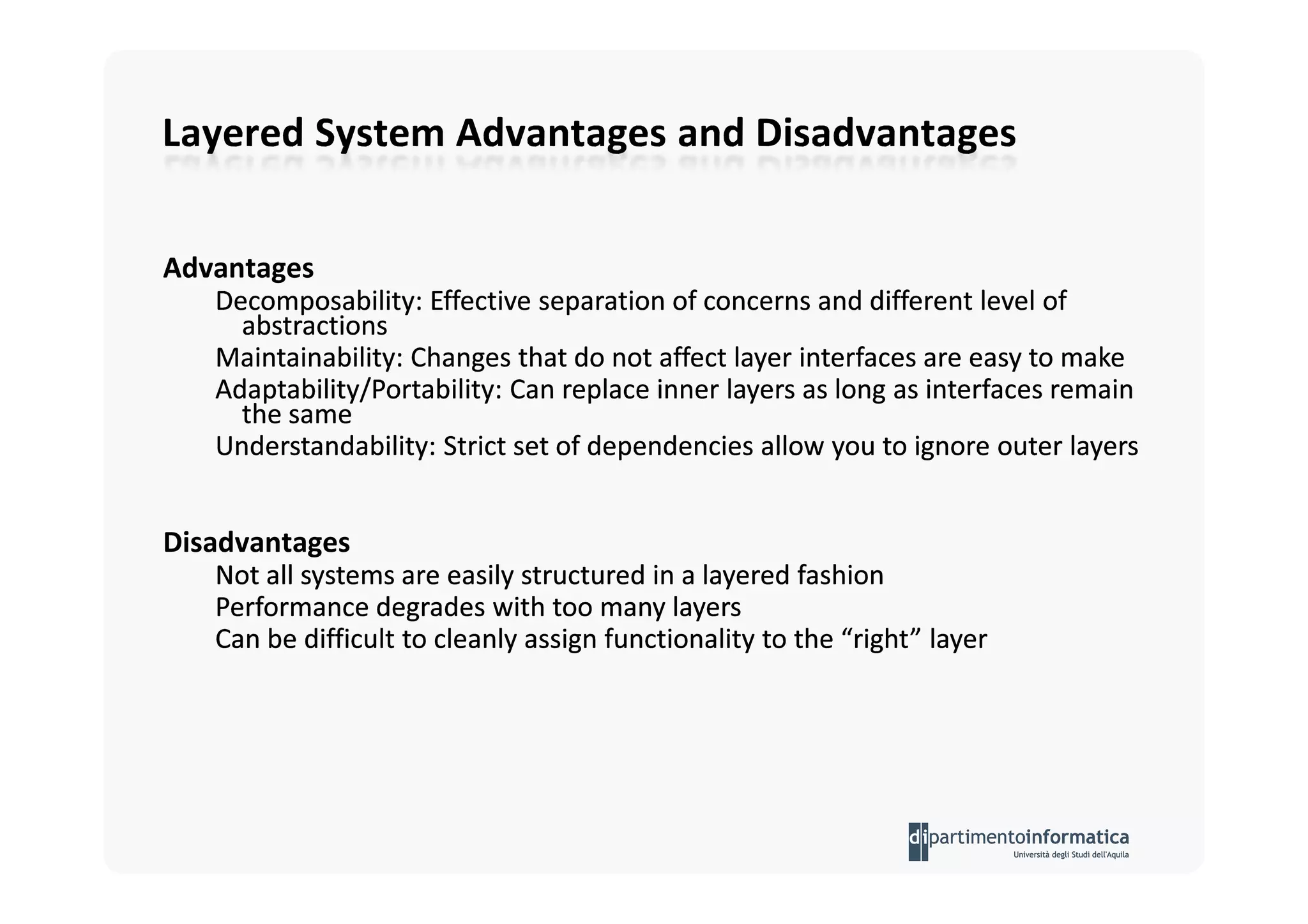
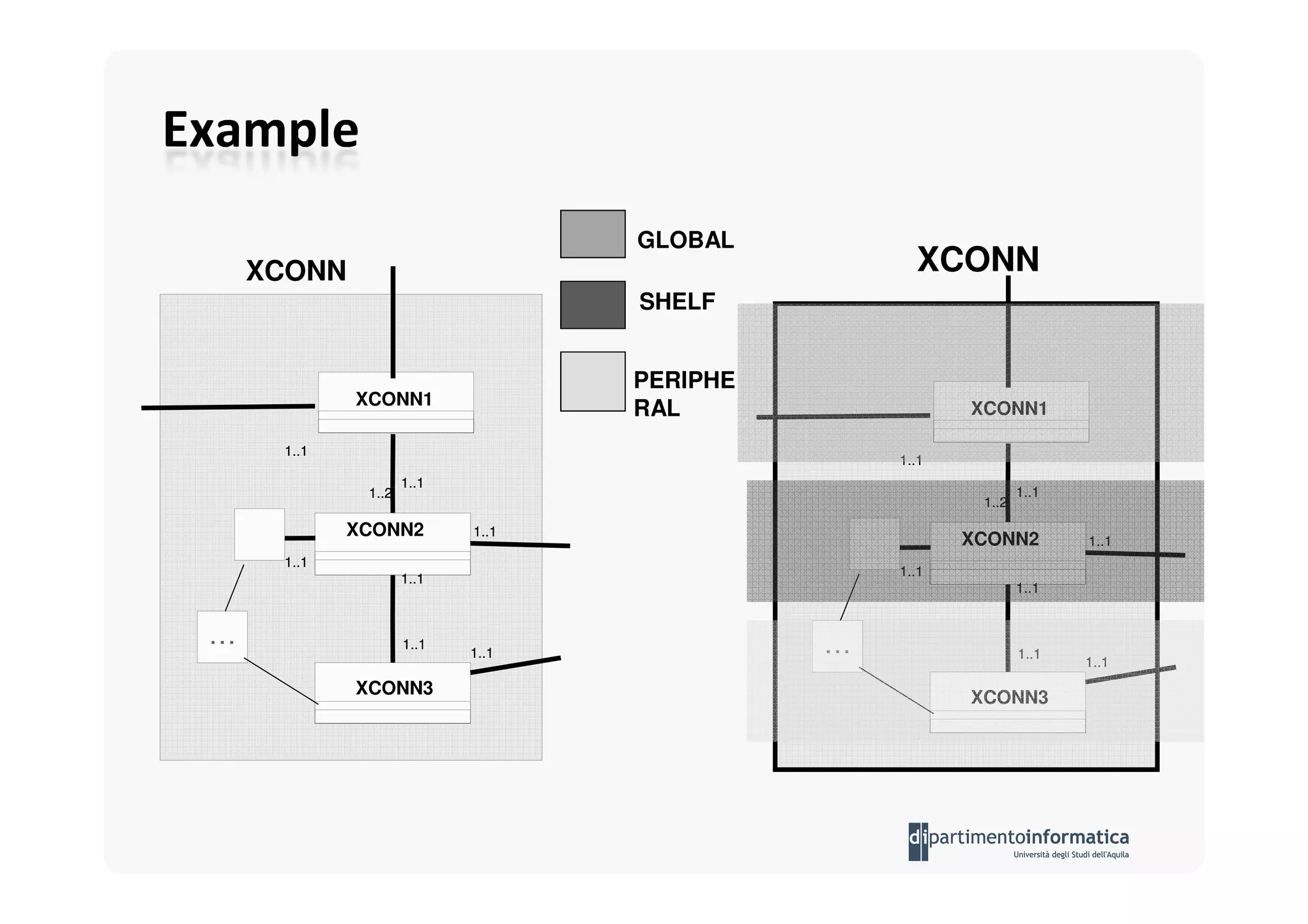
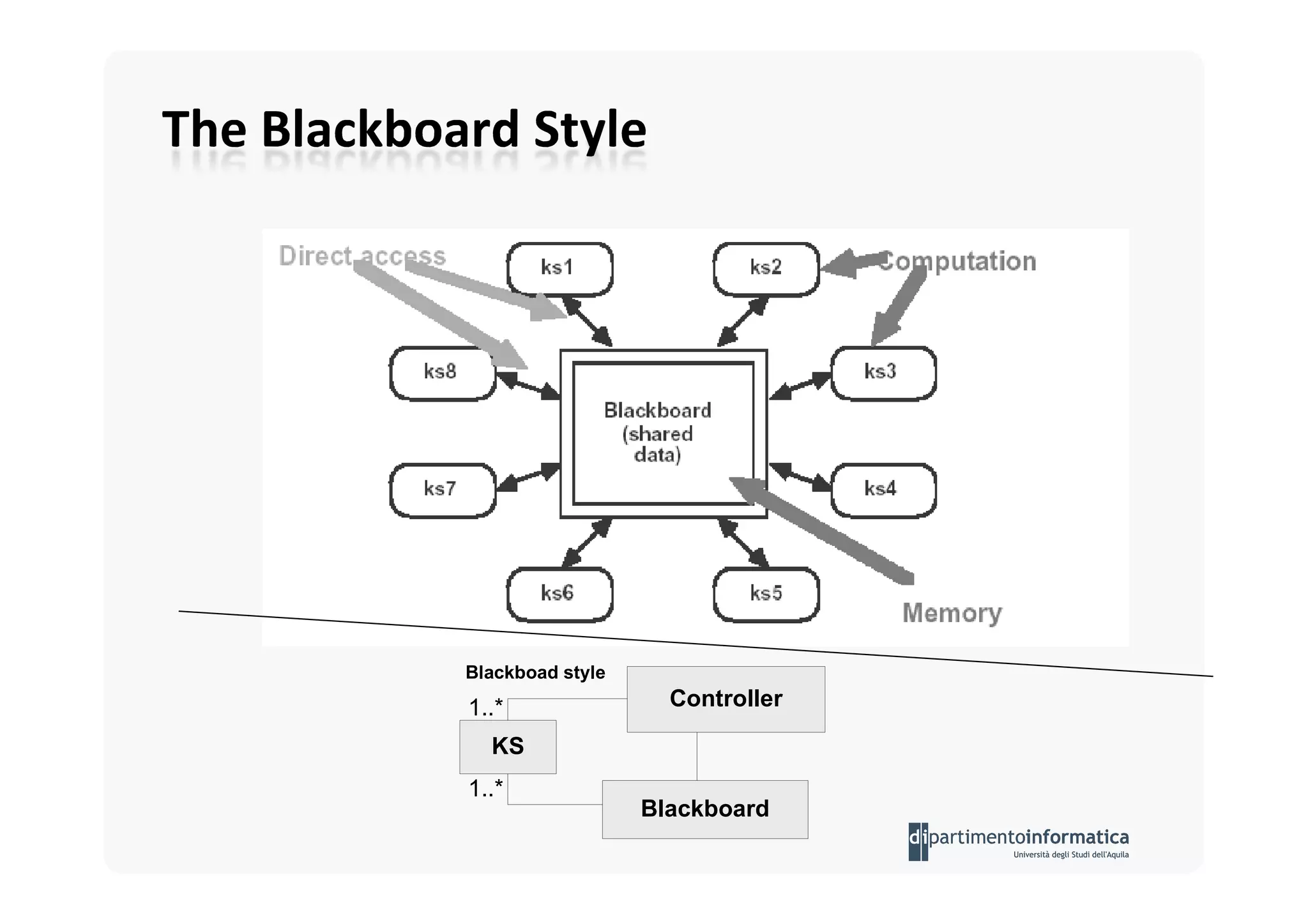
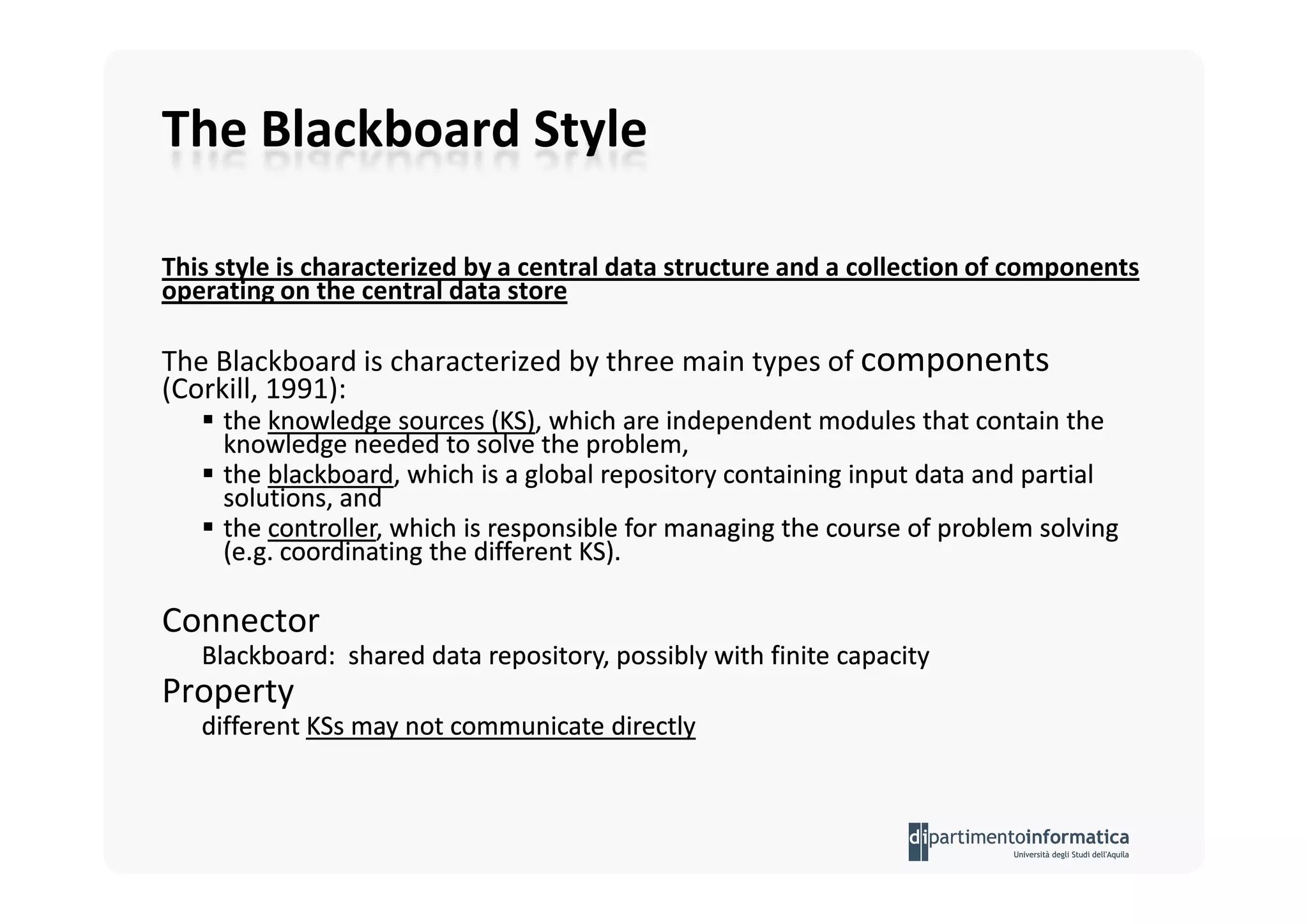
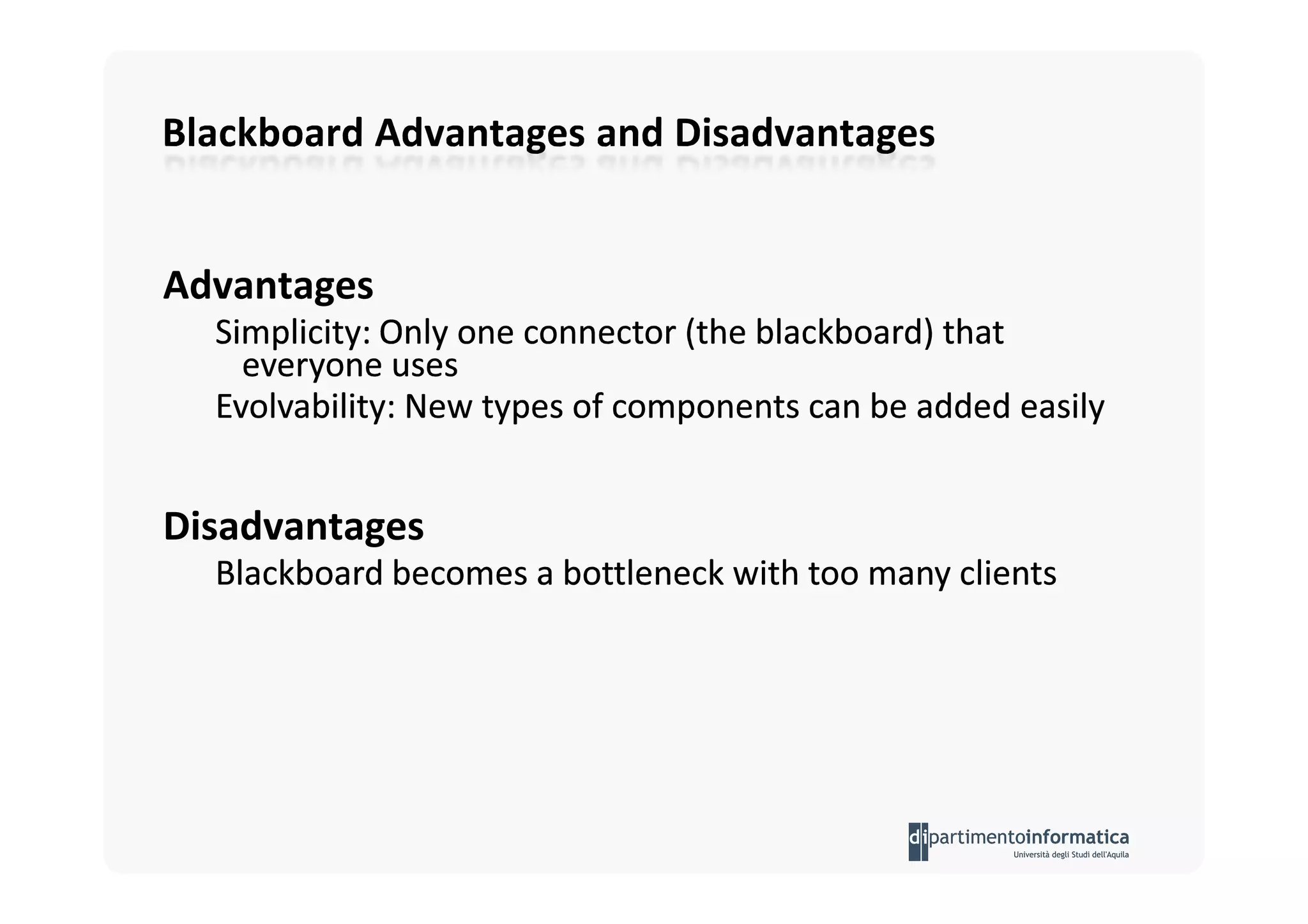
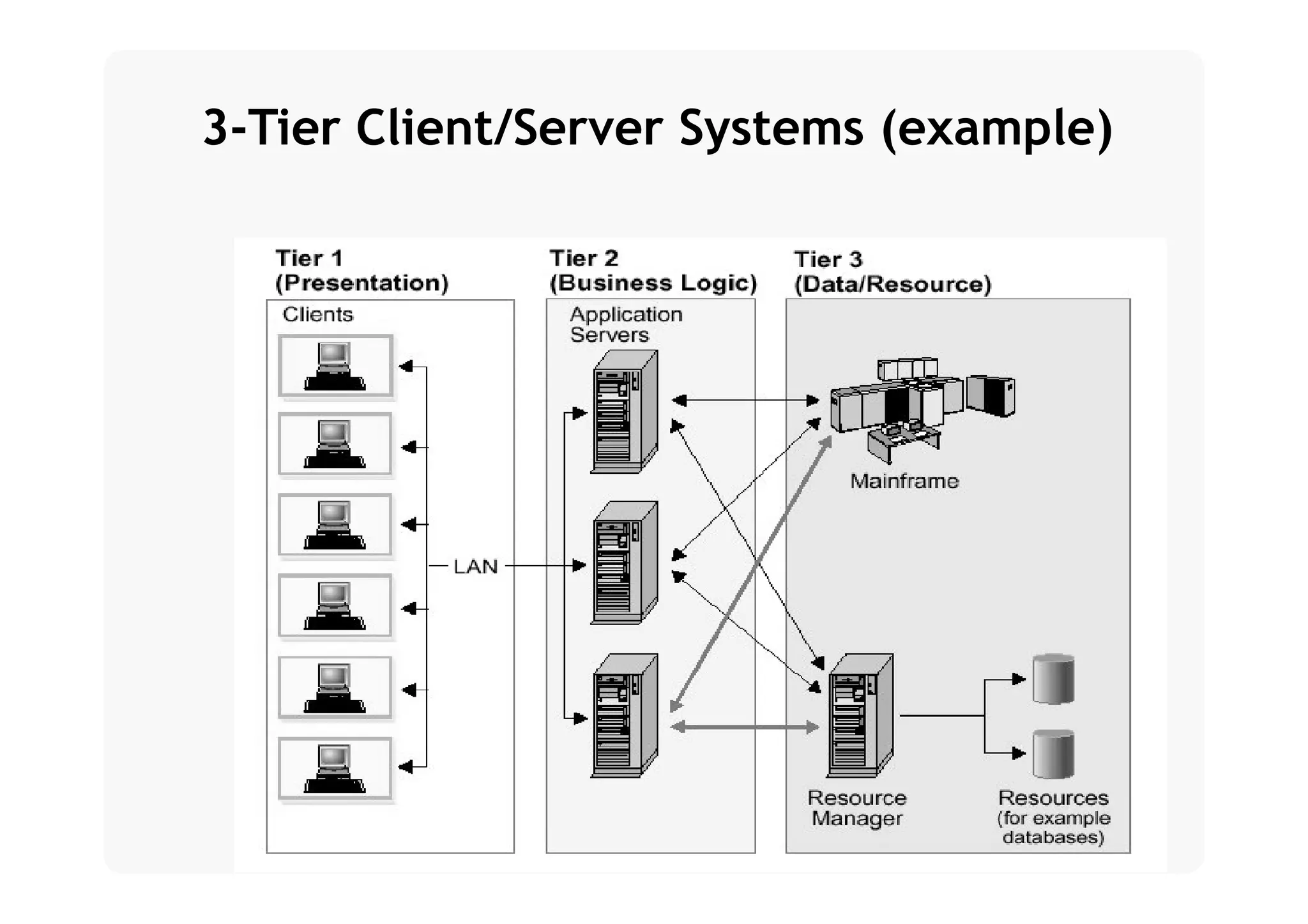
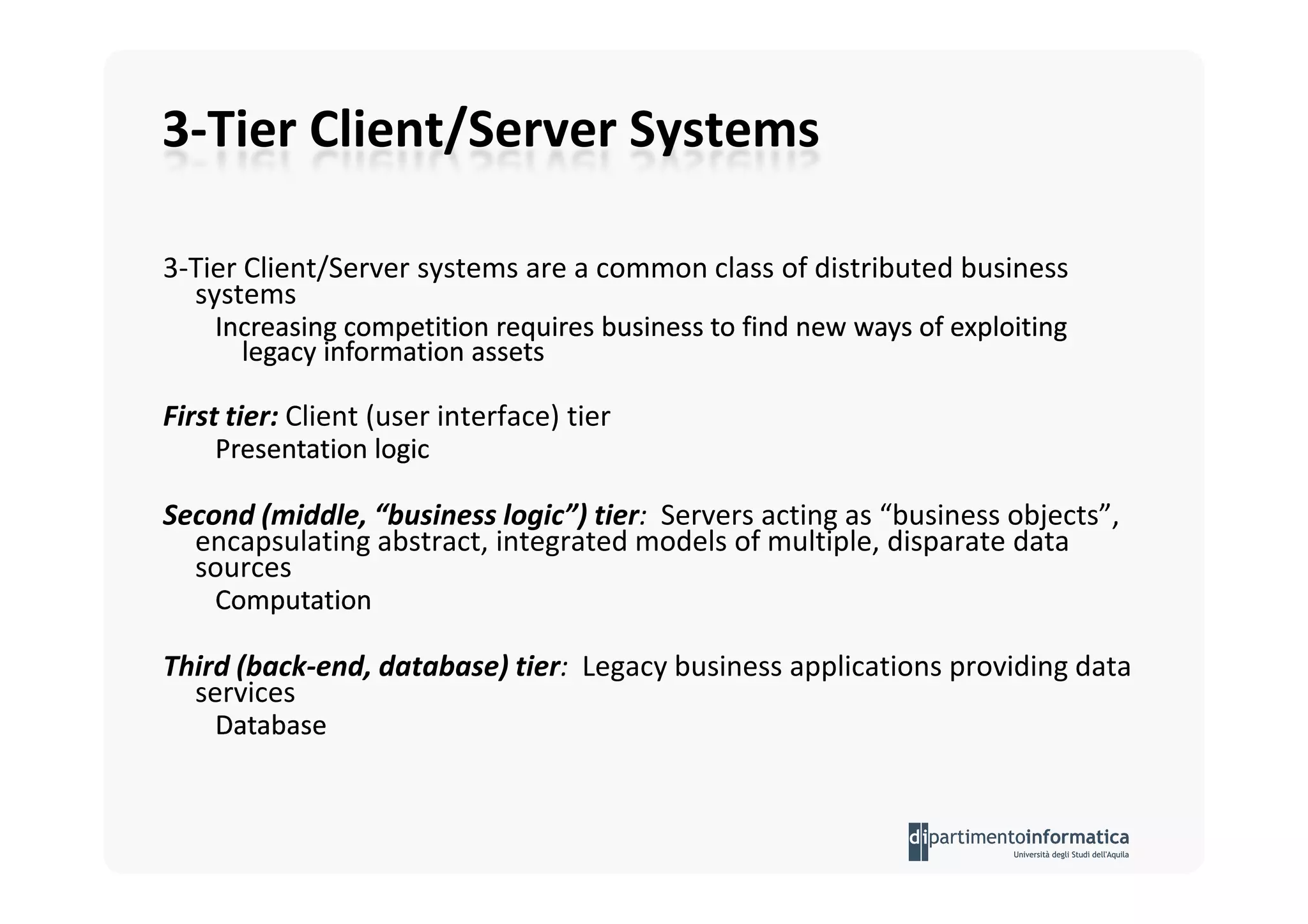
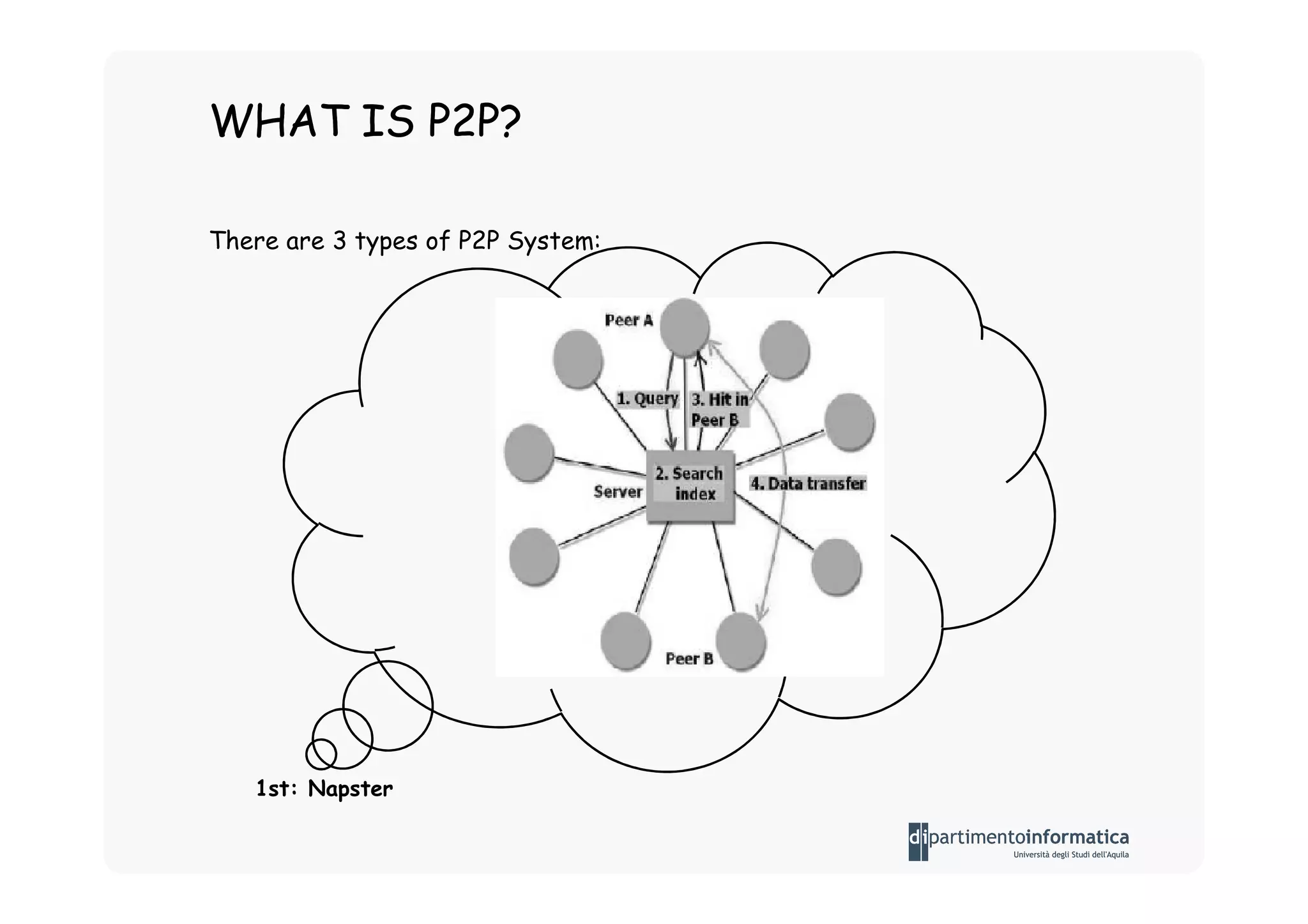
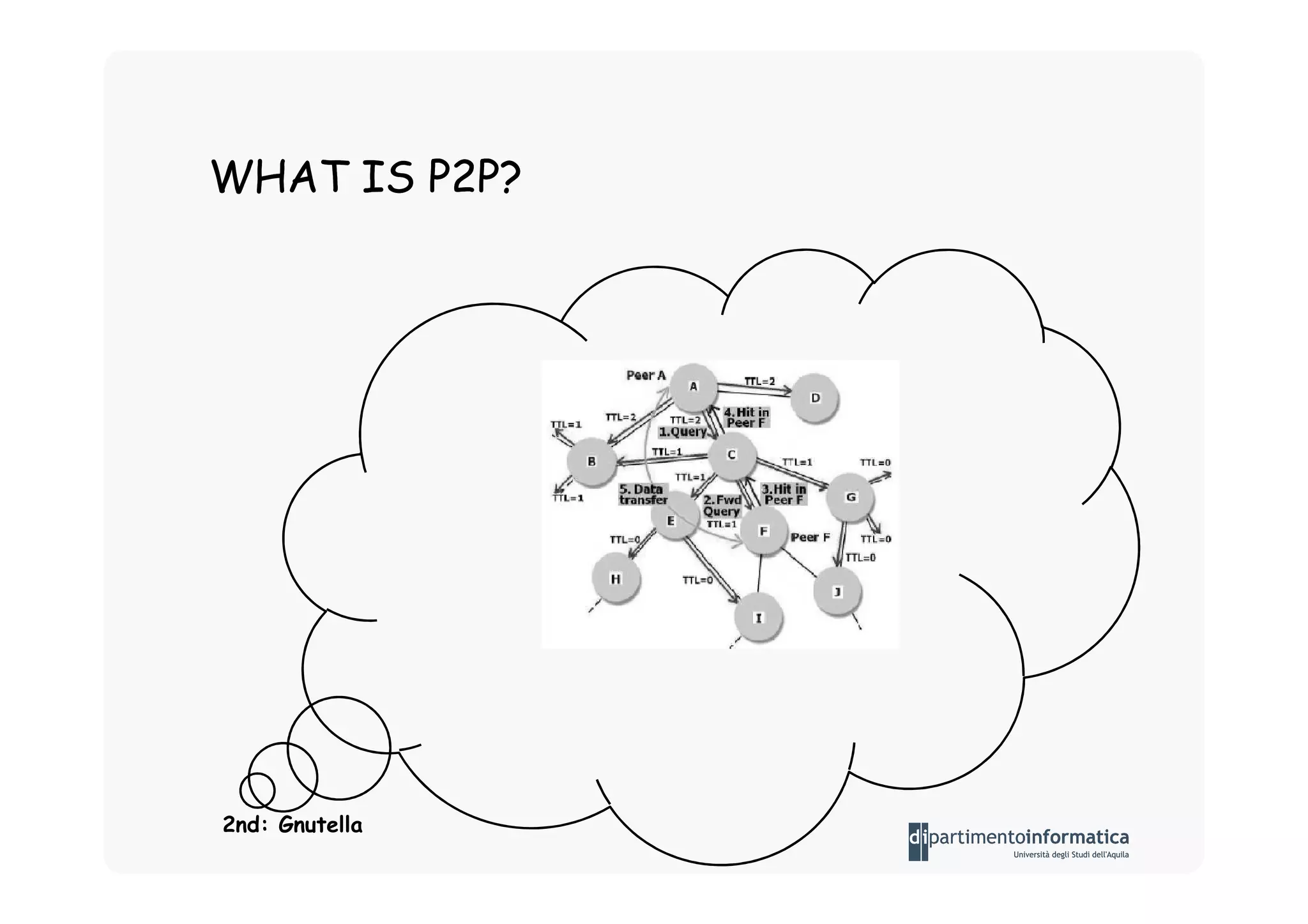
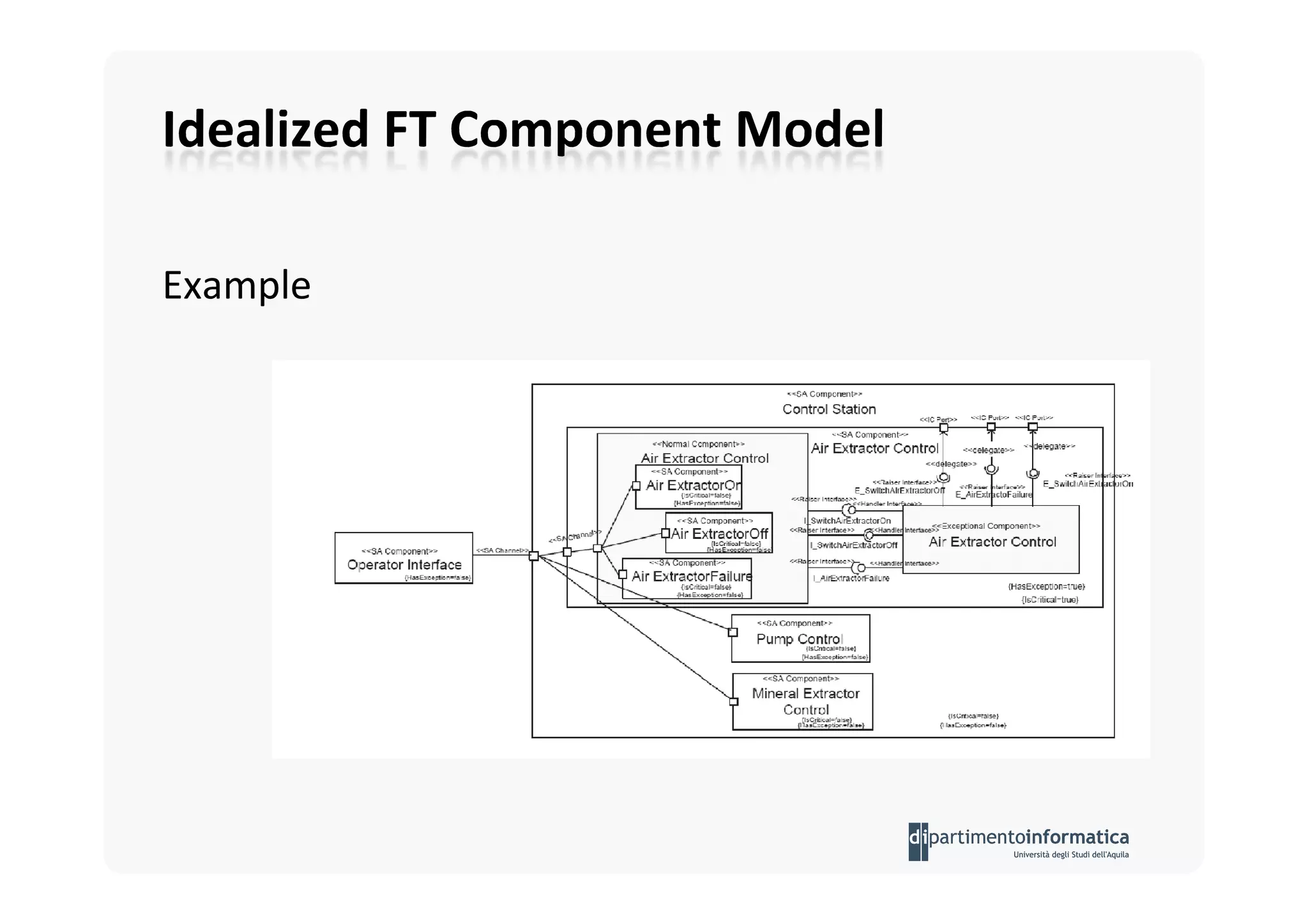
The document provides an introduction to software architecture and various architectural styles, such as layered systems, blackboard style, and peer-to-peer systems. It discusses design rules, component communication through connectors, and the role of architectural languages in promoting desirable properties in software. Additionally, the document outlines the structure and functioning of different system types including client/server and three-tier systems.




![Architectural styles typically determine four kinds of properties [AAG93]: IMP](https://image.slidesharecdn.com/04sastyle-121022082838-phpapp01/75/Software-Architecture-Styles-6-2048.jpg)