This document discusses using the RSA algorithm to provide security in cloud computing environments. It first provides background on cloud computing and discusses some of the security challenges in cloud environments. It then describes how public key cryptography algorithms like RSA can help address some of these security issues by allowing for secure storage and transmission of data through encryption with public/private key pairs. The document goes on to provide an overview of how the RSA algorithm works, including key generation and the encryption/decryption process. It proposes implementing RSA to provide security for data stored in the cloud.

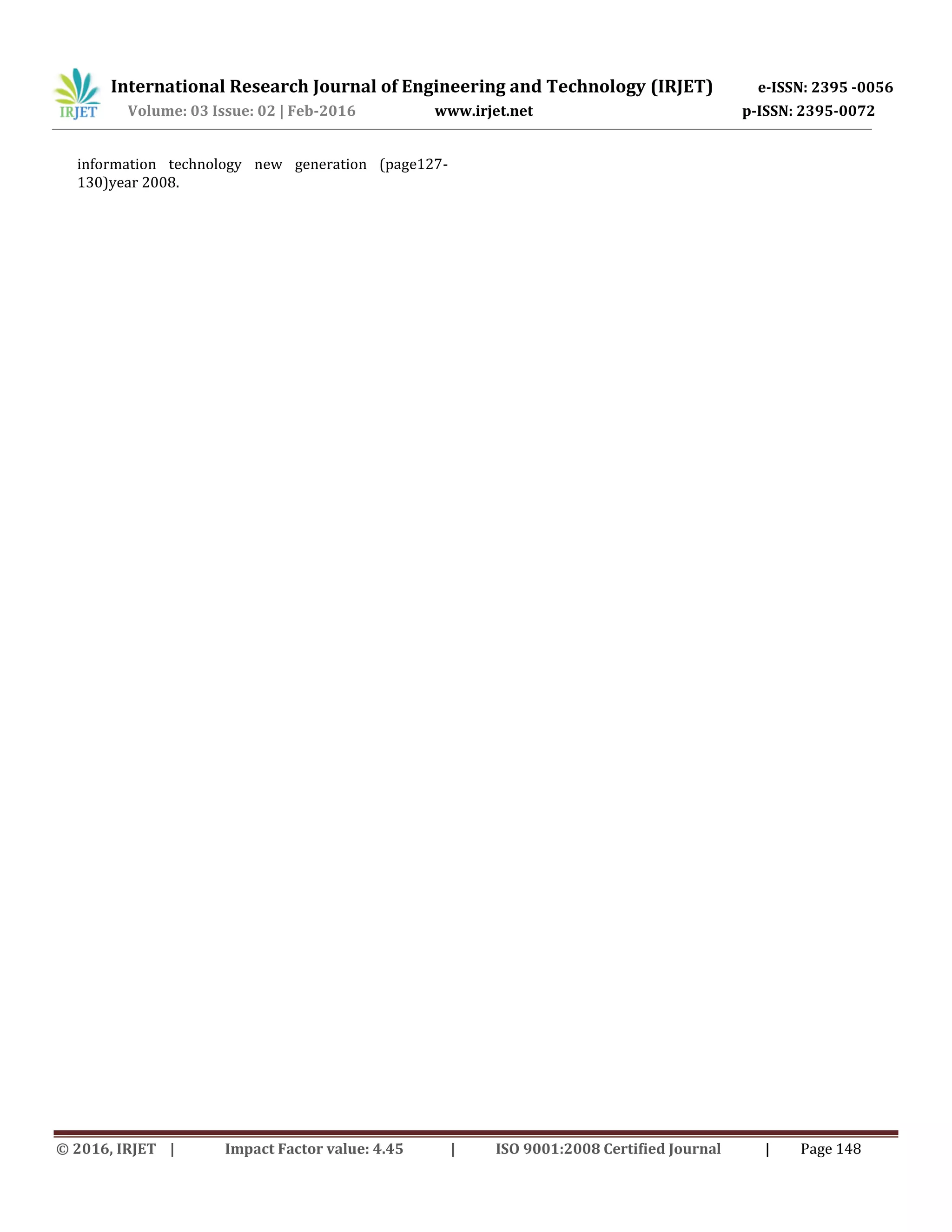
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395 -0056 Volume: 03 Issue: 02 | Feb-2016 www.irjet.net p-ISSN: 2395-0072 © 2016, IRJET | Impact Factor value: 4.45 | ISO 9001:2008 Certified Journal | Page 144 keysystem is that can provide a method for digital signatures. Authentication via secret key system. a disadvantage of using public key cryptography for encryption is speed they are very slow in processing. 2.LITERATURE SURVEY Rahul bhatnagar et al.(2013) in security in cloud computing have proposed an analysis of technical component and some research in threats for cloud computing users and threats for cloud service providers then provide many security, data and privacy protection, virtualization security, security arichitecture, model and frame work, security management and audit technology. shivashankar ragi(2011) with in a research thesis security approach for protecting data in cloud computing have described the security threats and identify the safety approaches for security in cloud computing and measured the protection challenges and security methods of clouds. in cryptography the advanced encryption standard(AES) is a symmertic key encryption standard. each of these cipher has 128-bit block size ,bit respectively[1]. survey of cryptography algorithm for cloud computing rashmi,manaoj jhuria,dr.shailendra.author discuss about the cloud computing is the emerging field in the modern era.cloud computing is defind as the set of resources or services offered through the internet to the user on their demand by cloud providers. it conveys everything as service over the internet based on user demand ,for instance operating system, hardware, srorag. resources, and software.cloud computing conveys everything as a service over the web supports user demand.to secure the cloud storage[2]. AES in cryptography the advanced encryption standard is a symmetric key encryption standard each of these cipher has a 128-bit block size, with size of 128,192 and 256 bit respectively. elliptic cureve cryptography provides confidentiality and authentication of data between cloud.it explores data security in cloud computing by implementing digital signature and encryption[4].during the data transformation to the cloud we use standard encryption method to secure the operation and the storage of the data. holomorphic encryption to execuite operation and the storage of the storage of the data without decryption. it enables providing result of the calculations on encrypted data without knowing the raw data on which the calculation was carried out[5].the management of security in cloud computing ramgovind s.et.al[2010].in this paper author discuss about the management of the cloud computing. cloud computing is new and emerging information technology that changes the way it architectural solution are put forward by means of moving towards the theme of virtualization of data storage,of local networks as well as software cloud computing. has elevated it to newer limits by offering the market environment data storage and capacity with flexible scalable computing processing power to match elastic demand and supply. using cloud computing can help in keeping on as it budget to a bare minimum. cloud computing can computing can deliver a real time using many different types resources such as hardware, software, virtual storage once logged on to a cloud[6]. data security in cloud architecture based on diffie hellman and elliptical curve cryptography neha tirthani ganesan r. in this paper, author discuss about the data security in cloud computing. now a days, cloud computing becomes a difficult task. cloud computing refer to a network computer,connected through internet, sharing the resources given by cloud providers. cloud computing is a model for enabling convenient , on demand network access to a shared pool of configurable computing resources. the security in cloud computing is big issue the security threats such as maintenance of data integrity, data hiding and data safety dominate[7]. 3.PROPOSED WORK RSA: This is an internet encryption and authentication system that uses an algorithm developed in 1977 by Ron Rivest, adi shamer,and leonard adleman.the RSA algorithm is the most commonly used encryption.till now it is the only algorithm used for private and public key generation and encryption.it is a fast encryption. KEY GENRATION Before the data is encryption key generation should be done. this process is done between the cloud service provider and the user.](https://image.slidesharecdn.com/irjet-v3i226-171024082410/75/Secure-Cloud-Environment-Using-RSA-Algorithm-2-2048.jpg)
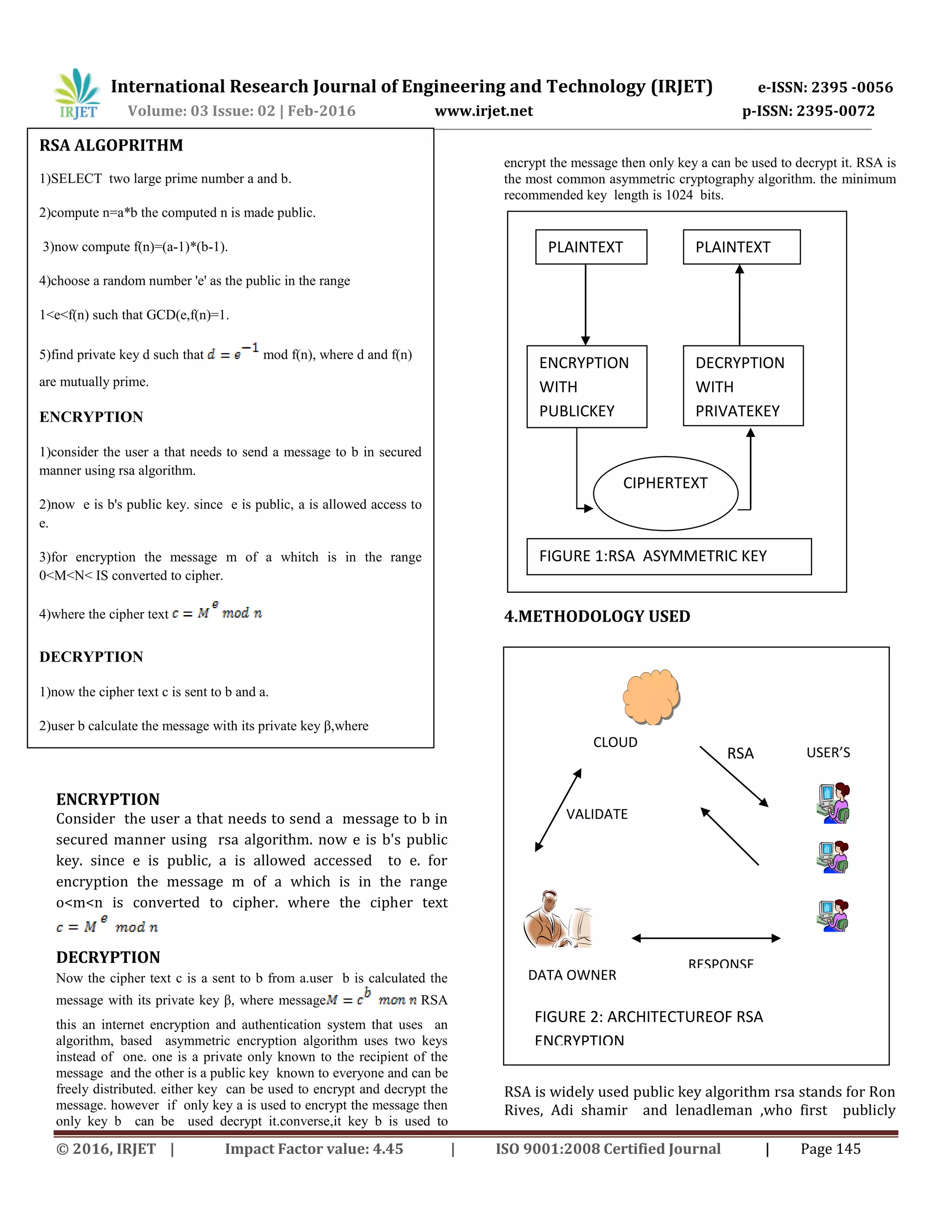
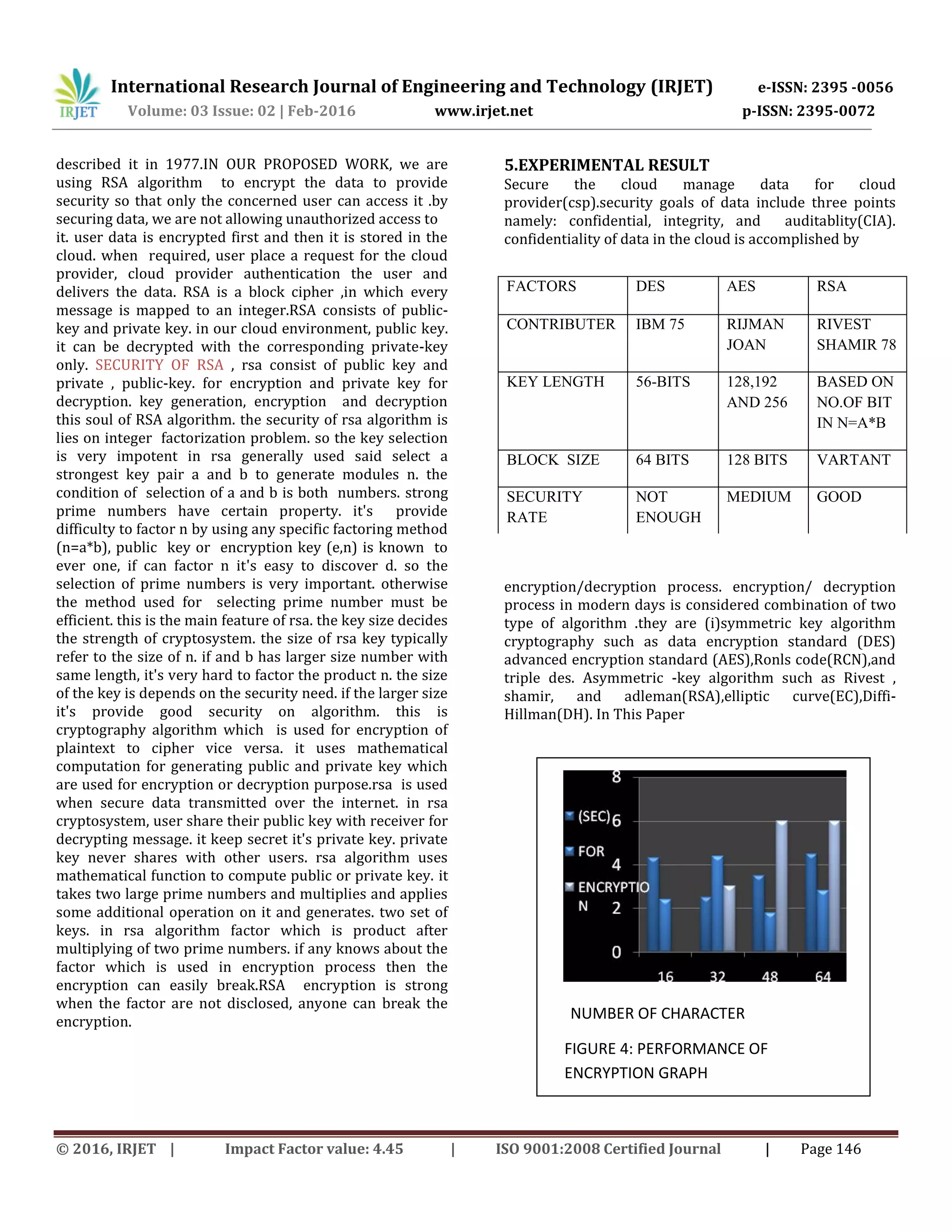
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395 -0056 Volume: 03 Issue: 02 | Feb-2016 www.irjet.net p-ISSN: 2395-0072 © 2016, IRJET | Impact Factor value: 4.45 | ISO 9001:2008 Certified Journal | Page 147 asymmetric algorithm are those algorithm which, use the same key for both encryption and decryption. hence the key is kept secret. symmetric algorithm have the advantage of consuming too much of computing power and it works with high speed in encryption. symmetric key algorithm are divided into two types: block cipher and stream cipher. in block cipher input is taken as a block of plaintext of fixed size is applied on to block of the same size as the block of plaintext is obtained. in rsa cryptosystem, used share their public key with receiver for decryption message. it keep secret it is private key never shard with other user. for this paper different type algorithm to compare secure algorithm. in this Table efficient cryptosystem can produce best possible result if key size comparable to the size packet to be transmitted over the network. algorithm on the basis of parameter like key length, block size, type and features. As we know that the data is stored on some else location in the cloud computing so we need high processing speed as well as high security. here the graph shows the performance of our proposed scenario. Bars are showing that how much time it will take to encrypt data. different experimental result are shown in the graph which are done on the basis of different experiments. 6.CONCLUSION cloud computing is the latest trend in it. but security is the biggest challenge in this area. each and every day new security prevention method is discovered, but it's not a permanent solution. encryption is the best security method , now different kinds of encryption technique apply in cloud computing environment , some extend hacking can be prevented in this way. so it's very important to provide a good level security in this environment is the one of decide the strength of the cryptosystem, when we selected large key size prime number, its cannot be easily factored and discovered. so provide a good level security the keys used should be powerful. but generation main problem of RSA is increasing key generation time when we select large key size number, the key generation time is also increase, this problem can be solved by applying asymmetric key algorithm. a drawback of RSA using public key cryptography for encryption is speed they are medium process. FUTURE scope using various algorithm as described cloud security can be ensured in real time environment. REFERENCES [1] Guannan hu and wemhao zhu "A dynamic user integrated cloud computing architecture" proceedings of the 2011 international conference on innovative computing and cloud computing(Iccc,11).pp3640,2011 [2] Rashmi nigoti,Manoj jura,D.r shalendra singh, A survey of cryptographic algorithm for cloud computing, international association of scientific innovation and research. [3] Priyanka arora,aran singh,himanshu tyagi "Evaluation and comparison of security issues on cloud computing environment" in world of computer science and information technology journal.(WCSIT)ISSN:2221- 0741 VOL.2,NO 5-179-183,2012. [4] M.Sudha,Dr,Bandaru rama krishna rao,m.monica, a compare sensive approach to ensure secure data communication in cloud environment, international journal of computer application (0975-8887)volume 12-no 8,dec 2010,pp-19-23) [5] Sameera abualrahaman almulla,chan yeobyeun, cloud computing security management engineering system management and is application(ICESMA),2010. [6] Ramgovind s, eloff mm,smith e,the management of security in cloud computing, 978-4244.2010 IEEE. [7] Neha tirthani ganesan r, data security in cloud architecture based on diffie hellman and elliptical curve cryptography. [8] Birend ragoswami, dr.s.nsingh, enhance security in cloud computing using public key cryptography with matrices,(IJERA).vol:2 issue 4,pp(331-334)2012. [9] Sheruf el-etrby, eman m.mohamed. modern encryption techniques for cloud computing, proceeding of the informatics and system 8th international conference ,cc-1,cc-6 year.2012. [10] Saffer jaboudl , mohamed a.al- fayoumil,2-mustafa al- fayoowni 3rd haidar s.jabbar.an efficient rsa public key encryption. schema,15th international conference on 0 2 4 6 8 16 32 48 64 (SEC) FOR DECRYPTION NUMBER OF CHARACTER FIGURE 5:PERFORMANCE OF DECRYPTION GRAPH](https://image.slidesharecdn.com/irjet-v3i226-171024082410/75/Secure-Cloud-Environment-Using-RSA-Algorithm-5-2048.jpg)