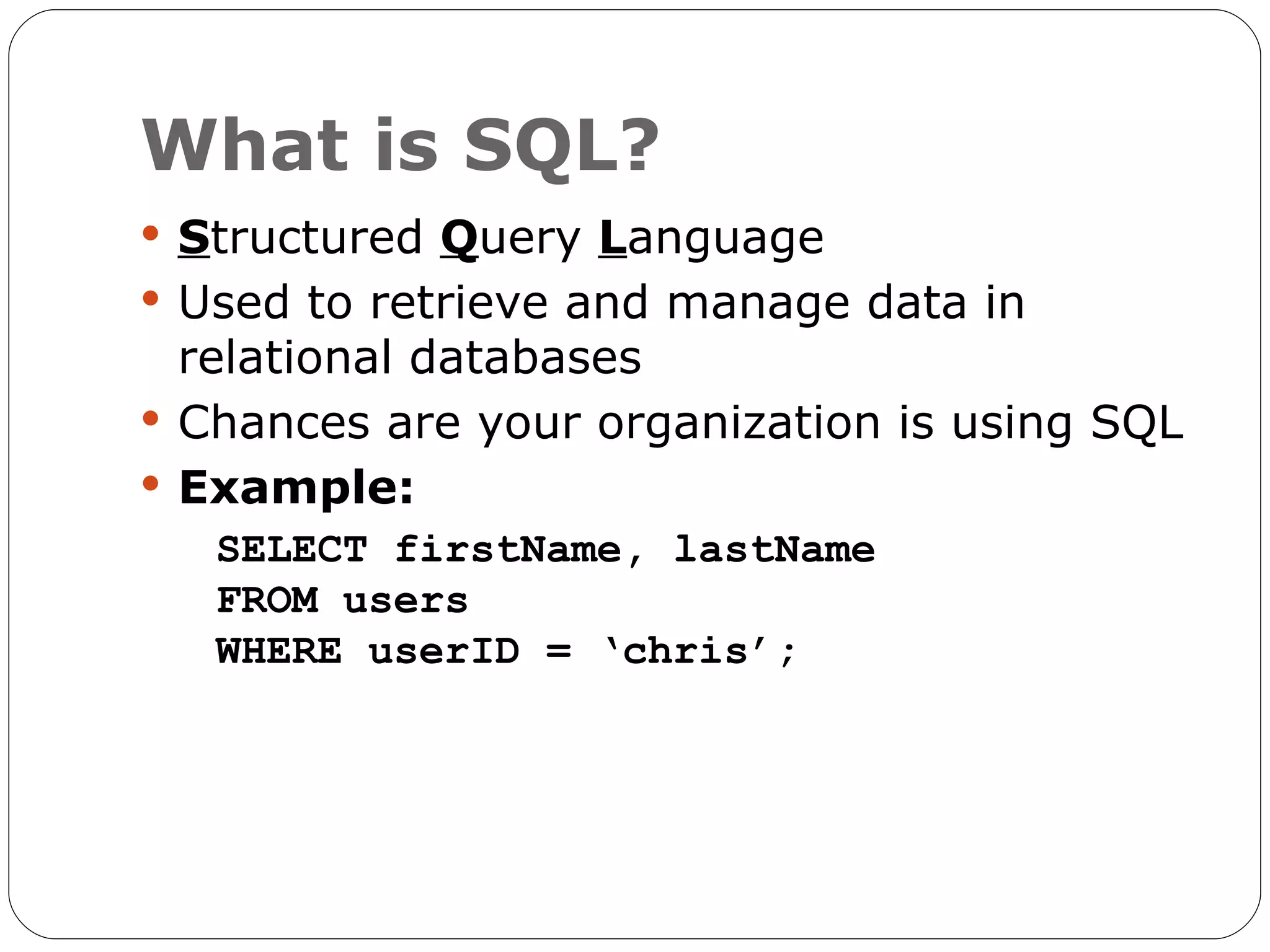
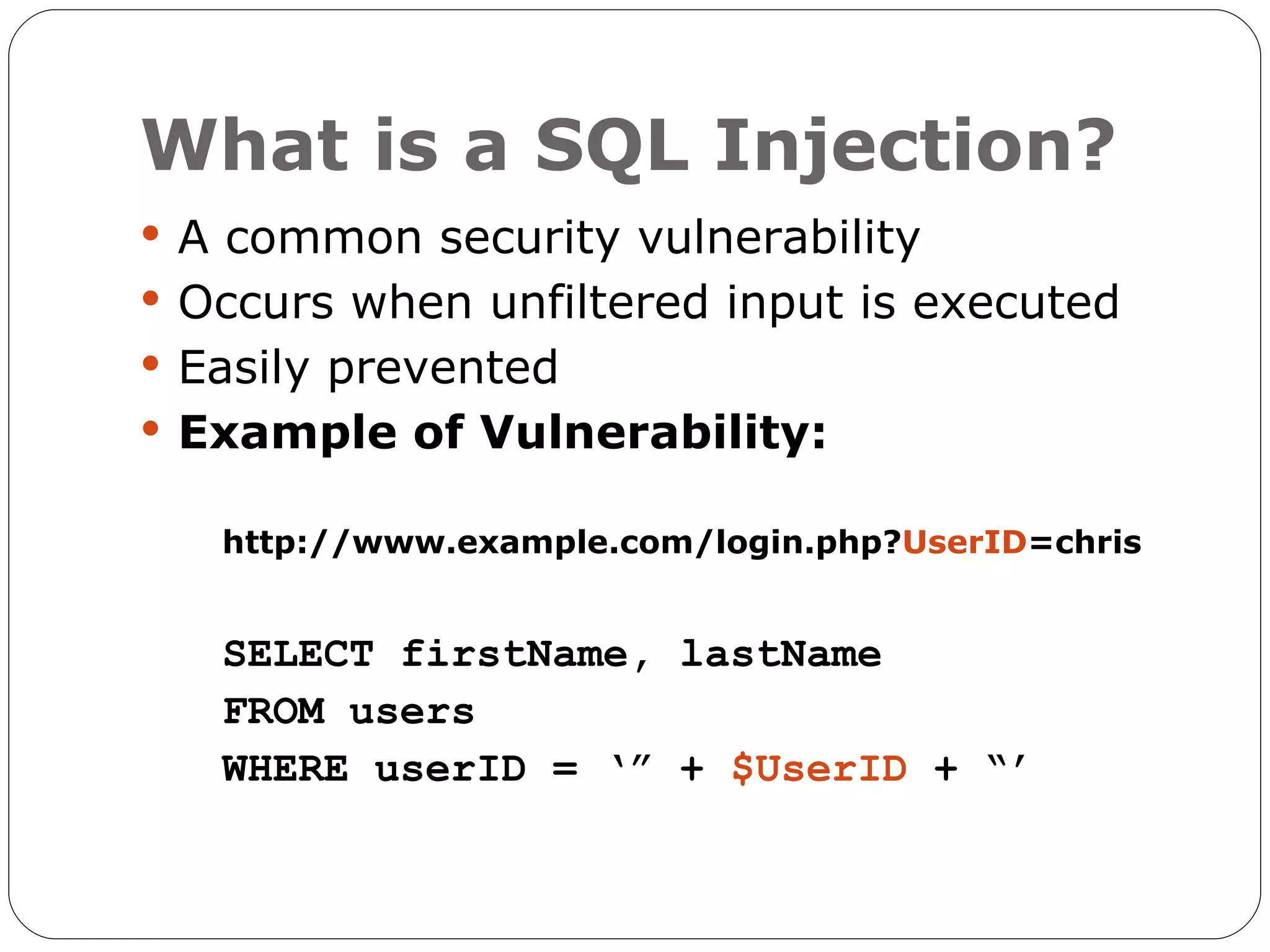
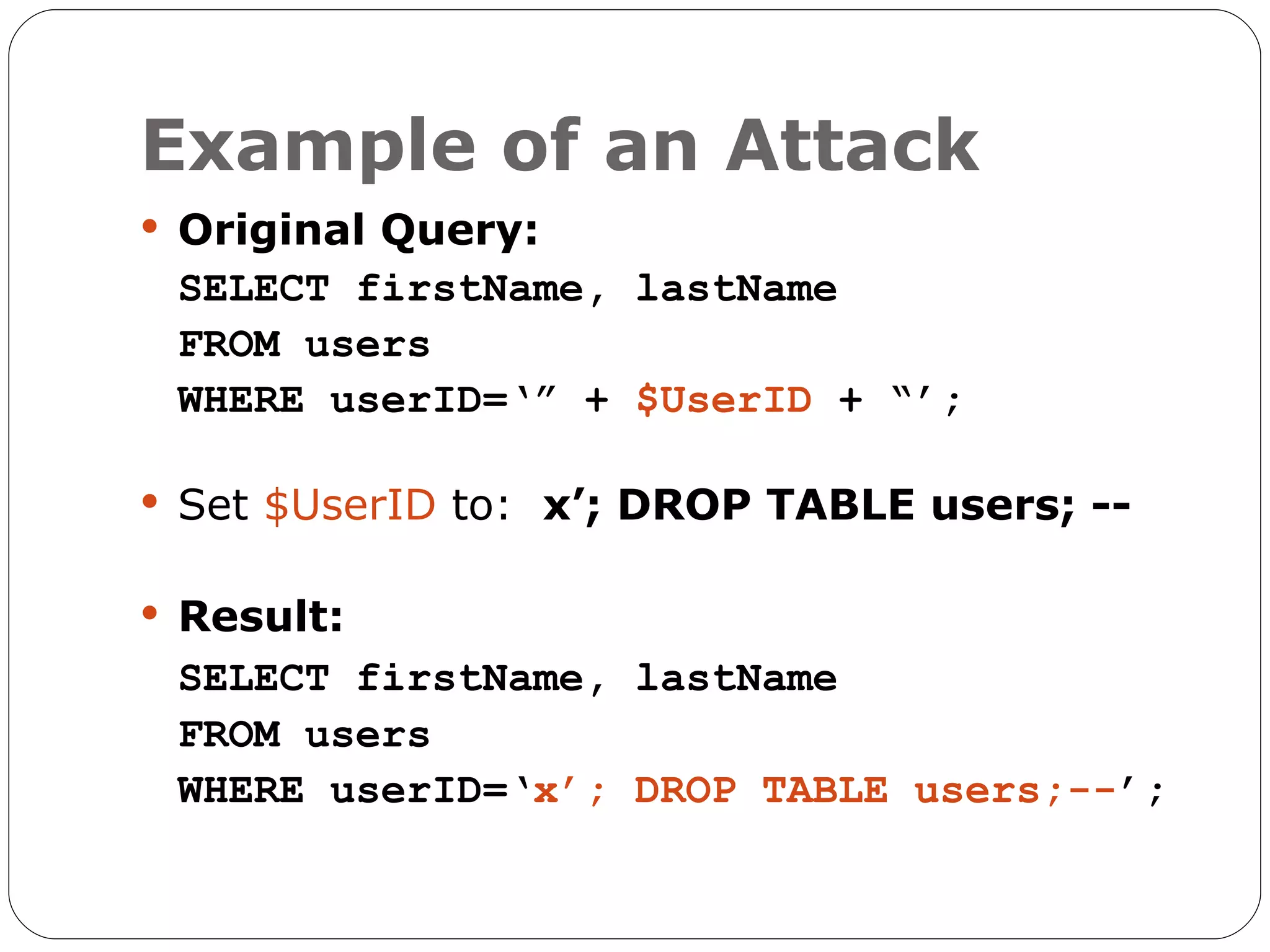
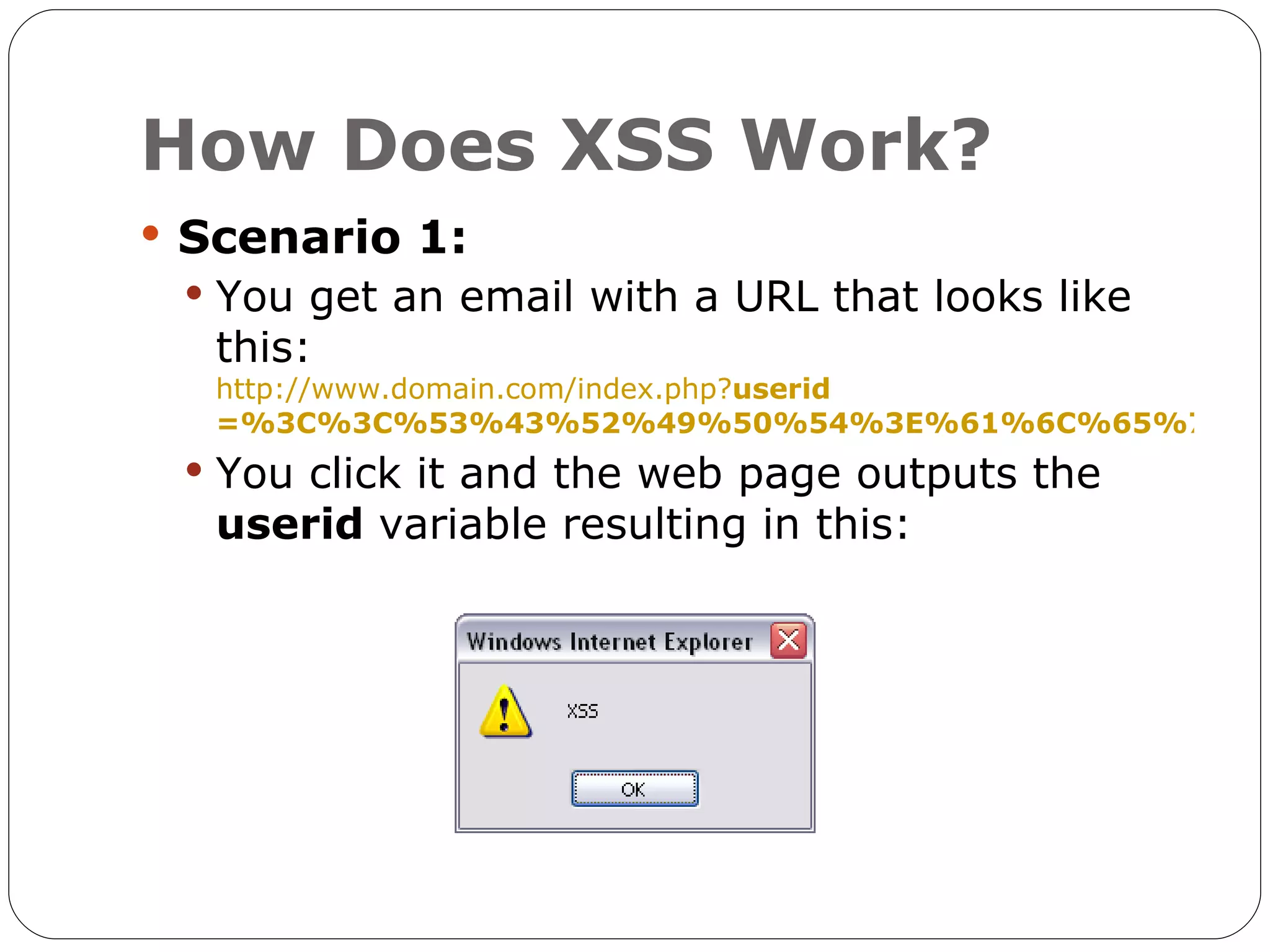
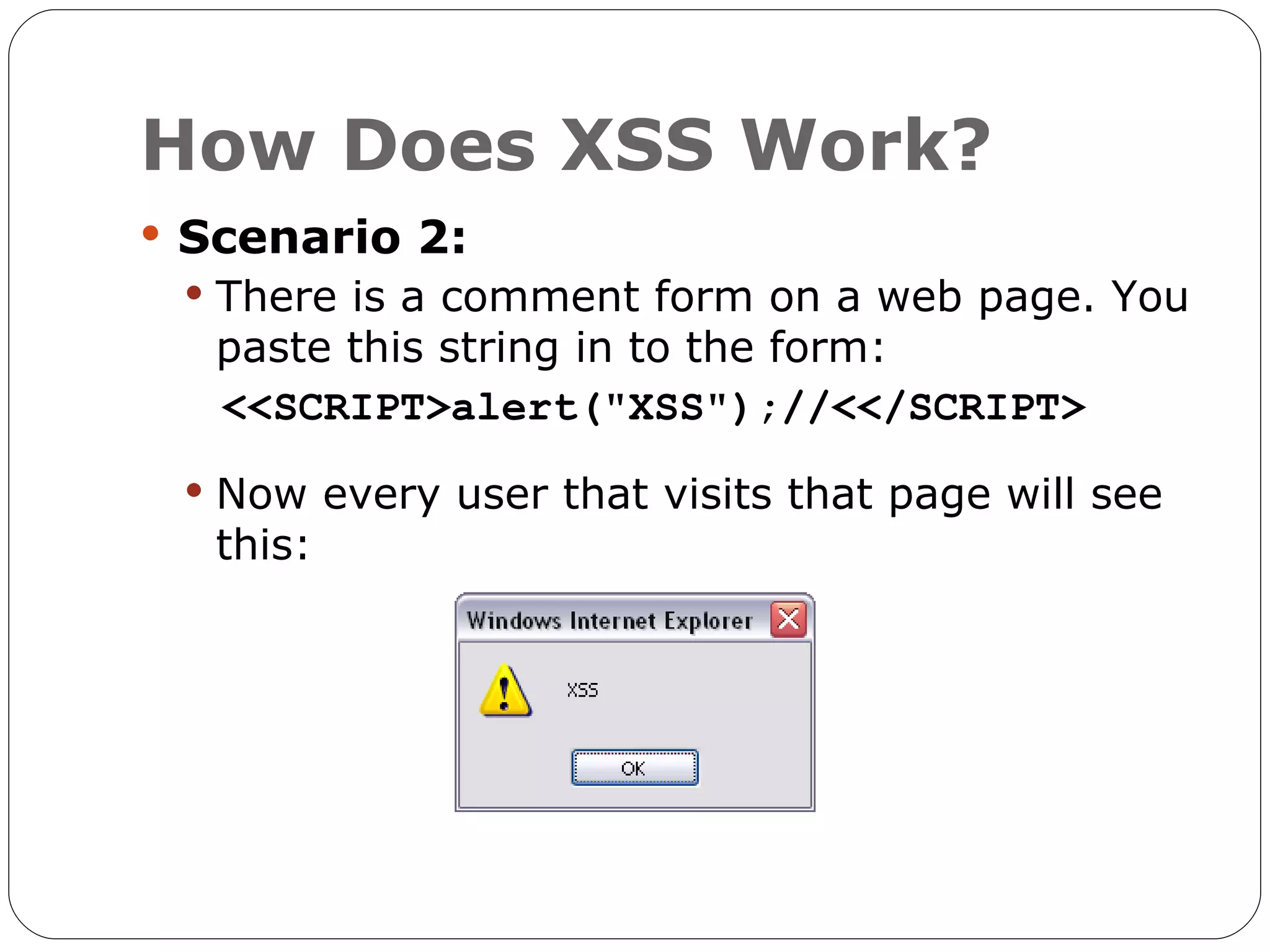
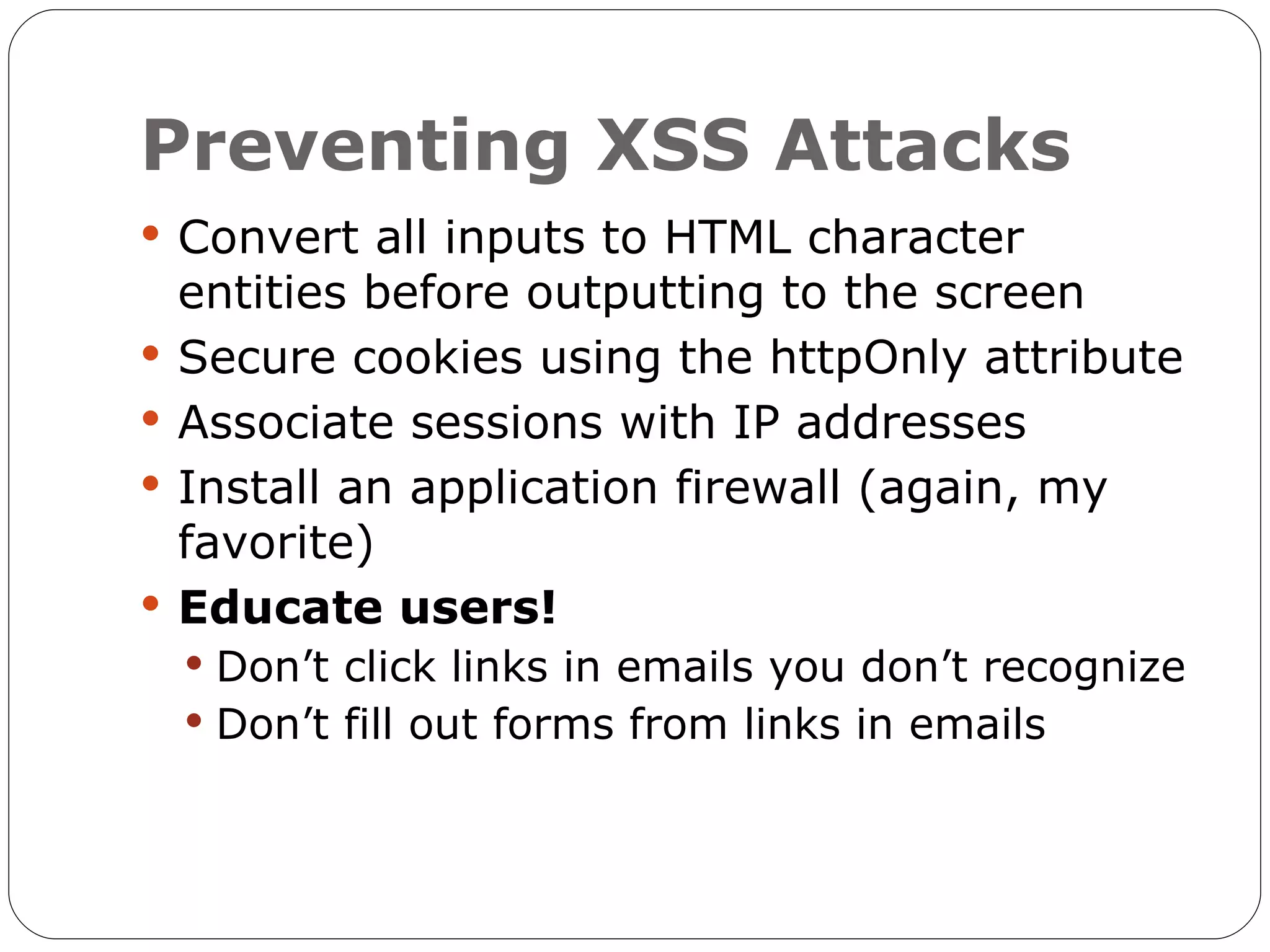
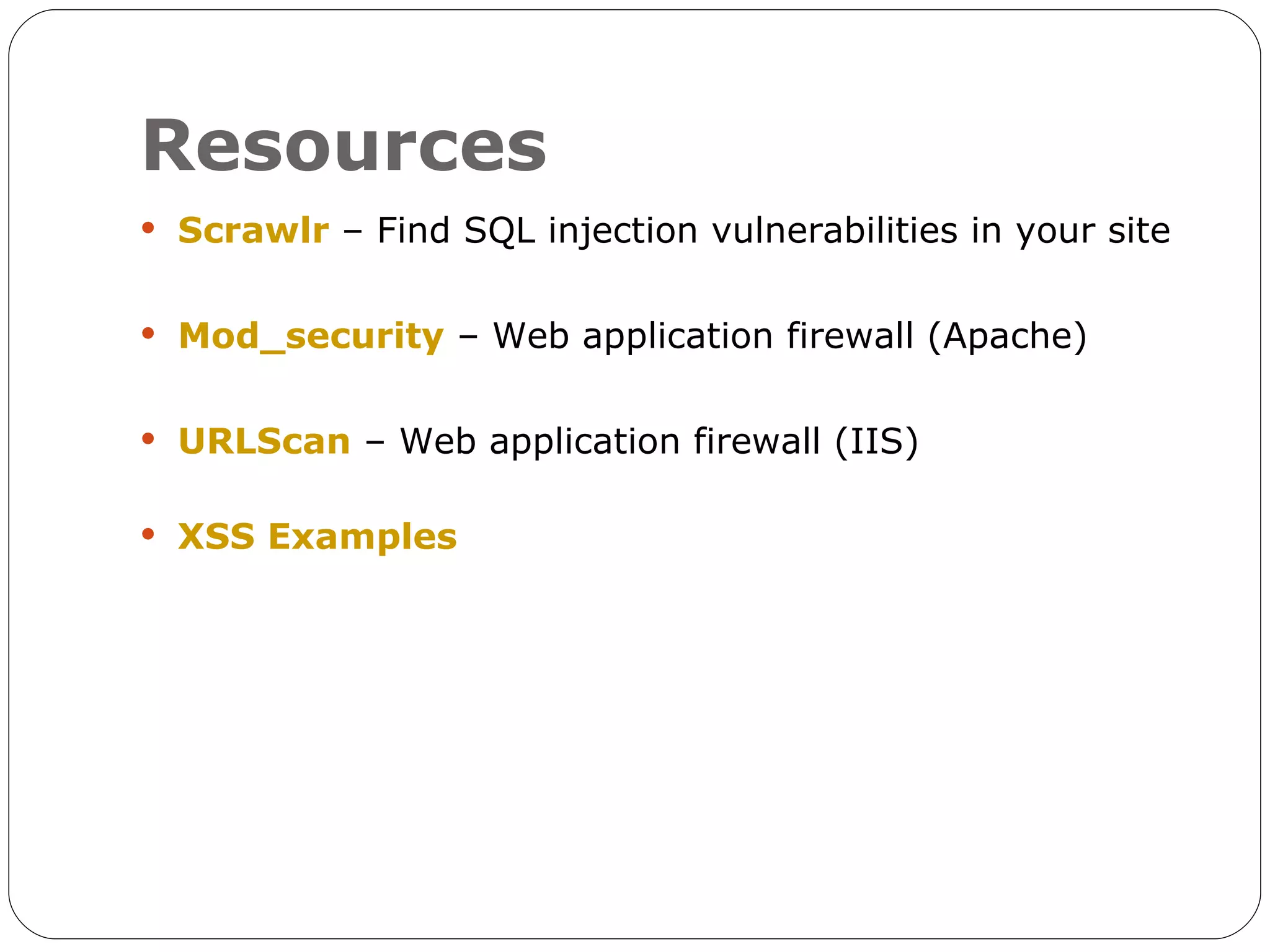
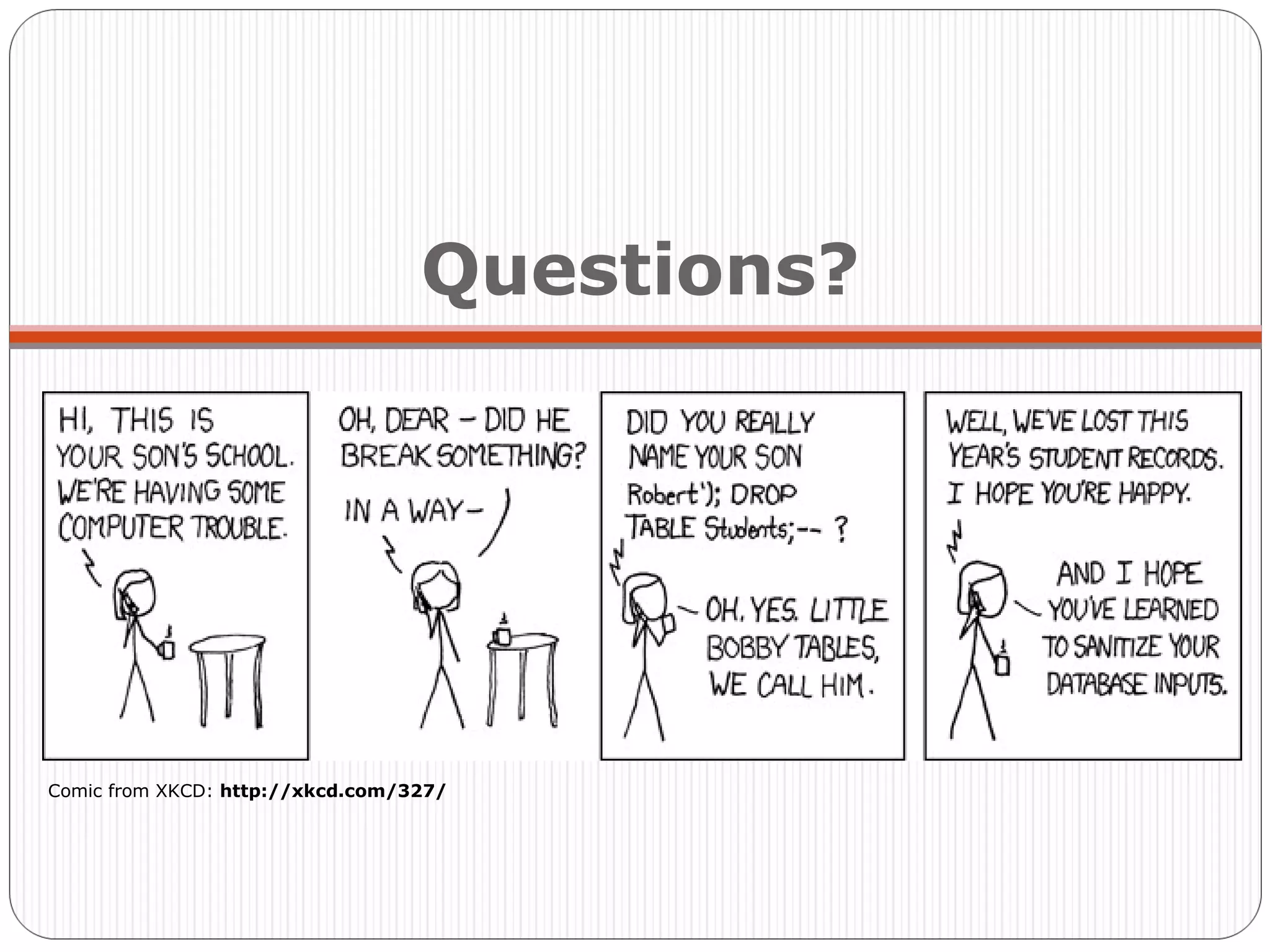
The document discusses the threats of SQL injection and cross-site scripting (XSS) vulnerabilities in web applications, including examples of attacks and their potential impacts such as unauthorized access, data loss, and identity theft. It offers strategies for preventing these attacks, including input sanitization, use of parameterized statements, secure cookies, and installing application firewalls. The author emphasizes the importance of proactive security measures and user education to mitigate these risks.