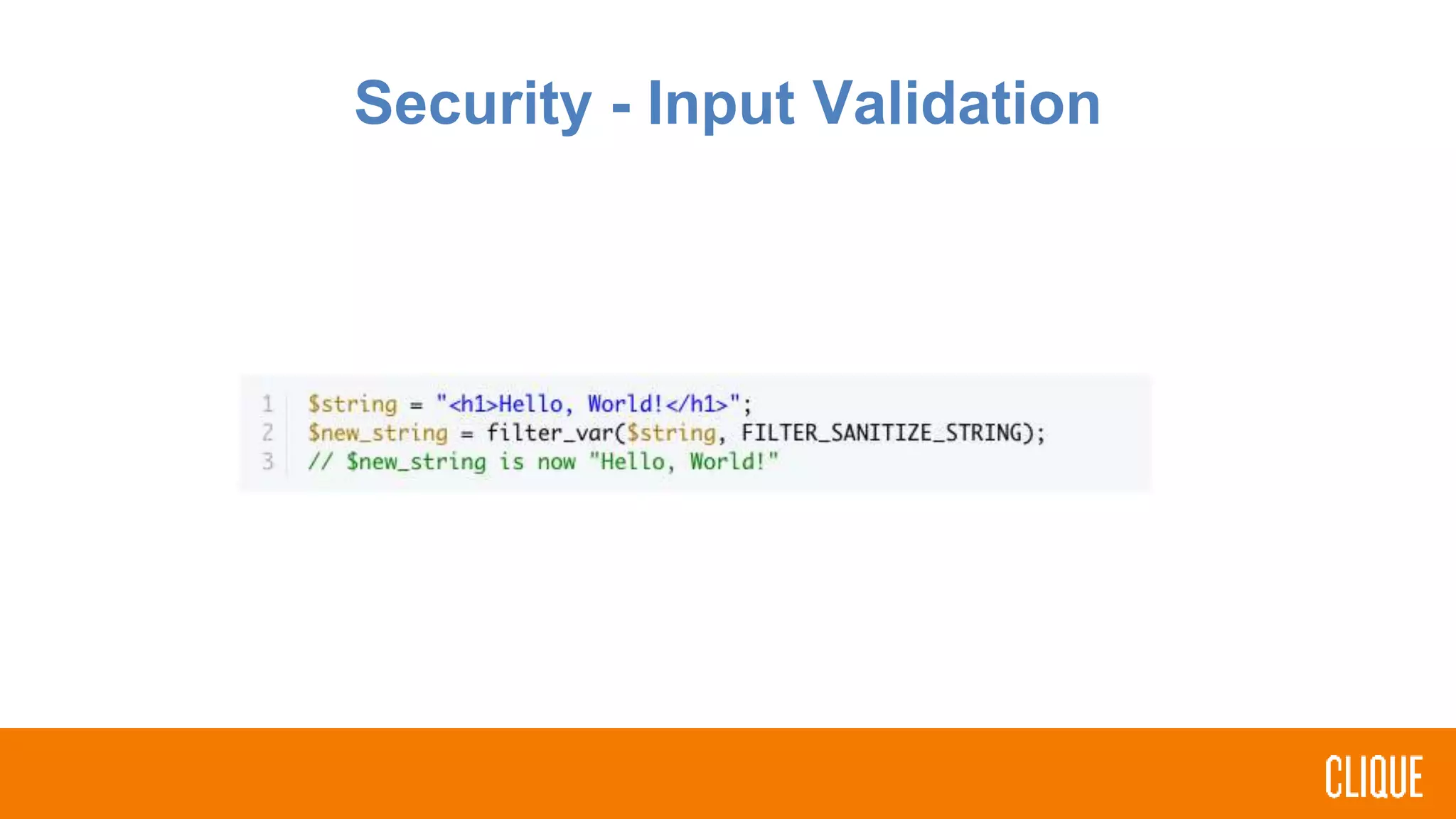
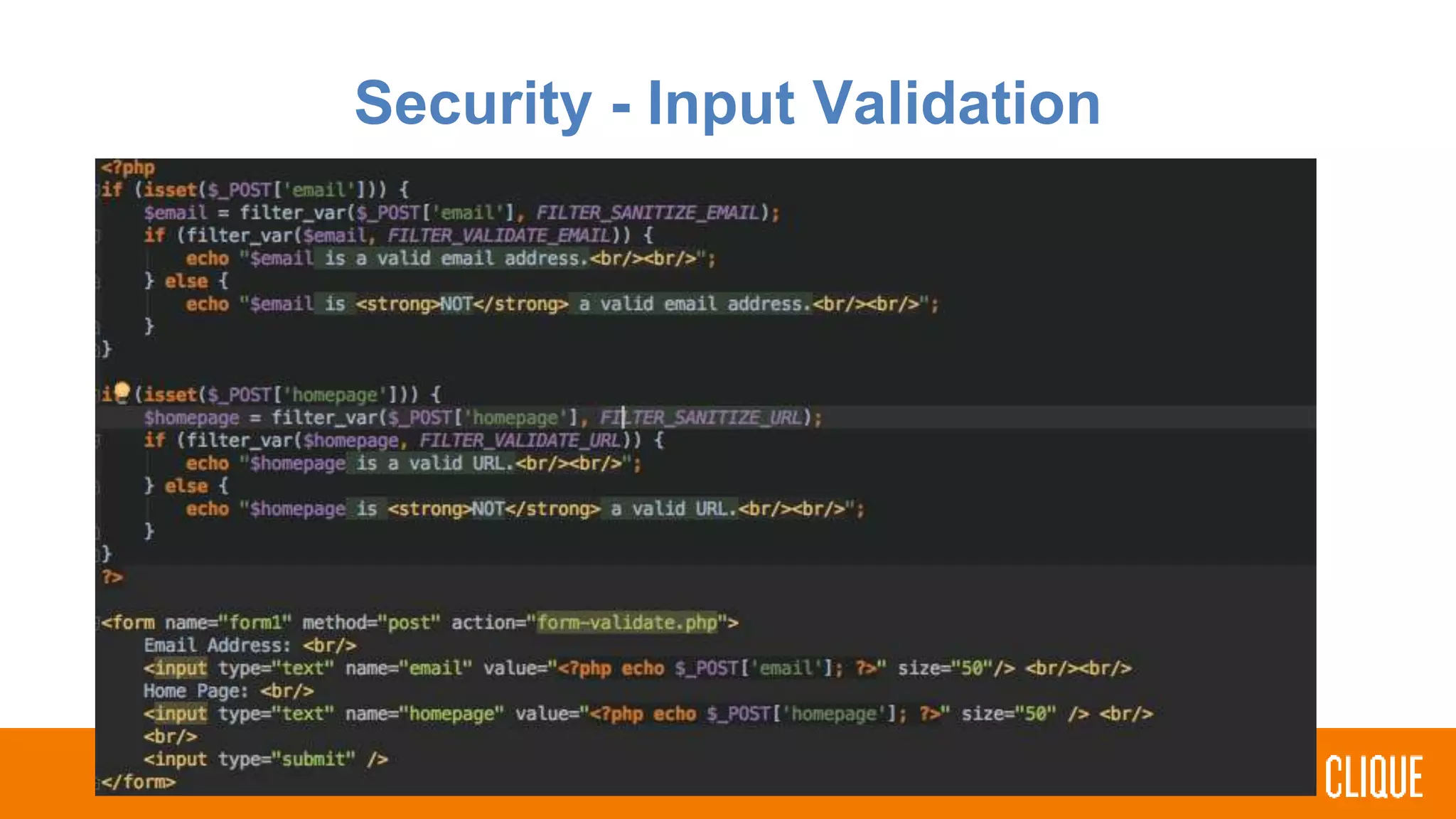
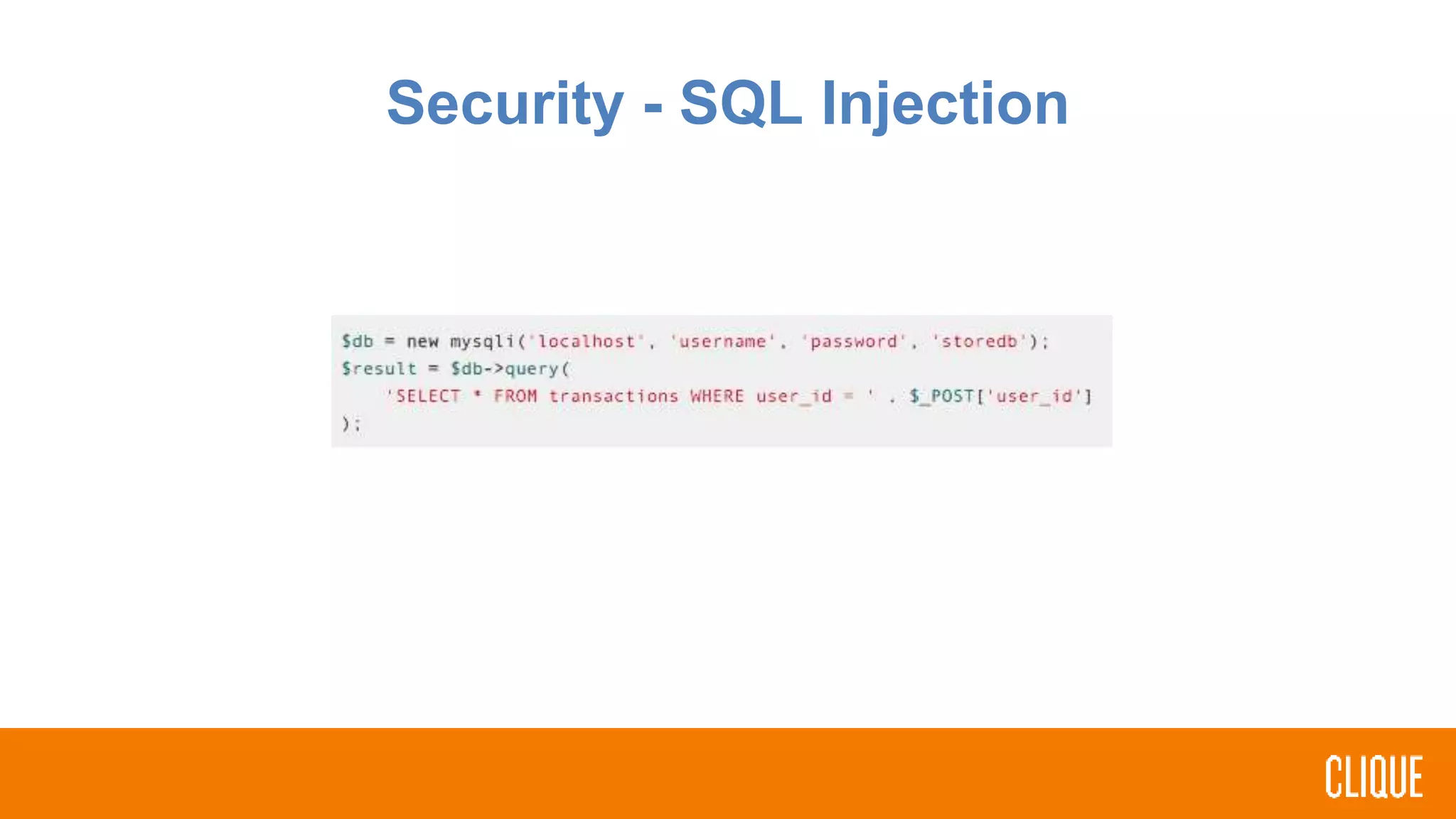
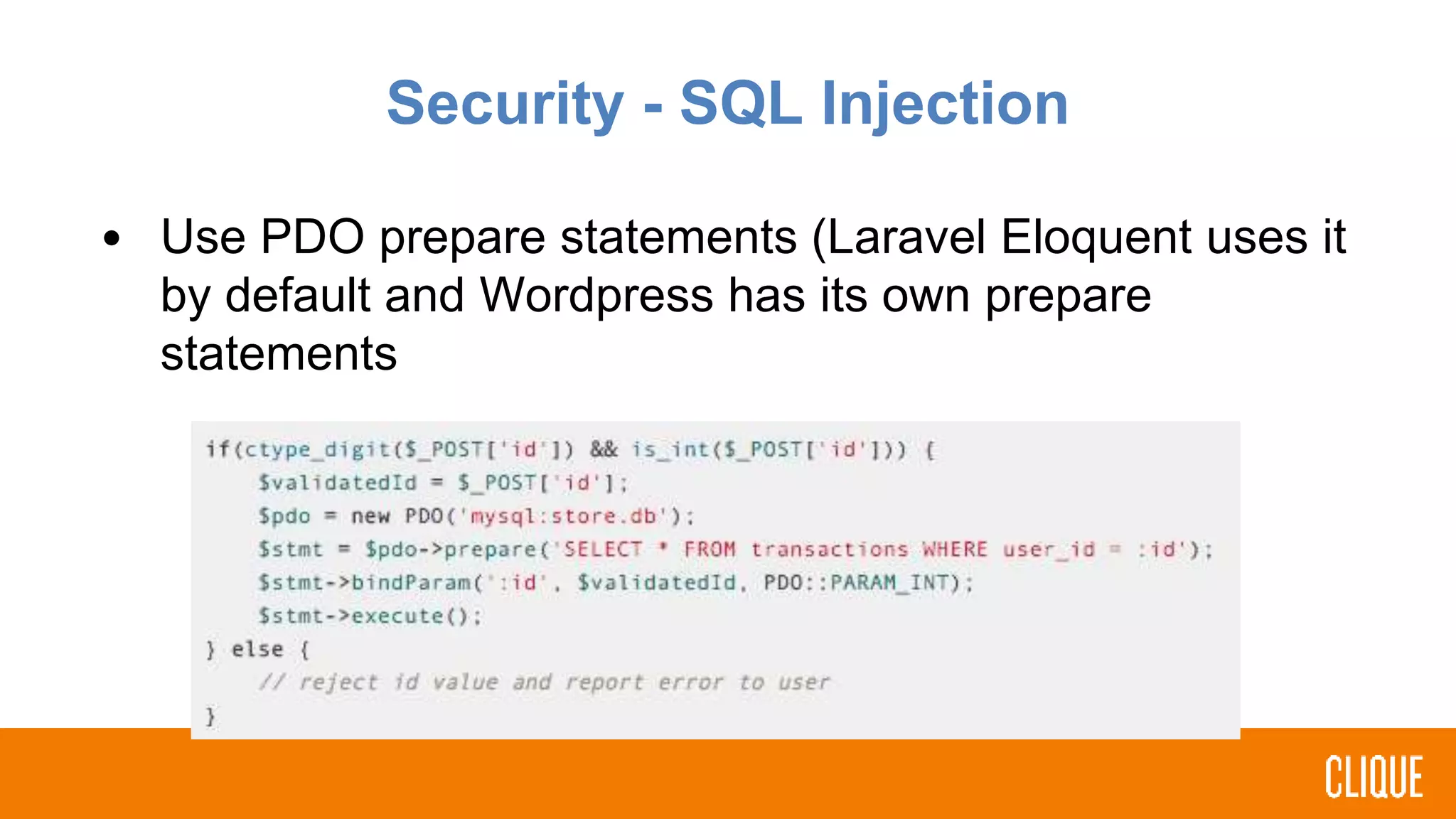
The document outlines best practices for writing safer, faster, and more robust PHP code, focusing on coding styles, practices, security, and error handling. It emphasizes the importance of using namespaces, adhering to PHP standards recommendations, and implementing input validation to prevent SQL injection. Additionally, it highlights the significance of handling errors and exceptions through standardized practices, encouraging developers to review and optimize their existing projects.