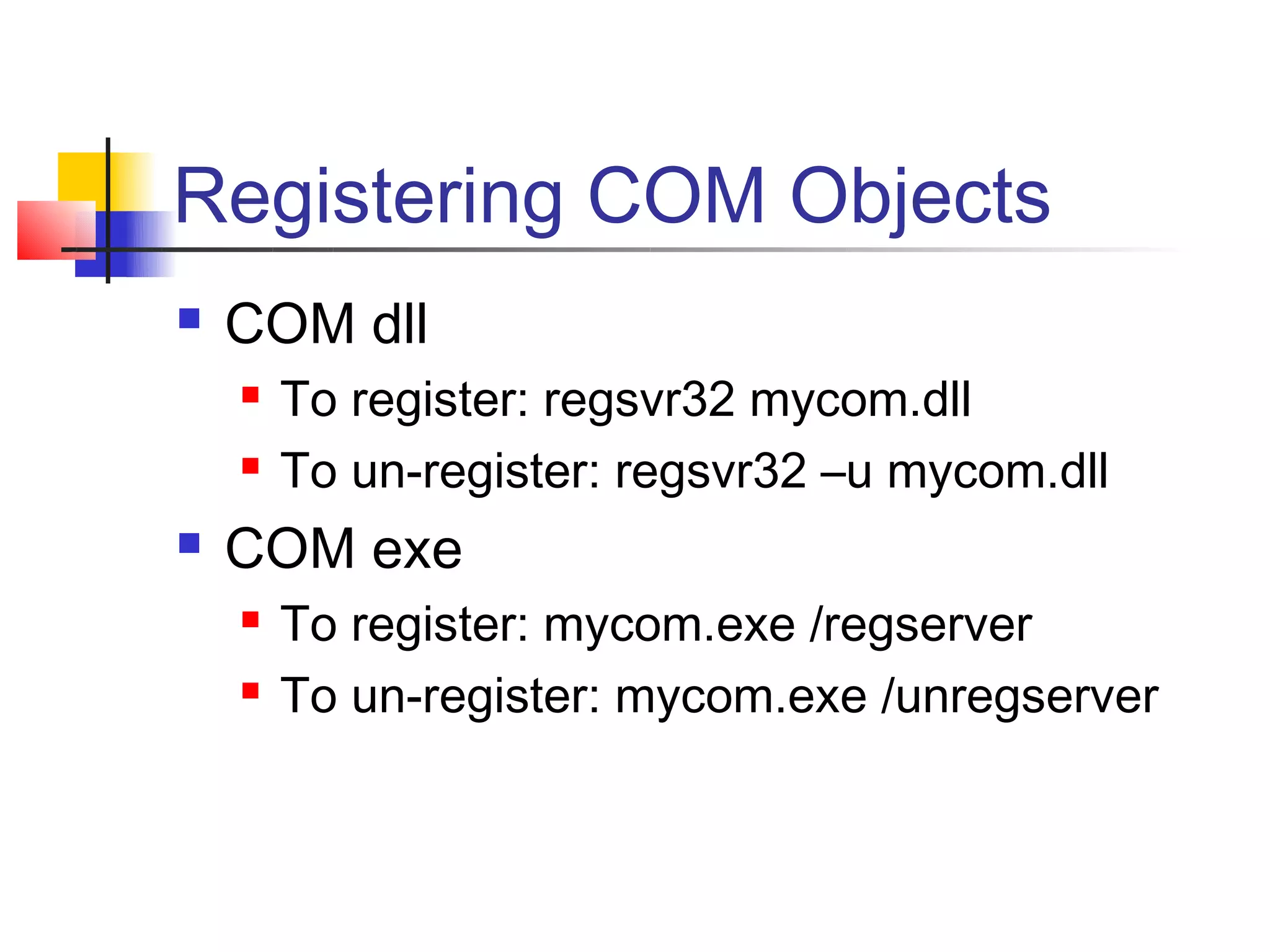
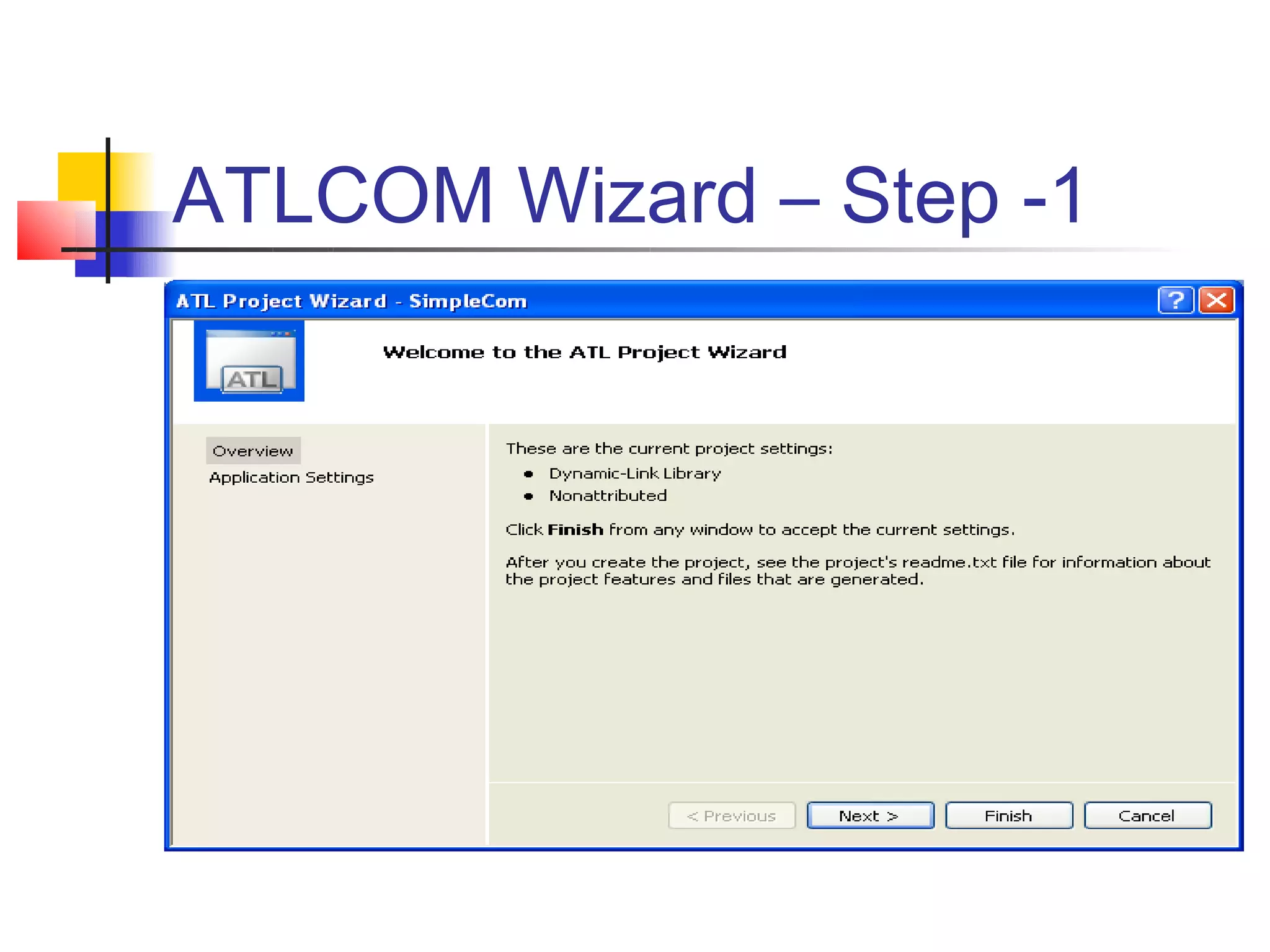
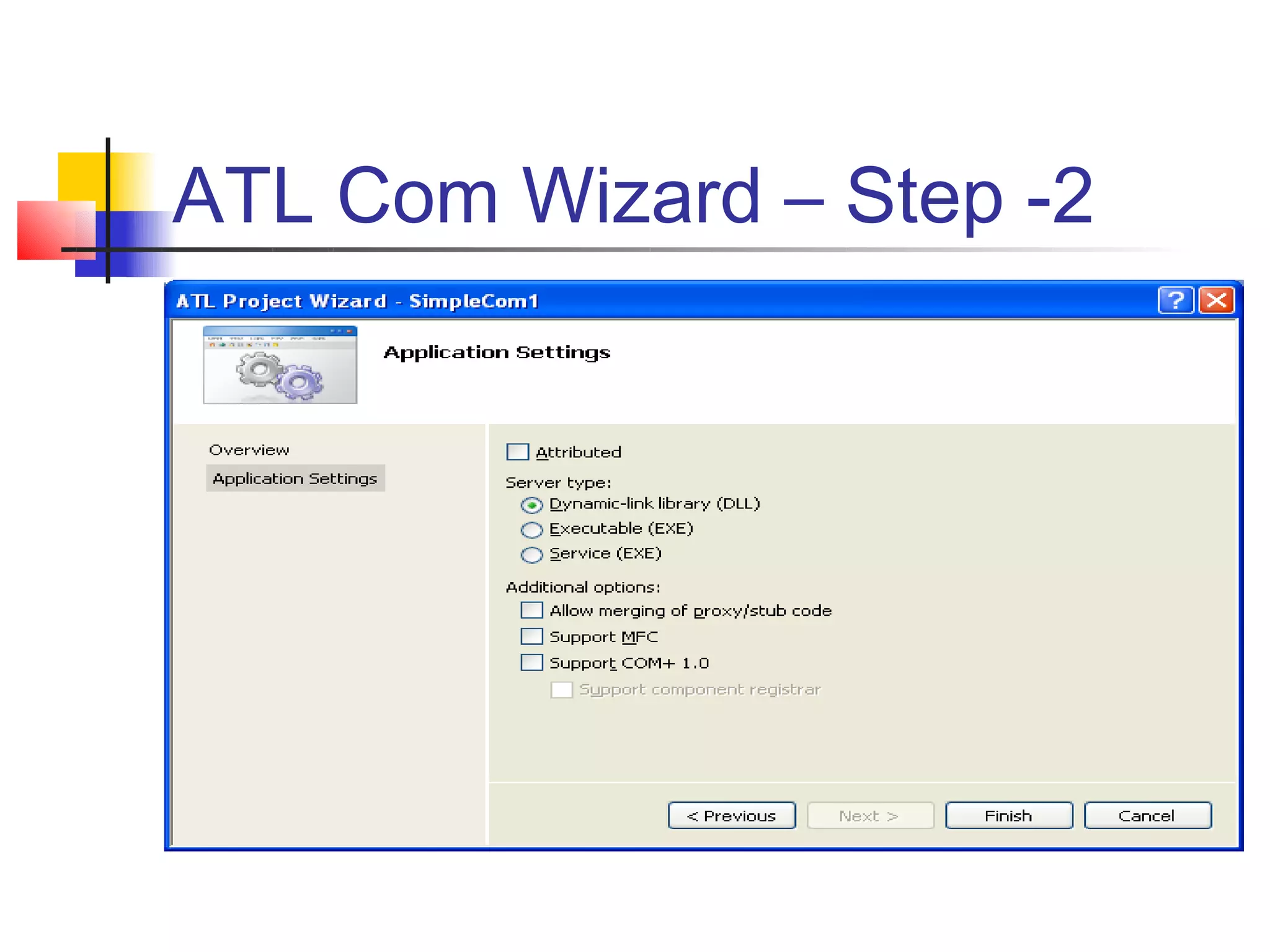
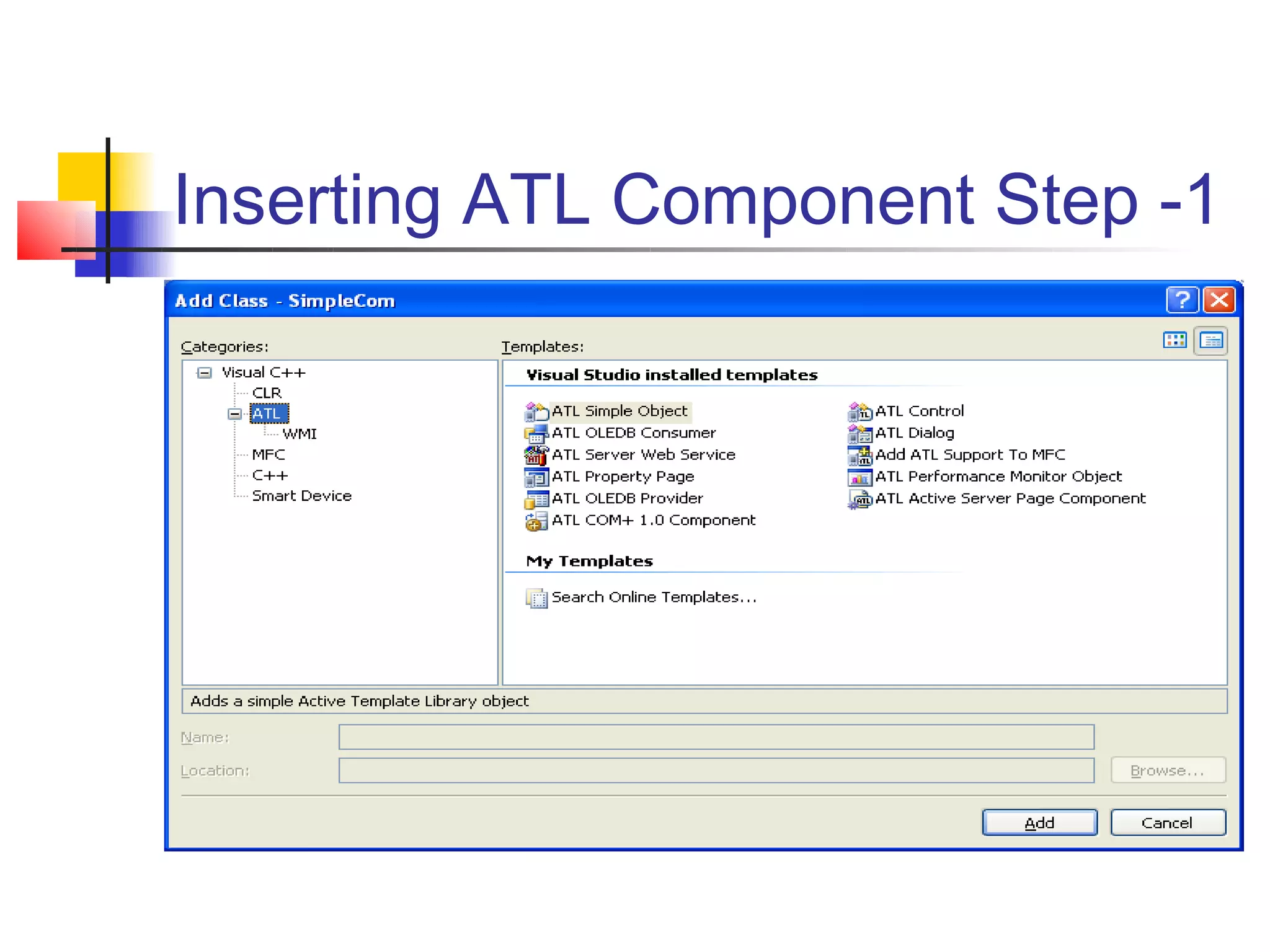
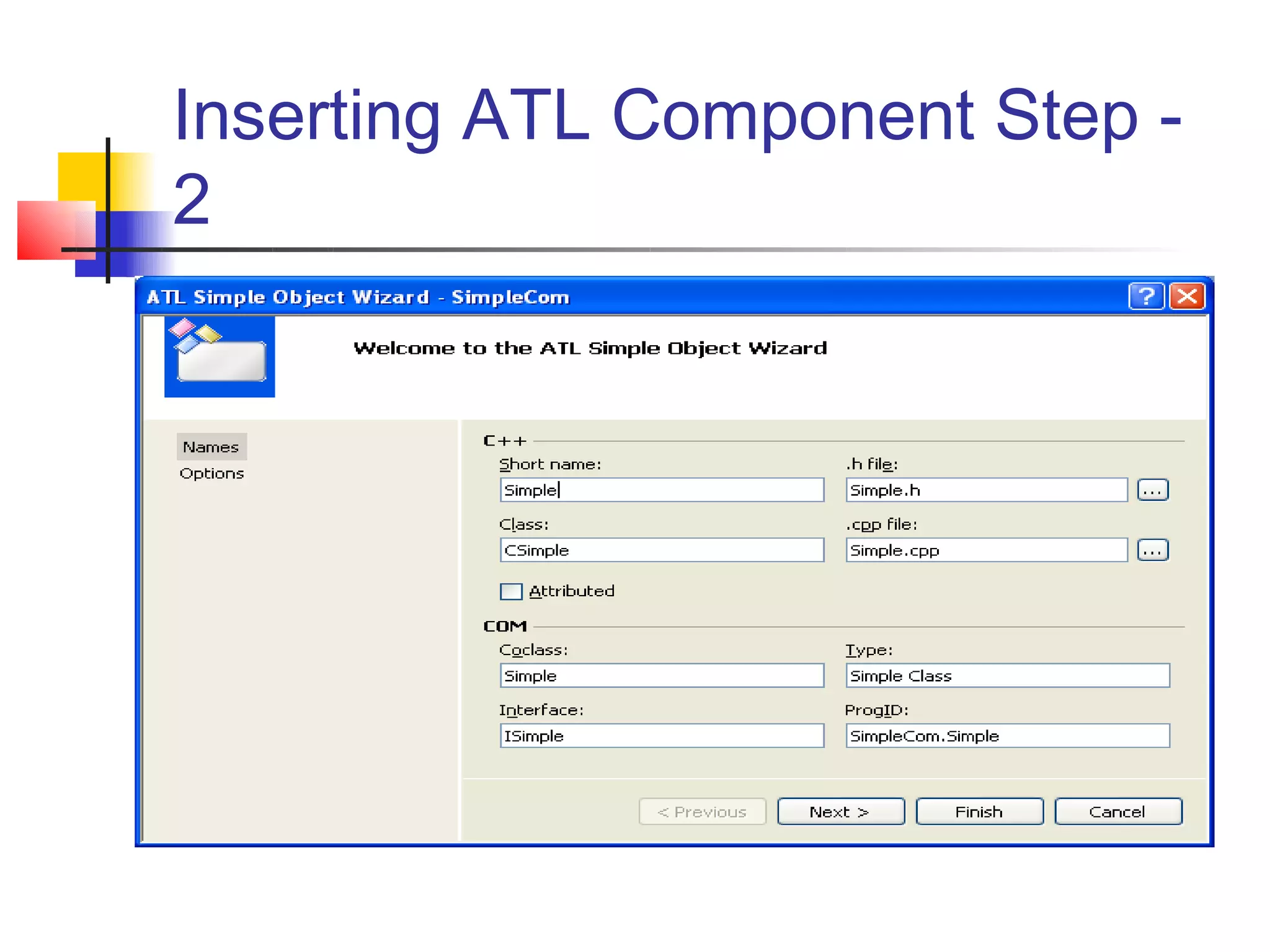
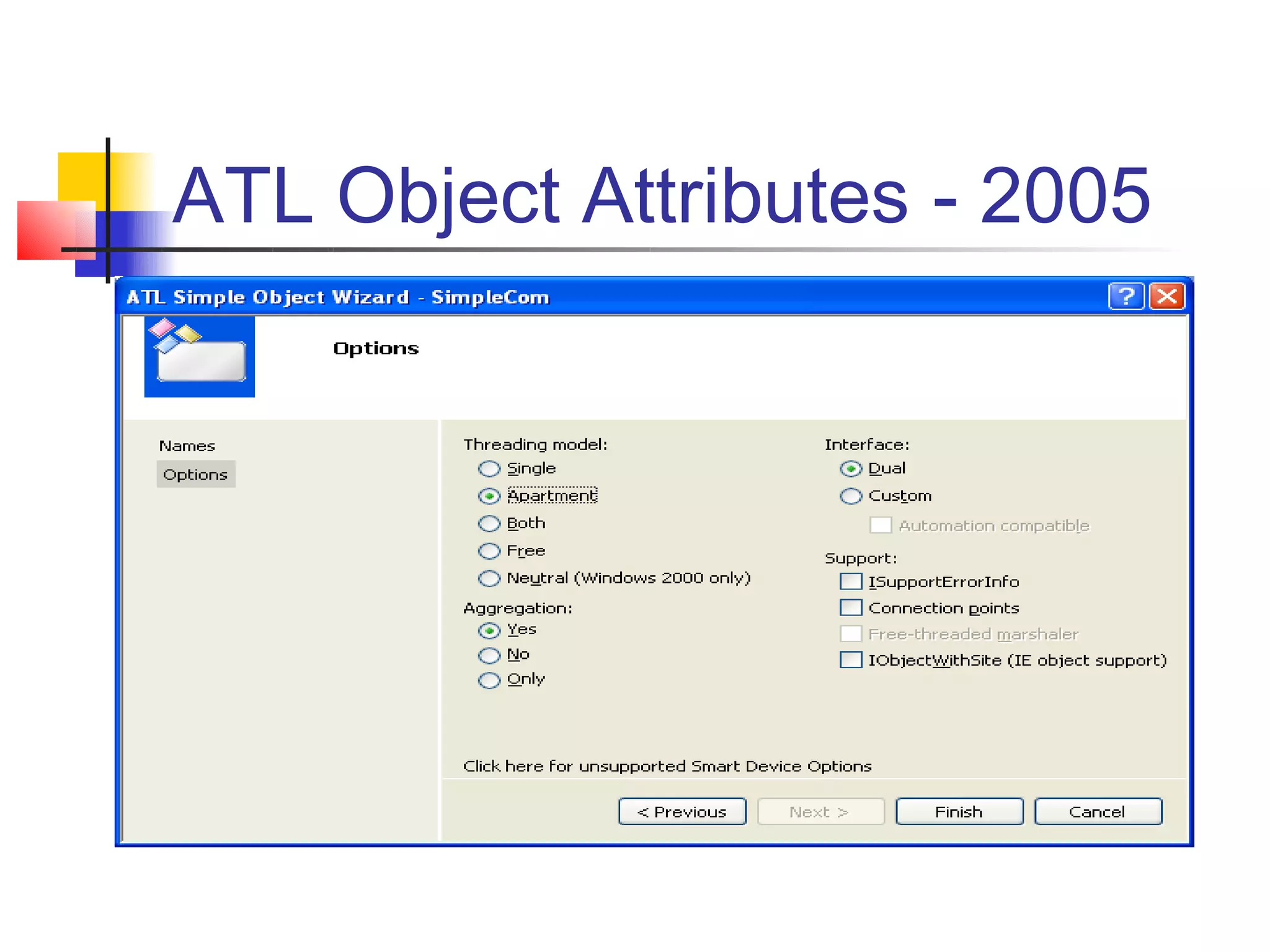
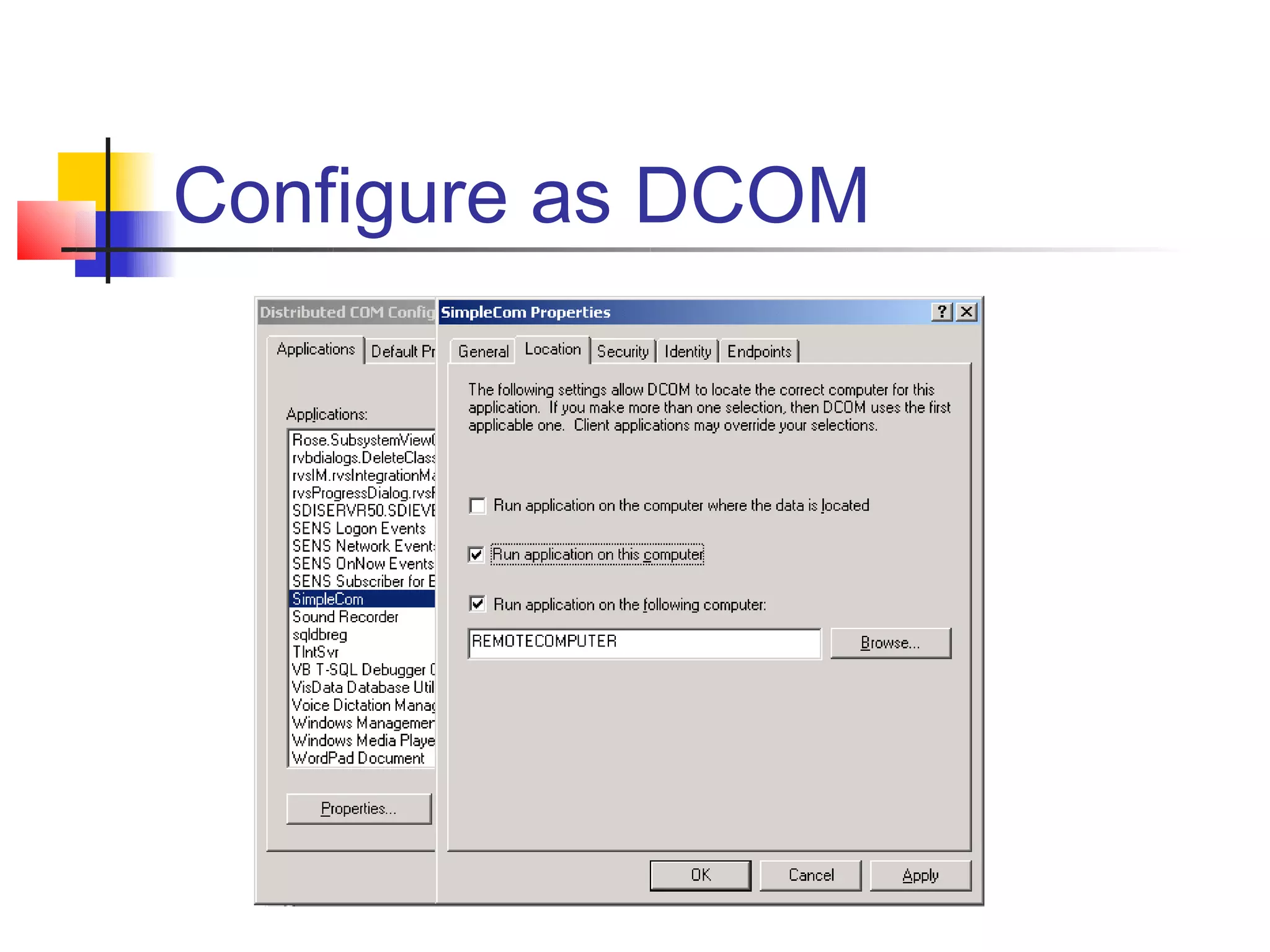
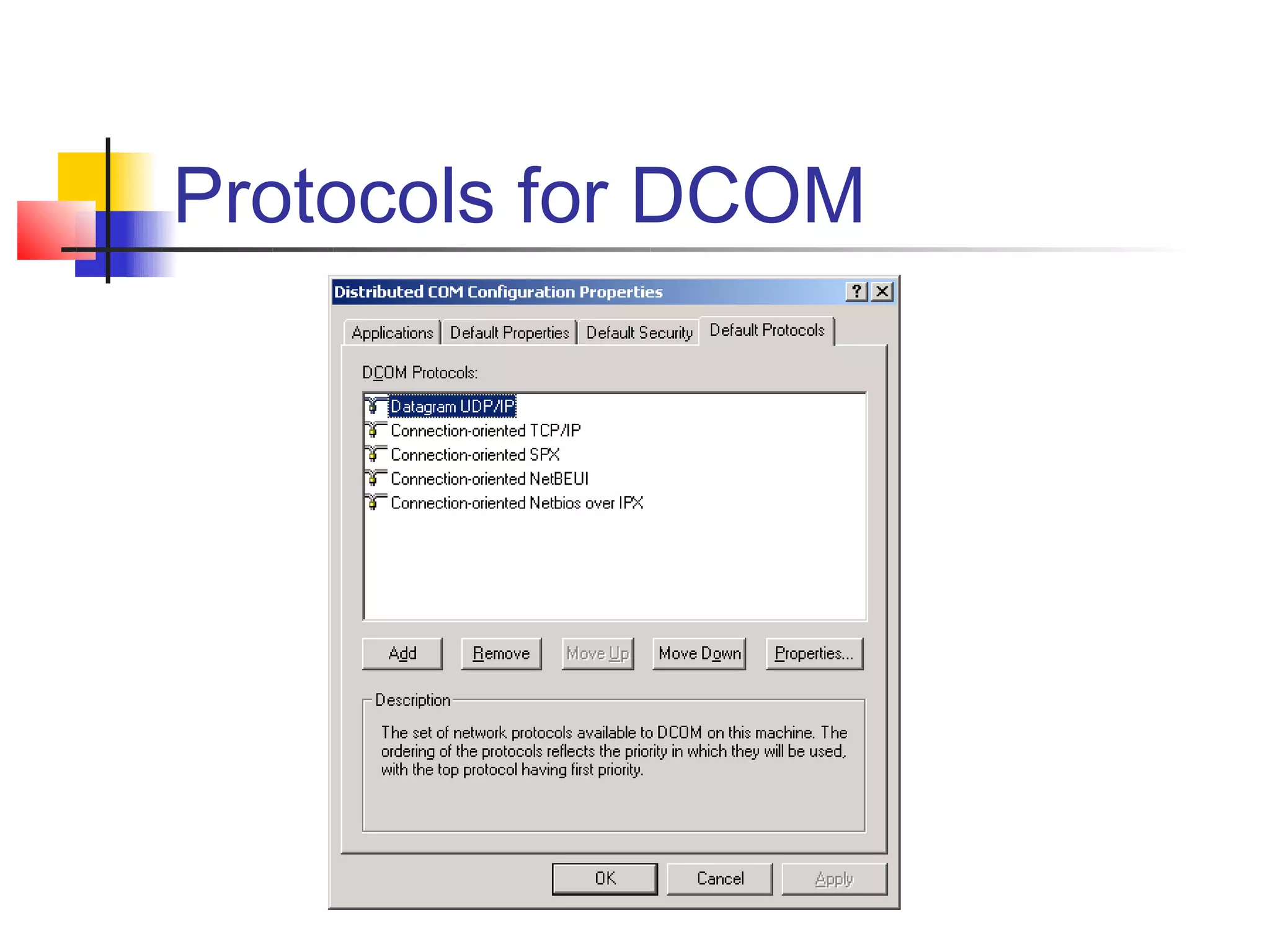
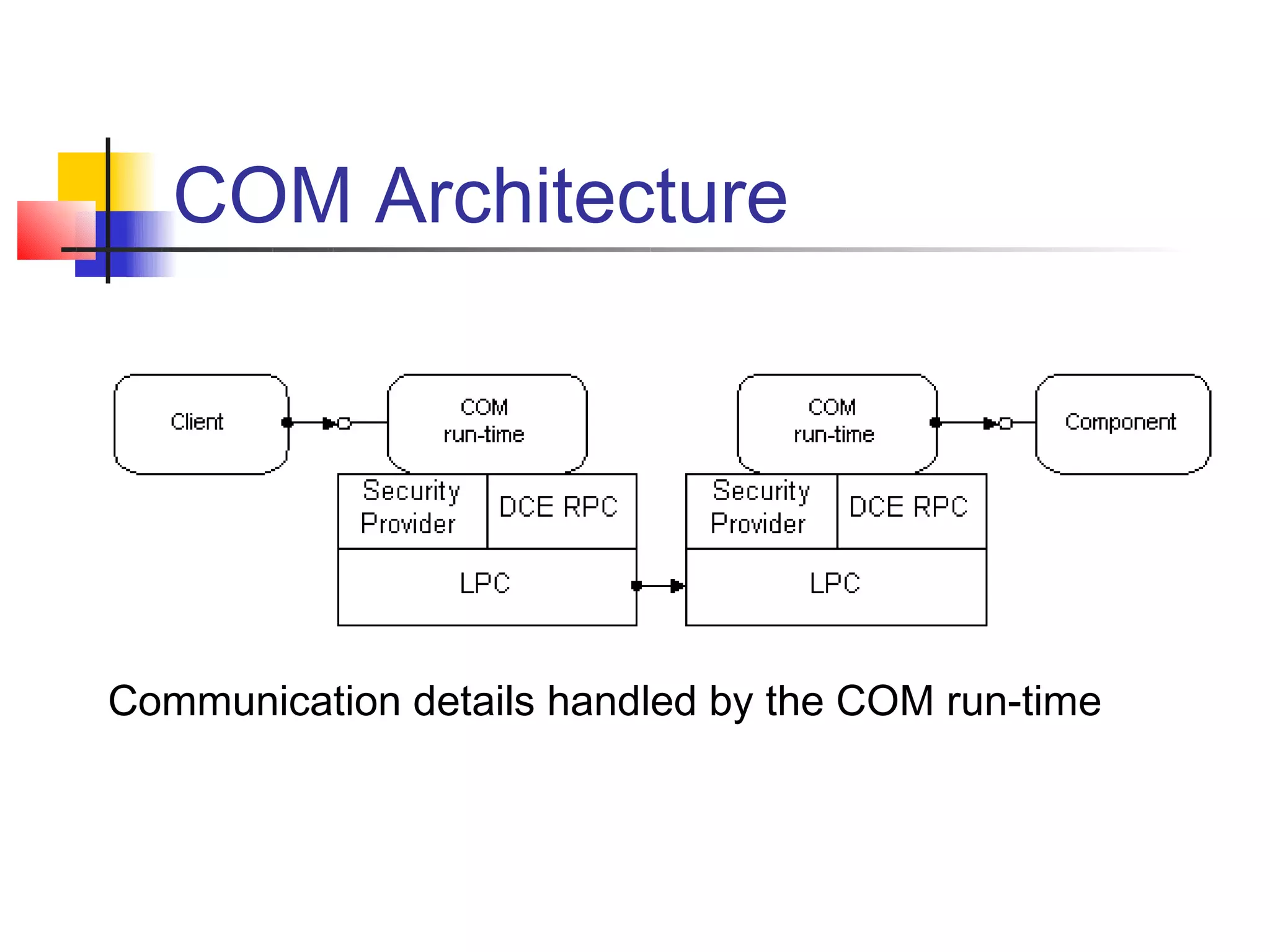
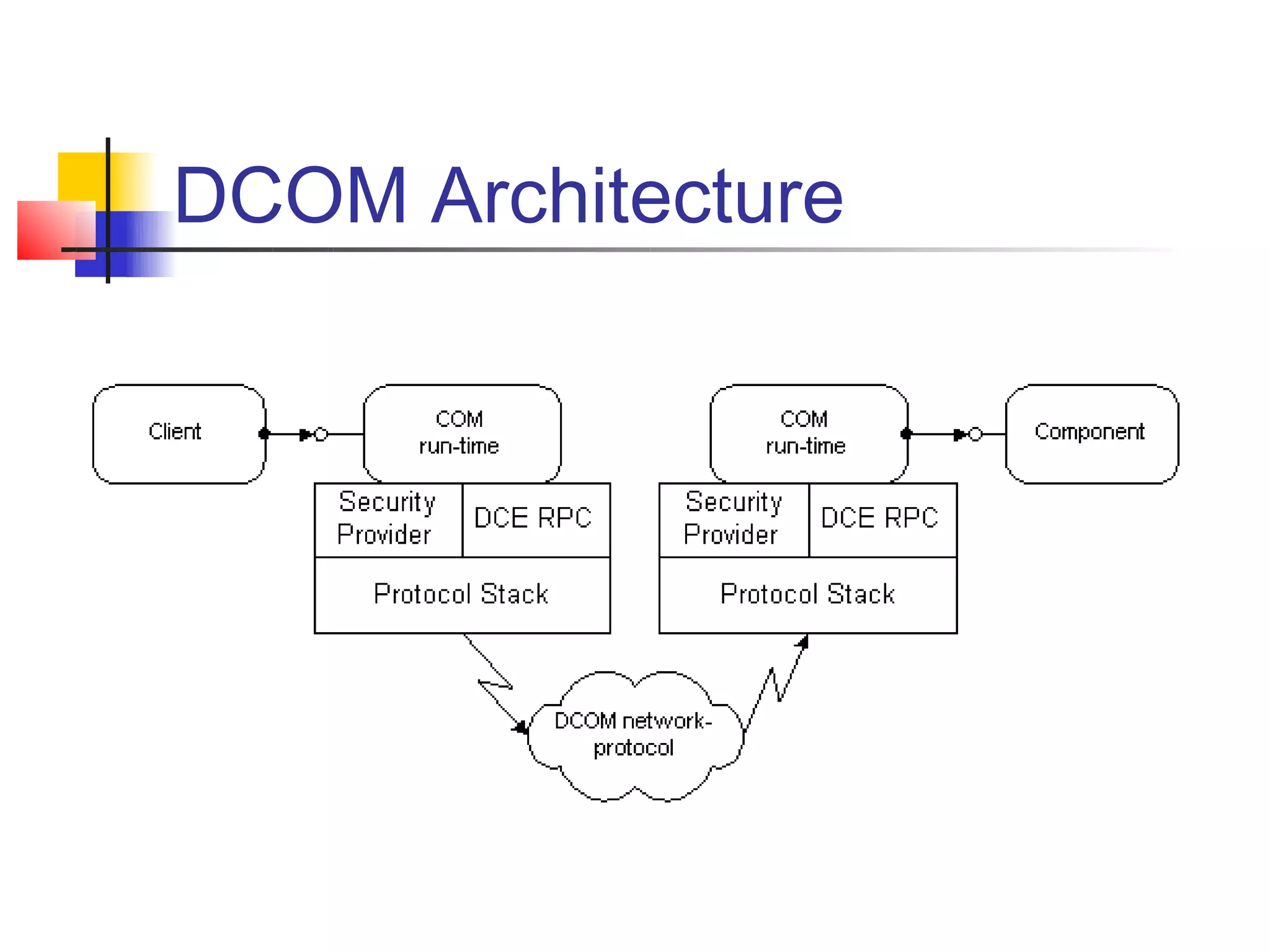
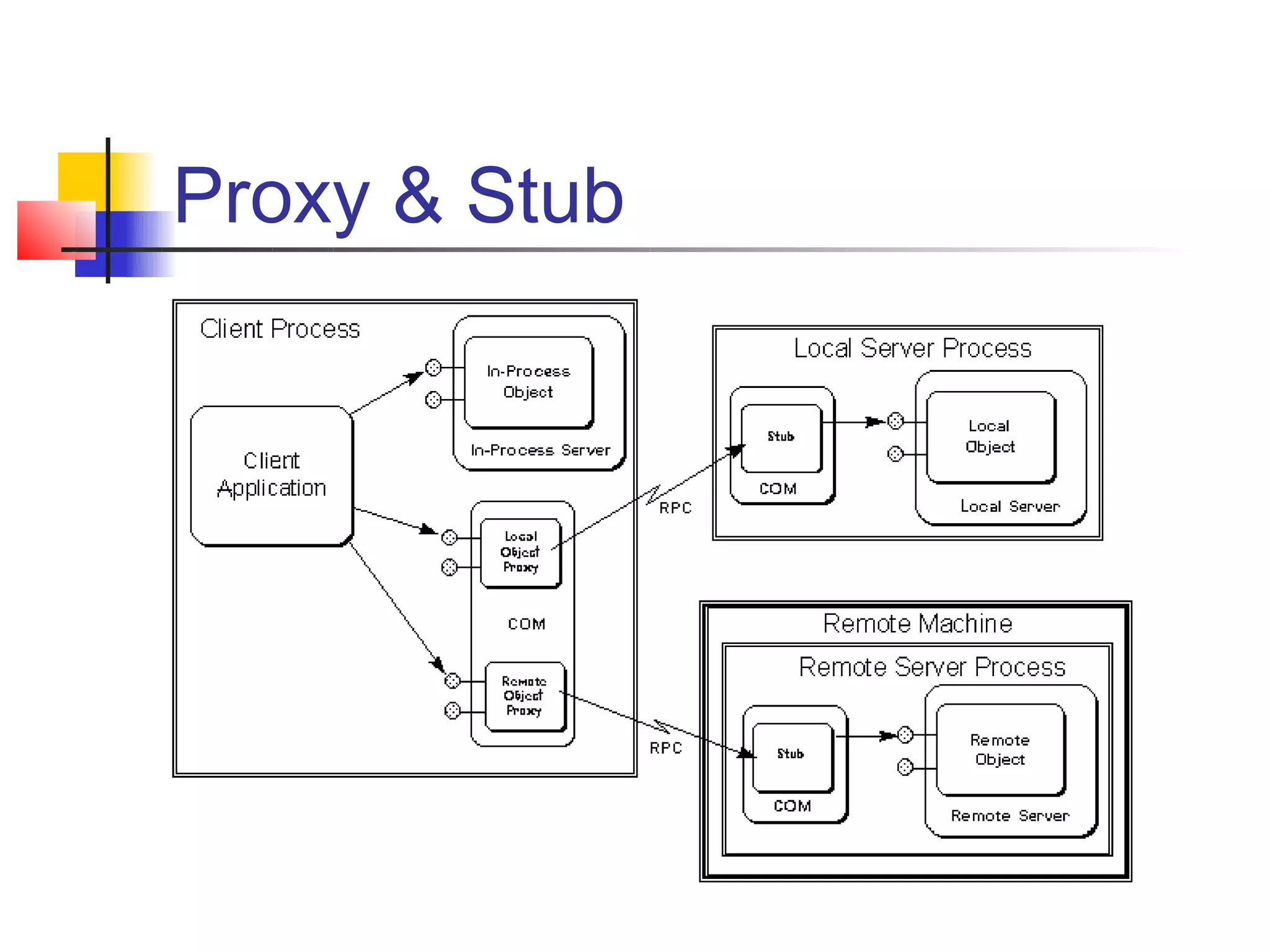
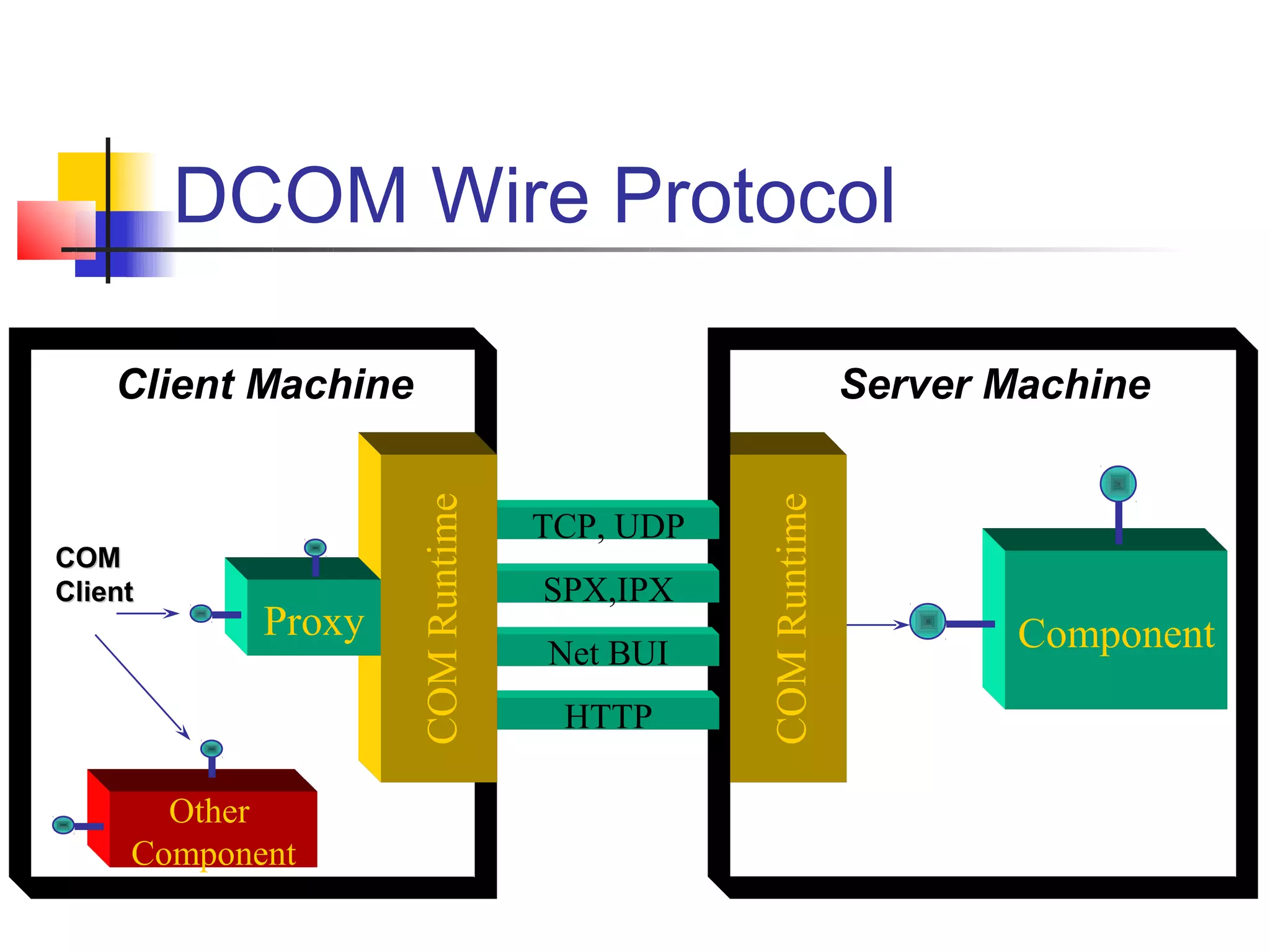
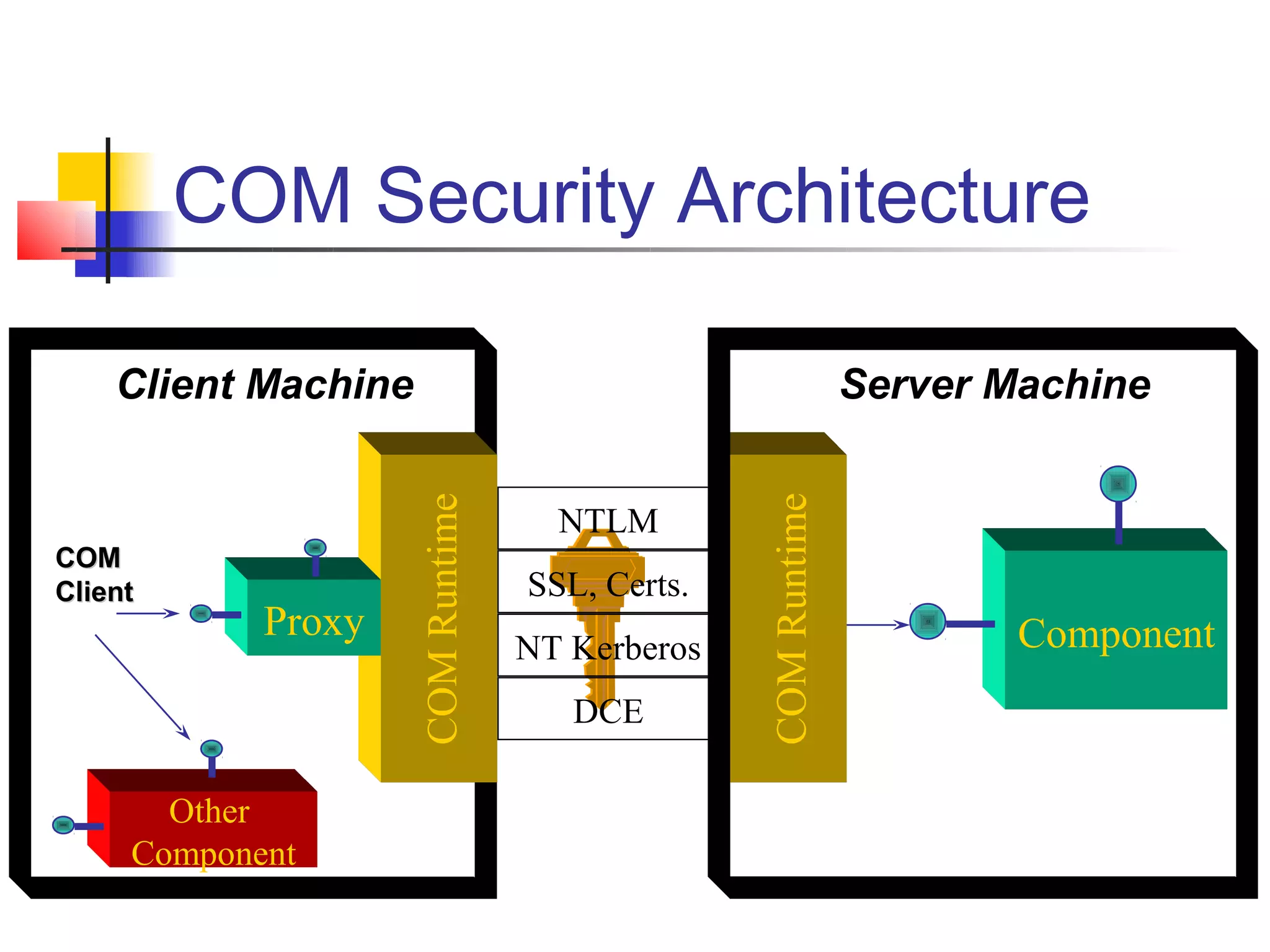
DCOM extends COM to allow communication between objects on different computers. It uses proxies, stubs, and remote procedure calls to marshal parameters and return values across process boundaries in a transparent way. DCOM provides security, location transparency, language neutrality, and other benefits for distributed object communication.











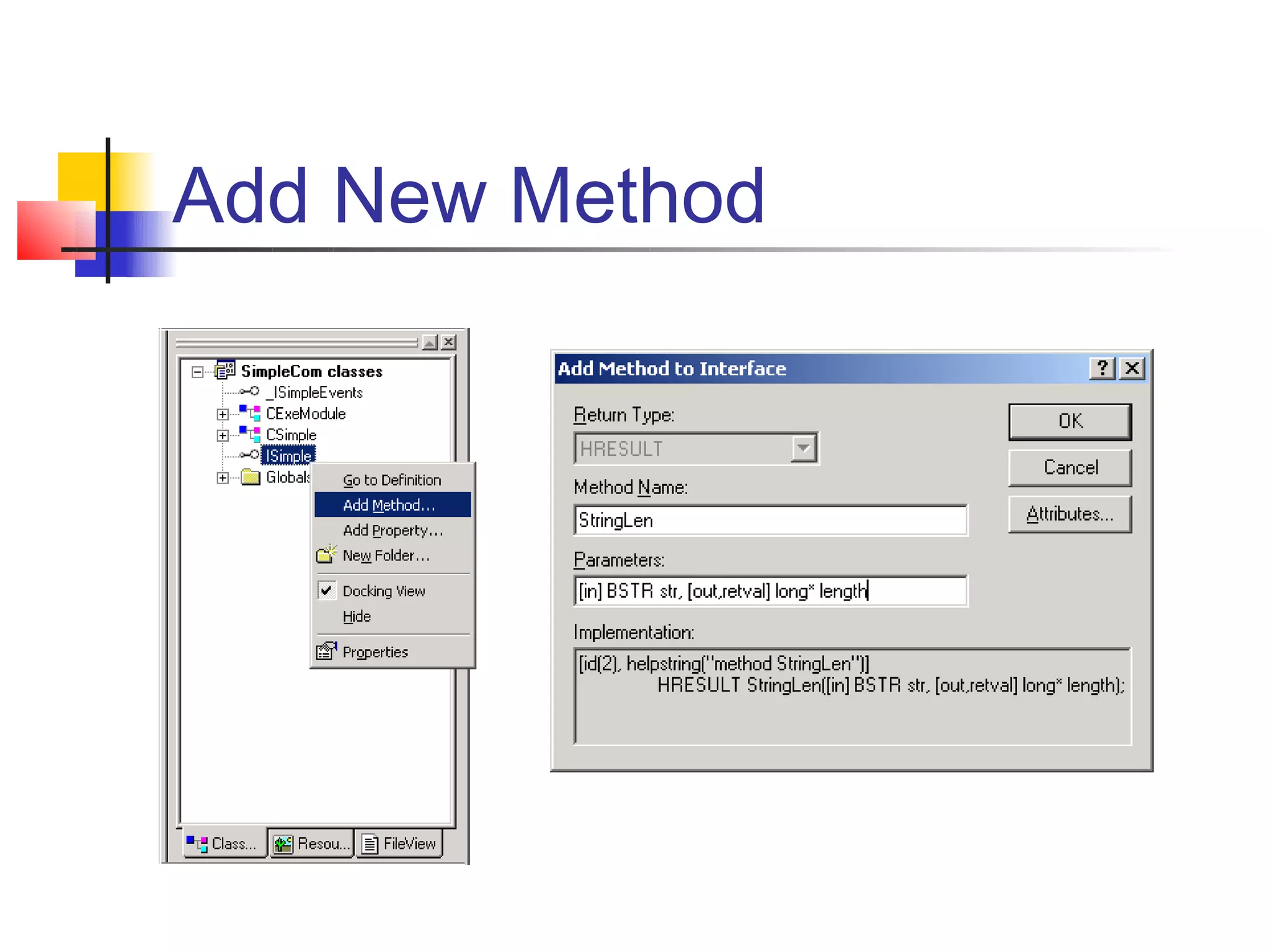
![Interface Definition Language ... [ object, uuid(79522A15-BA3D-46A5-92D6-DA4BE60646F4), dual, helpstring("ISimple Interface"), pointer_default(unique) ] interface ISimple : IDispatch { [id(1), helpstring("method StringLen")] HRESULT StringLen([in] BSTR str, [out,retval] long* length); }; ...](https://image.slidesharecdn.com/presentationoncomdcom-13455445593015-phpapp01-120821052342-phpapp01/75/Presentation-On-Com-Dcom-31-2048.jpg)
![Source & Header File Source: STDMETHODIMP CSimple::StringLen(BSTR str, long* length) { *length = SysStringLen(str); return S_OK; } Header: ... public: STDMETHOD(StringLen)(/*[in]*/ BSTR str, /*[out,retval]*/ long* length); ...](https://image.slidesharecdn.com/presentationoncomdcom-13455445593015-phpapp01-120821052342-phpapp01/75/Presentation-On-Com-Dcom-32-2048.jpg)
![Creating a Simple COM Client #include <stdio.h> #import "SimpleCom.exe" int main(int argc, char* argv[]) { SIMPLECOMLib::ISimplePtr pSimple; long len; CoInitialize(NULL); pSimple.CreateInstance(__uuidof(SIMPLECOMLib::Simple)); len = pSimple->StringLen("sample"); printf("Length = %dn", len); CoUninitialize(); return 0; }](https://image.slidesharecdn.com/presentationoncomdcom-13455445593015-phpapp01-120821052342-phpapp01/75/Presentation-On-Com-Dcom-33-2048.jpg)