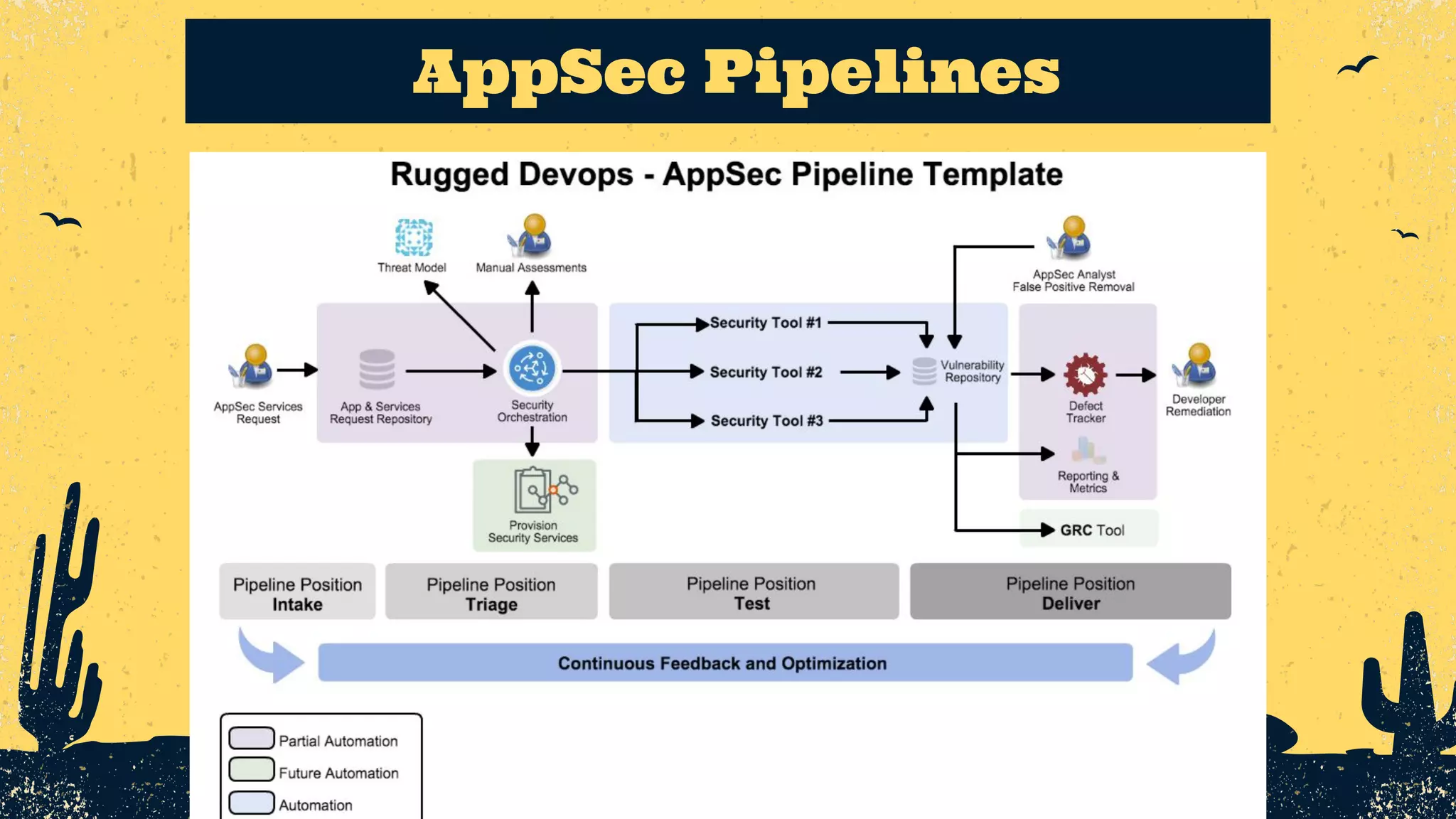
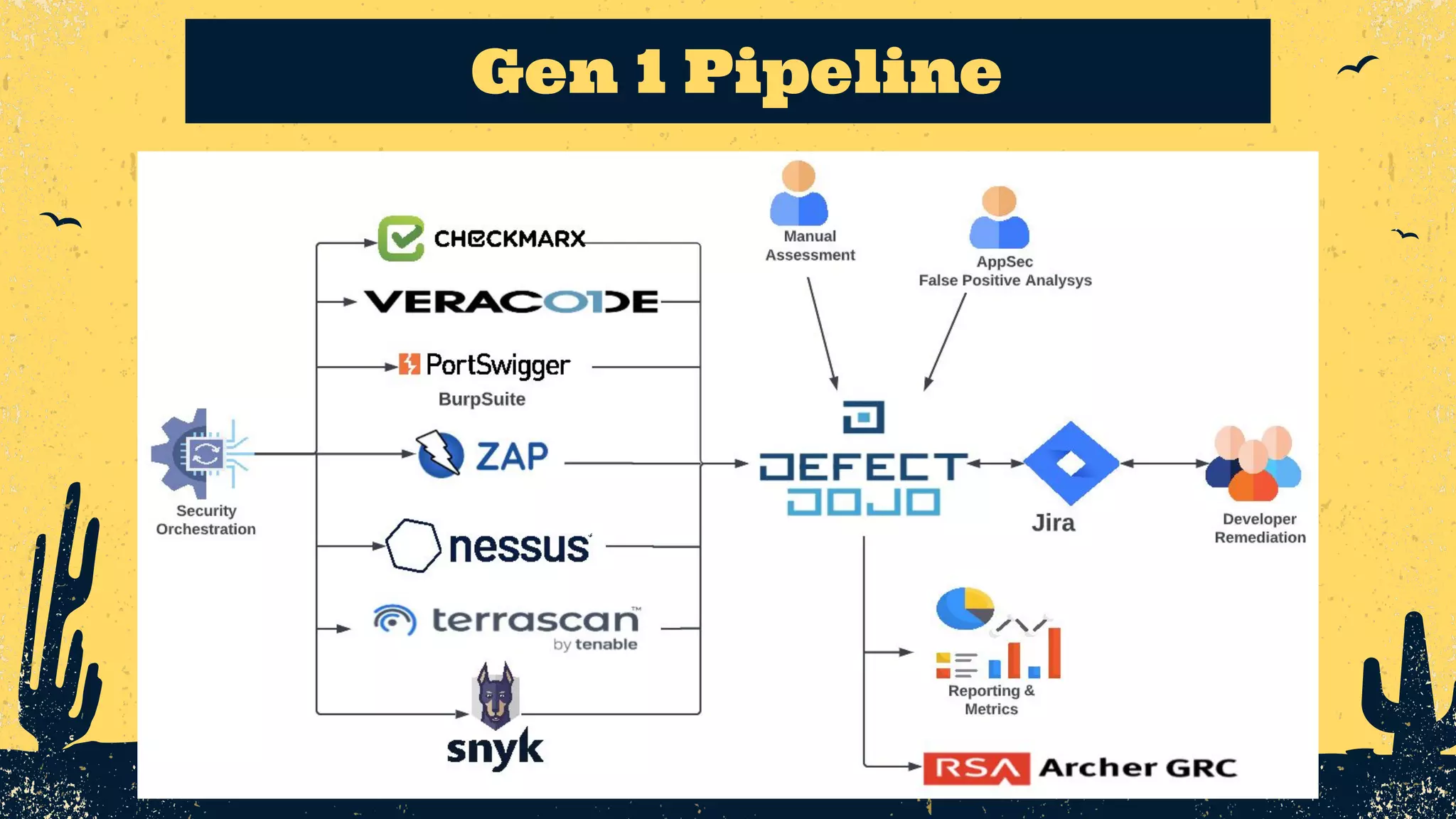
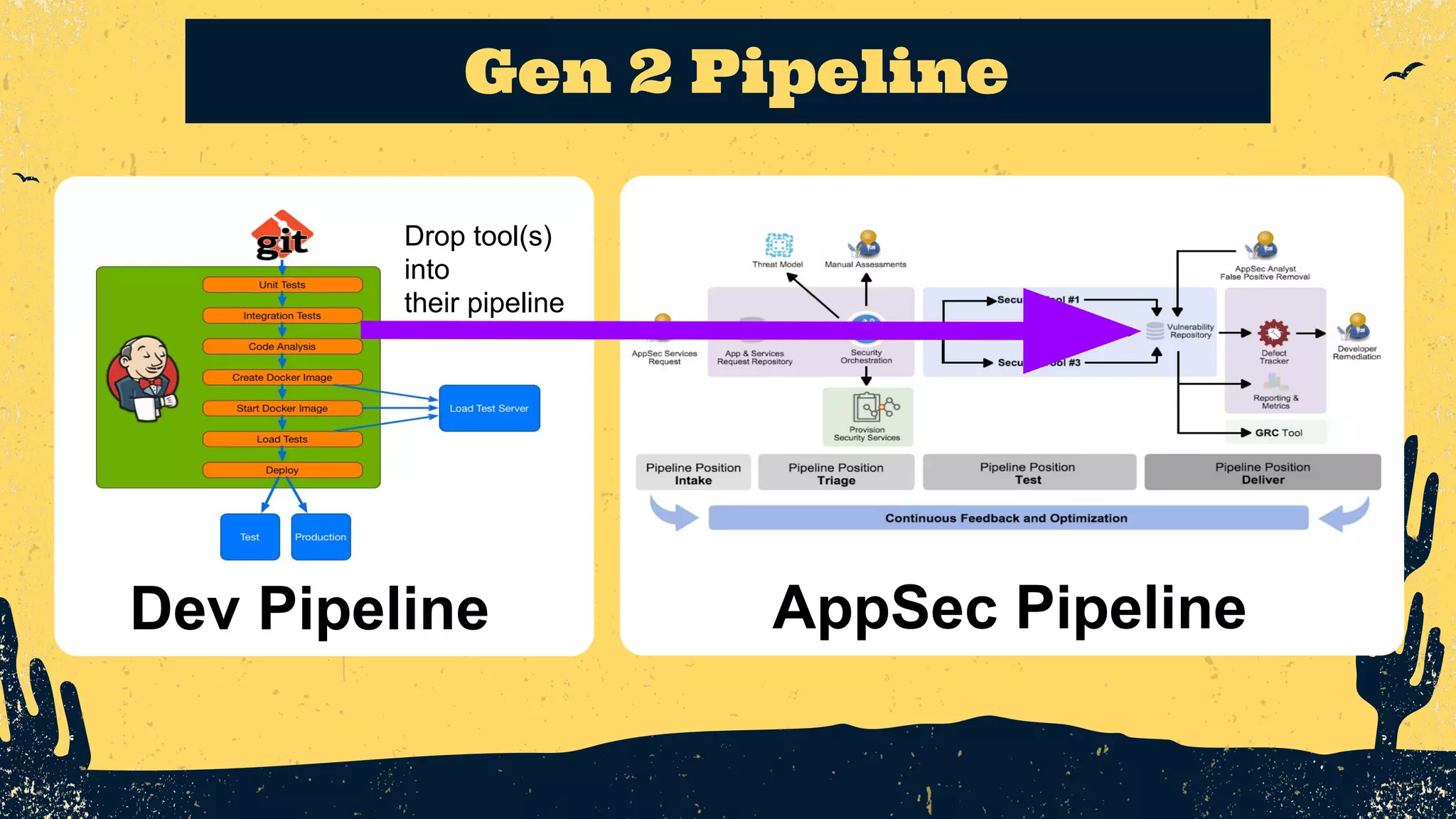
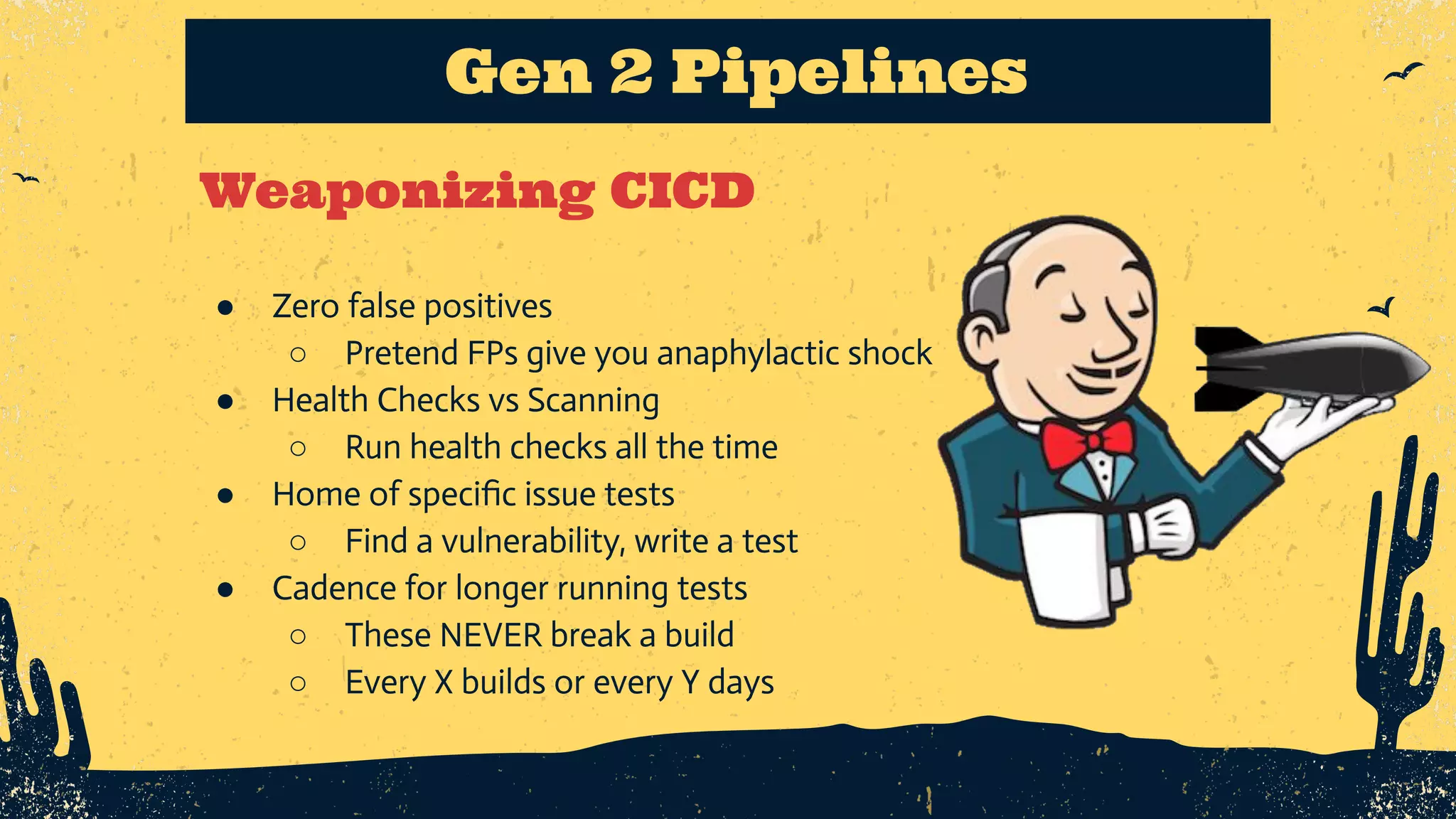
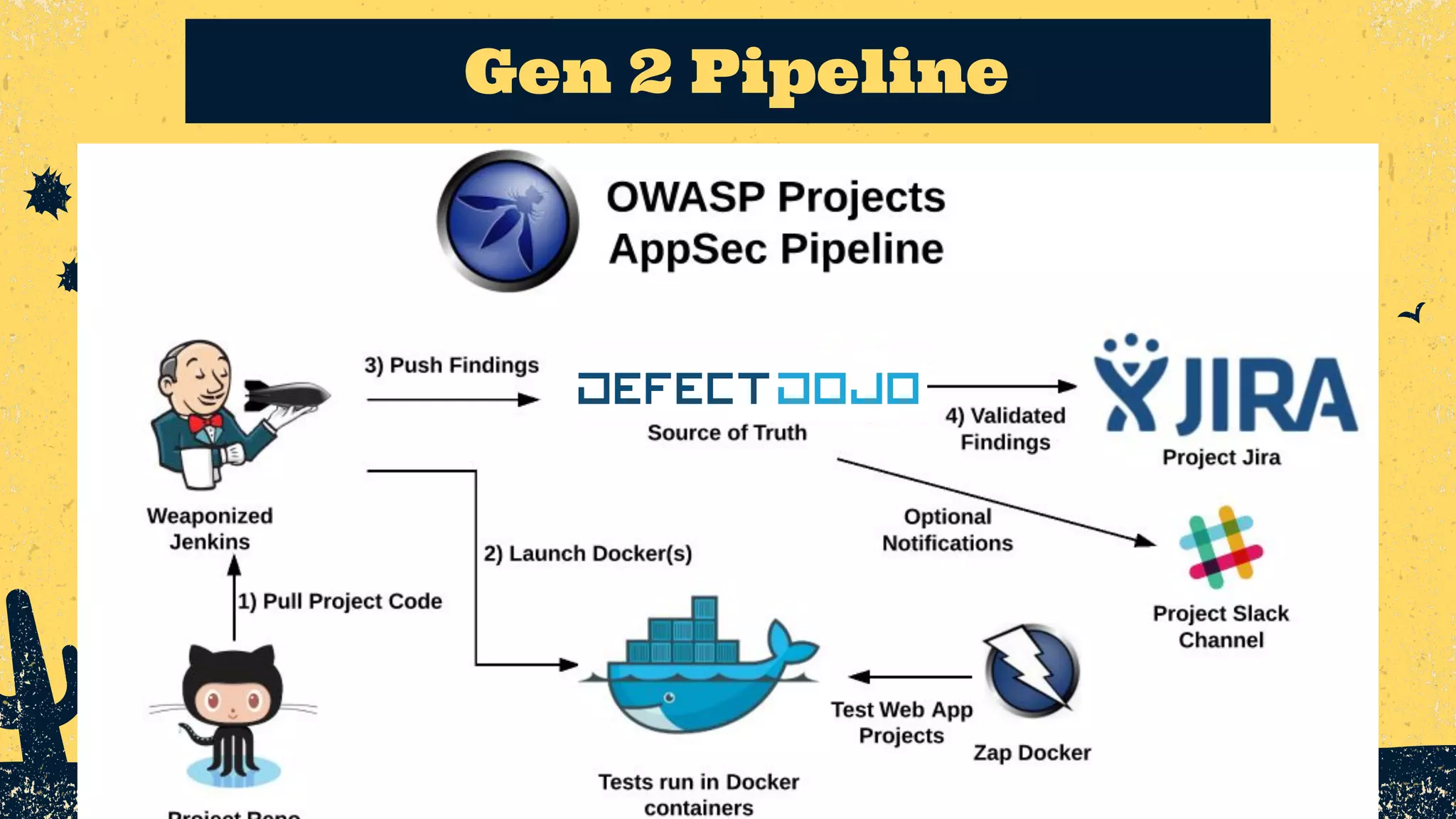
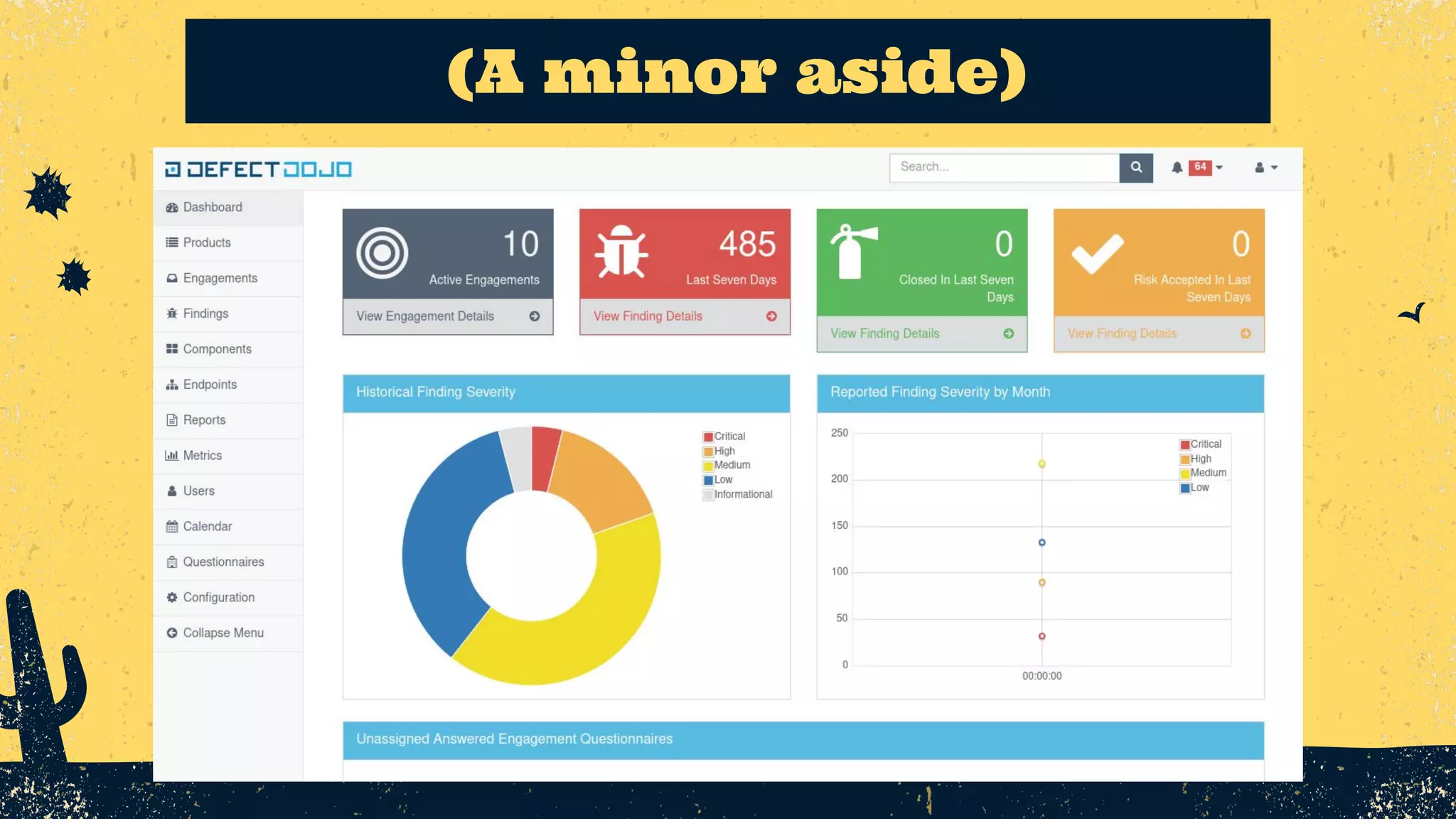
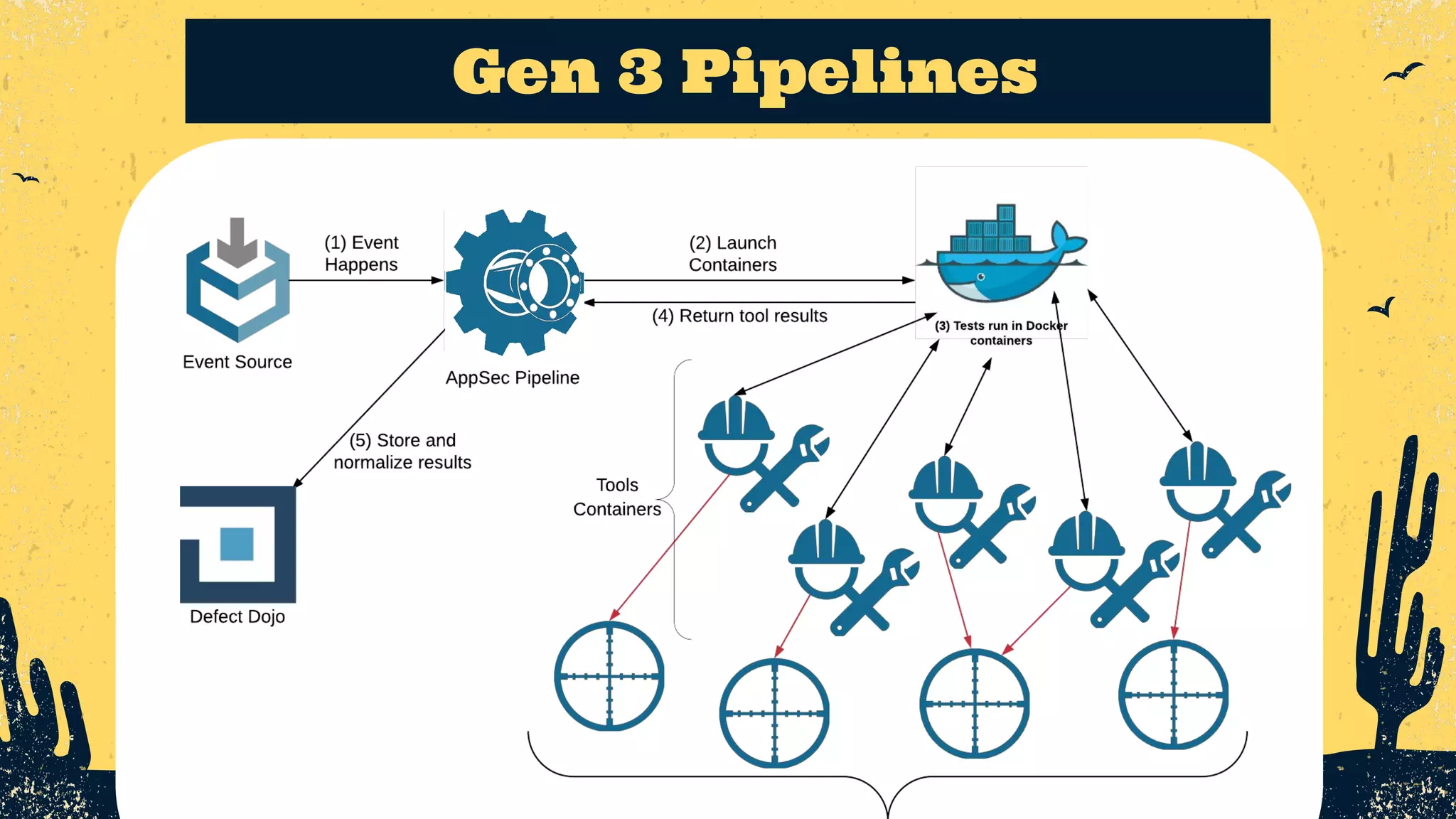
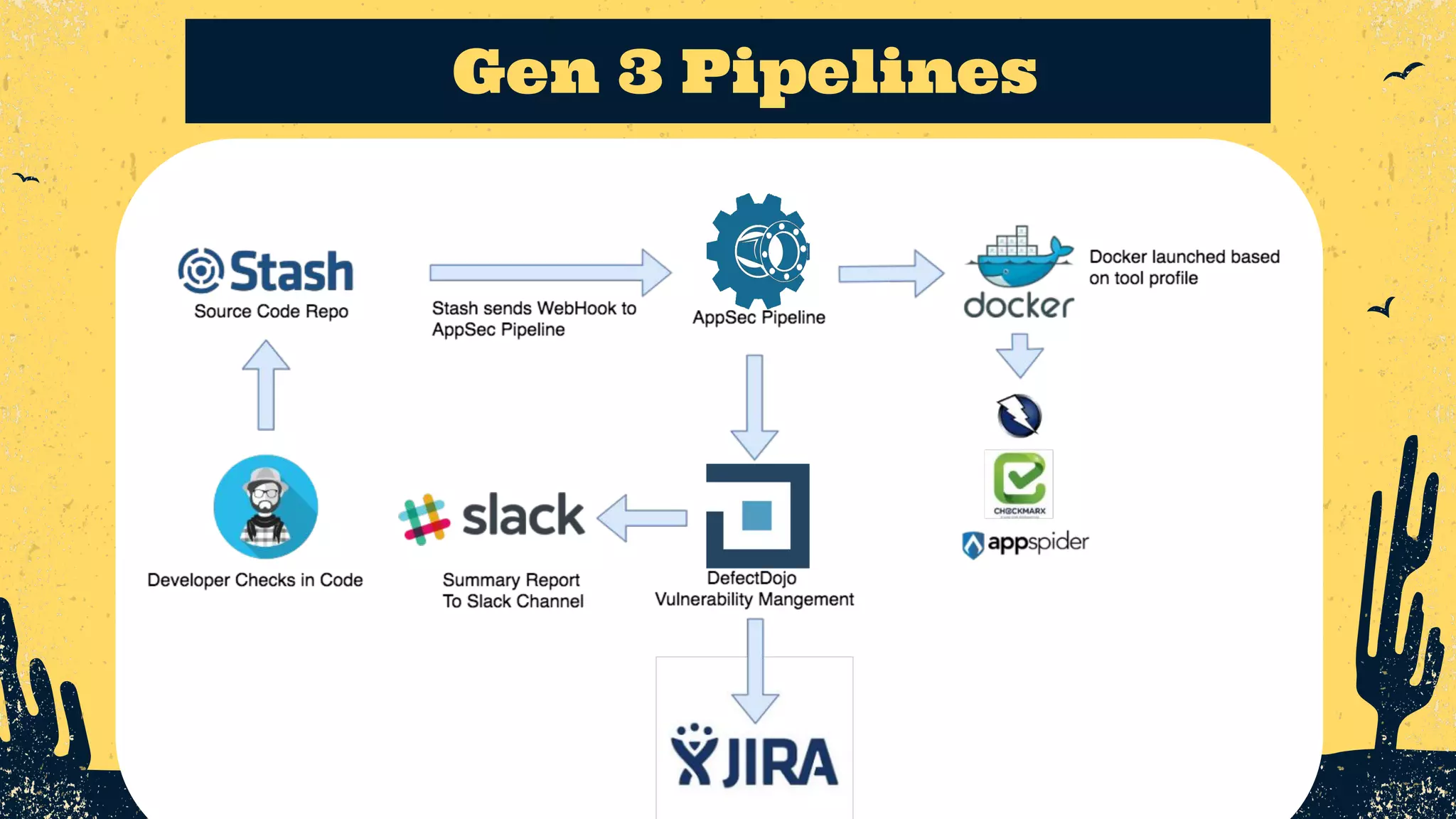
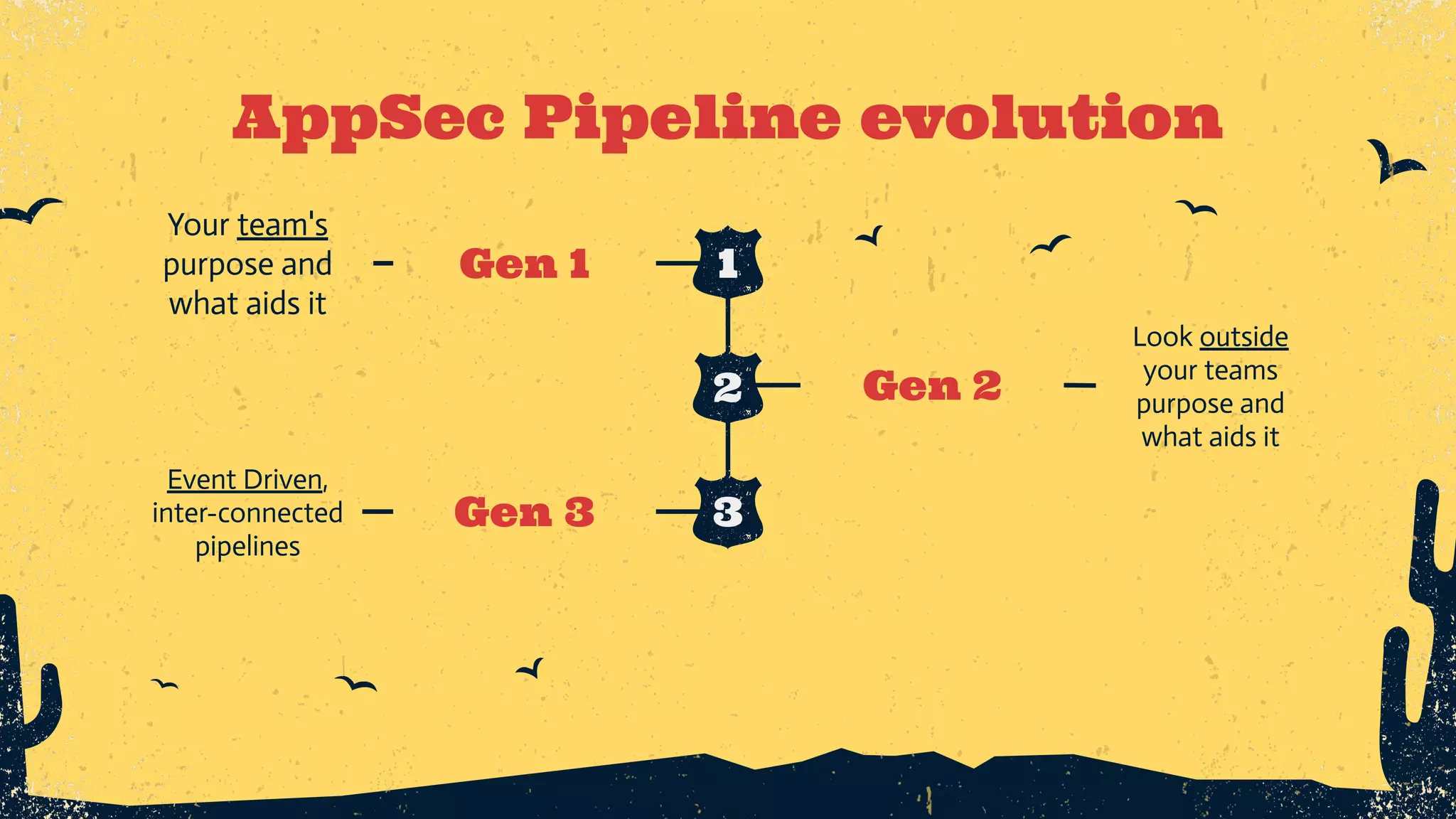
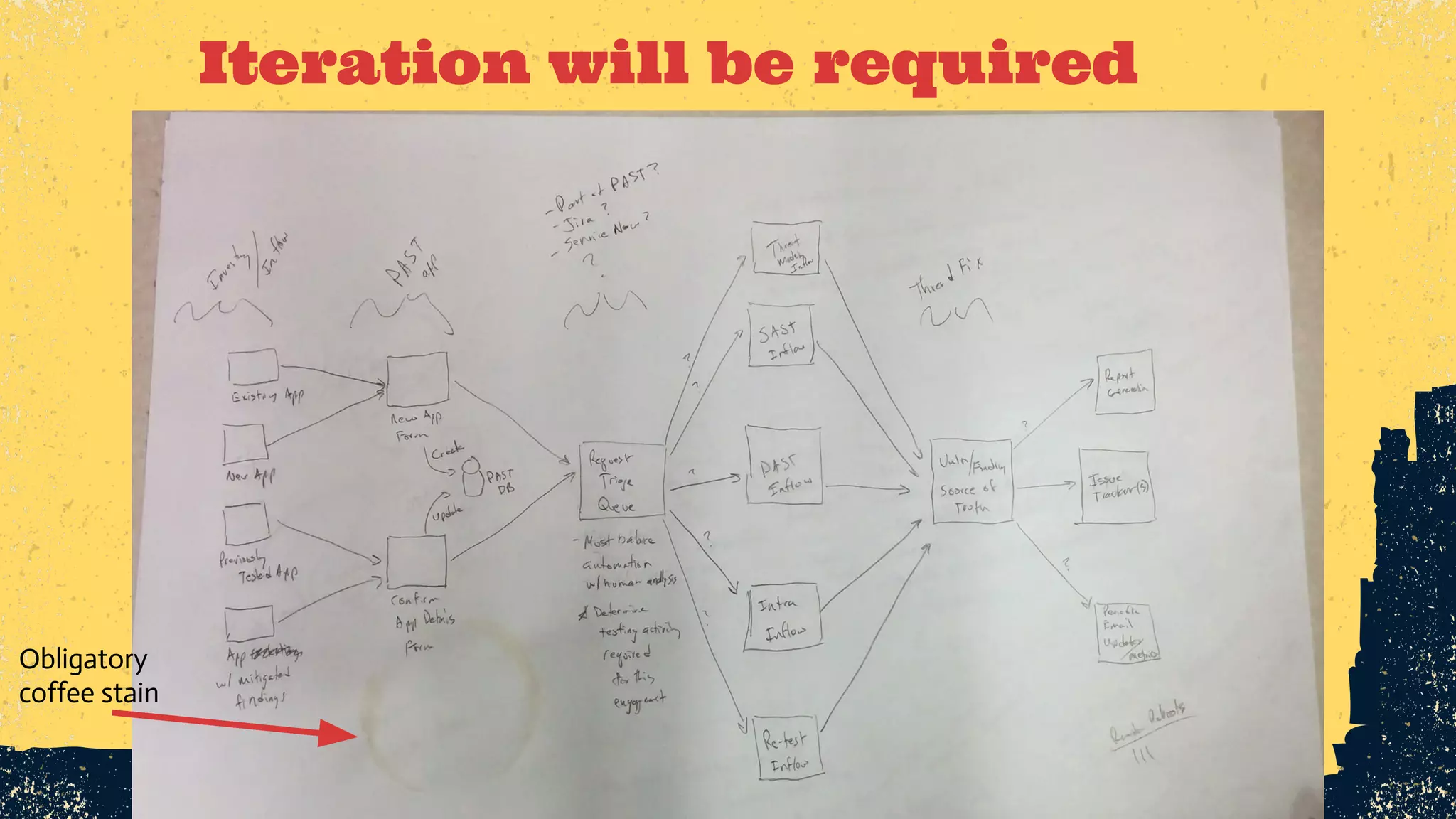
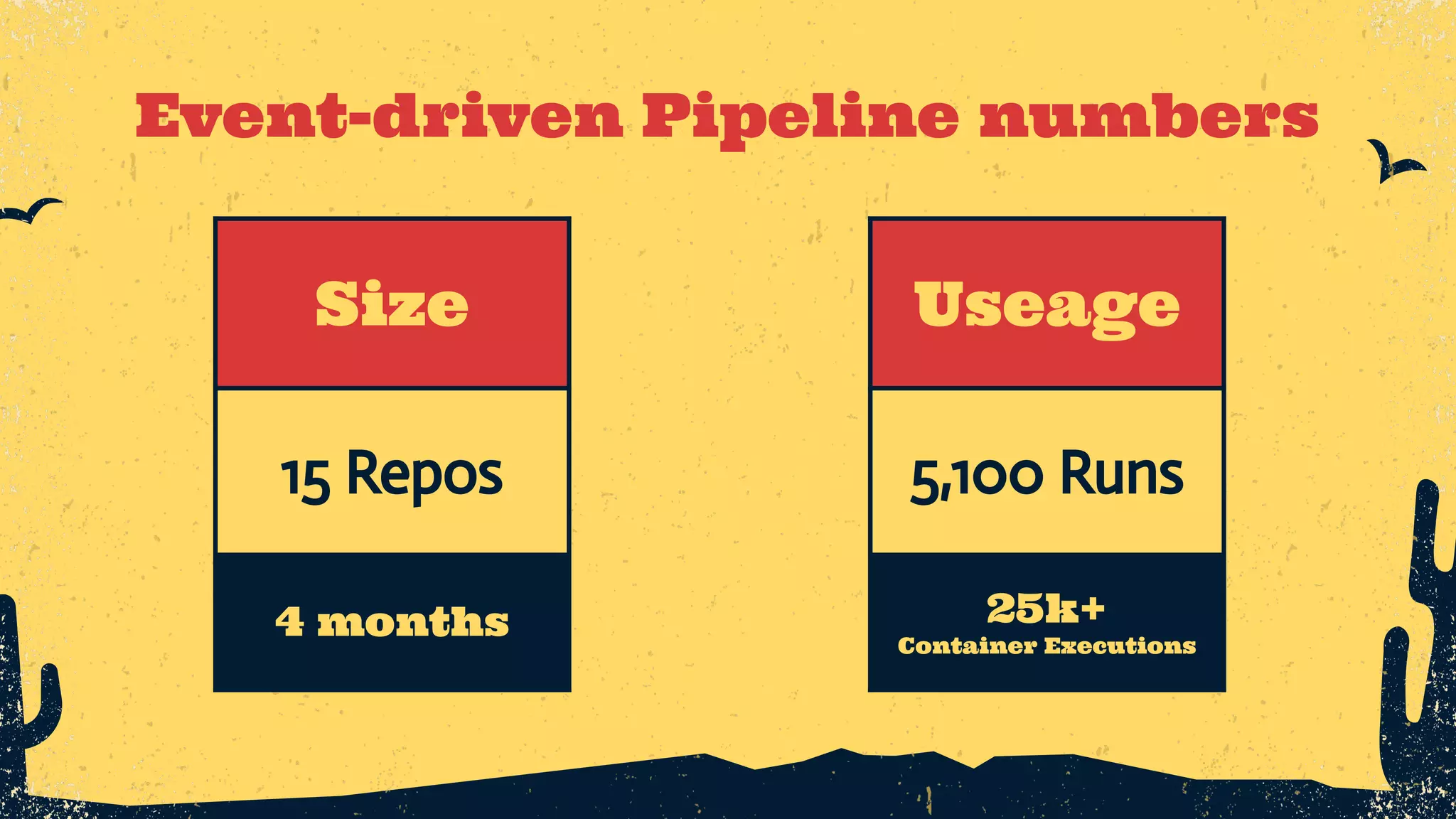
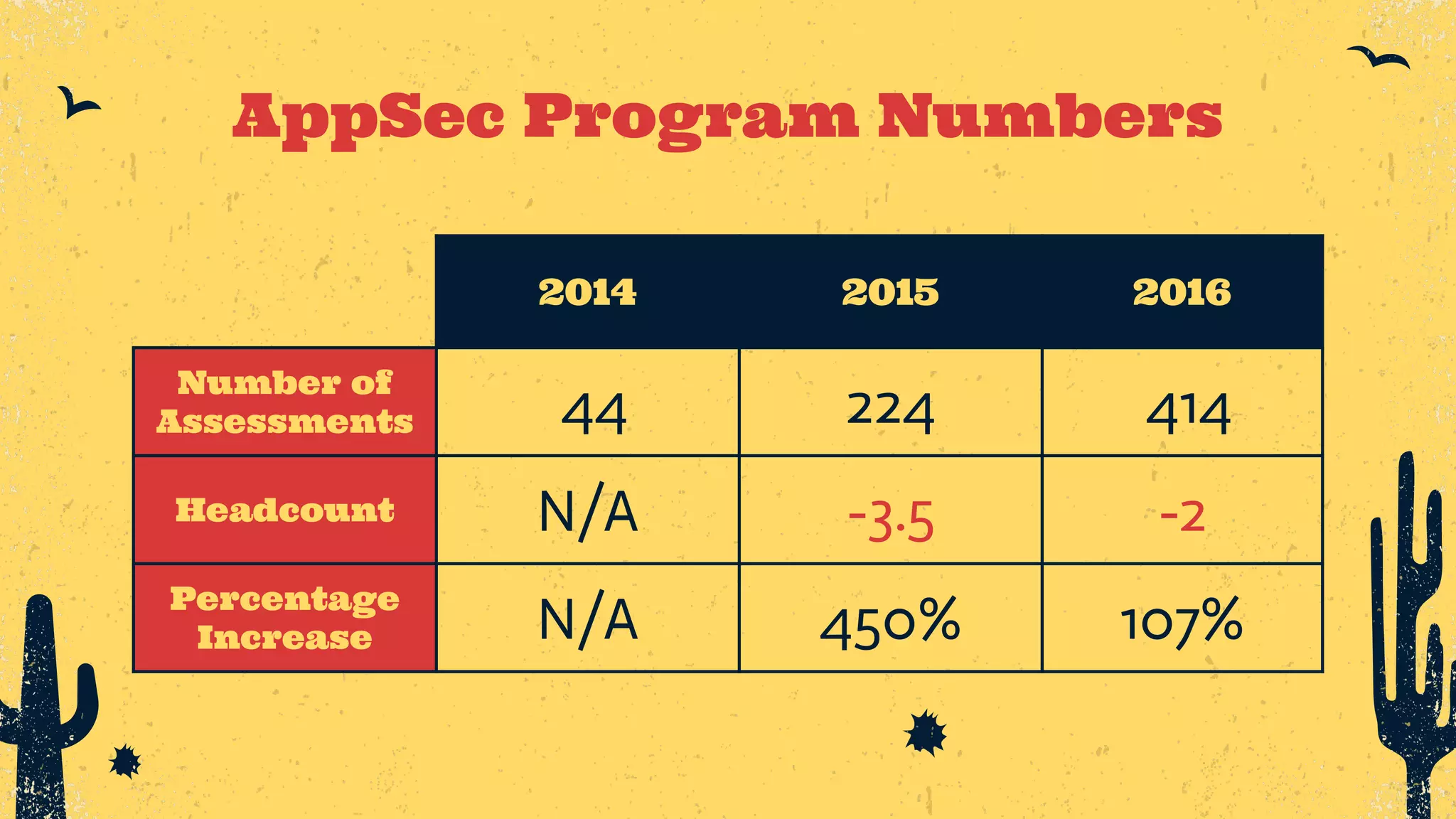
The document outlines the principles of DevSecOps, comparing its transformative impact to that of steam trains on American travel, and emphasizes the importance of optimizing workflows, improving feedback loops, and fostering a culture of experimentation within software development. It introduces the evolution of application security (AppSec) pipelines, detailing three generations aimed at enhancing automation, visibility, and integration with development processes. Key takeaways include the necessity for continuous improvement and the critical role of effective feedback in successfully implementing DevSecOps strategies.









![Look at your purpose and those processes which aid it ● Make sure the process is correct from the beginning to end then look at ways to speed up that process ● Value Stream - the name of the process which provides value to the business ● Working from left to right e.g. like a timeline business / development => customer / operations ● Flow [rate] - speed work goes through the process. #1 Workflow](https://image.slidesharecdn.com/practicaldevsecopsmatt-tesauroonug-fall-2022-221030185302-0f8e02cc/75/Practical-DevSecOps-Fundamentals-of-Successful-Programs-12-2048.jpg)