Downloaded 53 times




The document discusses penetration testing (pen testing), which is the practice of evaluating a system's security by identifying vulnerabilities that could be exploited by attackers. It provides insights into methodologies and components used in the Metasploit framework, including exploit modules, payloads, and listeners. The text emphasizes the role of good security practices and the tools available for conducting effective pen tests.









Overview of Penetration Testing using Metasploit, presented by Aashish R, Shravan Chandrasekhar, and Saurav.
Pen test is a practice to test systems/networks for vulnerabilities; also assesses security responses.
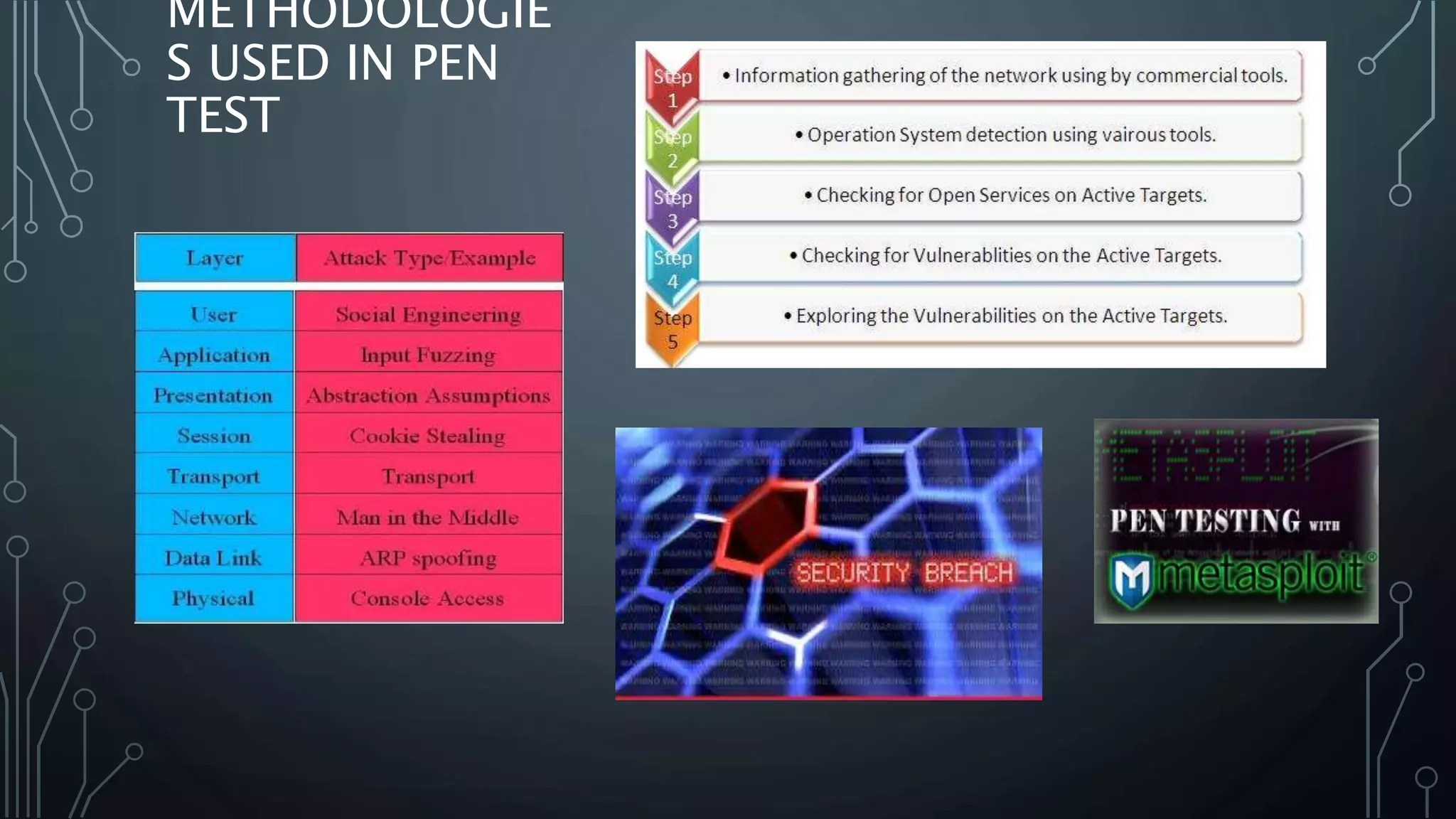
Discussion on various methodologies implemented during penetration testing for effective assessments.
Insight into the methodologies adapted to conduct penetration testing effectively.
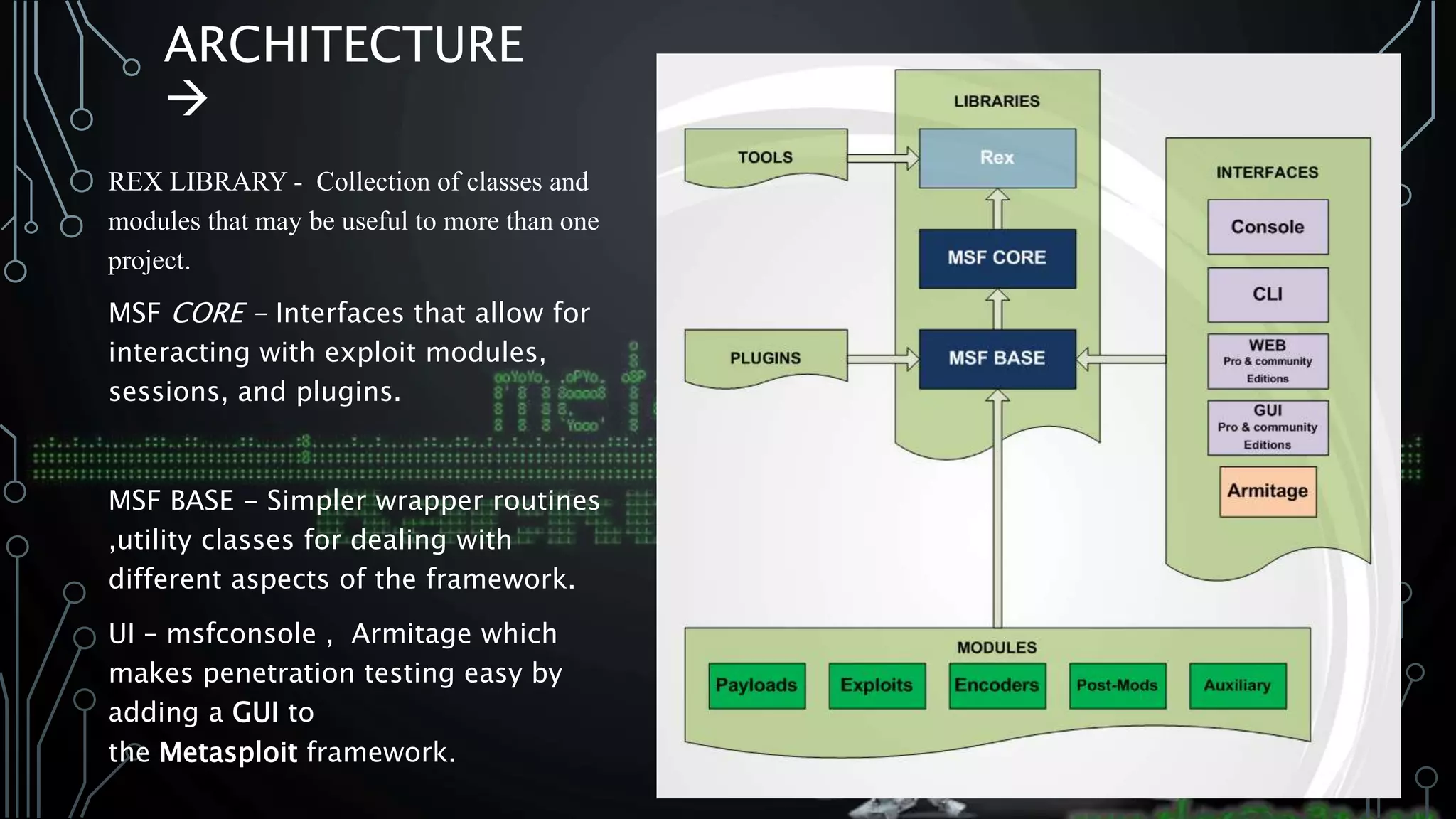
Introduction to Metasploit components: REX Library, MSF CORE, MSF BASE, and GUI tools.
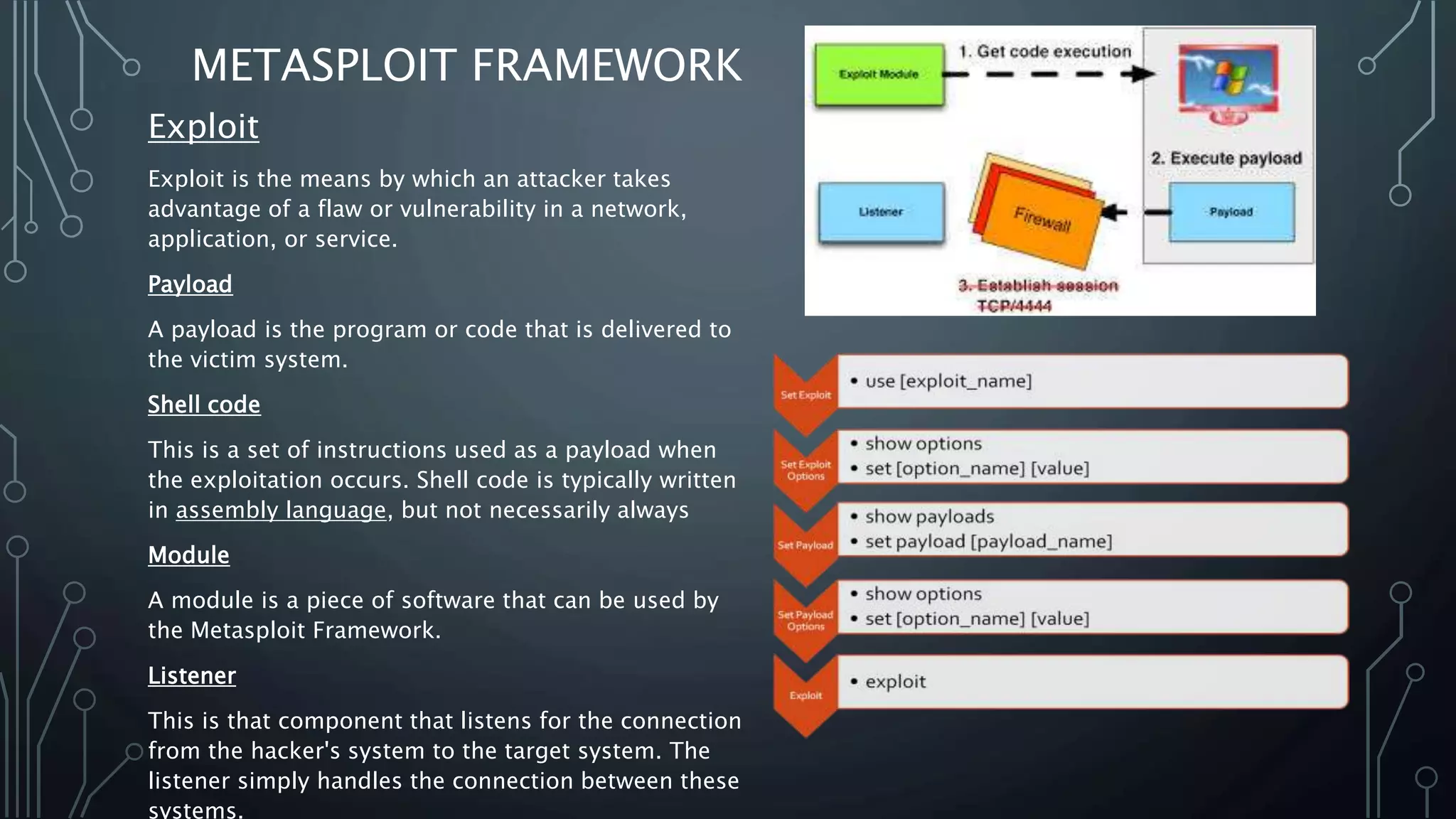
Explanation of key Metasploit terms: Exploits, Payloads, Shell code, Modules, and Listeners.
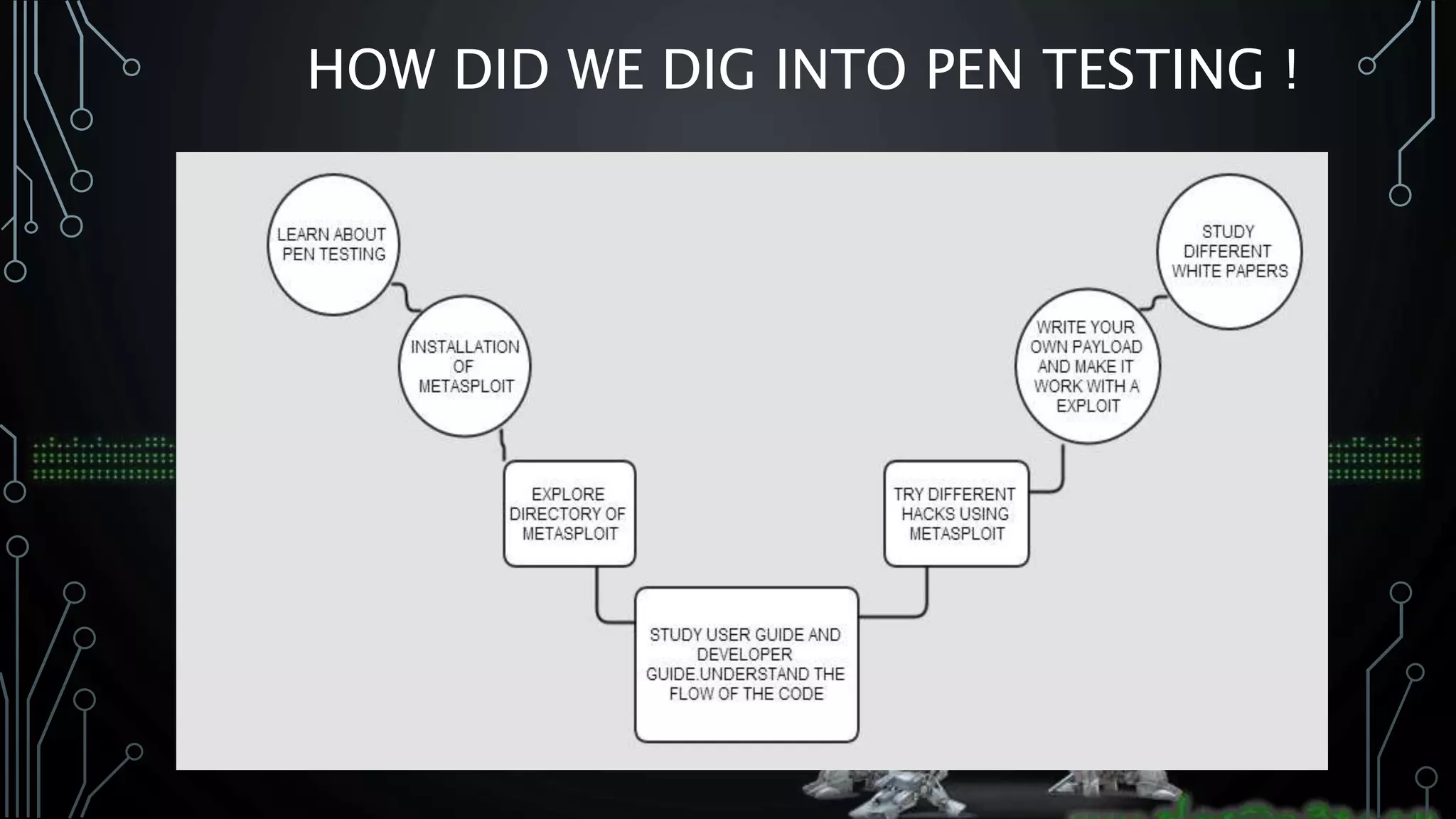
Summary of the activities conducted during the penetration testing project.
Analysis and observations made from the penetration testing efforts and outcomes.