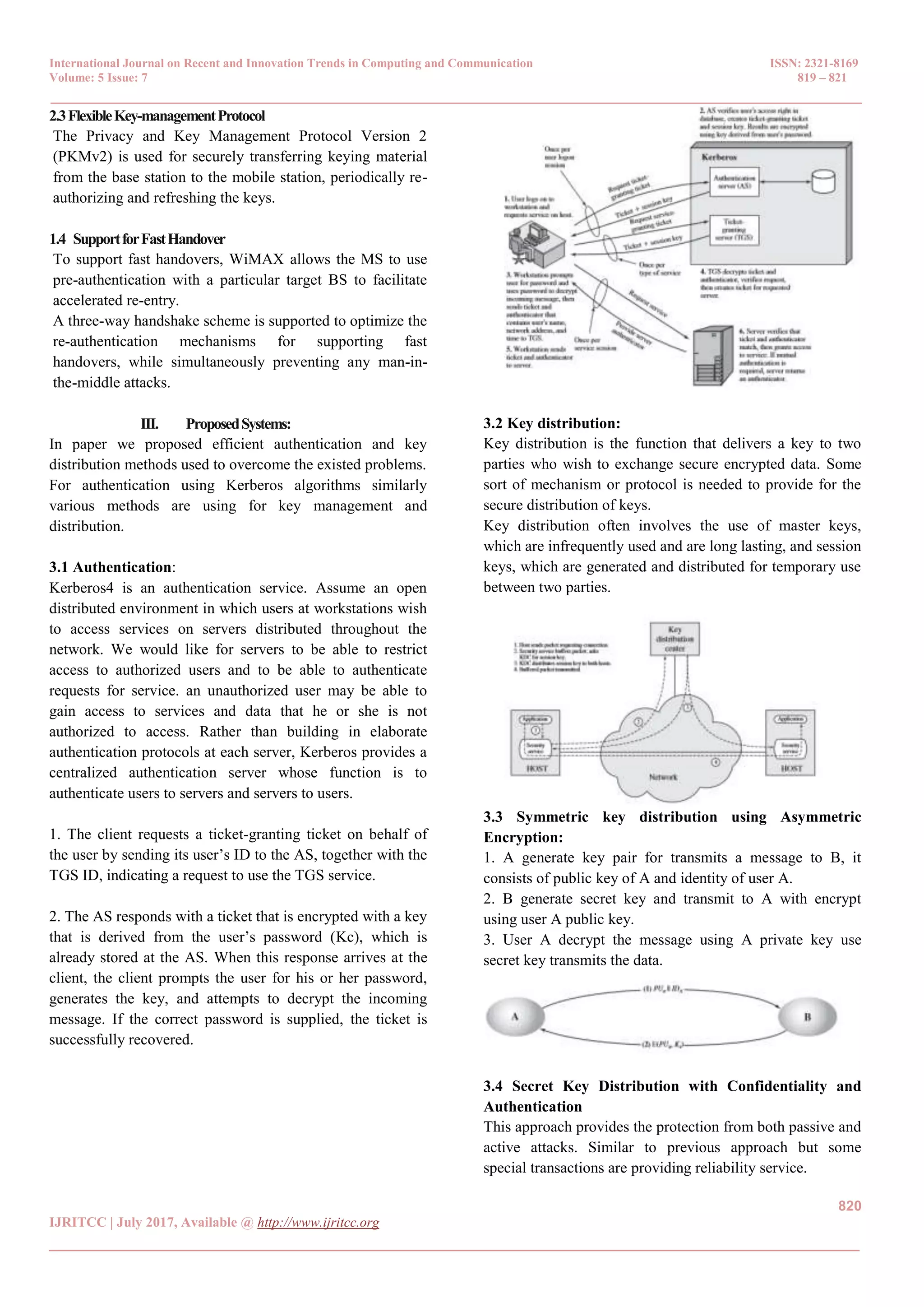
The document discusses a new approach for implementing authentication and key distribution in WiMAX networks, highlighting the technology's enhanced security needs due to its broader range and higher bandwidth compared to Wi-Fi. It details the limitations of existing security methods, particularly in terms of privacy and key management, and proposes using Kerberos for authentication and asymmetric encryption for key distribution to enhance security against potential attacks. The study emphasizes the importance of strong security protocols in wireless networks to protect all transactions.

![International Journal on Recent and Innovation Trends in Computing and Communication ISSN: 2321-8169 Volume: 5 Issue: 7 819 – 821 _______________________________________________________________________________________________ 821 IJRITCC | July 2017, Available @ http://www.ijritcc.org _______________________________________________________________________________________ Share the identities with their respective key pairs and also share the session’s keys to make more secure. And also some challenge questions are transmit the each other for authenticate. IV. Conclusion: Security is a major issue in wireless environment, need to protect for every transaction. In existing using symmetric algorithms for authentication and key distribution but this approach not sufficient for wireless network and easy to effect by attacks. In this paper we proposed asymmetric key distribution for exchange the keys with secret keys. For authentication use Kerberos algorithm. References: [1] V. Gunasekaran, F. Harmantzis, “Emerging wireless technologies for developing countries”, Technology in Society 29 23–42, 2009. [2] V. Abel, “Survey of Current and Future Trends in Security in Wireless Networks”, International Journal of Scientific & Engineering Research (ISSN 2229-5518), April 2011 [3] V. Abel, A. Mnaouer, “On the Study of the WiMAX Security Threats and Current Solution Trends”, Journal of the Caribbean Academy of Sciences, 2010. [4] N.Sastry, J. Crowcroft, K. Sollins, “Architecting Citywide Ubiquitous Wi-Fi Access” [5] R.Barton,S.Hwu,M.Khayat,A.Schlesinger, “Lunar Surface EVA 802.16 Radio Study”, NASA – Johnson Space Center, October 13, 2008 [6] V.Abel, R.Rambally, “An Analysis of WiMax Security Vulnerabilities”, International conference on wireless networks and embedded systems WECON 2009 [7] V.Abel, “Survey of Attacks on Mobile Adhoc Wireless Networks”, International Journal on Computer Science and Engineering, ISSN : 0975-3397, Vol. 3 No. 2, 2 Feb 2011.](https://image.slidesharecdn.com/156150191970705-08-2017-180102130810/75/New-Approach-to-Implement-Authentication-and-Key-Distribution-on-WI-Max-Networks-3-2048.jpg)