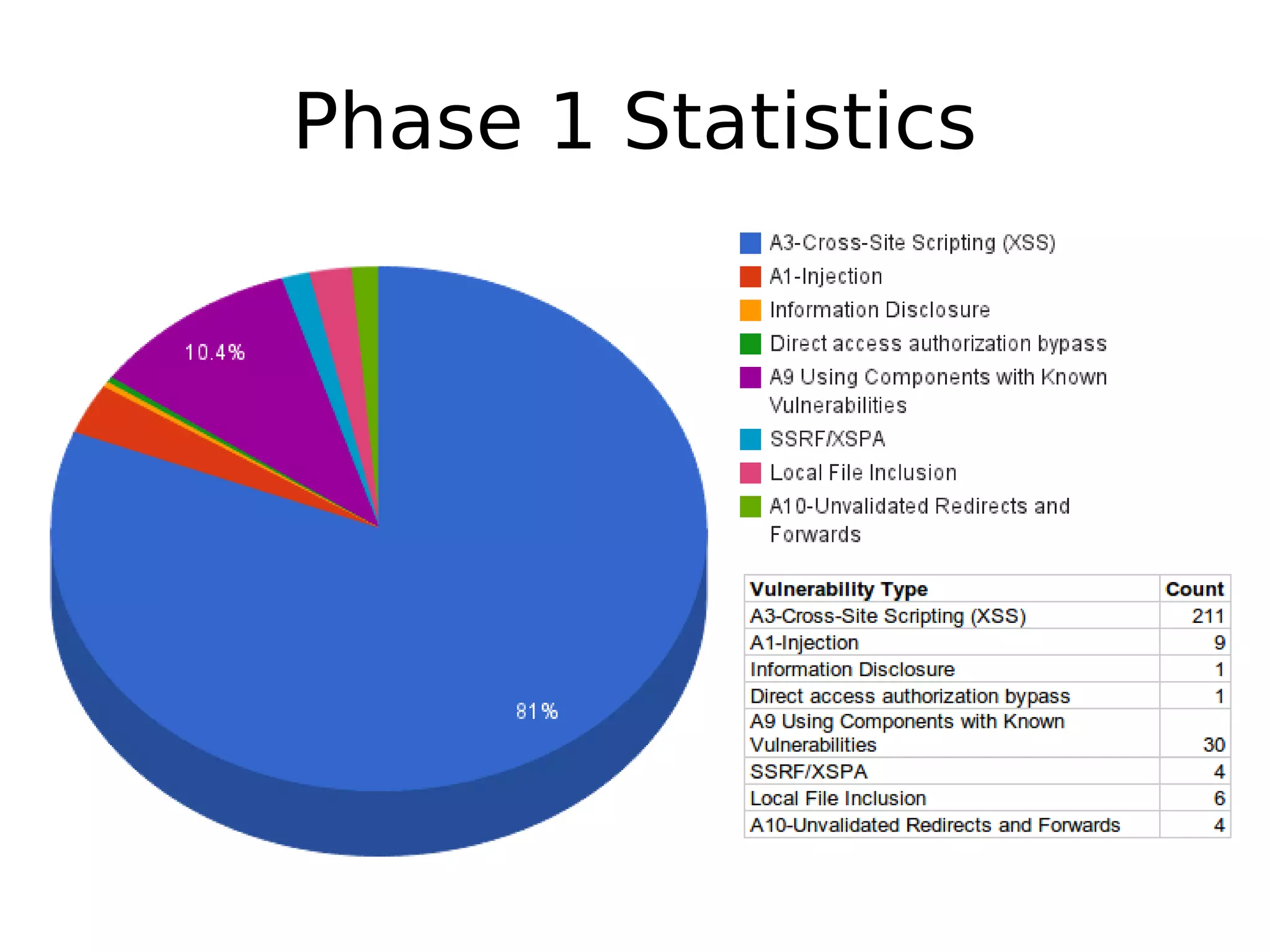
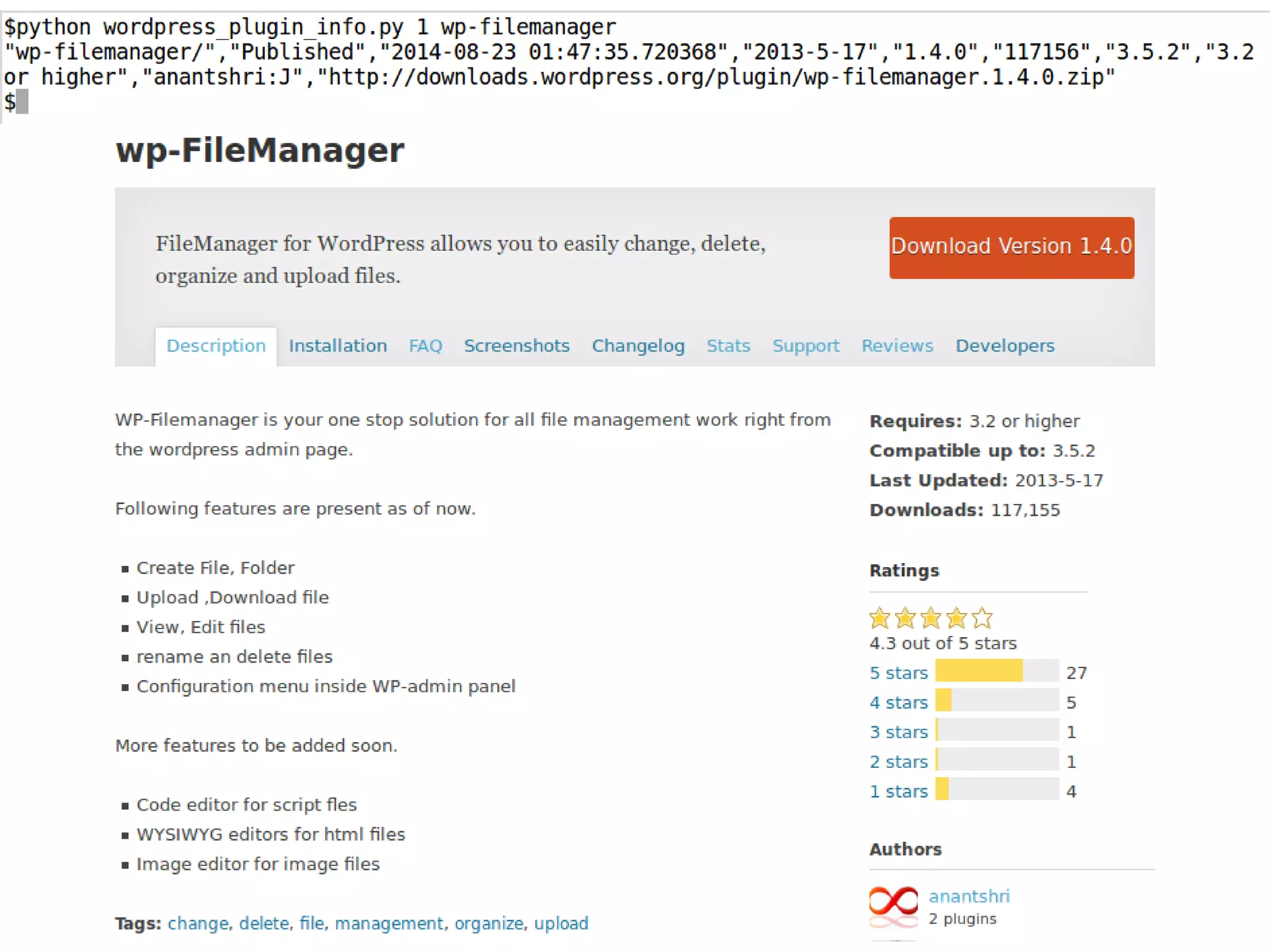
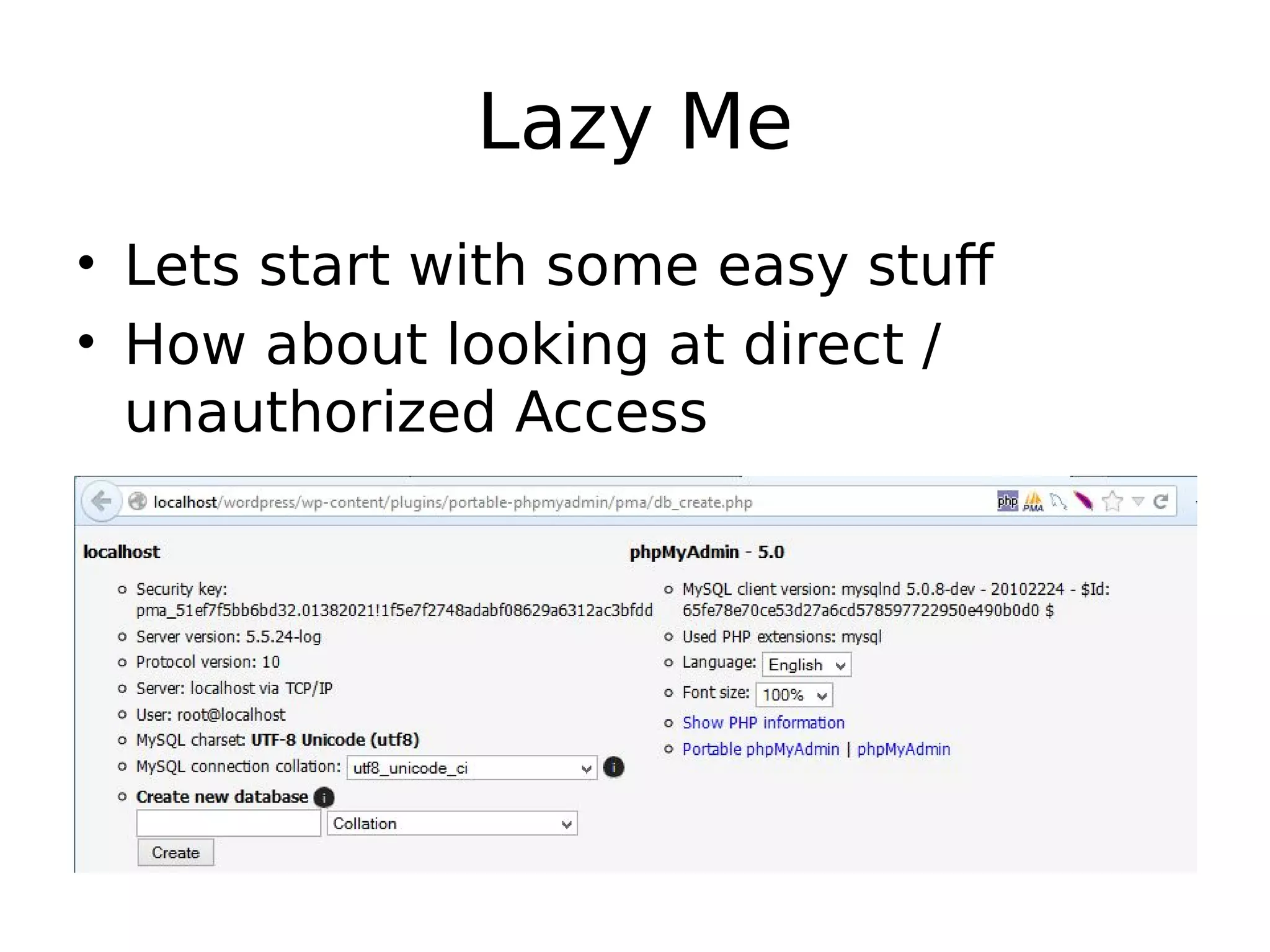
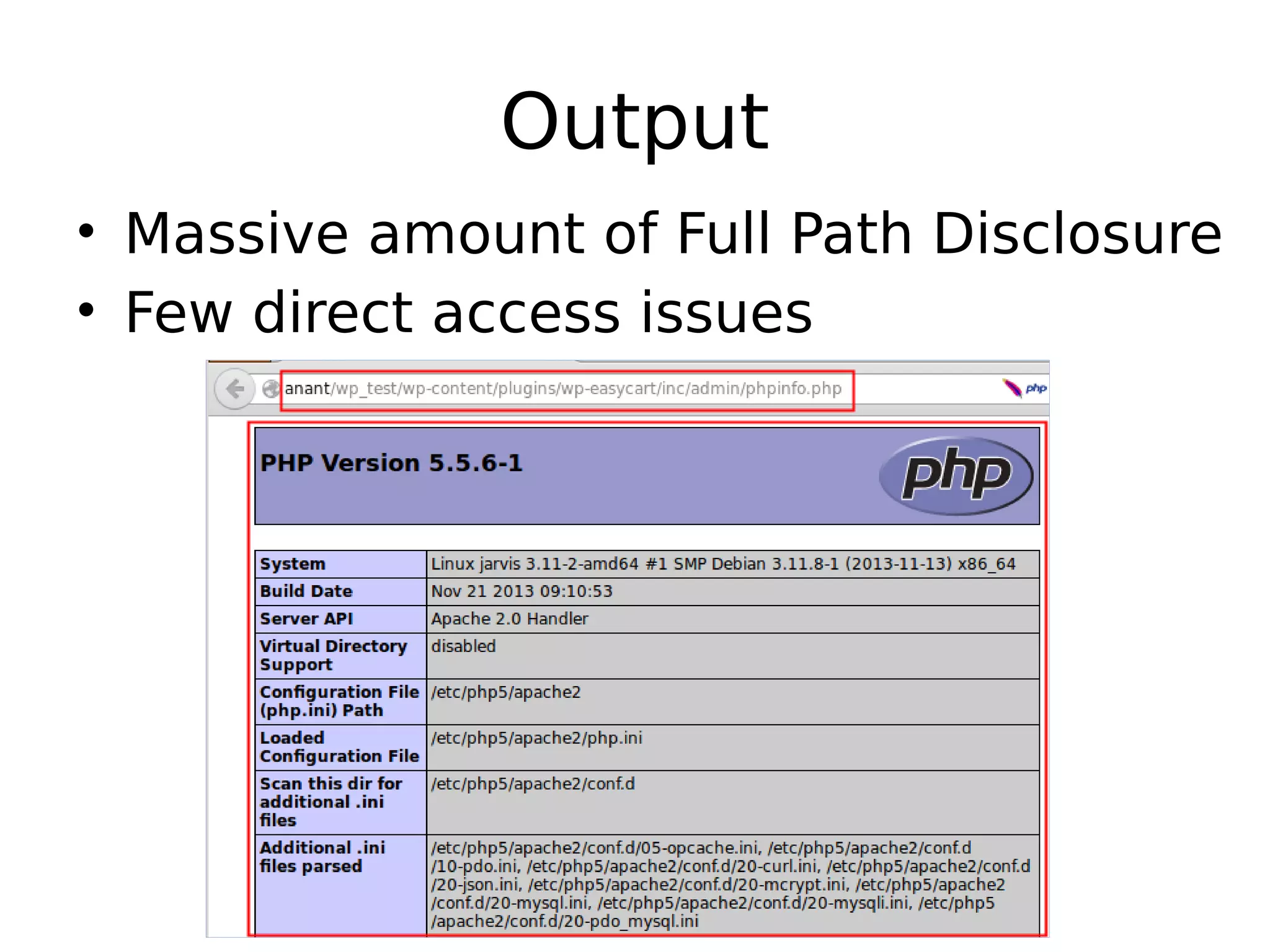
- The author discusses their journey doing source code reviews to find bugs in WordPress plugins and themes. They started with just two people manually reviewing code but then automated the process and expanded their team. - Through their Phase 1 efforts analyzing over 250 plugins, they found over 250 issues. They are now focusing on authenticated vulnerabilities in Phase 2 like SQL injection, XSS, and CSRF. - They have created some open source tools to help with the process and are seeking volunteers to help make open source software more secure by joining their Codevigilant platform.




















![XSS • We thought its as simple as getting a <script>alert(‘XSS’)</script> back • Alas that should have been the case. • How to find it via Source code review. – Echo $_GET[‘input’]; • Grep “echo $_GET” should work](https://image.slidesharecdn.com/mytrystwithsourcecodereviewanantc0c0n2014day2-150404234111-conversion-gate01/75/My-tryst-with-sourcecode-review-28-2048.jpg)