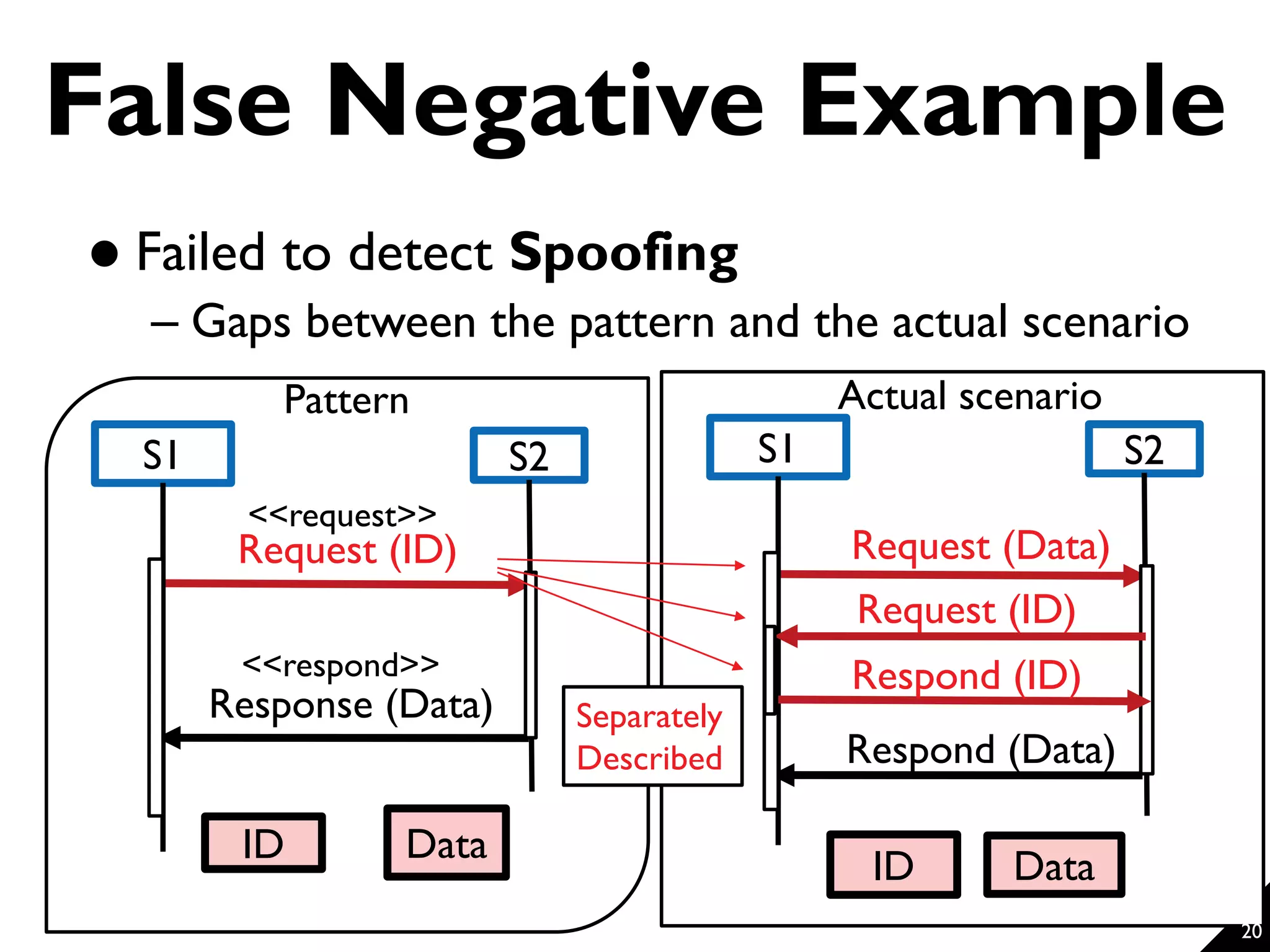
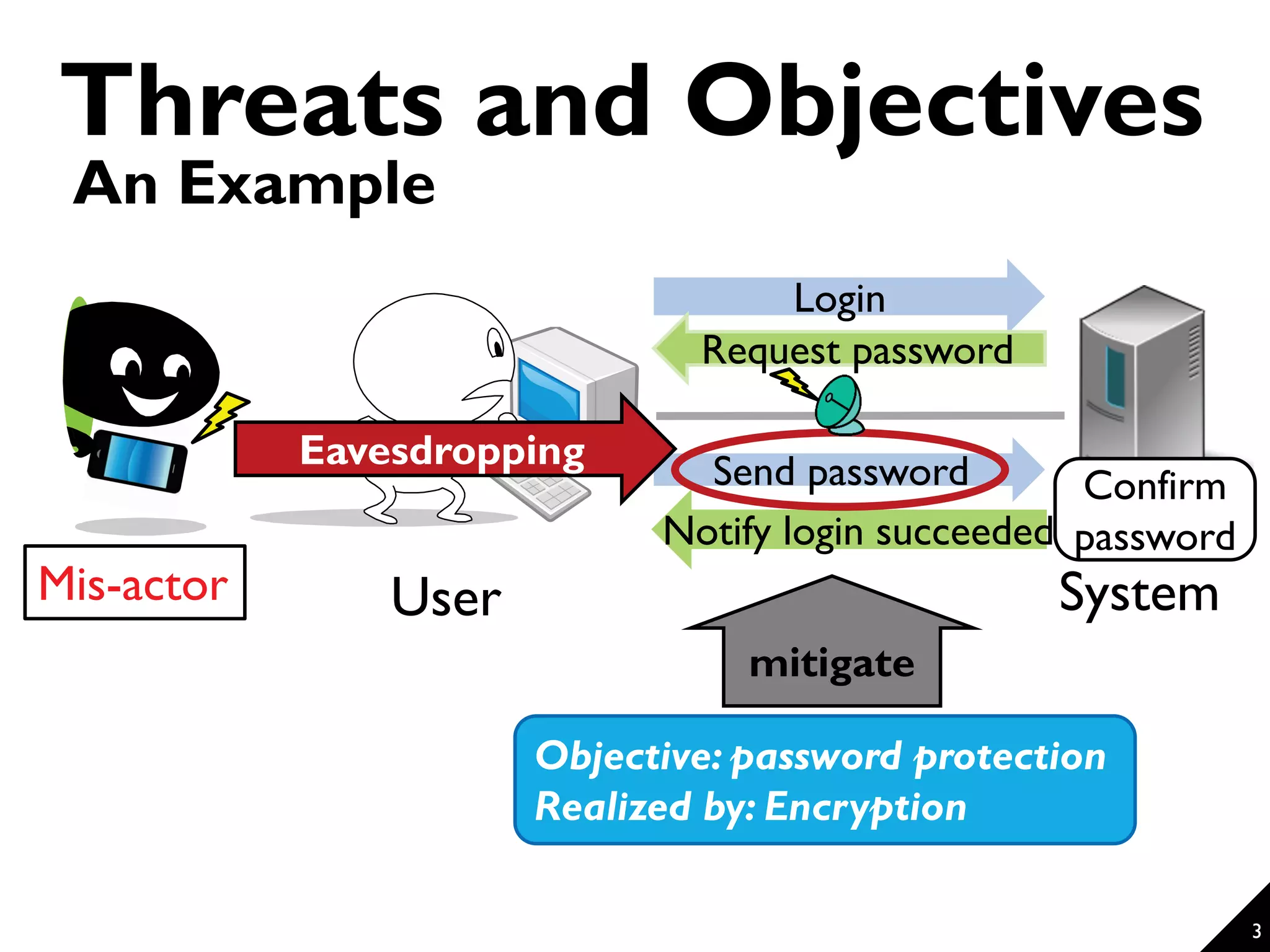
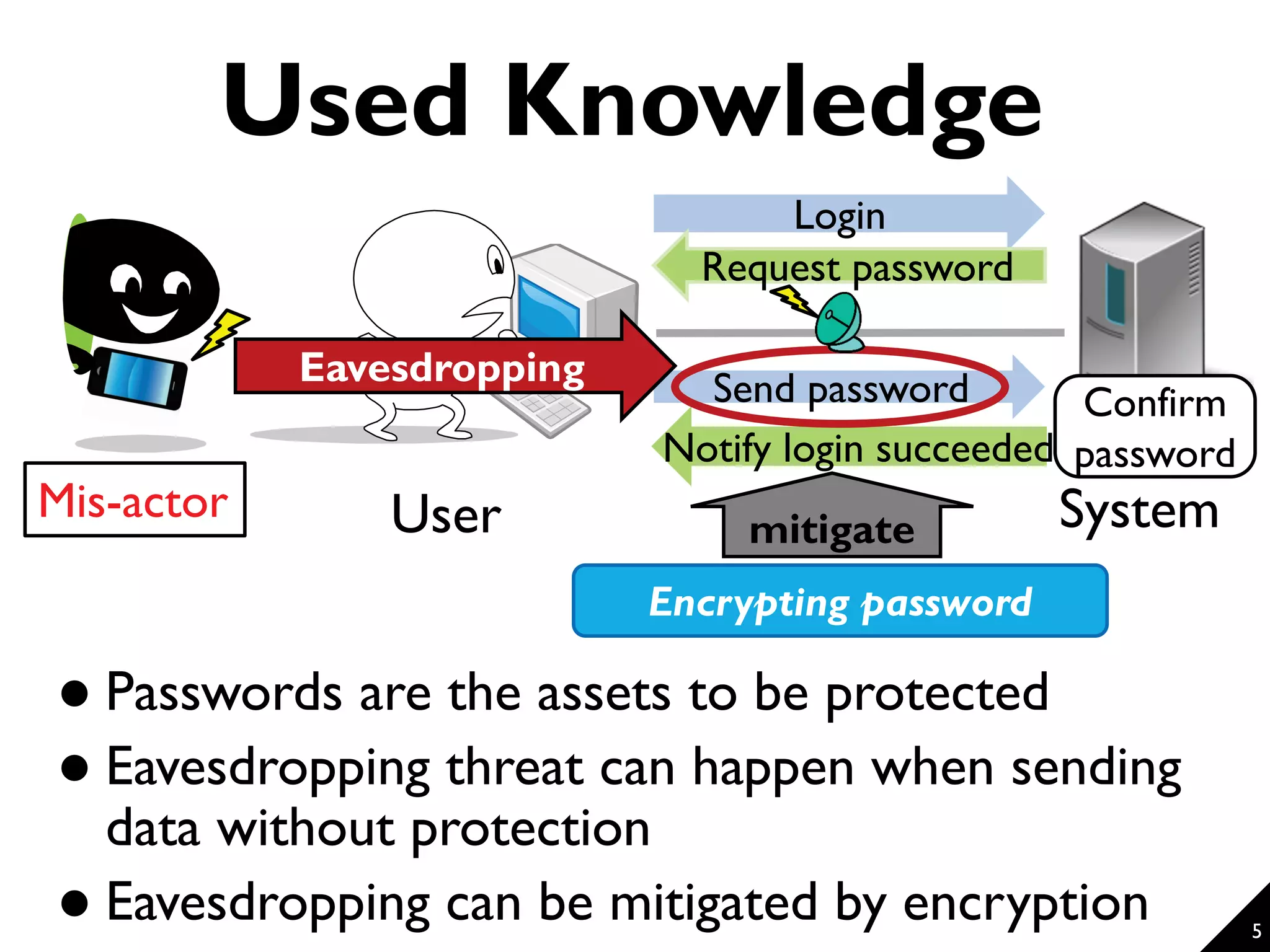
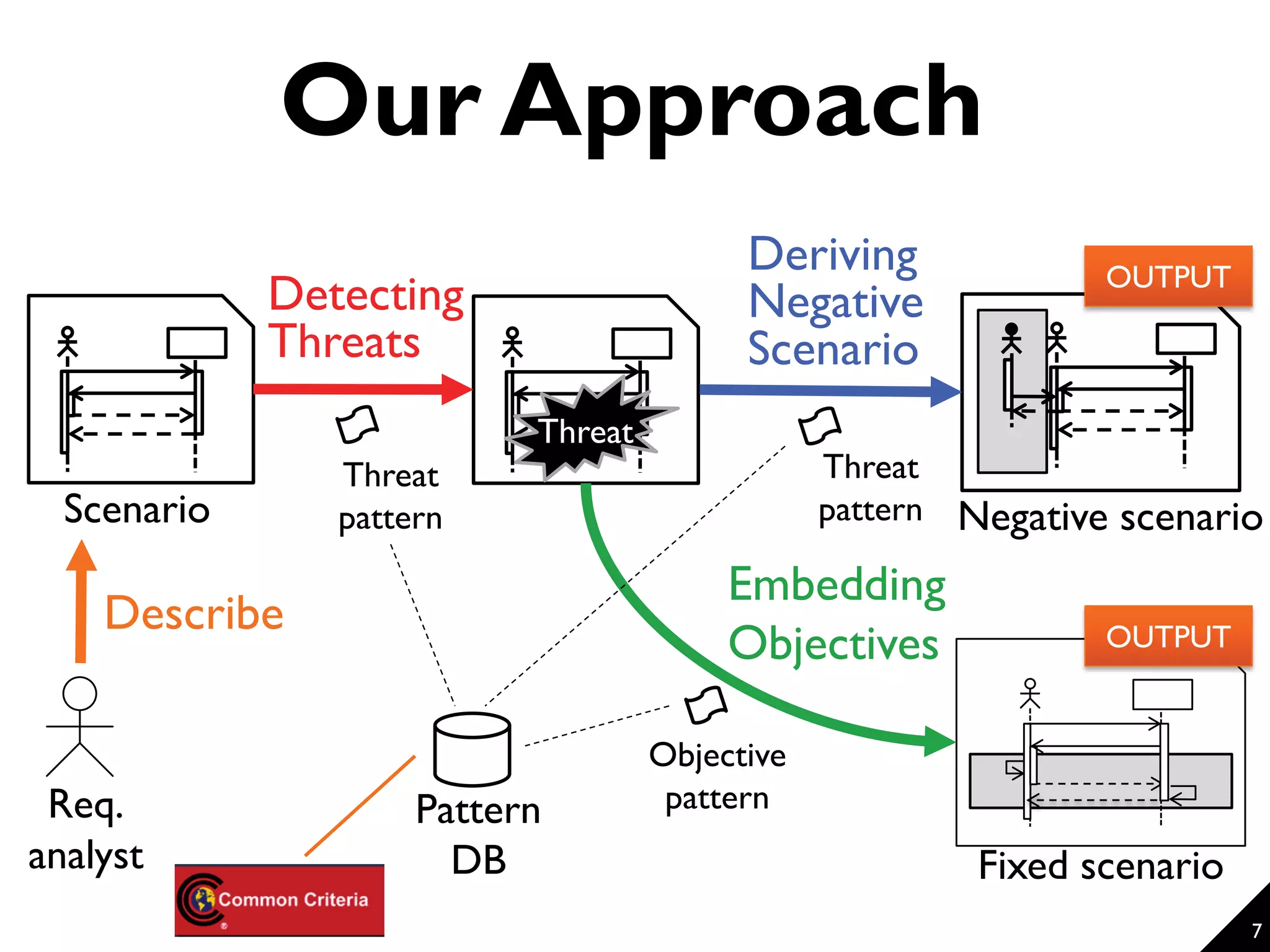
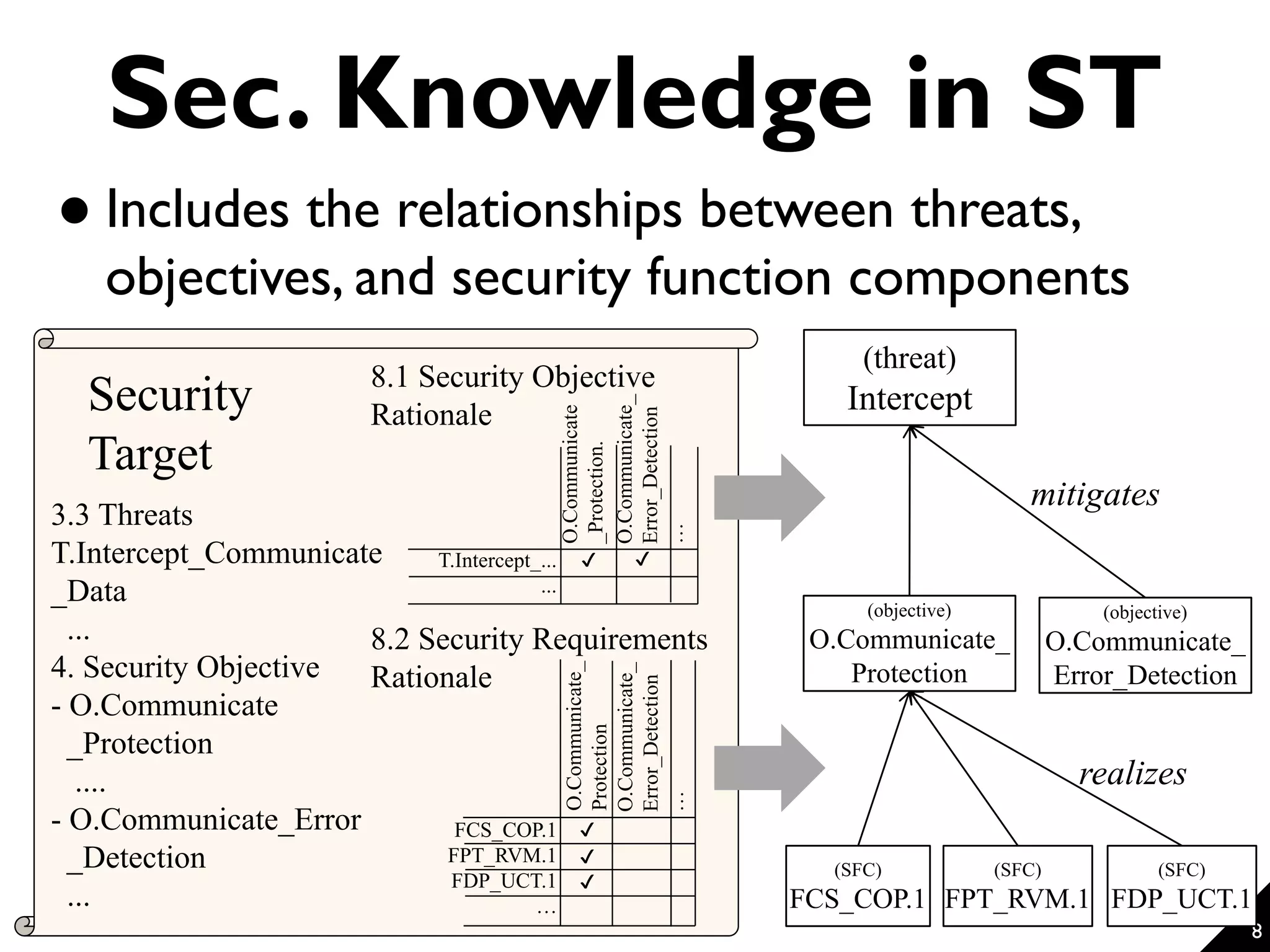
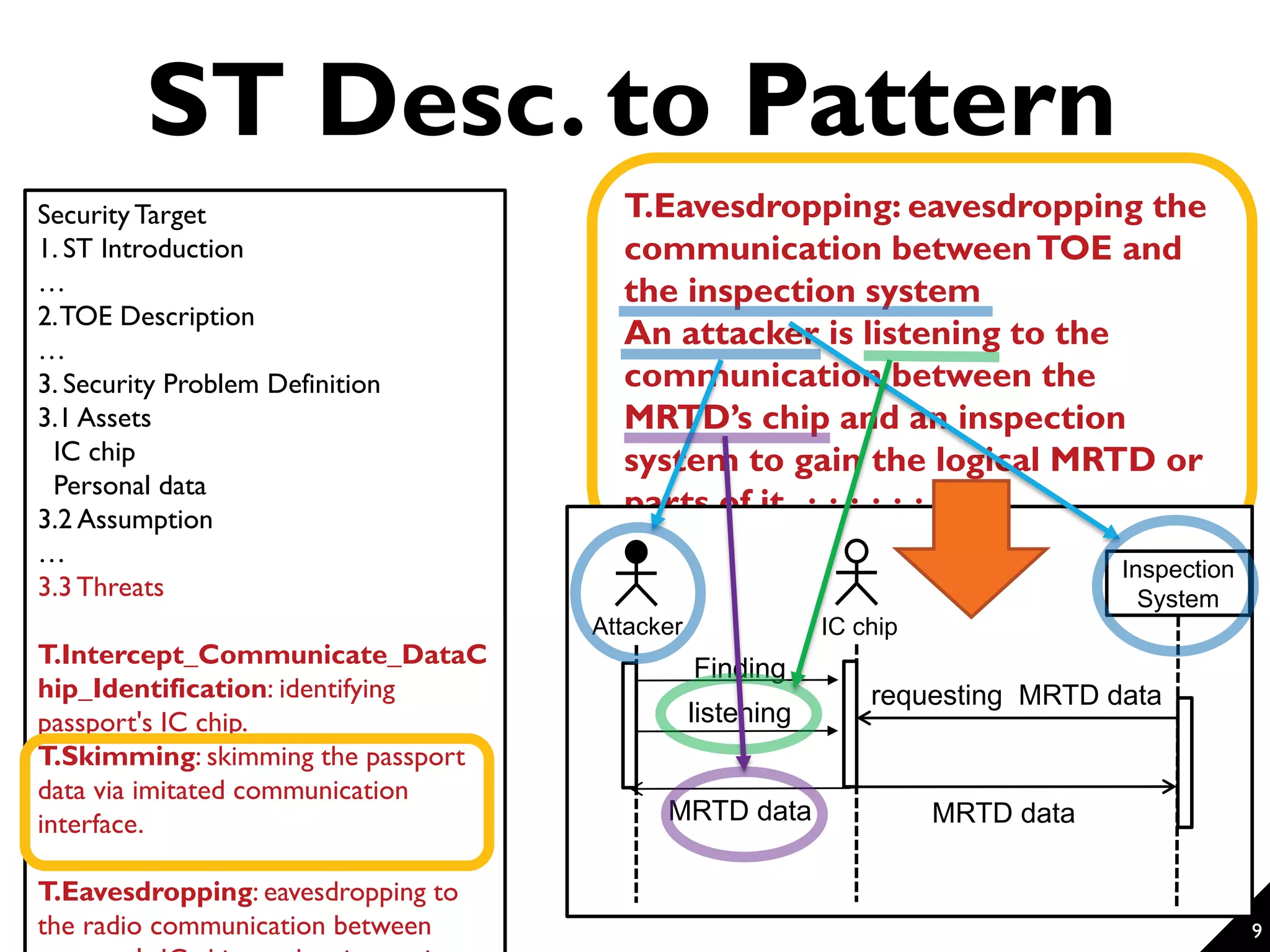
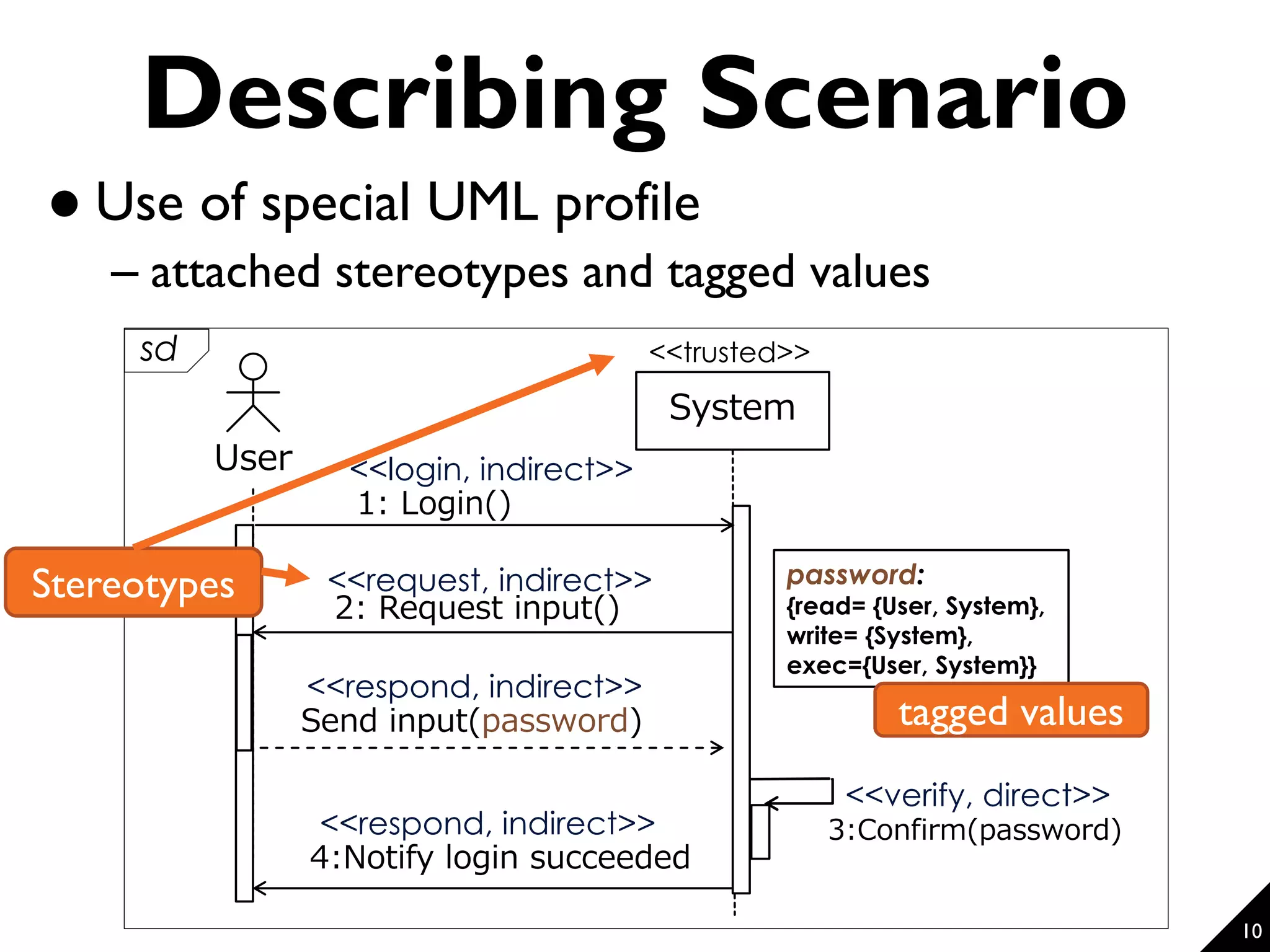
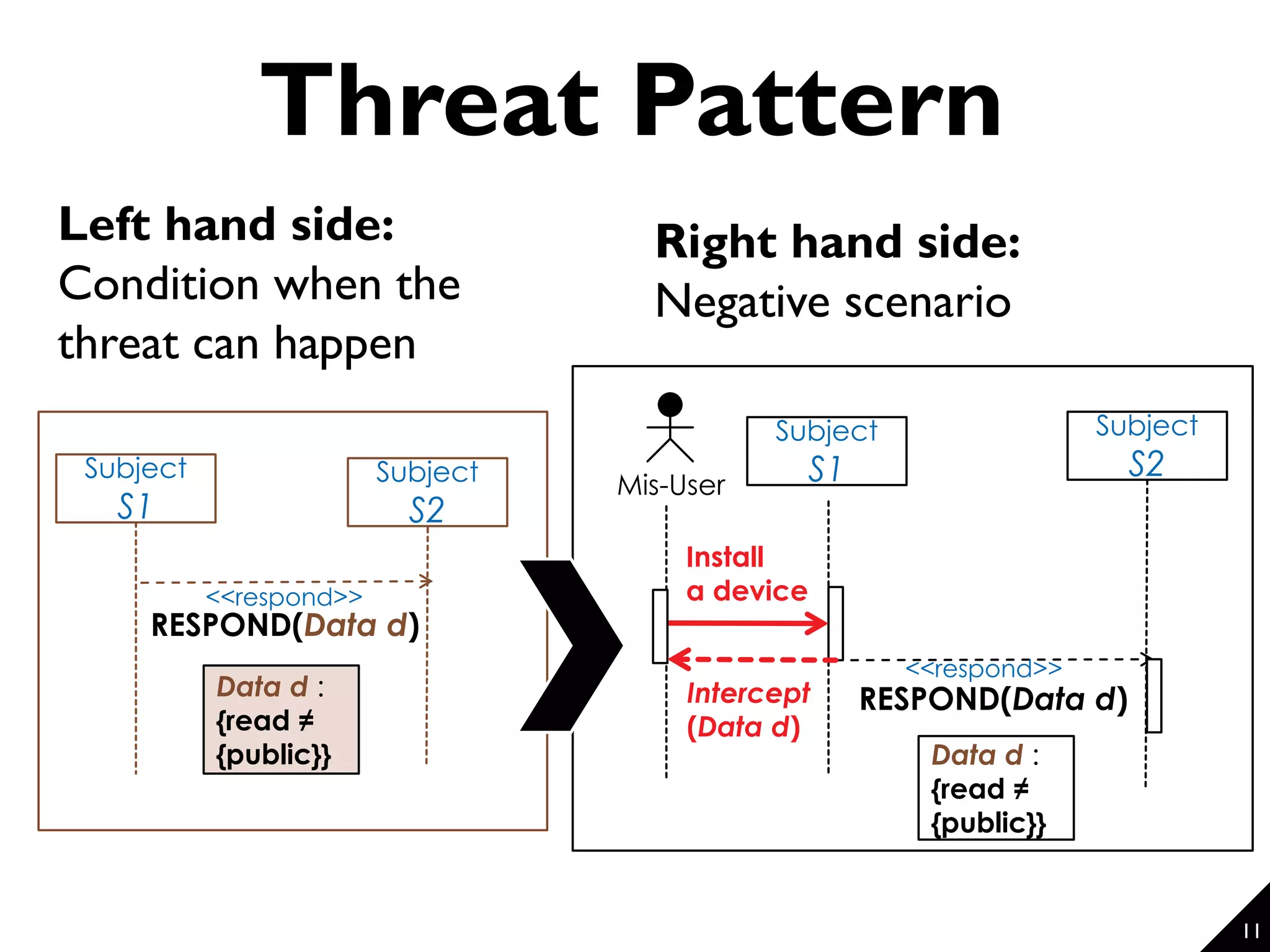
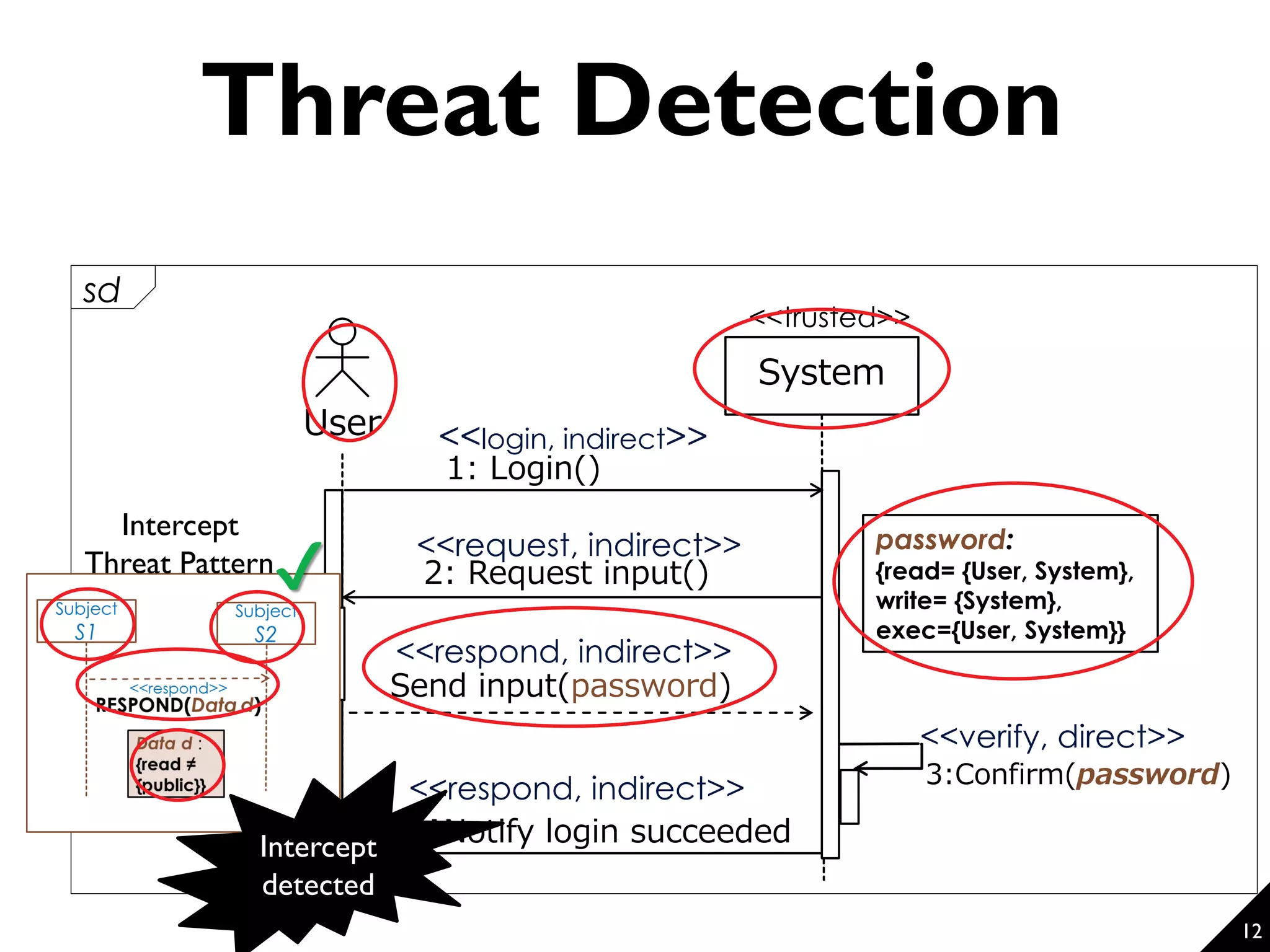
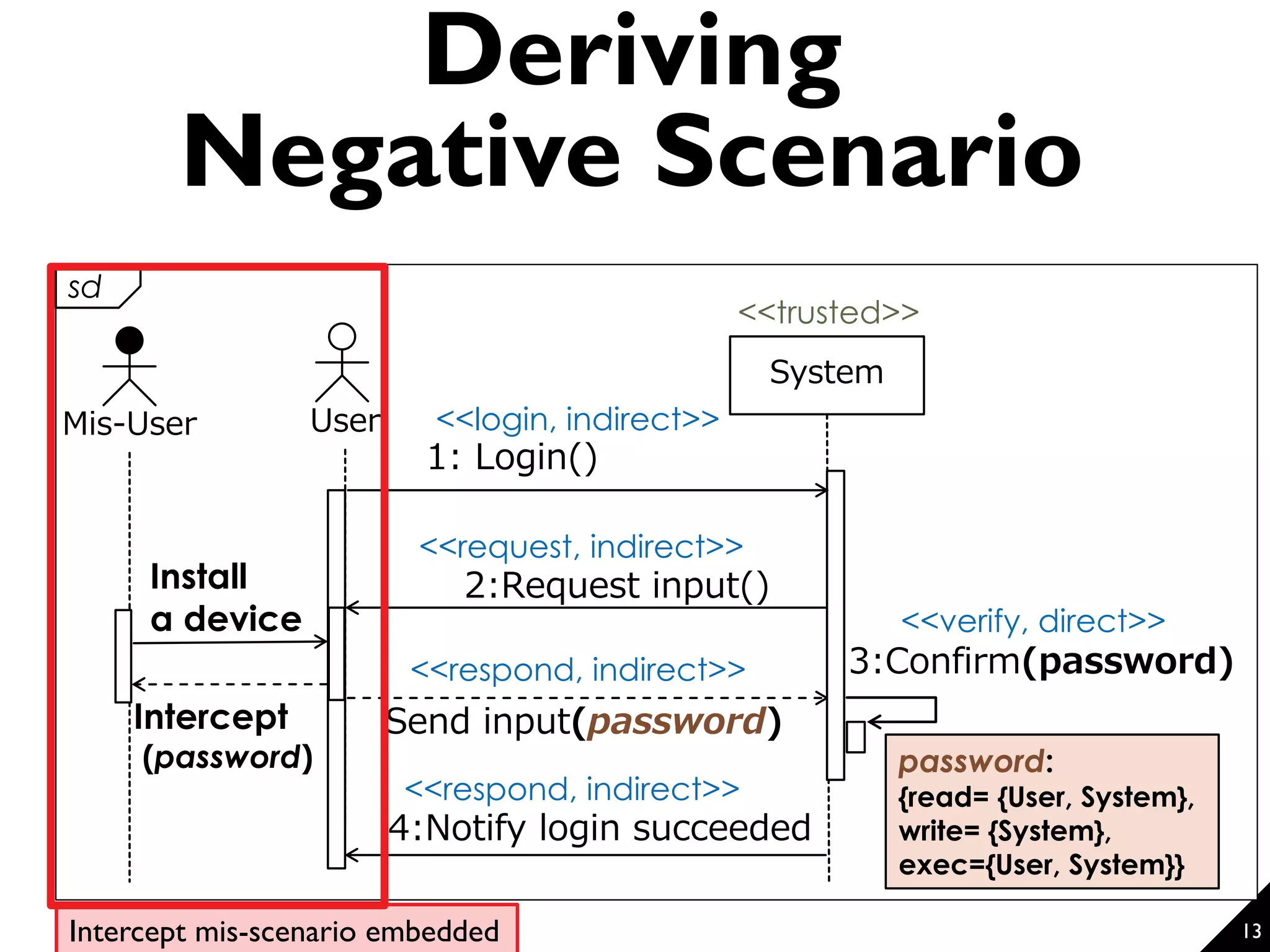
This document proposes a technique for eliciting security requirements early in the development process. It involves using security knowledge from security targets and common criteria standards. Potential threats are detected by matching scenario descriptions to threat patterns using graph transformation. When a threat is detected, a negative scenario is derived and security objectives are embedded to address the threat. An evaluation of the technique found it could accurately detect threats in scenarios from different domains, though some false positives and negatives occurred. Overall, the technique shows promise for aiding the elicitation of security requirements.





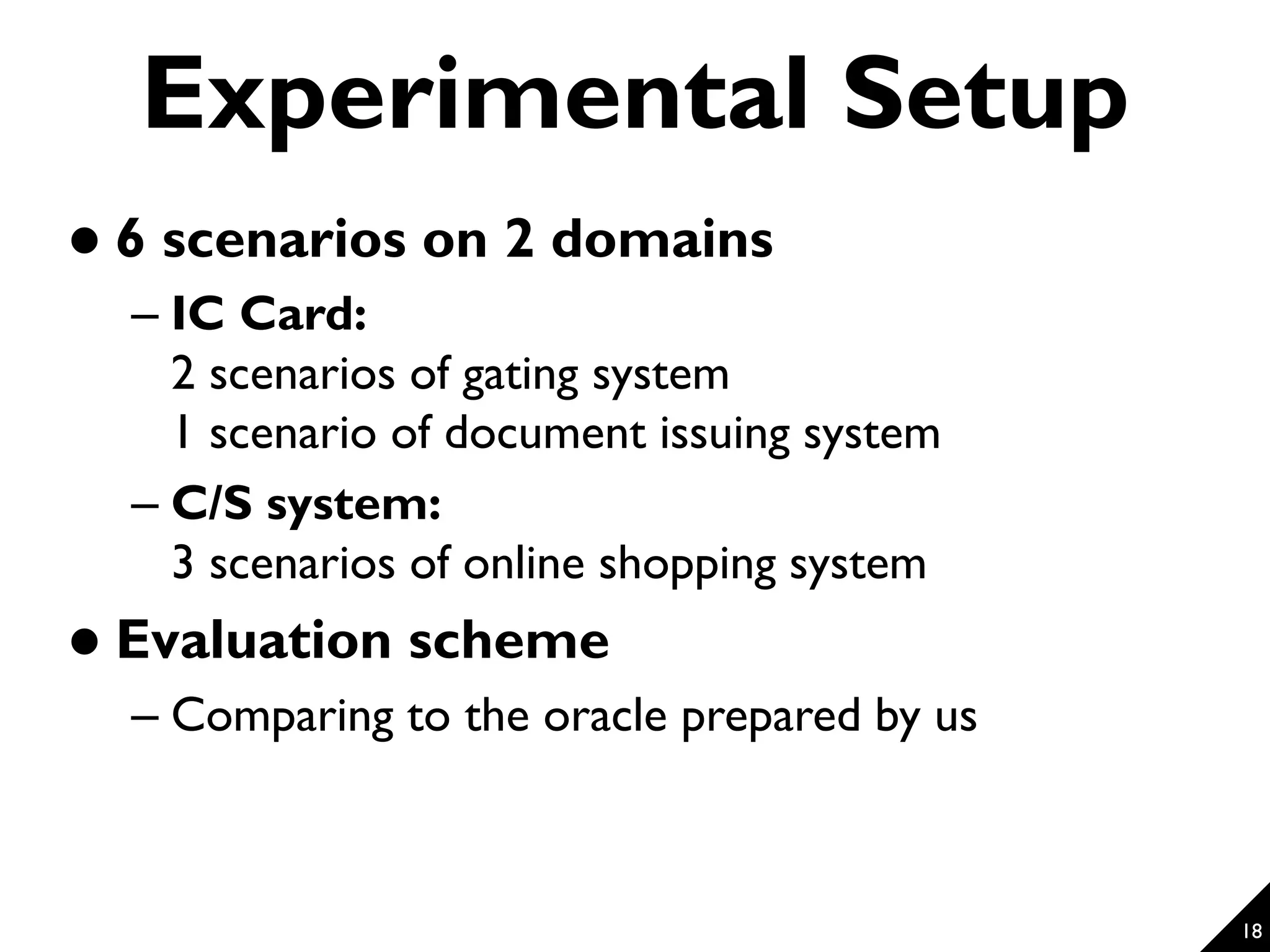
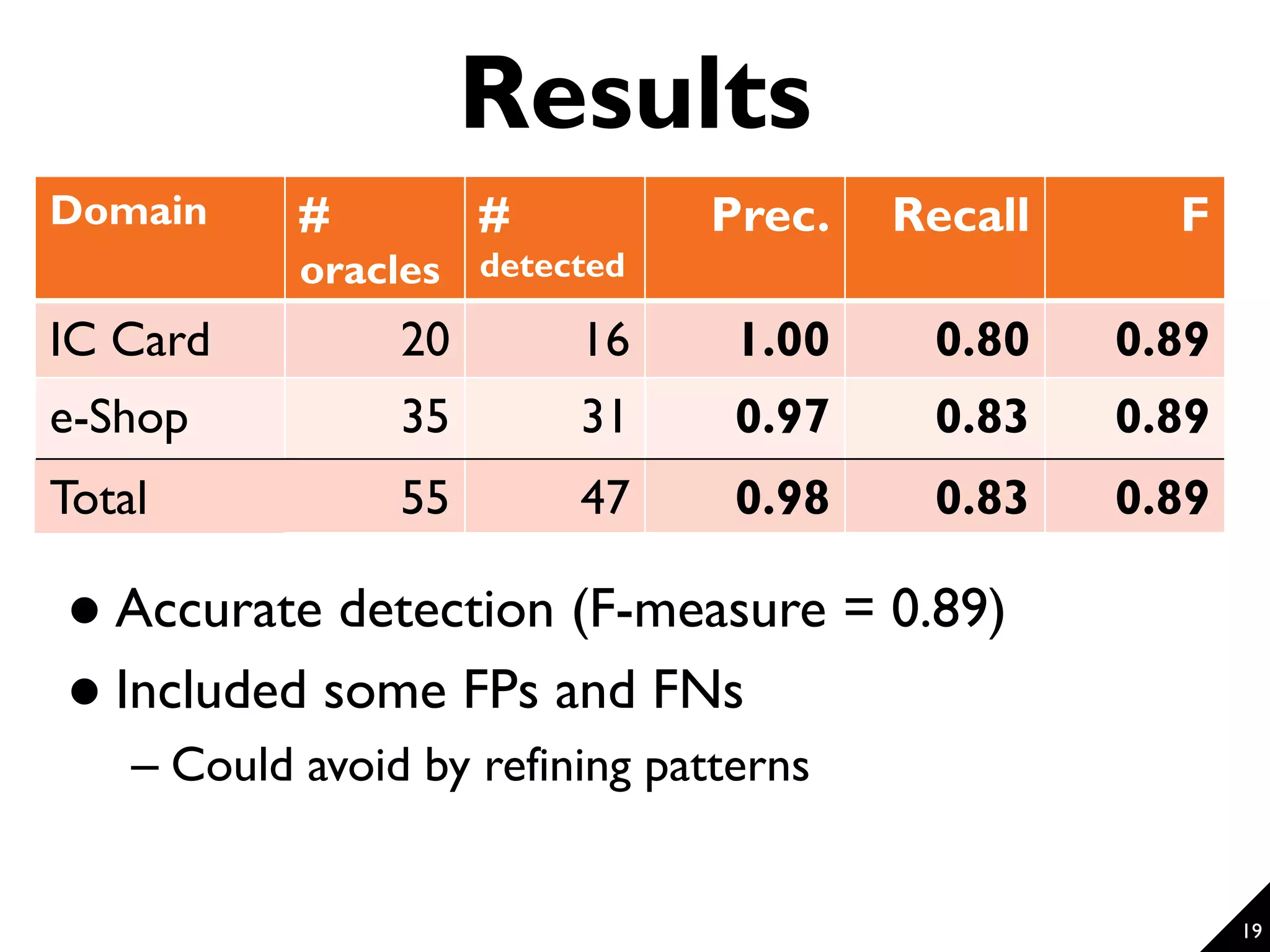
![17 Preliminary Evaluation [Evaluation Question 1] To what extent does the proposed technique accurately detect threats in the given scenarios and introduce objectives based on the detected threats? [Evaluation Question 2] Do the differences of the problem domains of the given scenarios affect the accuracy of the detection? Accurately detected (F-measure = 89%) Accurately detected for all systems (though only 2 domains)](https://image.slidesharecdn.com/modelingandutilizingsecurityknowledgeforelicitingsecurityrequirements-161215005616/75/Modeling-and-Utilizing-Security-Knowledge-for-Eliciting-Security-Requirements-17-2048.jpg)