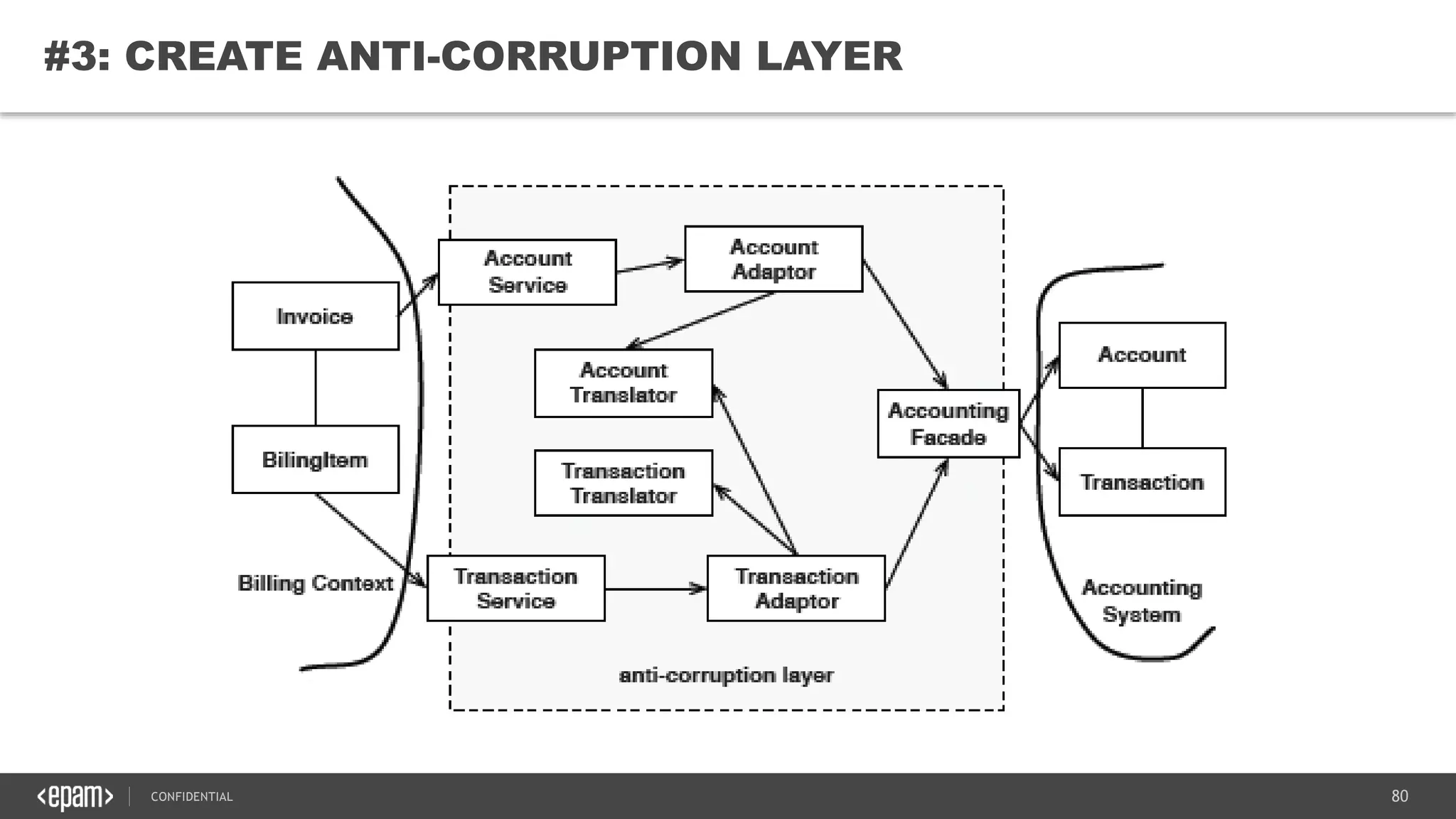
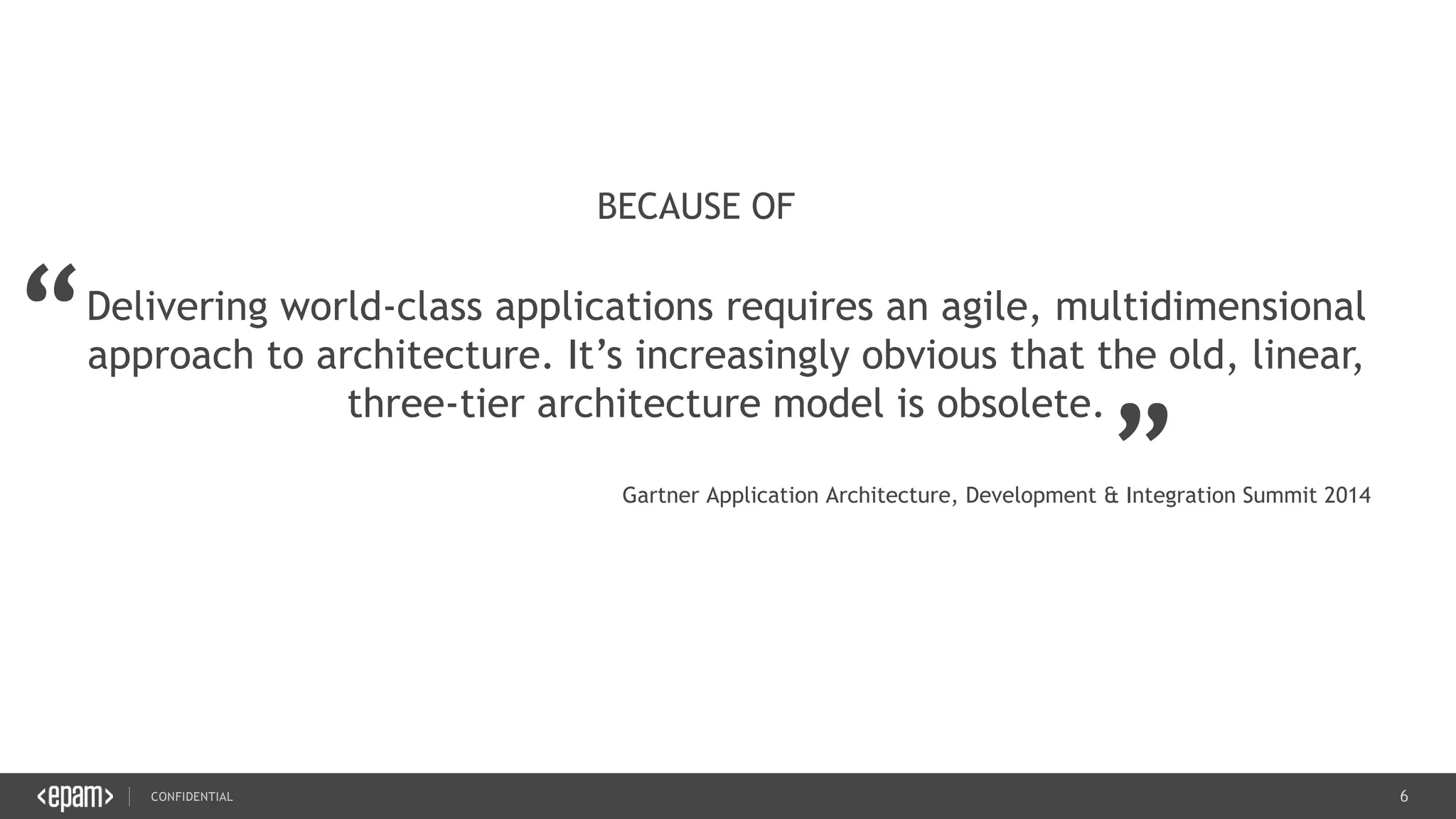
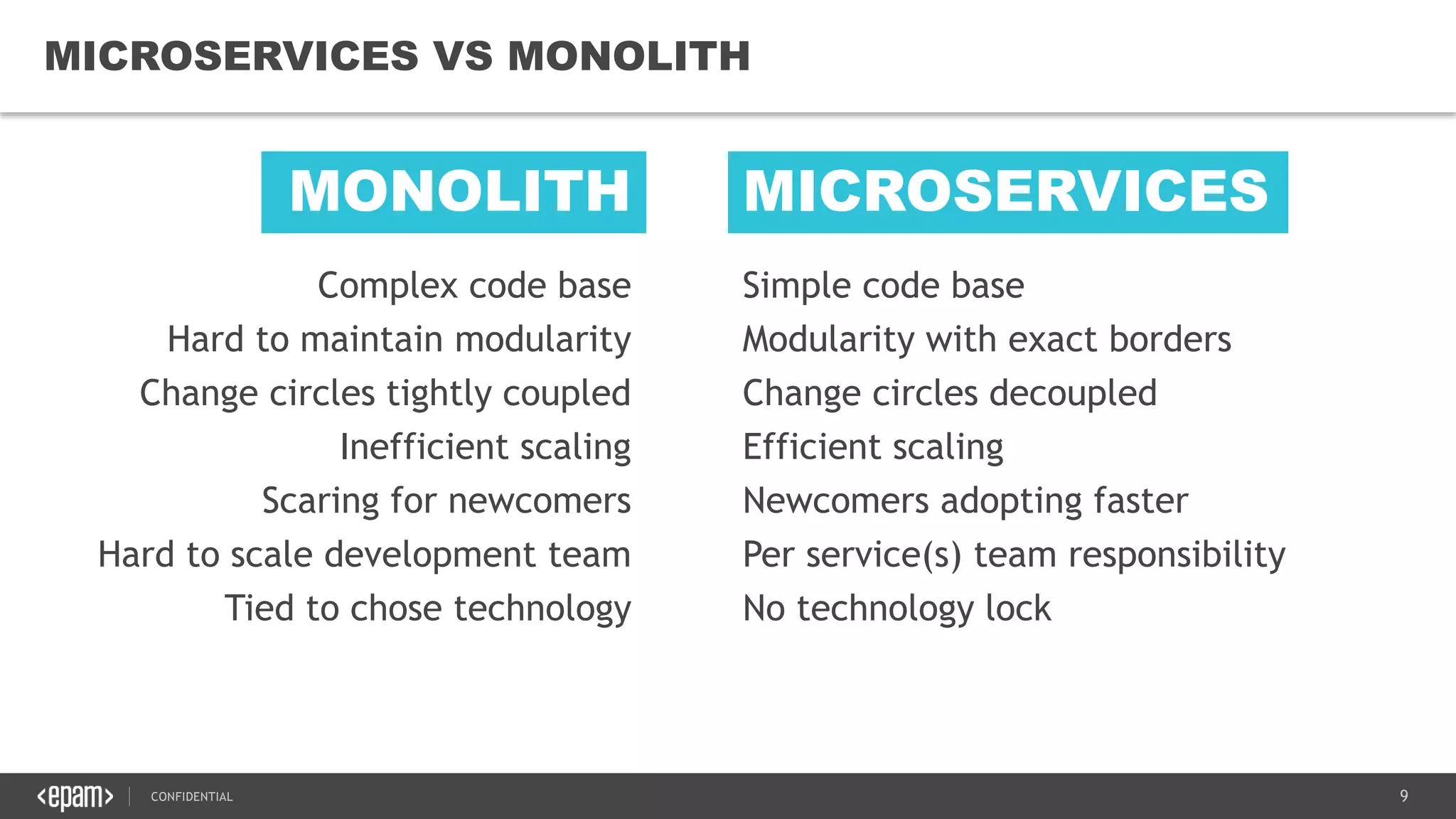
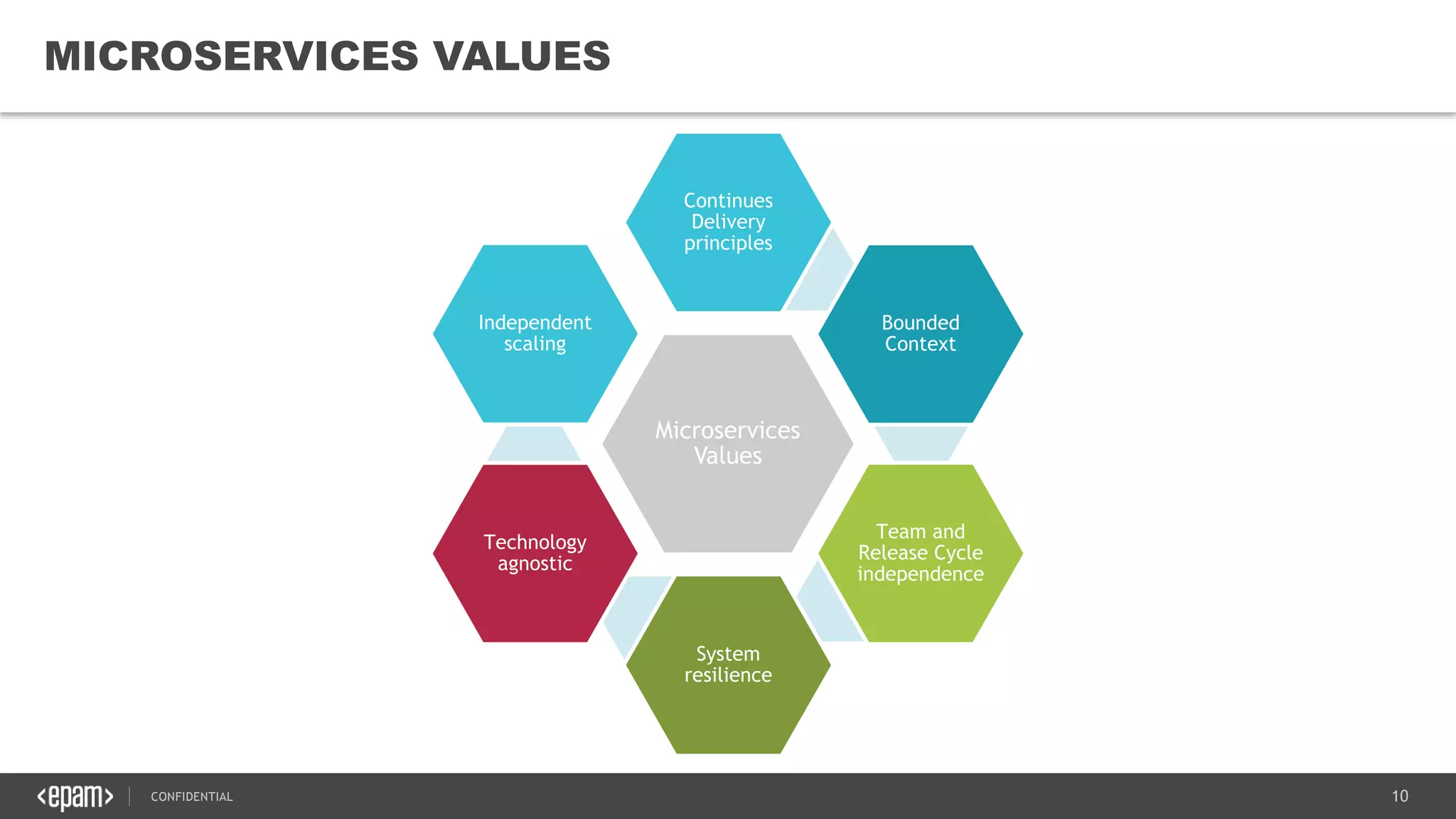
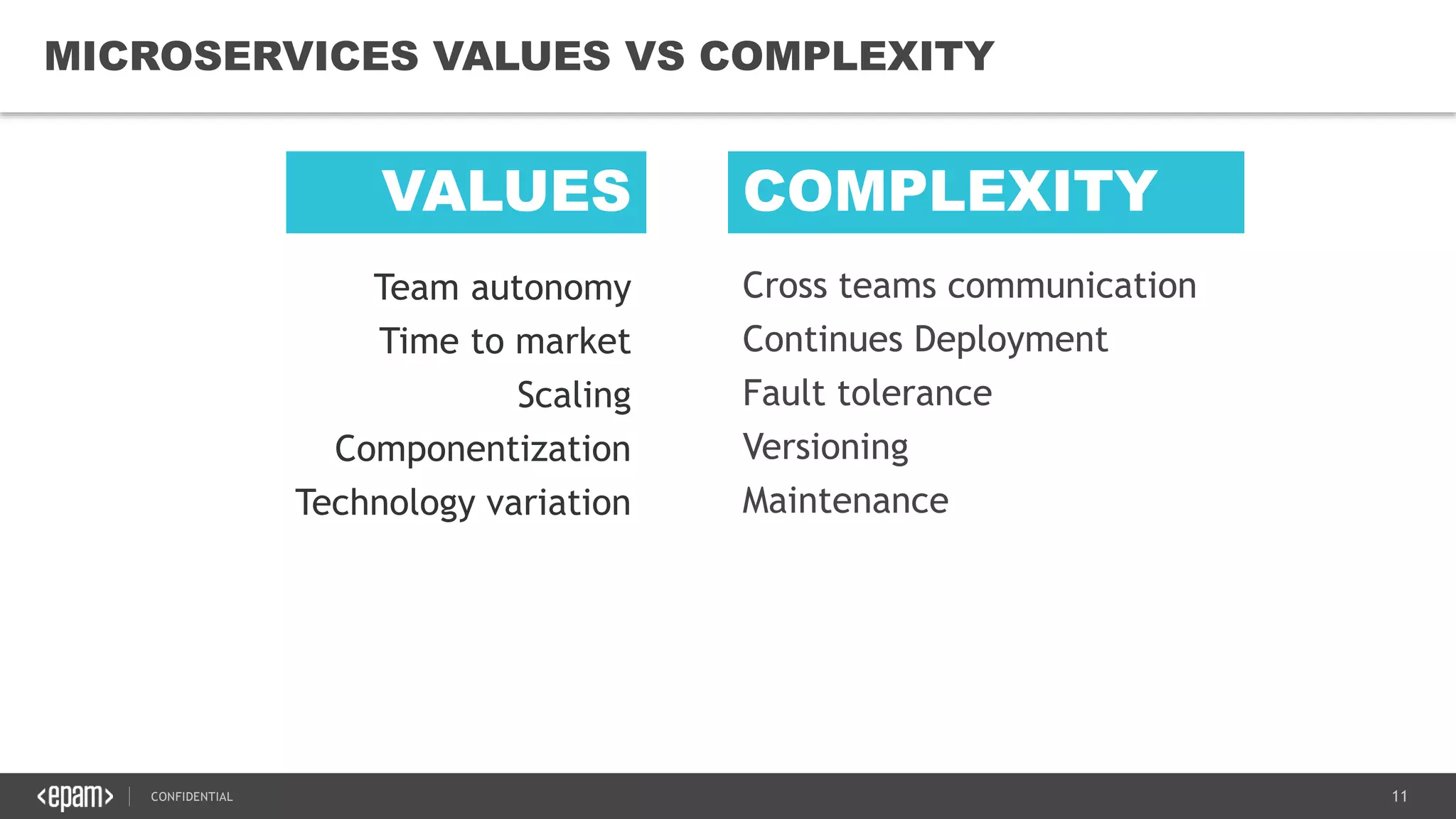
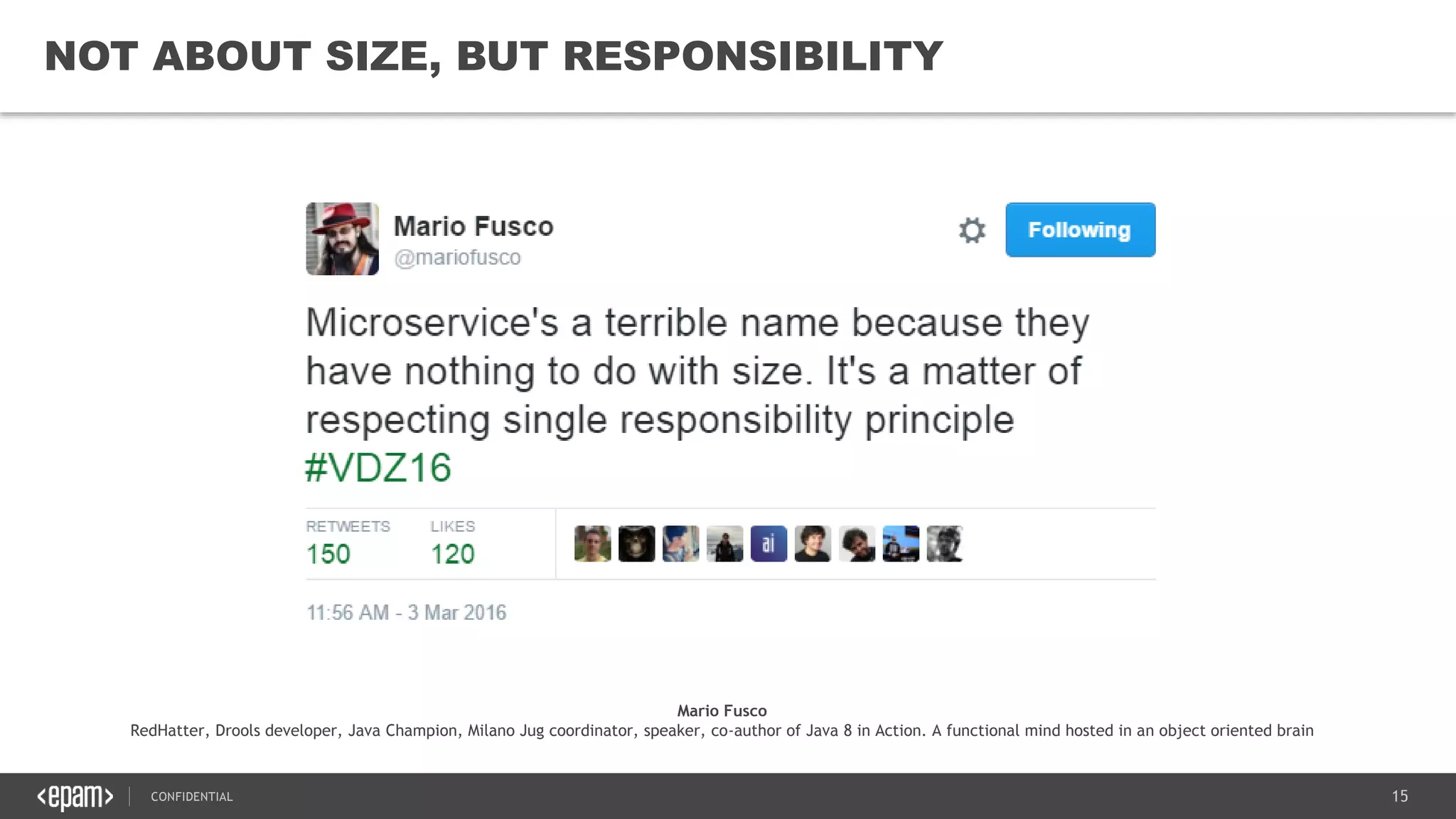
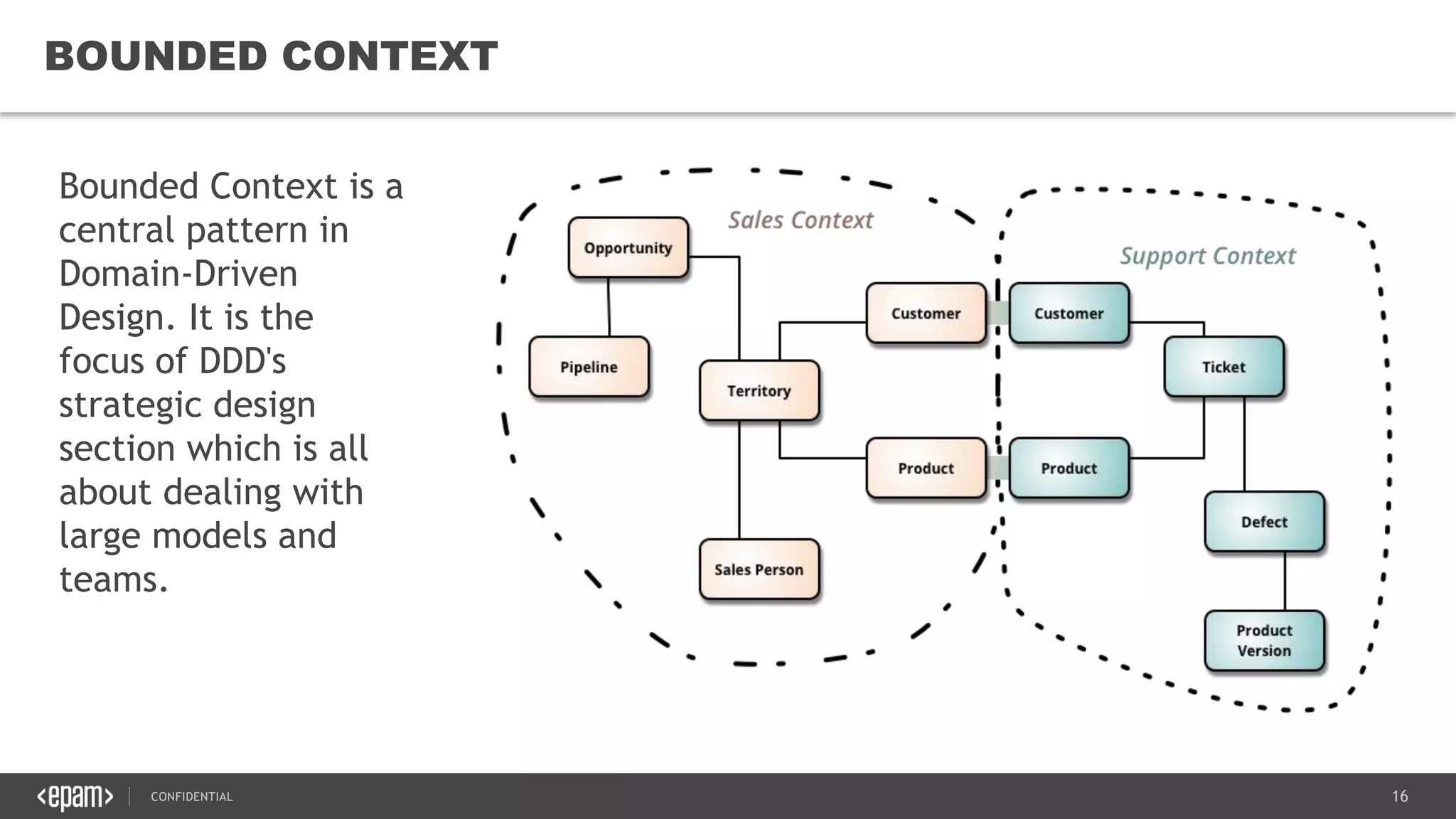
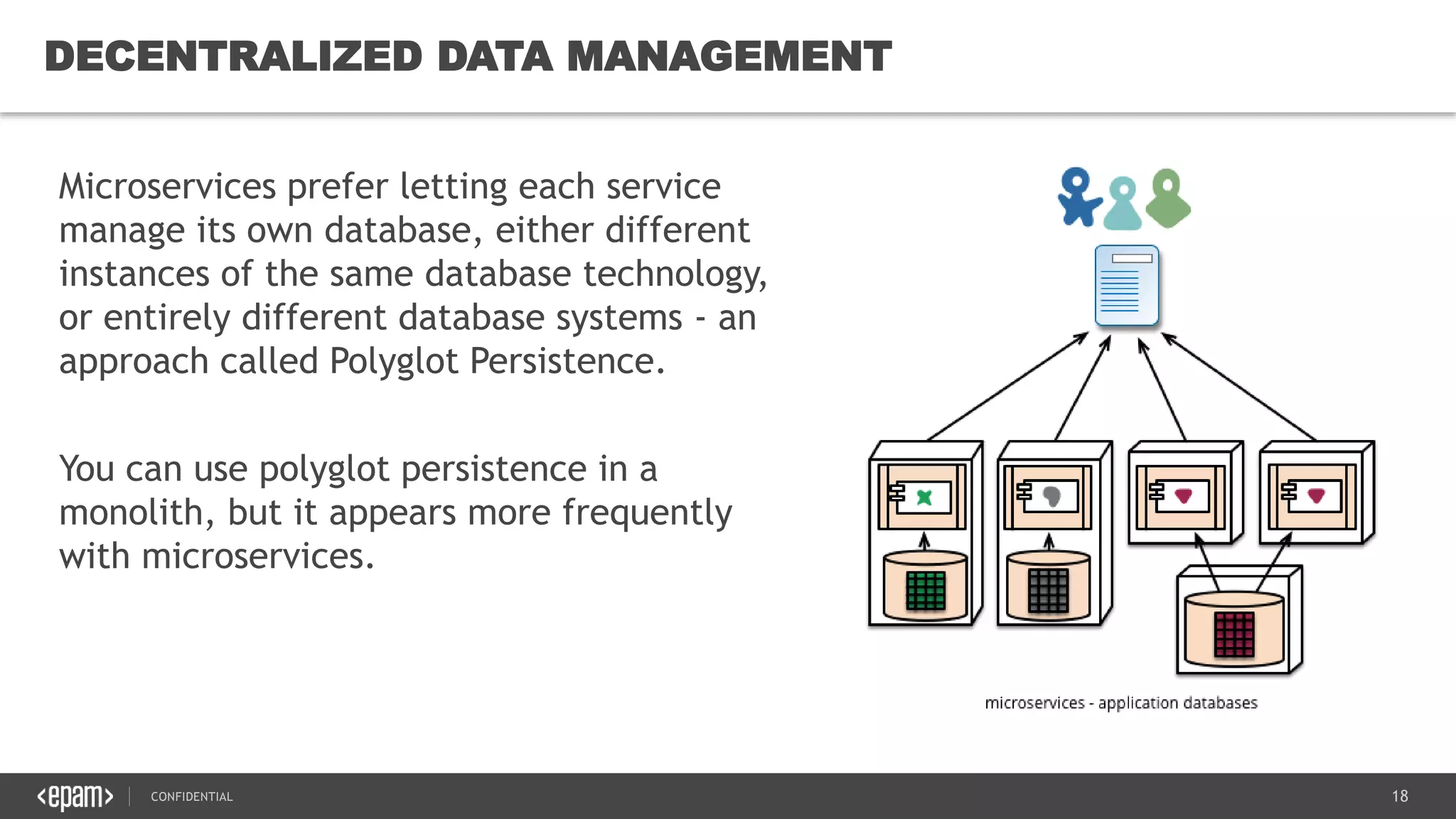
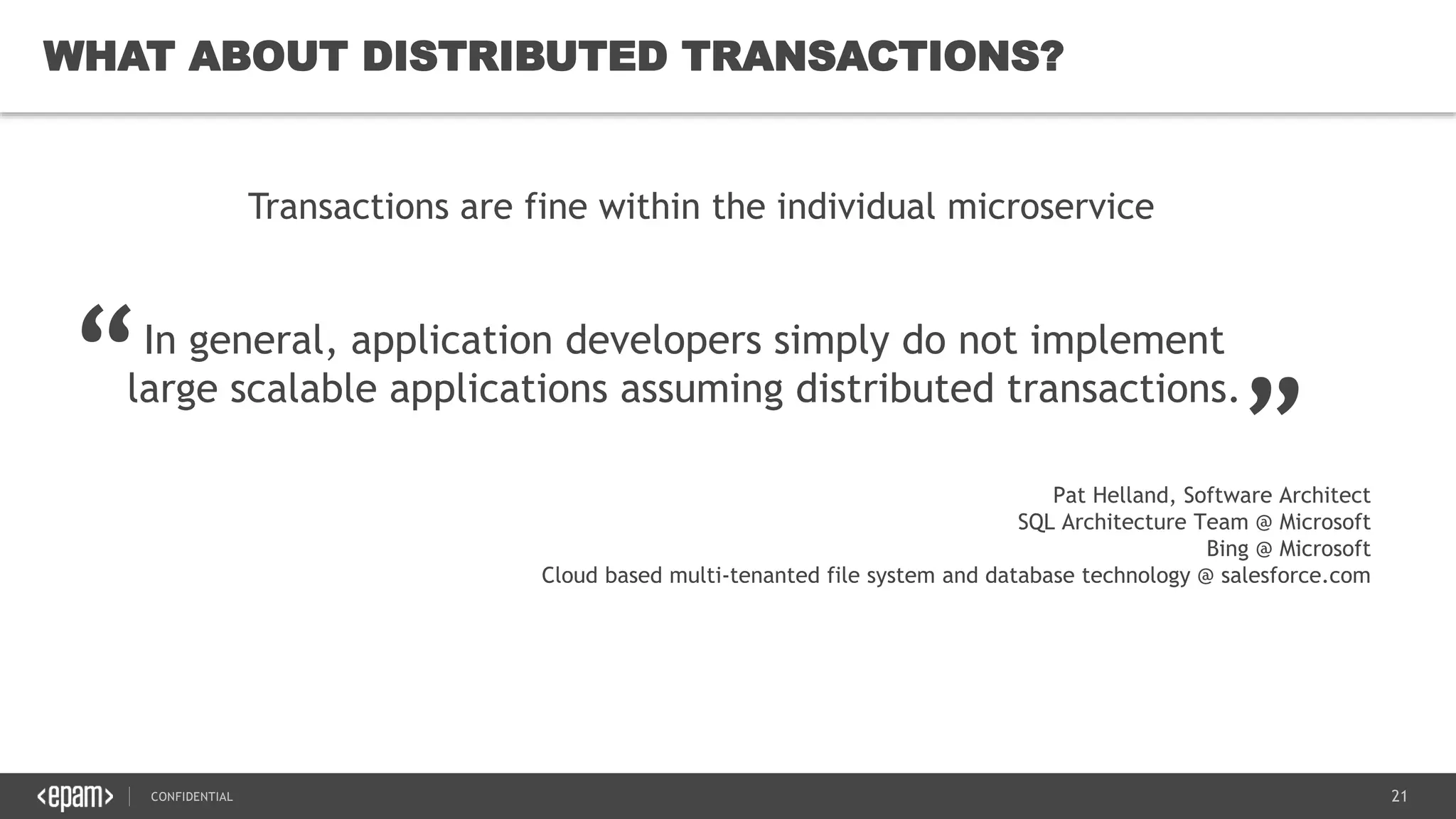
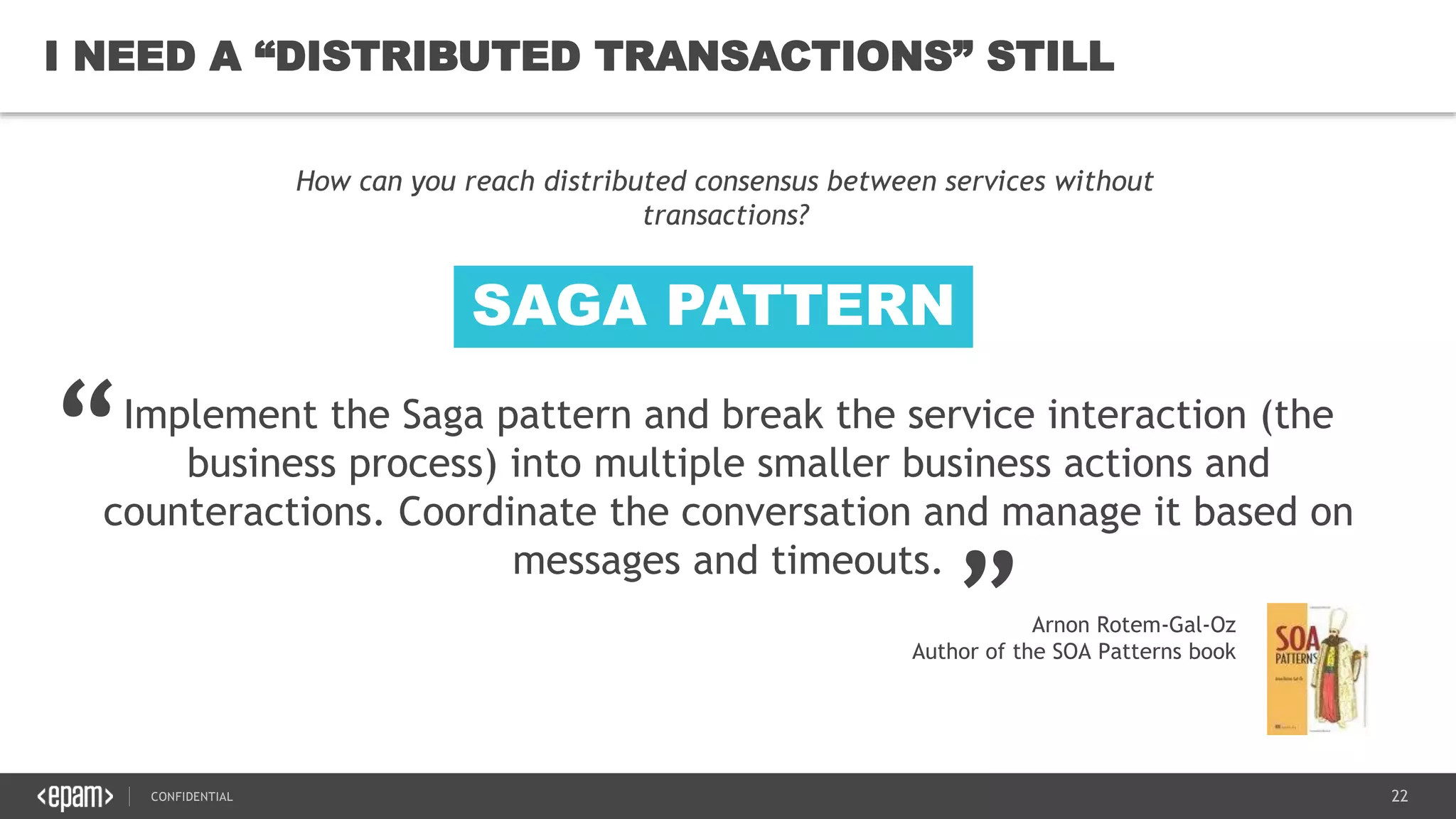
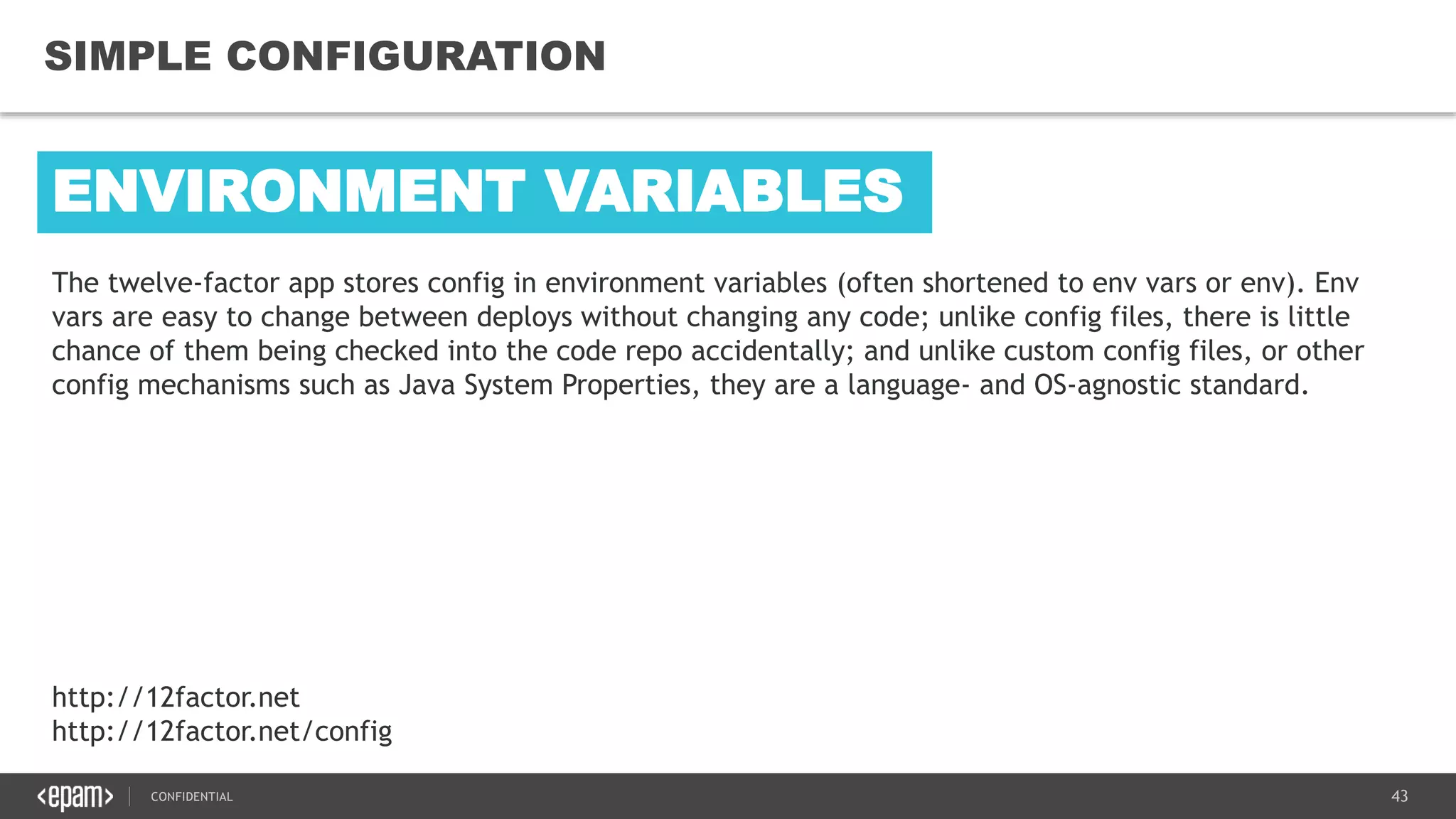
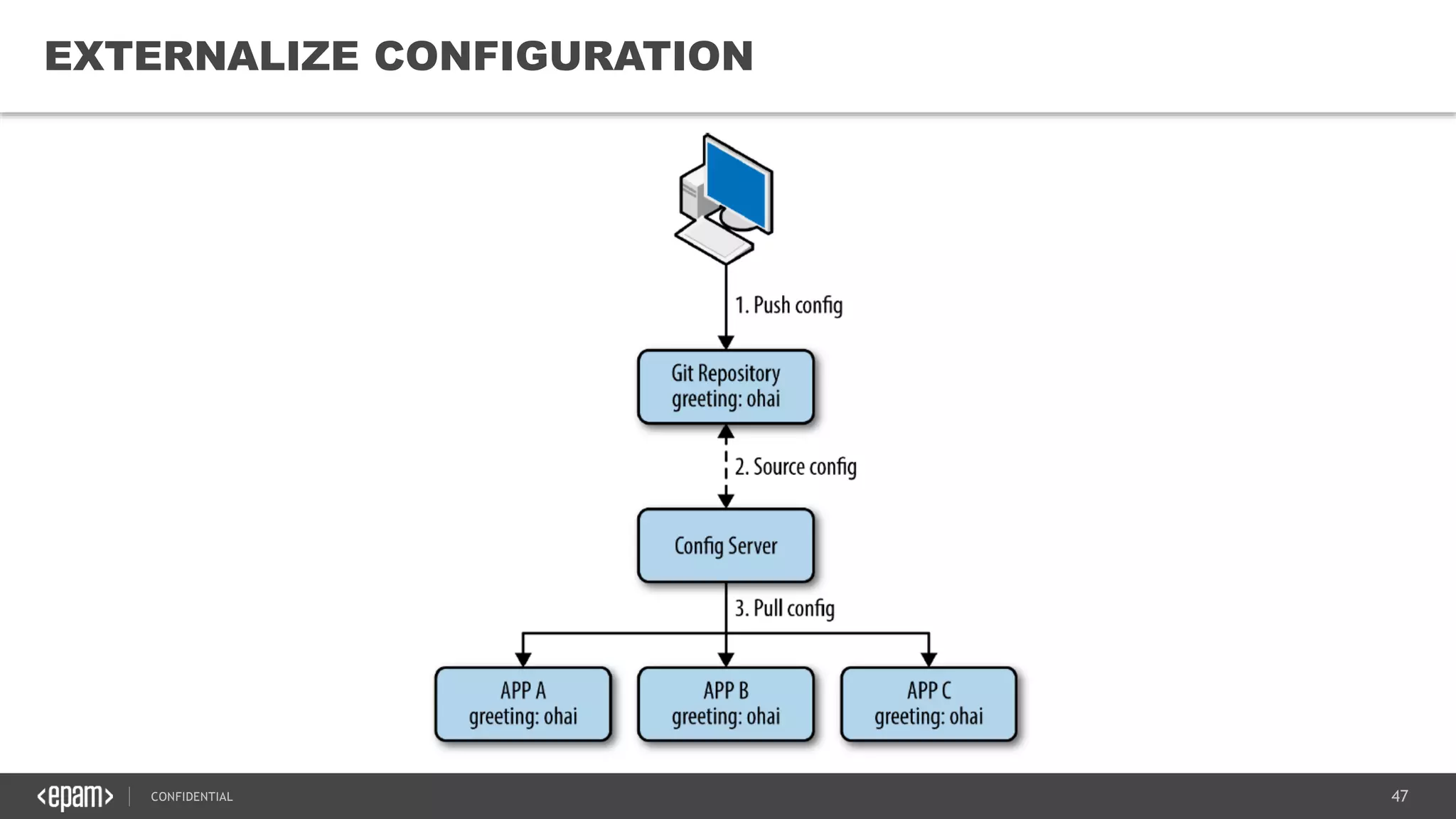
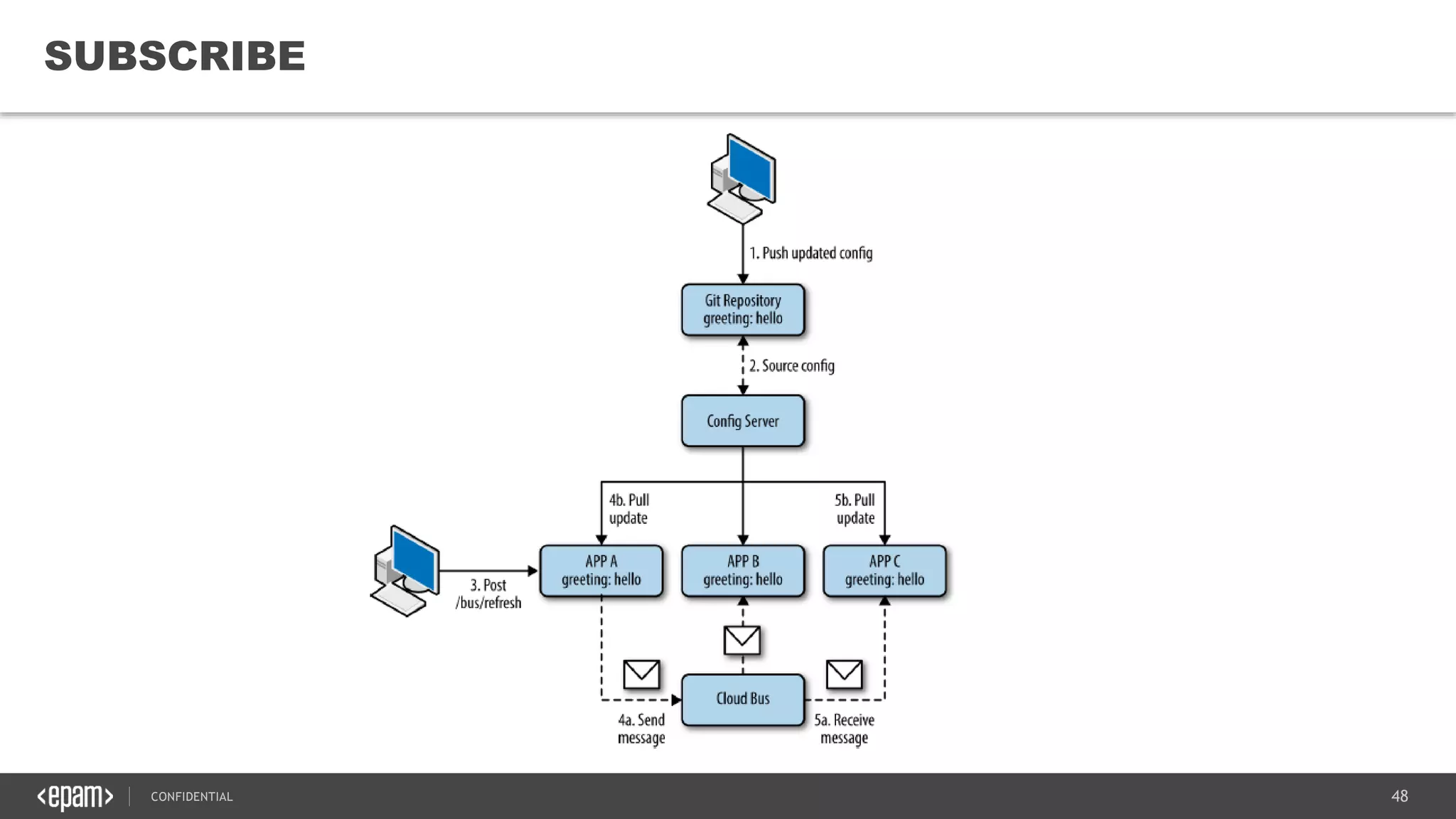
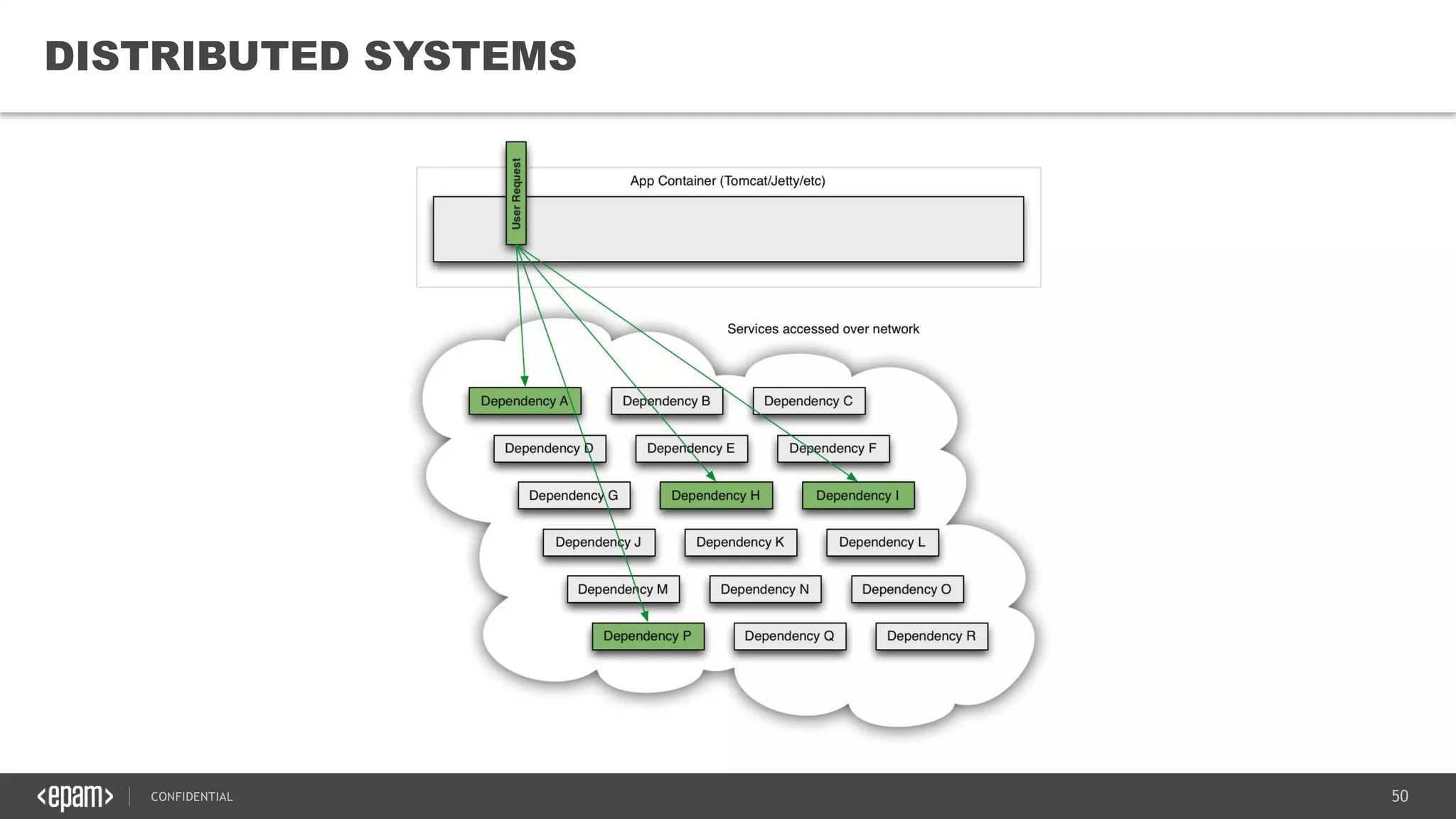
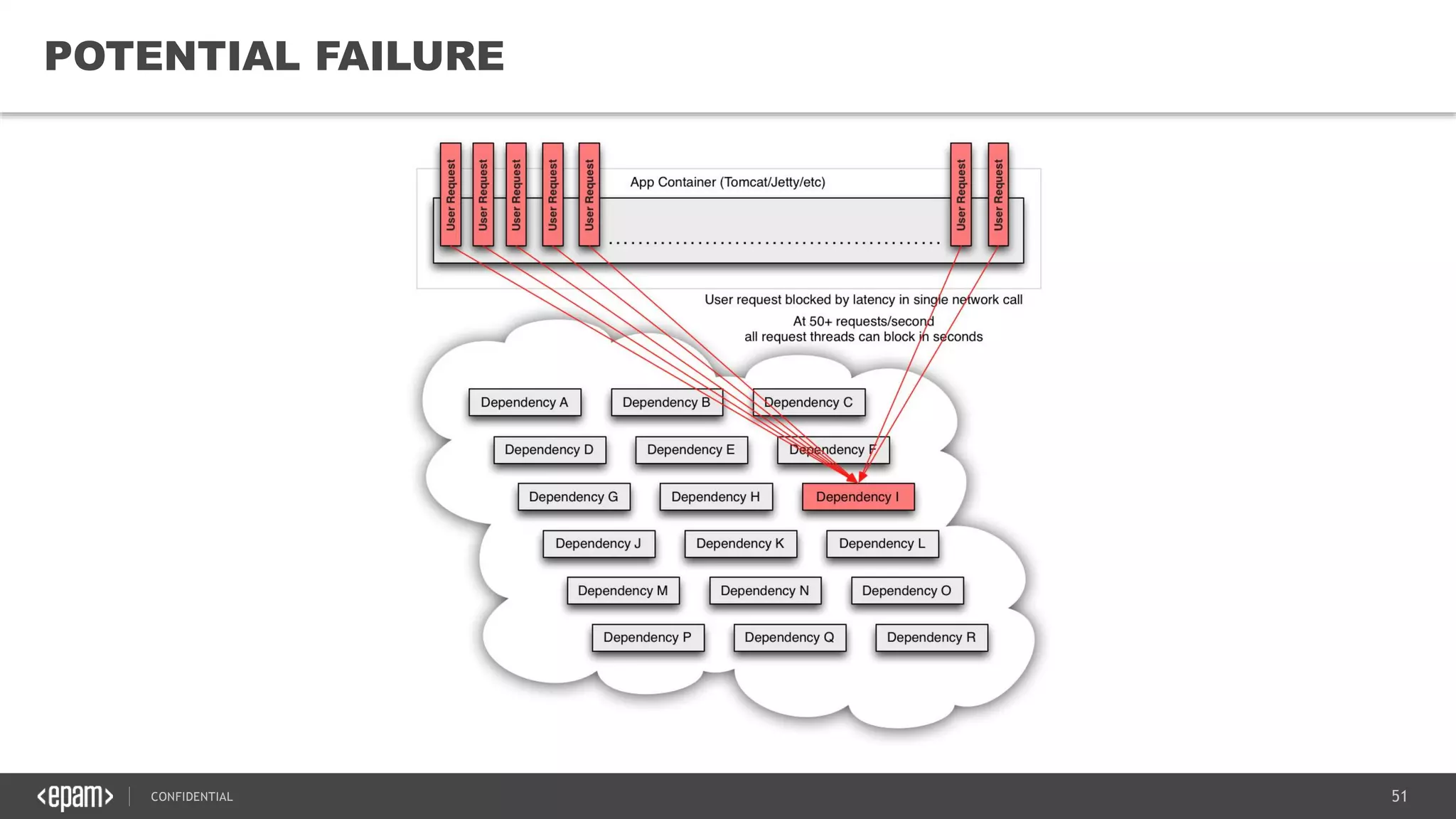
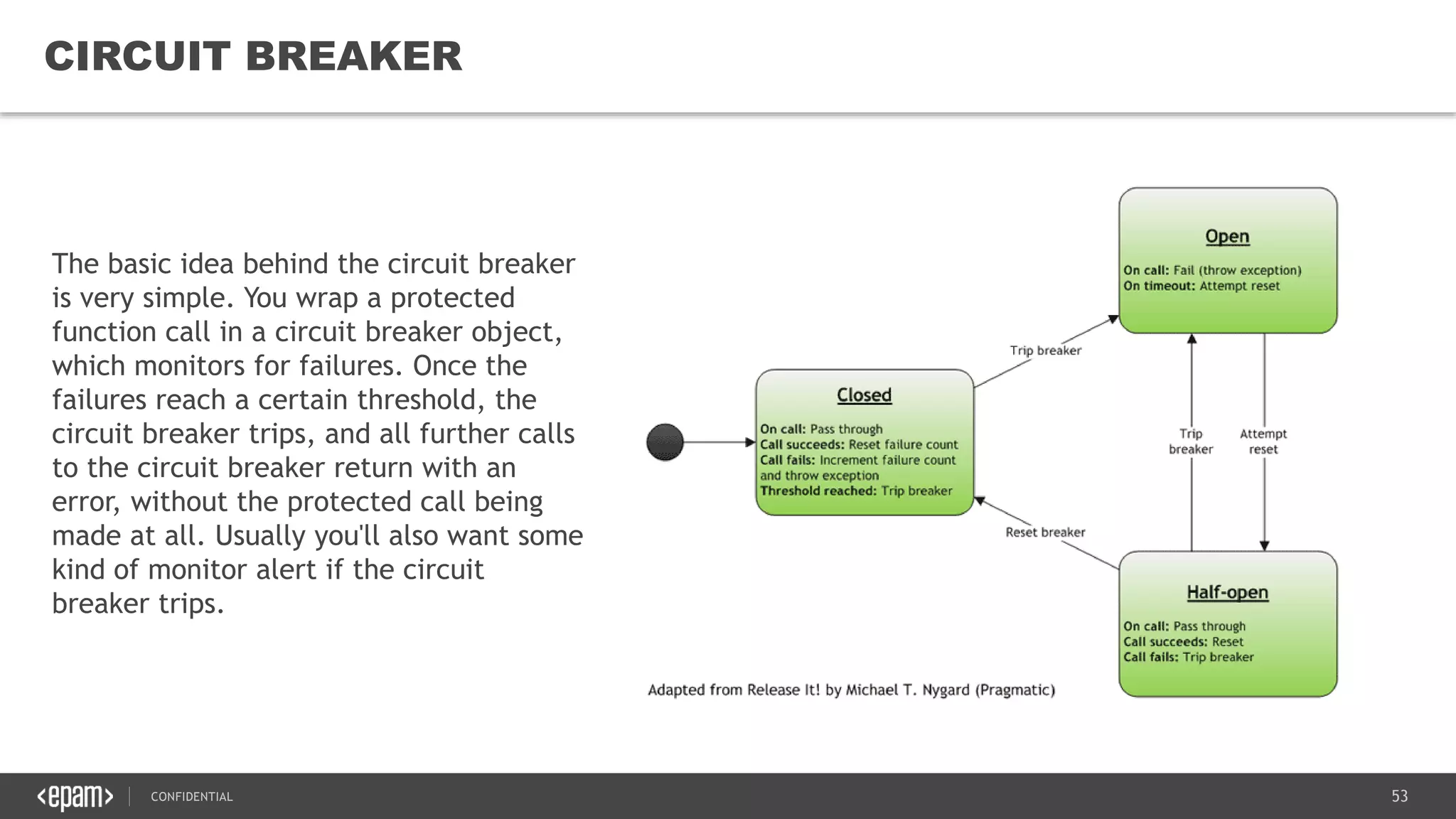
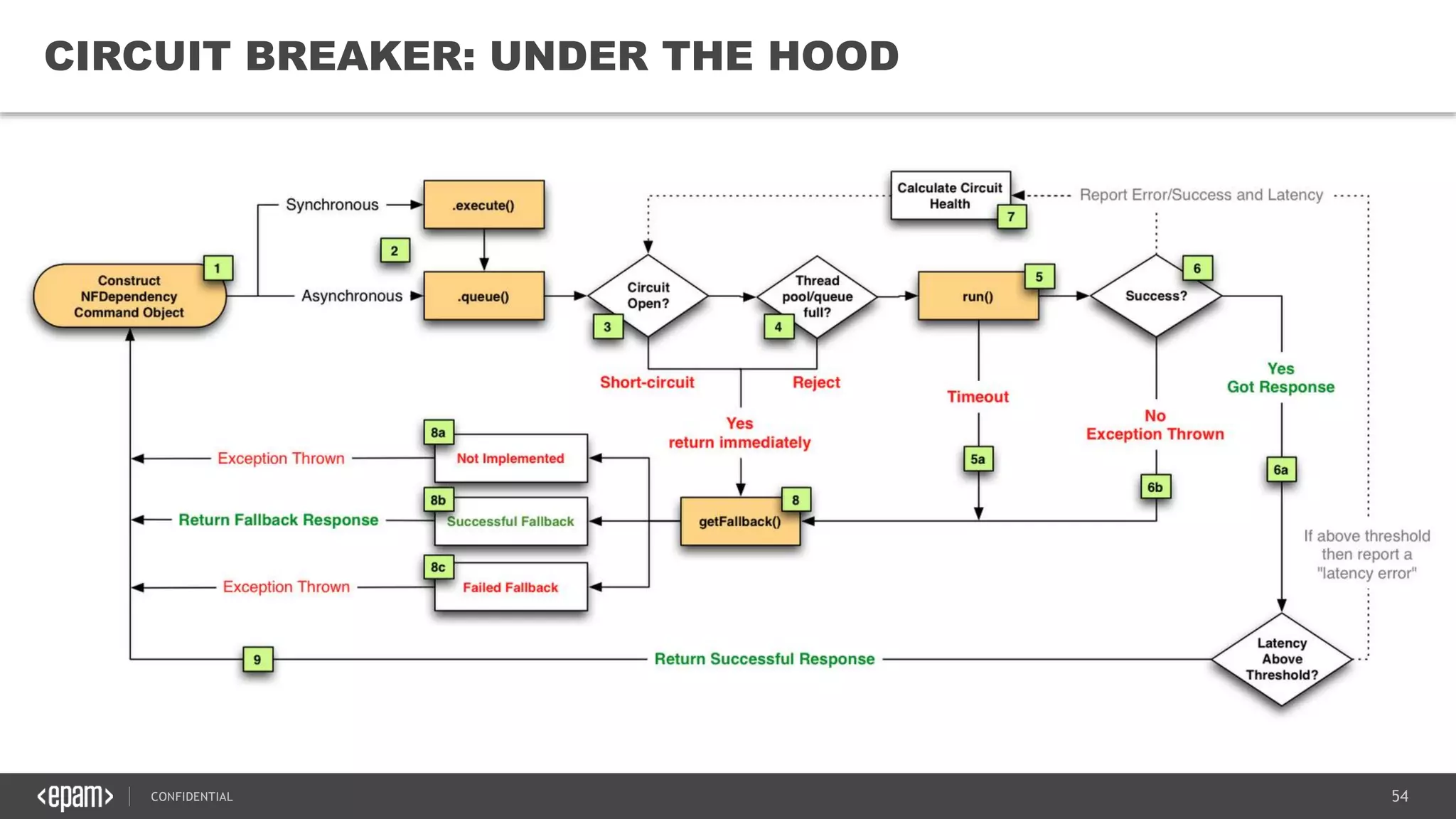
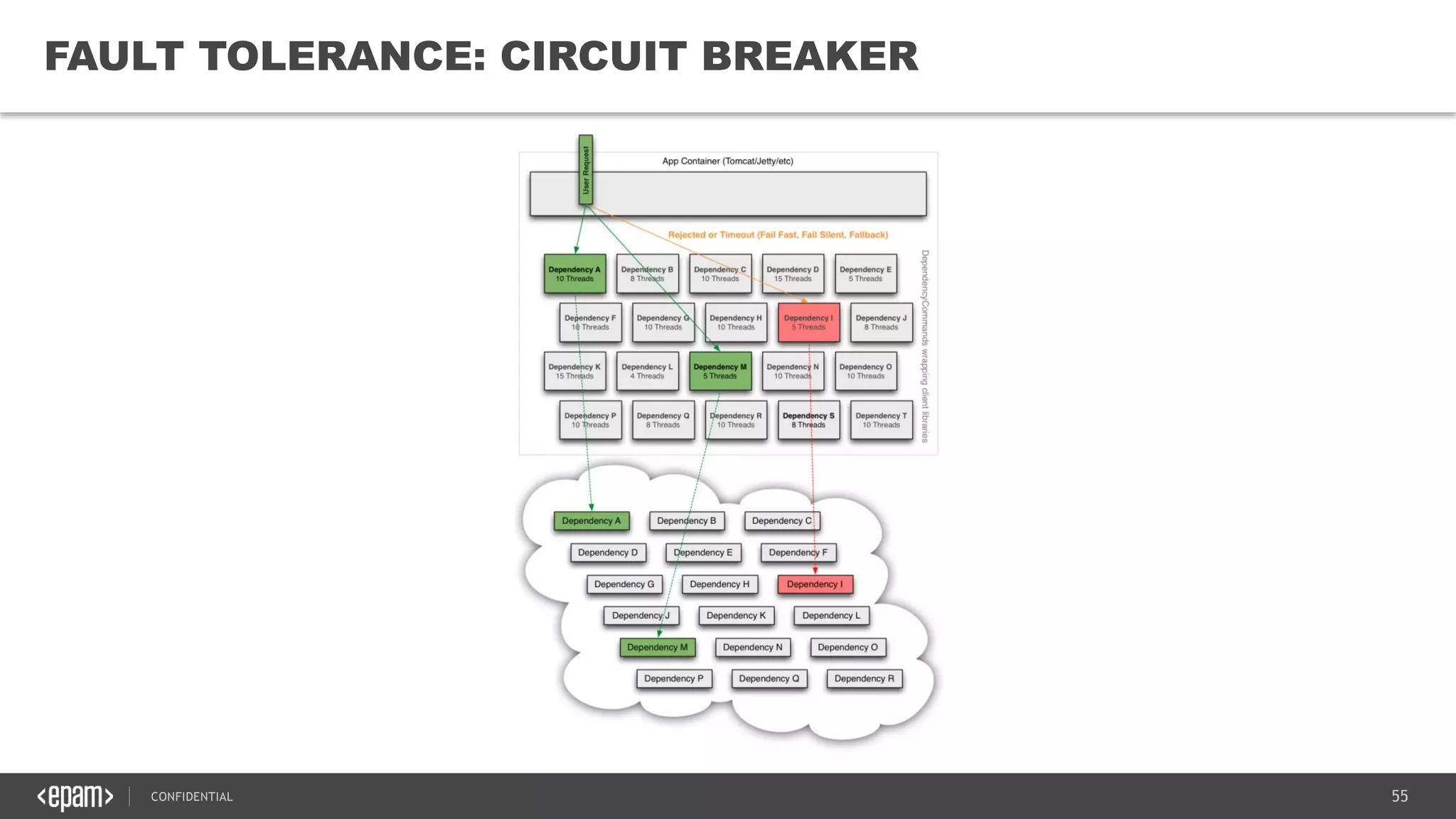
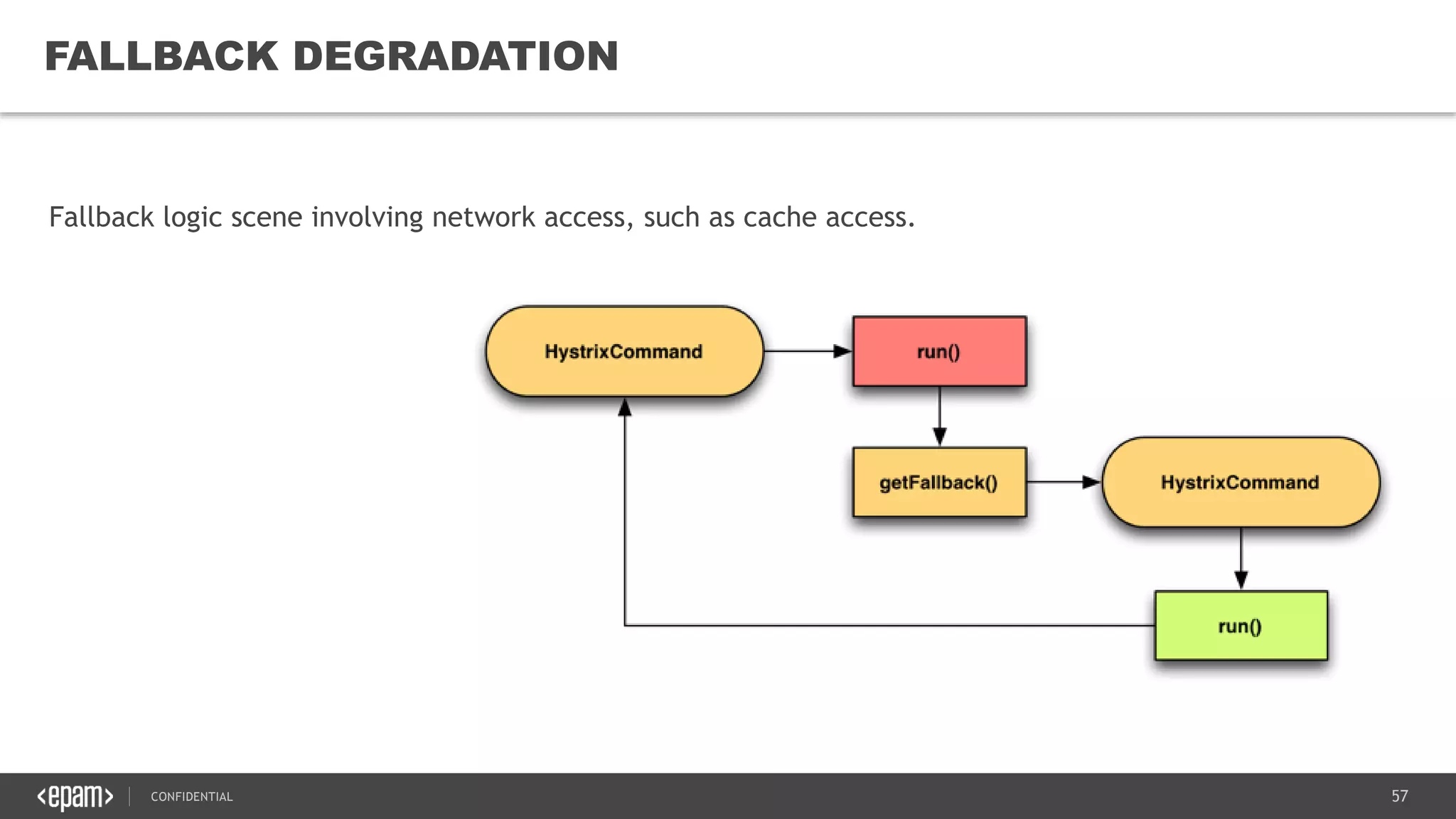
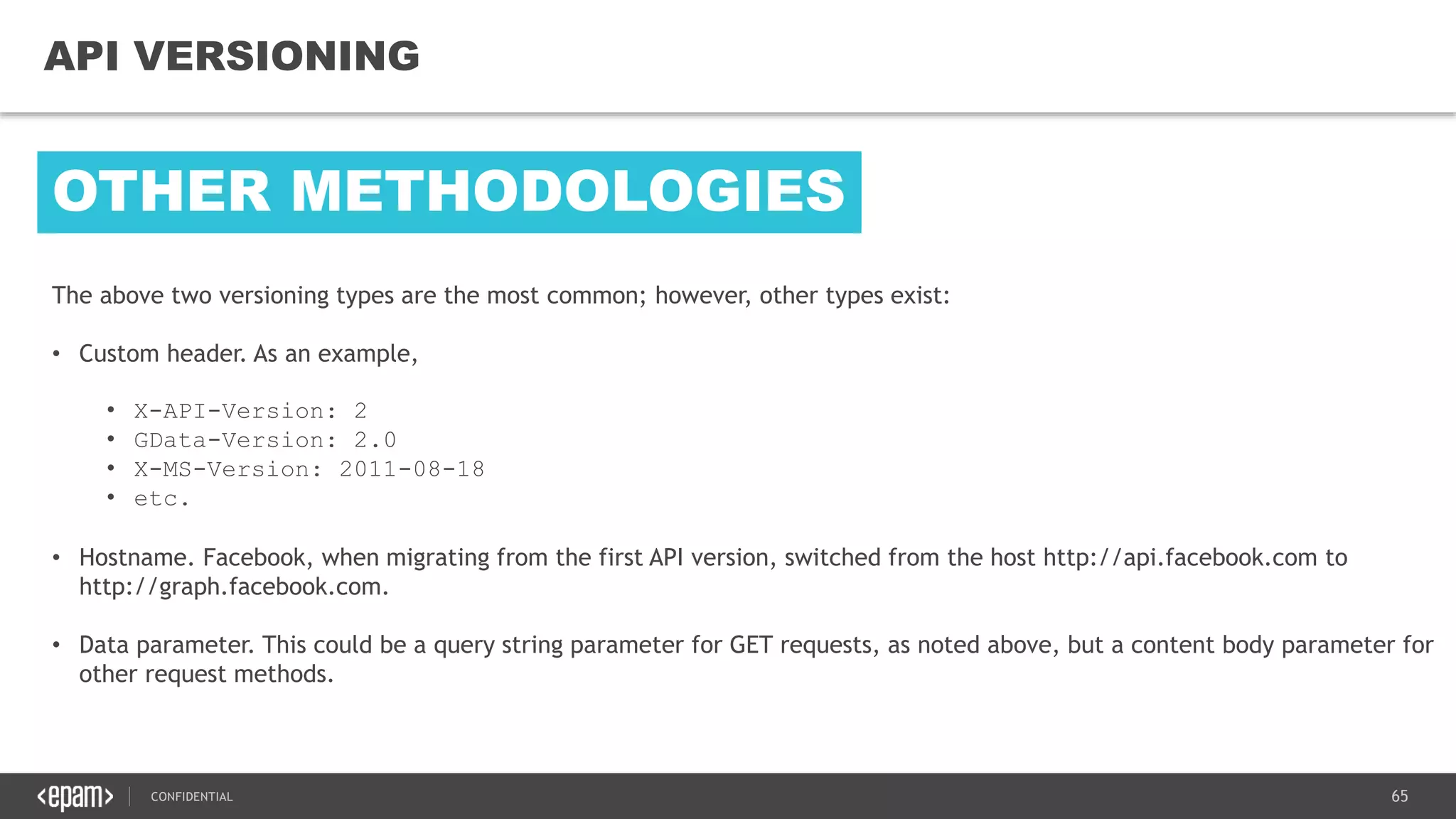
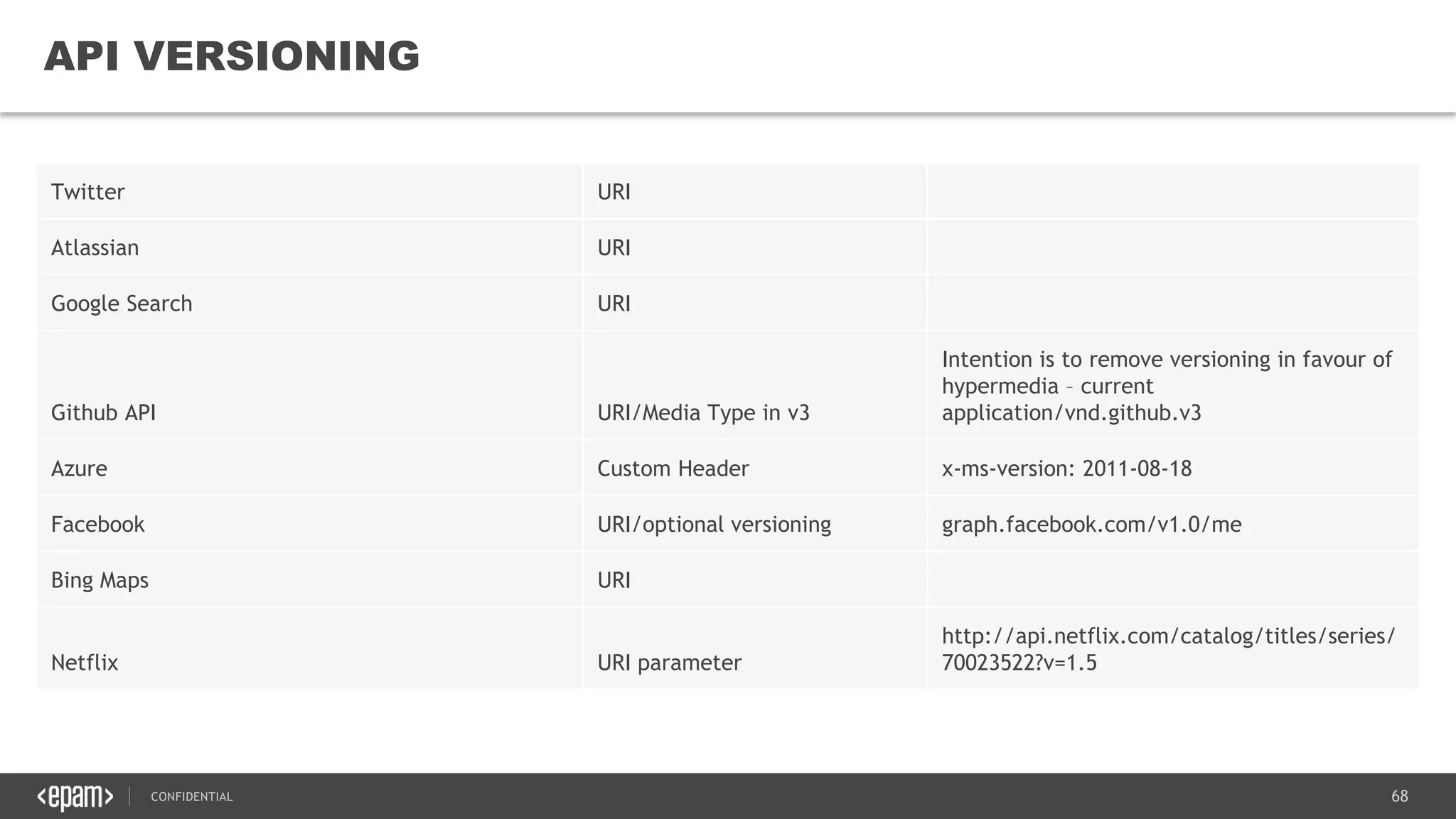
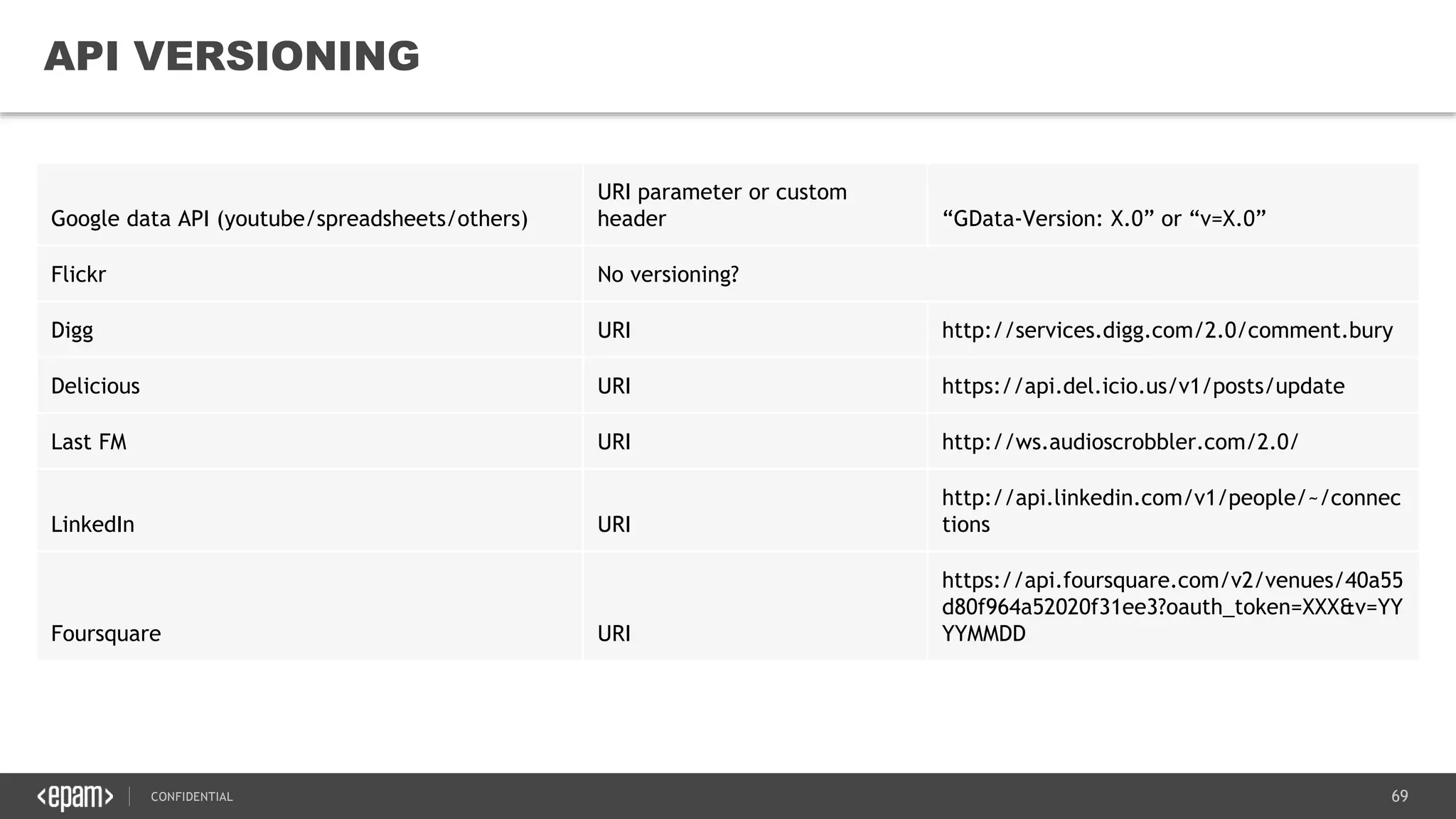
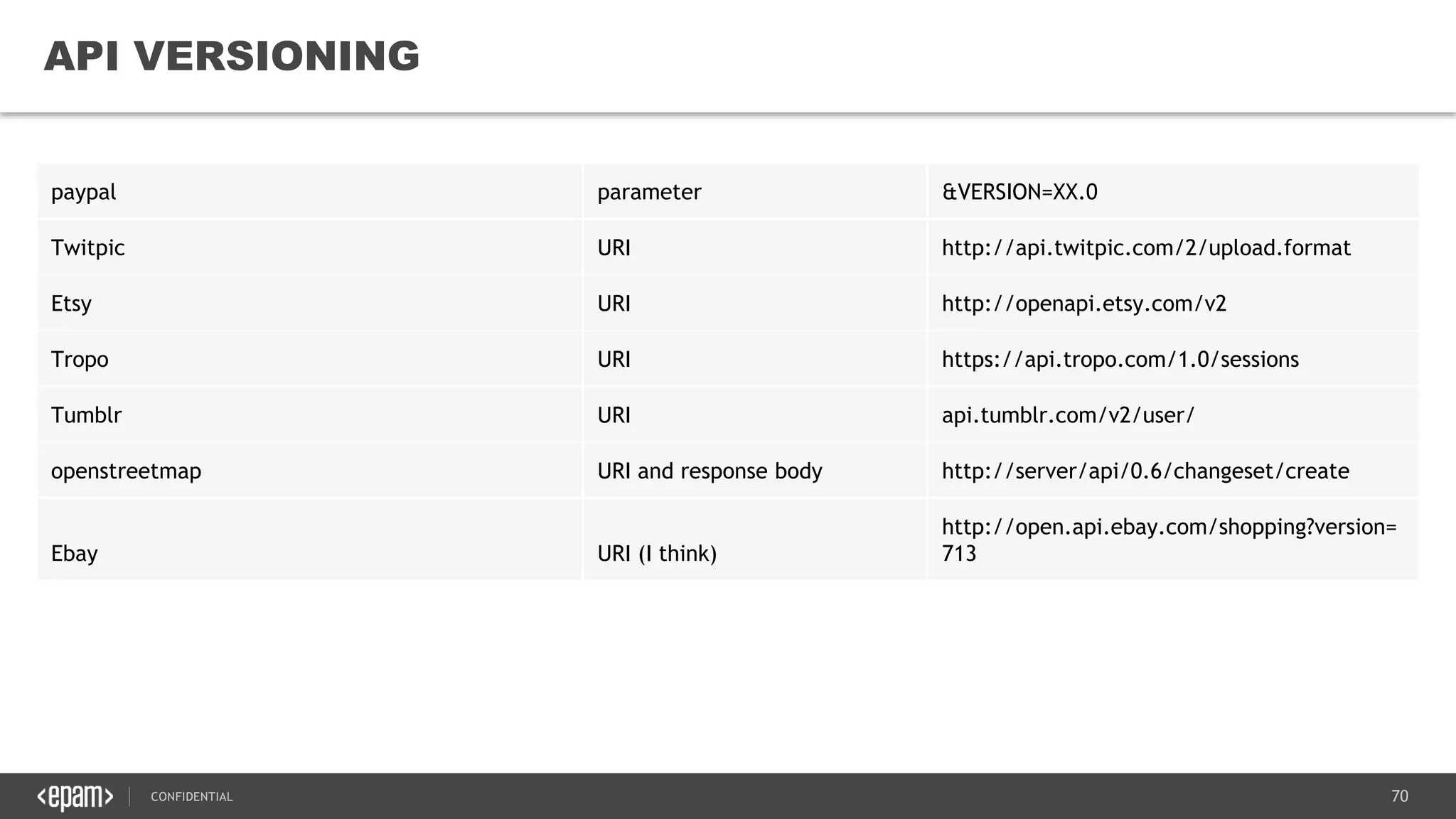
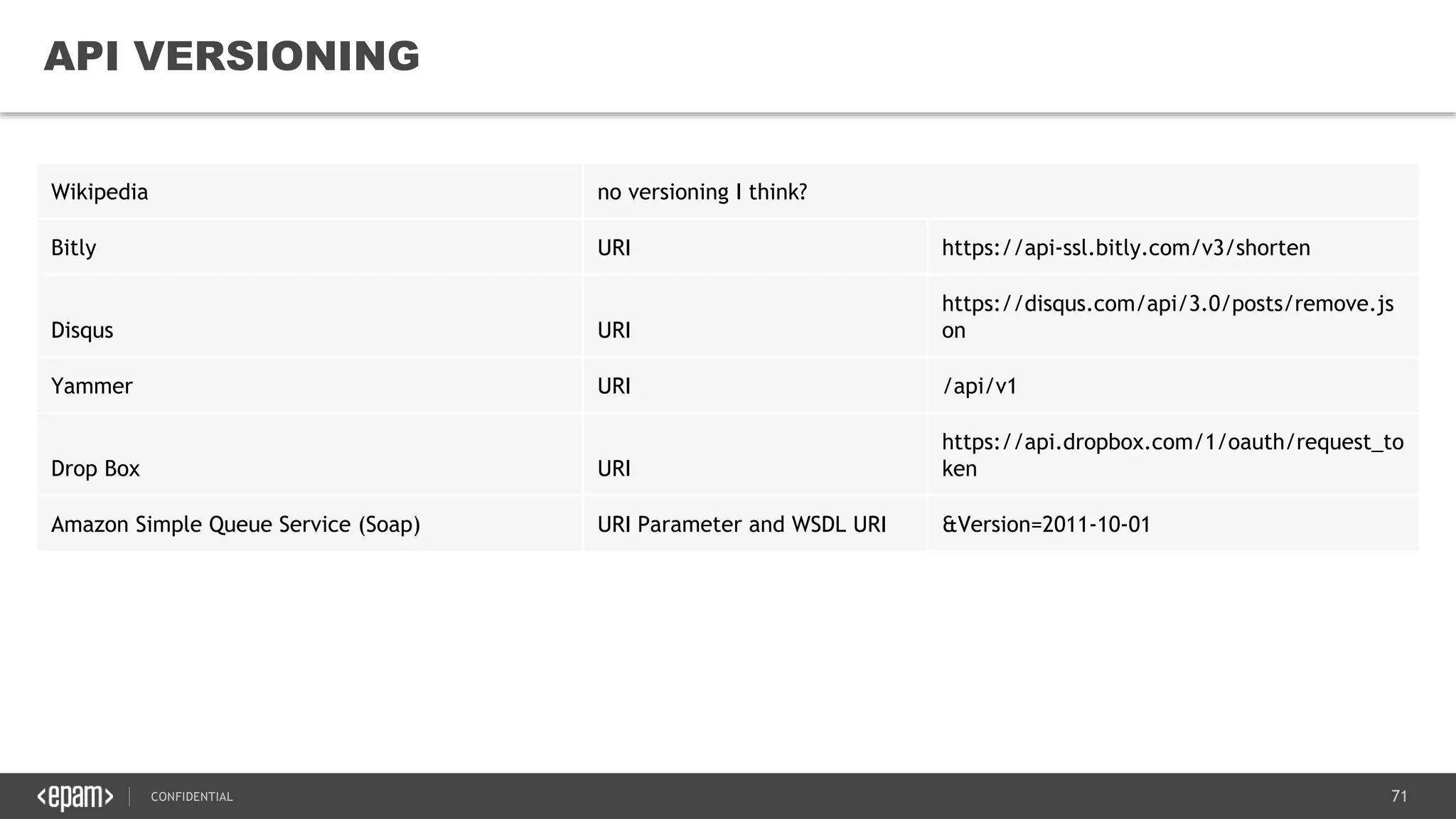
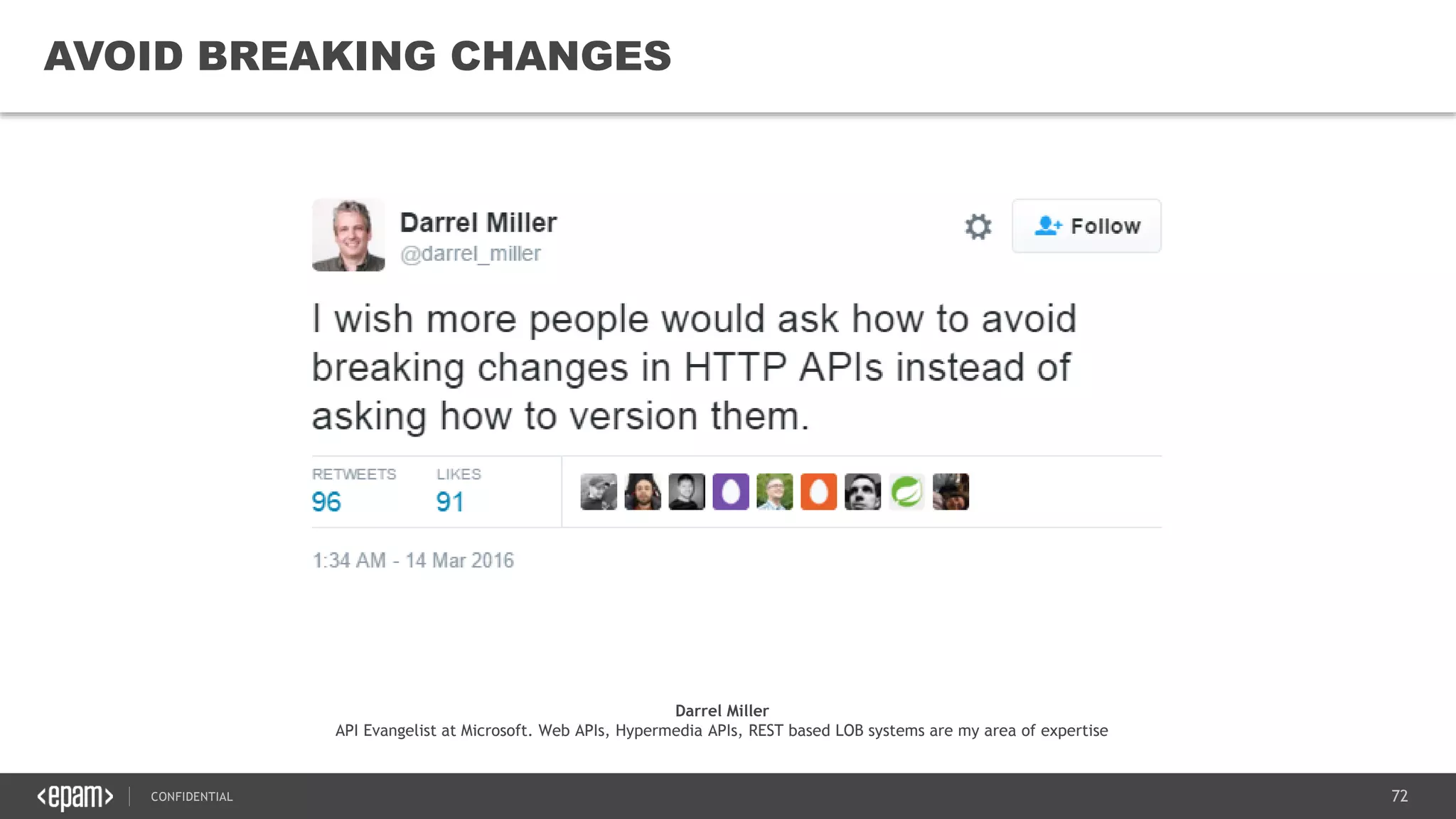
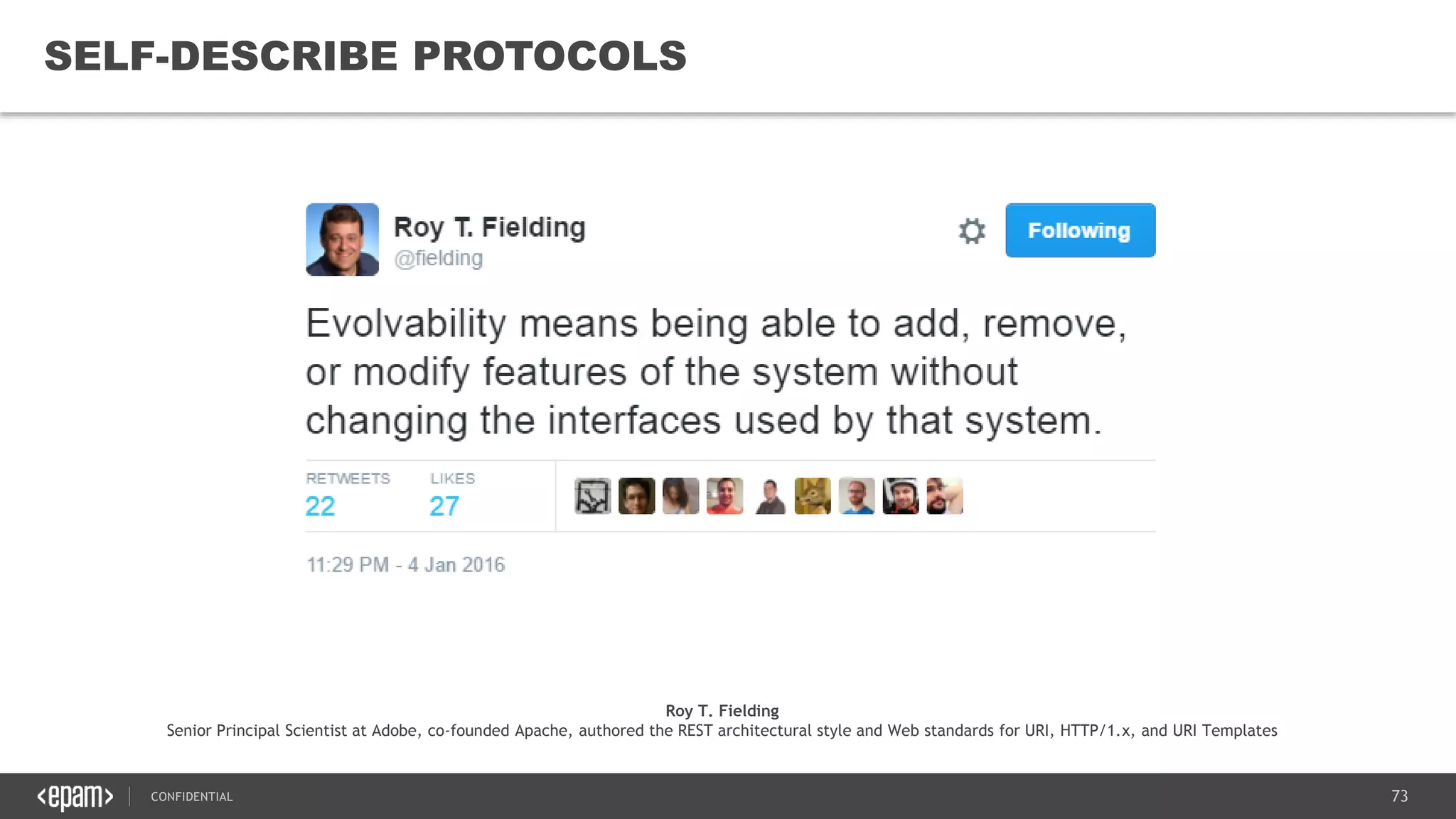
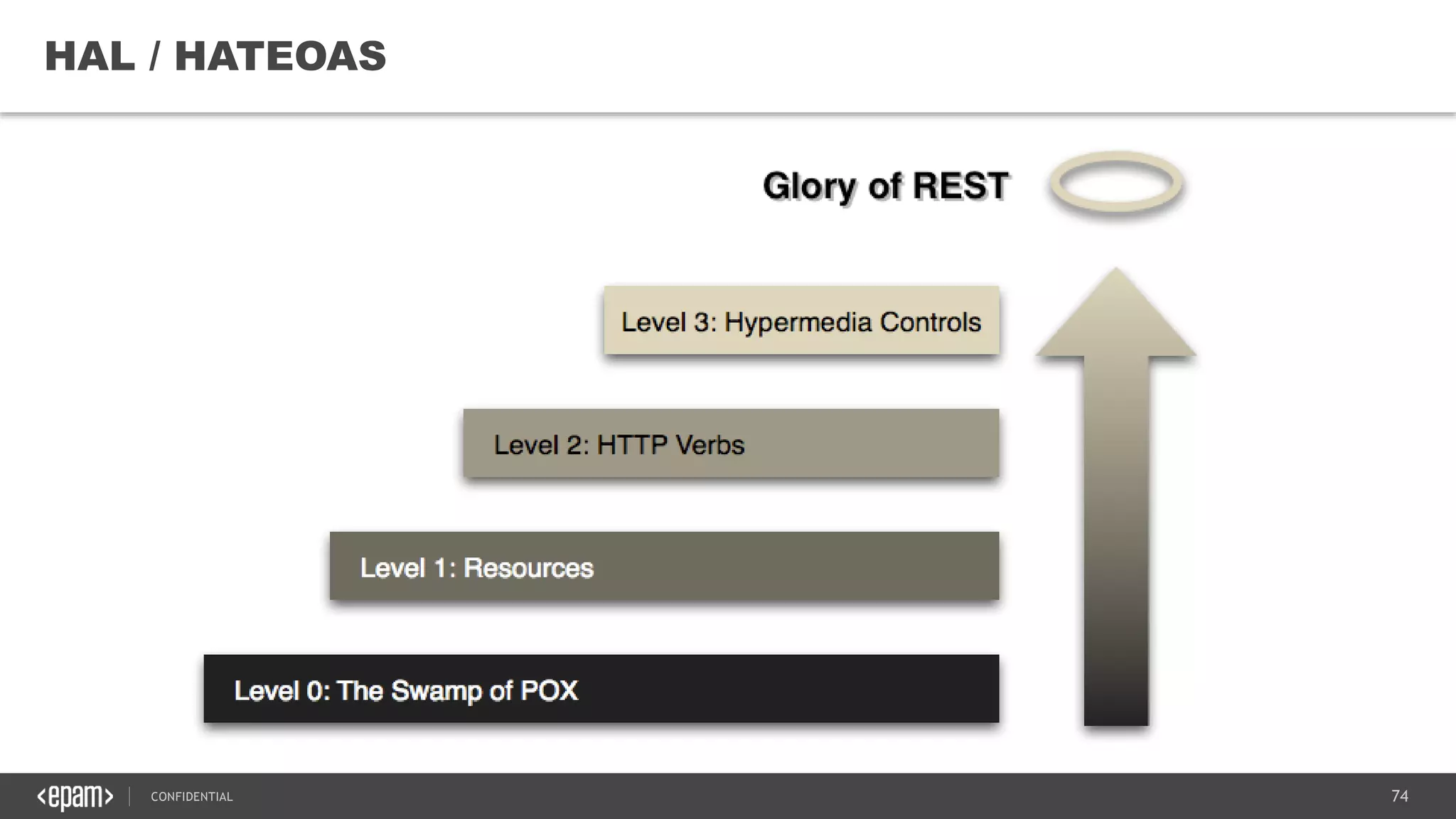
The document provides an overview of microservices architecture, highlighting its necessity due to the obsolescence of traditional linear architectures and the demand for agility. It outlines key principles and values of microservices, such as team independence, resilience, and technology agnosticism, as well as essential architecture patterns including API gateways and service discovery. Additionally, it discusses challenges like fault tolerance, request collapsing, and API versioning, underscoring the complexity of distributed systems.
























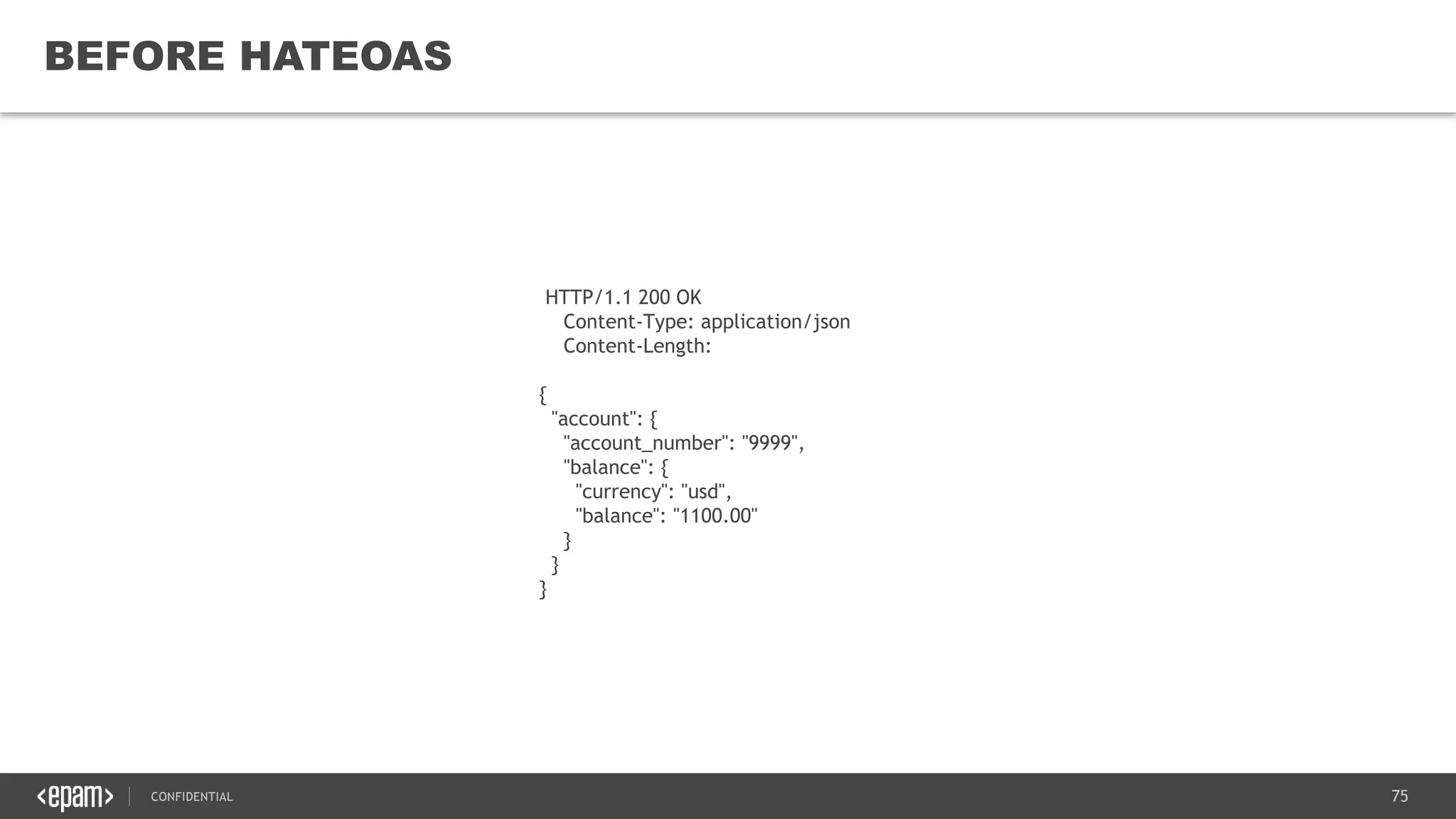
![76CONFIDENTIAL 76 AFTER HATEOAS HTTP/1.1 200 OK Content-Type: application/json Content-Length: { "account": { "account_number": "9999", "balance": { "currency": "usd", "balance": "1100.00" }, "links": [ { "rel": "deposit", "href": “/v1/account/9999/deposit" }, { "rel": "withdraw", "href": "/v2/account/9999/withdraw" }, { "rel": "transfer", "href": "/v1/account/9999/transfer" }, { "rel": "close", "href": "/v1/account/9999/close" } ] } }](https://image.slidesharecdn.com/microservicesarchitectureoverviewv3-160518155733/75/Microservices-architecture-overview-v3-72-2048.jpg)