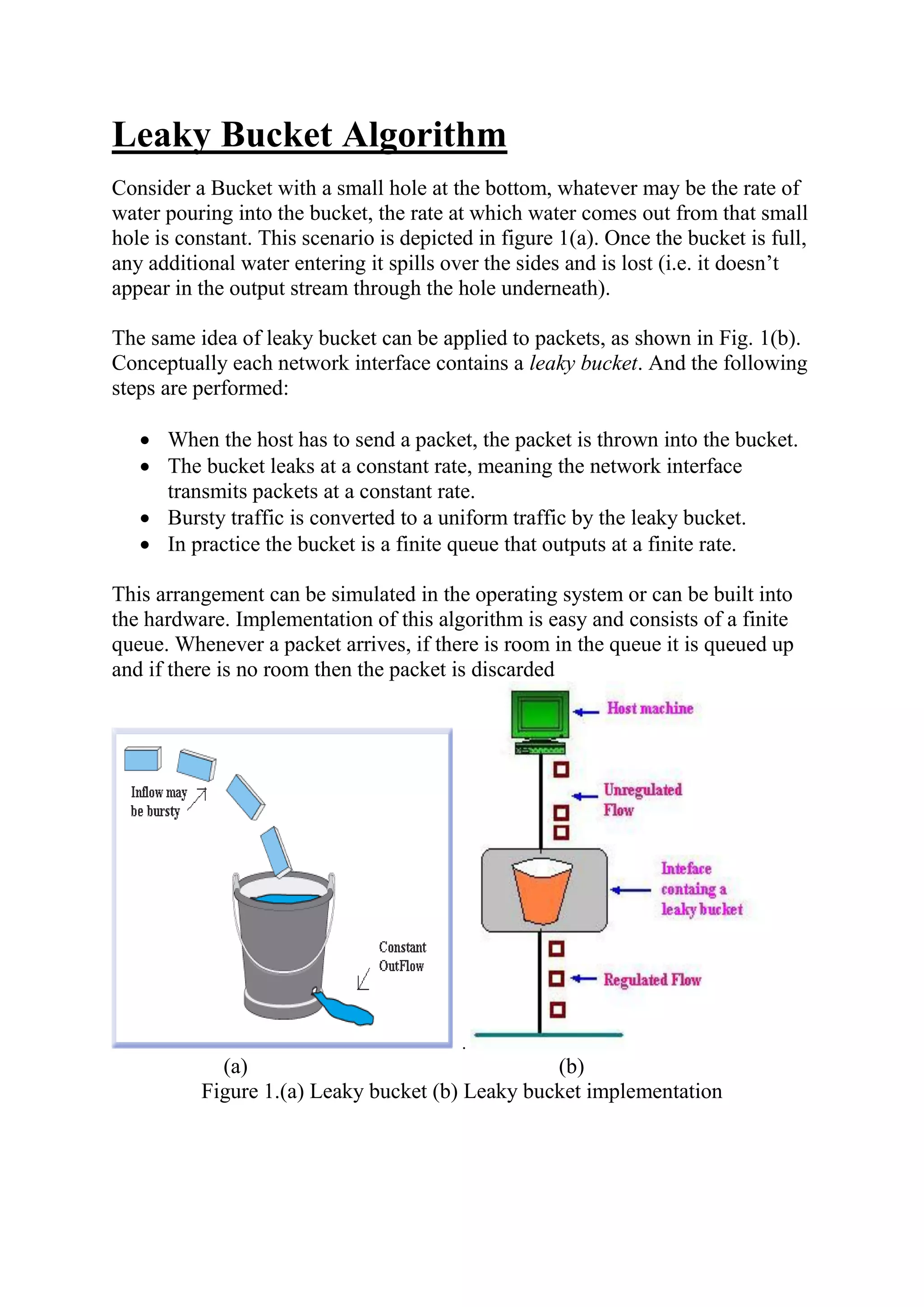
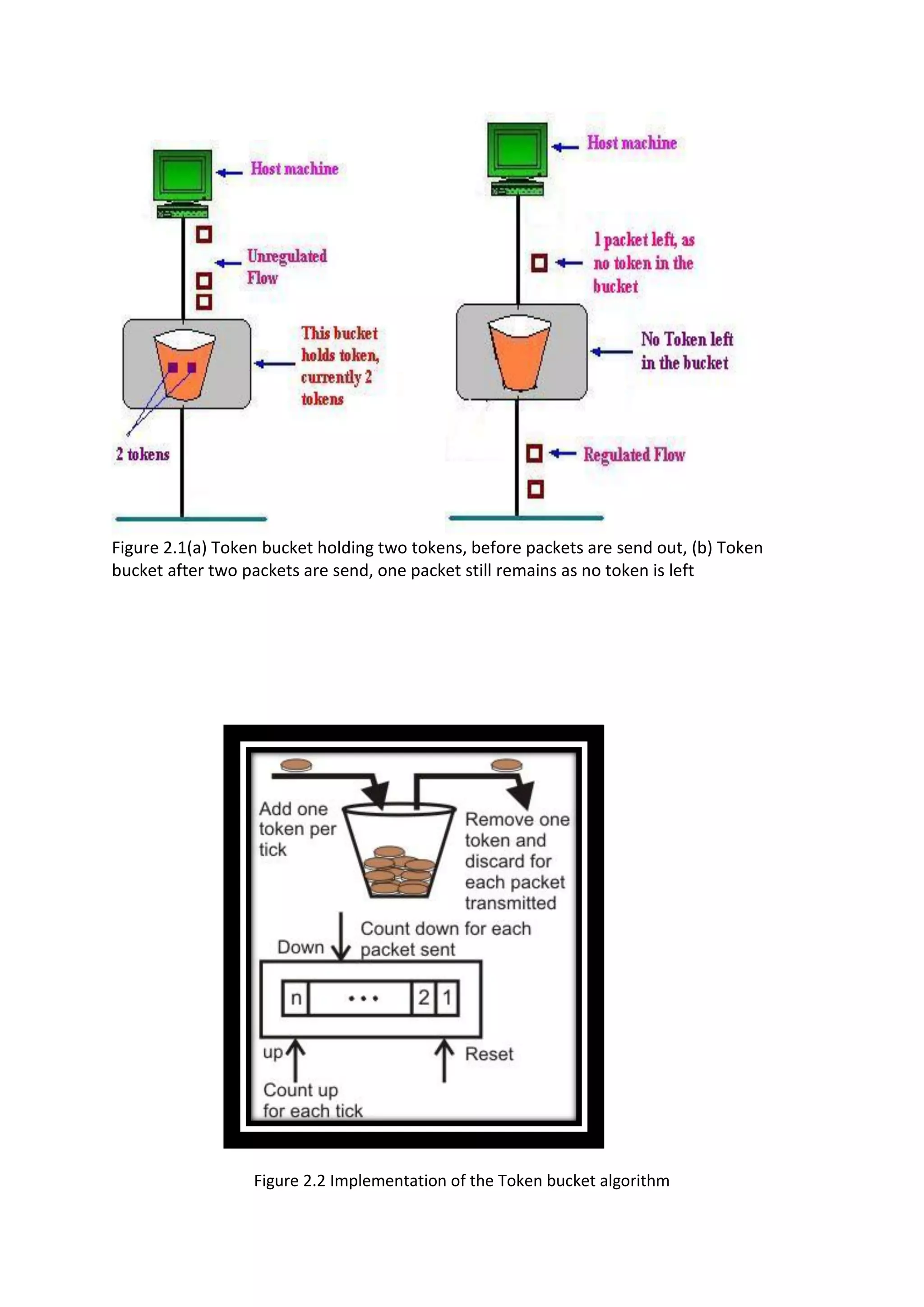
This document discusses two algorithms for regulating network traffic: 1) The Leaky Bucket Algorithm models traffic as water entering a bucket with a hole, limiting output to a constant rate regardless of input rate. Packets are discarded if the bucket is full. 2) The Token Bucket Algorithm generates tokens periodically and removes a token for each packet sent. This allows bursts proportional to the number of tokens, rather than rigidly limiting output. It is implemented with a counter that is incremented with new tokens and decremented when packets are sent.