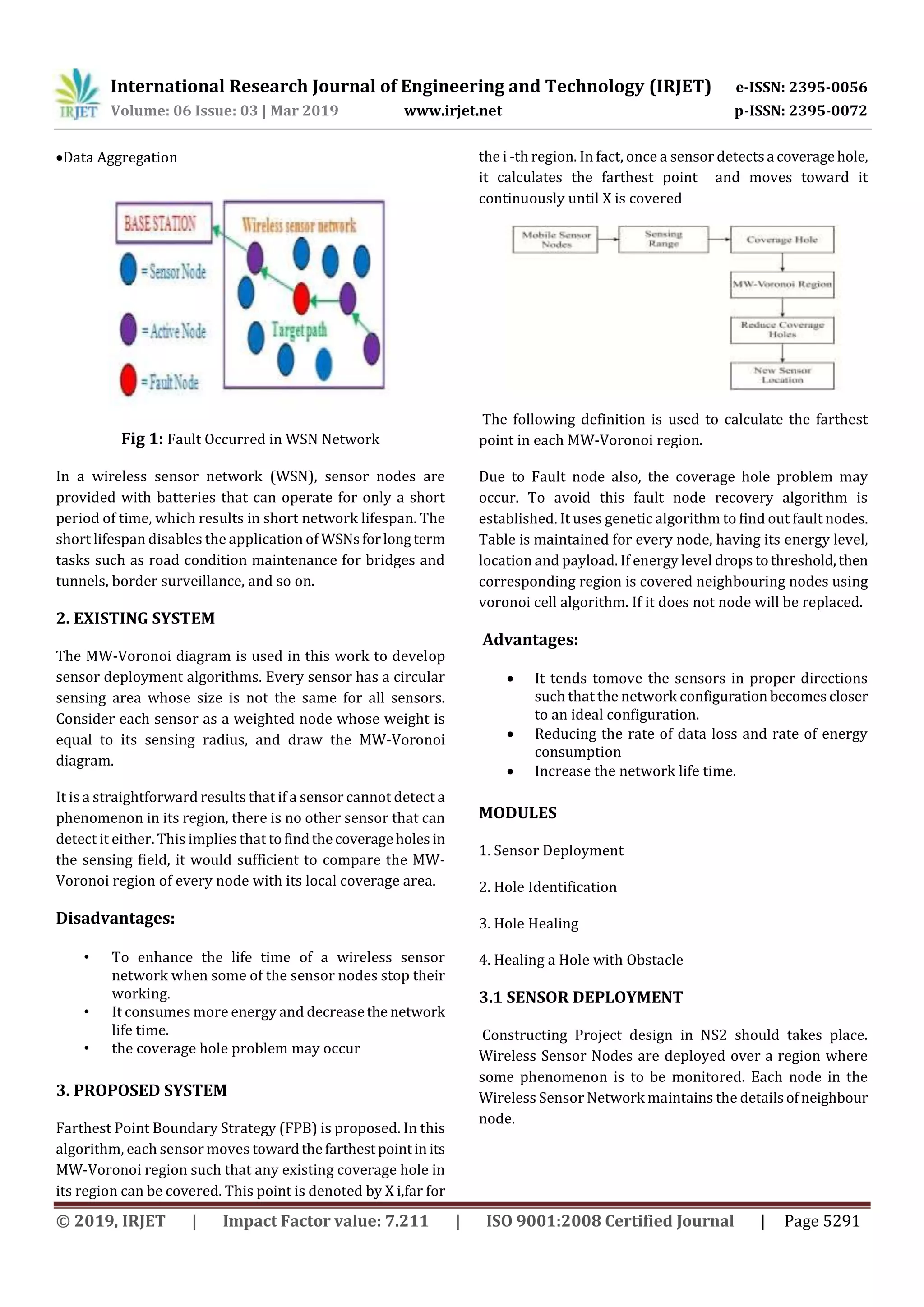
This document presents a fault node recovery algorithm for wireless sensor networks. It proposes combining the Grade Diffusion algorithm with a genetic algorithm to identify and replace faulty sensor nodes. The goal is to replace fewer sensor nodes while reusing existing routing paths, which increases the lifetime of the wireless sensor network and reduces replacement costs. It describes modules for sensor deployment, hole identification when sensors fail, hole healing by moving neighboring sensors, and healing holes when obstacles are present. The algorithm is implemented and evaluated using the Network Simulator NS2 tool. The results show the proposed algorithm increases the number of active sensor nodes and reduces the rate of energy consumption compared to other approaches.


![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 06 Issue: 03 | Mar 2019 www.irjet.net p-ISSN: 2395-0072 © 2019, IRJET | Impact Factor value: 7.211 | ISO 9001:2008 Certified Journal | Page 5293 allow combined simulation of wired and wireless networks. MobileIP was also extended to the wireless model. 7. CONCLUSIONS Efficient sensor coordination algorithms are developed in this work to increase sensing coverage in a network of mobile sensors with non-identical sensing ranges. The sensing field is first partitioned using the multiplicatively weighted Voronoi (MW-Voronoi) diagram, and three distributed deployment algorithms are subsequently developed. Under the proposed algorithms, the sensors move iteratively in such a way that coverage holes are reduced in size. The algorithms tend to move the sensors in proper directions such that the network configuration (in terms of the distance of sensors from the vertices of the MW-Voronoi regions) becomes closer to an ideal configuration. To avoid complex non-convex optimization problems, novel geometric methods are used to findthenewsensorlocations in the MW-Voronoi regions. The proposed algorithms are compared with other techniques with different number of sensors. Our system proposes a faulty node recovery and replacement algorithm for WSN basedonthegradediffusion algorithm combined with genetic algorithm. The FNR algorithm requires replacing fewer sensor nodesandreuses the most routing paths, increasing the WSN lifetime and reducing the replacement cost. In the simulation, the proposed algorithm increases the number of active nodes reduces the rate of energy consumption. REFERENCES [1] Z. Zou, Y. Bao, H. Li, B. F. Spencer, and J.Ou, “Embedding compressive sensing-based data lossrecoveryalgorithminto wireless smart sensors for structural health monitoring,” IEEE Sensors Journal, vol. 15, no. 2, pp. 797–808, 2015. [2] X. Wang, S. Han, Y. Wu, and X. Wang, “Coverage and energy consump- tion control in mobile heterogeneous wireless sensor networks,” IEEE Transactions on Automatic Control, vol. 58, no. 4, pp. 975–988, 2013. [3] S. Zhu and Z. Ding, “Distributed cooperative localization of wireless sensor networks with convex hull constraint,” IEEE Transactions on Wireless Communications, vol. 10, no. 7, pp. 2150–2161, 2011. [4] M. Pourali and A. Mosleh, “Afunctional sensorplacement optimization method for power systems healthmonitoring,” IEEE Transactions on Industry Applications, vol. 49, no. 4, pp. 1711–1719, 2013. [5] T. Shu, M. Krunz, and S. Liu, “Secure data collection in wireless sensor networks using randomized dispersive routes,” IEEE Trans. Mobile Comput., vol. 9, no. 7, pp. 941- 954, Jul. 2010. [6] M. Kurt and S. Peter, Algorithms andData Structures:The Basic Toolbox. Springer, 2008. pp. 198-199 [6] G. Zhan, W. Shi, and J. Deng, “Design and implementation of TARF: A trust-aware routing framework for WSNs,” IEEE Trans. Dependable Secure Comput.,vol.9,no.2, pp.184-197, Mar./Apr. 2012. [7] A. Ahmed, K. A. Bakar, M. I. Channa, K. Haseeb, and A. W. Khan, “TERP: A Trust andEnergyAwareRoutingProtocol for Wireless Sensor Network,” IEEE Sensors J. vol. 15,no.12, pp. 6962-6972, Dec. 2015. [8] Y. Liu, M. Dong, K. Ota, and A. Liu, “ActiveTrust: Secure and Trustable Routing in Wireless Sensor Networks,” IEEE Trans. Inf. Forensics Security., vol. 11, no. 9, pp. 2013-2027, Sep. 2016. [9] X. Chen, J.-H Cho, and S. Zhu, “GlobalTrust: An Attack- Resilient Reputation System for Tactical Networks,” in Proc. IEEE SECON 2014. Singapore, 2014, pp. 275-283. [10] T. Shu, M. Krunz, and S. Liu, “Secure data collection in wireless sensor networks using randomized dispersive routes,” IEEE Trans. Mobile Comput., vol. 9, no. 7, pp. 941- 954, Jul. 2010. [11] S. Li, L. D. Xu, and S. Zhao, “The Internet of Things: A survey,” Inf. Syst. Frontiers, vol. 17, no. 2, pp. 243-259, Apr. 2015. [12] J.-H. Cho, A. Swami, and I.-R Chen, “A Survey on Trust Management for Mobile Ad Hoc Networks,” IEEE Commun. Surv](https://image.slidesharecdn.com/irjet-v6i31359-191023094456/75/IRJET-Coverage-Hole-Avoidance-using-Fault-Node-Recovery-in-Mobile-Sensor-Network-4-2048.jpg)