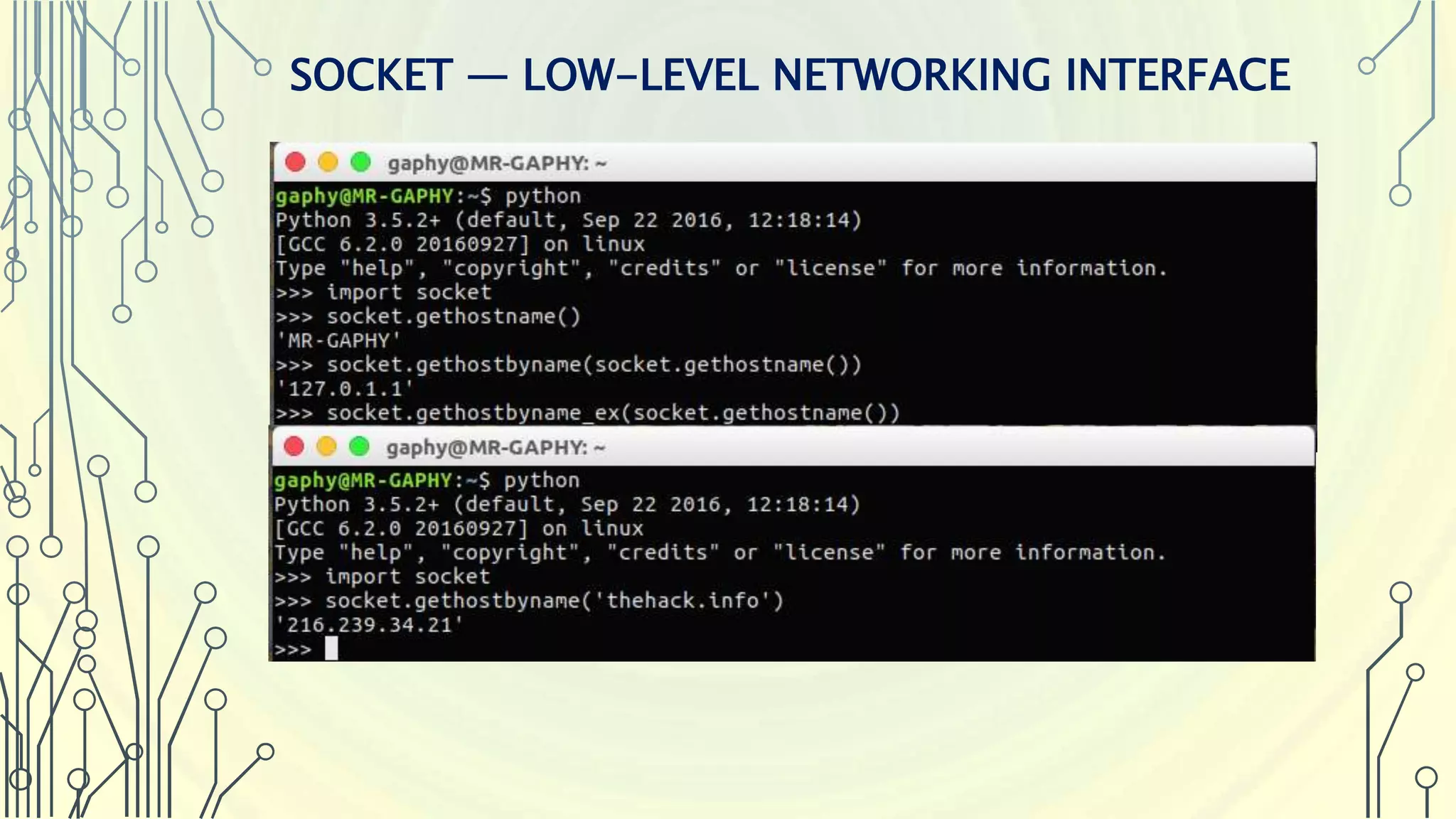
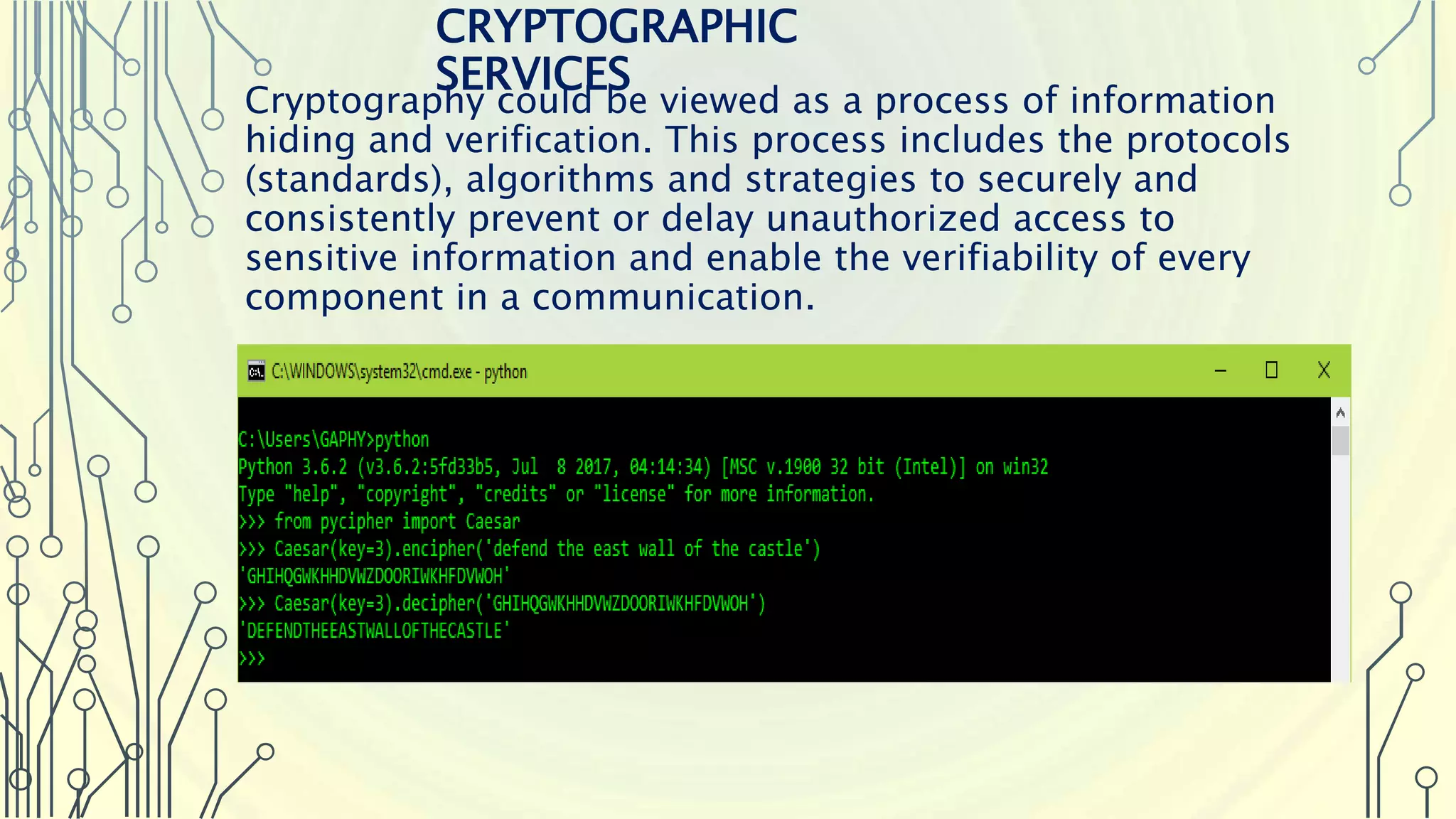
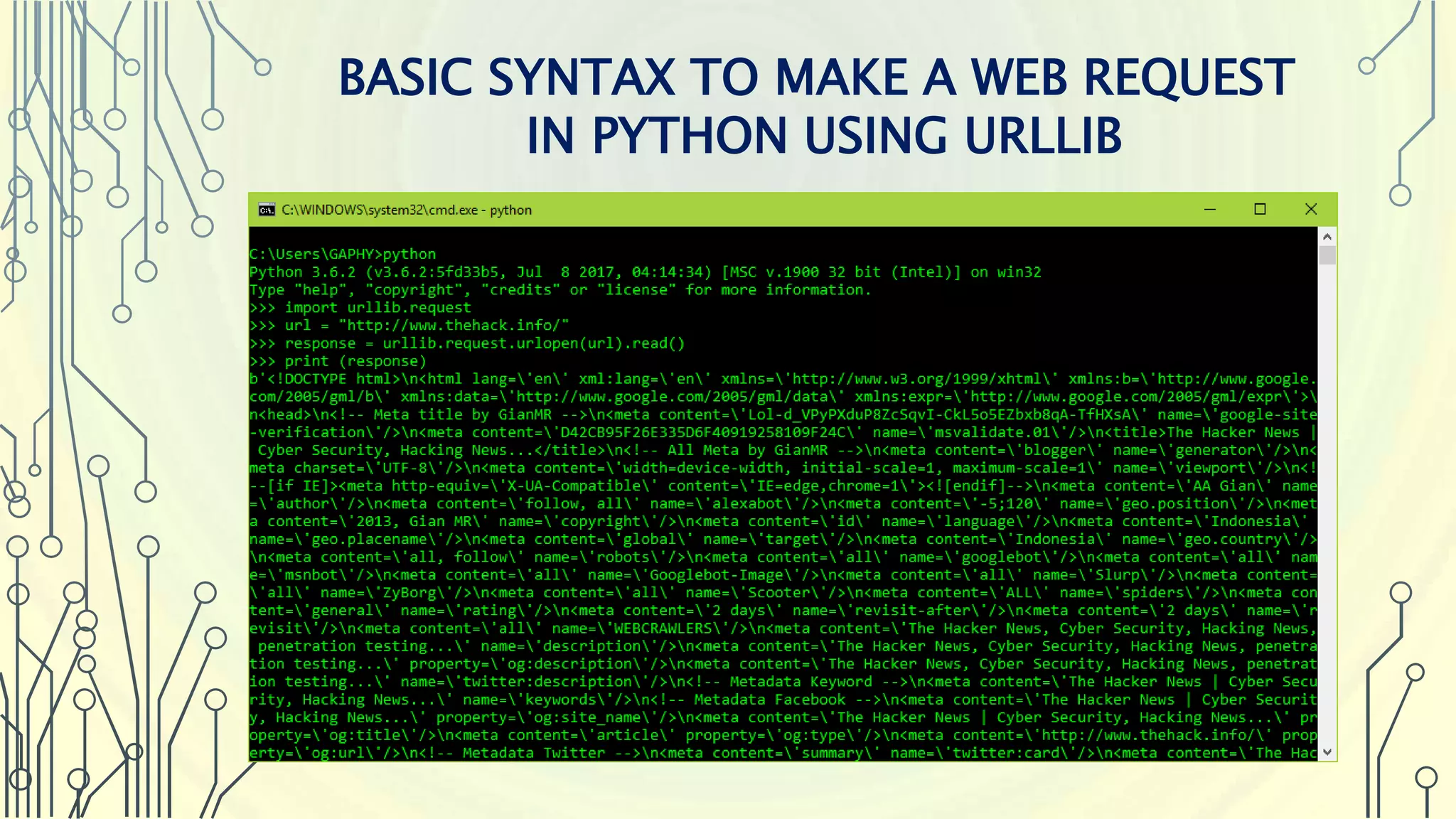
The document introduces Python as a programming language for cybersecurity, emphasizing its role in enhancing agility and performance for security professionals. It outlines key features of Python, such as its simplicity, extensive libraries for penetration testing, and automation capabilities. Additionally, it highlights the importance of Python modules and provides examples of libraries used in web application assessments and various cybersecurity tools.



![DATA TYPES Strings - “Hello” Numbers - 123 Lists – [‘hello’,’2’,’1’] Tuples - (‘1’,’2’,’3’) (immutable) Dictionaries – d = {‘key1’:’dog’,’key2’:’cat’} PYTHON 101 Python is a brilliant language. It is known to be a lazy programming l Used to write small lines of codes that does many tasks. This is a simple print line statement >>> print(“Welcome, Pentesters” @mrgaphy @abdulgaphy](https://image.slidesharecdn.com/introductiontopythonforcybersecurity-pythonminna-180604022648/75/Introduction-to-python-for-cybersecurity-pythonminna-6-2048.jpg)