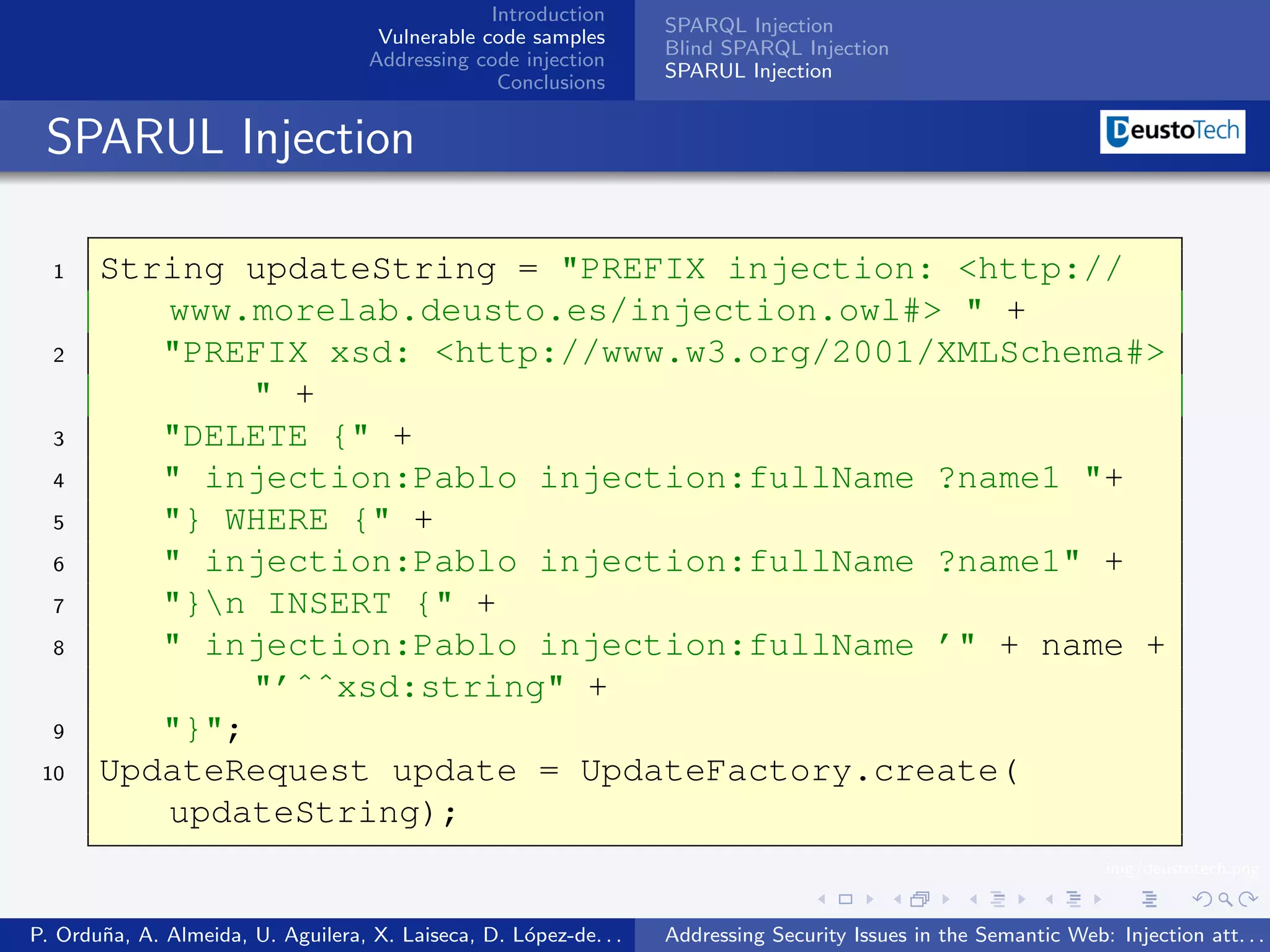
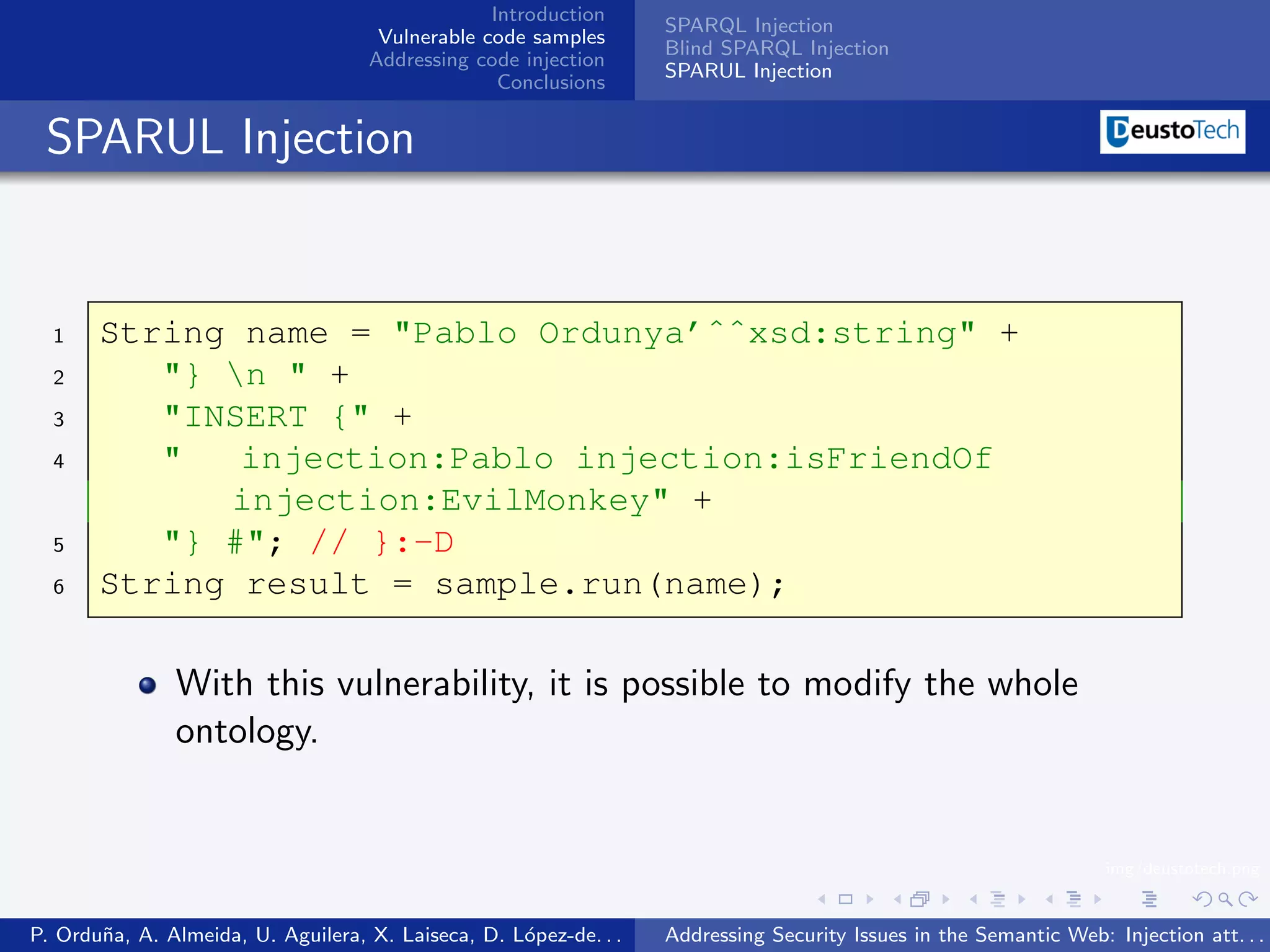
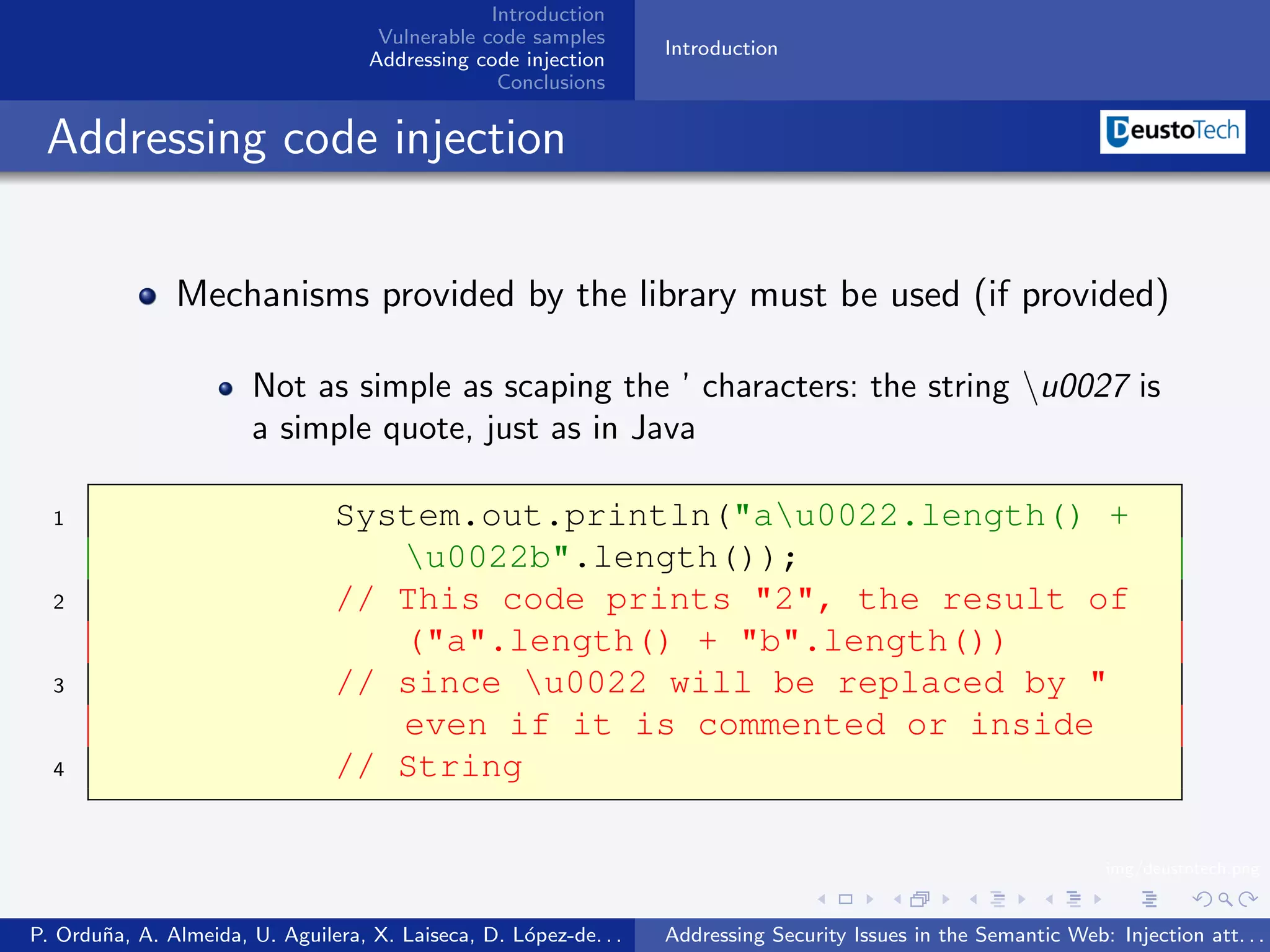
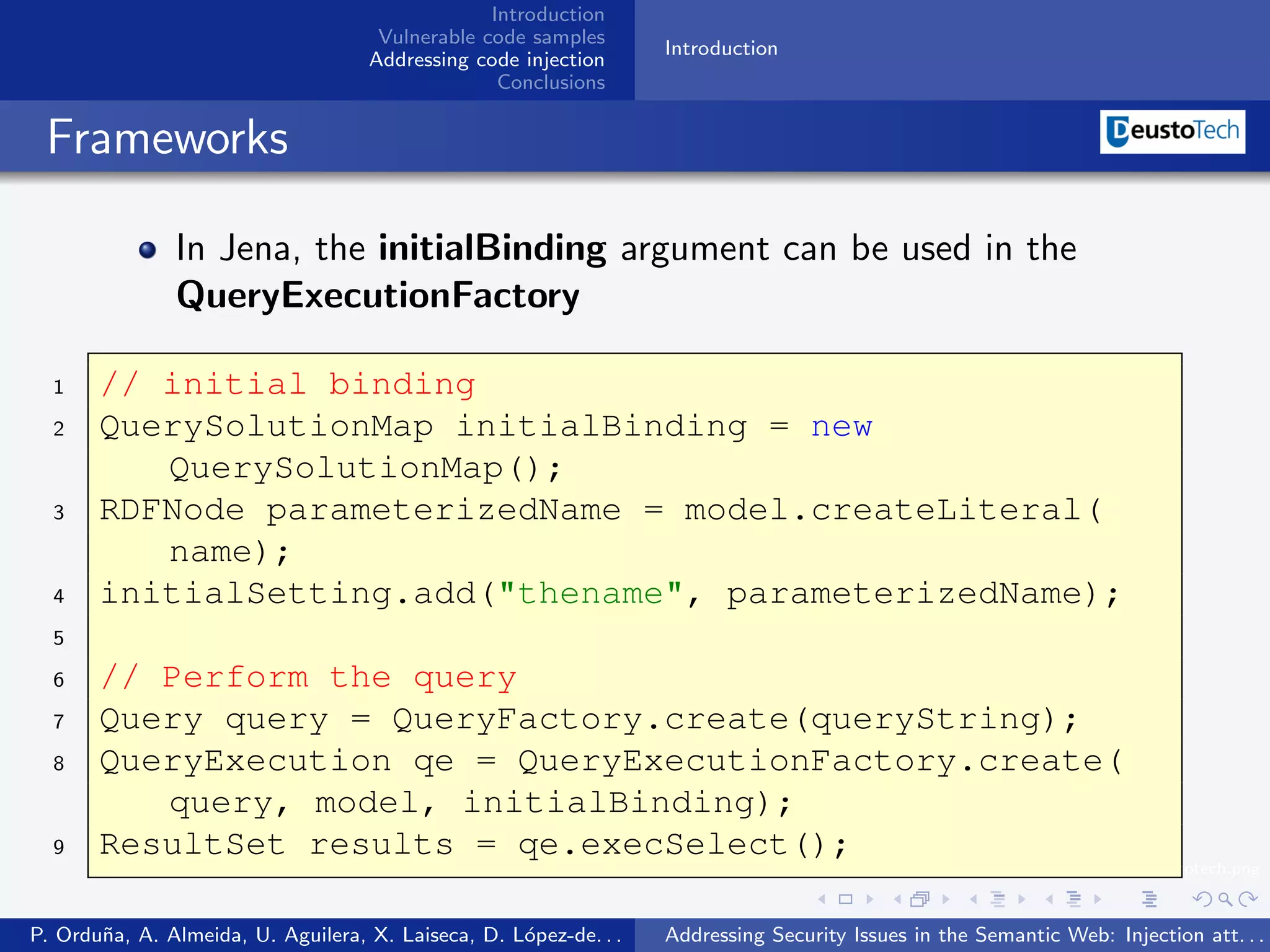
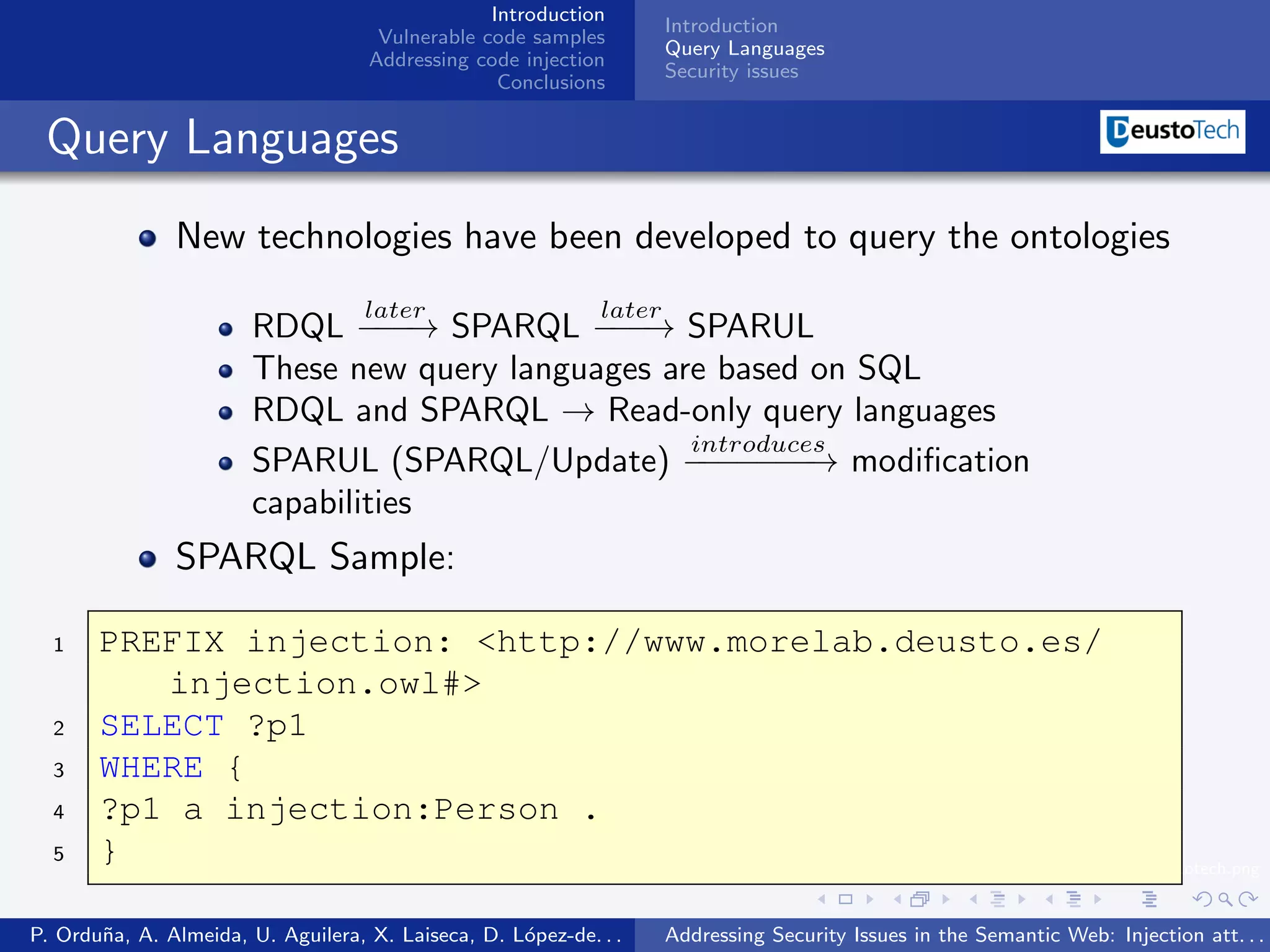
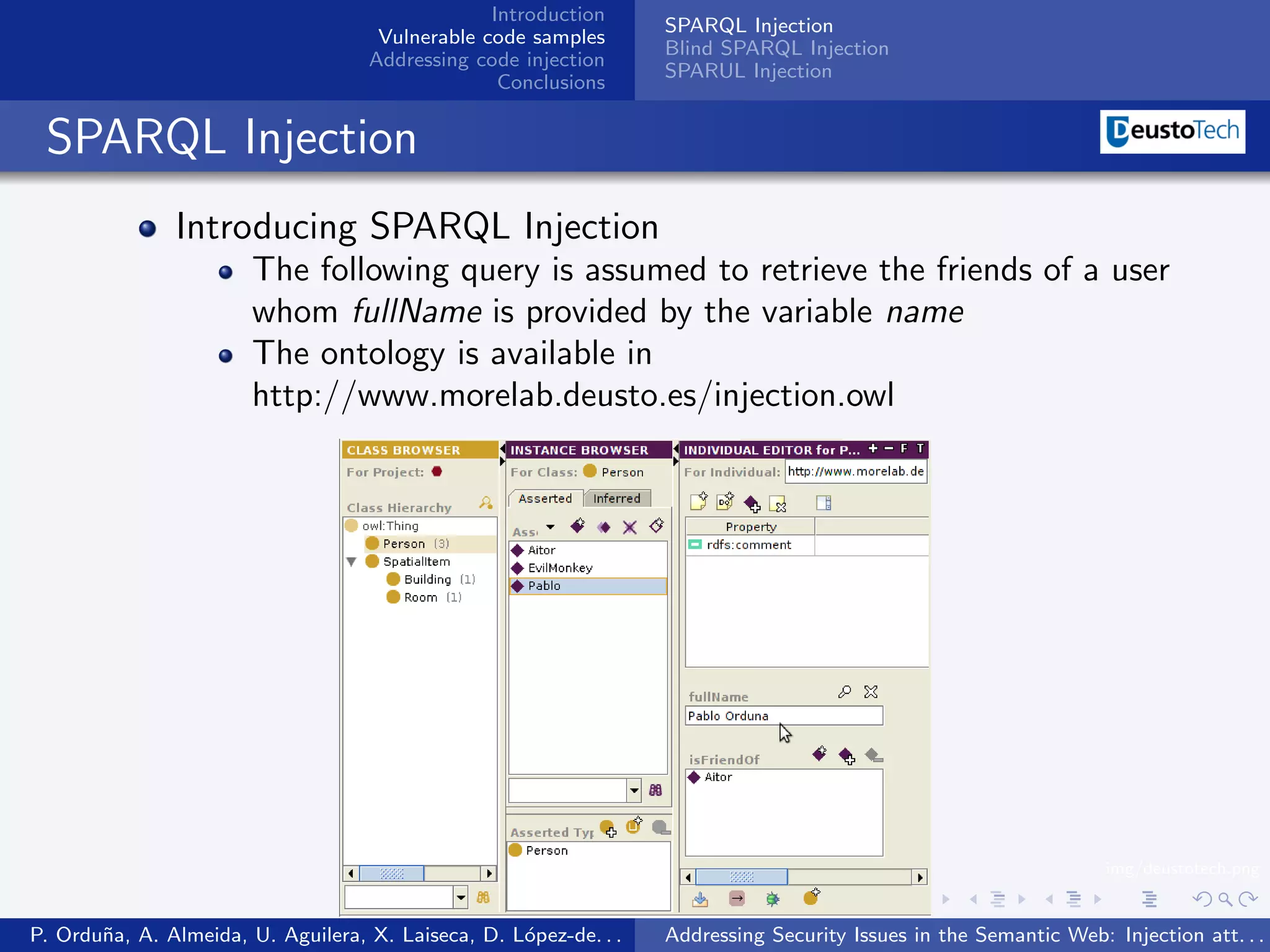
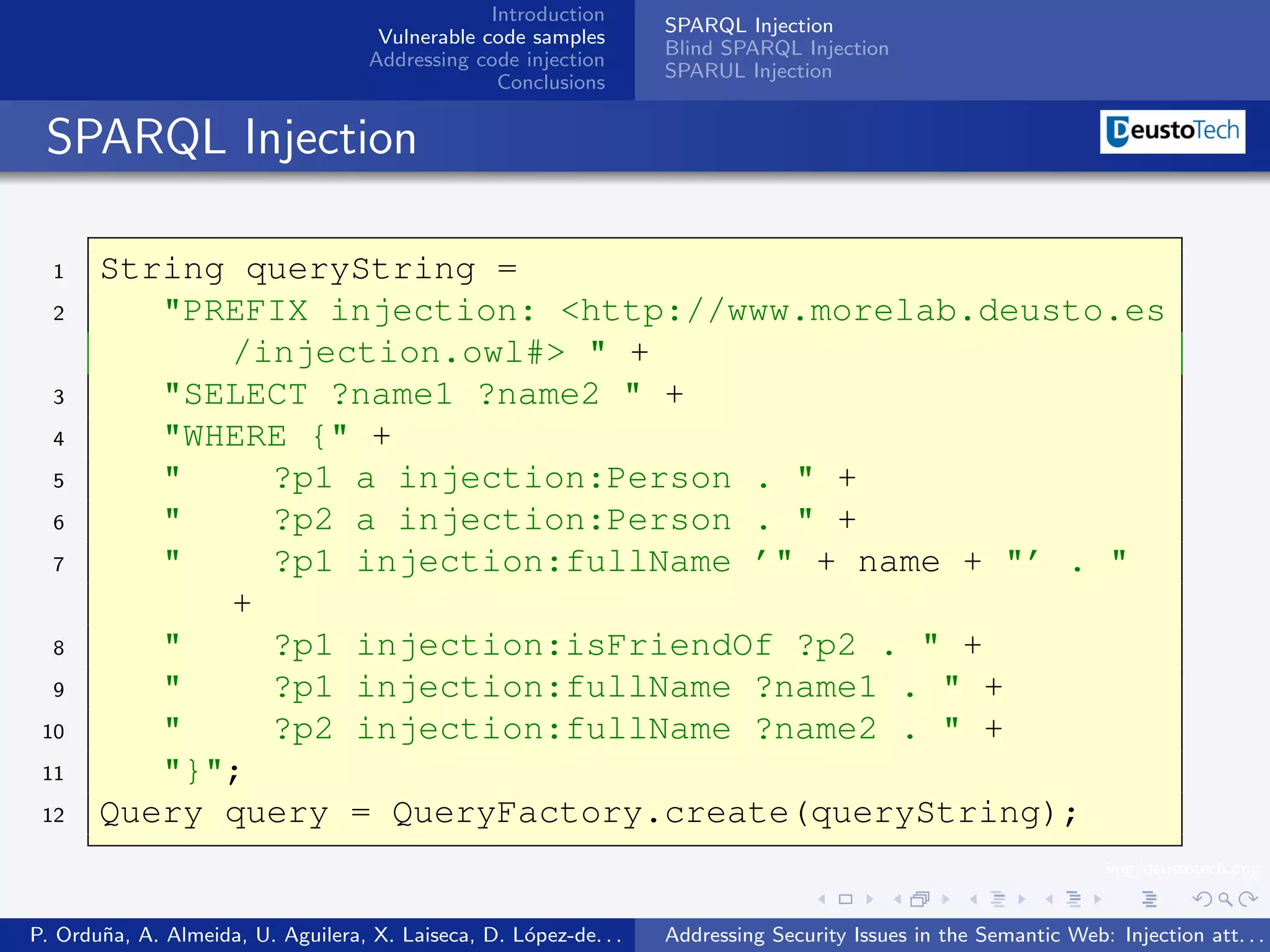
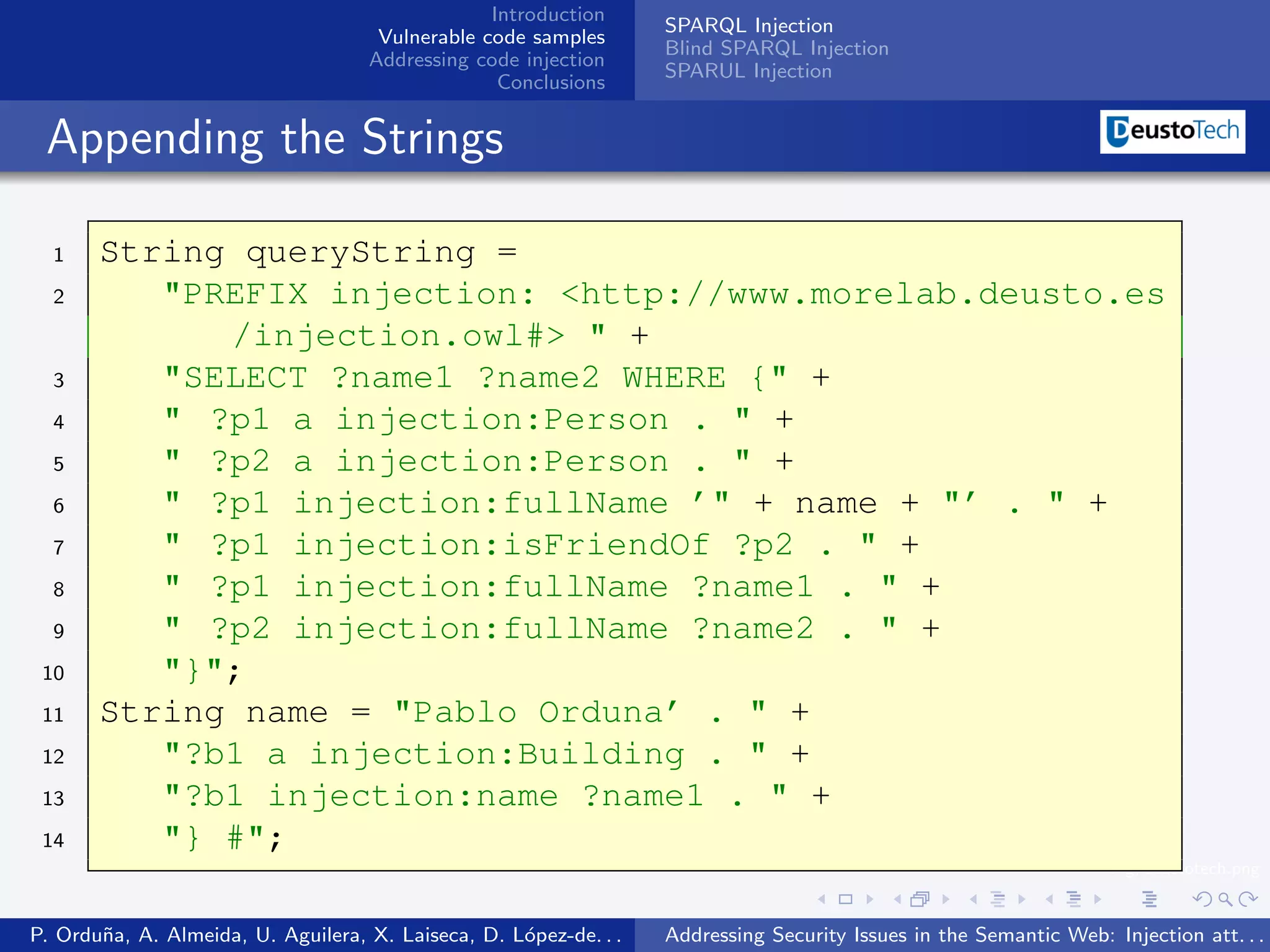
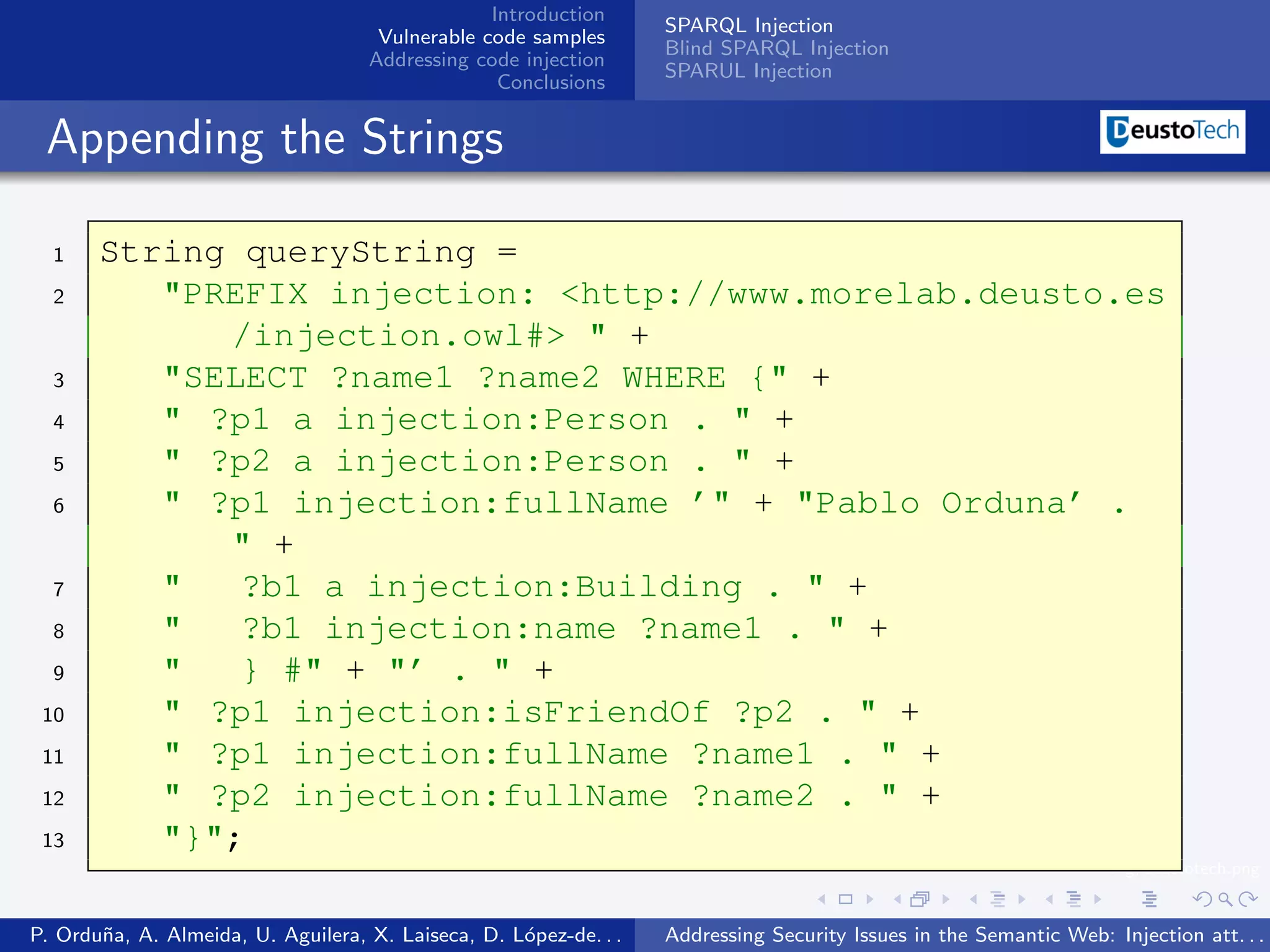
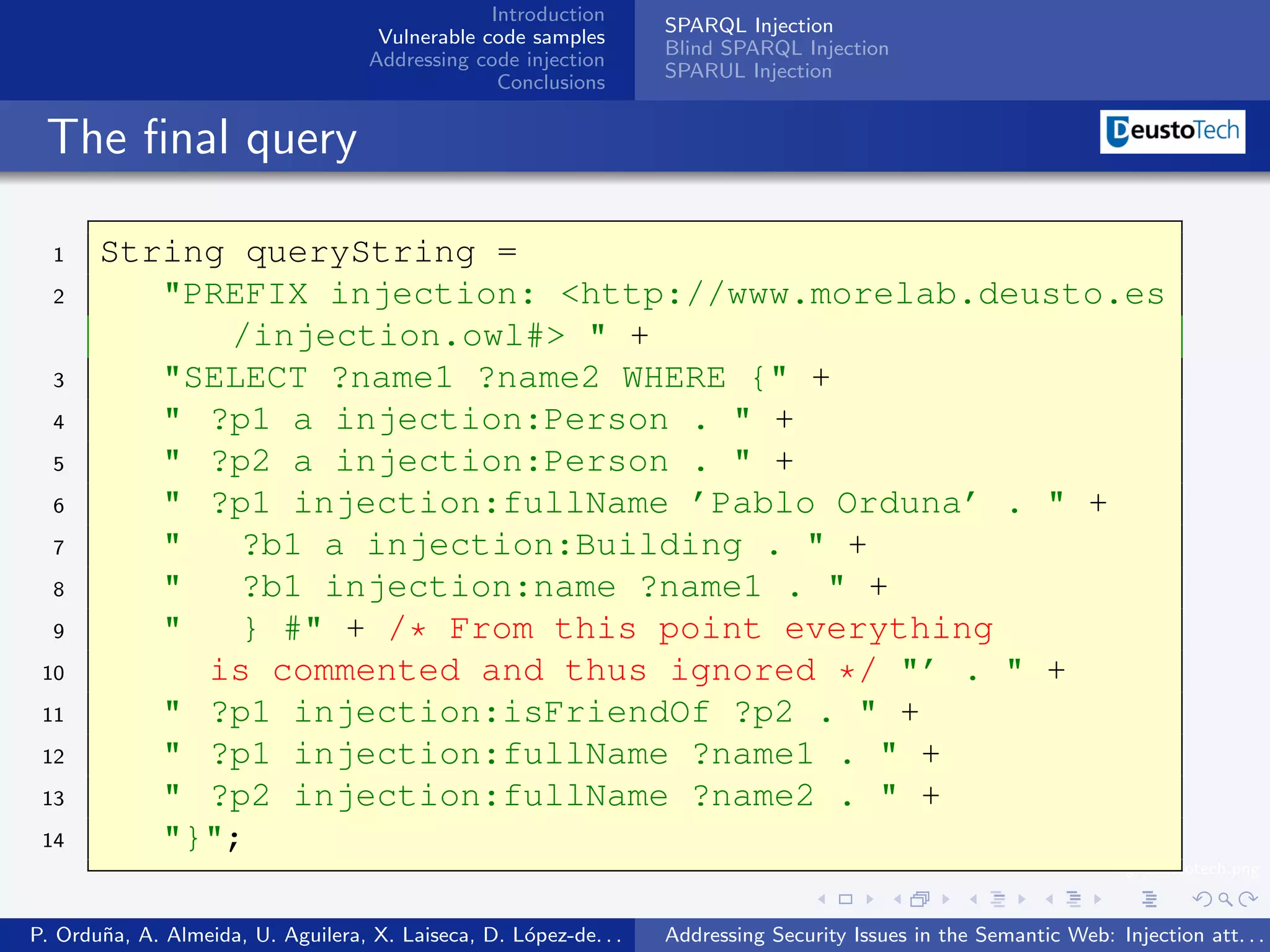
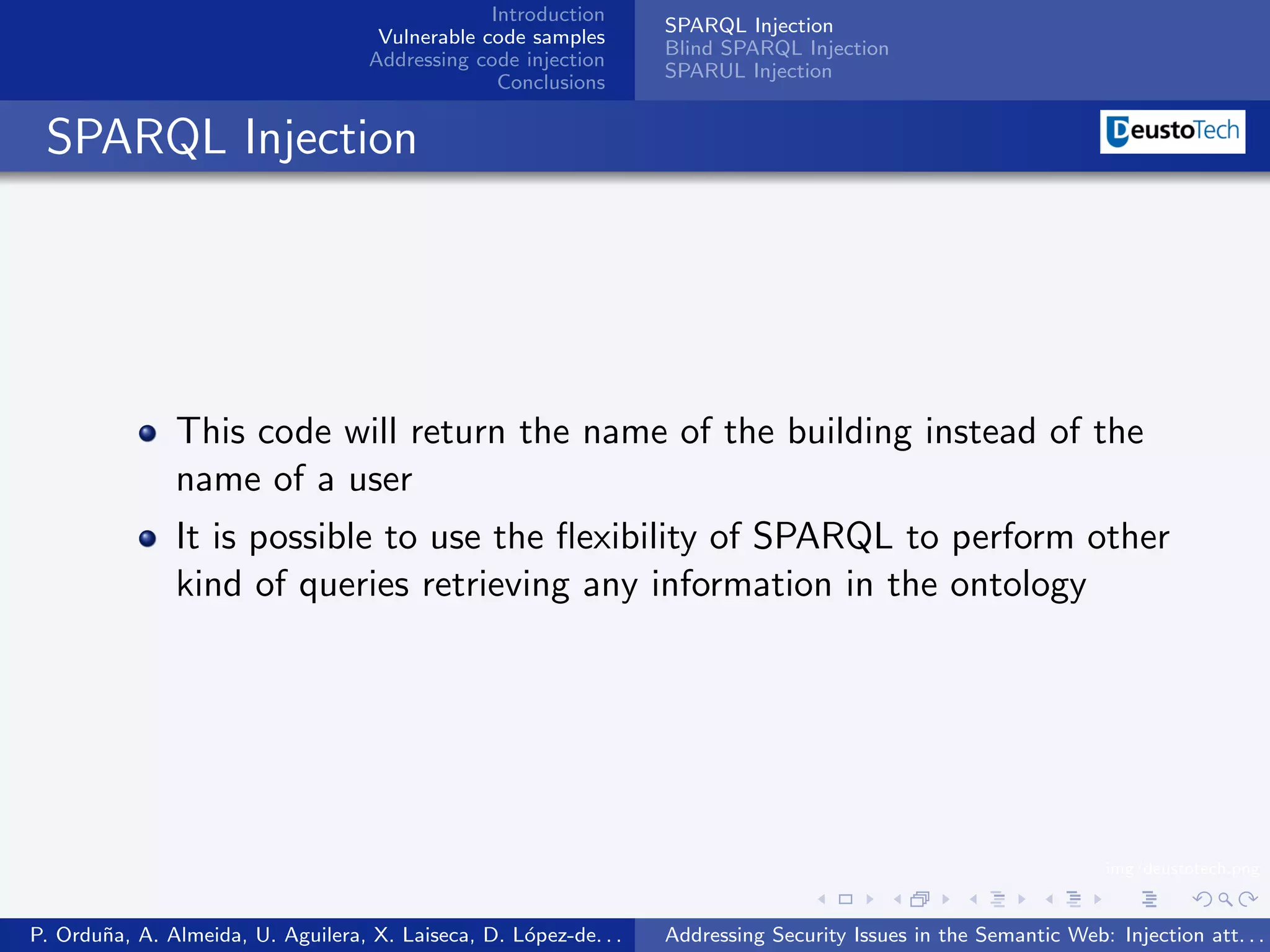
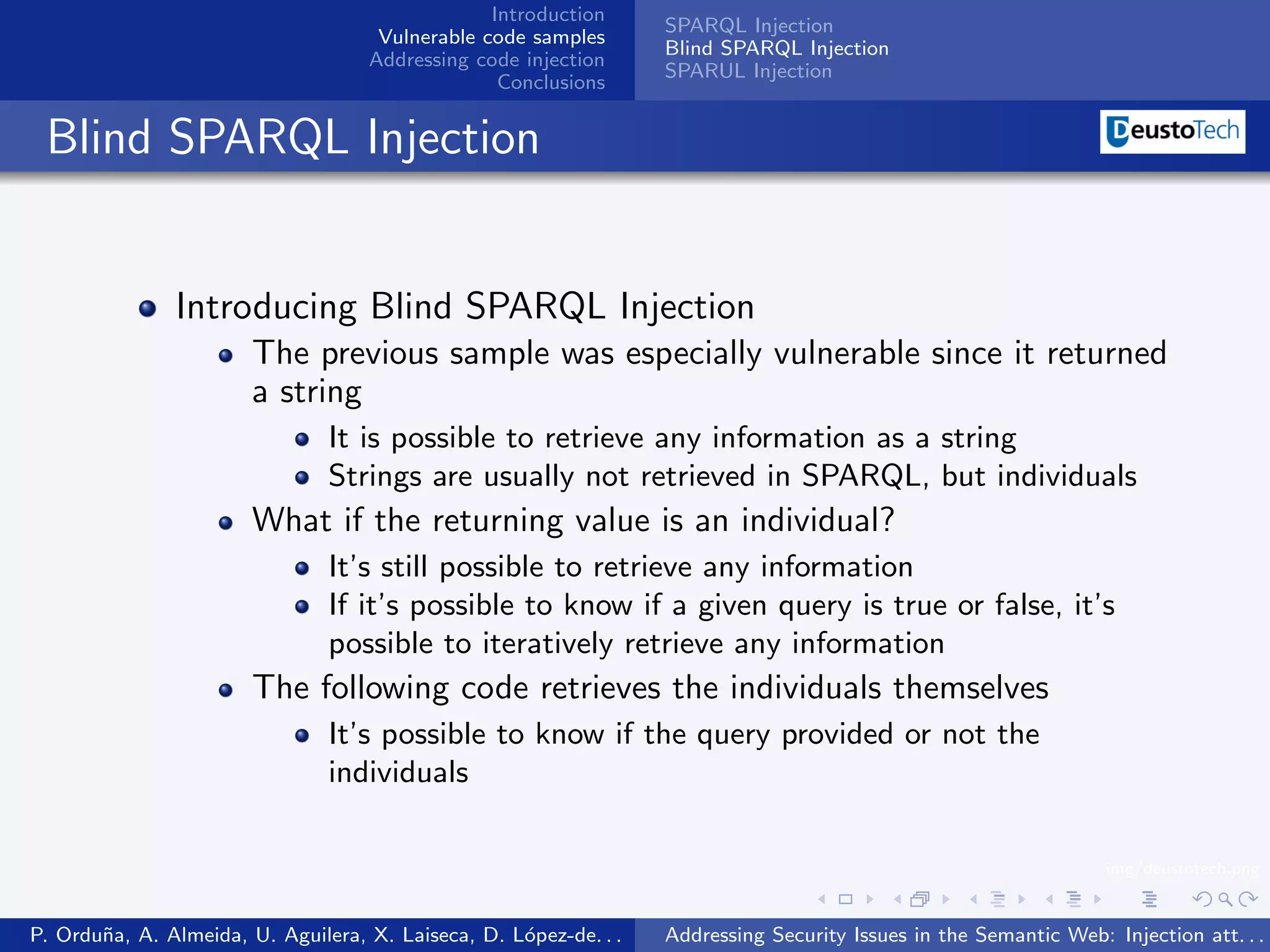
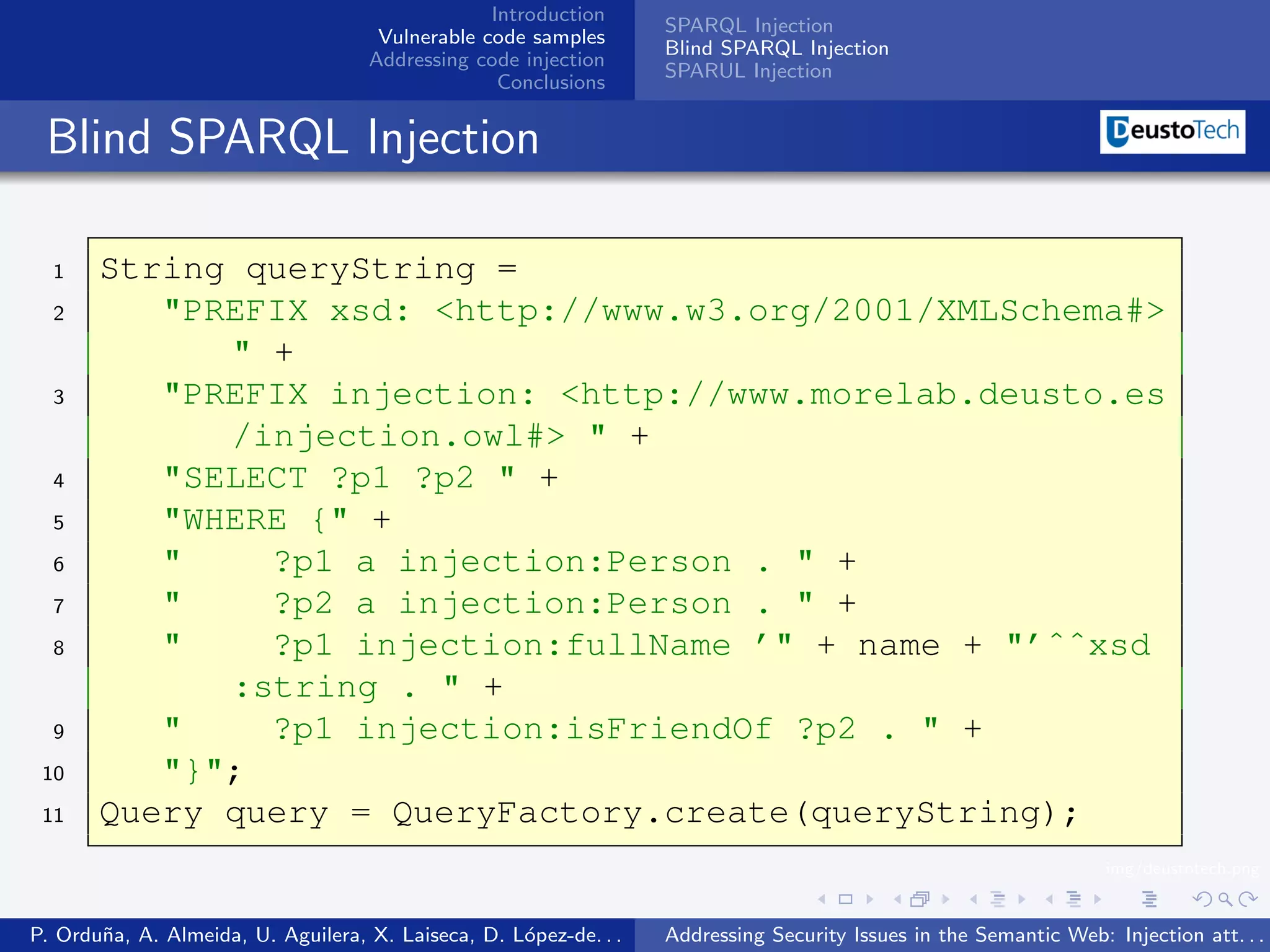
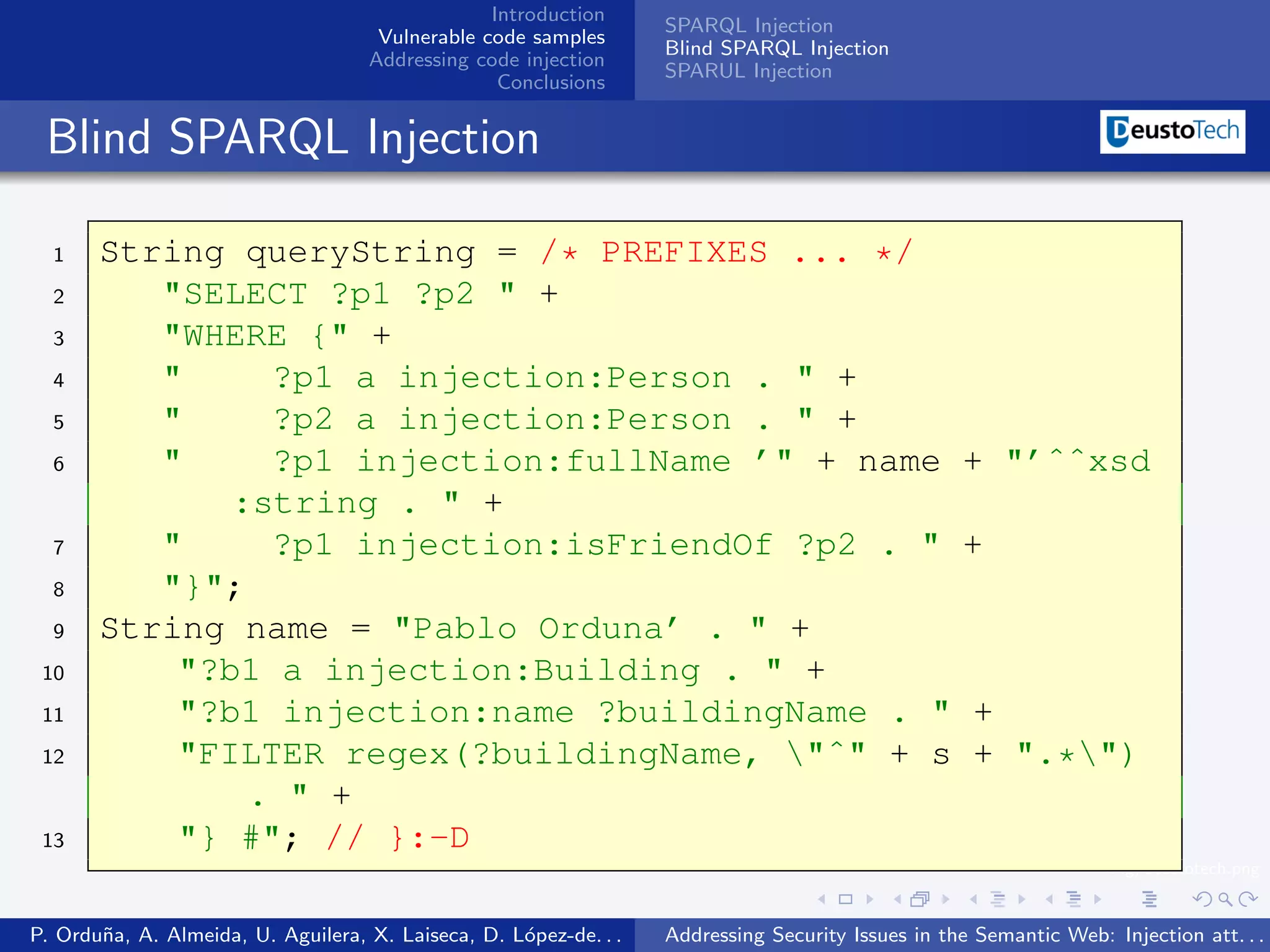
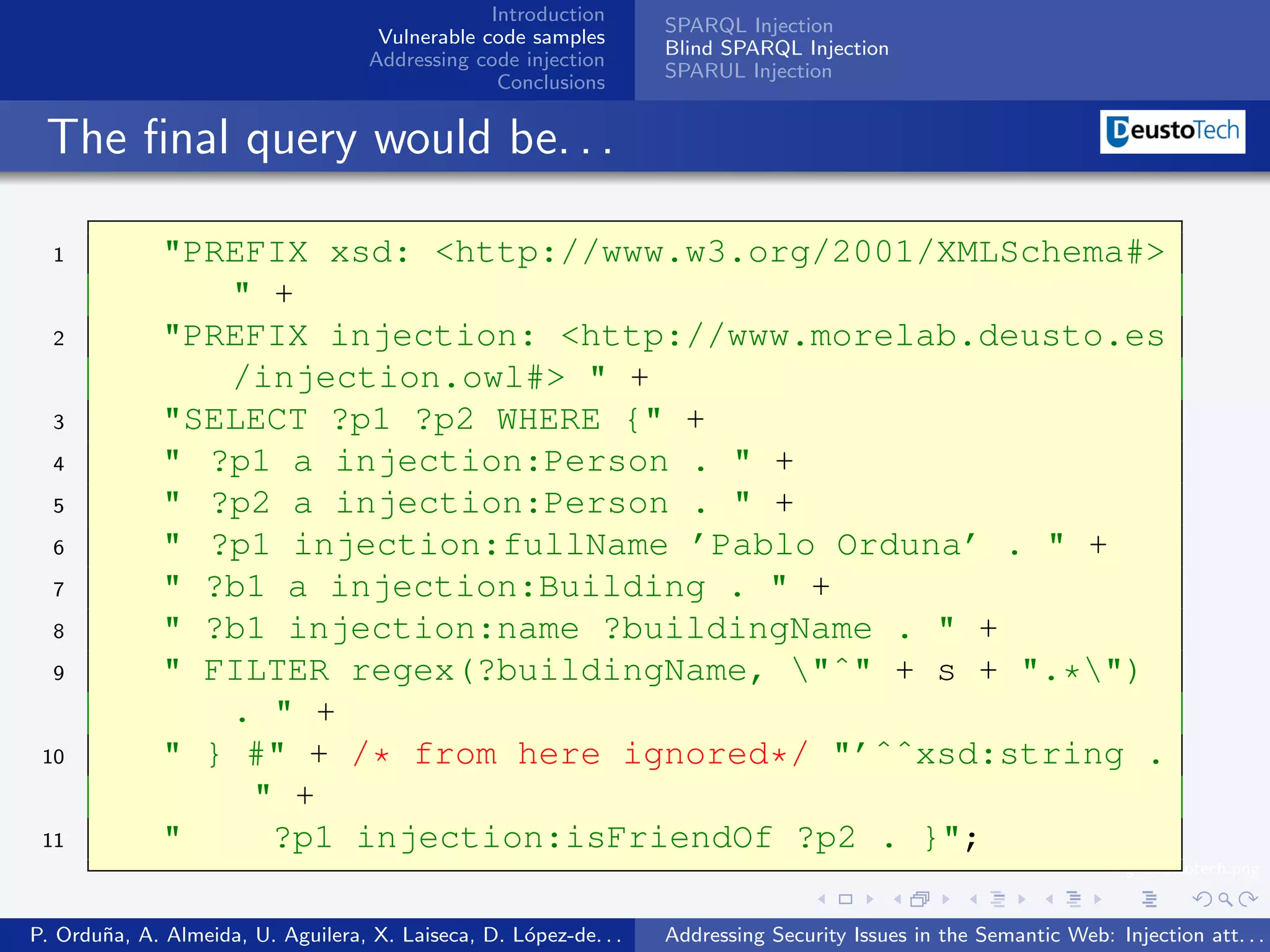
The document discusses security issues related to injection attacks in semantic query languages like SPARQL. It introduces SPARQL injection by showing an example query that is vulnerable because it appends a user-provided name variable without sanitization. This allows the variable to contain malicious SPARQL code that can modify the query. The document also briefly mentions blind SPARQL injection and SPARUL injection as other issues.




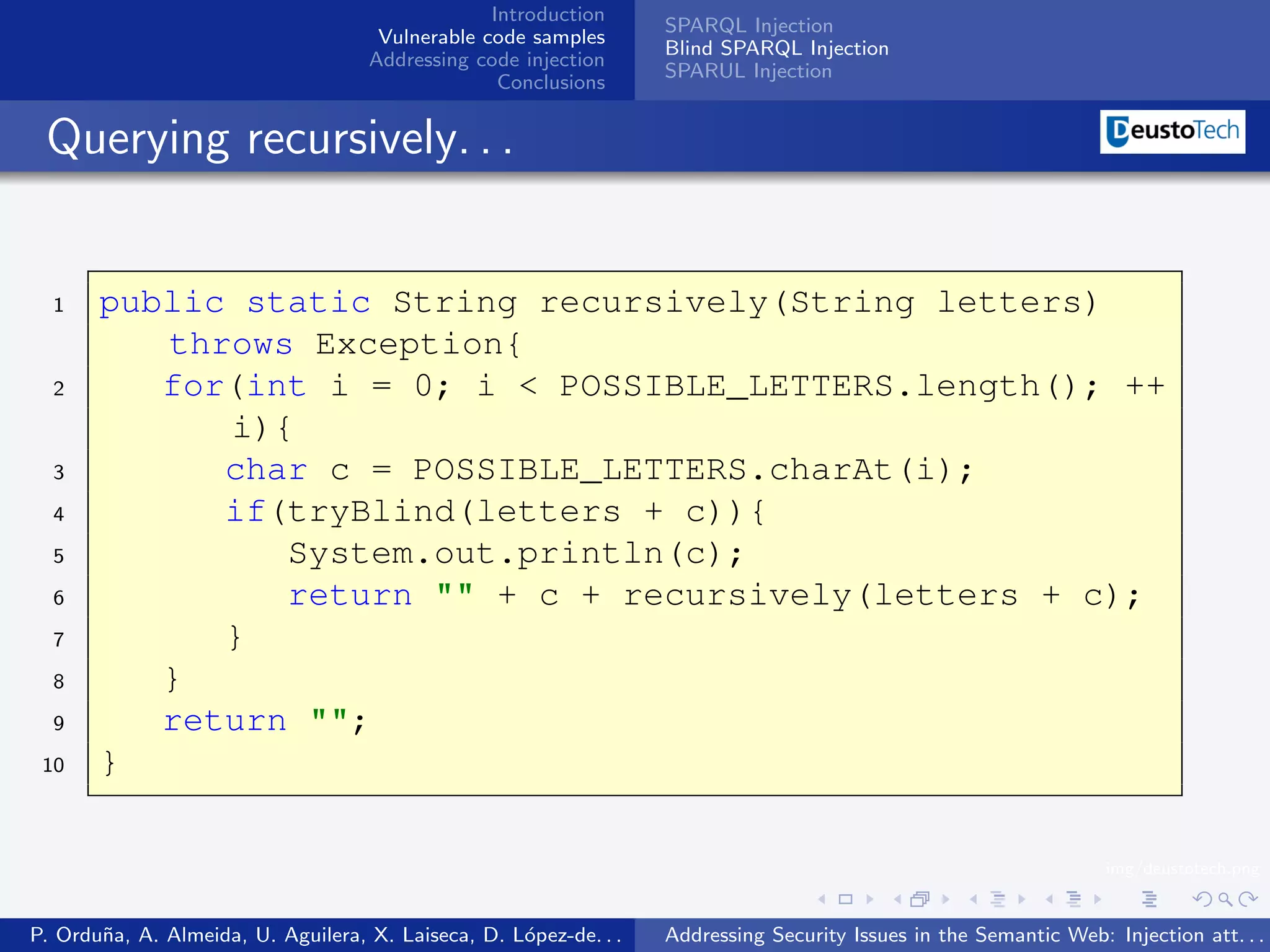
![Introduction SPARQL Injection Vulnerable code samples Blind SPARQL Injection Addressing code injection SPARUL Injection Conclusions Blind SPARQL Injection It is possible to optimize this system using binary search Performing queries using Regular Expressions like ˆ[A-M].* to know if the char is between the char A and M Given a charset of length 64, we would reduce the number of iterations from 64 times 10 (640) to 6 times 10 (60) Using the whole UTF-16 charset, it would reduce the number of iterations from 65536 times 10 (655360) to 16 times 10 (160) The point is that it’s possible to retrieve any information in the ontology independently from the values returned by the query img/deustotech.png P. Ordu˜a, A. Almeida, U. Aguilera, X. Laiseca, D. L´pez-de. . . n o Addressing Security Issues in the Semantic Web: Injection att. . .](https://image.slidesharecdn.com/sparqlinjection-100913041919-phpapp01/75/Identifying-Security-Issues-in-the-Semantic-Web-Injection-attacks-in-the-Semantic-Query-Languages-18-2048.jpg)