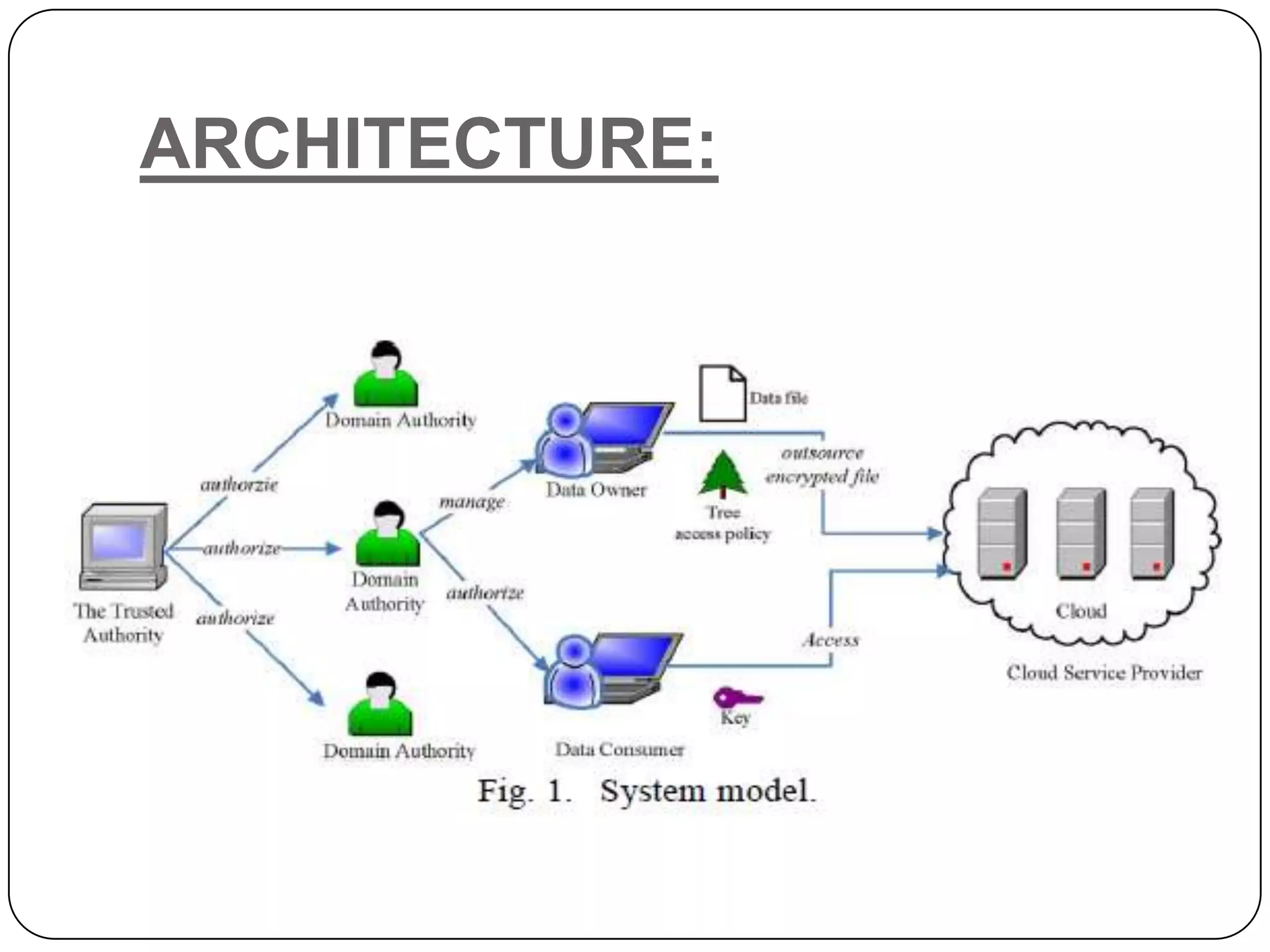
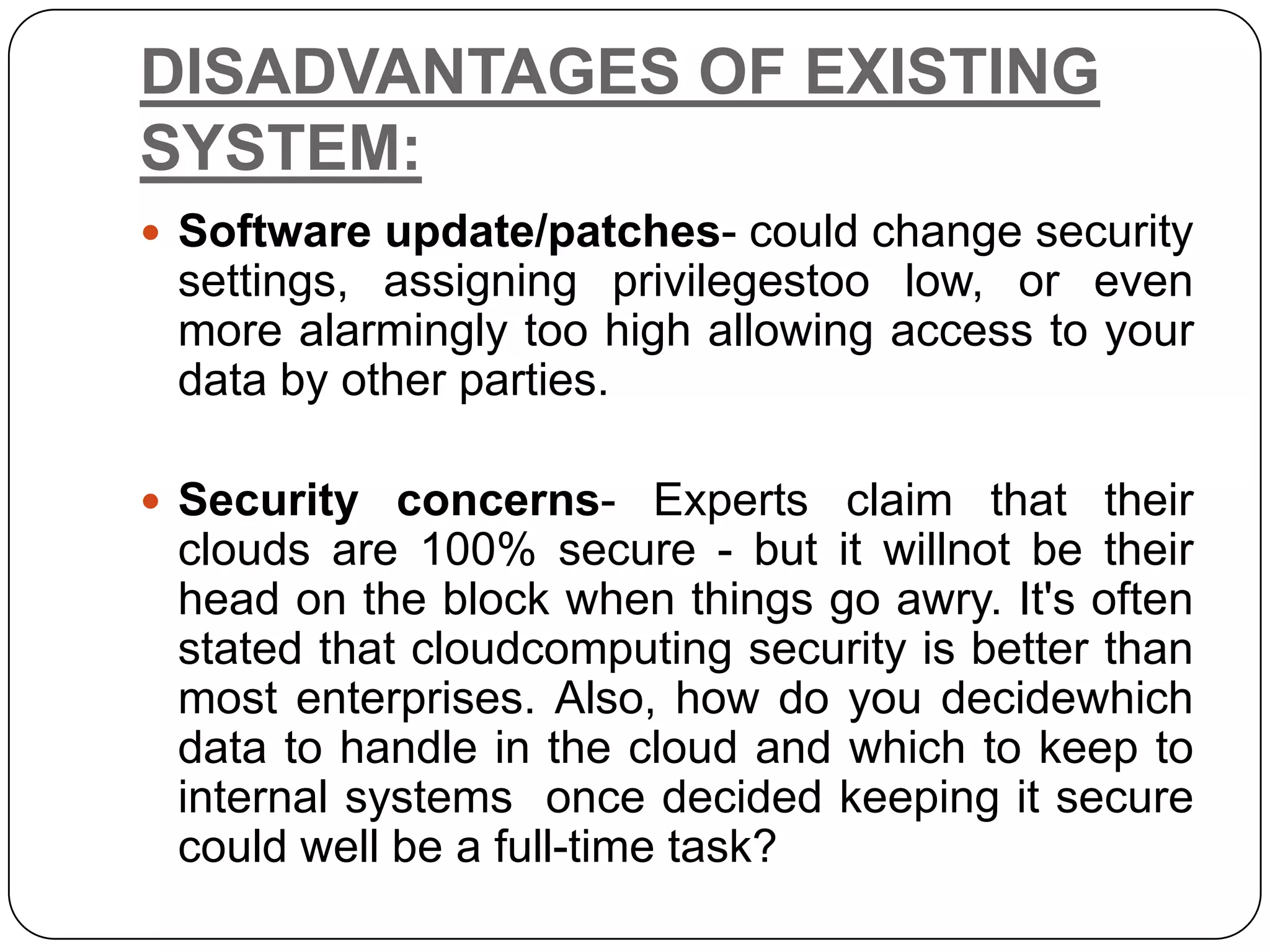
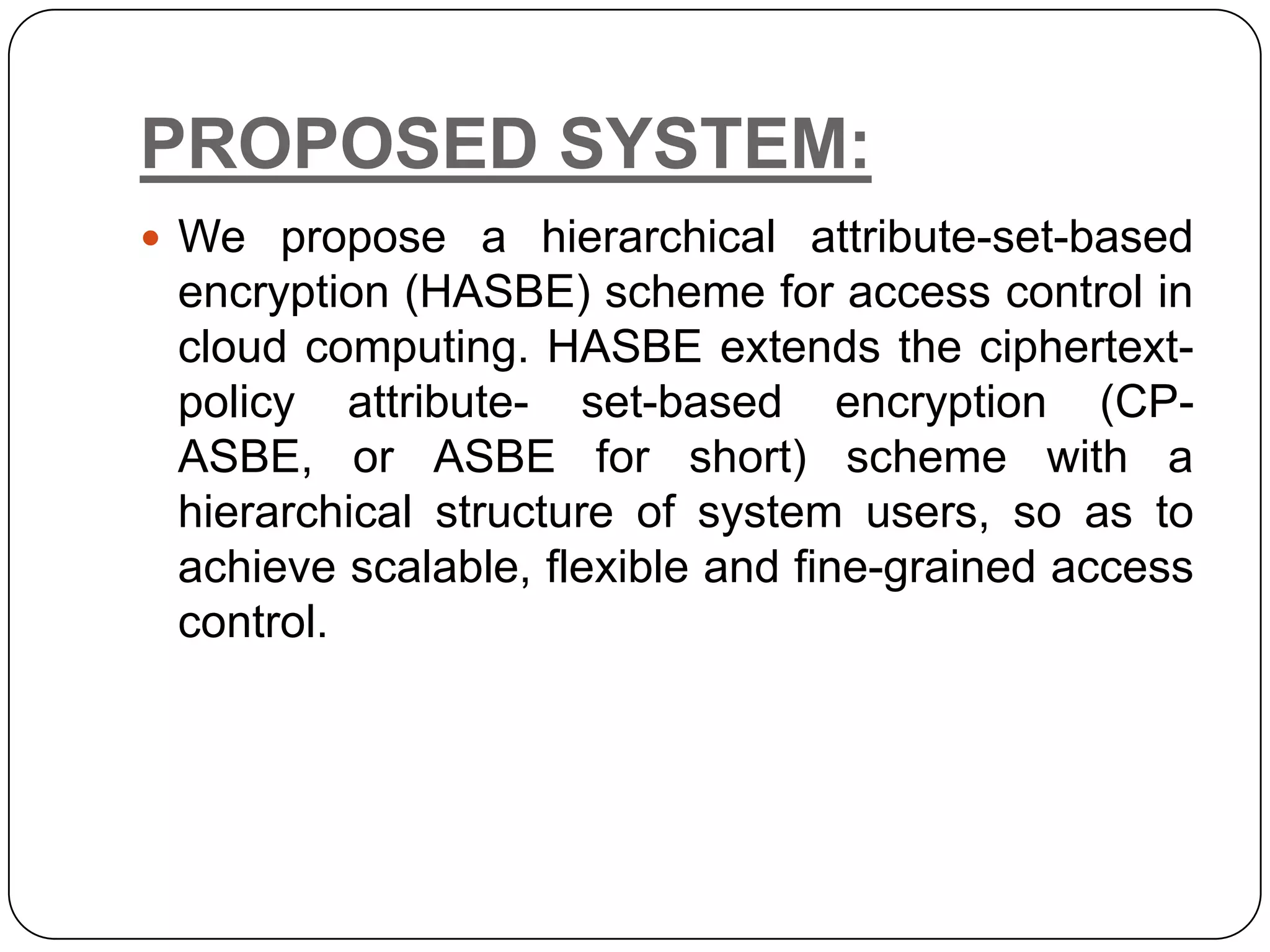
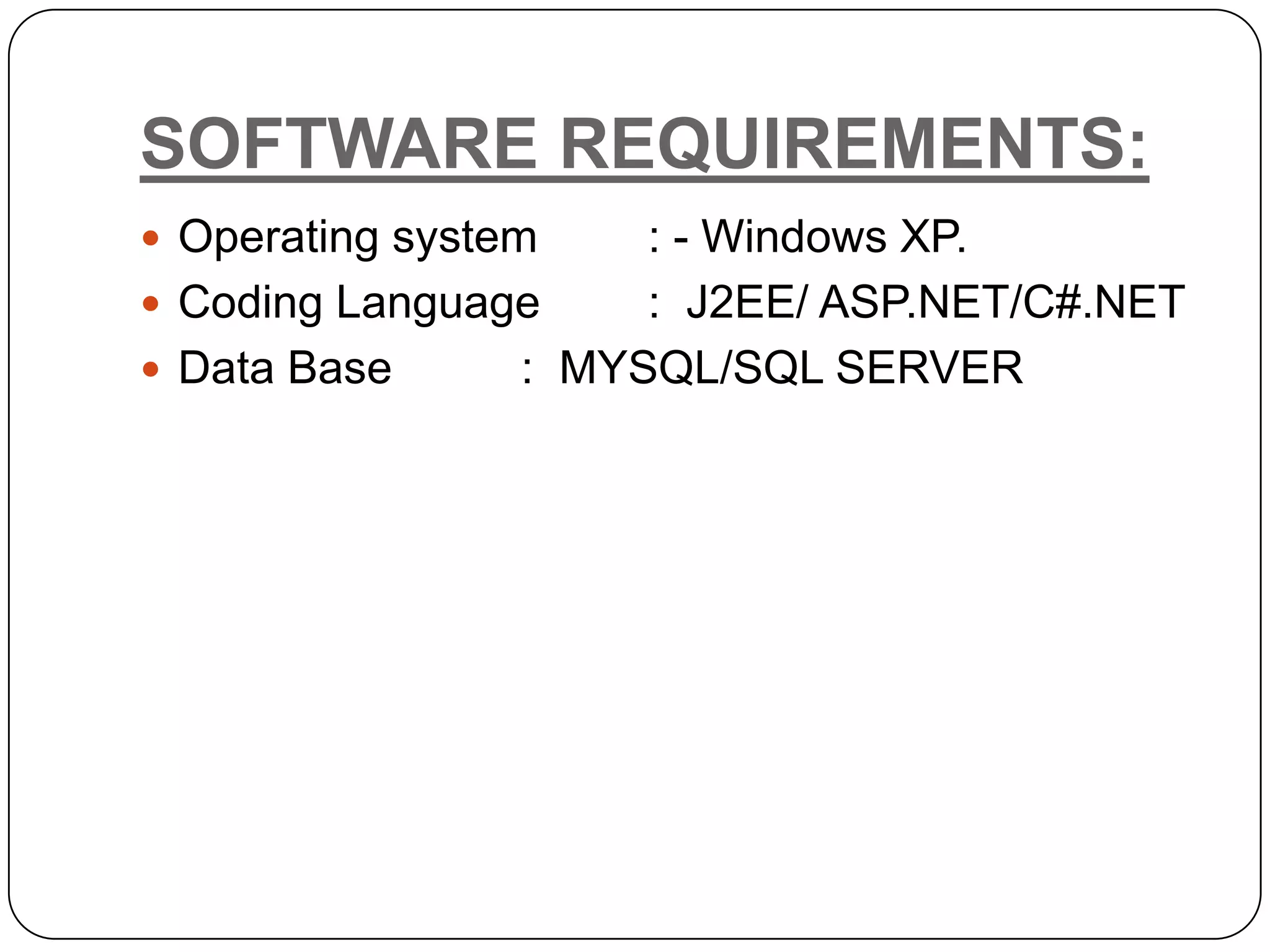
The document presents a Hierarchical Attribute-set-Based Encryption (HASBE) scheme designed for flexible and scalable access control in cloud computing, which enhances security and efficiency compared to existing solutions. HASBE incorporates a hierarchical structure allowing for fine-grained access management and efficient user revocation, addressing limitations related to computation overhead and security concerns in traditional systems. Additionally, the proposed system supports seamless data sharing between data owners and consumers while maintaining strong security measures.