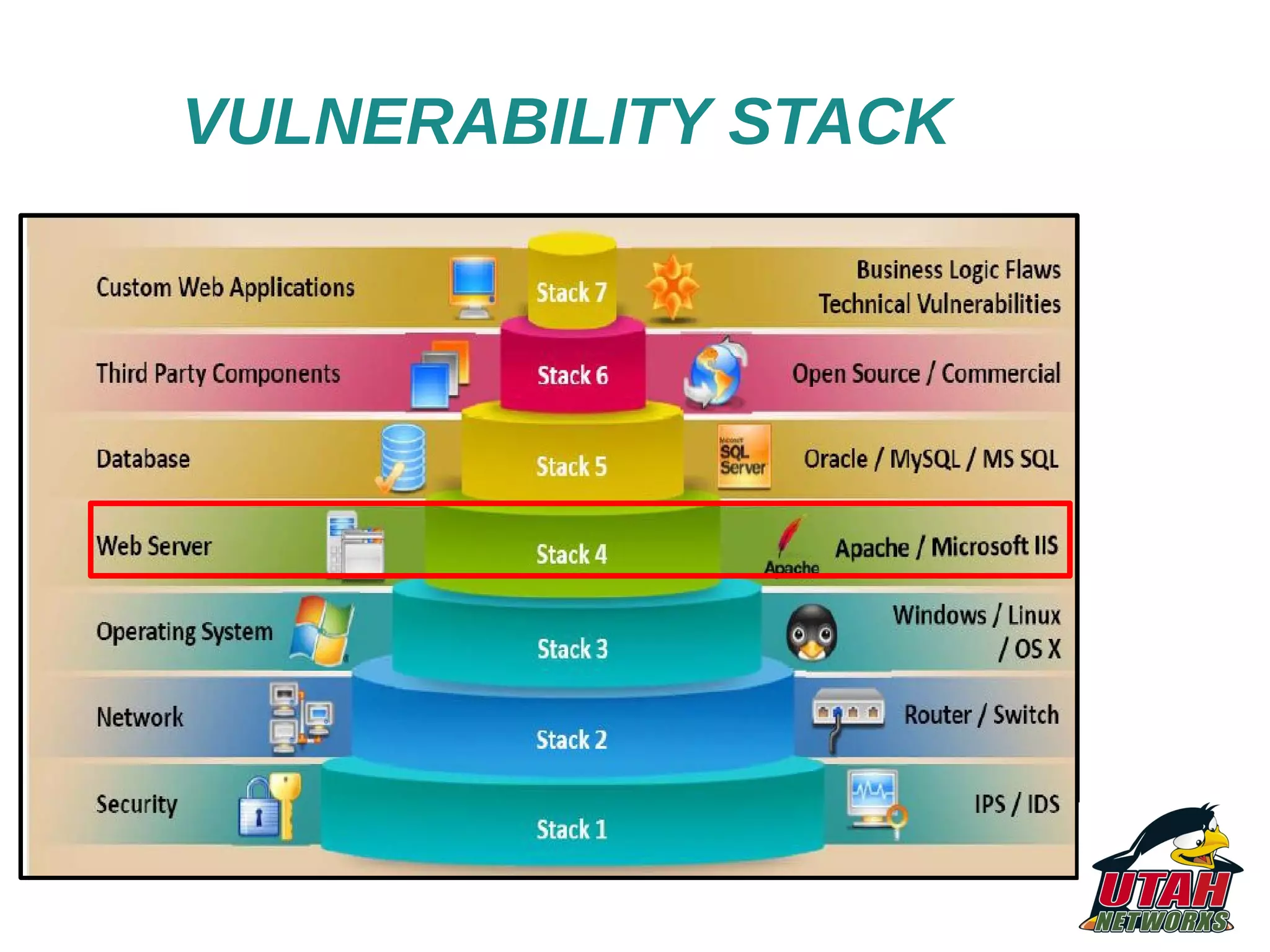
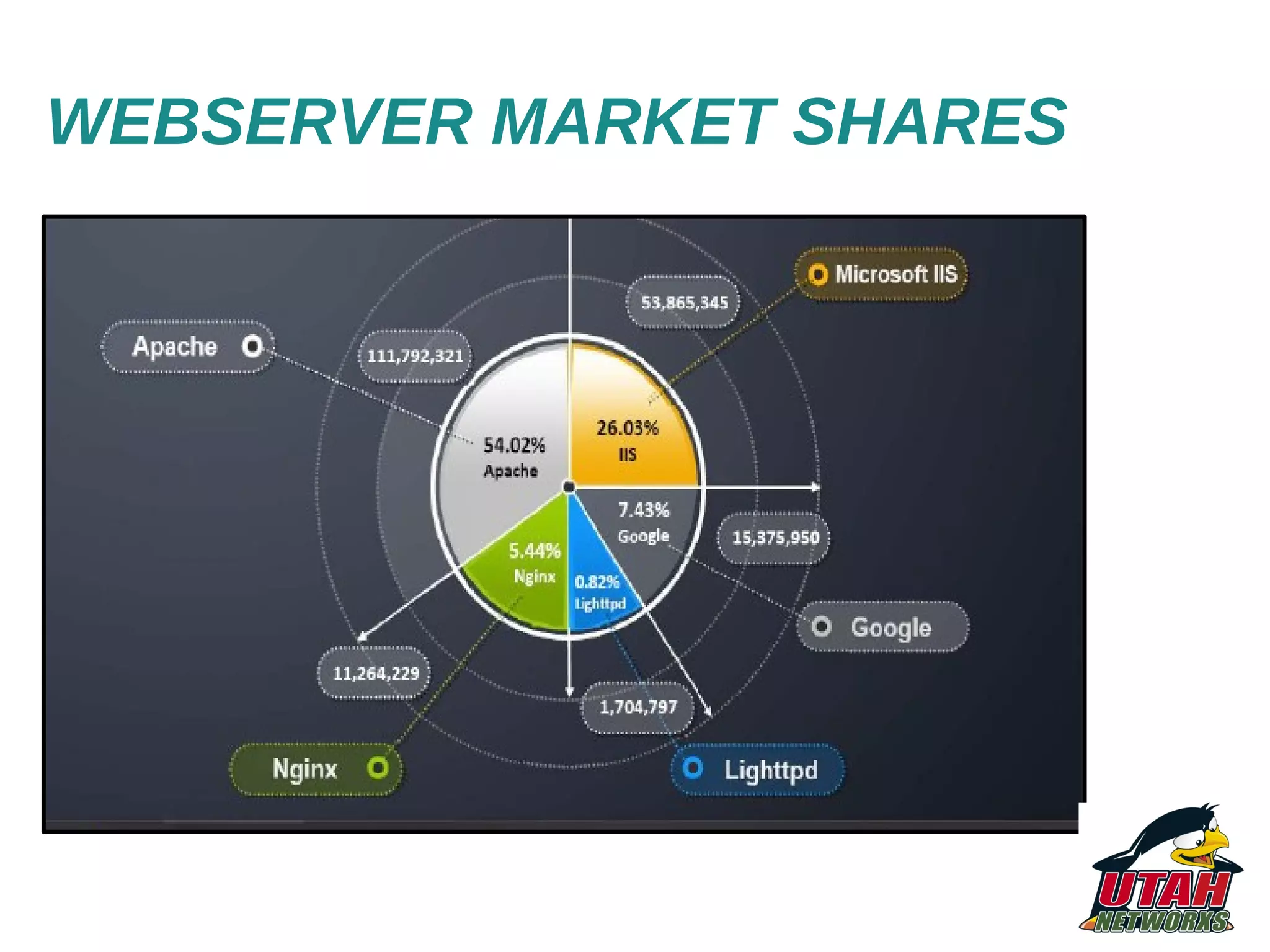
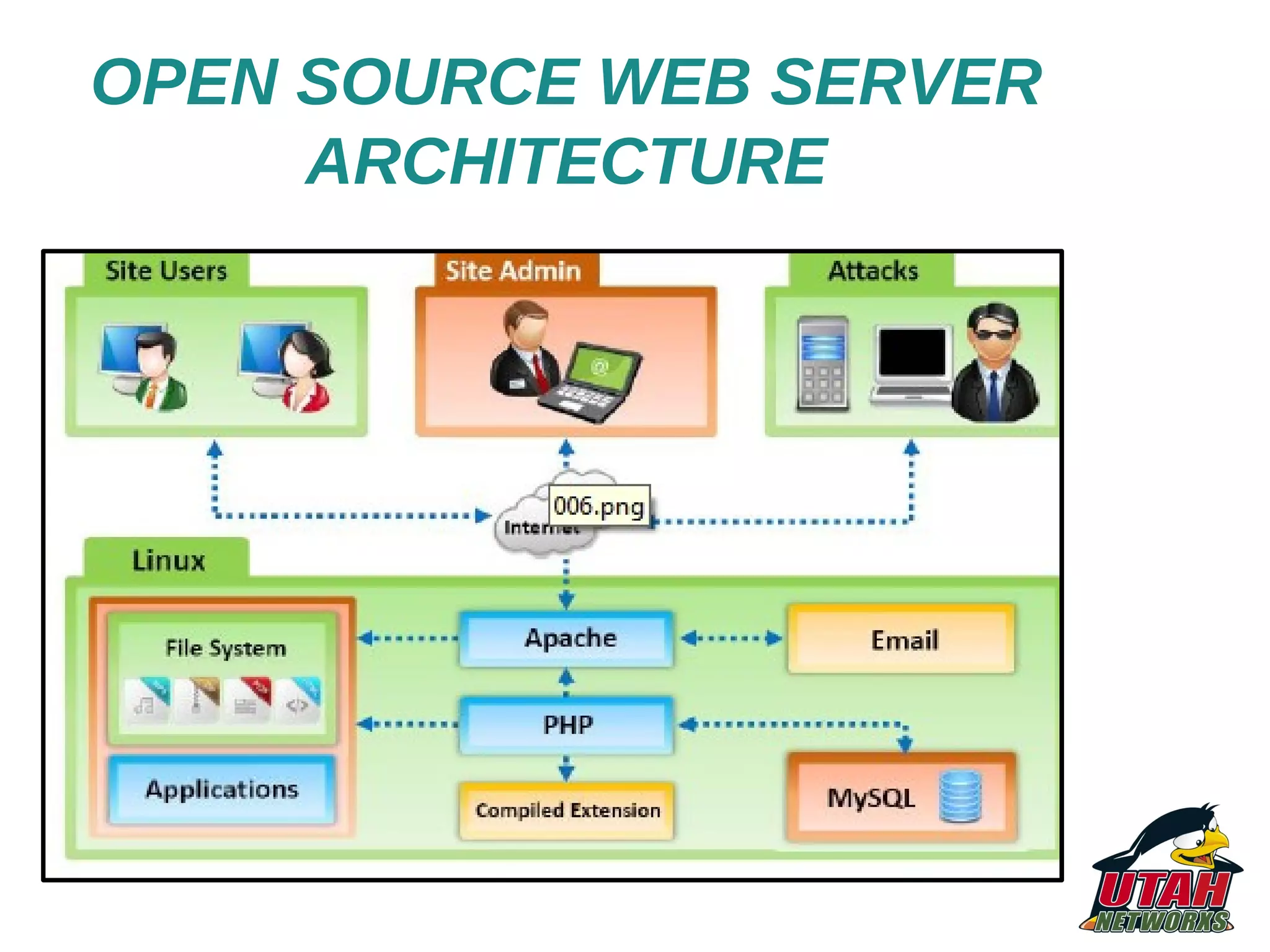
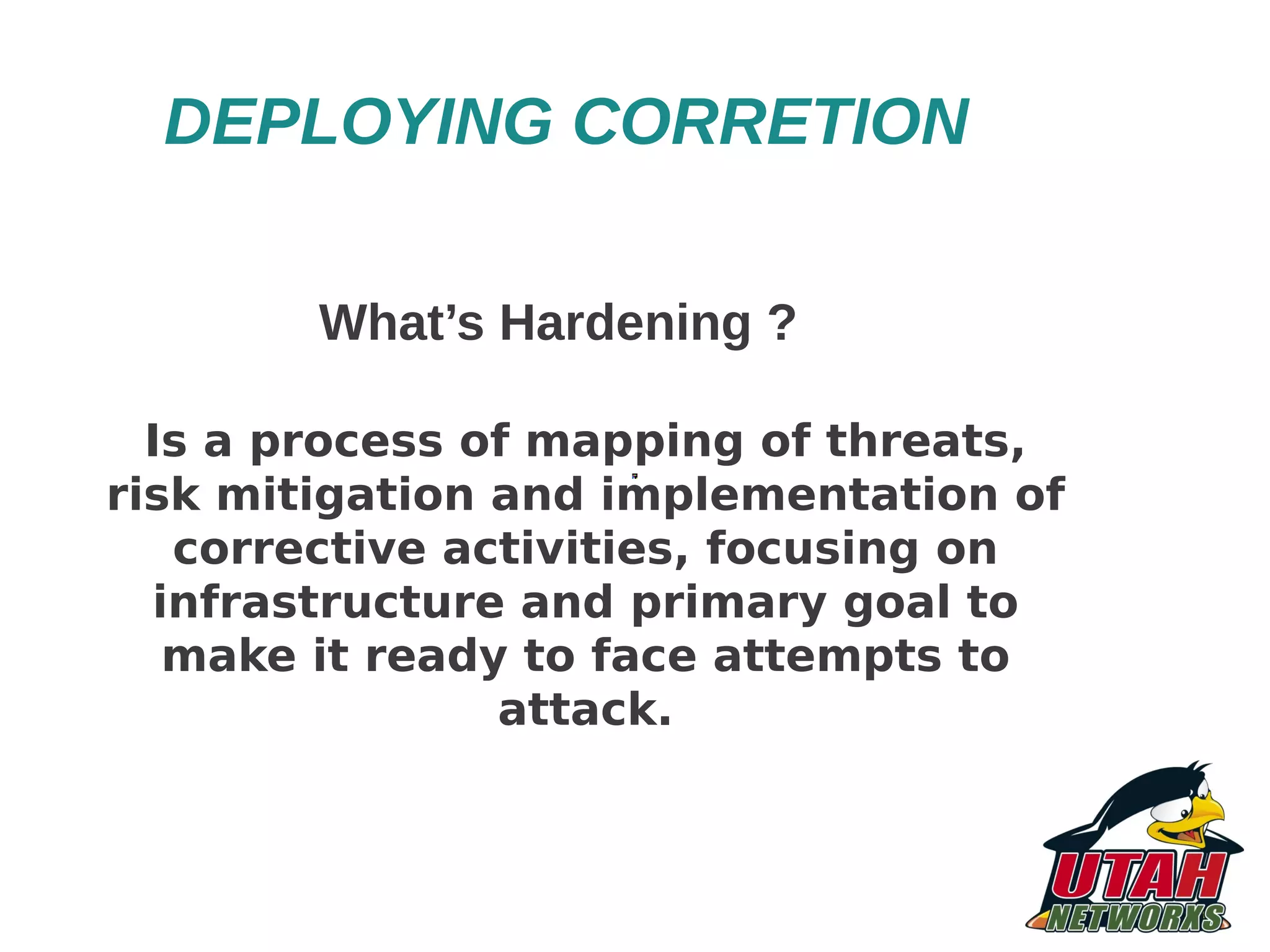
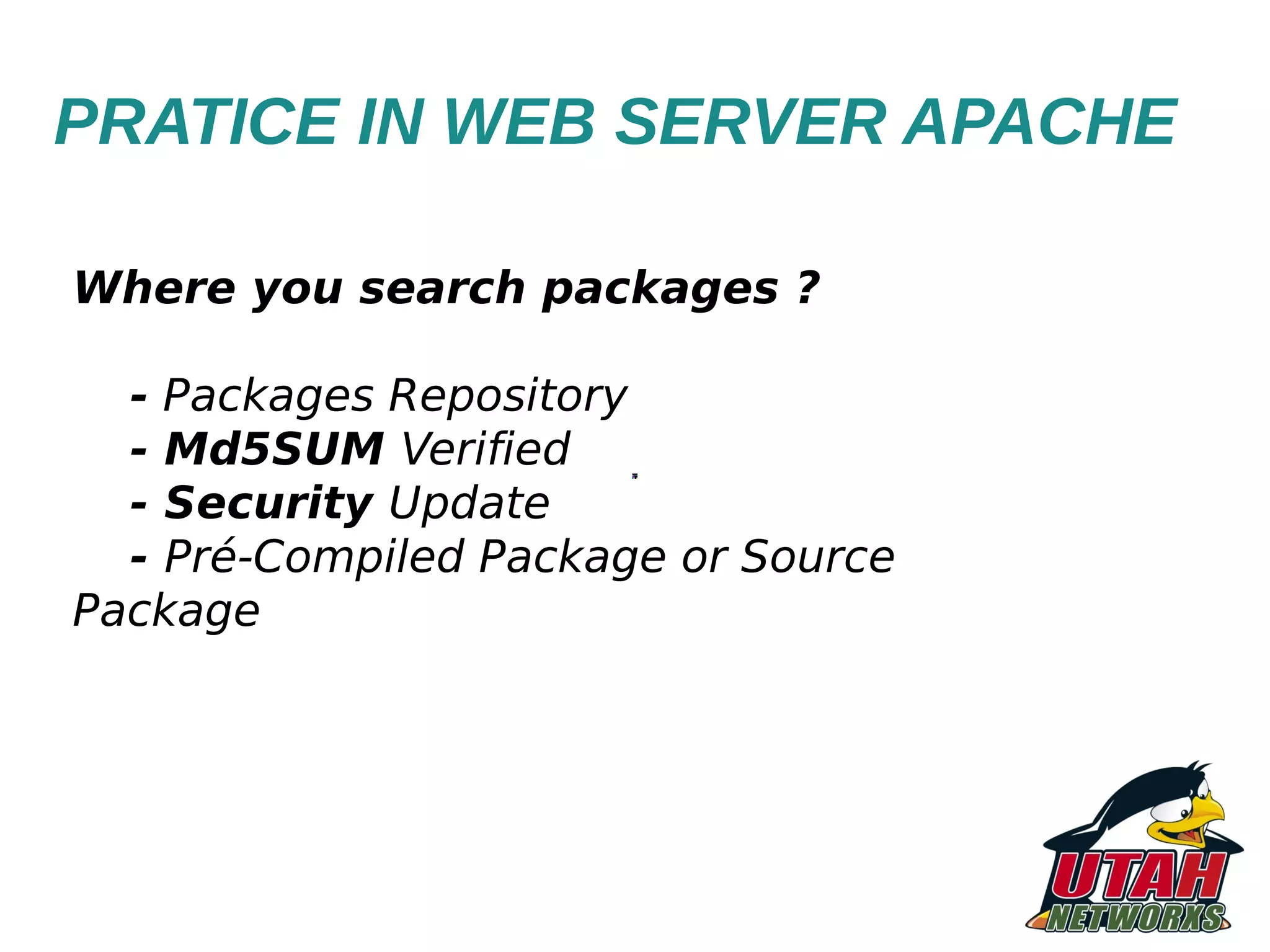
The document discusses threat mapping, risk mitigation, and corrective activities for web servers, focusing on hardening techniques and tools to protect against various types of attacks. It highlights the importance of proper server configurations and provides detailed practices for securing Apache servers, including permissions, vulnerabilities, and the use of security tools. Additionally, it outlines an educational background and experience of the author, Fabio Pires, in Linux and web server consulting in Brazil.







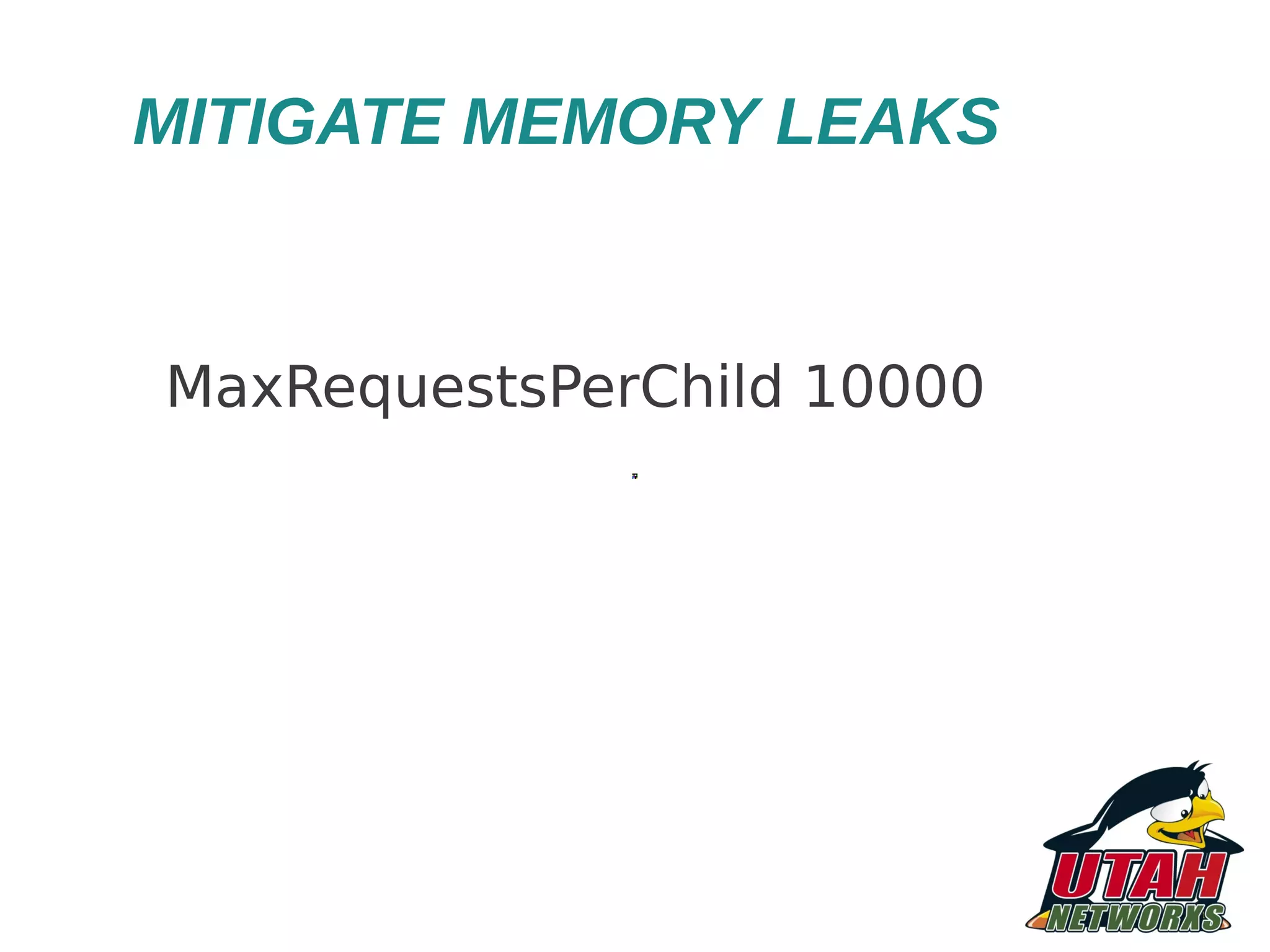
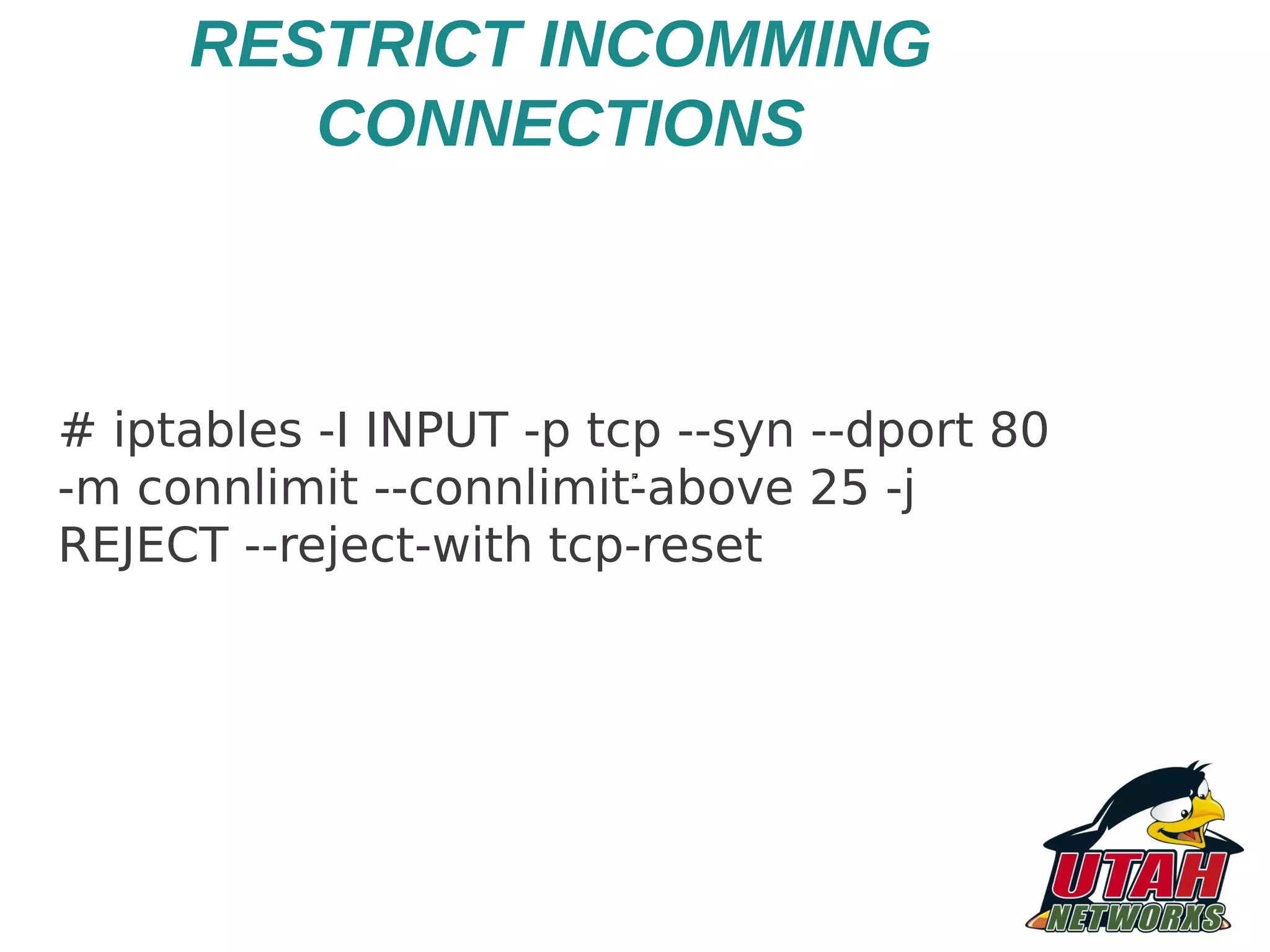
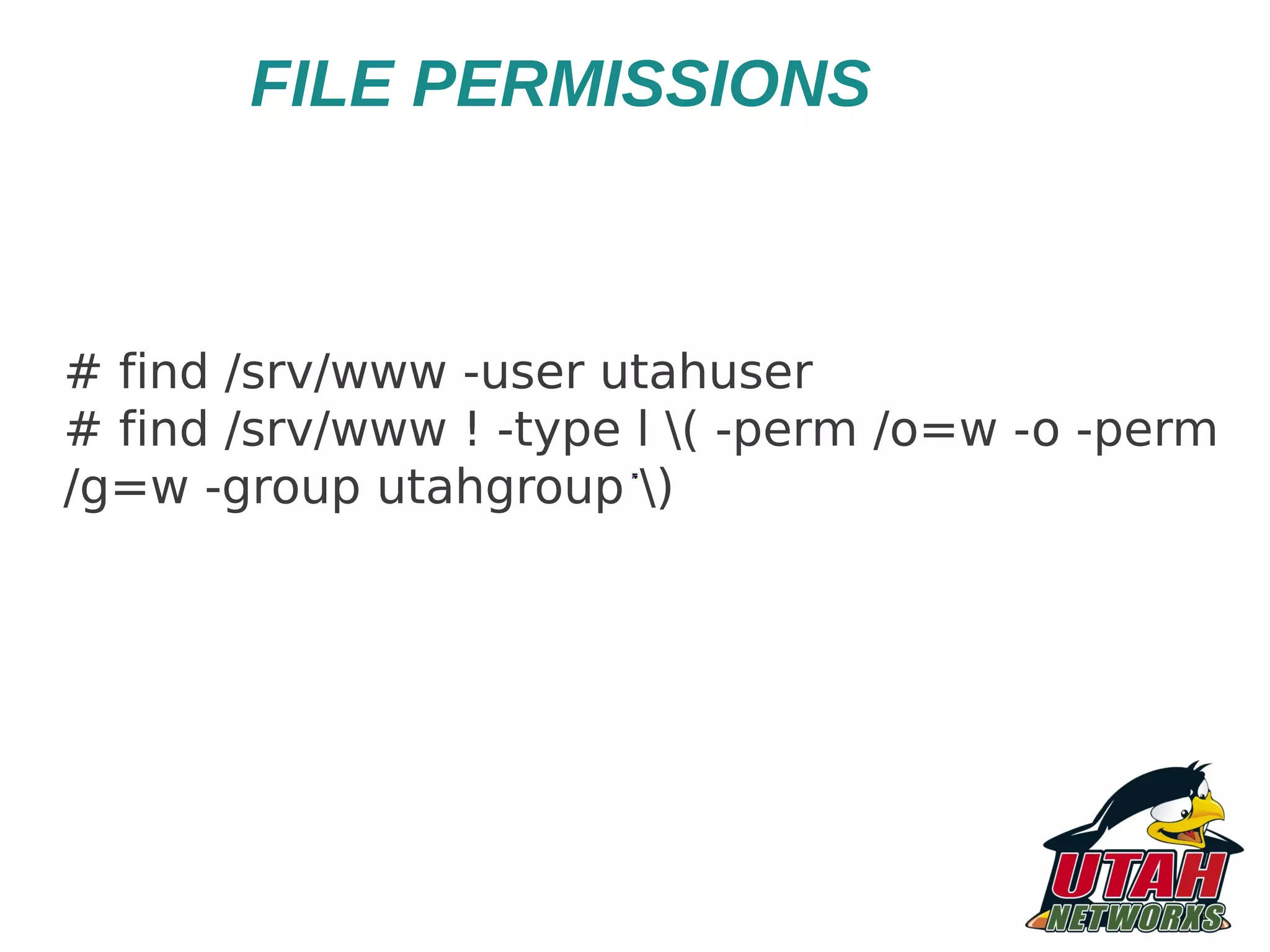
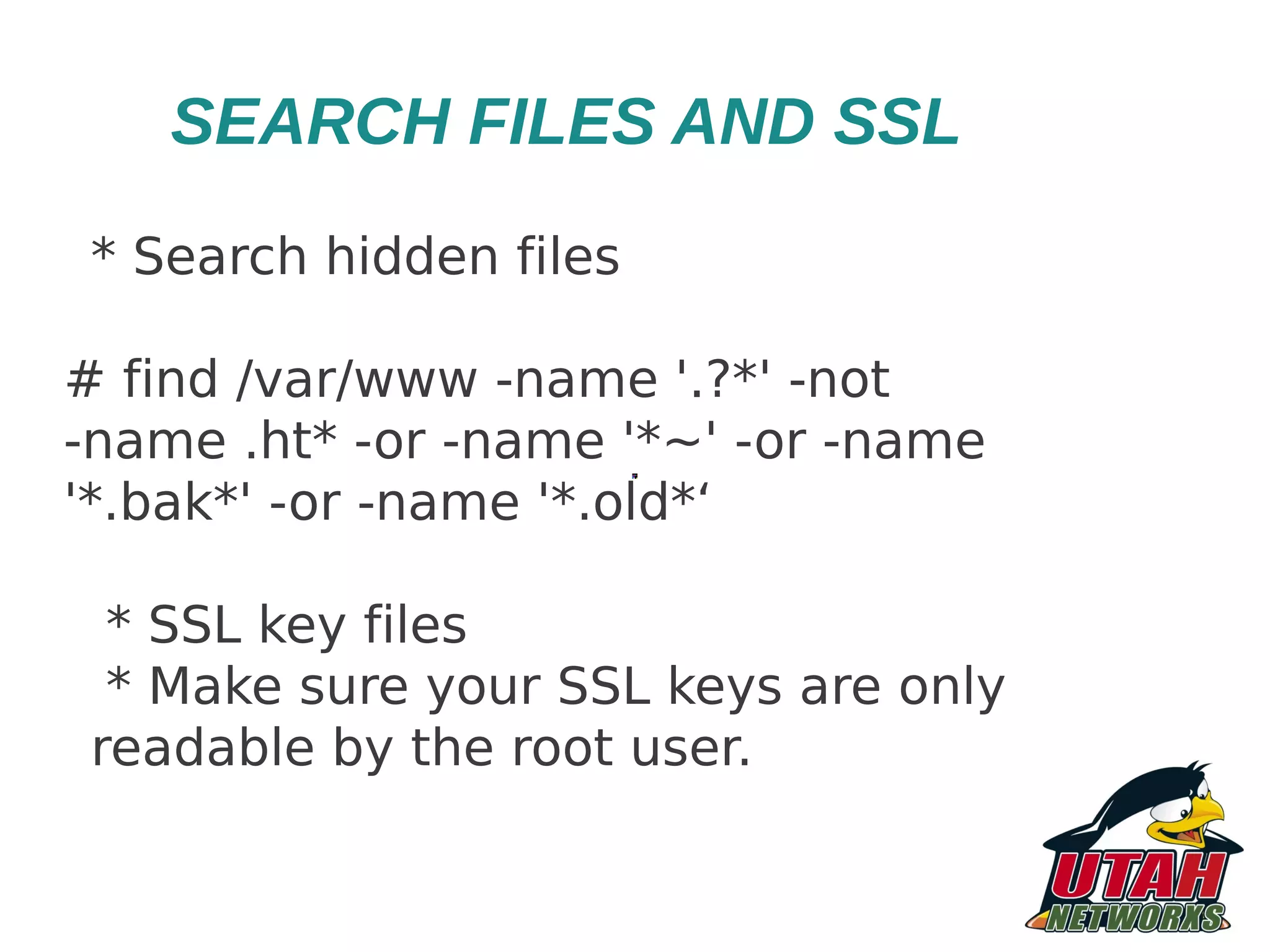
![OTHER APACHE CONFIG * Bewarec of certain RewriteRules # INSECURE configuration, don't use! RewriteRule ^/old/directory/(.*)$ /$1 Use this # SECURE - Use RewriteRule ^/old/directory/(.*)$ /$1 [PT] * Don't use Limit/LimitExcept (conf.d/security) TraceEnable off](https://image.slidesharecdn.com/newmappingthreatsmitigatingriskandimplementing-121204074439-phpapp01/75/HARDENING-IN-APACHE-WEB-SERVER-23-2048.jpg)