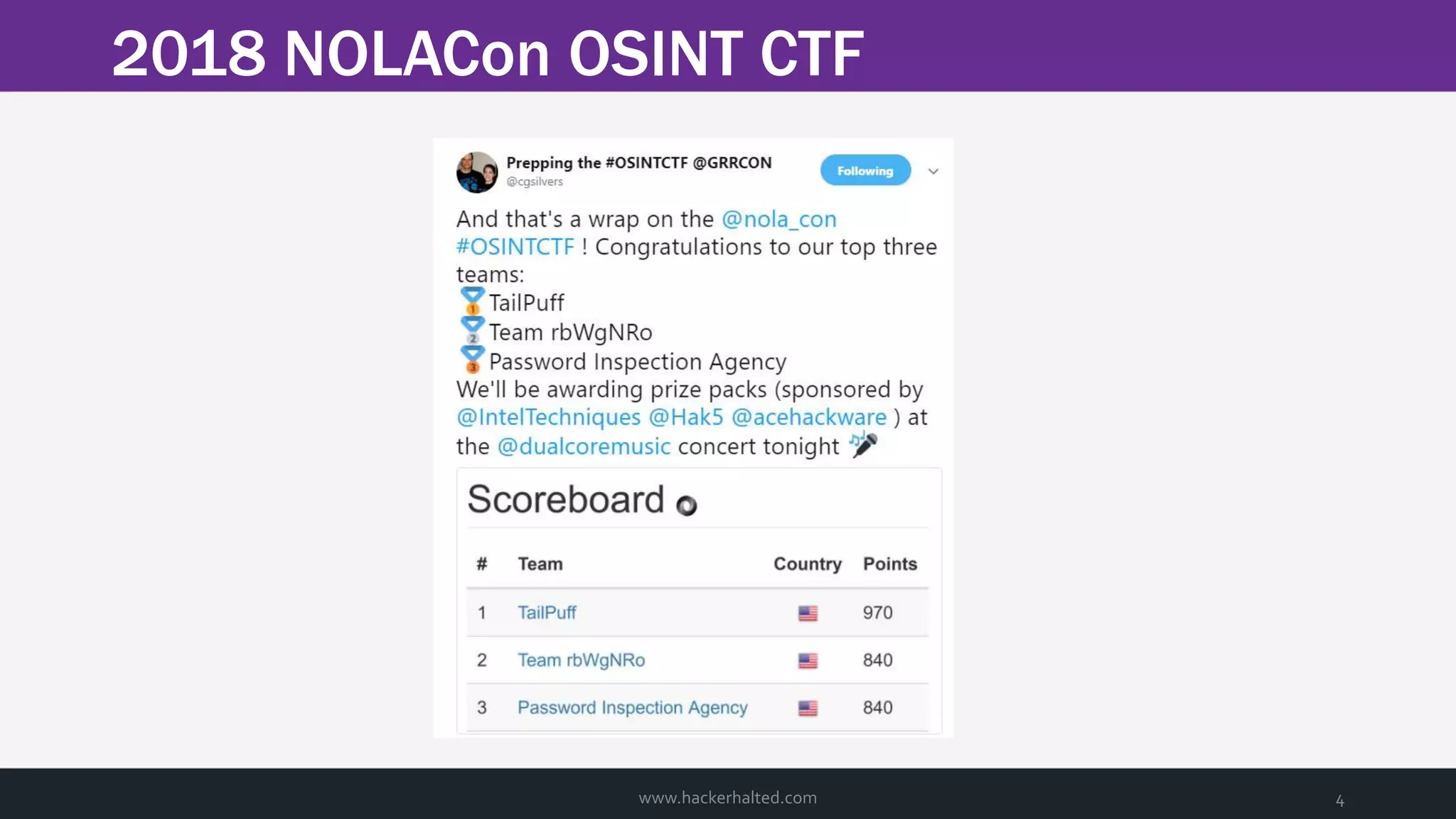
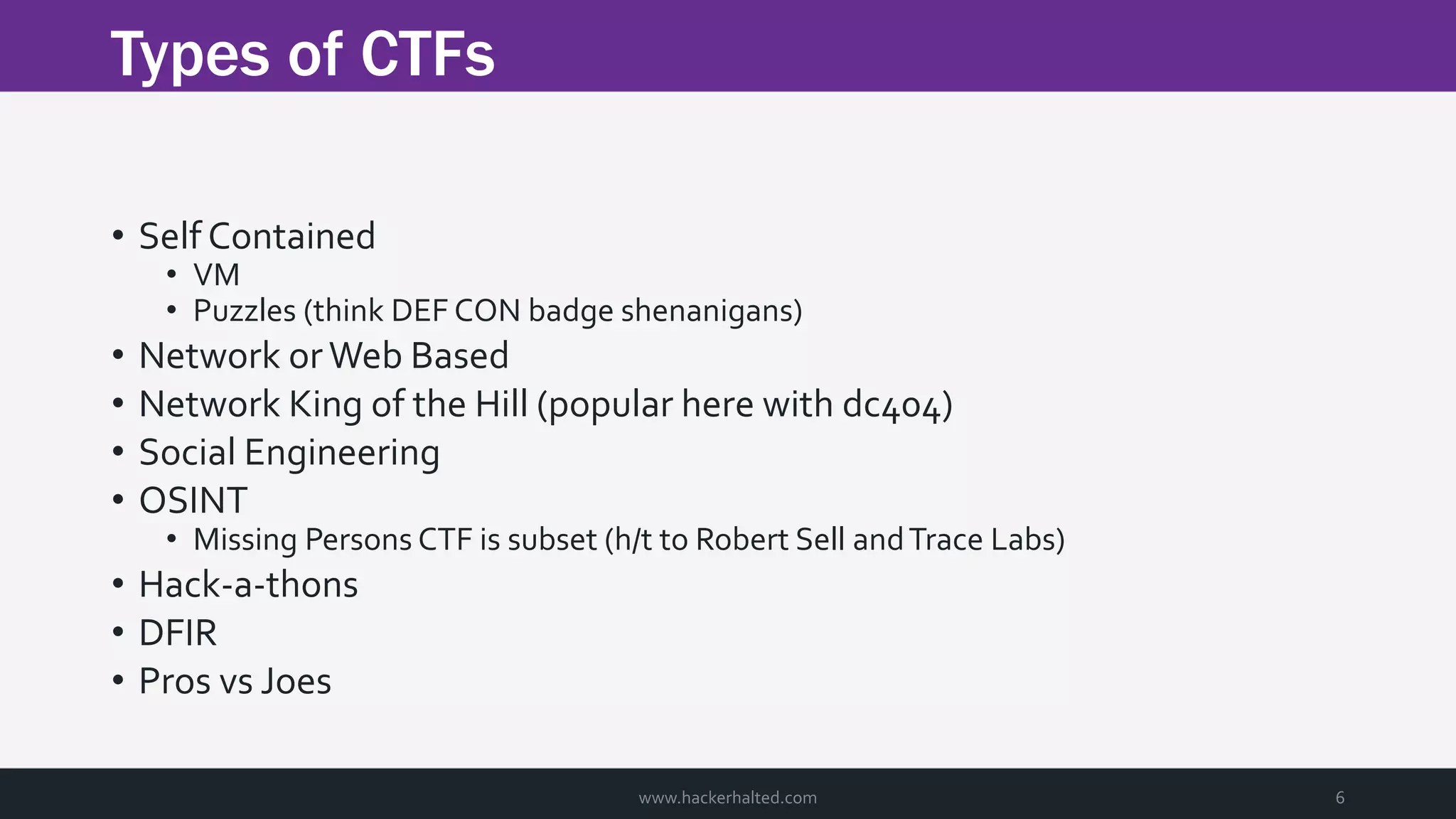
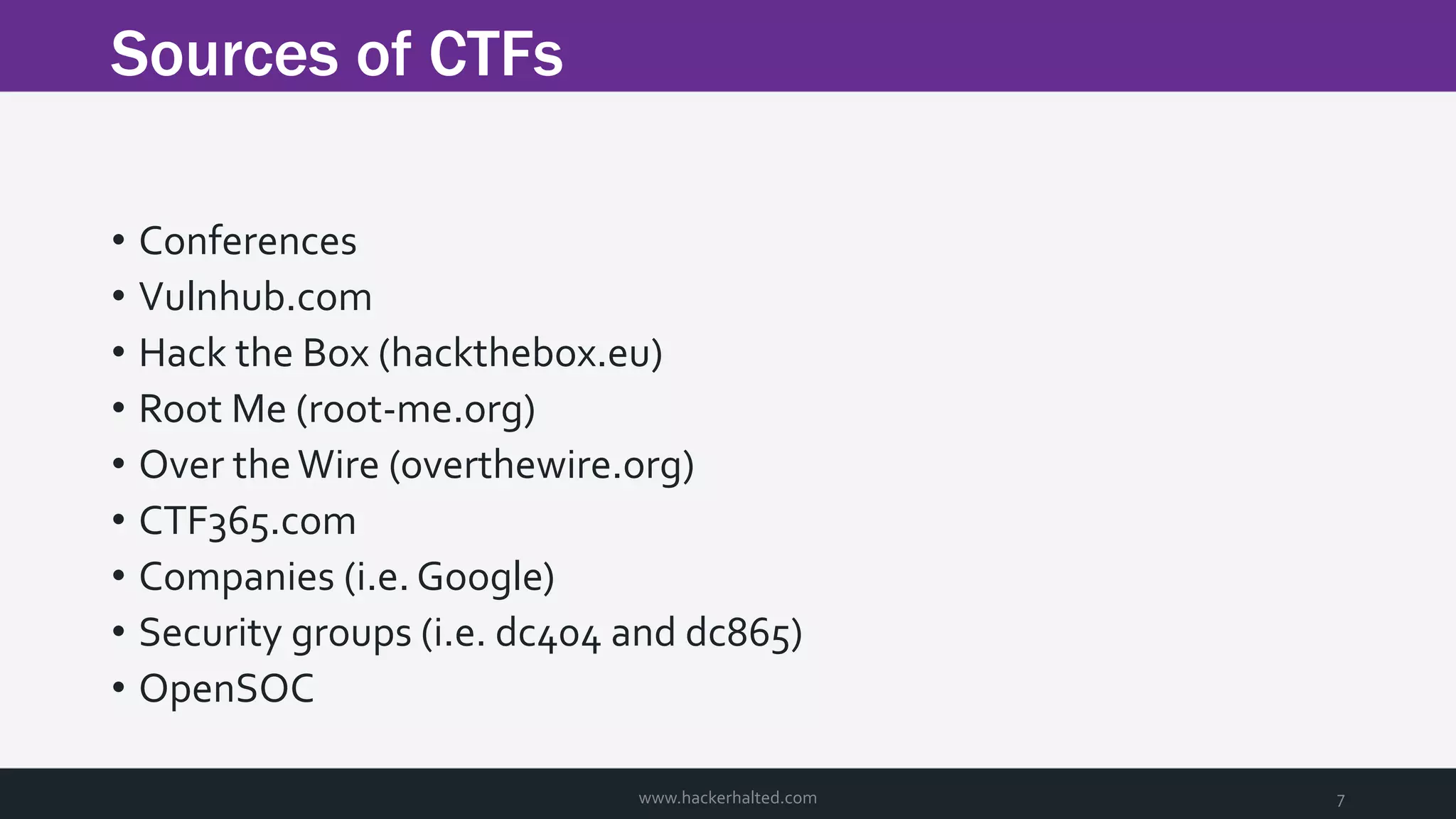
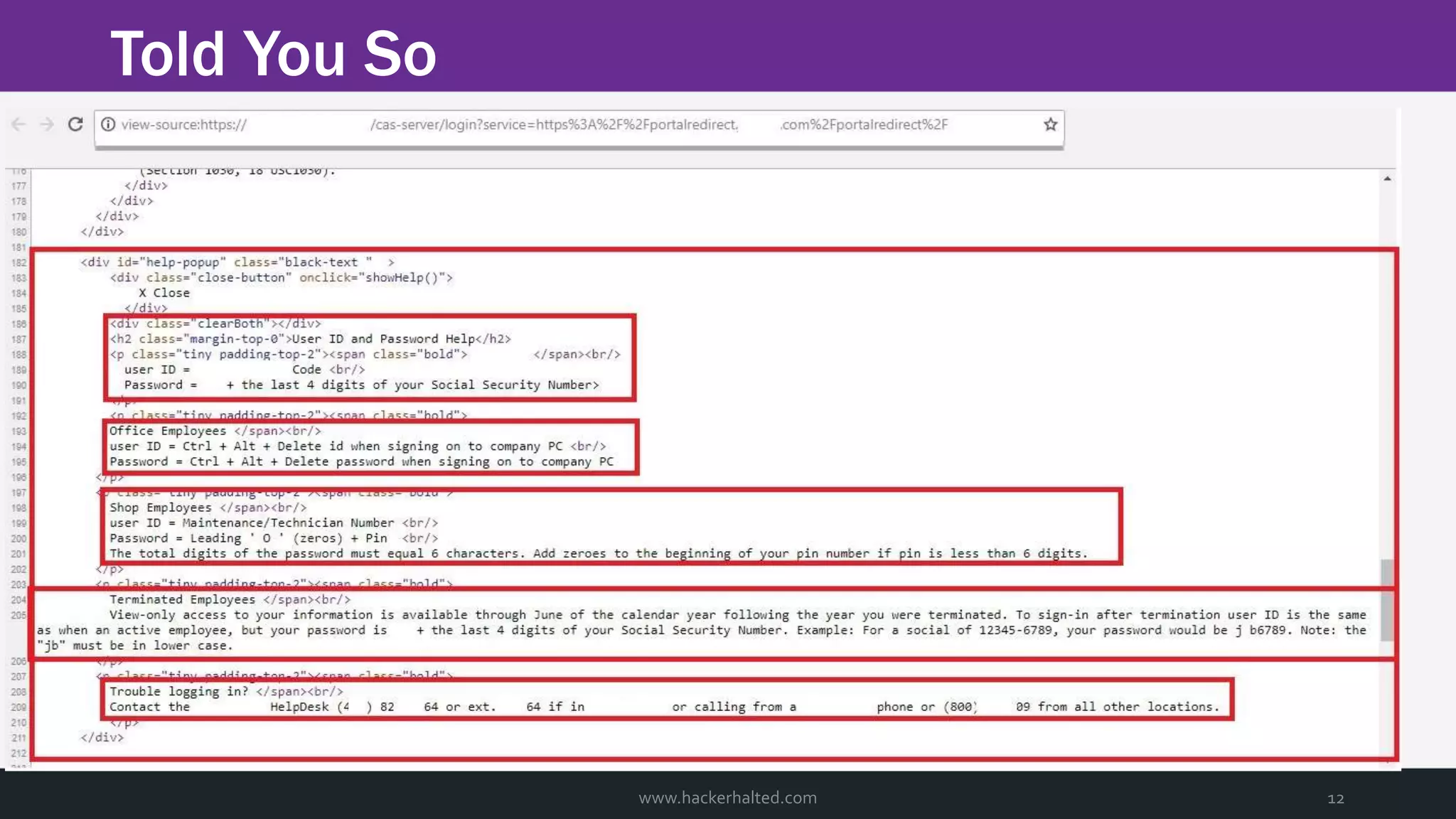
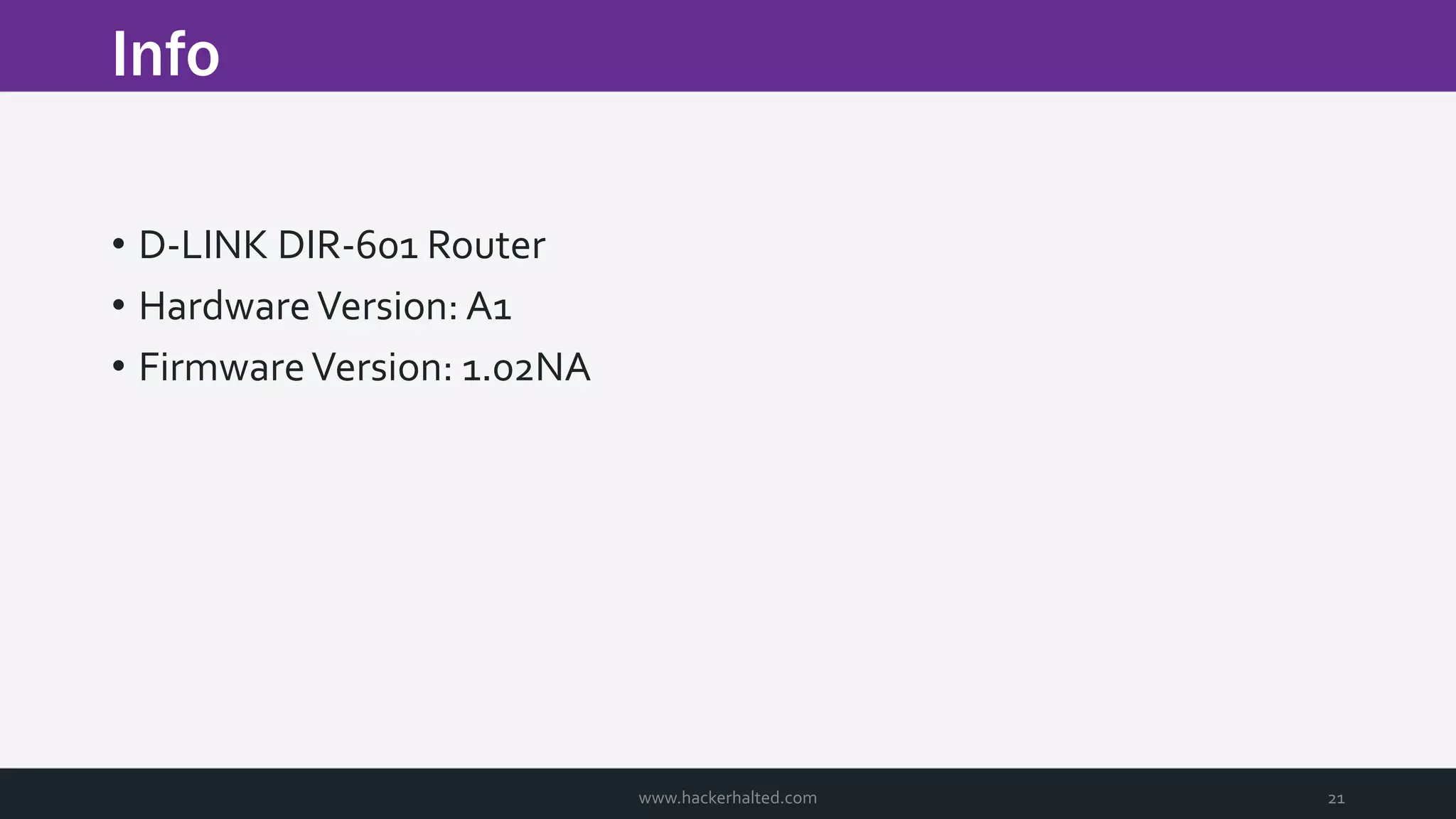
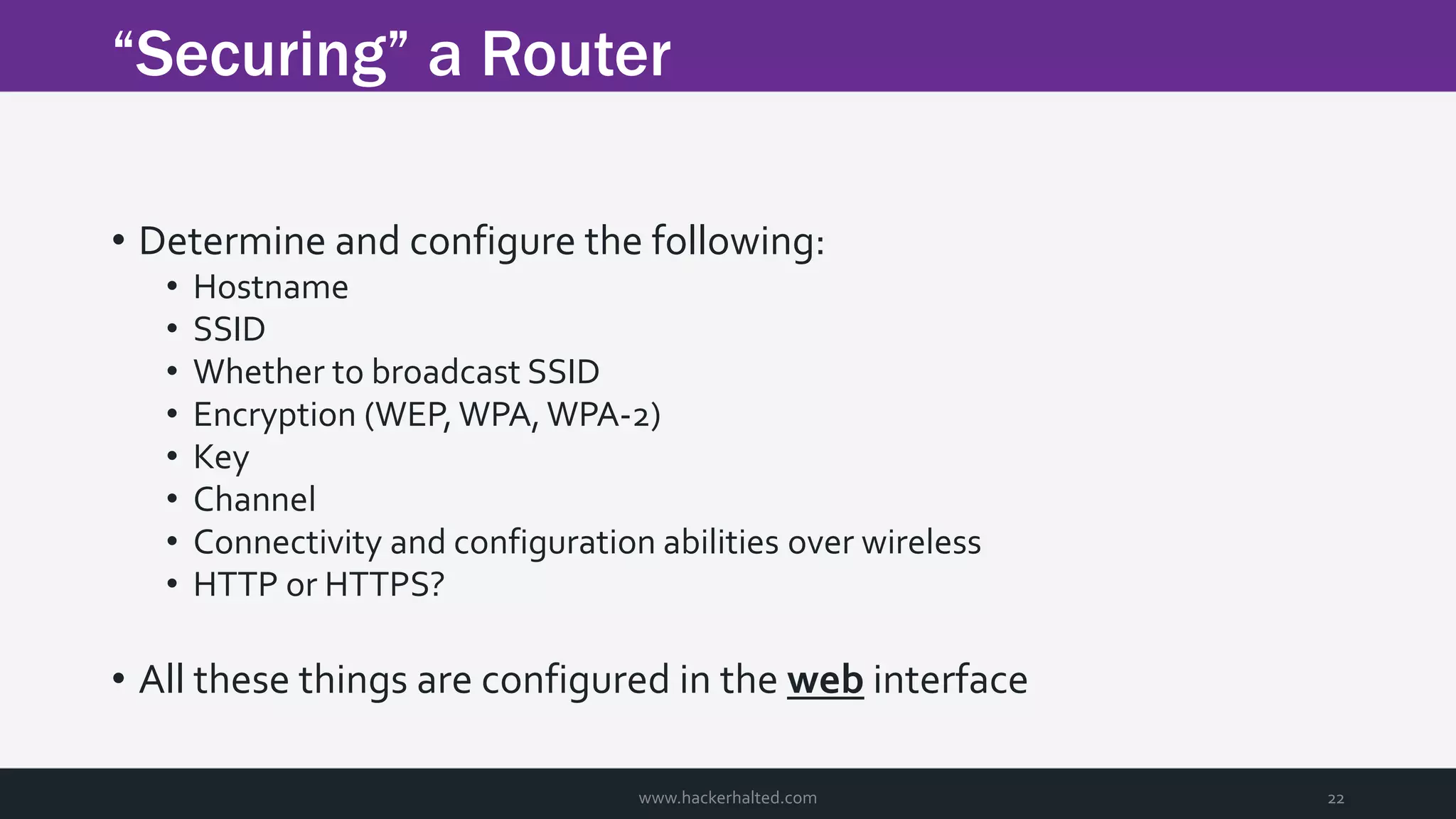
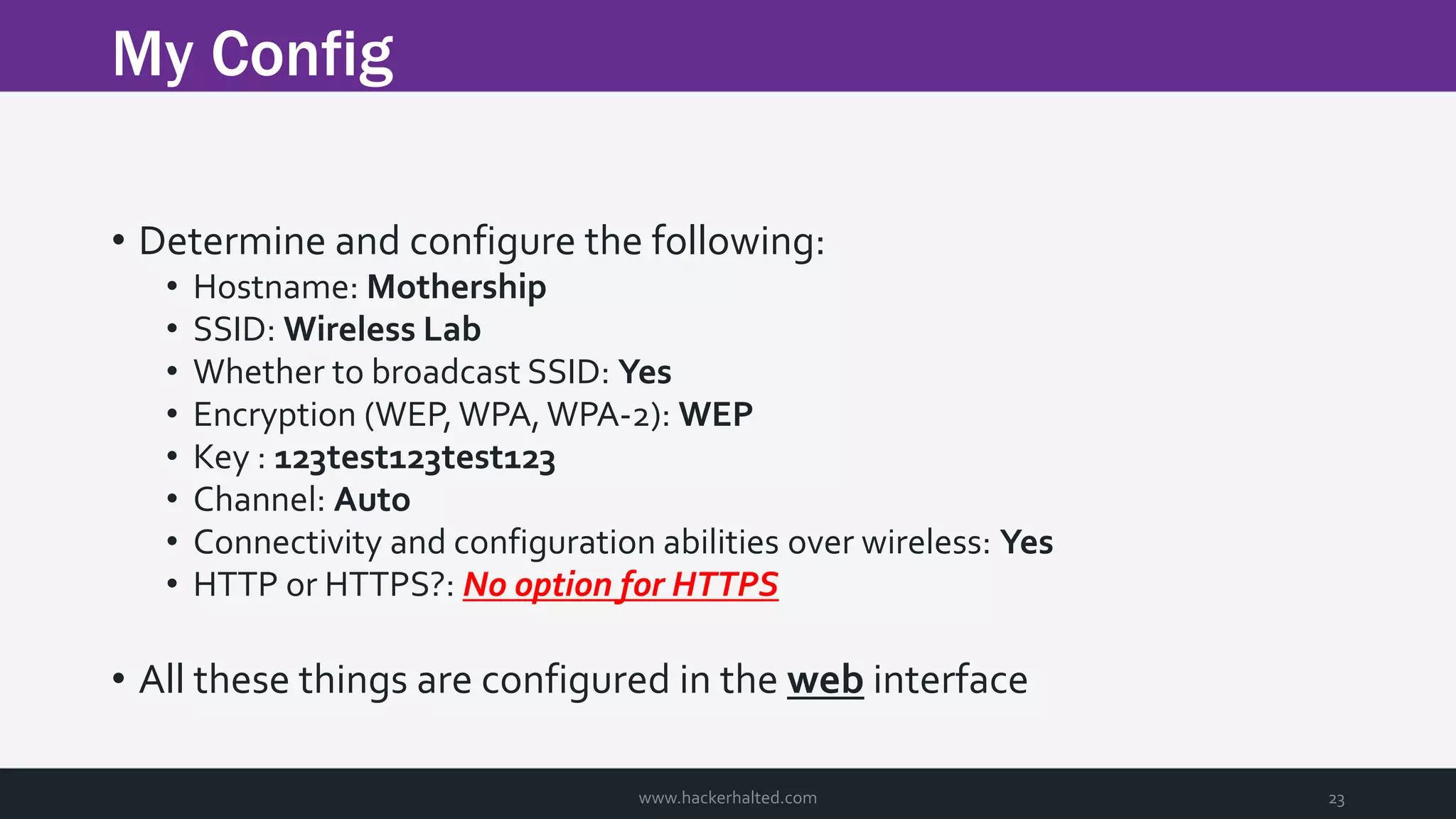
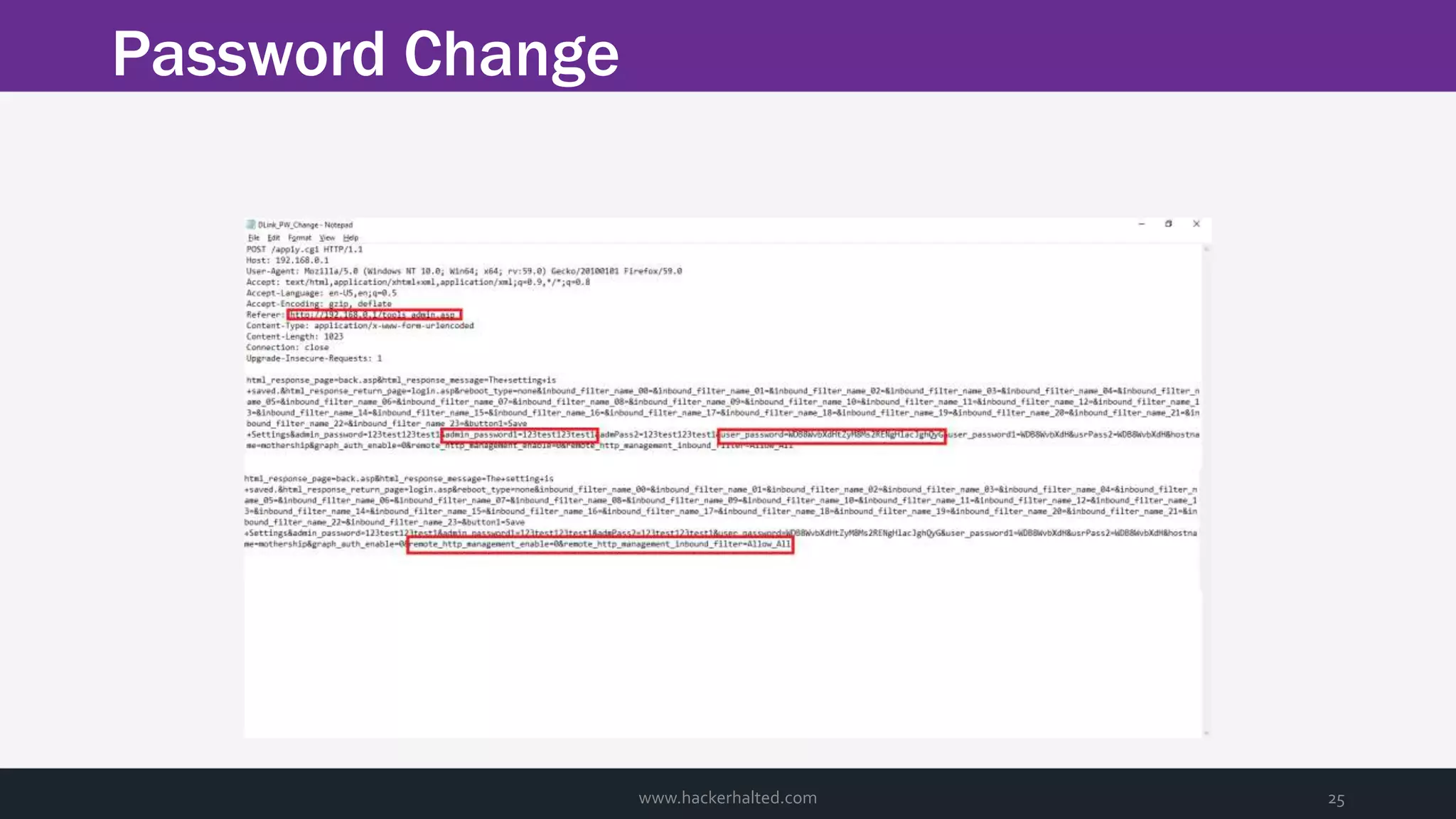
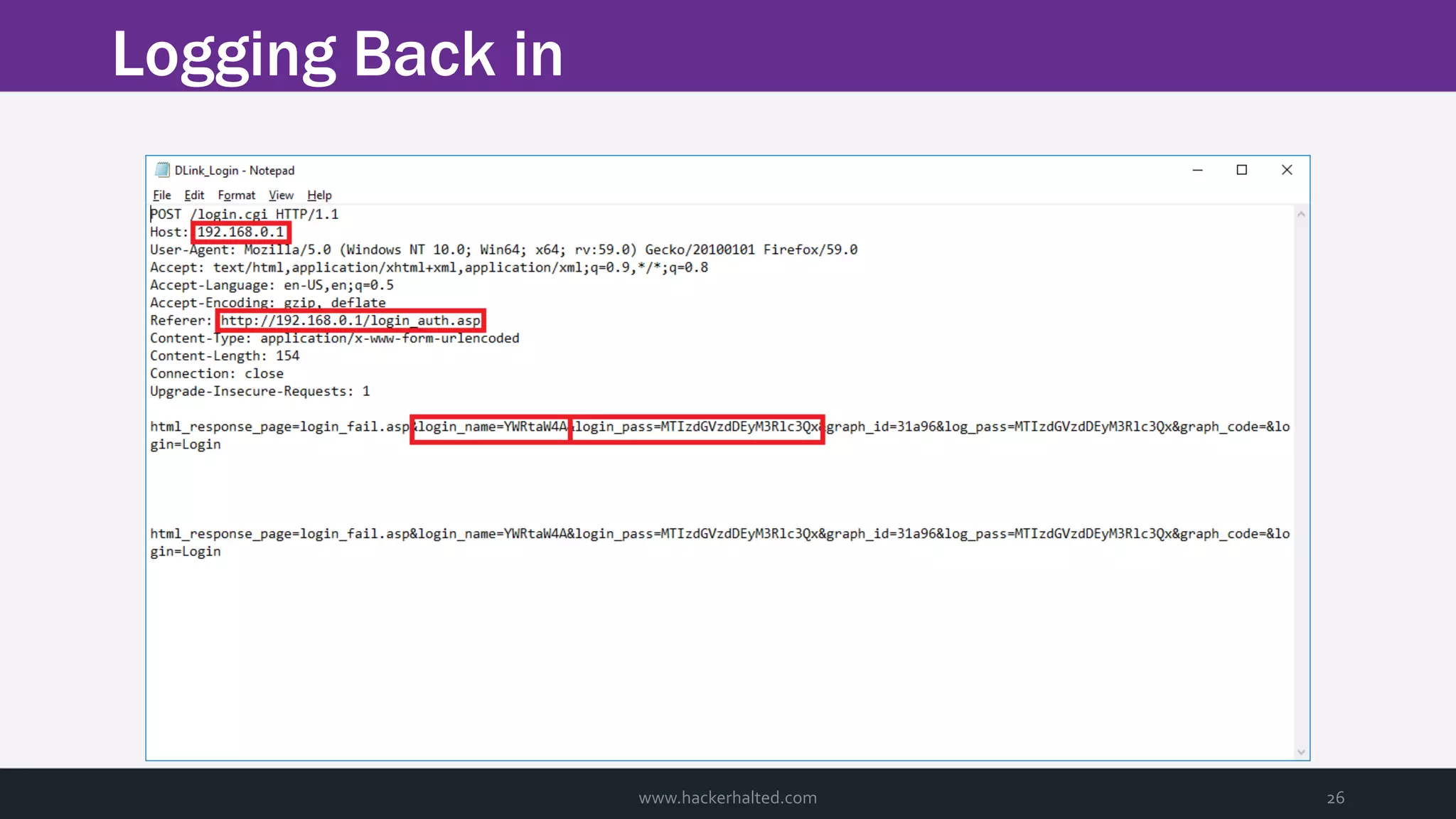
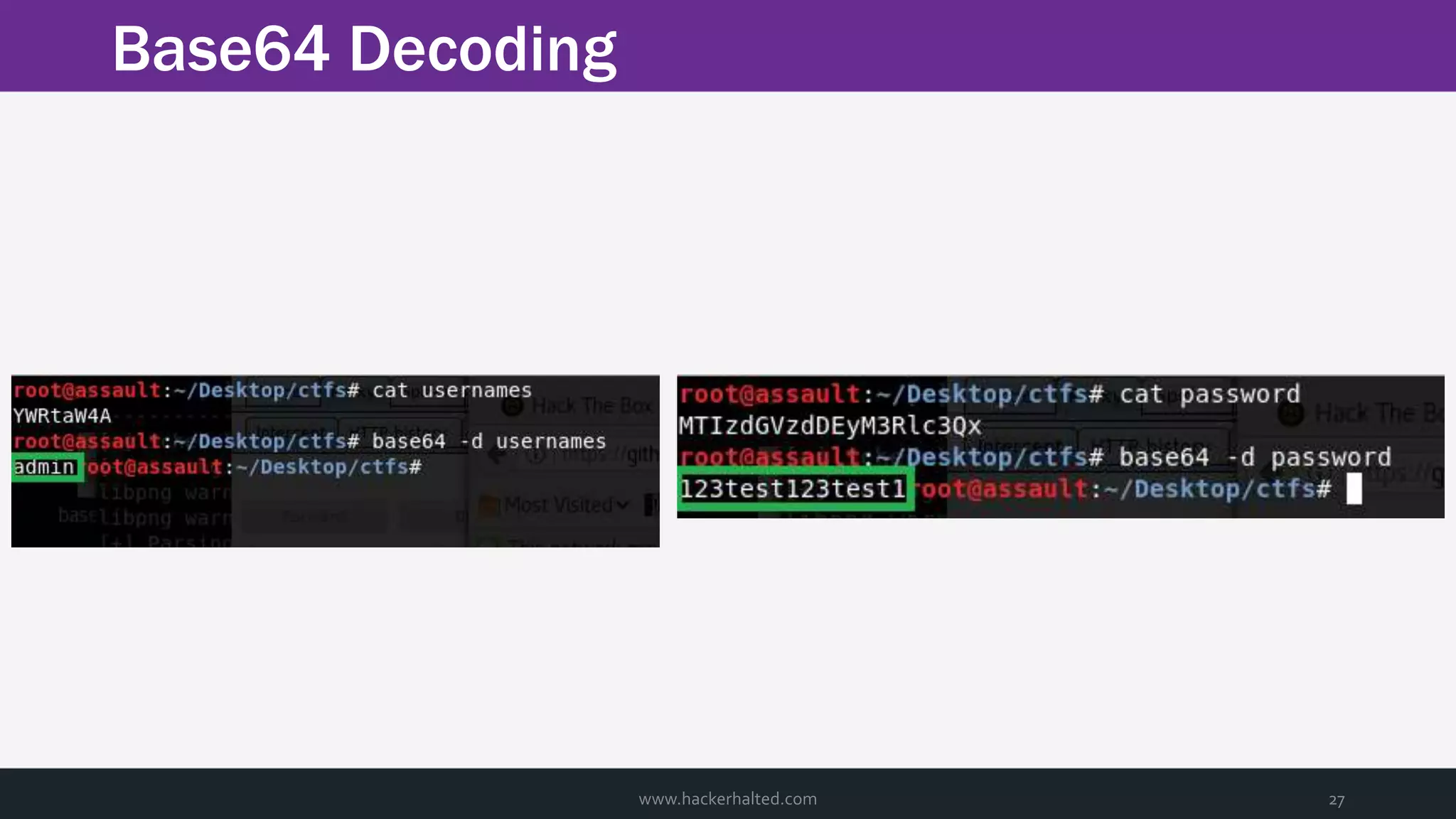
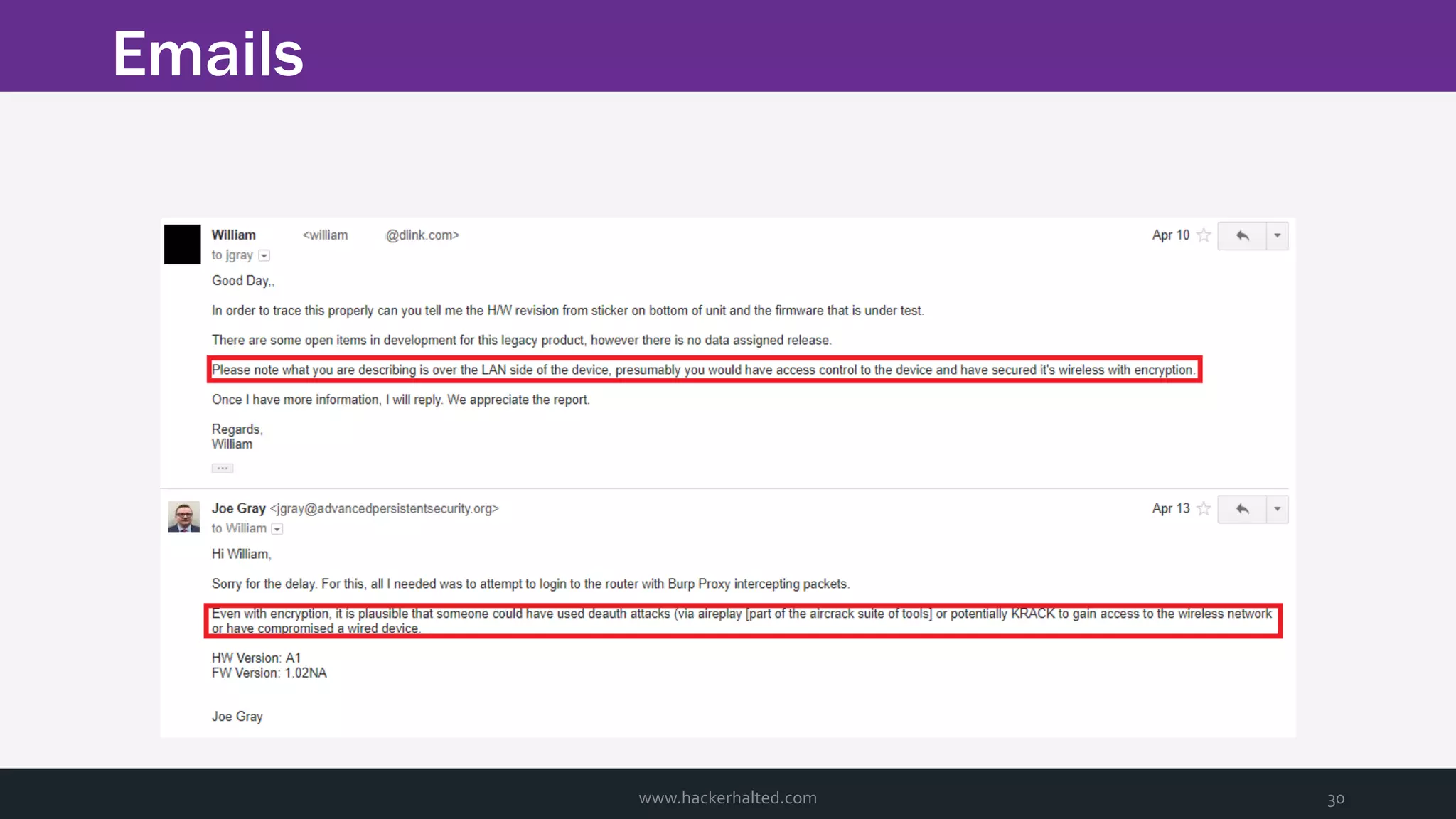
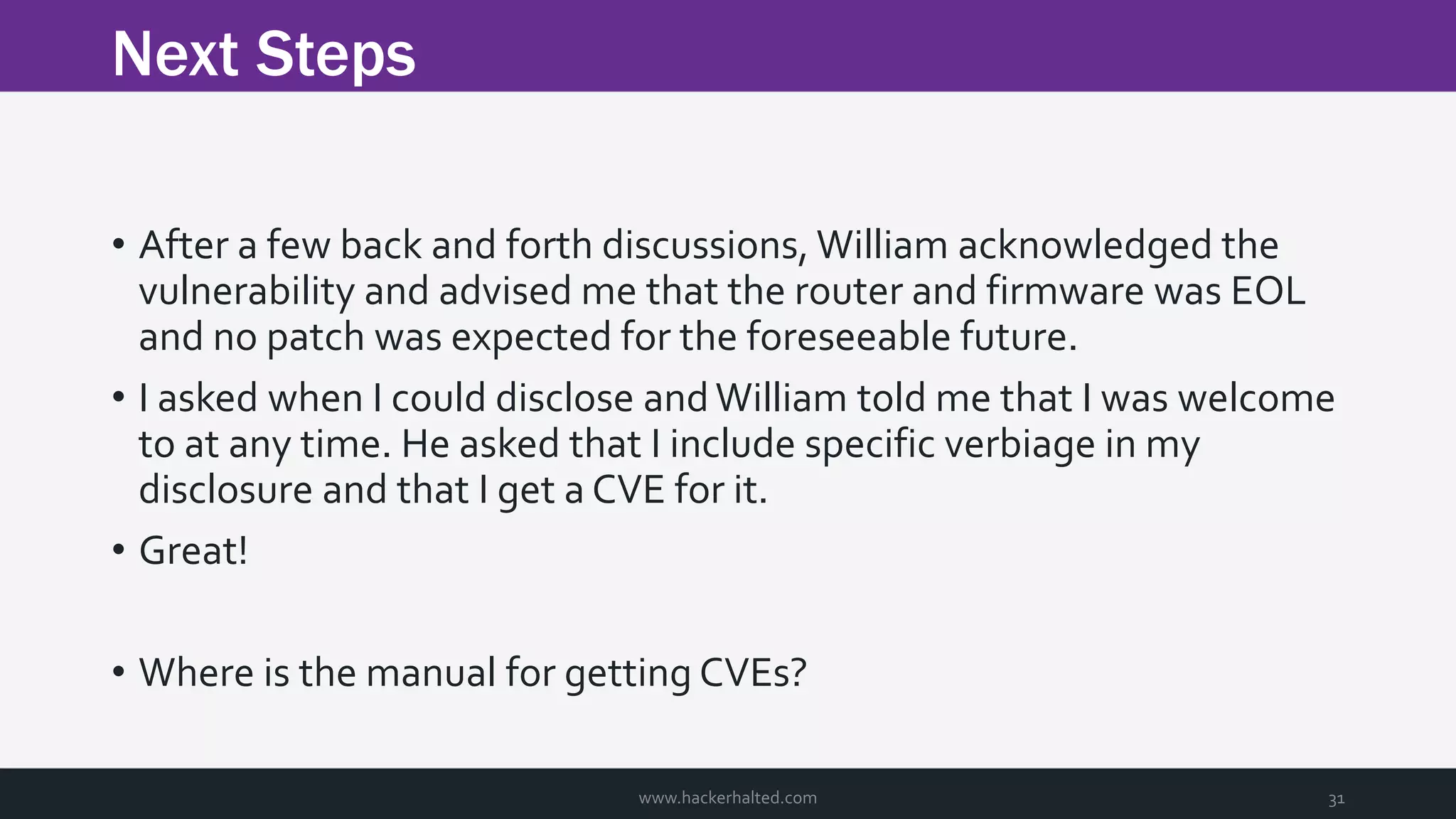
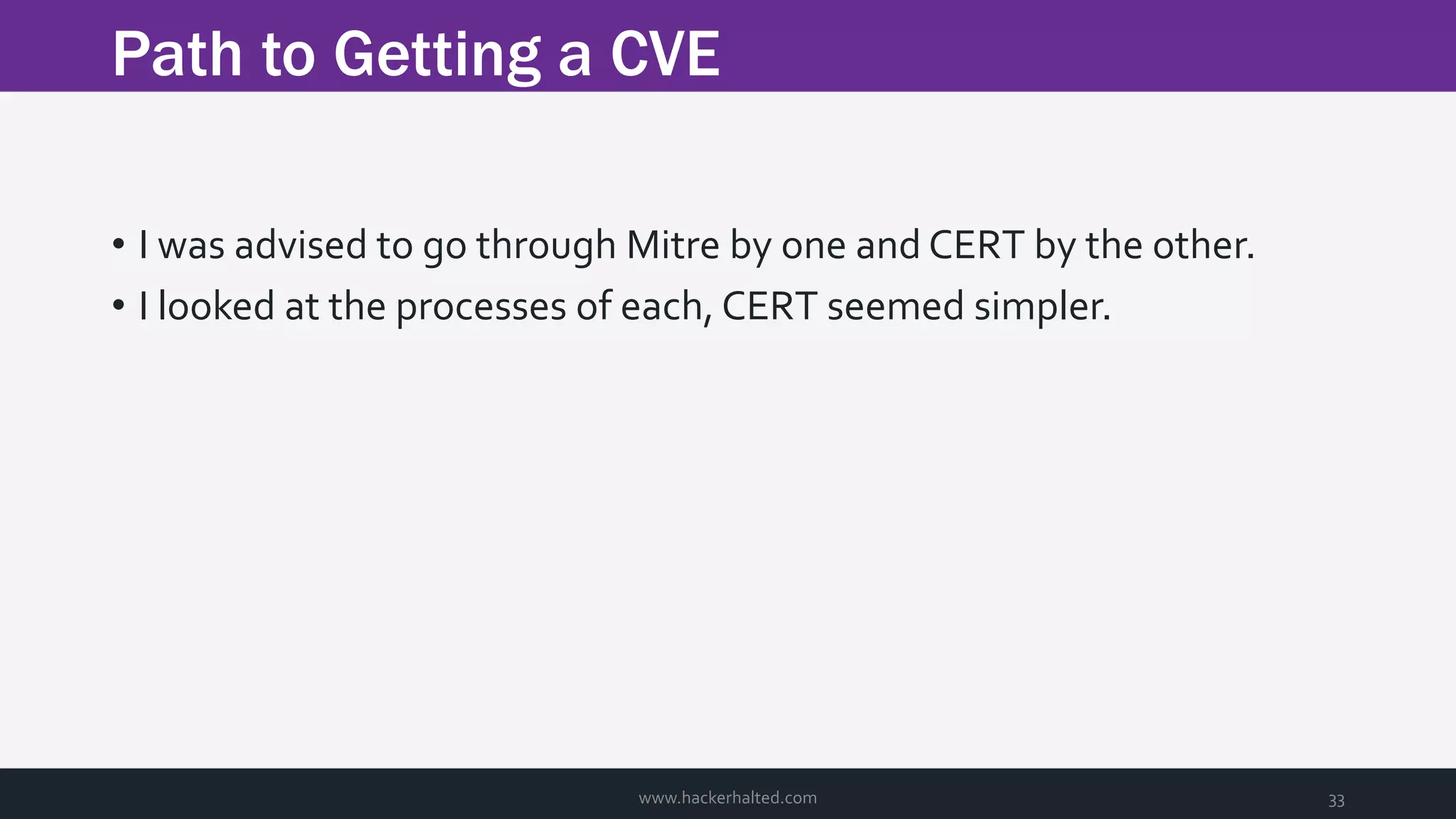
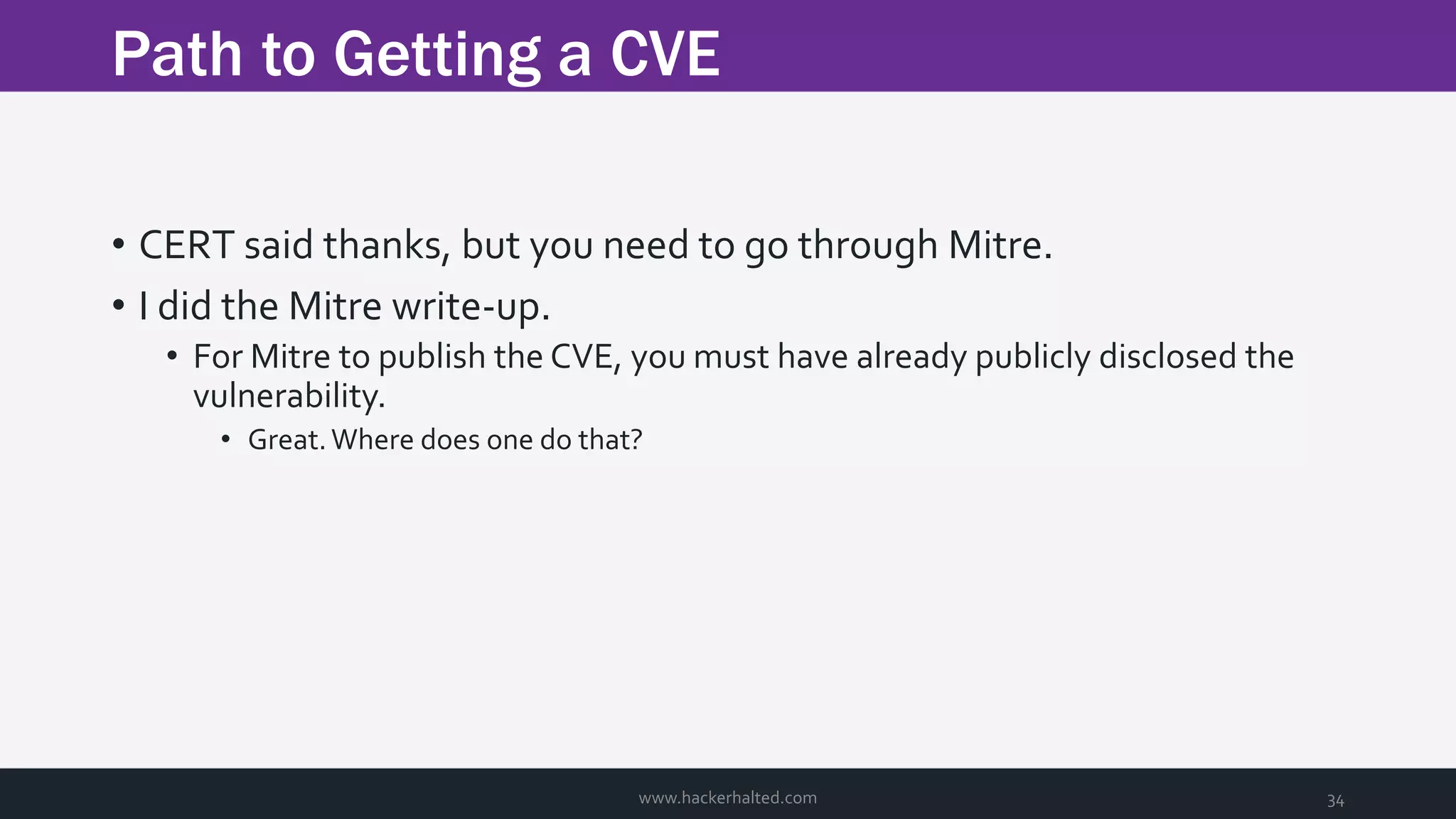
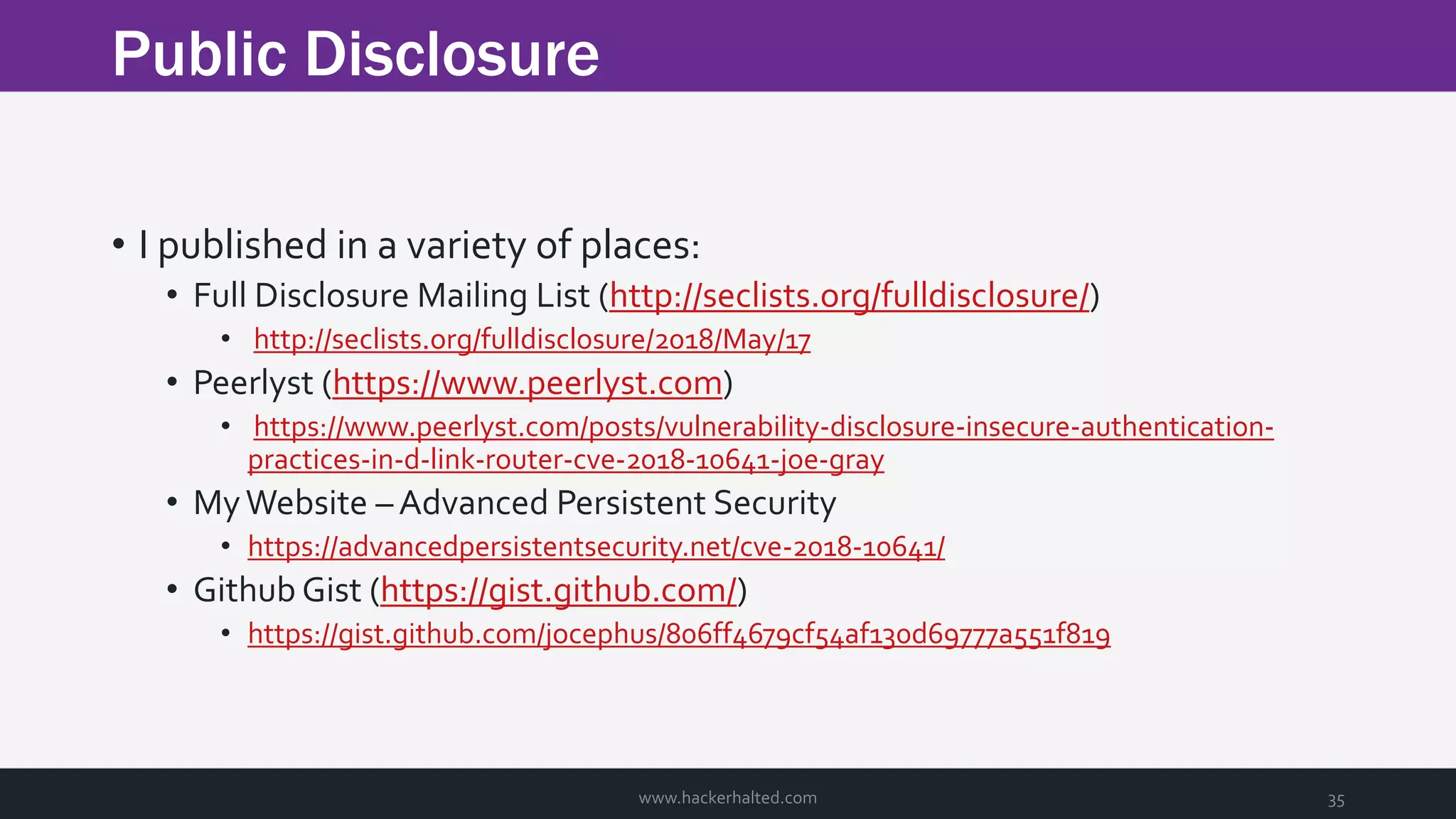
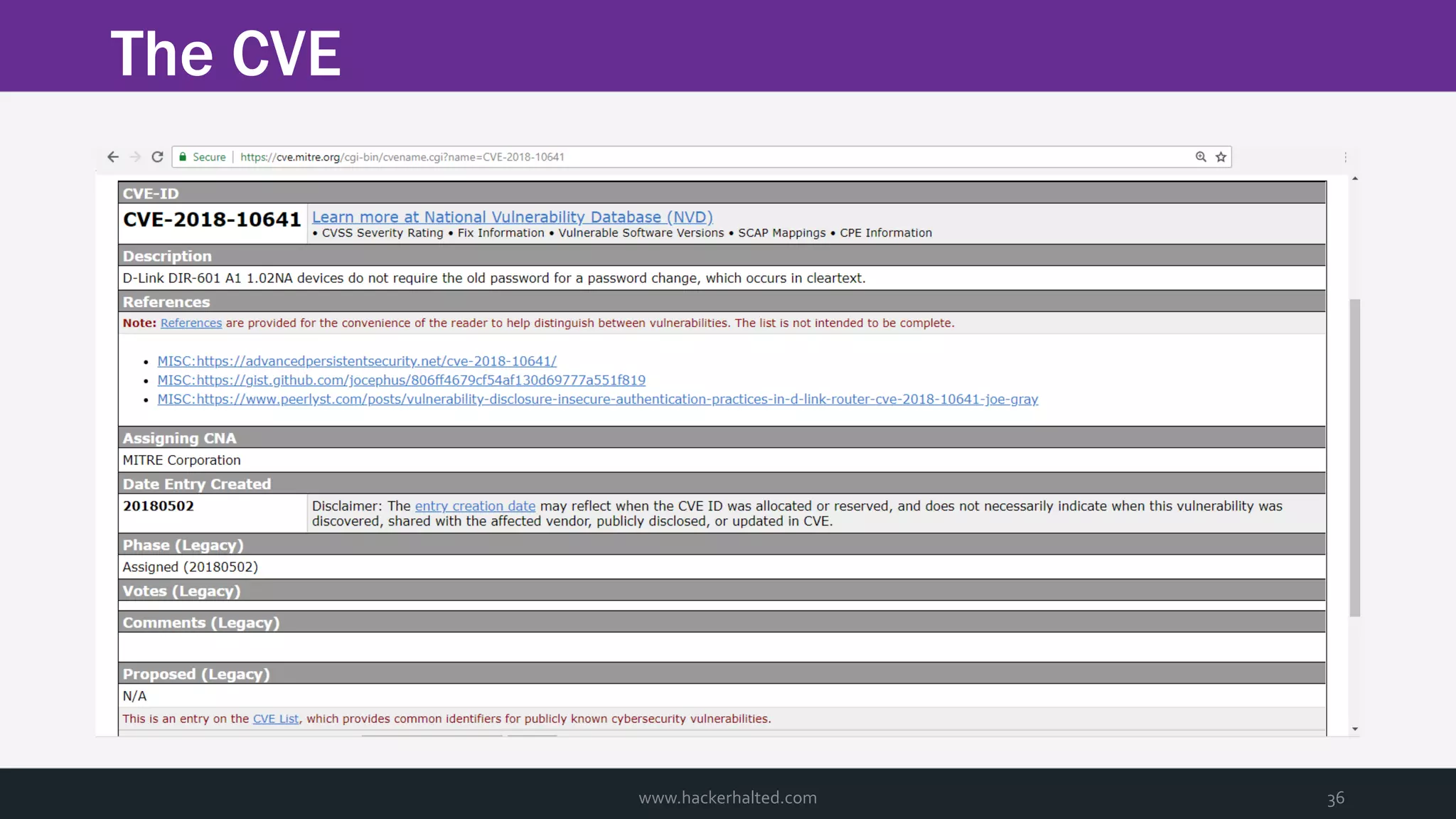
The document discusses the transition from Capture The Flags (CTFs) to Common Vulnerabilities and Exposures (CVEs), detailing various CTF types, sources, tools, and the realism of CTF challenges. It shares the author's journey of identifying a vulnerability in a D-Link router, engaging with the manufacturer, and navigating the CVE disclosure process. Key insights include the importance of community support in vulnerability disclosure and the value of hands-on experience in security training.