






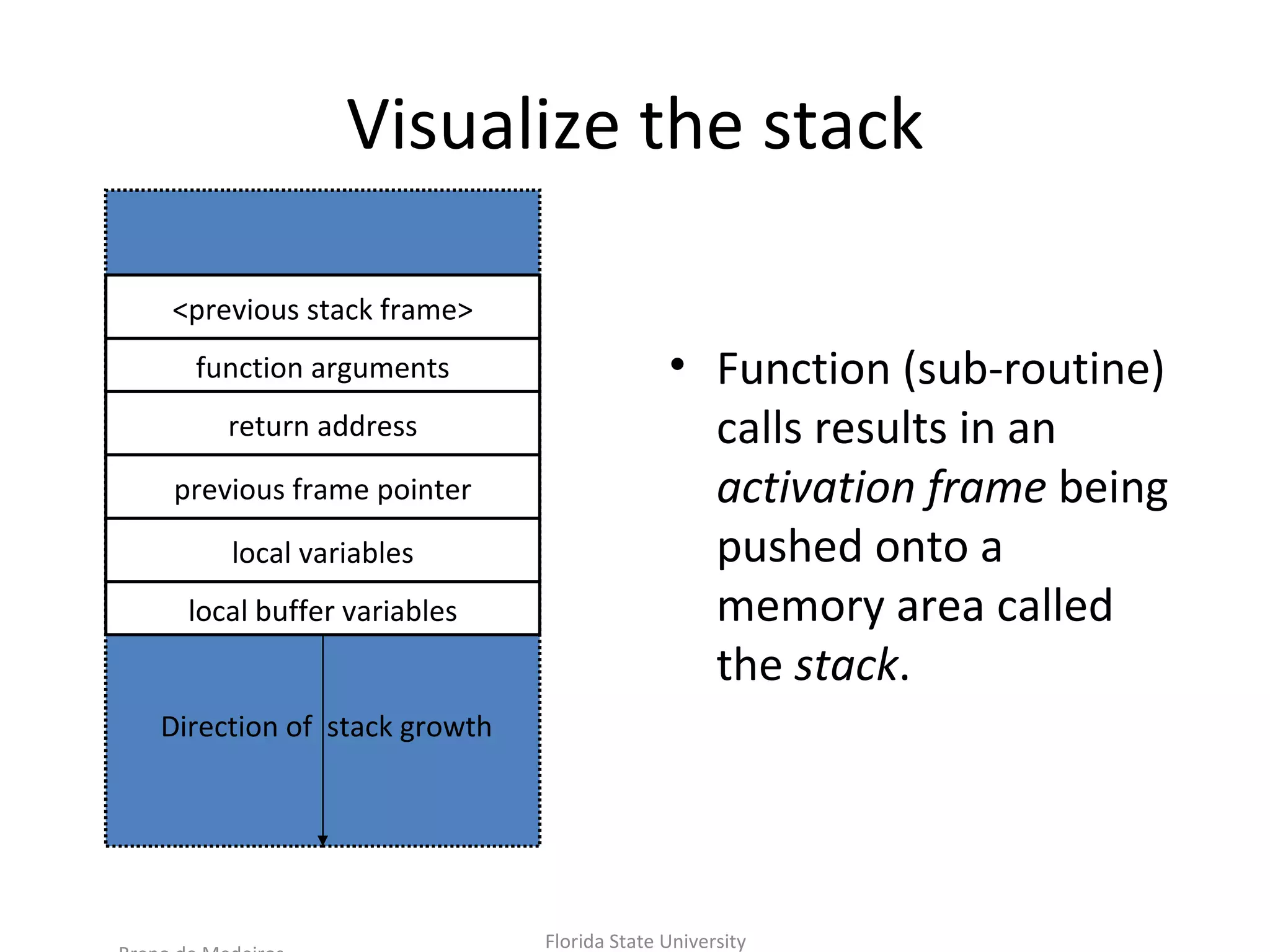
![Time to visualize the exploit void get_input() { char buf[1024]; gets(buf); } void main(int argc, char*argv[]){ get_input(); } Vulnerable to Buffer overflow because , gets() doesn’t check the size of the buffer causing it to overflow.According to the slide before, if we give 1024 + 8 bytes we overwrite saved return address which can be the address of our shellcode in memory to alter the execution path of our program.](https://image.slidesharecdn.com/exploitingstackoverflow101-111125002336-phpapp02/75/Exploiting-stack-overflow-101-9-2048.jpg)



This document provides an overview of exploiting a stack overflow vulnerability in EasyRmtoMp3 player software. It discusses the stack and function calls in assembly, and how a buffer overflow can be used to overwrite the return address and redirect program execution to injected shellcode. The agenda includes setting up the environment in Immunity Debugger and Metasploit, explaining the theory behind stack overflows, visualizing how it works, and demonstrating an exploit against the vulnerable software.








![Time to visualize the exploit void get_input() { char buf[1024]; gets(buf); } void main(int argc, char*argv[]){ get_input(); } Vulnerable to Buffer overflow because , gets() doesn’t check the size of the buffer causing it to overflow.According to the slide before, if we give 1024 + 8 bytes we overwrite saved return address which can be the address of our shellcode in memory to alter the execution path of our program.](https://image.slidesharecdn.com/exploitingstackoverflow101-111125002336-phpapp02/75/Exploiting-stack-overflow-101-9-2048.jpg)


