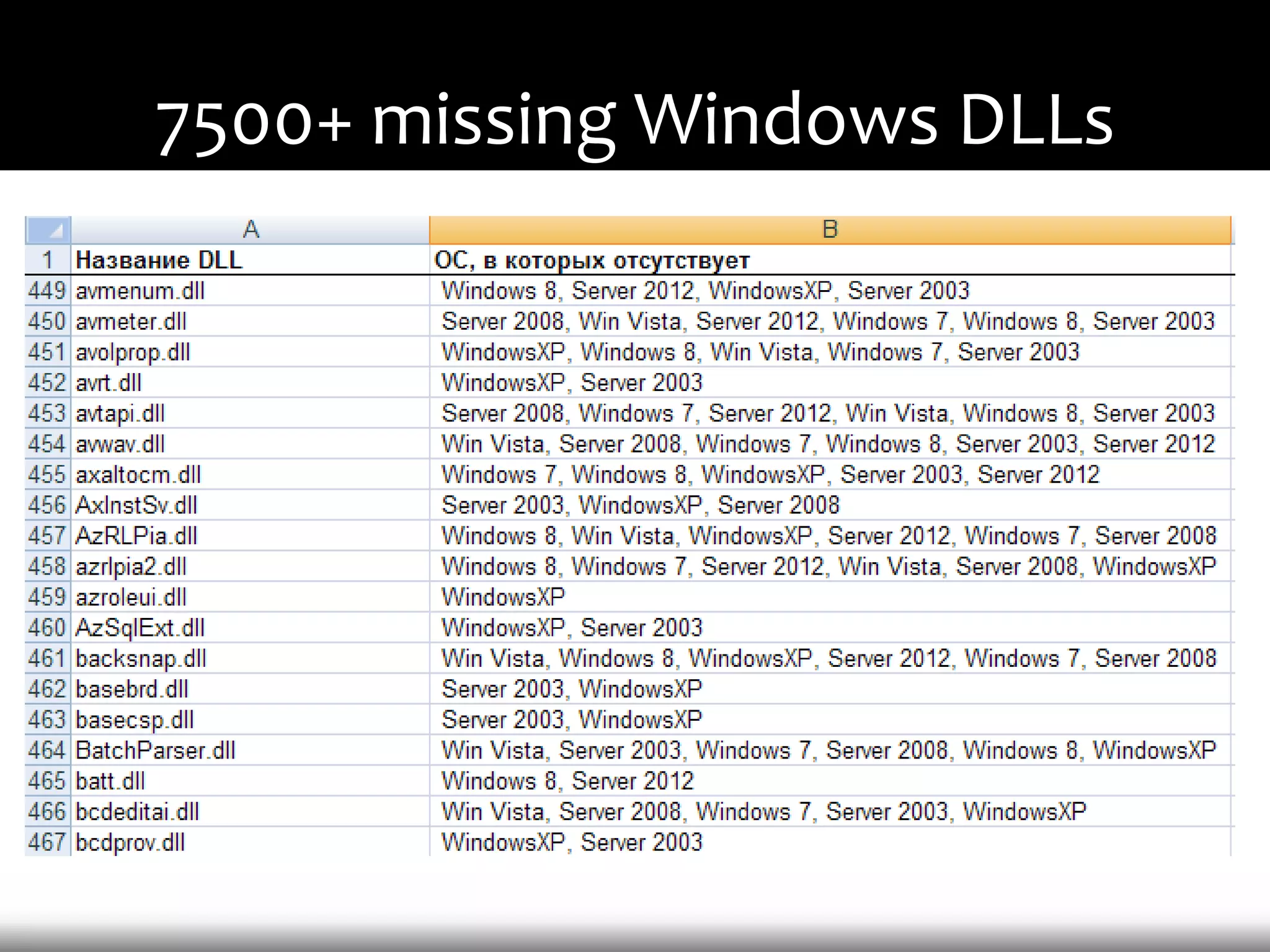
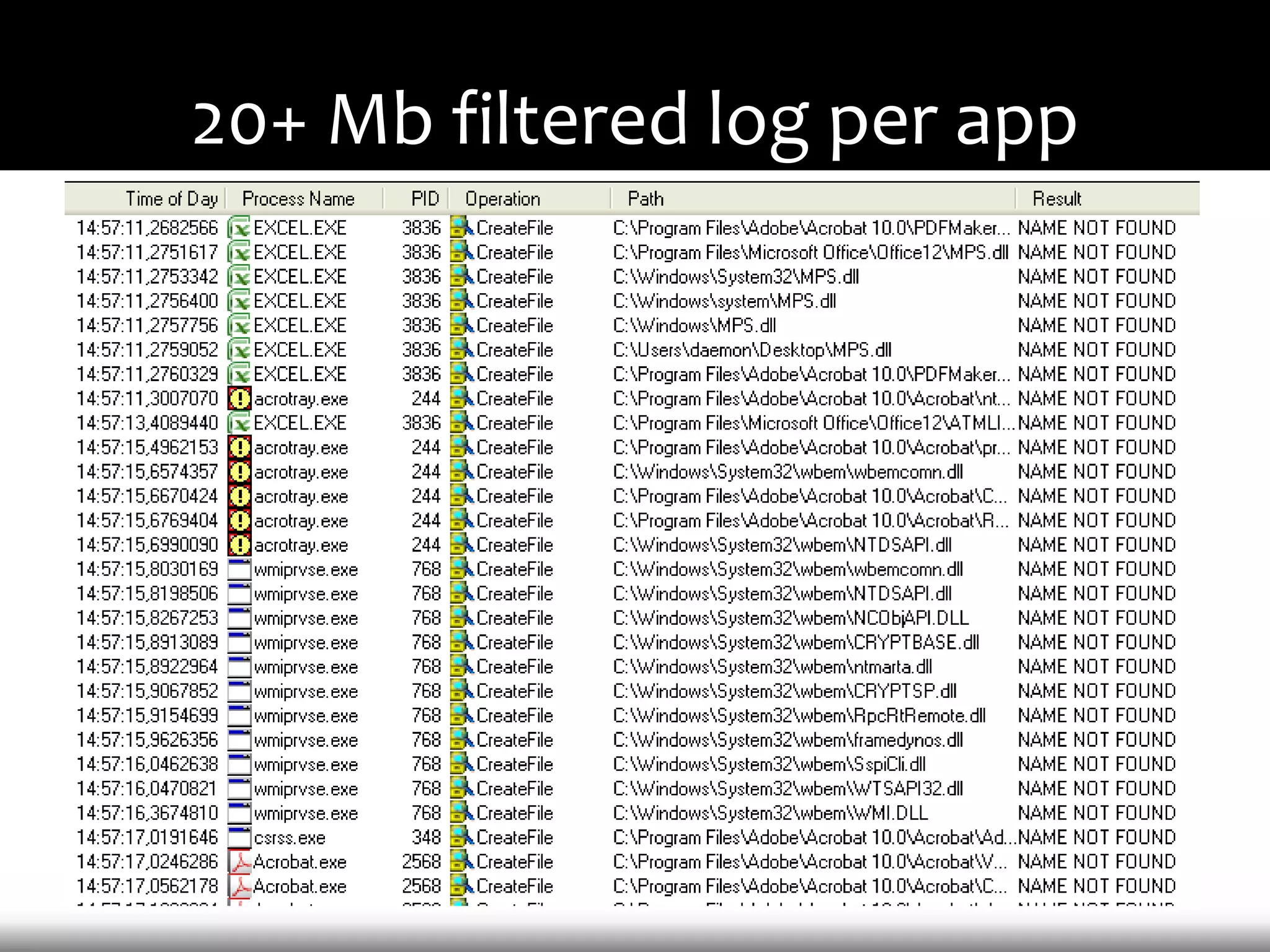
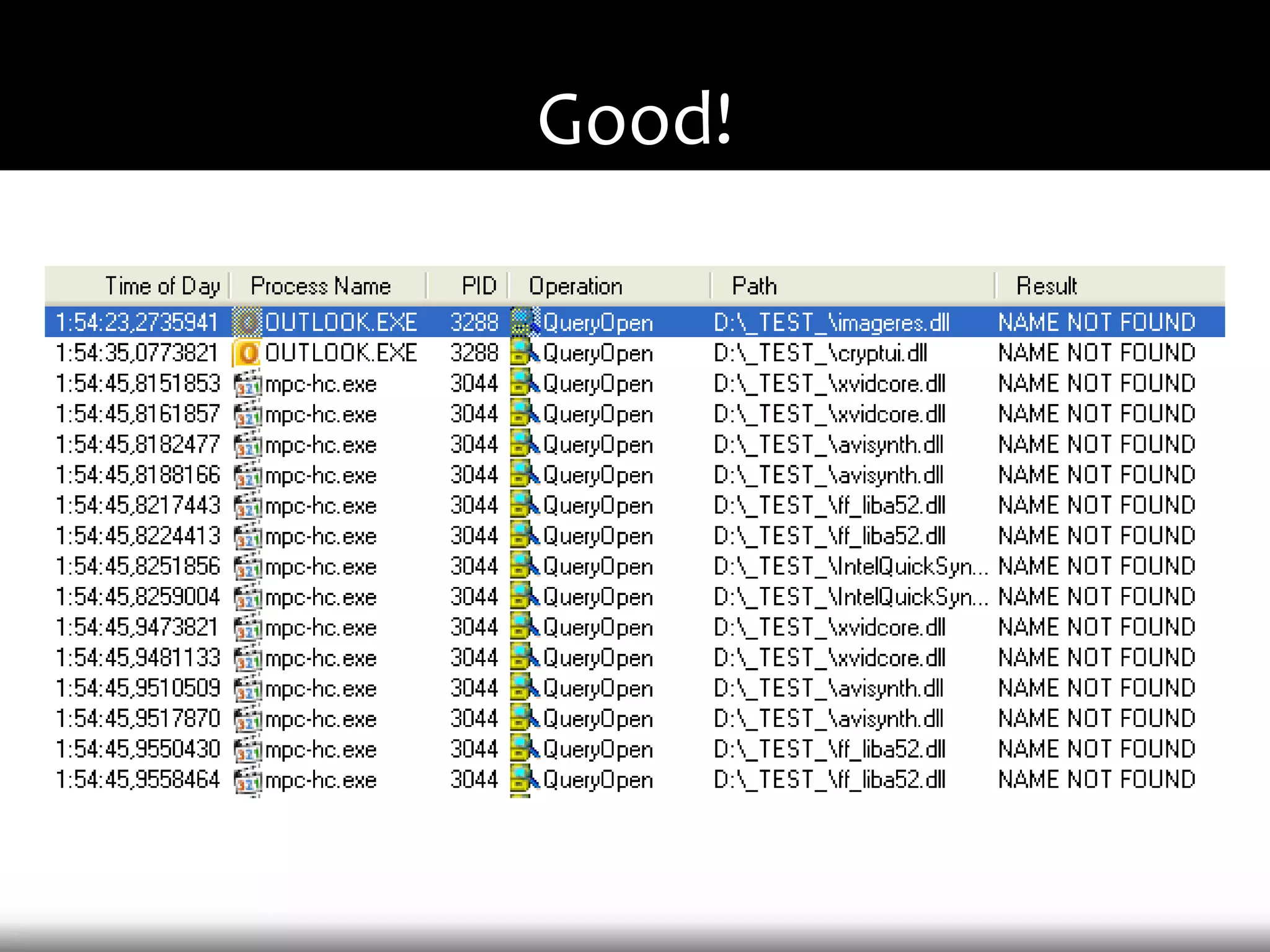
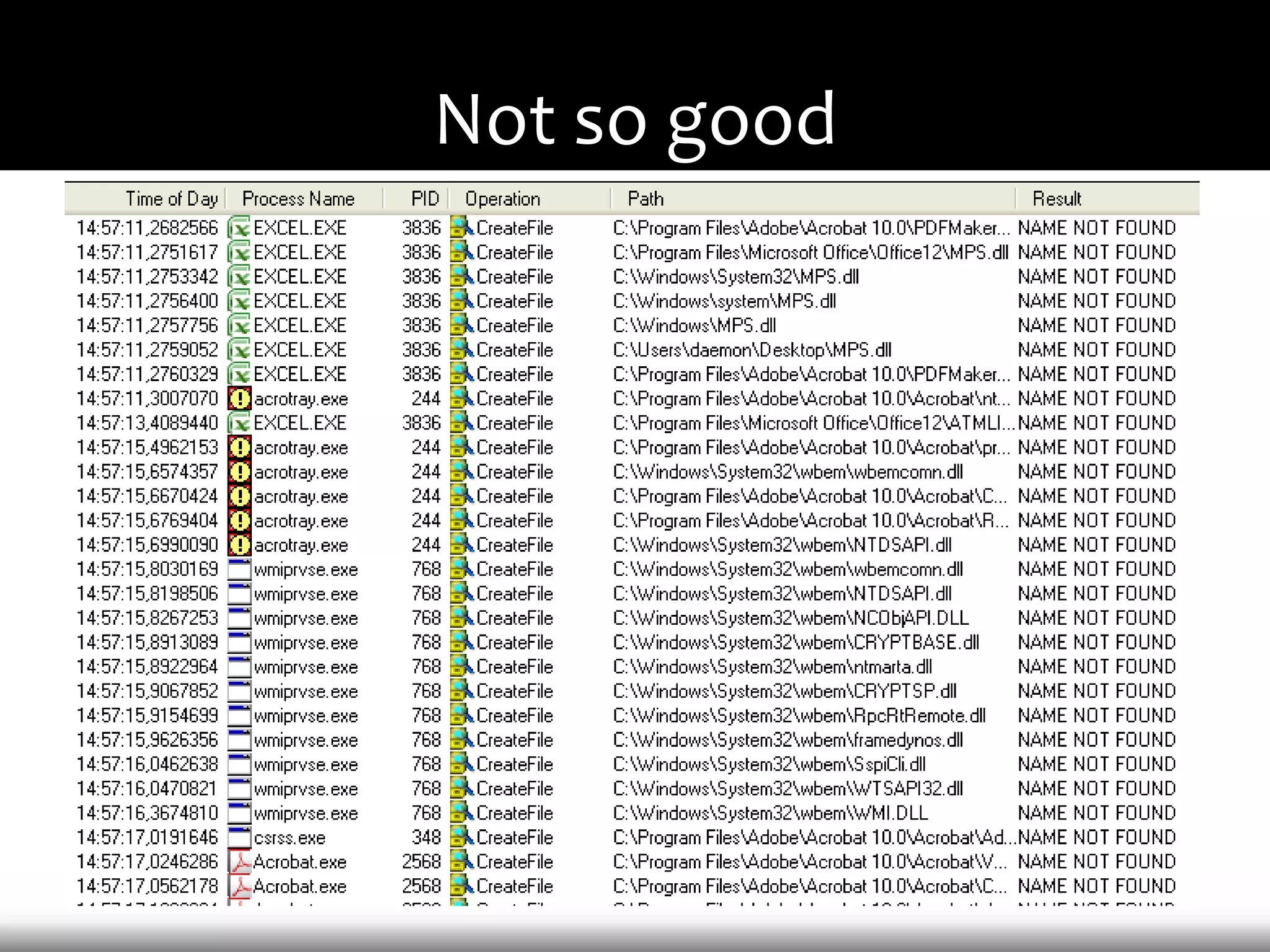
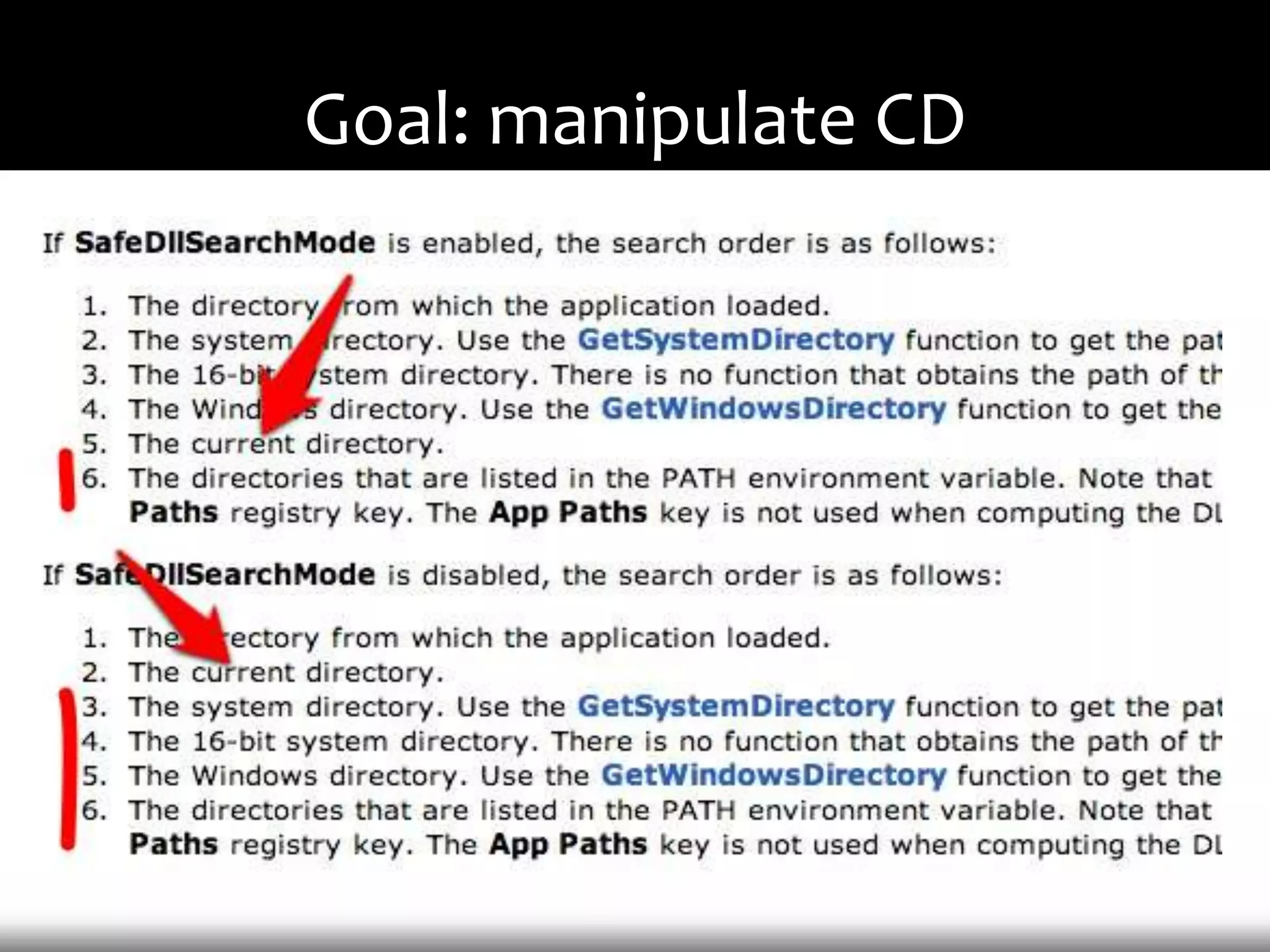
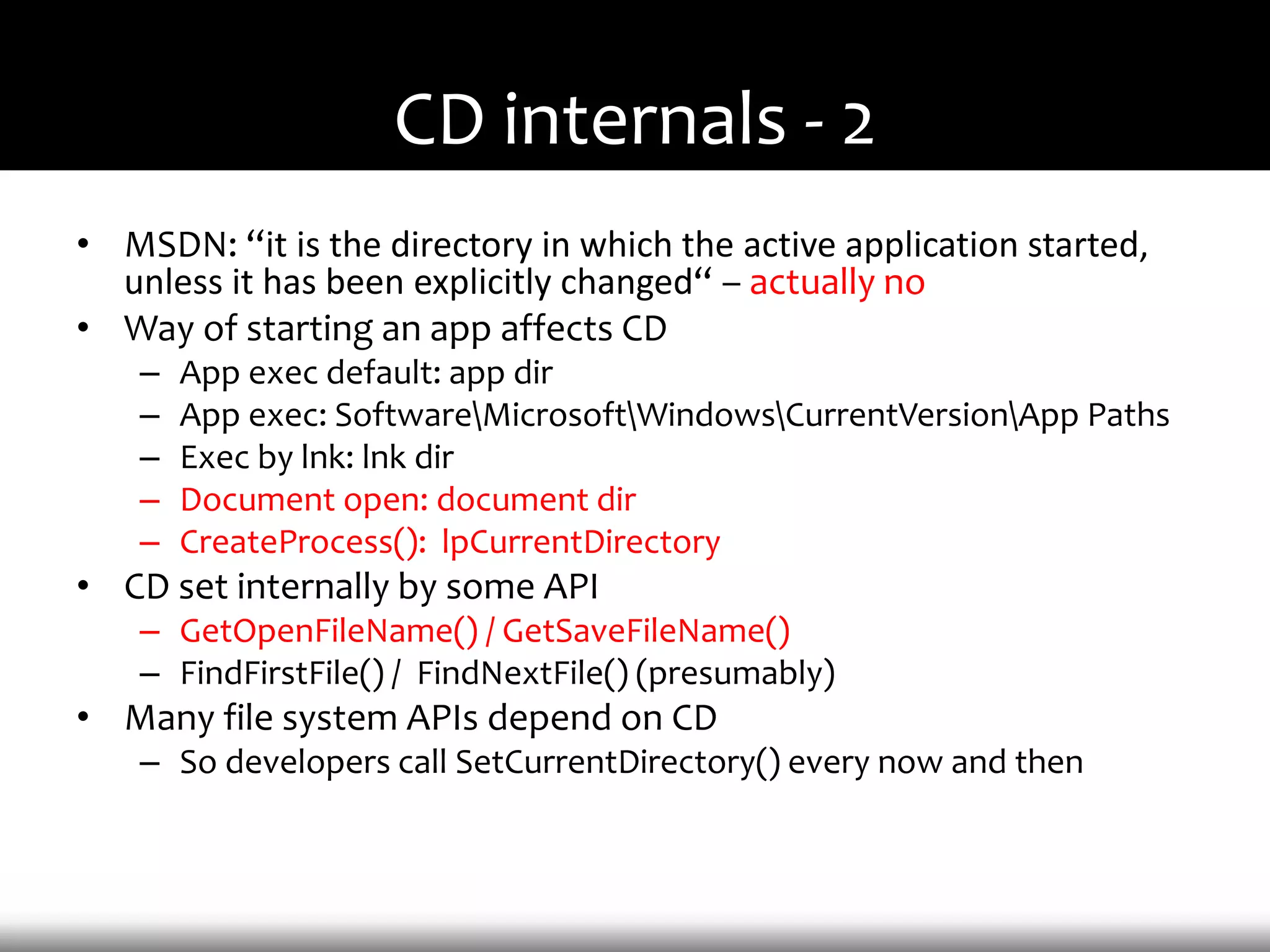
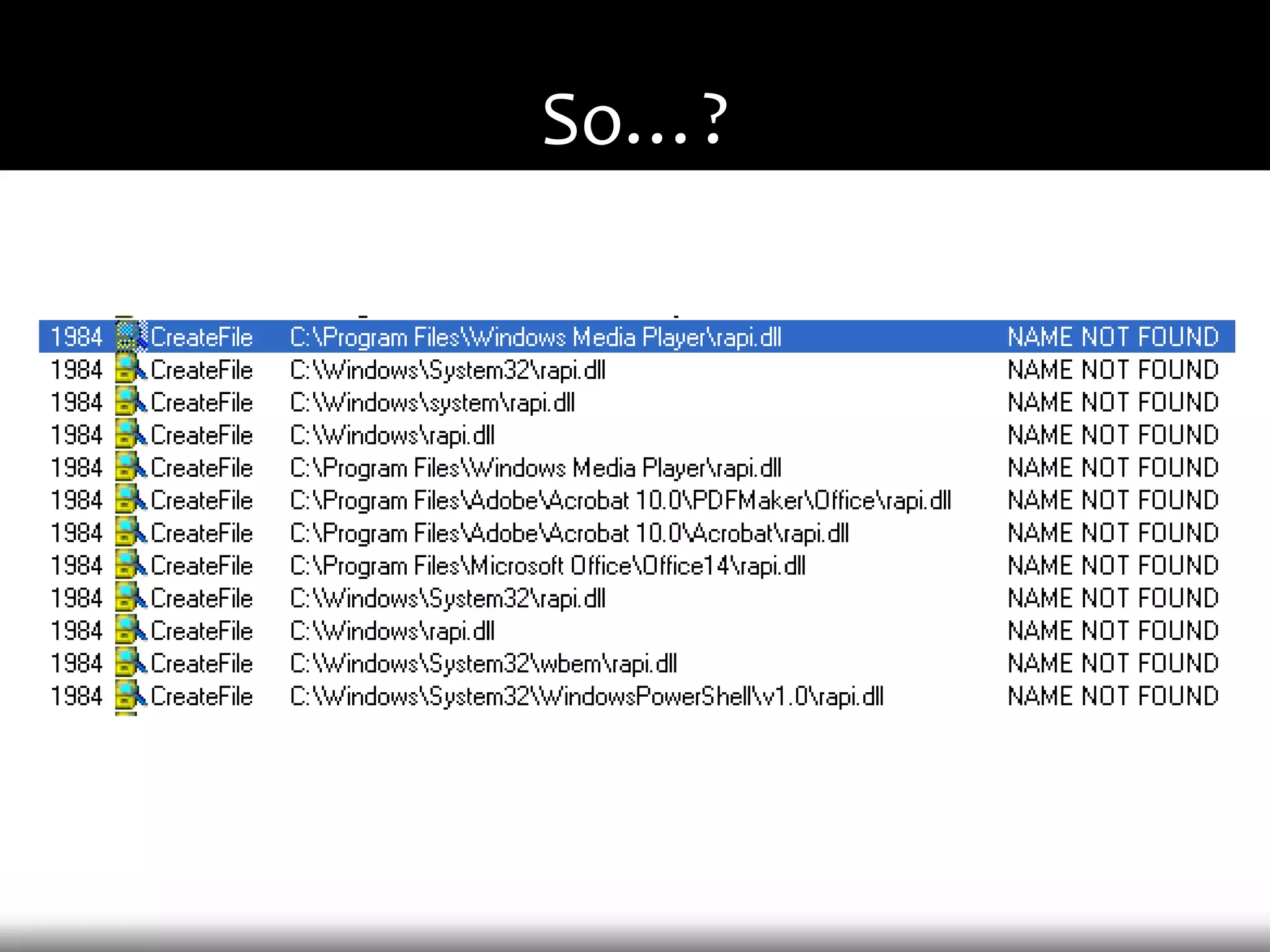
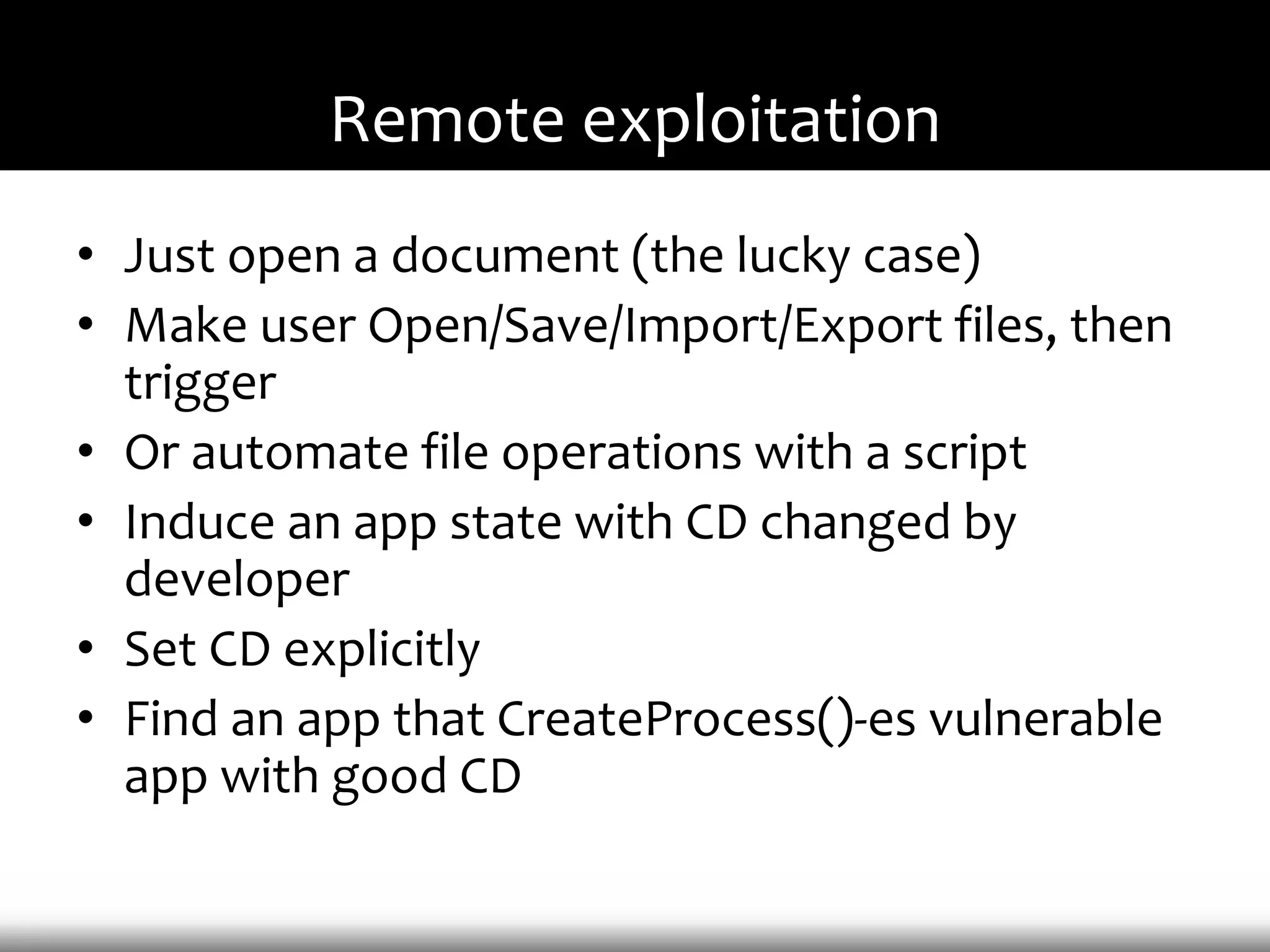
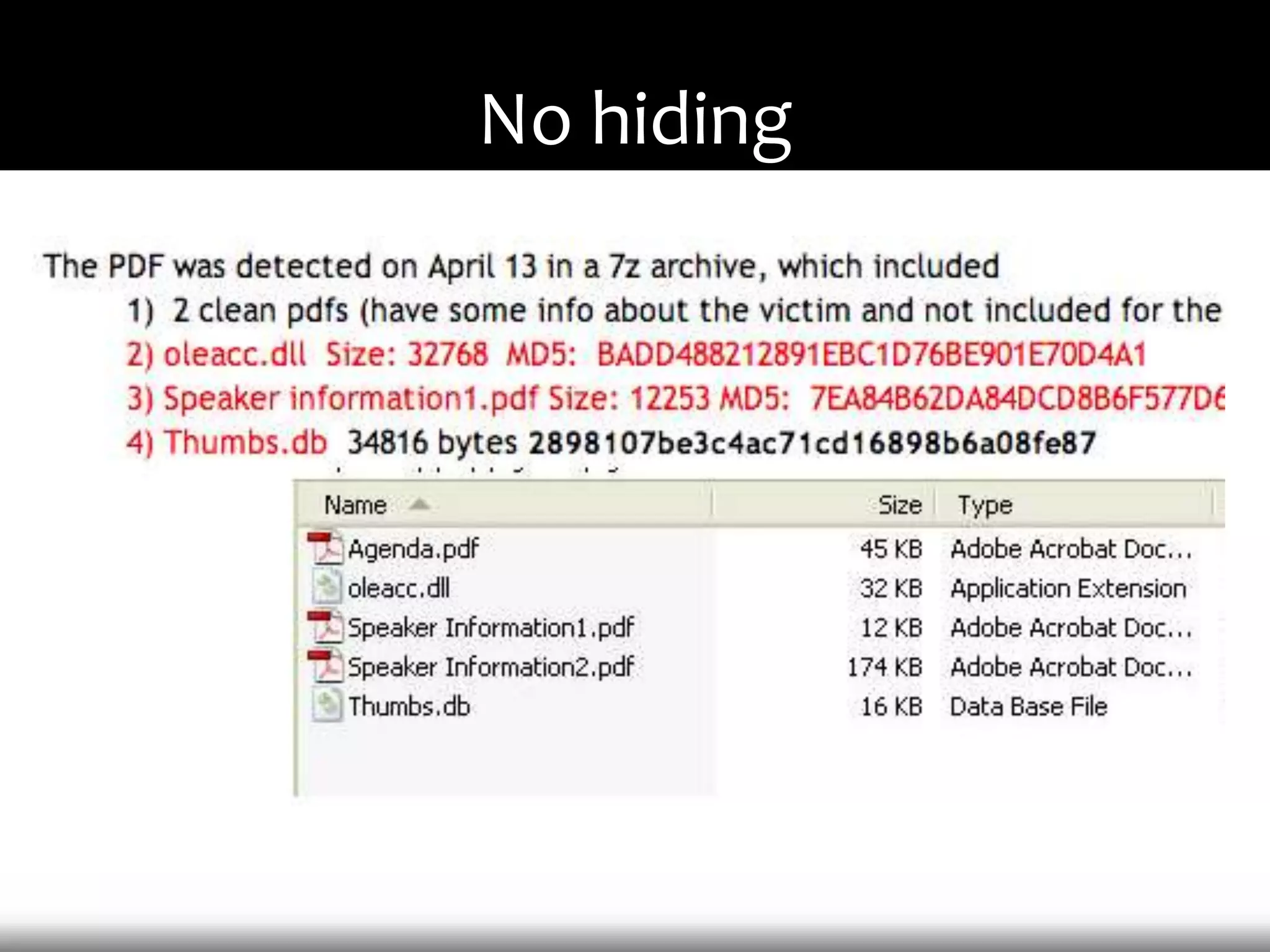
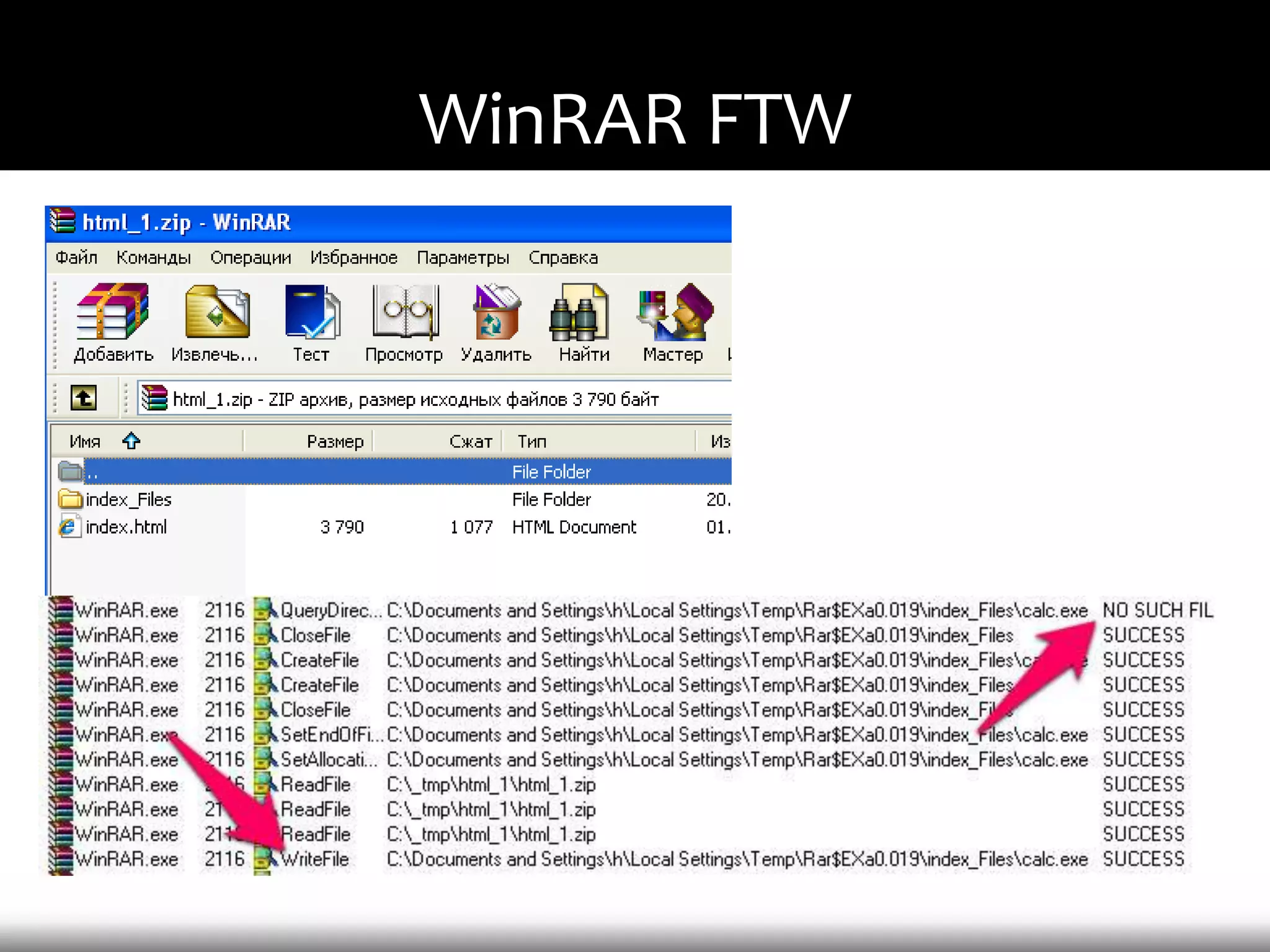
This document discusses techniques for exploiting DLL hijacking vulnerabilities remotely without user interaction. It outlines challenges with traditional fuzzing and static analysis approaches and argues that DLL hijacking remains a viable attack vector. Several methods are proposed for manipulating the current directory to execute an exploit DLL from a remote location, including browser UI redressing, macros, MHT files, archives, and multistage attacks. The document concludes DLL hijacking is well-suited for targeted attacks but not mass attacks due to reliance on user interaction and 0-days.