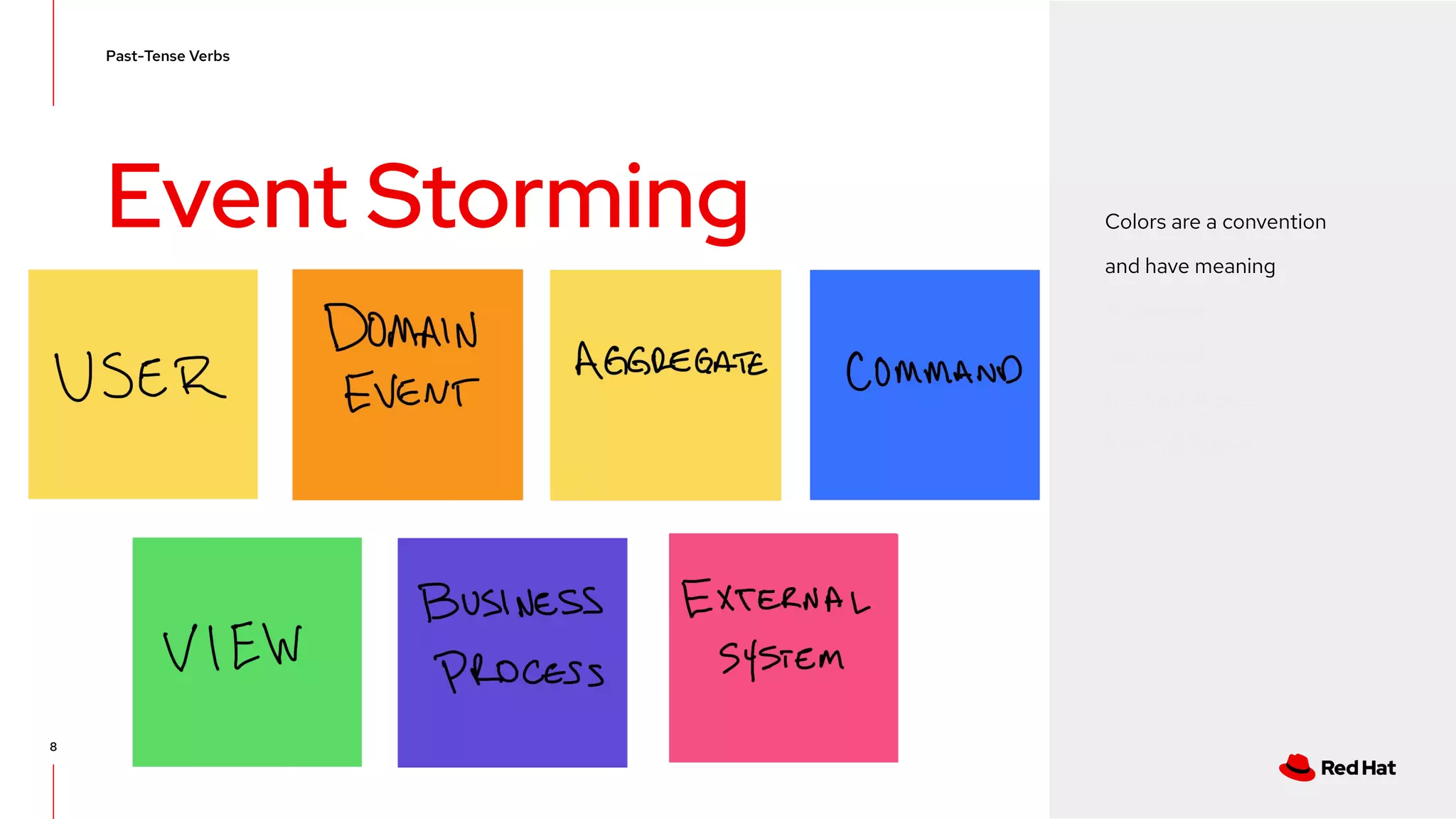
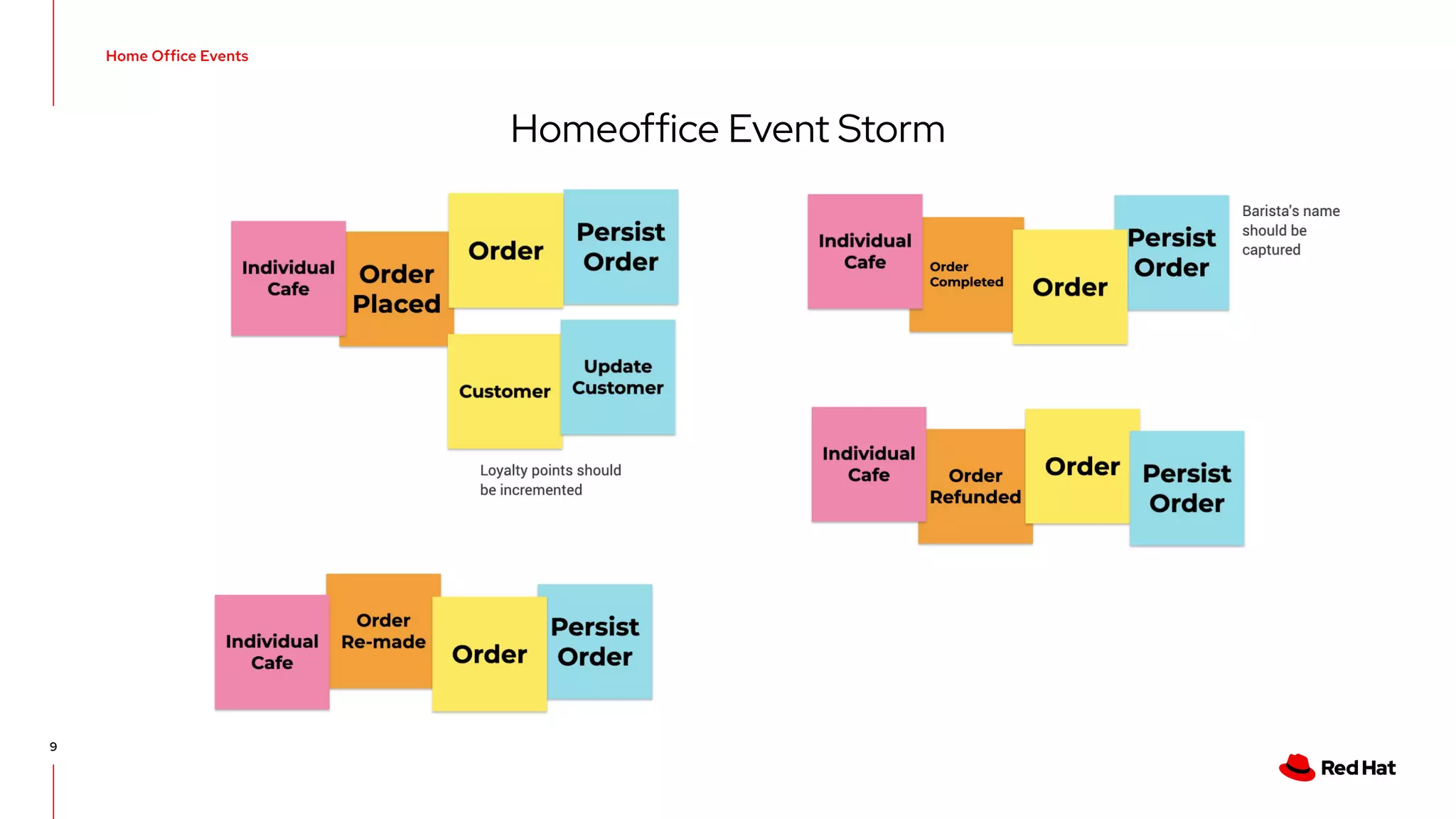
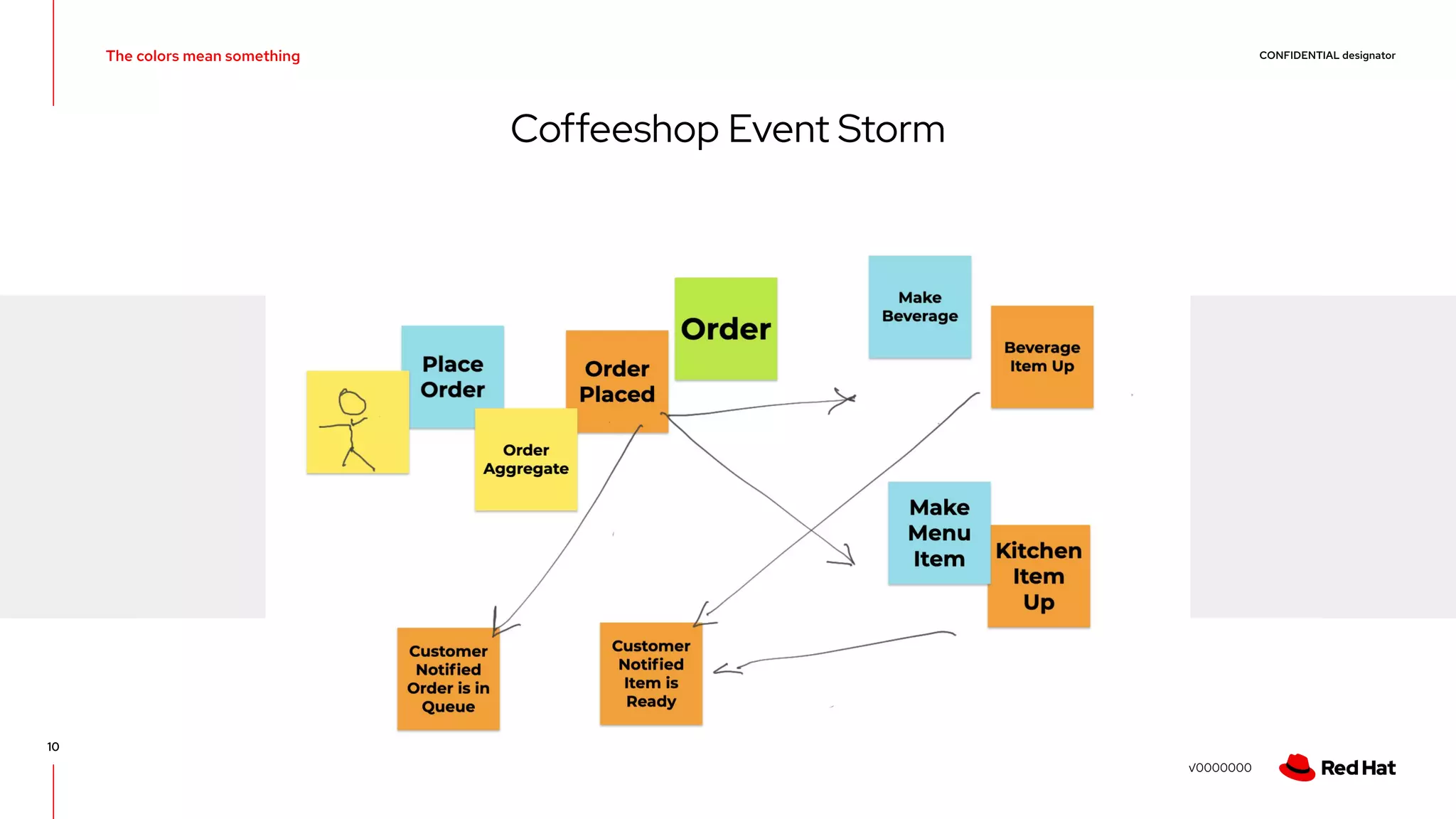
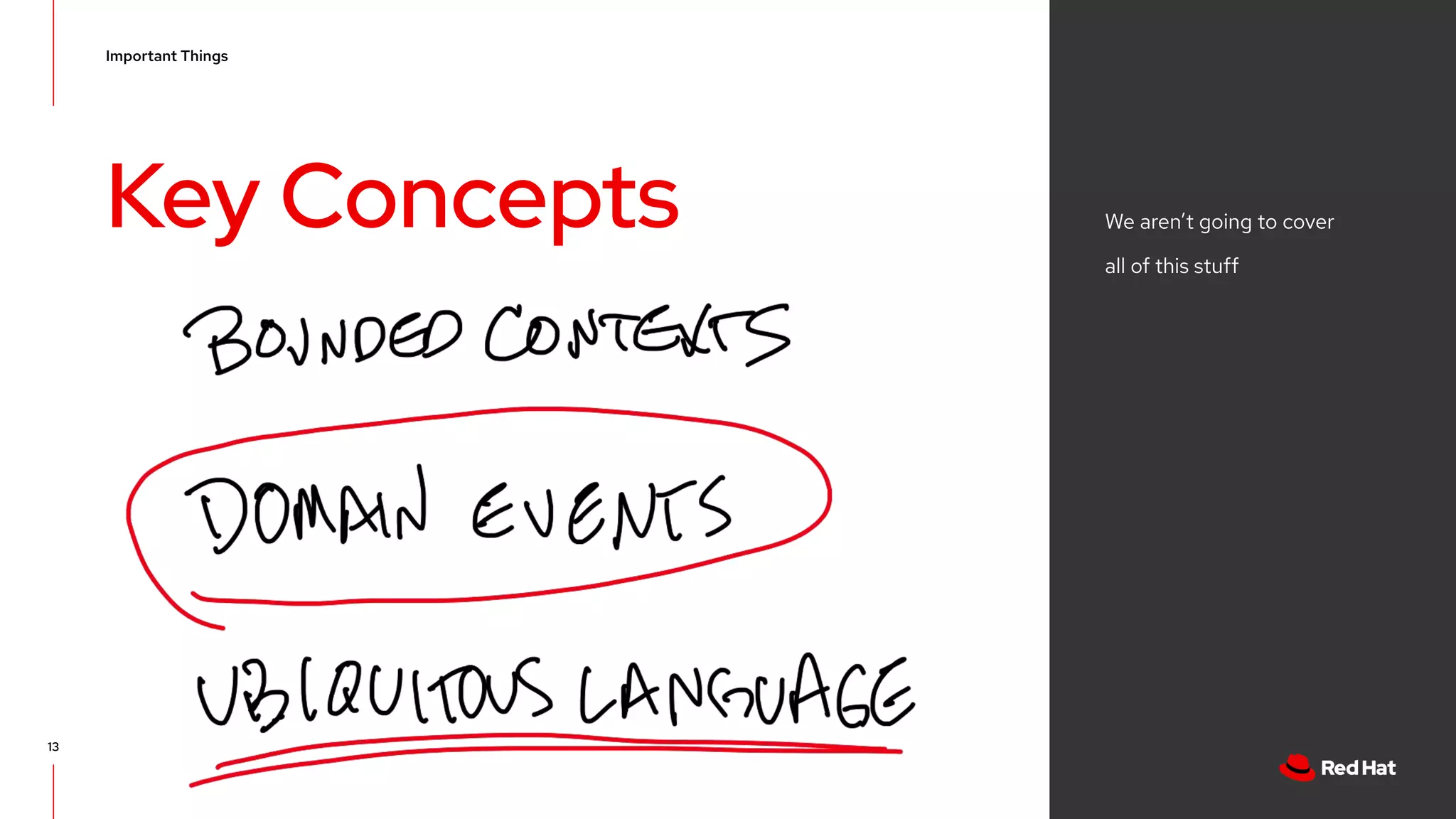
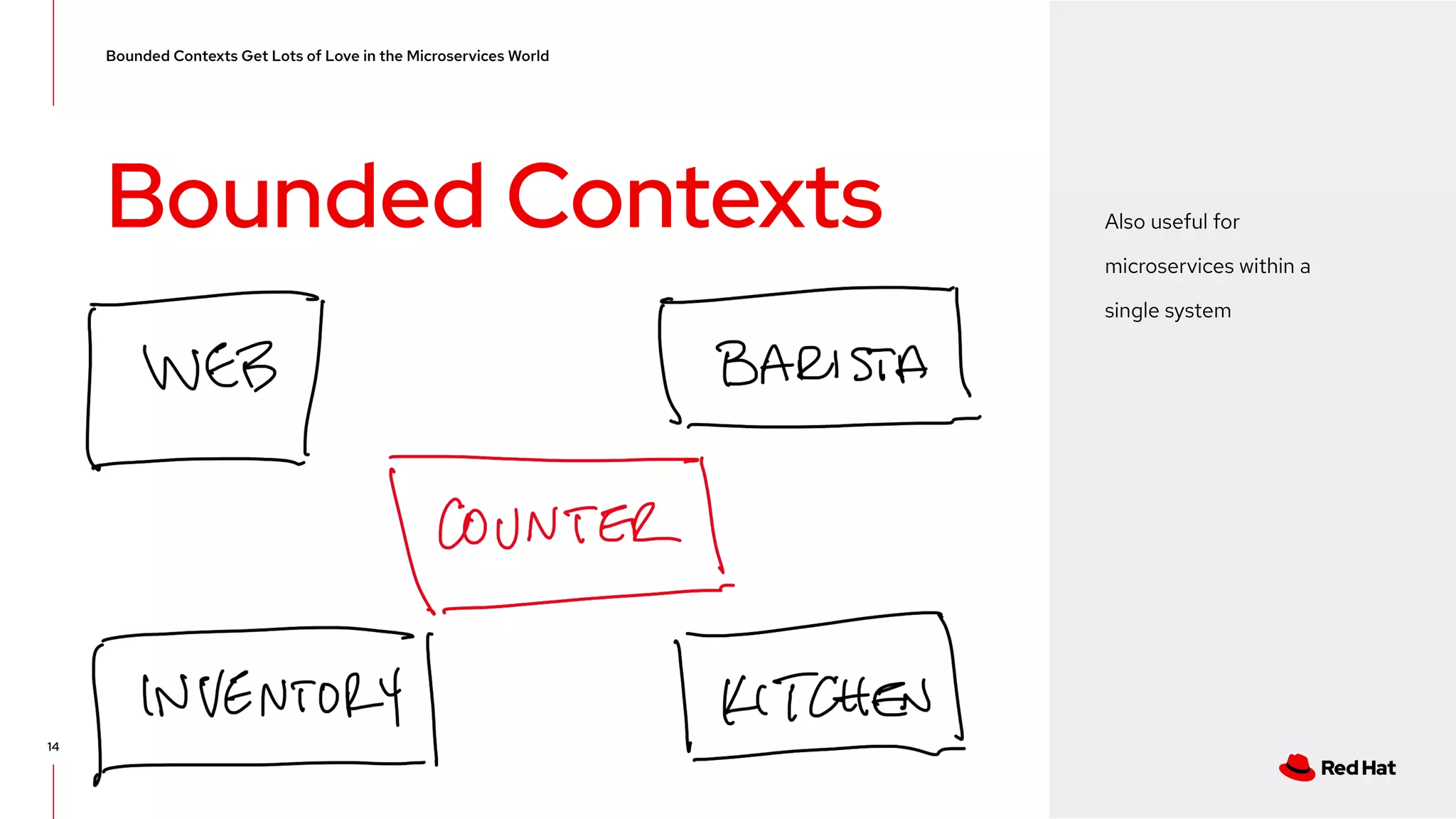
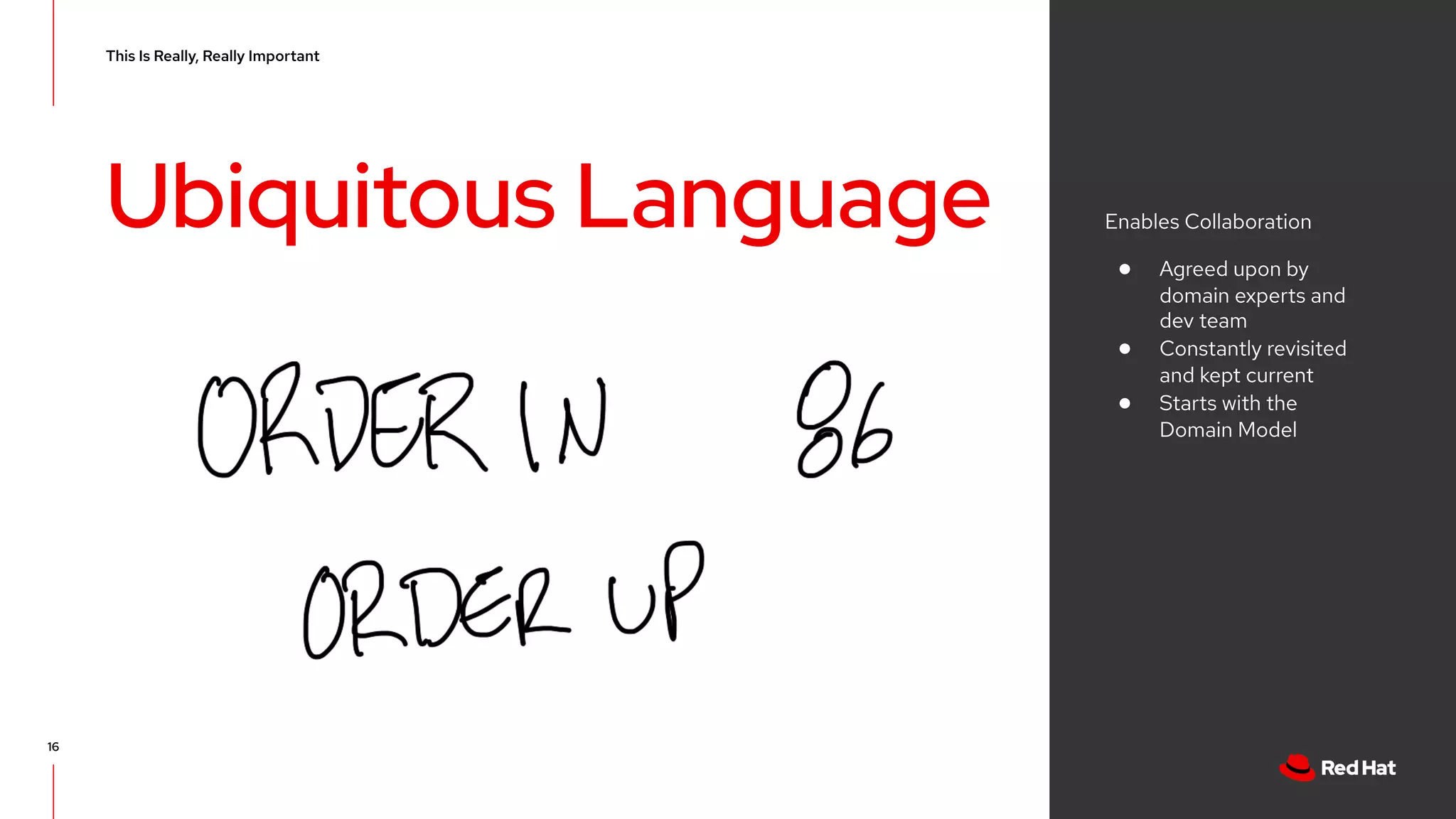
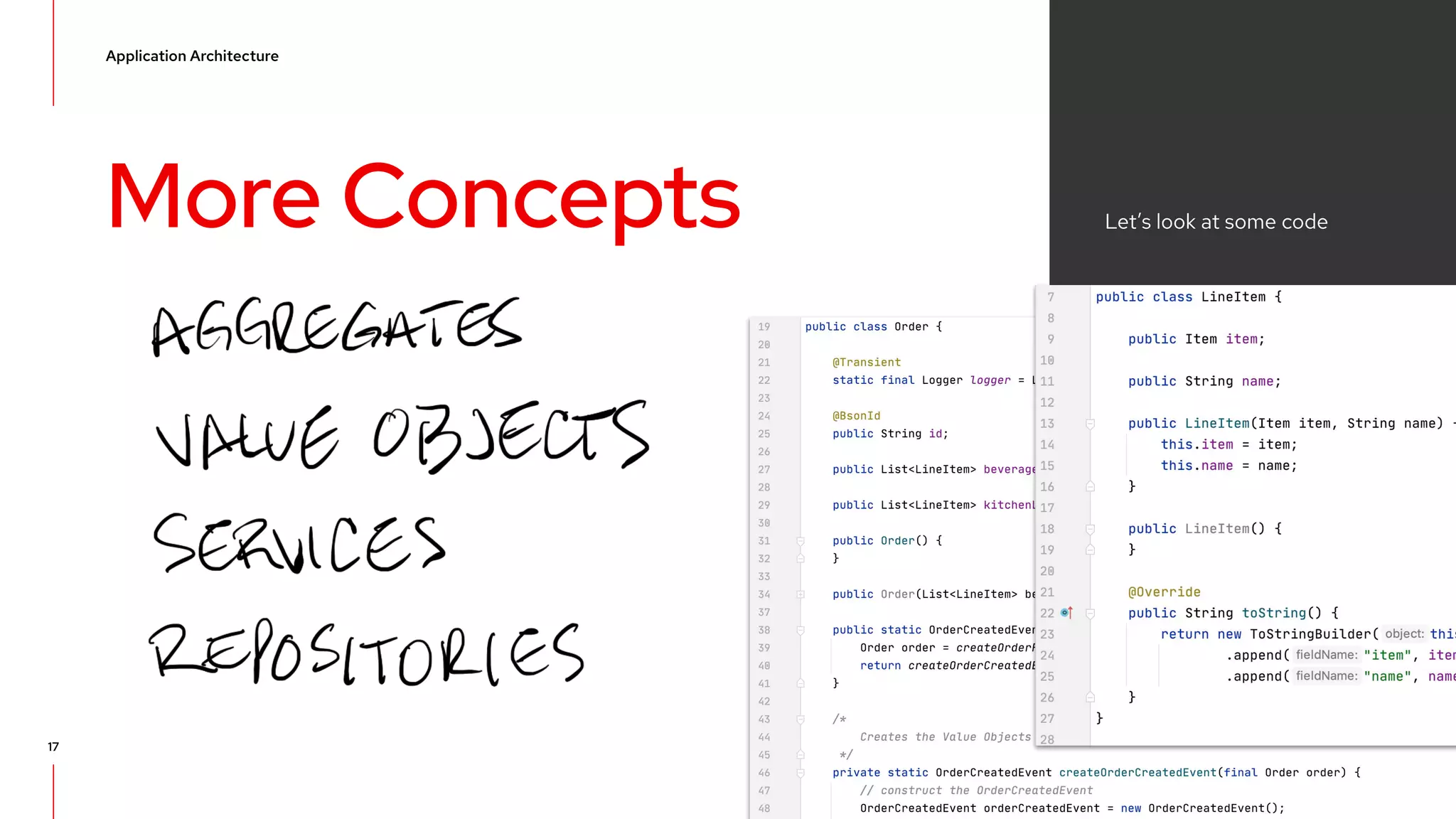
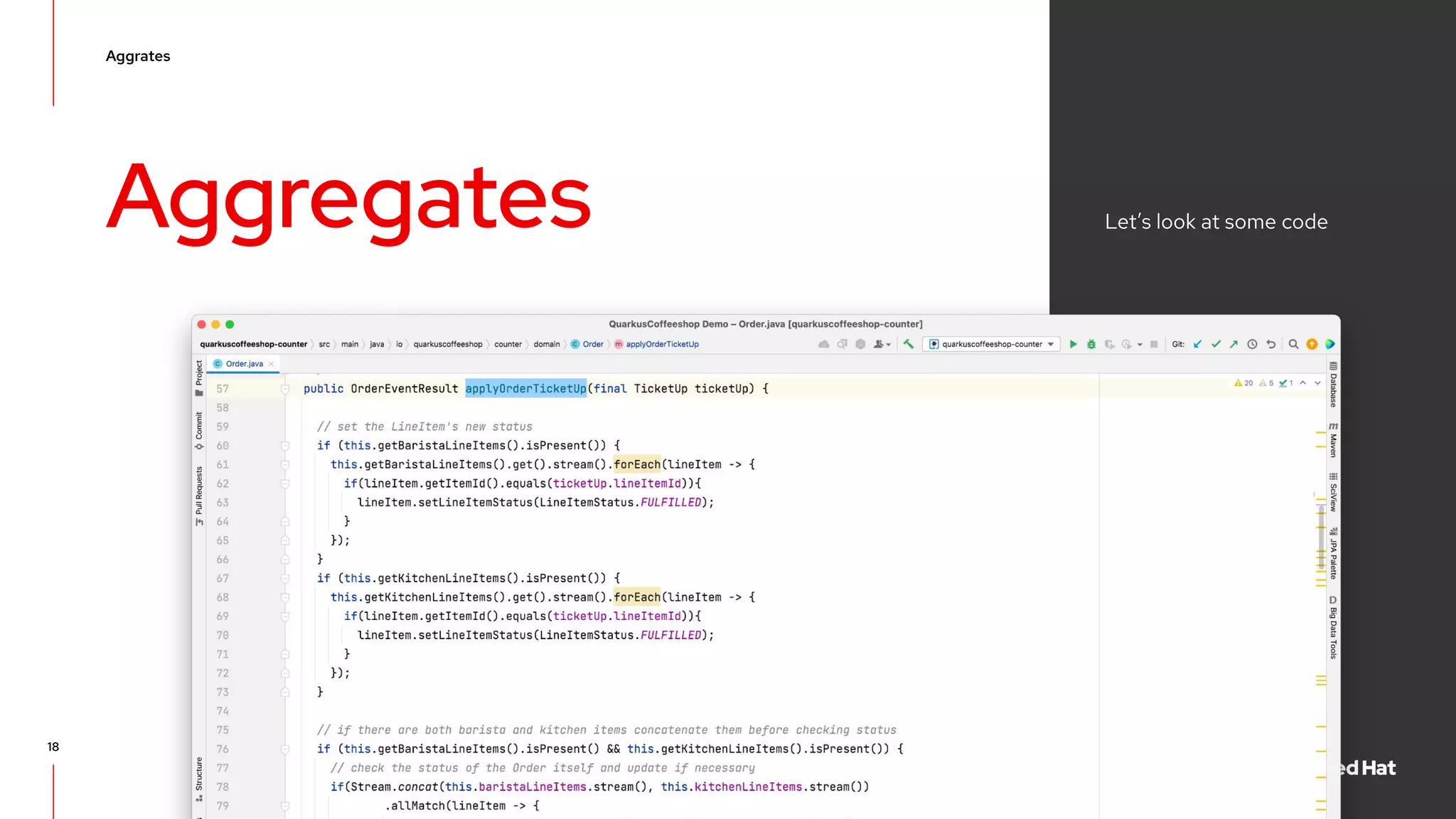
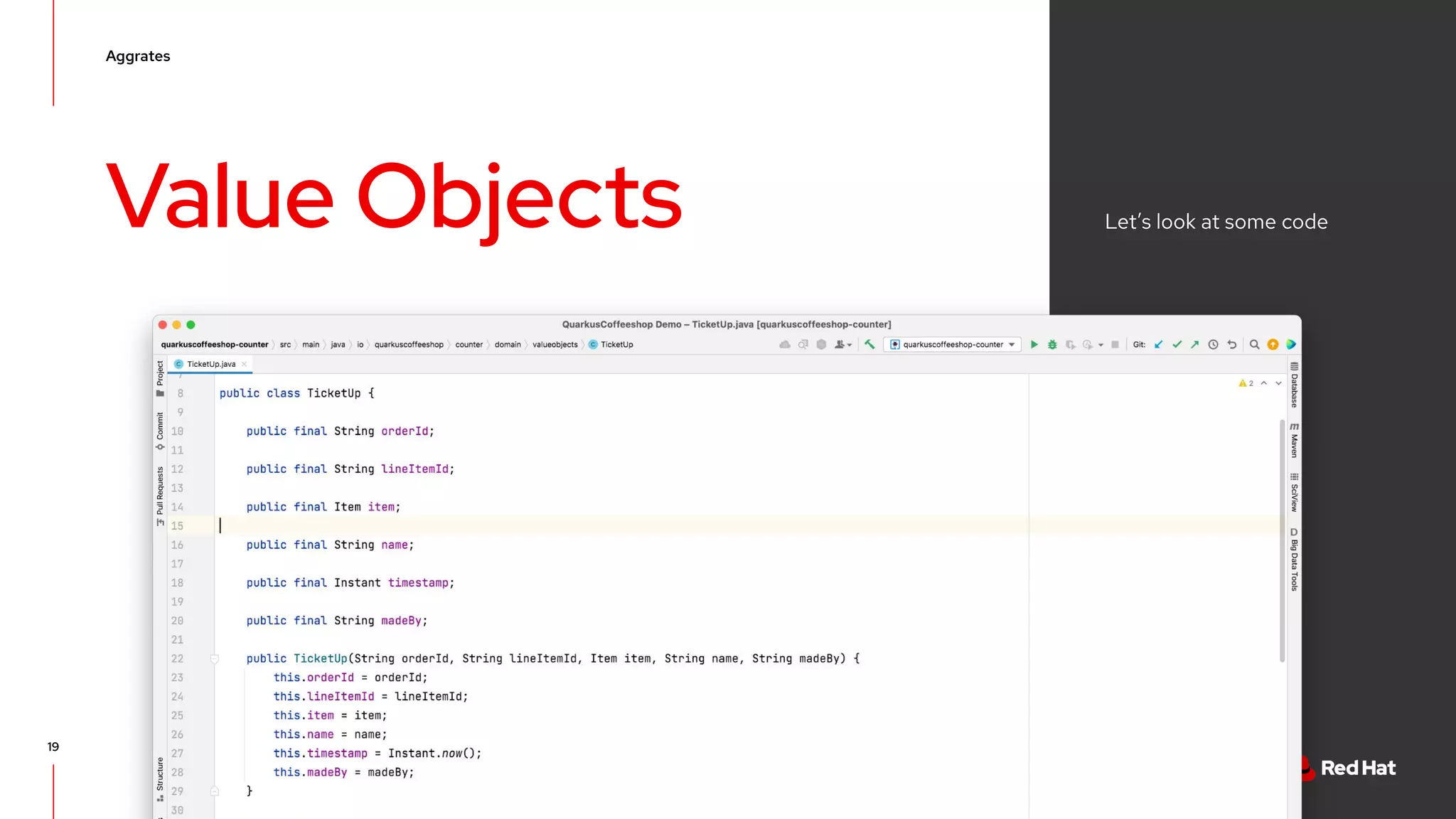
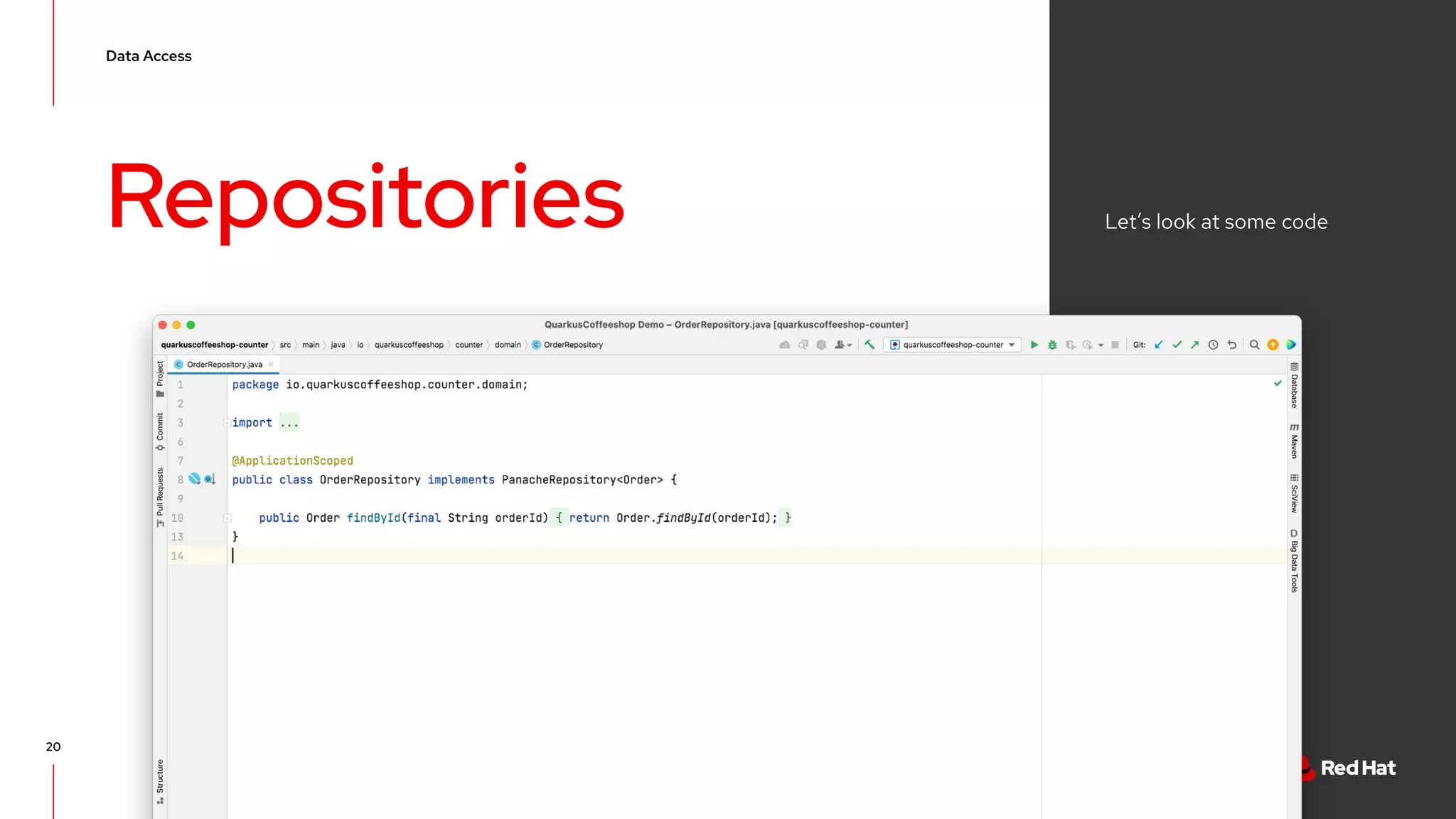
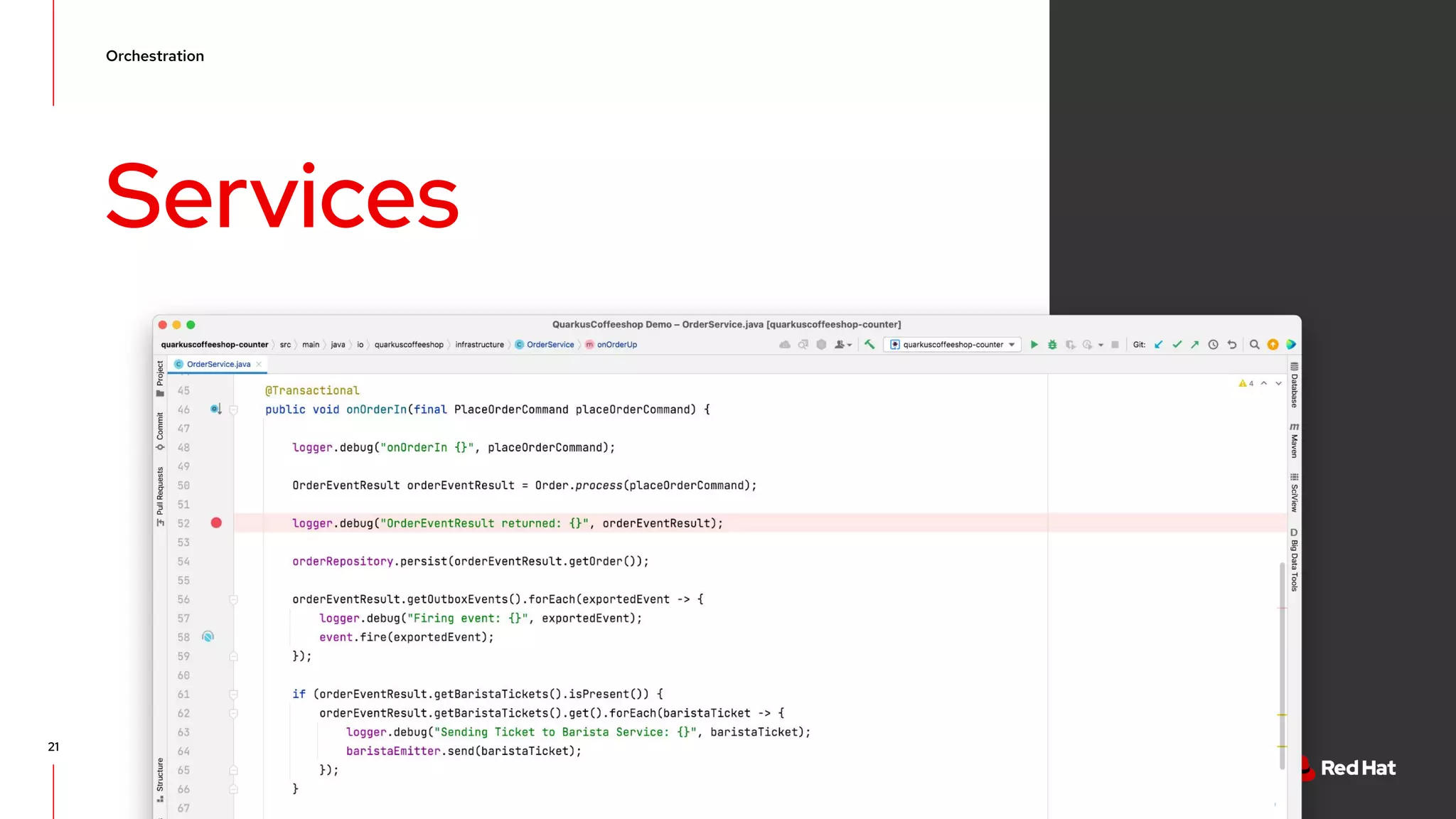
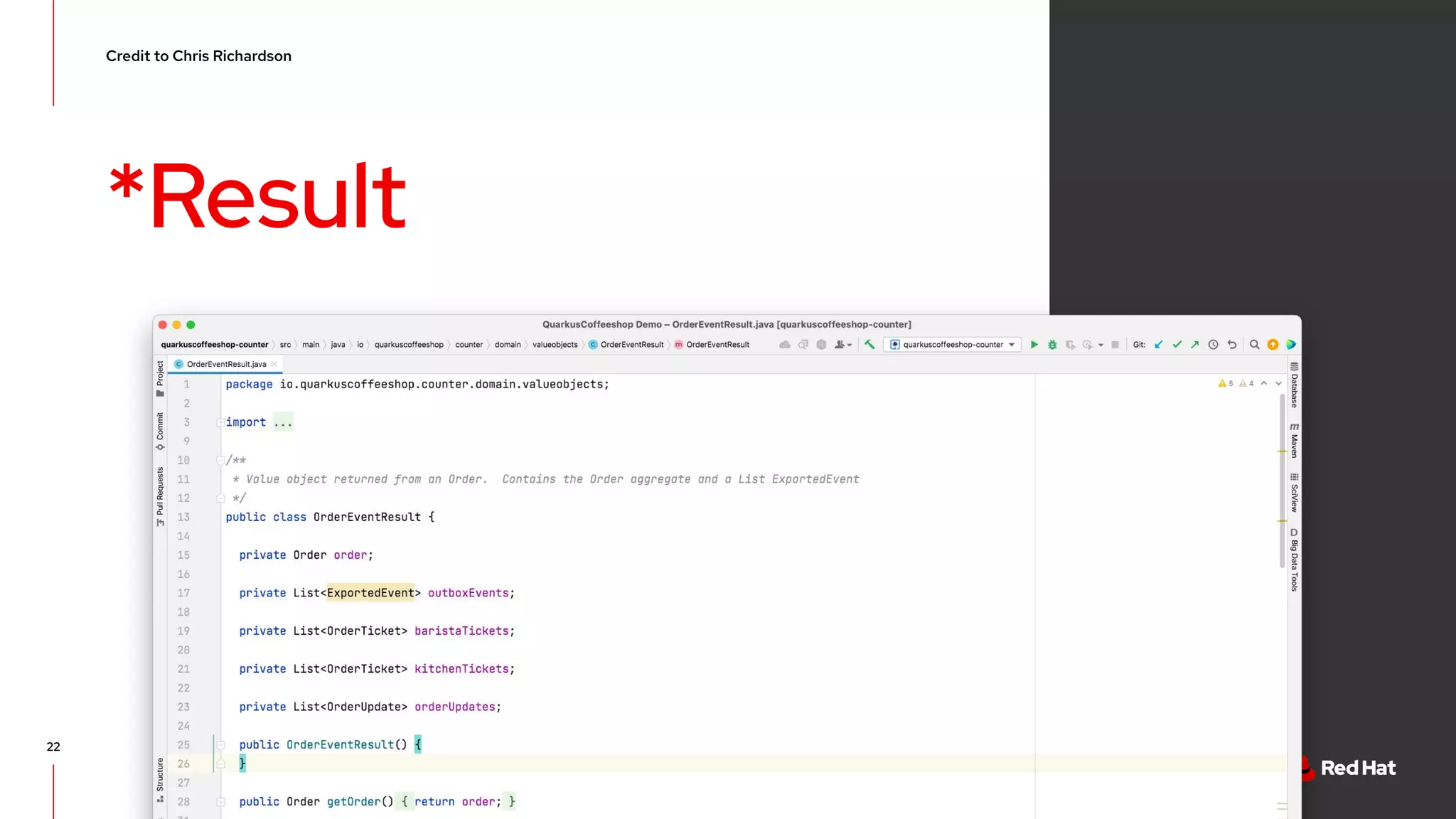
The document discusses event-driven architecture and domain-driven design, emphasizing the importance of event storming as a collaborative learning tool. It outlines key concepts such as bounded contexts, ubiquitous language, and various components like aggregates and value objects in application architecture. Resources for further learning, including links to relevant platforms and GitHub projects, are also provided.