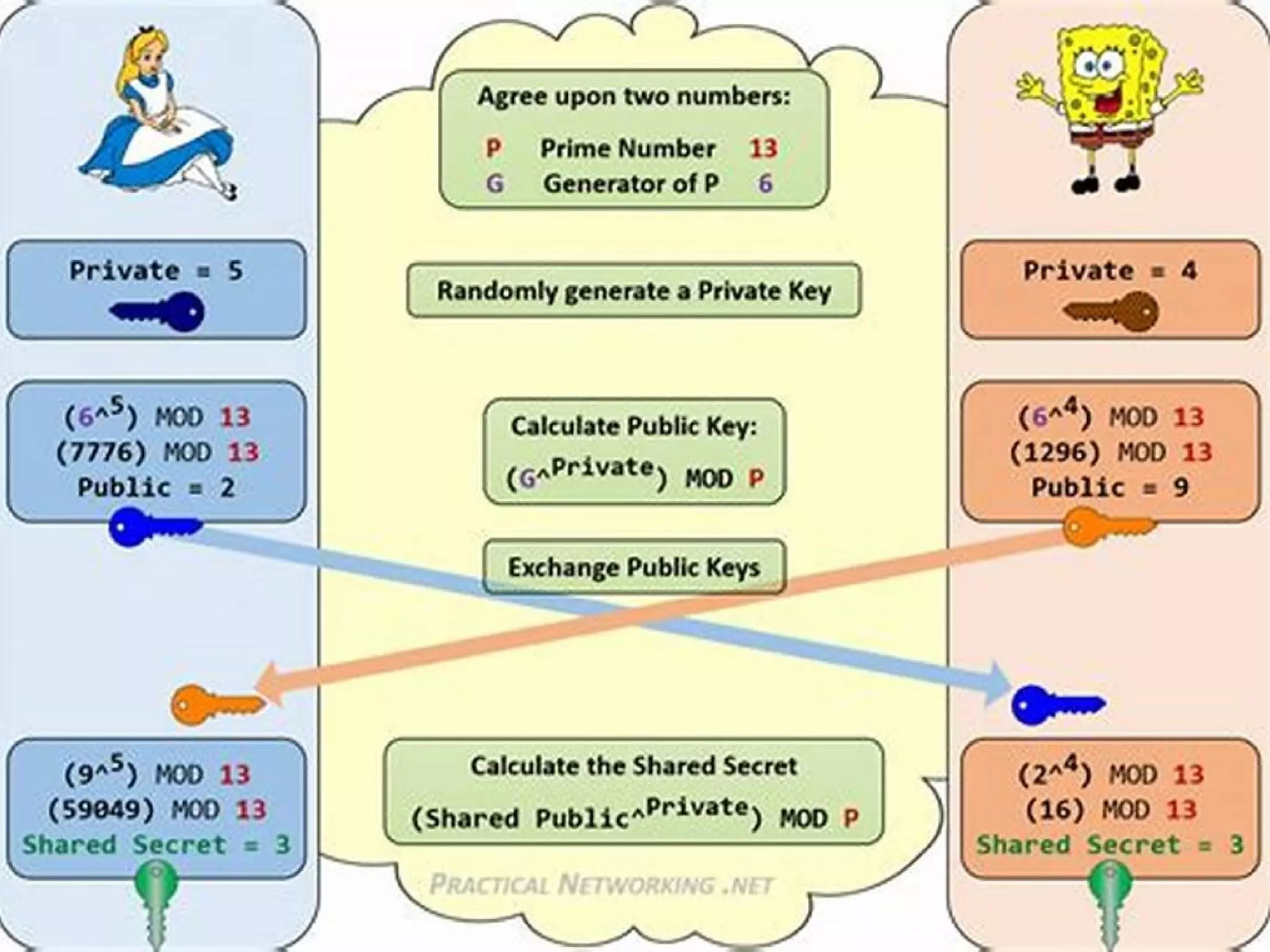
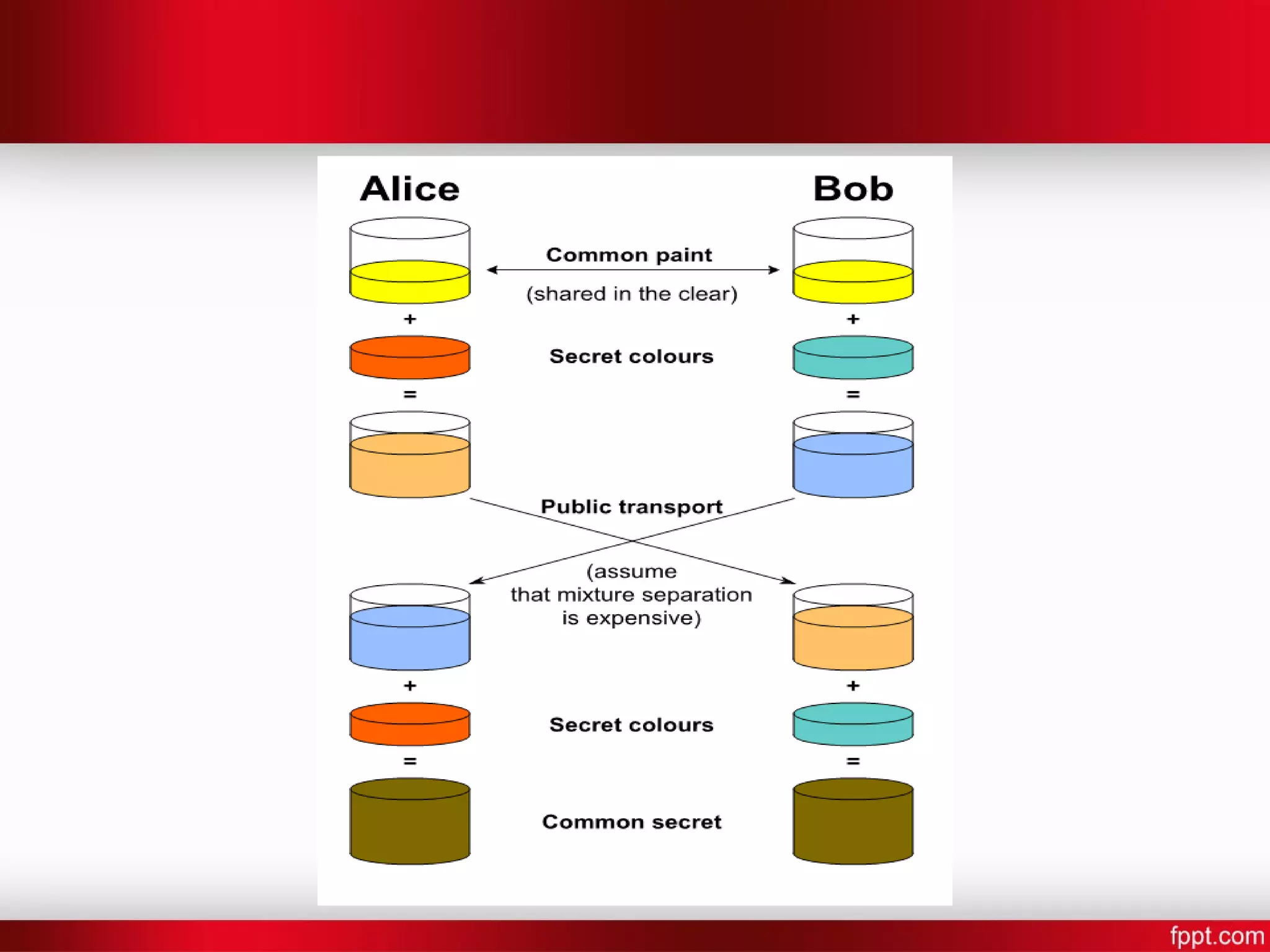
The Diffie-Hellman algorithm, developed in 1976 by Whitfield Diffie and Martin Hellman, enables two parties to generate a shared cryptographic key for secure communication over an insecure channel without transferring the key itself. The process involves agreeing on a prime number and a primitive root, where each party computes their public key using a secret key and shares it to compute a final shared secret key. While this method allows secure key sharing and communication, it is slower and requires more processing power compared to symmetric encryption.


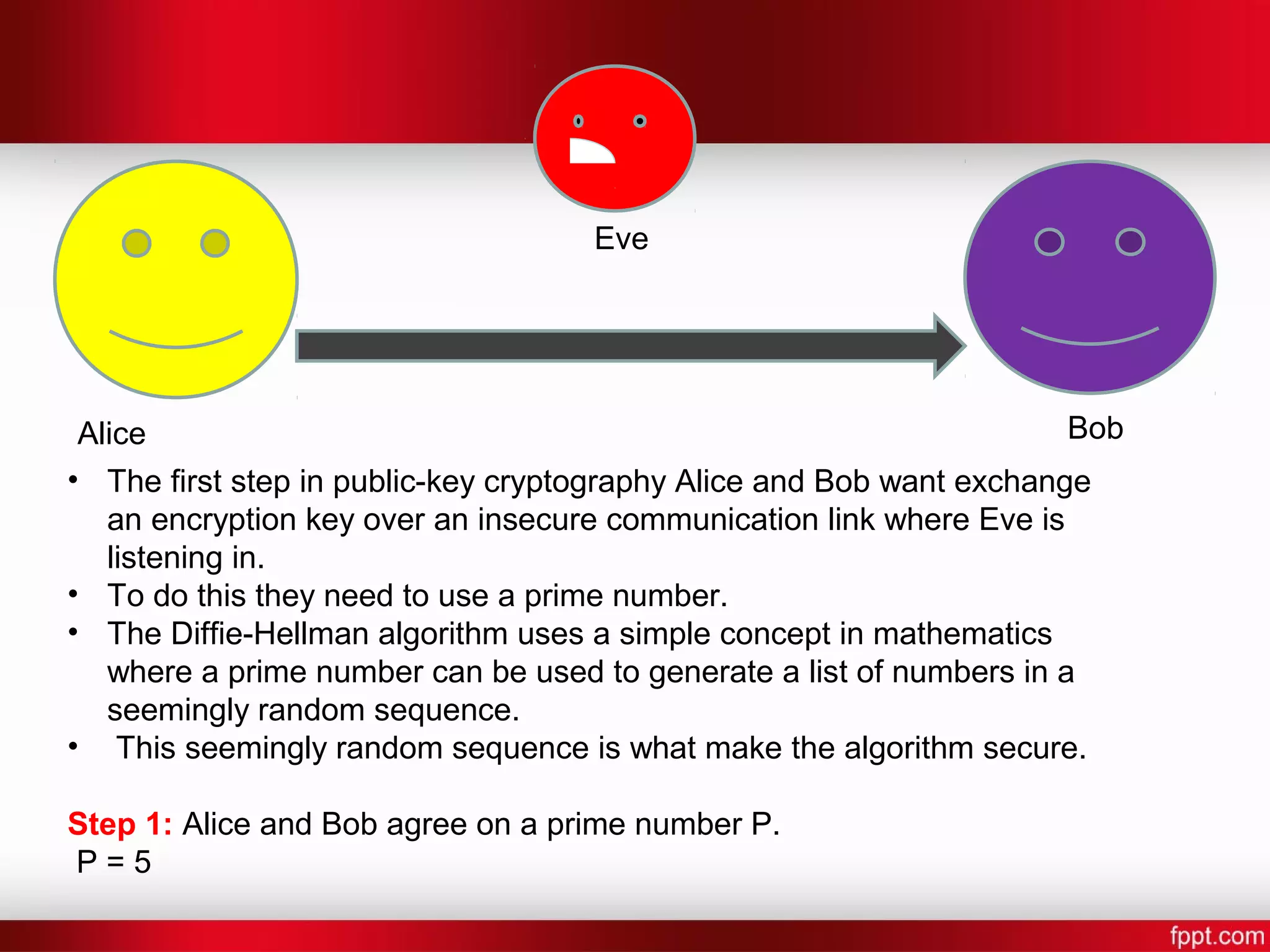
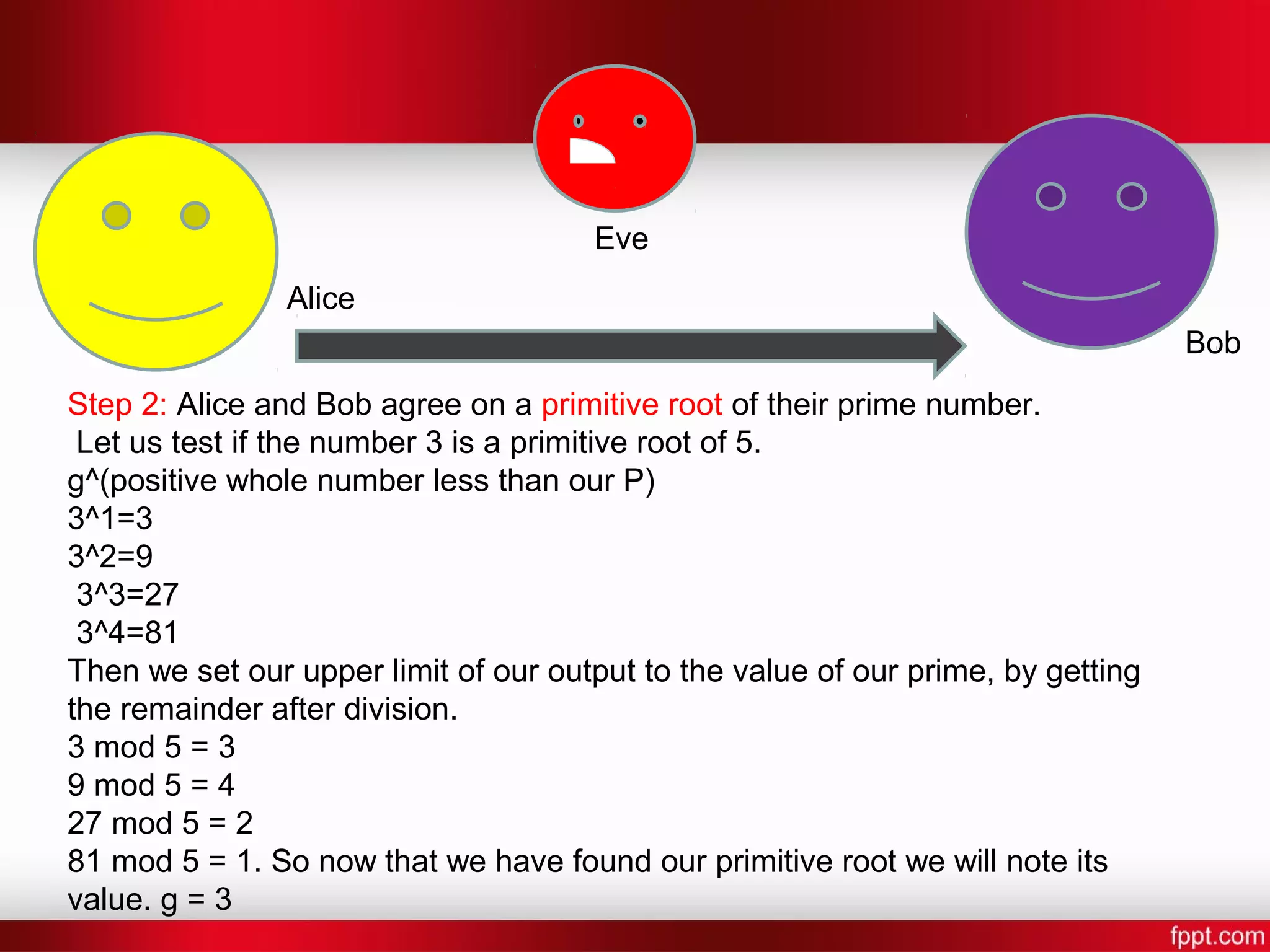
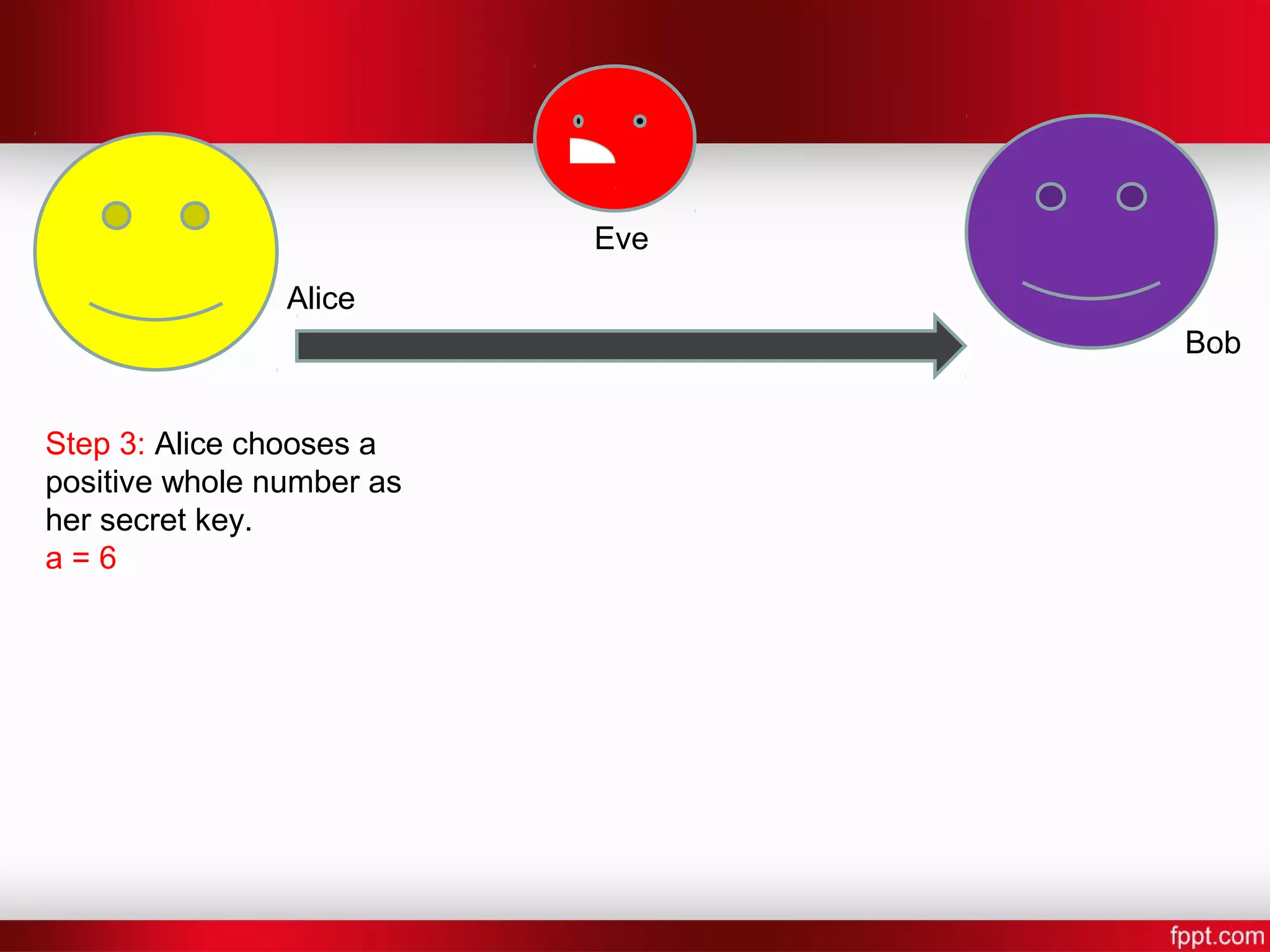
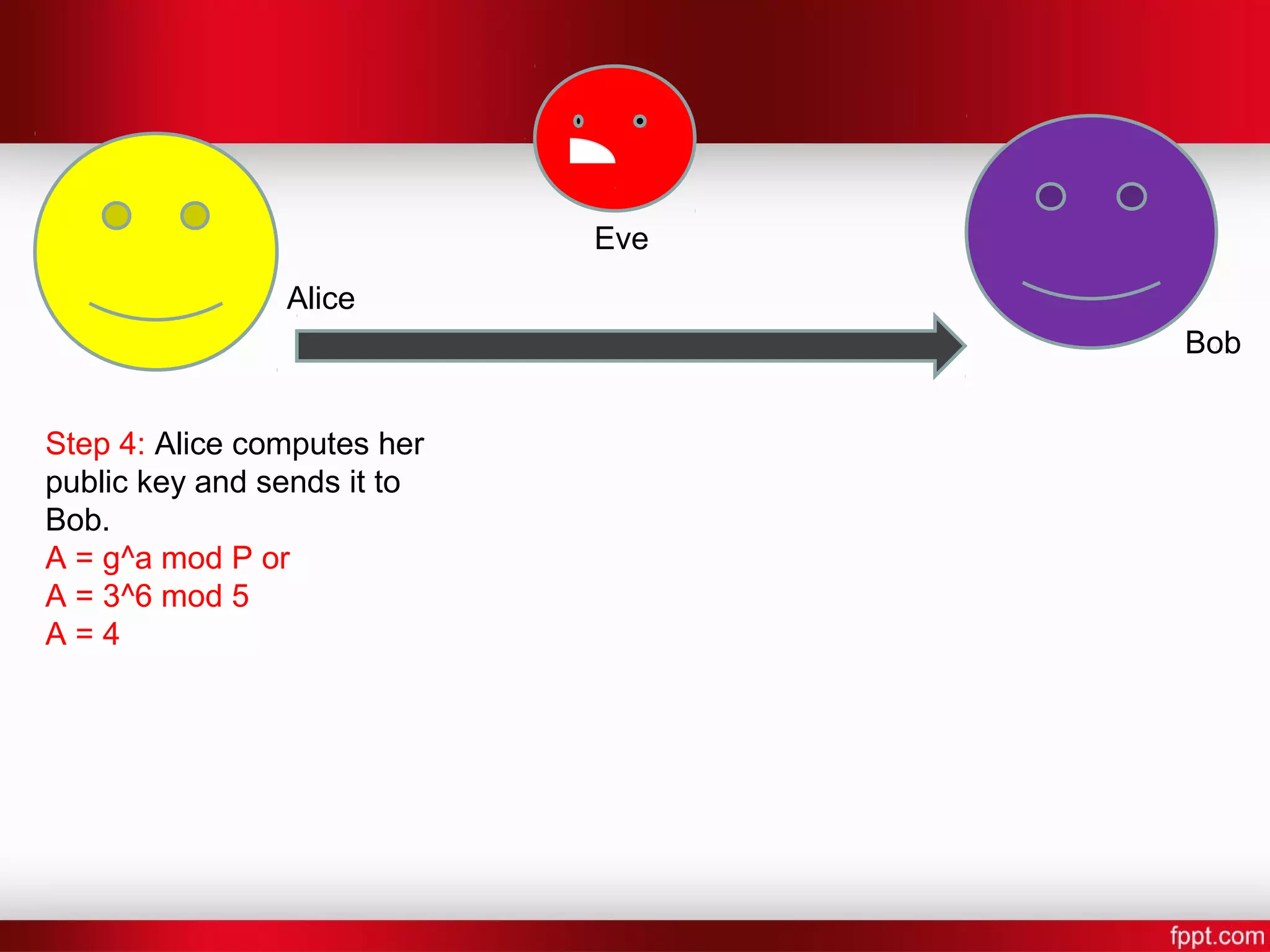
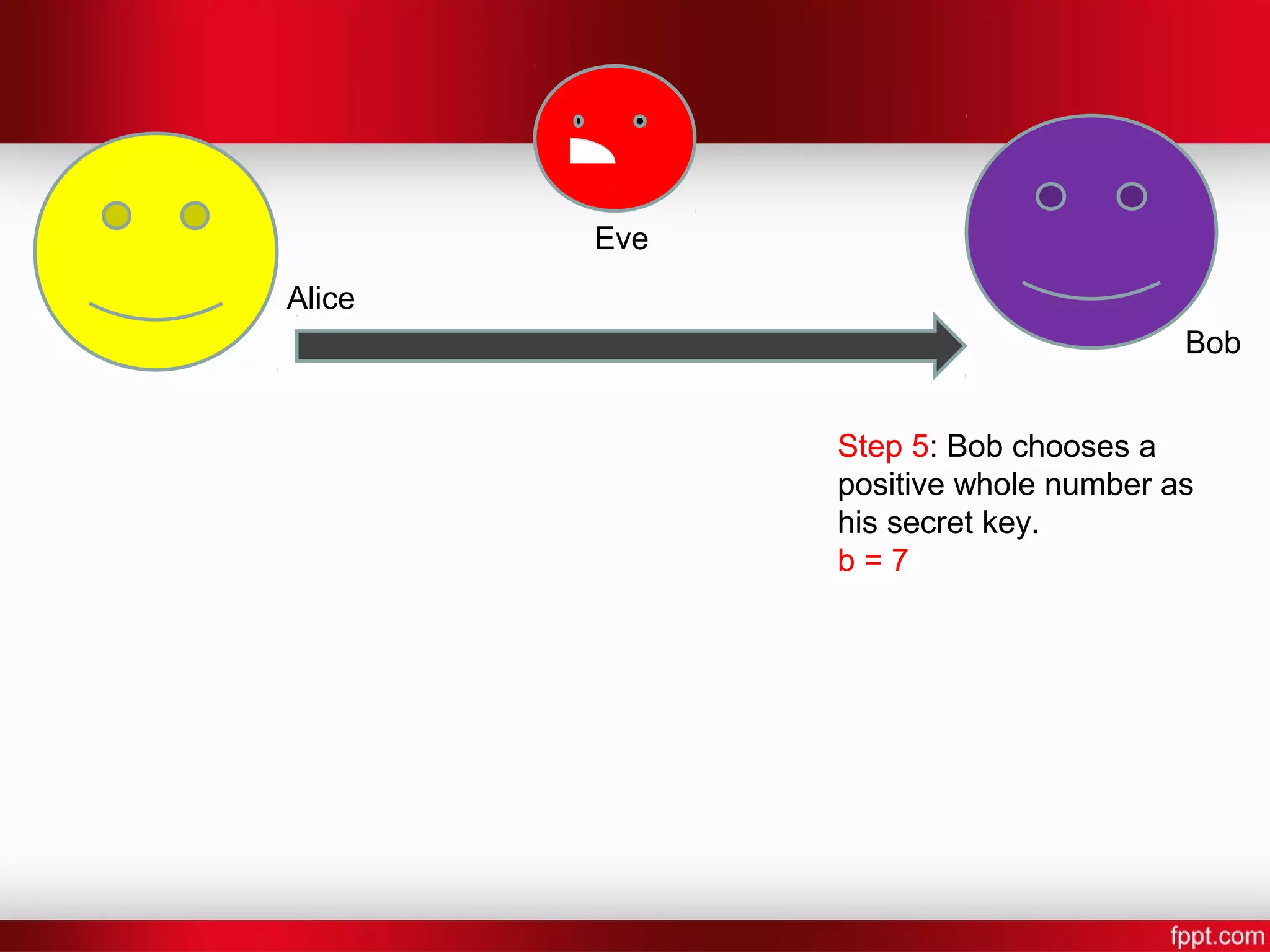
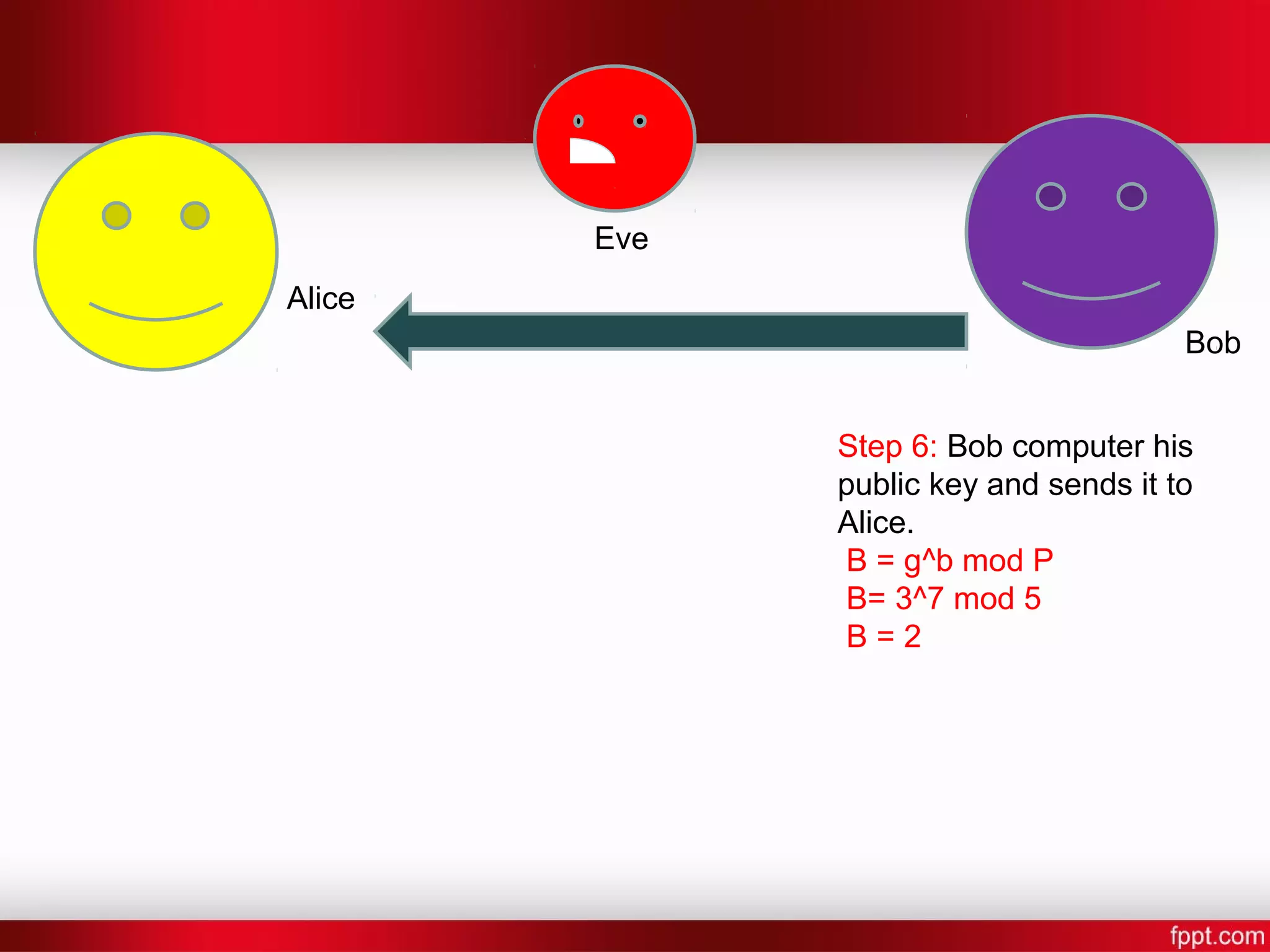
![Alice Bob Eve Step 7: Alice and Bob now compute a shared secret key [Shared Key] = [other persons public key]^[their own secret key] mod P Bob: S = 4^7 mod 5 Alice: S = 2^6 mod 5 S = 4](https://image.slidesharecdn.com/difi-181112182343/75/Diffie-hellman-algorithm-12-2048.jpg)