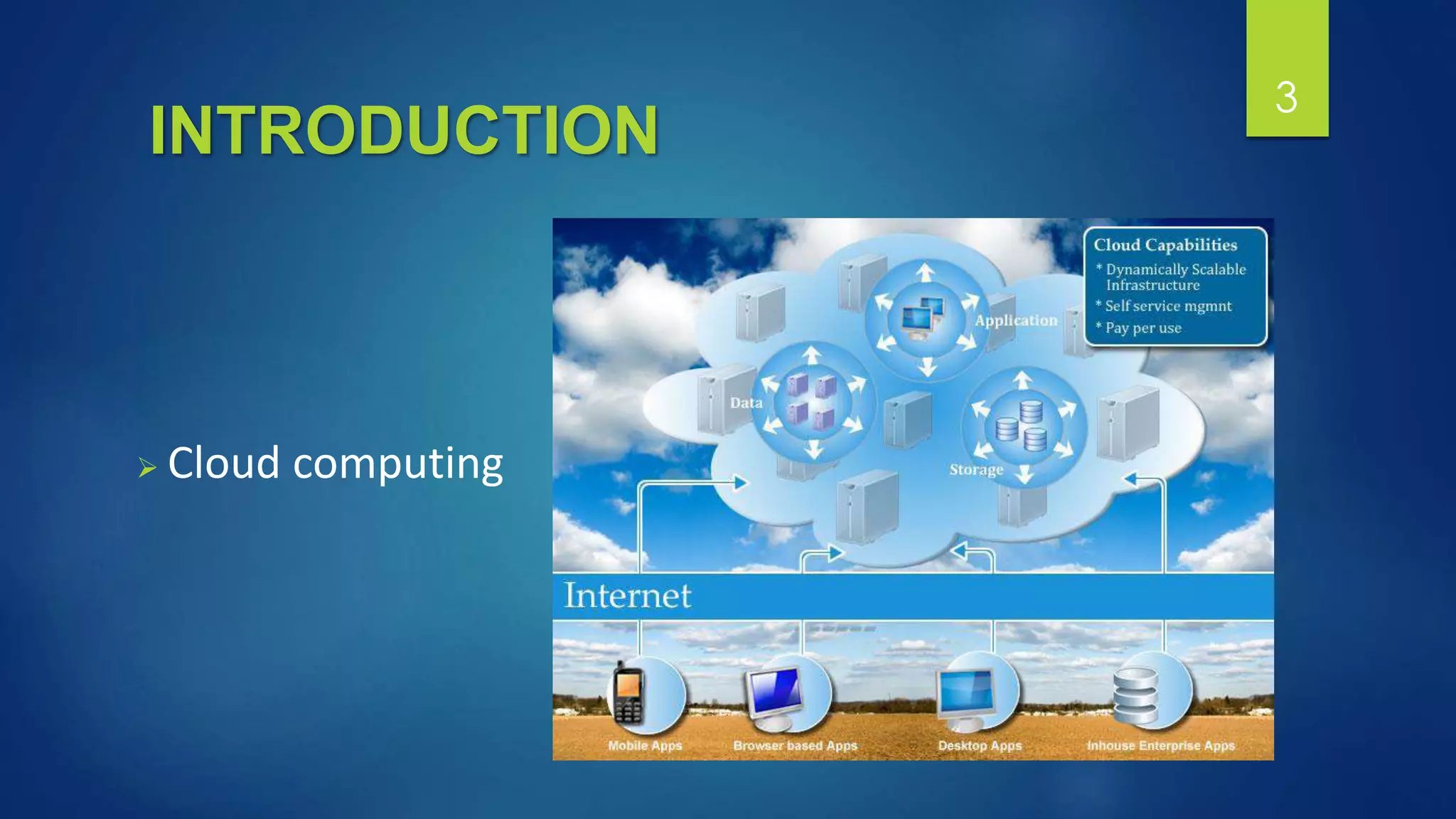
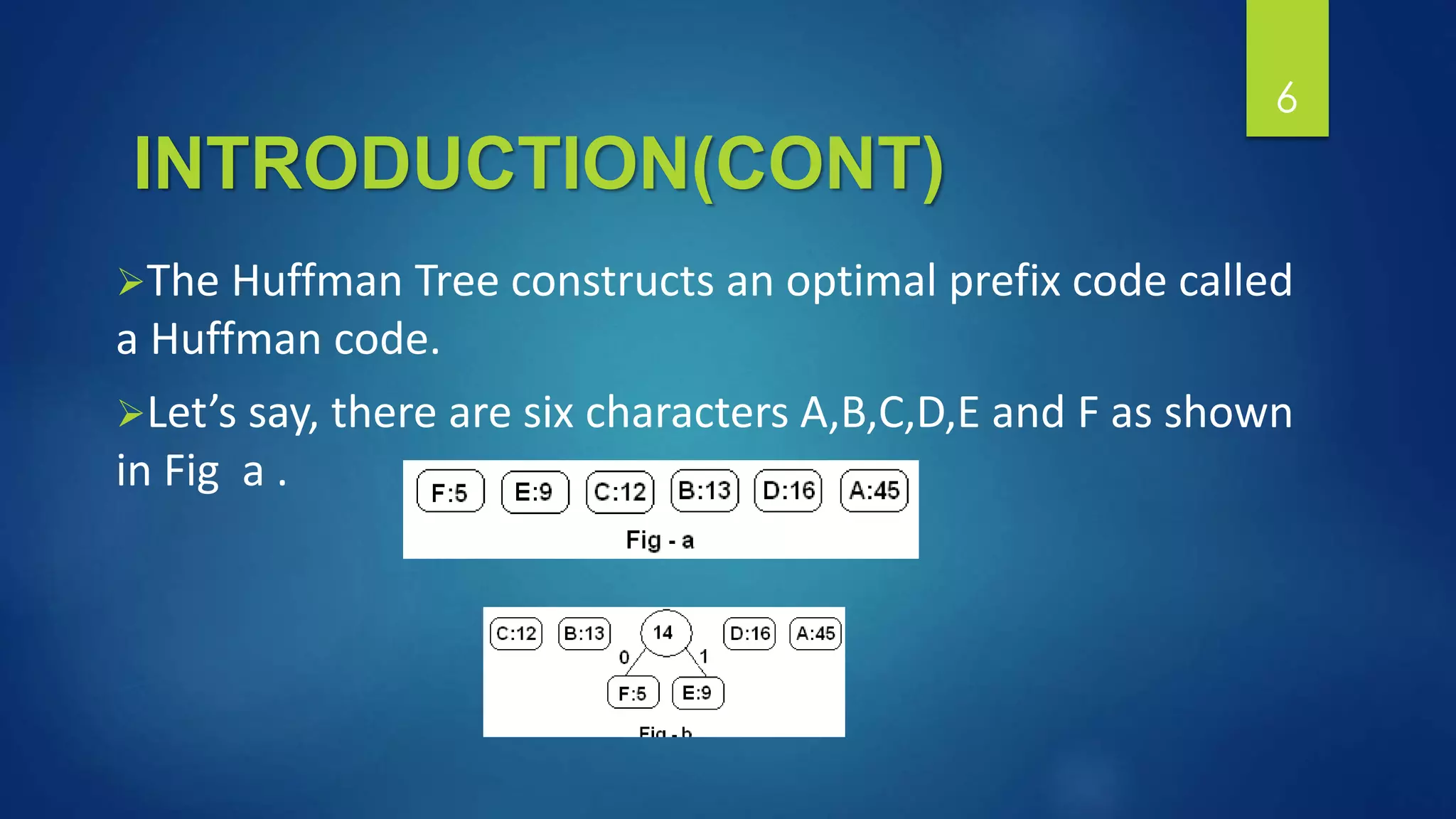
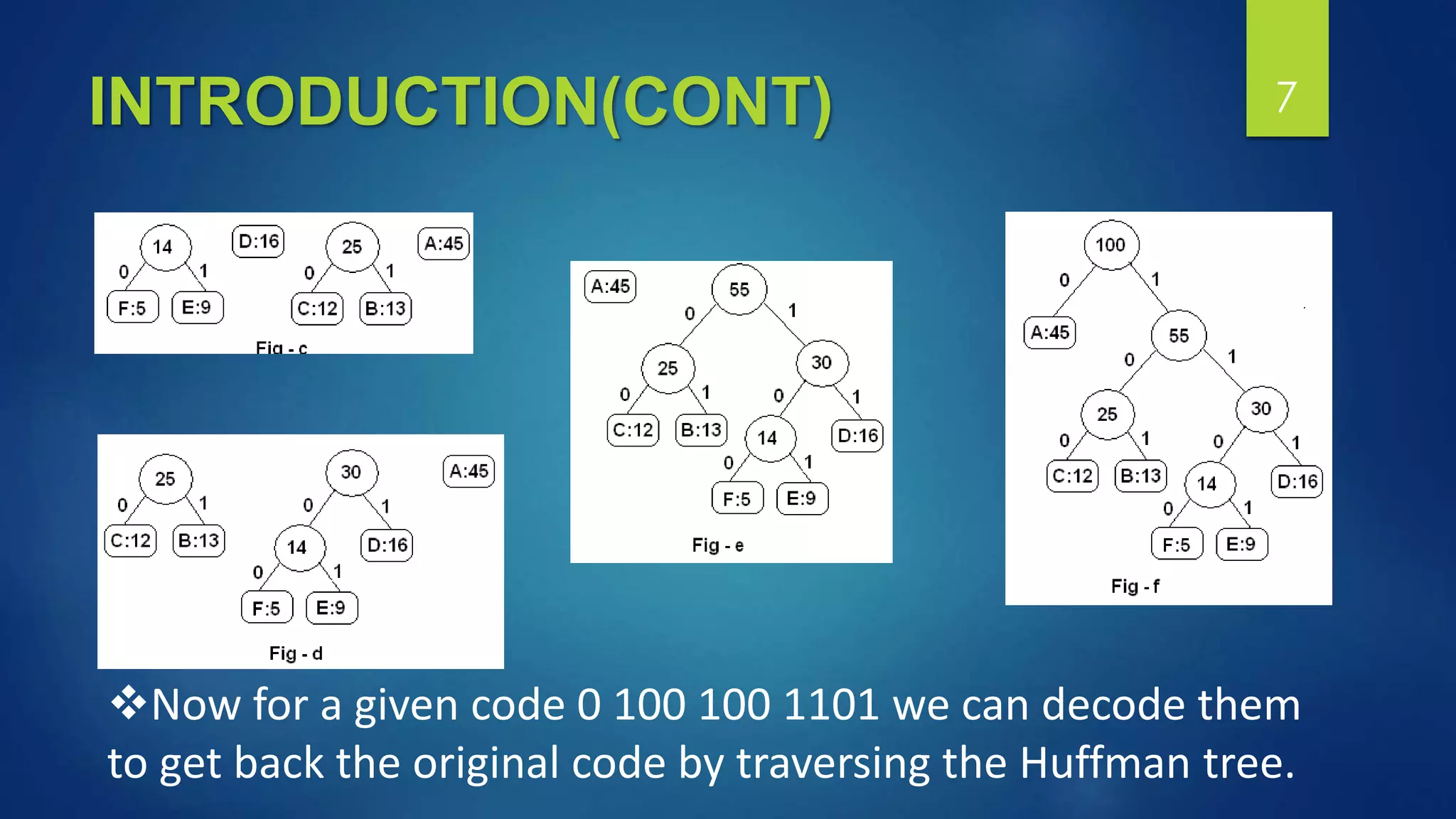
Stenographic approach to ensure data storage security in cloud computing using Huffman coding. The system embeds data into images using steganography after encoding the data and frequency of characters using Huffman coding. This is done to provide security when storing data in the cloud. The encoding and embedding processes ensure the data is not readable without the decoding algorithm and Huffman tree, providing protection from unauthorized access.












![Hiding Data within Images Steganography Deals the pre-requisite requirements like : load image, store file name, image index finally call the MdfImg operation which will map data from file to images. ALGORITHM 3: STEGANOGRAPHY() 1. procedure 2. Load Image_Index = ImageSearch (Image_Database) 3. Store (FName, BCount, Image_Index) 4. MdfImg (Image_Database [Image_Index]); 5. end procedure. 20](https://image.slidesharecdn.com/ion-151026044717-lva1-app6892/75/data-storage-security-technique-for-cloud-computing-20-2048.jpg)

![22 MAPPING DATA FROM A FILE TO IMAGE It does the actual steganographic operation by storing data into images. Algorithm 5: MdfImg (Image_Database [Image_Index]) 1. procedure 2. Read Image_Database [Image_Index]; 3. Compute Pixel Count for Image_Database[Image_Index]; 4. Open FN 5. while (Read Characters until EOF) 6. do if (Pixel Count < B Count) …](https://image.slidesharecdn.com/ion-151026044717-lva1-app6892/75/data-storage-security-technique-for-cloud-computing-22-2048.jpg)
![7. Last bit of each consecutive pixels of the Image_Database[Image_Index] is replaced by Store each character. 8. else 9. Load Image_Index1=ImageSearch(Image_Database) 10. Image_Database[Image_Index1].valid=Image_Index1 11. Image_Database [Image_Index1].valid=0 12. end if 13. end while 14. end procedure 23Algorithm 5: MdfImg (Image_Database [Image_Index]) (CNTD)](https://image.slidesharecdn.com/ion-151026044717-lva1-app6892/75/data-storage-security-technique-for-cloud-computing-23-2048.jpg)
![RETRIEVING DATA FROM IMAGE The following algorithm retrieves the data from the images which is kept in cloud storage. Algorithm 6: RetrieveData () 1. procedure 2. Read File_Database; 3. for F_Database (i), i=1 to m 4. do if (F exits) 5. I=Holds the address of image. 6. end if 7. end for 8. Open Image_Database; 9. Read Image_Database [I]; 10. Open a F Temp and a F Freq 24](https://image.slidesharecdn.com/ion-151026044717-lva1-app6892/75/data-storage-security-technique-for-cloud-computing-24-2048.jpg)
![11. while (Until we get 11111111 in Image_Database [I]) 12. do Read 4 bits at a time from 4 consecutive pixels 13. Convert them into decimal form. 14. sum =sum + 4 15. if ( decimal number is within 0 to 9 ) 16. Write that digit in F Freq 17. else 18. Write new line character in F Freq 19. end if 20. end while 21. sum= sum - BCount 22. Call Huffman-Tree( ) based on the frequency counts present in FFreq and create the HuffmanTree. 25](https://image.slidesharecdn.com/ion-151026044717-lva1-app6892/75/data-storage-security-technique-for-cloud-computing-25-2048.jpg)
![23. while ( sum <= BCount ) do 24. read bits from Image_Database [I] 25. Start traversing the Huffman-Tree from root. 26. When we reach leaf node, we will get character. 27. Append that character in FTemp . 28. Increment sum number of times we collect bits from Image_Database [I] 29. end while 30. Show F Temp to the user, after user closes the file FTemp, delete the file FTemp from system. 31. end procedure 26](https://image.slidesharecdn.com/ion-151026044717-lva1-app6892/75/data-storage-security-technique-for-cloud-computing-26-2048.jpg)






![REFERENCES [1] Peter Mell, Timothy Grance, “The NIST Definatin of Cloud Computing”, Jan, 2011.http://docs. ismgcorp.com/files/external/Draft-SP-800-145_clouddefinition.pdf. [2] Amazon.com, “Amazon Web Services (AWS)”, Online at hppt://aws.amazon.com, 2008. [3] Con Wang, Qian Wang, Kui Ren, and Wenjng Lou,“Ensuring Data Storage Security in CloudComputing”,17th International workshop on Quality of service, USA, pp1-9, 2009, IBSN:978-42443875-4. [4] Thomas H. Cormen, Charles E. Leiserson, Ronald L.Rivest, and Clifford Stein. Introduction to Algorithms,Third Edition, Prentice Hall of India, 2010. [5] B.P Rimal, Choi Eunmi,I.Lumb, “A Taxonomy and Survey of Cloud Computing Sytem”, Intl. Joint Conference on INC, IMS and IDC, 2009,pp.44-51, Seoul,Aug, 2009. DOI : 10.1109/NCM.2009.218. 33](https://image.slidesharecdn.com/ion-151026044717-lva1-app6892/75/data-storage-security-technique-for-cloud-computing-33-2048.jpg)
