The document is a comprehensive text on computer science fundamentals, authored by Ganesh B. Ingle, Vishwanath Mishra, and others, aimed at aiding marine engineering and nautical science students. It covers essential topics such as computer hardware, software, data types, programming concepts, number systems, and coding conventions. The authors express gratitude to various pioneers of computing and emphasize the importance of understanding computer science in modern society.
















![Computer Concepts and Fundamentals of Programming 20 void func2() { int k = main(); printf(nWithin func2(), k = %d, k); } A sample output of the program is given below: Within func1() Within main() Within main() Within func2(), k = -8 The output of the above code testifies that func1() is called first, after which main() function is executed, after which func2() function is called, which in turn explicitly calls main() function which in turn returns -8 which is stored in integer variable k. [N.B. Two underscores precede the word attribute and two underscores follows the word attribute in the statements: void func1(void) __attribute__((constructor)); and void func2(void) __attribute__((destructor));] For those working on the TurboC compiler, the following program can be used: #includestdio.h void func1(); void func2(); #pragma startup func1 #pragma exit func2 main() { printf(nWithin main()); return -8; } void func1() { system(clear); printf(nWithin func1()); } void func2() { int k = main(); printf(nWithin func2(), k = %d, k); }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-26-2048.jpg)
![Introduction 21 3.4.2 Executing a ‘C’ program using gcc Open an editor like gedit, kwrite Type the c program and save it with the extension .c if no error(s) then type the command: ./a.out Open terminal and type command gcc filename.c Compiling a 'C' program using gcc: exploring a few switches The gnu C compiler is widely used because of its versatility (it can carry out preprocessing, compilation, assembly and linking) and also it has set unmatched standards in terms of reliability. The gnu C compiler actually works in stages. The stages are as follows: the Source Code is converted into Translation Unit the Translation Unit is converted into Assembly Code the Assembly Code is converted into Object Code the Object Code is converted into an Executable File. As an instance, if a program is saved by the name test57.c, then on issuing the command: gcc test57.c the intermediate stages might be visualized as follows: test57.c → test57.i → test57.s → test57.o → a.out The following switches can be used with the gcc command line in order to examine the intermediate stages: gcc –E test57.c (in order to obtain the Translation Unit equivalent. In short the –E option tells gcc to stop compilation after preprocessing) gcc –S test57.c (in order to obtain the Assembly Code) gcc –c test57.c (in order to obtain the Object Code). gcc test57.c (in order to obtain the executable file a.out) [NOTE: The options –E and –S are in uppercase] Let us consider the code snippet (saved in a file test57.c, for instance) shown below: #includestdio.h main() { printf(Computer Science); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-27-2048.jpg)
![Computer Concepts and Fundamentals of Programming 22 In order to examine the intermediate assembly language file, the following commands can be used. $ gcc -S test57.c $ cat test57.s will produce the intermediate assembly language listing of the above code snippet. The command $ gcc -o test test57.c makes an executable file by the name of test. In order to look at the output now, the user can type the following command at the command line: $./test instead of typing./a.out. The GNU Compiler Collection (gcc) can compile programs written in several high level languages such as FORTRAN, C, C++, Java, Objective-C, etc. In order to determine languages whose programs can be compiled using gcc, the Package Manager rpm* can be used as illustrated below: $ rpm -qa | grep gcc A sample interaction with rpm (using it as suggested above) might appear as follows: compat-gcc-34-g77-3.4.6-4 gcc-4.1.2-14.el5 gcc-gfortran-4.1.1-52.el5 compat-gcc-34-c++-3.4.6-4 gcc-java-4.1.1-52.el5 compat-gcc-34-3.4.6-4 gcc-c++-4.1.1-52.el5 compat-libgcc-296-2.96-138 libgcc-4.1.2-14.el5 gcc-objc-4.1.1-52.el5 *rpm is a package manager which can be used to build, install, update, query and erase individual software packages. [N.B. gcc used to be the GNU 'C' Compiler, but is now used for GNU Compiler Collection.] In order to compile the program, the following instruction needs to be typed: gcc program-name.c -trigraphs To find out the version of gcc, one can use gcc -v The gdb utility in Linux gdb (GNU debugger) is an efficient utility for debugging a program that has been compiled by gcc (GNU compiler collection). In order to start gdb the user is only required to type gdb and press ENTER at the command line (although there are many alternatives of starting gdb). Let us understand using gdb through a sample program (Program listing one) Program listing one](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-28-2048.jpg)
![Introduction 23 #includestdio.h main() { double num1, num2, quot; printf(Enter the numerator: ); scanf(%lf, num1); printf(Enter the denominator: ); scanf(%lf, num2); quot=num1/num2; printf(n%lf/%lf=%lf, num1, num2, quot); return 0; } Suppose the above program is stored in a file by the name of test.c. In order to compile the program, the user may type: $ gcc -g test.c -o test It may not be meaningful to use gdb by compiling the program without the -g switch, since gdb will not have information related to variable names, function names, line numbers, etc. Once the program is compiled, the user can type $ gdb test Now, in order to run the program, the user can type run (or r) at the gdb prompt and press ENTER. [NOTE: The user can also type gdb -quiet test or gdb -q test in order to suppress the introductory and copyright messages which are displayed when gdb is invoked.] In order to list the program, the user can type list (or l) at the gdb prompt and press ENTER. In order to set a breakpoint at line number 10, the user can type b 10 at the gdb prompt and press ENTER. Function name can also be used for setting a breakpoint at the first executable statement within the function. After pausing at the indicated line, the user can type continue (or c) in order to continue executing the program. The breakpoint(s) can be deleted through the delete command. Once a breakpoint has been set, then the commands n (for next) and s (for step) can also be used to execute the next line of the program. The commands n and s work differently if the next line happens to be a function call. If n is used then the next pause will be at the statement following the function call, whereas, if s is used then the next pause will be at the first line of the function which is invoked. The bt command can be used for printing the current location within the program and the stack trace showing how the current location was reached if a function calls another function or itself i.e. there has been a series of function calls. The kill command can be used in order to terminate the program being executed in gdb. The help command can be typed at the gdb prompt if the user feels stuck anywhere. If the user wants to quit the gdb utility then the user should type q and press ENTER.](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-29-2048.jpg)

![Data types and operators 27 A sample output is shown below: Enter an integer: 786 The integer you entered is: 786 Sample Program 4.4 Obtaining a fractional number as input from the user: #includestdio.h main() { float num; printf(Enter a fractional value: ); scanf(%f, num); printf(nThe fractional value you entered is: %f, num); return 0; } A sample output is shown below: Enter a fractional value: 0.34 The fractional value you entered is: 0.340000 The sizeof() operator [sizeof() is an unary operator] in C can be used to determine the size (in bytes) of a variable, constant or datatype. Sample Program 4.5 #includestdio.h main() { printf(nsizeof(0.93) = %d, sizeof(0.93)); printf(nsizeof(0.93f) = %d, sizeof(0.93f)); printf(nsizeof(71) = %d, sizeof(71)); printf(nsizeof(71L) = %d, sizeof(71L)); /*lowercase L can also be used*/ return 0; } Obtaining a string as input from the user: Sample Program 4.6 #includestdio.h main() { char name[80]; printf(Enter your name: ); scanf(%s, name); printf(nThe name you entered is: %s, name); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-33-2048.jpg)
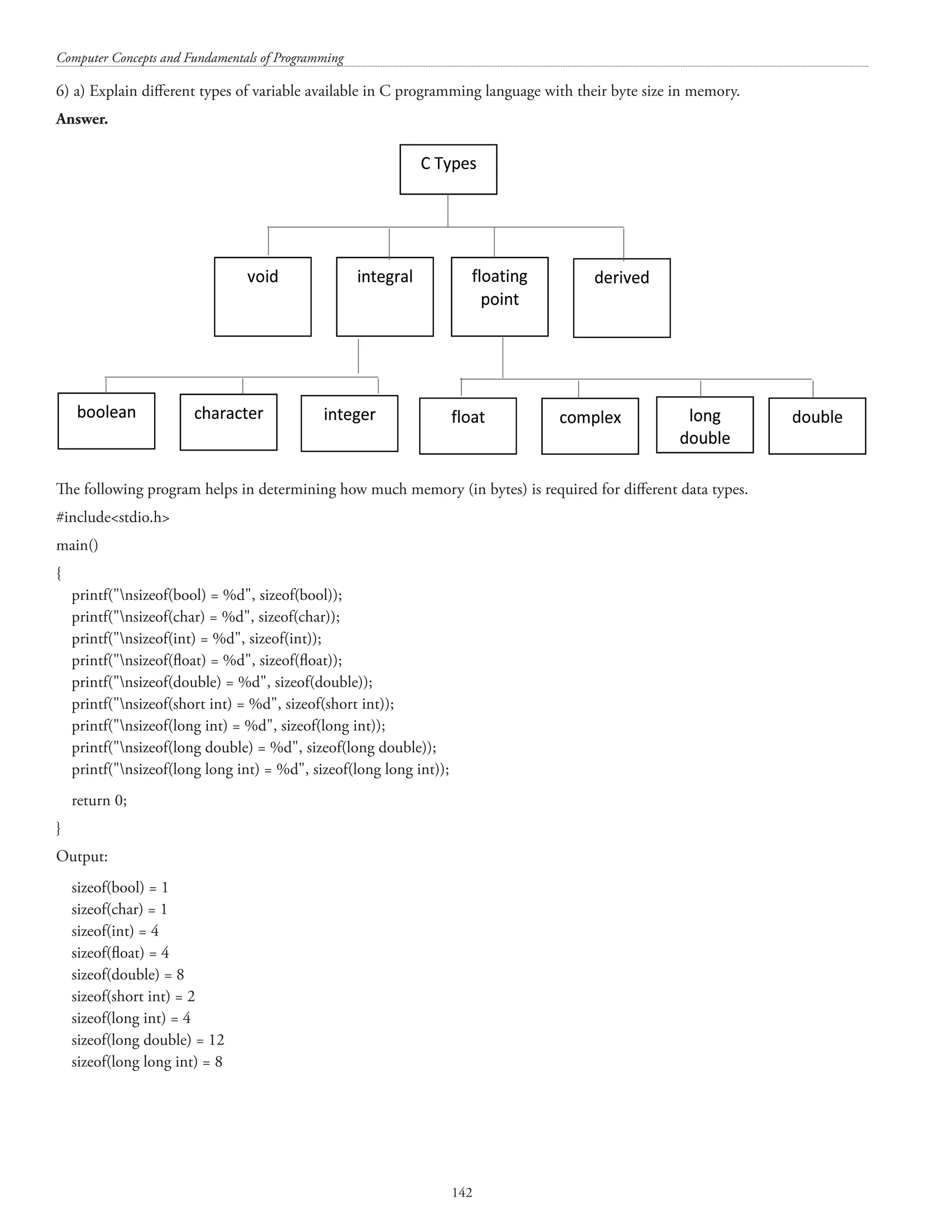
![Computer Concepts and Fundamentals of Programming 28 Enter your name: Ganesh Ingle The name you entered is: Ganesh When reading a string through scanf(%s, name); The scanf() stops reading after the first whitespace (tab, space or Enter). Therefore Ingle was not stored in name. In order to read blank spaces into a string variable, the scanf() function can be used as illustrated below: Sample Program 4.7 #includestdio.h main() { char name[81]; printf(nEnter your name: ); scanf(%[^n]s, name); /* whatever you type before pressing the ENTER key will be stored in name*/ printf(nYou entered: %s, name); return 0; } Enter your name:Ganesh Ingle You entered: Ganesh Ingle Sample program 4.8 /* Program illustrating the use of sizeof() operator */ #includestdio.h main() { printf(nsizeof(char) = %d, sizeof(char)); printf(nsizeof(int) = %d, sizeof(int)); printf(nsizeof(float) = %d, sizeof(float)); printf(nsizeof(double) = %d, sizeof(double)); printf(nsizeof(long int) = %d, sizeof(long int)); return 0; } sizeof(char) = 1 sizeof(int) = 4 sizeof(float) = 4 sizeof(double) = 8 sizeof(long int) = 4 sample program 4.9: The program below exemplifies the use of long long in 'C' langauage. Program listing #includestdio.h main() { long long n=1; /* The range of long long is from –9,223,372,036,854,775,808 to 9,223,372,036,854,775,807 */ int i;](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-34-2048.jpg)



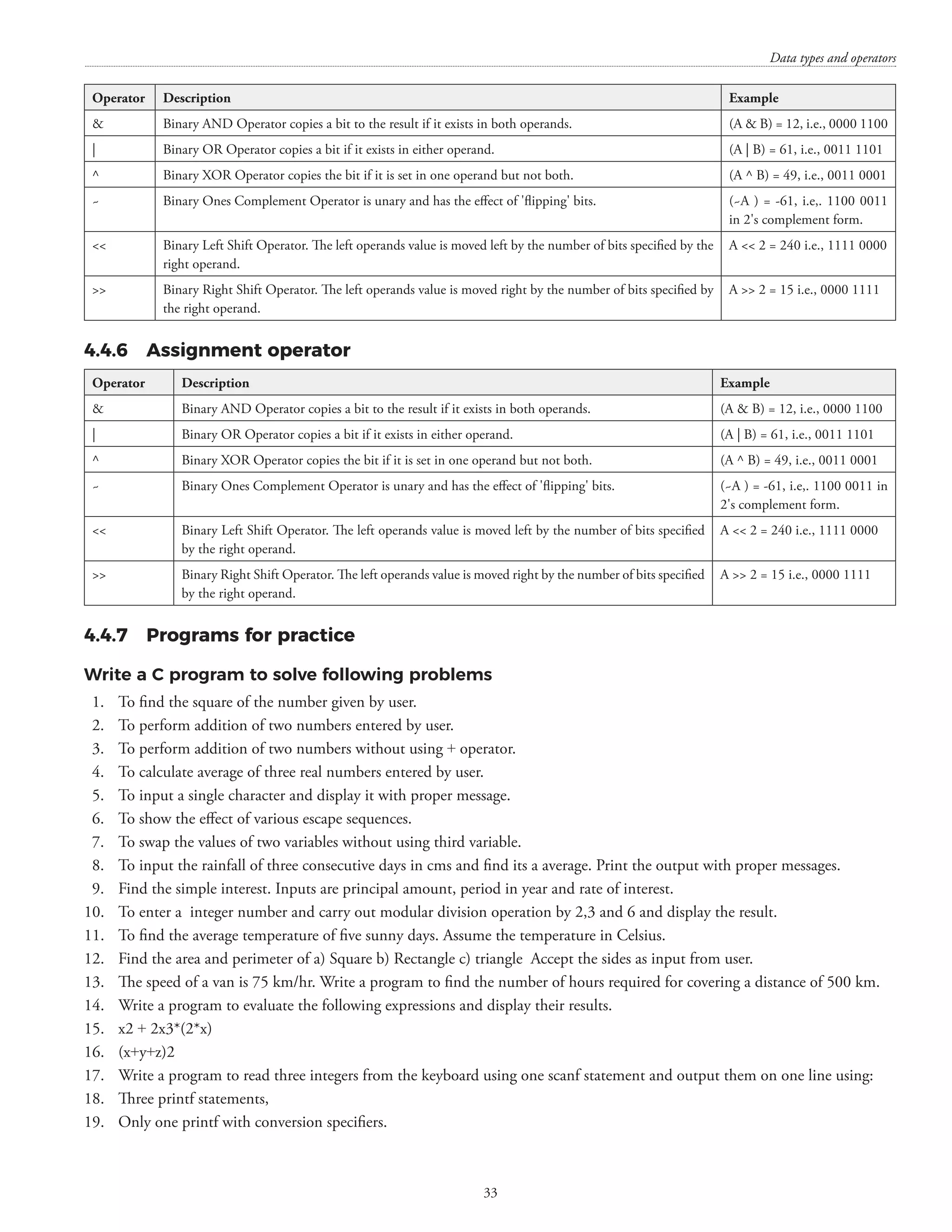










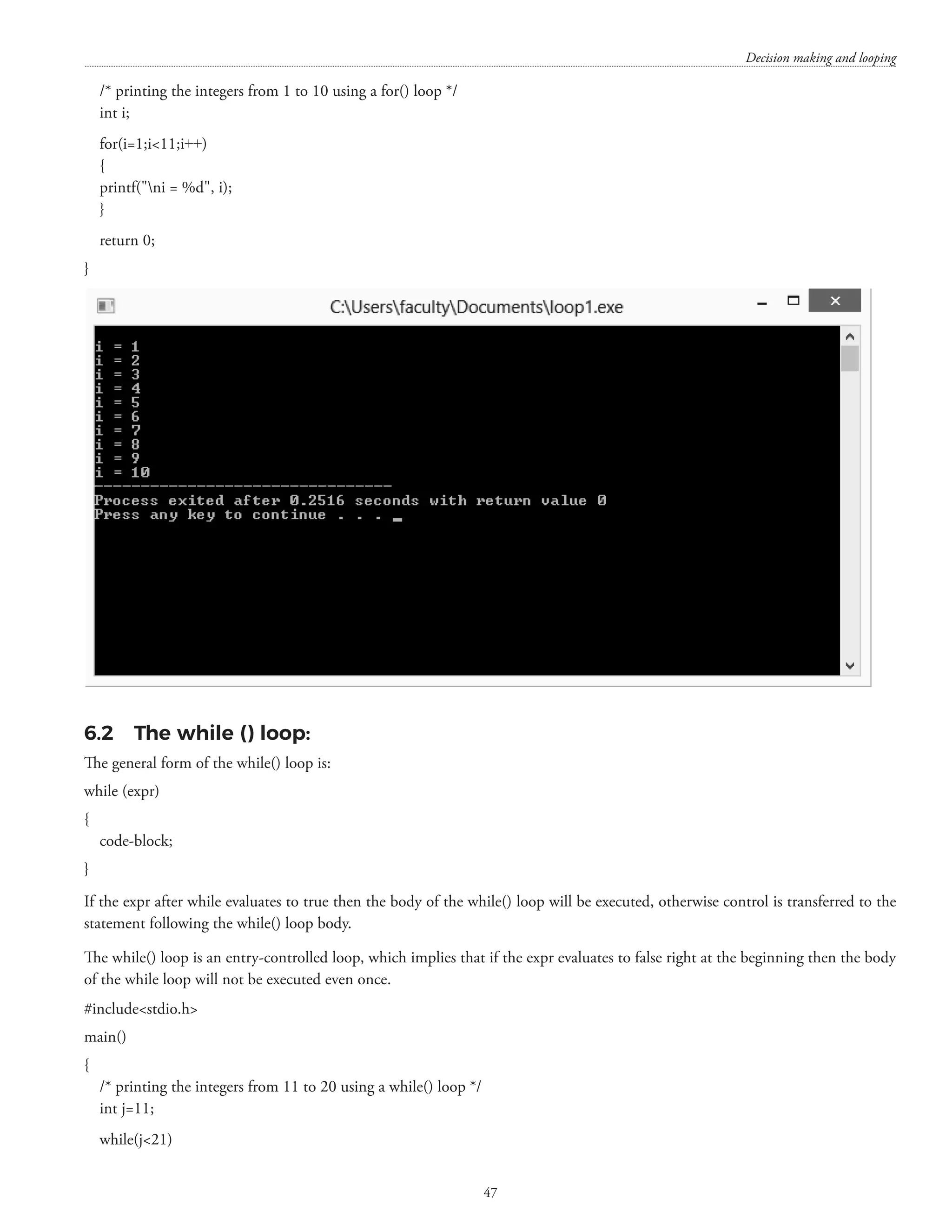
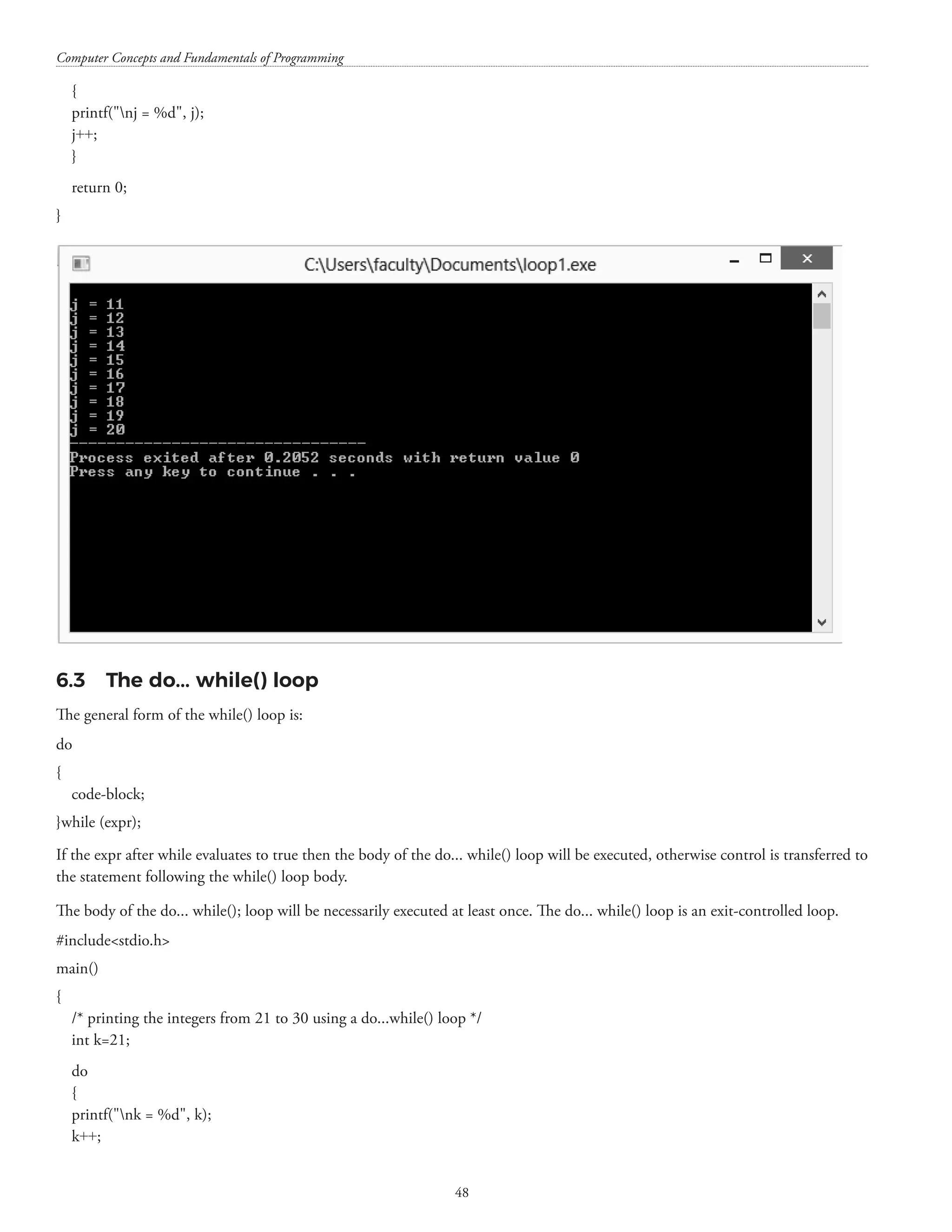
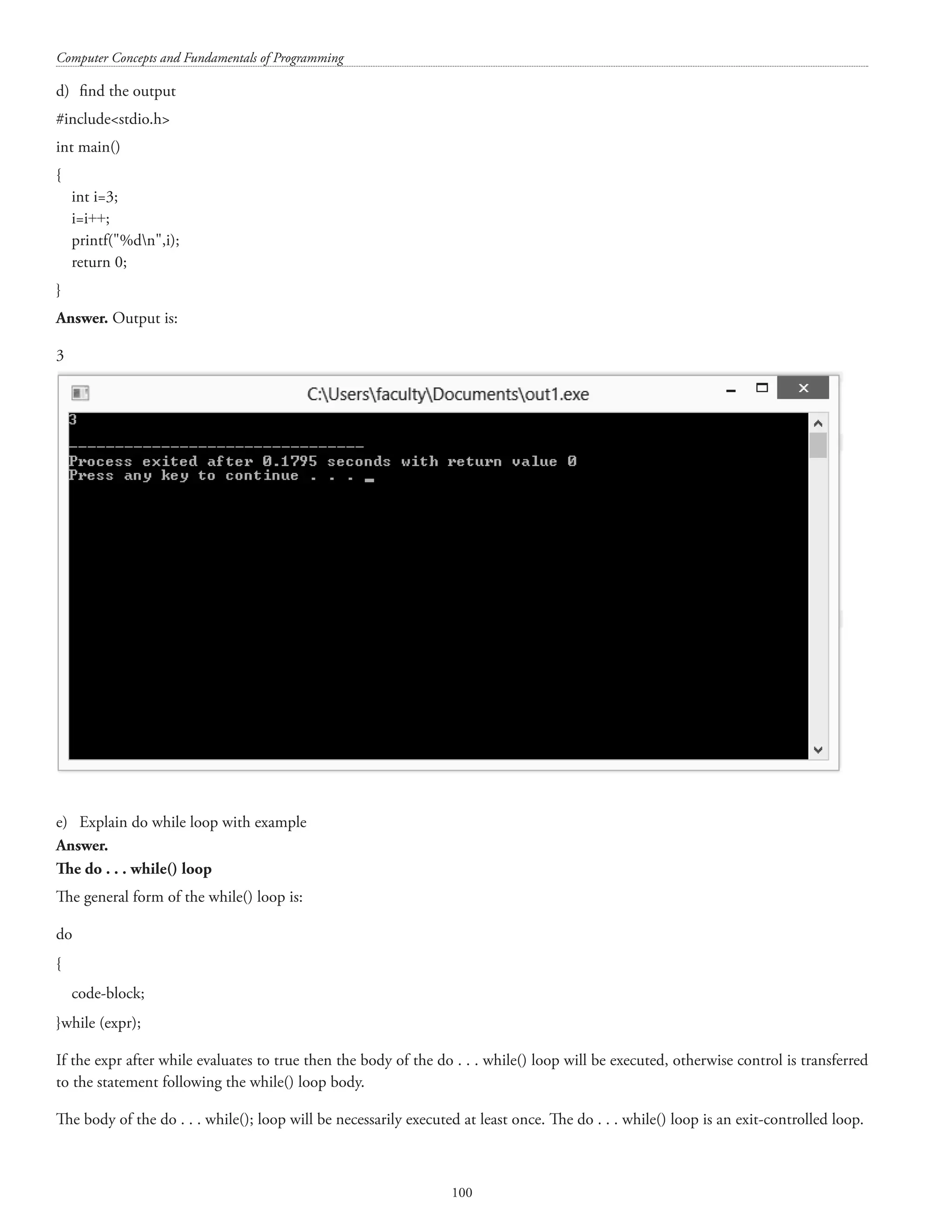
![CHAPTER – 6 DECISION MAKING AND LOOPING 6.1 The for() loop The for() loop can be used for executing a statement/statements a specific (or infinite) number of times. The general form of the for() loop is as follows: for(expr1; expr2; expr3) { code block; } expr1 is executed only once when the for() loop is executed for the first time. expr2 is evaluated every time before entry into the loop till the time it does not evaluate to false. expr3 is evaluated every time except for the first time. The for() loop is an entry-controlled loop. Different constructs of for loop (these syntax are correct syntax) • for( ;condition;) { Increment / decrement; } • for(i=0,j=0,k=100; i=200;i++,j++,k++) { } • for(;i10;i++ ) { } • for(;i10;i++ ); { } [N.B.: These programs have been executed using Dev-C++ Version 5.11] #includestdio.h main() {](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-52-2048.jpg)







![CHAPTER – 7 ARRAYS 7.1 Arrays Suppose we want to obtain 10 integer values, perform mathematical or other operations on them and then print the results, then we might require ten integer variables: var1, var2, var3,... , var10, for instance. Several programming languages provide the concept of arrays which help in reducing the number of variables because of a common name and indices for referencing individual elements. Let us consider an example: #includestdio.h main() { int num[10]; int i; printf(nNow obtaining 10 integer values: n); for(i=0;i10;i++) { printf(Enter %dth integer: , i); scanf(%d, num[i]); } printf(nThe 10 integer values which you entered are as follows:); for(i=0;i10;i++) printf(nnum[%d] = %d, i, num[i]); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-65-2048.jpg)
![Computer Concepts and Fundamentals of Programming 60 A sample interaction with the program might appear as follows: How arrays are stored in memory? The declaration int num[10]; indicates to the ‘C’ compiler that memory is to be reserved (continuous locations) for storing 10 integer values. The locations are individually identified as num[0], num[1], num[2],... , num[9]. If an integer requires 4 bytes for storage, and if the first integer is being stored in locations identified as 2358932, 2358933, 2358934, 2358935; then the second integer would be stored in the locations: 2358936, 2358937, 2358938 and 2358939. In the diagram below, the numbers on the right indicate the address of the individual array elements. num[0] 2358932 num[1] 2358936 num[2] 2358940 num[3] 2358944 num[4] 2358948 num[5] 2358952 num[6] 2358956 num[7] 2358960 num[8] 2358964 num[9] 2358968 A few important points pertaining to arrays: If an array is declared as:](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-66-2048.jpg)
![Arrays 61 int num[10]; (i) then the first element of the array will be referred to as num[0] and the last element of the array will be referred to as num[9]; (ii) If an array is declared as a global array [above main() ], then (a) It will be initialized with NULL values in case it is a char type array (b) It will be initialized with 0 (zero) in case it is a numeric array (iii) If an array is declared as a static array, then (a) It will be initialized with NULL values in case it is a char type array (b) It will be initialized with 0 (zero) in case it is a numeric array (iv) If a numeric type array is partially initialized at the place where it is declared, then the rest of the elements are automatically set to zero. (v) An array name is a pointer to itself. Thus num[0] and num would be the same. Two-dimensional arrays A declaration such as: int num[4][5]; creates an array of 4 rows and 5 columns and might be visualized as follows: Col 0 Col 1 Col 2 Col 3 Col 4 Row 0 Row 1 Row 2 Row 3 The individual elements might be accessed as follows: num[0][0] num[0][1] num[0][2] num[0][3] num[0][4] num[1][0] num[1][1] num[1][2] num[1][3] num[1][4] num[2][0] num[2][1] num[2][2] num[2][3] num[2][4] num[3][0] num[3][1] num[3][2] num[3][3] num[3][4] The program below demonstrates how to enter values into a two-dimensional array and then print the values. #includestdio.h #define ROWS 3 #define COLS 4 main() { int mat[ROWS][COLS]; int i, j; printf(nNow obtaining integers for %d X %d matrix:n, ROWS, COLS); for(i=0;iROWS;i++)](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-67-2048.jpg)
![Computer Concepts and Fundamentals of Programming 62 { for(j=0;jCOLS;j++) { printf(Enter integer for %dth row and %dth column: ,i,j); scanf(%d, mat[i][j]); } } printf(nThe matrix is as follows:n); for(i=0;iROWS;i++) { for(j=0;jCOLS;j++) { printf(%8d, mat[i][j]); } printf(n); } printf(nThe addresses of the matrix elements are as follows:n); printf(nAddress (matrix element)n); for(i=0;iROWS;i++) { for(j=0;jCOLS;j++) { printf(%u (%d) , mat[i][j], mat[i][j]); } printf(n); } return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-68-2048.jpg)
![Arrays 63 A sample output is shown below: Sample program 7.1 Program to illustrate matrix multiplication of two matrices of same order Matrix multiplication #include stdio.h main() { int m, n, p, q, c, d, k, sum = 0; int first[10][10], second[10][10], multiply[10][10]; printf(Enter the number of rows and columns of first matrixn); scanf(%d%d, m, n); printf(Enter the elements of first matrixn); for ( c = 0 ; c m ; c++ ) for ( d = 0 ; d n ; d++ ) scanf(%d, first[c][d]); printf(Enter the number of rows and columns of second matrixn); scanf(%d%d, p, q); if ( n != p ) printf(Matrices with entered orders can't be multiplied with each other.n); else { printf(Enter the elements of second matrixn); for ( c = 0 ; c p ; c++ )](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-69-2048.jpg)
![Computer Concepts and Fundamentals of Programming 64 for ( d = 0 ; d q ; d++ ) scanf(%d, second[c][d]); for ( c = 0 ; c m ; c++ ) { for ( d = 0 ; d q ; d++ ) { for ( k = 0 ; k p ; k++ ) { sum = sum + first[c][k]*second[k][d]; } multiply[c][d] = sum; sum = 0; } } printf(Product of entered matrices:-n); for ( c = 0 ; c m ; c++ ) { for ( d = 0 ; d q ; d++ ) printf(%dt, multiply[c][d]); printf(n); } } } Sample program 7.2 Write a first category function program to read a two matrices A and B of order 9x9 and print the following. a)A+B and b)A-B #includestdio.h main() { int a[3][3],b[3][3],c[3][3],i,j; printf(Enter the First 3x3 Matrix: ); for(i=0;i3;i++) { for(j=0;j3;j++) scanf(%d,a[i][j]); } printf(Enter the Second 3x3 Matrix: ); for(i=0;i3;i++) { for(j=0;j3;j++) scanf(%d,b[i][j]); } printf(nThe Sum of Matrices is: ); for(i=0;i3;i++)](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-70-2048.jpg)
![Arrays 65 { printf(n); for(j=0;j3;j++) { c[i][j]=a[i][j]+b[i][j]; printf(%d ,c[i][j]); } } printf(nnThe Difference of Matrices is: ); for(i=0;i3;i++) { printf(n); for(j=0;j3;j++) { c[i][j]=a[i][j]b[ i][j]; //2 mark printf(%d ,c[i][j]); } } } Sample program 7.3 Write a program that will put 8 queens on a Chessboard so that no queen can capture another. The size of the board is 8 x 8. One queen can capture another if it is standing in the same row (horizontal), or in the same column (vertical), or on the same diagonal as the other queen. #includestdio.h #includemath.h int a[30],count=0; int place(int pos) { int i; for(i=1;ipos;i++) { if((a[i]==a[pos])||((abs(a[i]a[pos])==abs(ipos)))) return 0; } return 1; } void print_sol(int n) { int i,j; count++; printf(nnSolution #%d:n,count);](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-71-2048.jpg)
![Computer Concepts and Fundamentals of Programming 66 for(i=1;i=n;i++) { for(j=1;j=n;j++) { if(a[i]==j) printf(Qt); else printf(*t); } printf(n); } } void queen(int n) //1 mark { int k=1; a[k]=0; while(k!=0) { a[k]=a[k]+1; while((a[k]=n)!place(k)) //1 mark a[k]++; if(a[k]=n) //1 mark { if(k==n) print_sol(n); else { k++; a[k]=0; //1 mark } } else k; } } main() //1 mark { int i,n; printf(Enter the number of Queensn); scanf(%d,n);](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-72-2048.jpg)
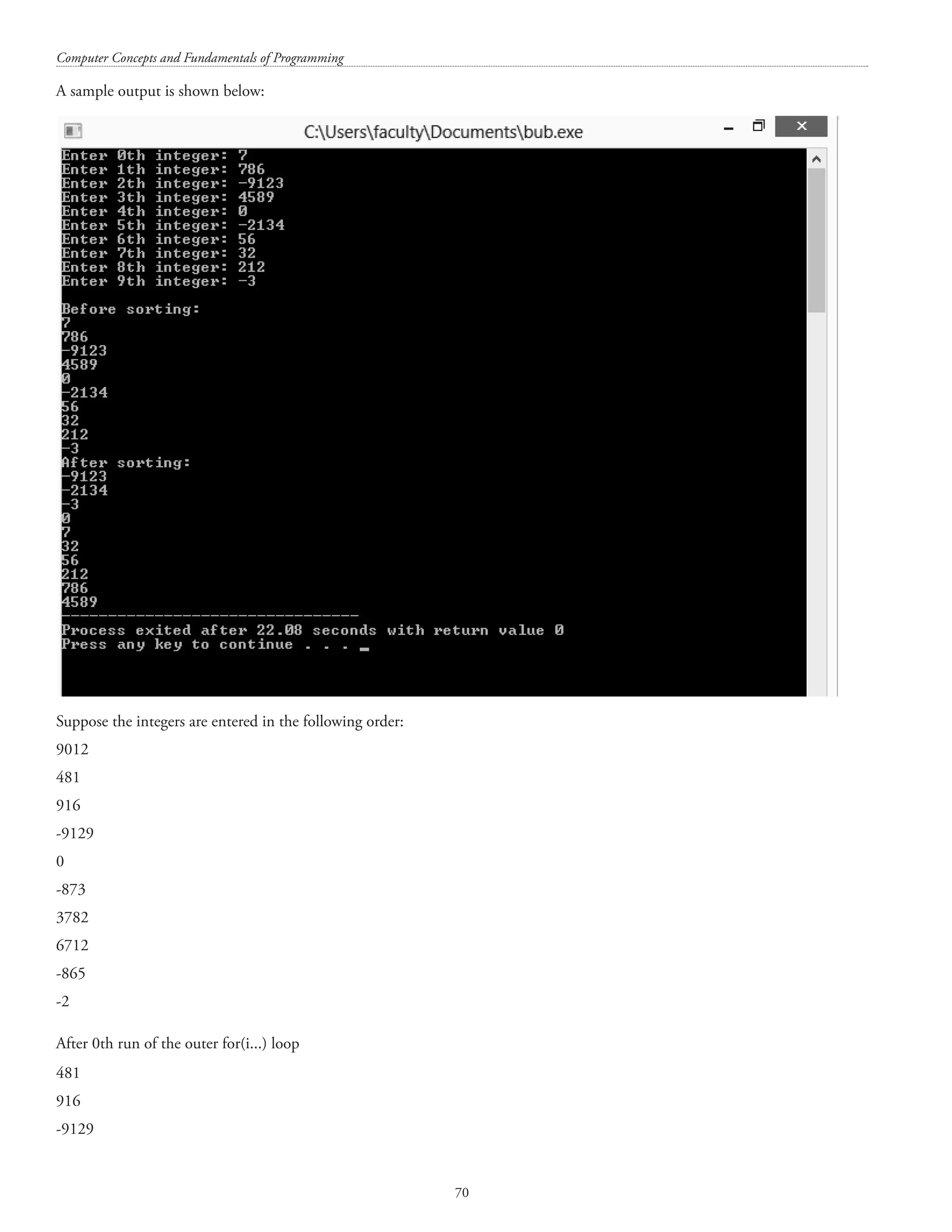
![Arrays 67 queen(n); printf(nTotal solutions=%d,count); } Selection Sort In Selection Sort, the element at the zeroth position is compared with all the elements below it and an interchange performed as and when required (depending on whether the elements have to be arranged in ascending or descending order). Thereafter, the element at the first position is compared with all the elements below it and an interchange performed as and when required. Similarly, the elements at the second, third,... position are compared with all the elements below them and an interchange performed as and when required. The program below is an implementation of Selection Sort: #includestdio.h #define SIZE 10 main() { int array[SIZE]; int i, j, t; printf(nNow obtaining %d integers: n, SIZE); for(i=0;iSIZE;i++) { printf(Enter %dth integer: , i); scanf(%d, array[i]); } printf(nnBefore sorting:); for(i=0;iSIZE;i++) printf(n%d, array[i]); for(i=0;iSIZE-1;i++) { for(j=i+1;jSIZE;j++) { if(array[i]array[j]) { t=array[i]; array[i]=array[j]; array[j]=t; } } } printf(nnAfter sorting:); for(i=0;iSIZE;i++) printf(n%d, array[i]); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-73-2048.jpg)
![Computer Concepts and Fundamentals of Programming 68 A sample output is shown below: Bubble sort In Bubble sort two successive elements are compared with each other and an interchange performed as and when required (depending on whether sorting is required in ascending or descending order). #includestdio.h #define SIZE 10 main() { int num[SIZE]; int i, j; int t; for(i=0;iSIZE;i++) {](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-74-2048.jpg)
![Arrays 69 printf(Enter %dth integer: , i); scanf(%d, num[i]); } printf(nBefore sorting: ); for(i=0;iSIZE;i++) printf(n%d, num[i]); for(i=0;iSIZE-1;i++) { for(j=0;jSIZE-1;j++) { if(num[j]num[j+1]) { t = num[j]; num[j]=num[j+1]; num[j+1]=t; } } } printf(nAfter sorting: ); for(i=0;iSIZE;i++) printf(n%d, num[i]); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-75-2048.jpg)




![CHAPTER – 8 STRINGS String functions in ‘C’ In ‘C’ language a string is an array of characters terminated by ‘0’ (the null character). Some of the most commonly used string functions in ‘C’ are: strcat(): for concatenating two strings, strchr(): used for locating the first occurrence of the character (second argument) in the string (first argument), strcmp(): used for comparing two strings, strcpy(): used for copying the string contained as the second argument to the function, in the first argument to the function, strncpy(): used for avoiding buffer overflow when copying, strlen(): for computing the length of the string, strncat(): for appending n bytes, strlwr(): for converting a string to lowercase strupr(): for converting a string to uppercase The programs below demonstrate the use of a few string functions. #includestdio.h #includestring.h main() { char str[80]; printf(nEnter any string:); scanf(%[^n], str); printf(nstr = %s, str); printf(nstrlwr(str) = %s, strlwr(str)); printf(nstrupr(str) = %s, strupr(str)); printf(nstrlen(str) = %d, strlen(str)); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-81-2048.jpg)
![Computer Concepts and Fundamentals of Programming 76 A sample output is shown below: #includestdio.h #includestring.h main() { char str1[] = Sky is the limit; char str2[] = Sky is Not the limit; char str3[80] = ; int result; printf(nnstr1 = %s, str1); printf(nnstr2 = %s, str2); printf(nnstr3 = %s, str3); strcpy(str3, str2); /*strcpy(destination, source)*/ printf(nnAfter copying str2 to str3, str3 = %s, str3); result = strcmp(str1, str2); /* strcmp(str1, str2) returns a value 0 if str1 alphabetically precedes str2, strcmp(str1, str2) returns a value 0 if str2 alphabetically precedes str1, strcmp(str1, str2) returns 0 if str1 is exactly the same as str2 */ printf(nnOn comparing str1 and str2, result = %d, result); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-82-2048.jpg)
![Strings 77 A sample output is shown below: const char* strstr(const char *str1, const char *str2); The strstr() function returns a pointer to the first occurrence of str2 in str1, or a null pointer if str2 is not a subset of str1. A program illustrating the use of strstr() follows: #includestdio.h #includestring.h main() { char str1[] = Sky is the limit; char *result; printf(nnstr1 = %s, str1); result= strstr(str1, the); printf(nnresult = %s, result); result= strstr(str1, star); printf(nnresult = %s, result); return 0; } A sample output is shown below: str1 = Sky is the limit result = the limit result = (null)](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-83-2048.jpg)







![Pointers 85 int *p; p can hold the address of a int variable only. int a; p=a; 10.6 Benefits of pointers • Reduces the storage space • Execution using pointer is faster (i.e) Reduces the execution time of the program • Memory is dynamically allocated, allows us to resize the dynamically allocated memory block 10.7 Arrays and Pointers Array and pointers are closely related with each other. The name of an array without a subscript (index number) is a pointer constant. When the name is used without the subscript it references the address of element 0 of the array. int myarray[10]; /* Declare an array */ int *myptr; /* Declare a pointer (not initialized)*/ printf (“%dn”, myarray); /* print address of myarray[0] */ scanf (“%d”,myarray[0]); /* get value from keyboard and store in myarray[0] */ myptr = myarray[2]; /* Assign the address of the third element of myarray to myptr*/ printf(“%d”, *myptr); /* Print the value of what myptr is pointing to, i.e., the value of myarray[2] */ Note that the * in front of myptr de-references the pointer. That is, it says “use the value in the address that is pointed to.” Sample Program 10.2 /* Printing array values and addresses */ #include stdio.h int main ( ) { int k; float a[4] = {100, 200, 300, 400}; for (k=0; k4; k++) printf (%d %ld %ld %fn, k, a, a[k], a[k]); } 10.8 Pointer Arithmetic Arithmetic operations can be performed on pointers, but only limited operations can be performed on pointers. A pointer may be: • incremented ( ++ ) • decremented ( — ) • an integer may be added to a pointer ( + or += ) • an integer may be subtracted from a pointer ( – or -= ) • Pointer comparison ( , == , ) °° See which pointer points to the higher numbered array element °° Also, see if a pointer points to 0 • Pointers of the same type can be assigned to each other](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-91-2048.jpg)
![Computer Concepts and Fundamentals of Programming 86 • Operations meaningless unless performed on an array • addition, multiplication and division operations on two pointer variables cannot be performed Data Type Initial Address Operation Address after Operations Required Bytes int 4000 ++ 4002 2 int 4000 -- 3998 2 char 4000 ++ 4001 1 char 4000 -- 3999 1 float 4000 ++ 4004 4 float 4000 -- 3996 4 long 4000 ++ 4004 4 long 4000 -- 3996 4 Expression Result Address + number Address Address - number Address Address - Address Number Address + Address Illegal Note: The value by which the address of the pointer variable will increment/ decrement is not fixed. It depends upon the data type of the pointer variable. Sample program 10.3 /*program to find sum of all elements stored in an array */ #includestdio.h #includeconio.h main () { int a [5] ={5,10,15,20,25}; int i, sum=0,*p; p = a; for (i = 0; i5; i++) { sum = sum+(*p); p++; } printf (the sum is % d, sum); getch (); } Output the sum is 75 Sample program 10.4 Palindrome string #includestdio.h #includestring.h int main()](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-92-2048.jpg)
![Pointers 87 { char str[30]; char *p,*t; printf(Enter any string: ); gets(str); for(p=str ; *p!=NULL ; p++); for(t=str, p-- ; p=t; ) { if(*p==*t) { p--; t++; } else break; } if(tp) printf(nString is palindrome); else printf(nString is Not palindrome); } Sample program 10.5 Write a program to compare two string using pointers.(Note: Do not use strcmp function) #includestdio.h int compare_string(char*, char*); main() { char first[100], second[100]; int result; printf(Enter first stringn); gets(first); printf(Enter second stringn); gets(second); result = compare_string(first, second); if ( result == 0 ) printf(Both strings are same.n); else printf(Entered strings are not equal.n); } int compare_string(char *first, char *second) { while(*first==*second)](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-93-2048.jpg)

![CHAPTER – 11 STRUCTURES AND UNIONS 11.1 Introduction Structure is a user-defined datatype in C language. A structure is used to represent a group of data items of different datatype, whereas array is the group of similar data items i.e data items of same datatype. Structures are used to handle a group logically related data items. For example to keep track of student details, the following a set of attributes about a student may be used: name, roll_no, marks and gender. Structures can be used to organize these complex data in a useful way. Defining a Structure Unlike predefined datatypes, structures must be first defined for their format that may be later used for declaring the structure variables. The general format for defining a structure struct tag_name { datatype member 1; datatype member 2; ------------ datatype member m; }; In this definition, struct is a required keyword, tag is a name that identifies structures of this type. It should be terminated with a semicolon. Each member should be independently declared for its name and type. For example consider a student database consisting of name, roll_no, marks and gender, a structure can be defined as follows struct student { char name [30]; int roll_no; float marks; char gender; }; Student is a user-defined datatype and variables of this type can be declared and used in the program. Declaring a structure variable](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-95-2048.jpg)
![Computer Concepts and Fundamentals of Programming 90 After defining a structure, we can declare variables of that type. The general format of declaring structure variable struct tag_name struct_variable; example struct student s1,s2,s3; this statement declares s1,s2 and s3 as structure variables of type student. Each one of these variable have four members name, roll_no, marks and gender. C language allows to combine both the structure definition and variables declaration in one statement as follows struct student { char name [30]; int roll_no; float marks; char gender; }s1,s2,s3; Structure initialization struct student s1 = {“John”,780123,67.5,’m’}; struct student s2 = {“Priya”,780122,85.5,’f’}; Note: the order of values enclosed in braces must match the order of members in the structure definition. It is allowed to initialize first few members and leave the remaining blank. The uninitialized members should be only at the end of the list. For example struct student s2 = {“Priya”,780122}; /* initializes name and roll_no leaving marks and gender blank */ Accessing members of the structure The members of a structure are usually processed individually. Therefore, we must be able to access the individual structure members. A structure member can be accessed by (.) period operator struct_variable.member_name. The (.) operator is a member of the highest precedence group, and its associativity is left-to-right. Sample Program 1 struct student { char name [30]; int roll_no; float marks; char gender; }; main() { struct student s1; printf(“ enter the name of the student “); scanf(“%s”, s1.name);](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-96-2048.jpg)
![Structures and unions 91 printf(“ enter the roll_no of the student “); scanf(“%d”, s1.roll_no); printf(“ enter the gender of the student “); scanf(“%c”, s1.gender); s1.marks=75.5; /* the details of the student */ printf (“Name: %s”, s1.name); printf (“Roll no: %d”, s1.roll_no); printf (“ Gender: %c”, s1.gender); printf (“ Marks: %f”, s1.marks); } Arrays of structure If we have to maintain the details of more than one student then array of structures can be used. Array of structure may be declared as follows struct student s[50]; s is an array of 50 elements in which each element is of type struct student s[0].name /* refers to the name of the first student */ s[5].marks /* refers to the marks of the 6th student */ Sample Program 2 /* To read and print the details of 50 students and find if a student scored first class or not */ struct student { char name [30]; int roll_no; float marks; char gender; }; main() { struct student s[50]; int i; for(i=0;i50;i++) { printf(“ enter the name of the student “); scanf(“%s”, s[i].name); printf(“ enter the roll_no of the student “); scanf(“%d”, s[i].roll_no);](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-97-2048.jpg)
![Computer Concepts and Fundamentals of Programming 92 printf(“ enter the gender of the student “); scanf(“%c”, s[i].gender); printf(“ enter the marks of the student “); scanf(“%f”, s[i].marks); } /* the details of the student */ for(i=0;i50;i++) { printf (“Name: %s”, s[i].name); printf (“Roll no: %d”, s[i].roll_no); printf (“ Gender: %c”, s[i].gender); if(s[i]=60) { printf (“First class”); } } } Structure within Structure (Nested Structure) A structure can be nested inside another structure. In other words, the members of a structure can be of any other type including structure. The general format for nested structures structure tagname_1 { member1; member2; member3; structure tagname_2 member4; ... membern; }; Example struct date { int day; int month; int year; }; struct student {](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-98-2048.jpg)
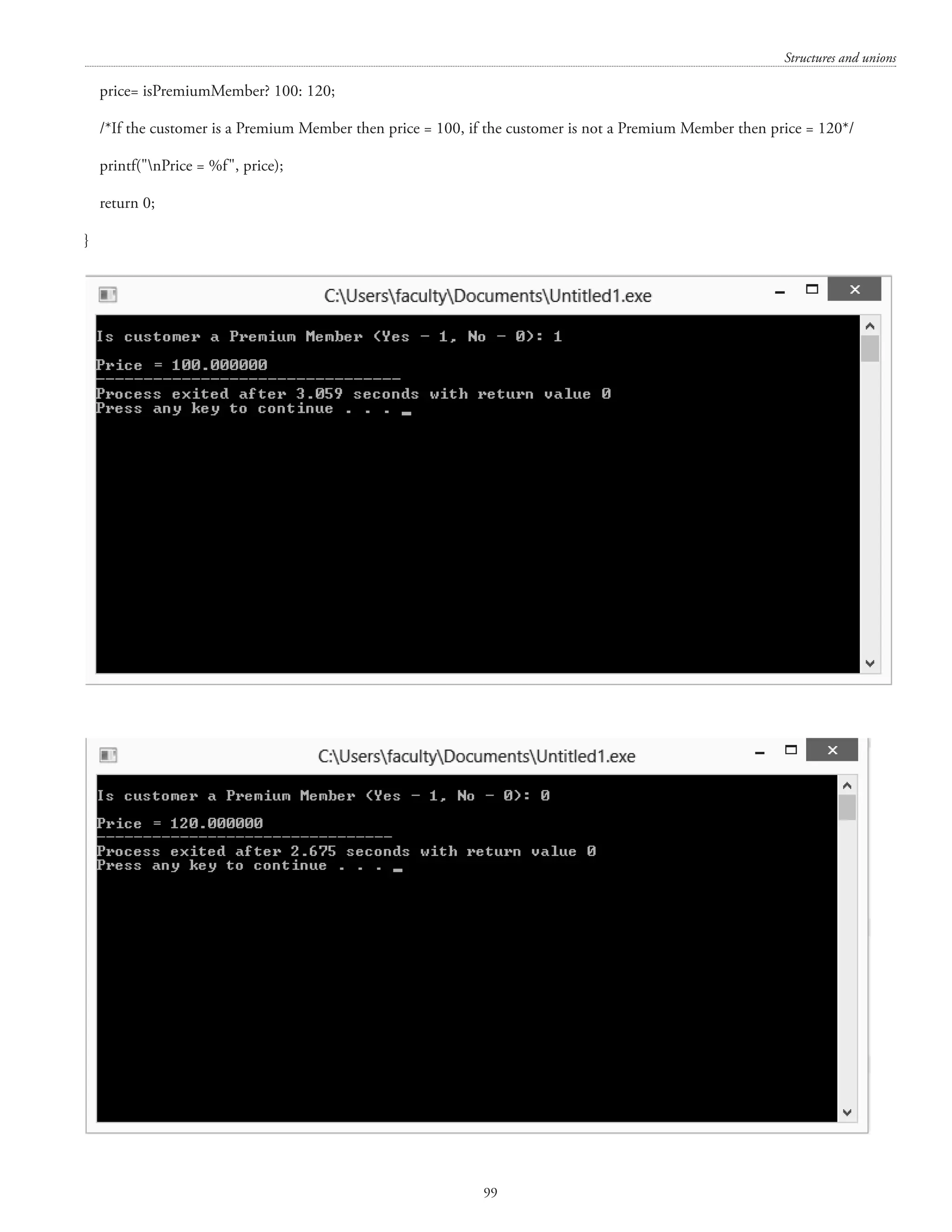
![Structures and unions 93 char name [30]; int roll_no; struct date dob; }; struct student s; The structure student has a member dob which itself is a structure with three members. The members in the inner structure can be referred as s.dob.day=25; s.dob.month=11; union A union is a user data type like structure that is used to handle different data types in a unit. Union follows the format of structure for definition of union, declaration of union variable and accessing of members union union_name { datatype member 1; datatype member 2; ------------ datatype member m; } [one or more union variables]; At the end of the union's definition, before the final semicolon, you can specify one or more union variables but it is optional. Otherwise you can later declare variable as follows union union_name var1,var2; To access any member of a union, the period operator (.) is to be used Example union subject { char name[50]; int subject_code; }; union subject s1 ={“computer science”, 2205}; /*union initialization */ union subject s2; /*declare union variable */ strcpy(s2.name,”mathematics”); /* access union member */ 11.3 Difference between structure and union The difference between structure and union is, union use less memory than structures. Each member of a structure is allotted separate memory space (ie) the size of structure in equal to the sum of size of all its members, whereas in case of union, size is equal to size of largest member. For example struct student { char name [30];](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-99-2048.jpg)
![Computer Concepts and Fundamentals of Programming 94 int roll_no; float marks; char gender; } s1; The structure variable s1 requires 37 bytes ( 30 for name, 2 for roll_no, 4 for marks and 1 for gender). Each member get separate memory location, so all can be used at a time. union student { char name [30]; int roll_no; float marks; char gender; } s2; The union variable s2 requires only 30 bytes, ie the size of largest member. But only one member can contain a value or used at any given time. Another example union subject { char name[50]; int subject_code; }; The union above could be used to either store name or subject_code at a particular time. Presumably there are times when you would want one or the other, but not both. #includestdio.h #includeconio.h union subject { char name[50]; int subject_code; }; void main() { union subject s; clrscr(); printf(Enter subject Name: ); scanf(%s,s.name); printf(The subject Name: %sn,s.name); printf(Enter subject code: ); scanf(%d,s.subject_code); printf(The subject code: %d,s.subject_code); }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-100-2048.jpg)
![Structures and unions 95 Output Enter subject Name: computer science The subject Name: computer science Enter subject code: 2205 The subject code: 2205 Appendix Opening a web browser via a ‘C’ program Is it possible to open a web page in a browser using a 'C' program? The program below provides an answer to the aforementioned question: Program listing one #includestdio.h main() { char url[25] = www.mail.yahoo.com; char launch[255]; system(clear); sprintf(launch, gnome-open %s, url); system(launch); return 0; } [NOTE: 1. The above code should be compiled on a Linux system. 2. Parallel methods for opening a web-browser are available for Windows/Mac OSs. For instance, on a Mac OS, system(“open http://url”); might be used.] An alternative method of opening a web page is given below: Program listing two #includestdio.h main() { char url[25] = www.iiml.ac.in; char launch[255]; system(clear); sprintf(launch, firefox %s, url); system(launch); return 0; } [Note: The code in Program listing two assumes that firefox is installed on the workstation and the appropriate PATH has been set.]](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-101-2048.jpg)






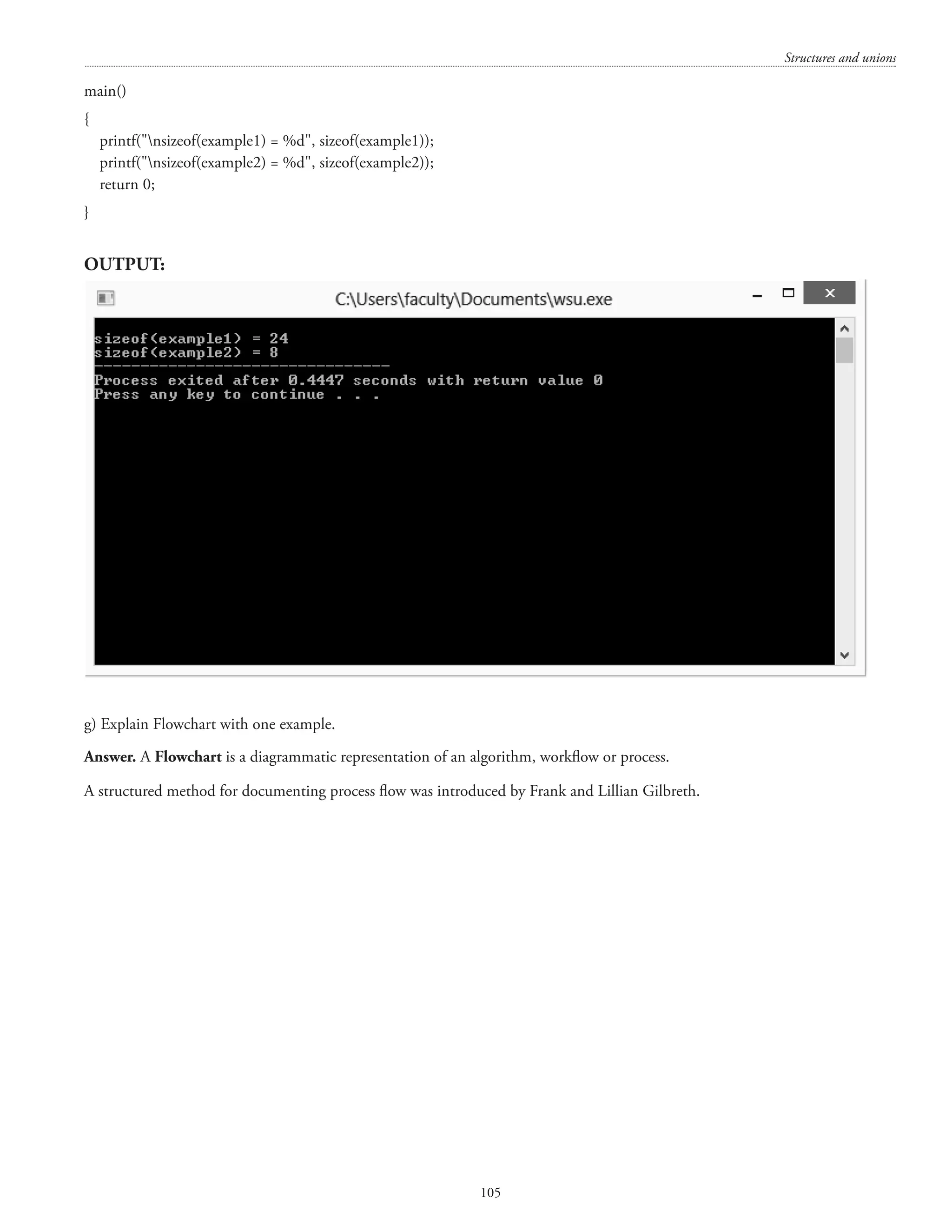
![Structures and unions 107 #includestdio.h main() { int num; printf(Enter an integer: ); scanf(%d, num); printf(nThe integer you entered is: %d, num); return 0; } A sample output is shown below: Enter an integer: 786 The integer you entered is: 786 i) Define Function and its advantages. Answer. A function in ‘C’ is an independent module which can be invoked for performing a particular task. When a function is called, then the control is transferred from the calling function to the called function and once the execution of the called function is over, the control returns to the calling function. [The programs hereafter in this section have been executed using Dev-C++ Version 5.11] #includestdio.h float sumfunc(float x, float y); main() { float num1, num2, sum; printf(nEnter first number: ); scanf(%f, num1); printf(nEnter second number: ); scanf(%f, num2); sum = sumfunc(num1, num2); function invocation or function call printf(nSum of %f and %f = %f, num1, num2, sum); return 0; } function declaration or function prototyping](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-113-2048.jpg)
![Computer Concepts and Fundamentals of Programming 108 float sumfunc(float x, float y) function header { float temp; temp = x + y; function body return temp; } OUTPUT: The function declaration: float sumfunc(float x, float y); contains three parts, namely, (i). type of return value from the function, (ii). name of the function, (iii). number and type of parameters being passed into the function. type of return value function name number and types of parameters being passed into the function float sumfunc(float x, float y); Advantages: (i) Programs can be divided into smaller, manageable segments. (ii) Functions help in reusing code which might be required more than once in a program. (iii) Functions can be used for protecting data. j) What is the Byte size of ‘char’ and ‘float’ in C. Answer. [The size of ‘char’ and ‘float’ is machine dependent and compiler dependent.] function definition](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-114-2048.jpg)
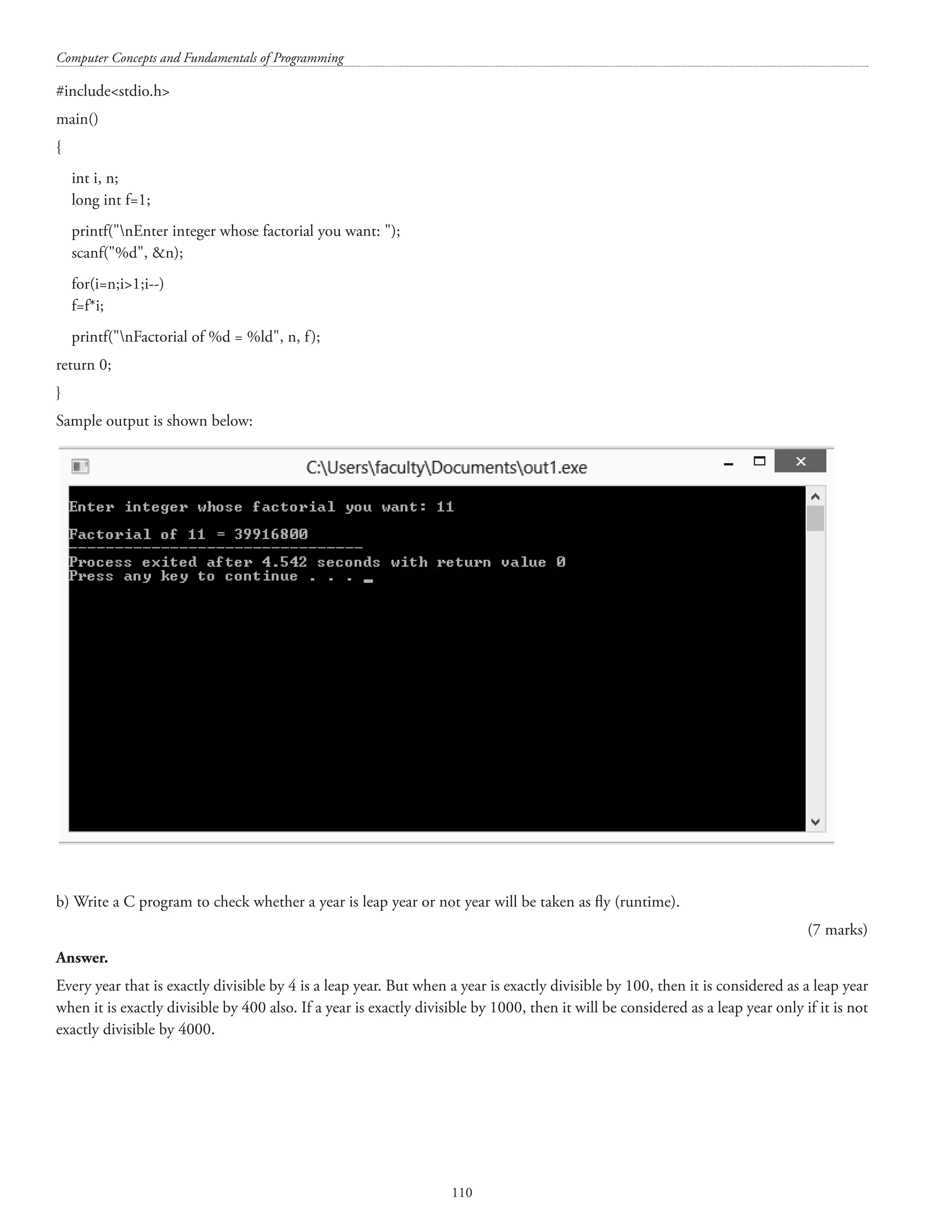
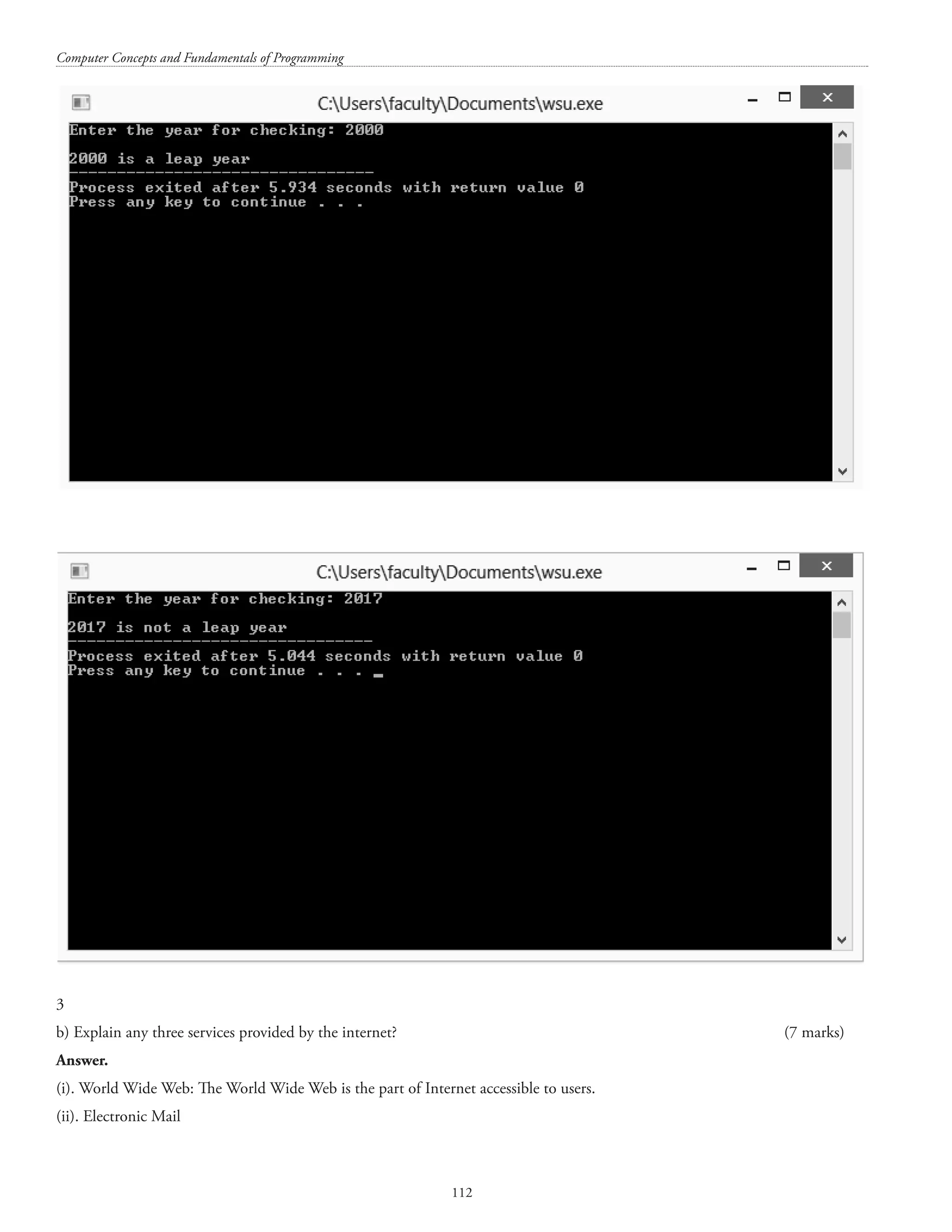
![Structures and unions 109 #includestdio.h main() { printf(nsizeof(char) = %d, sizeof(char)); printf(nsizeof(int) = %d, sizeof(int)); printf(nsizeof(float) = %d, sizeof(float)); printf(nsizeof(double) = %d, sizeof(double)); printf(nsizeof(long) = %d, sizeof(long)); printf(nsizeof(long double) = %d, sizeof(long double)); return 0; } Sample output is shown below: PART – B Marks: 5 X 14 = 70 (Answer any 5 of the following) 2. a) Write a C program to find the factorial of a number where number will be taken as fly (runtime) (7 marks) Answer. [N.B.: The phrase ‘on the fly’ implies something that is being changed while the process that is being affected by the change is being carried out/executed. Switching computer parts on the fly implies replacing parts of the computer while the computer is running.]](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-115-2048.jpg)


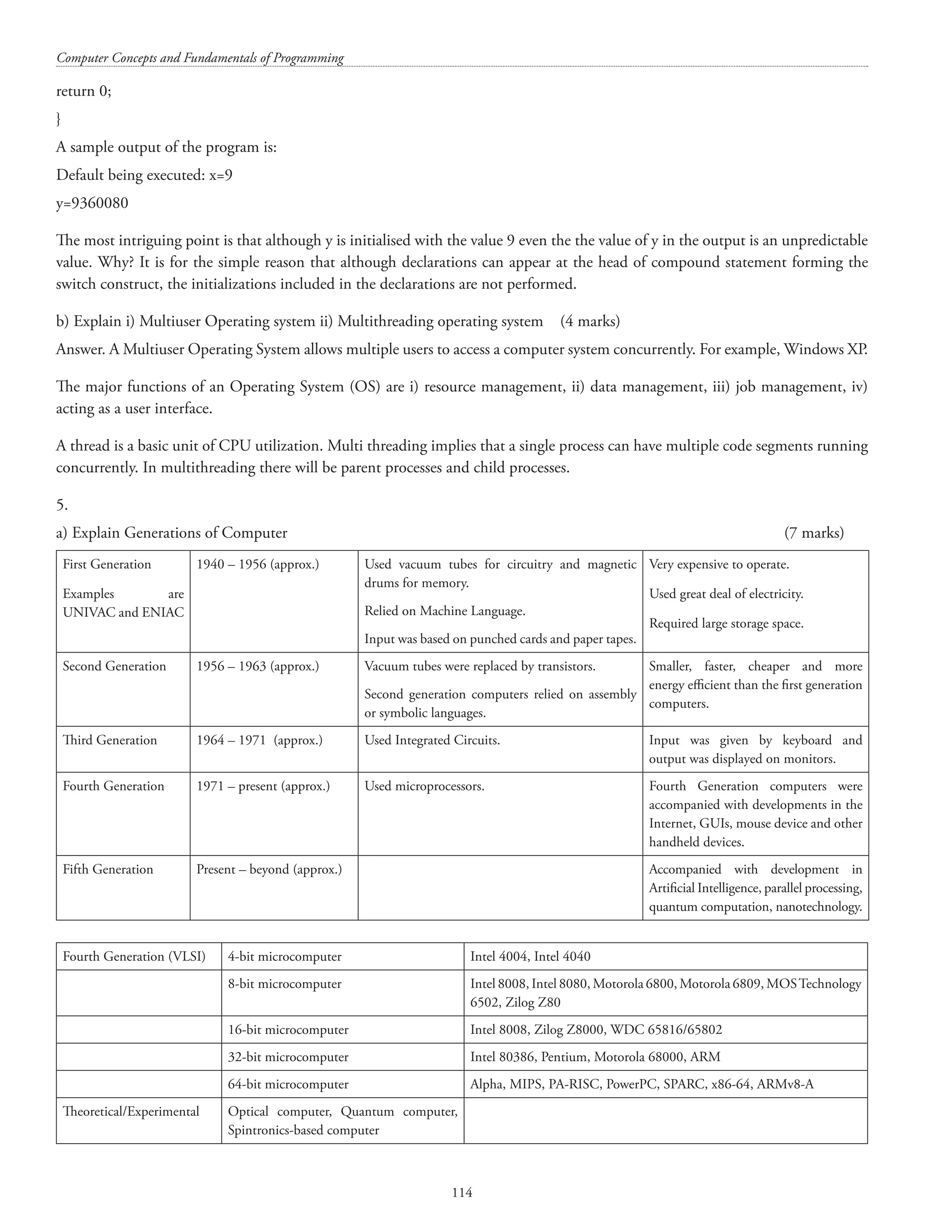
![Structures and unions 115 b) Write a Program in C to find the Transpose of a Matrix (7 marks) #includestdio.h main() { int nrows, ncols; /*nrows is for number of rows and ncols is for number of columns */ printf(nNumber of rows in the matrix: ); scanf(%d, nrows); printf(nNumber of cols in the matrix: ); scanf(%d, ncols); int mat[nrows][ncols]; int tranmat[ncols][nrows]; /*tranmat[][] is for holding the transpose */ int i, j; printf(nNow obtaining integers for the %d by %d matrixn, nrows, ncols); for(i=0;inrows;i++) { for(j=0;jncols;j++) { printf(Enter integer for %d row and %d col: ,i,j); scanf(%d, mat[i][j]); } } for(i=0;inrows;i++) { for(j=0;jncols;j++) { tranmat[j][i] = mat[i][j]; } } printf(nOriginal matrix:n); for(i=0;inrows;i++) { for(j=0;jncols;j++) { printf(%7d, mat[i][j]); } printf(n); } printf(nTranspose matrix:n); for(i=0;incols;i++) { for(j=0;jnrows;j++)](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-121-2048.jpg)
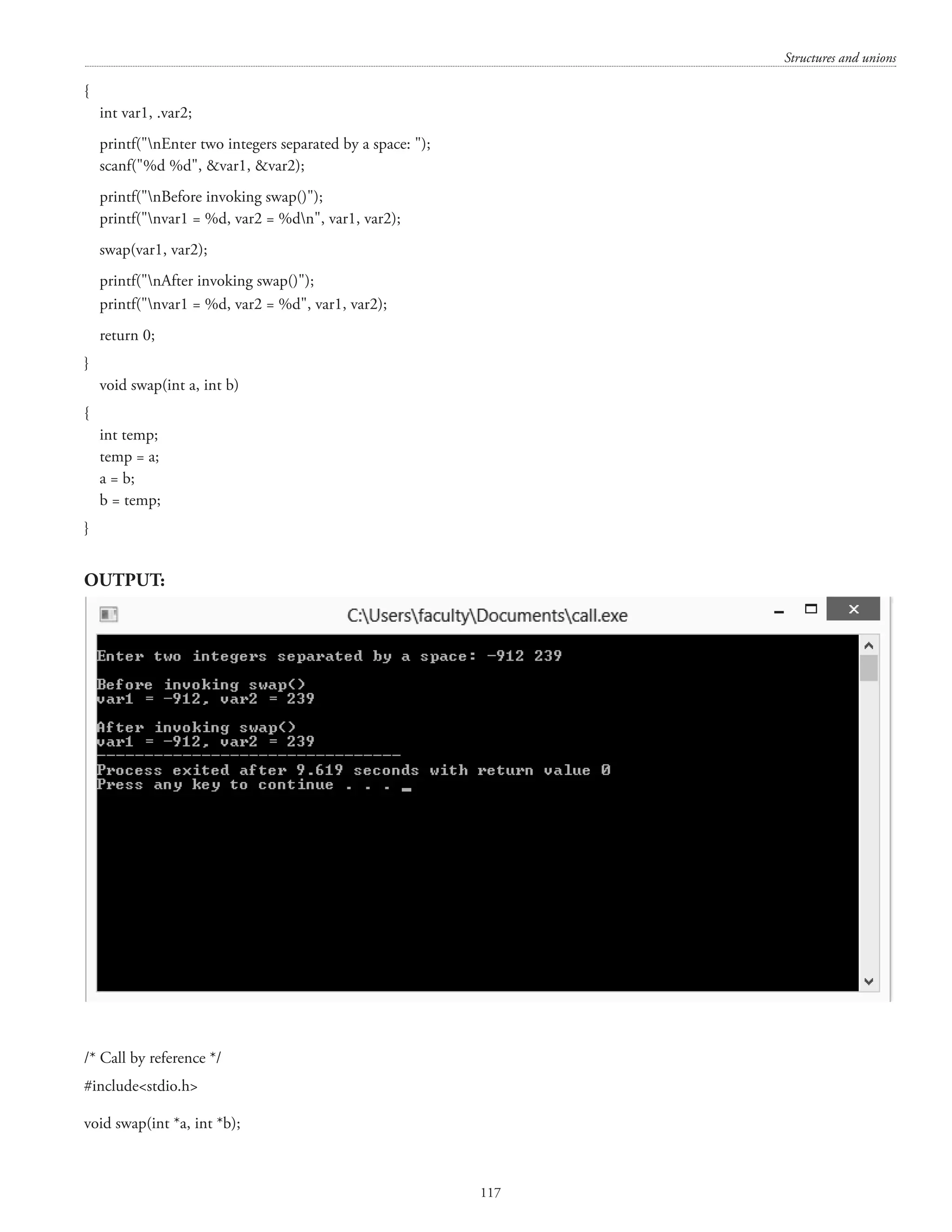
![Computer Concepts and Fundamentals of Programming 116 { printf(%7d, tranmat[i][j]); } printf(n); } return 0; } A sample output is shown below: 6. a) Explain i) Call by Value ii) Call be reference with example. (10 marks) /* Call by value */ #includestdio.h void swap(int a, int b); main()](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-122-2048.jpg)
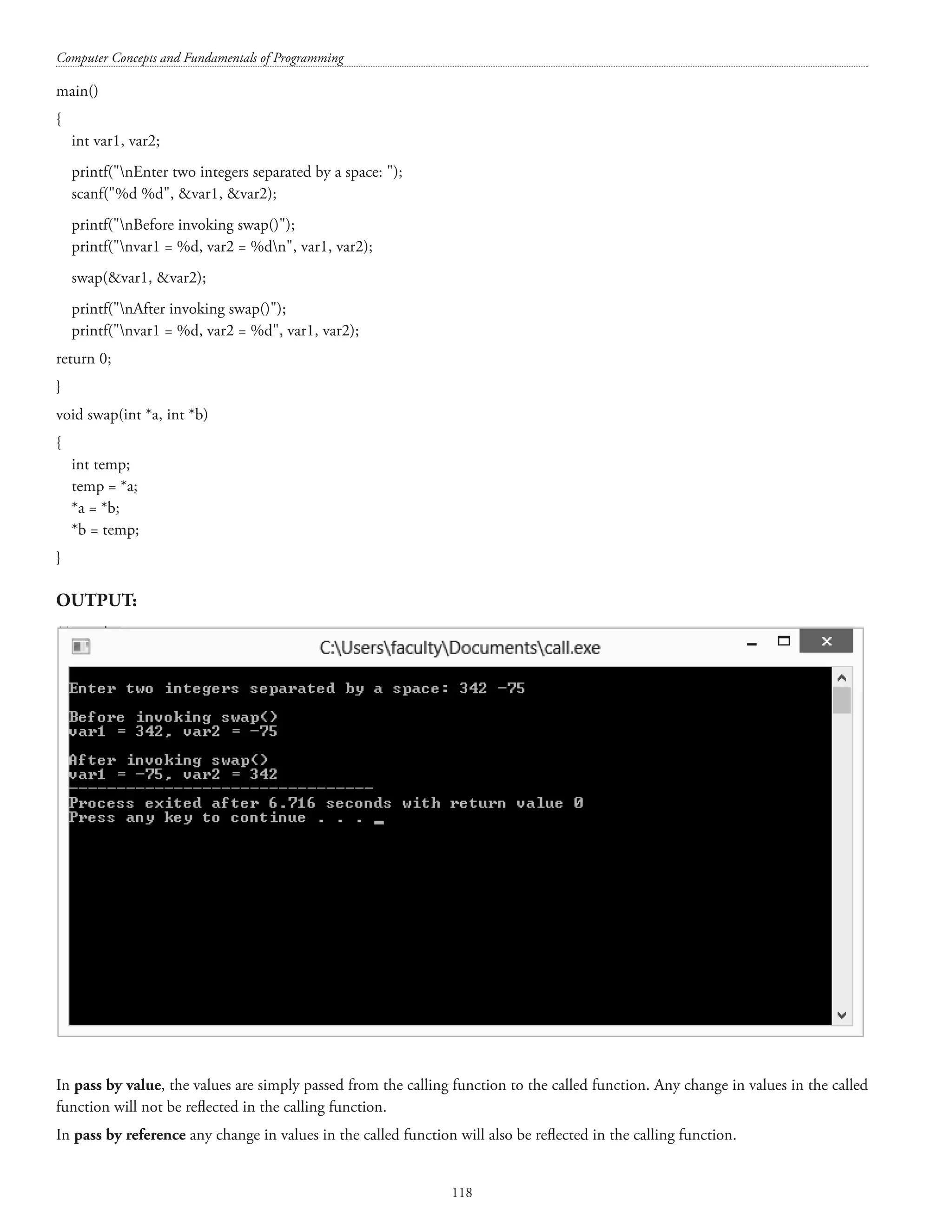
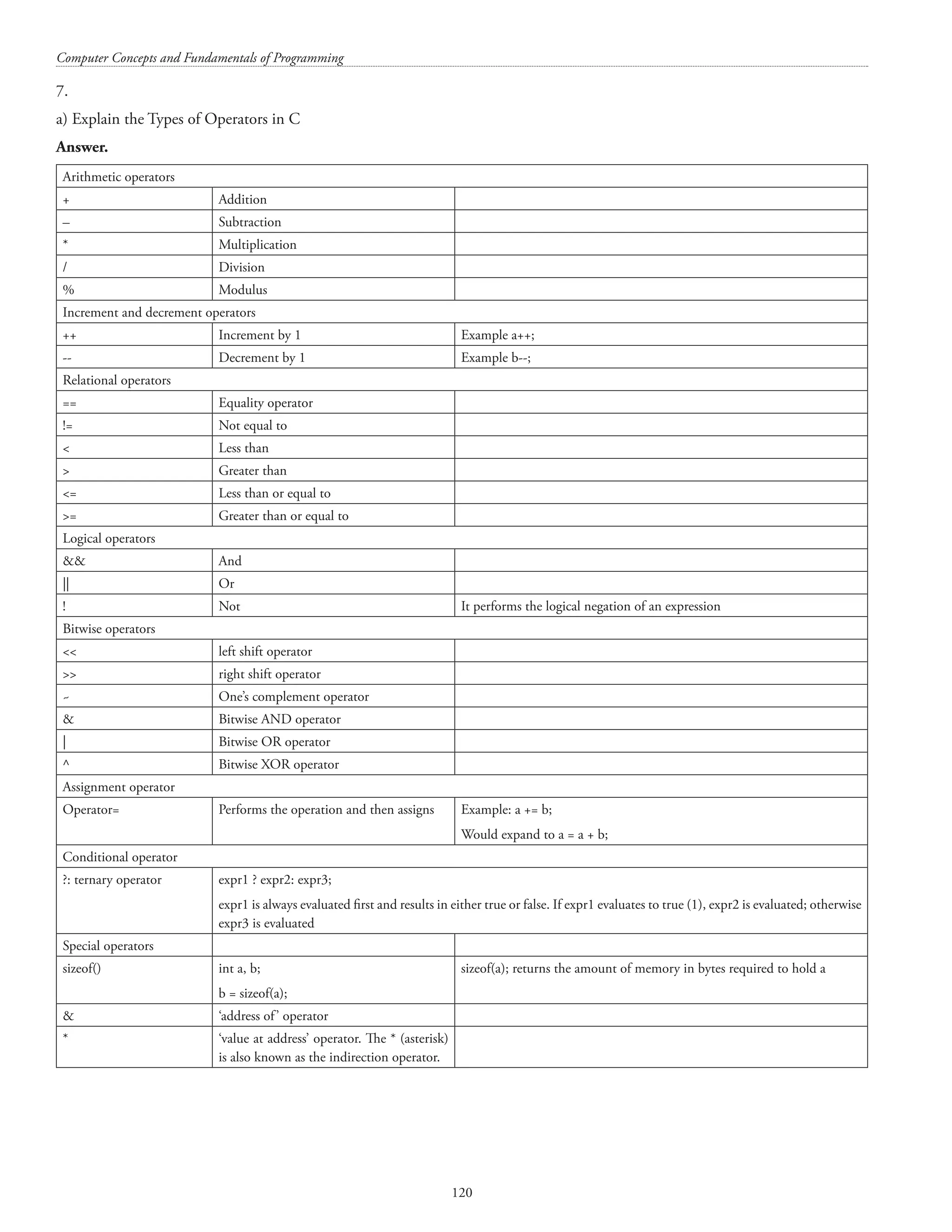
![Structures and unions 119 [Important Note: There is no pass by reference in ‘C’. is also known as referencing operator in C++.] b) Explain gets() and puts(). (4 marks) Answer. The gets() function in ‘C’ reads a line from the input stream and terminates it by ‘0’. The puts() function is used for displaying a string on the standard output. The puts() function automatically inserts a newline character at the end of each string it displays. #includestdio.h main() { char str[80]; printf(nEnter any string: ); gets(str); puts(nThe string you entered is: ); puts(str); return 0; } OUTPUT:](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-125-2048.jpg)
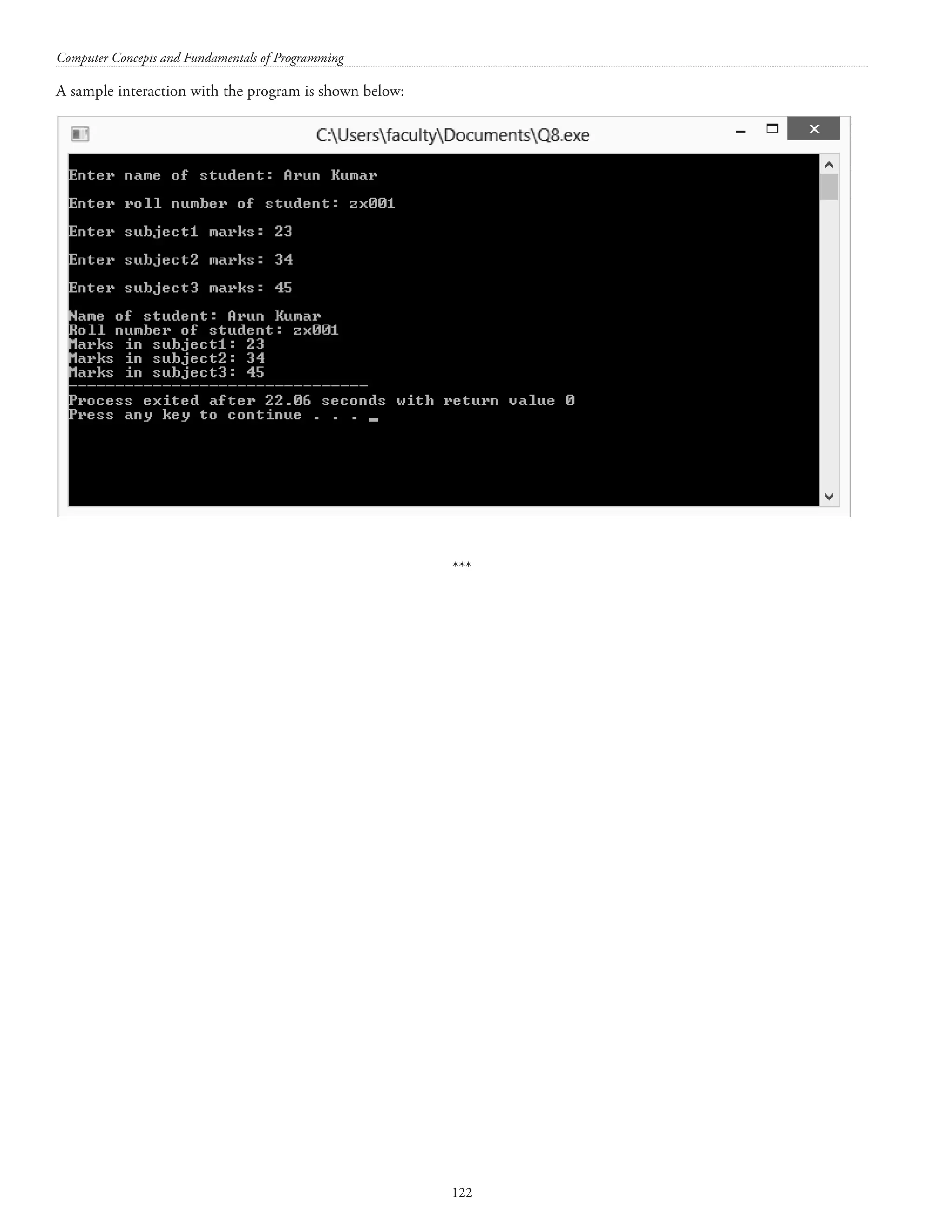
![Structures and unions 121 8. Write a C program to store information (name, roll and marks) of Student using Structure data where information will be taken as fly (runtime) (10 marks) #includestdio.h struct student_data { char name[40]; char rollno[20]; int marks_sub_1; int marks_sub_2; int marks_sub_3; }; main() { struct student_data svar1; printf(nEnter name of student: ); scanf(%[^n], svar1.name); fflush(stdin); printf(nEnter roll number of student: ); scanf(%[^n], svar1.rollno); printf(nEnter subject1 marks: ); scanf(%d, svar1.marks_sub_1); printf(nEnter subject2 marks: ); scanf(%d, svar1.marks_sub_2); printf(nEnter subject3 marks: ); scanf(%d, svar1.marks_sub_3); printf(nName of student: %s, svar1.name); printf(nRoll number of student: %s, svar1.rollno); printf(nMarks in subject1: %d, svar1.marks_sub_1); printf(nMarks in subject2: %d, svar1.marks_sub_2); printf(nMarks in subject3: %d, svar1.marks_sub_3); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-127-2048.jpg)
![Structures and unions 123 INDIAN MARITIME UNIVERSITY (Central University, Government of India) May/June 2016 End Semester Examinations B.Tech. (Marine Engineering) Second Semester – Computer Science – (UG11 T1205/T2205) Date: 17.06.2016 Maximum Marks: 100 Time: 3 Hrs Pass Marks: 50 PART – A Marks: 10 X 3 = 30 Compulsory Question 1) a) Can a calculator be considered as a computer? Answer. Calculator Computer Definition An electronic device used for mathematical calculations and has a small keyboard and display screen that shows the results. An electronic device which is capable of receiving information and performing a sequence of operations according to the instructions given (program). Development Wilhelm Schickard (according to two letters written by Schickard to Johannes Kepler in 1623 and 1624) invented the calculator. Blaise Pascal also developed a calculator. Gottfried Leibniz spent forty years designing a four-operation mechanical calculator. The Antikythera mechanism is believed to be the world’s first analog “computer” according to Derek J. de Solla Price. It was designed for calculating astronomical positions. Charles Babbage who is considered the “father of computer” developed the difference engine and thereafter the Analytical Engine. The principle of the modern computer was proposed by Alan Turing in the paper On Computable Numbers (1936). [N.B.: According to the Oxford English Dictionary, the first known use of the word “computer” was in 1613 in a book bearing the name The Yong Mans Gleanings authored by Richard Braithwait.] A programmable calculator can be considered as a computer. The idea of a universal computational device was described by Alan Turing in 1937. Alan Turing proposed that all computations could be performed by a special kind of a machine, now known as a Turing machine. Around 1944 – 45, John von Neumann proposed that along with the data, the programs should also be stored in the memory of a computer. b) Choose the correct one (i) A header file is: (A) A file that contains standard library functions](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-129-2048.jpg)
![Computer Concepts and Fundamentals of Programming 124 (B) A file contains definitions and macros (C) A file that contains user defined functions (D) A file that is present in current working directory Answer. (A) A header file in ‘C’ is a file that contains prototype statements and other declarations. It is placed in a library for shared use. (ii) A character variable can at a time store (A) 1 character (B) 8 character (C) 254 characters (D) None of the above Answer. (A) The C standard provides two character types: char and wchar_t. The size of char in ‘C’ is machine dependent. Normally it is one byte or eight bits. [Note: The programs of this section have been executed on Dev C++ Version 5.11] c) Write a C program for adding two numbers. #includestdio.h main() { double num1, num2, result; printf(nEnter first number: ); scanf(%lf, num1); printf(nEnter second number: ); scanf(%lf, num2); result = num1 + num2; printf(n%lf + %lf = %lf, num1,num2, result); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-130-2048.jpg)
![Structures and unions 125 A shorter method: #includestdio.h main() { double num1, num2; printf(nEnter two numbers: ); scanf(%lf %lf, num1, num2); printf(n%lf + %lf = %lf, num1,num2, num1 + num2); return 0; } d) Differentiate between data and information. Answer. Data refers to facts and figures. Data are unstructured facts and figures. Information is data that is contextualised, categorized, calculated and condensed. Information is data with relevance and purpose. e) What do you understand by secondary memory Answer. Auxiliary storage is also known as secondary storage. The programs and data are stored permanently in the secondary storage. The programs and data remain in the secondary storage, even when the computer is switched off. Auxiliary storage is used for both input and output. Secondary memory includes all permanent or persistent storage devices, such as flash drives, hard disk drives, magnetic tapes, ROM. Secondary memory is slower than primary memory. [N.B.: Primary storage is also known as main memory. The programs and data are stored temporarily in the main memory during processing. The data in primary storage are erased when the computer is switched off (or in case of logging off from a time- sharing computer). ]](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-131-2048.jpg)
![Computer Concepts and Fundamentals of Programming 126 f) How is an array represented in memory? Answer. An array is a collection of elements of the same data type. The name of an array refers to the first byte of the array. The index represents an offset from the beginning of the array to the element being referenced. ‘C’ calculates the address of any element of the array using the formula given below: element address = array base address + (sizeof(element) * index) int num[5]; num[0] num[1] num[2] num[3] num[4] g) (i) What do you mean by Nested structure? Answer. #includestdio.h struct date_of_birth { int dd; int mm; int yy; }; struct personal_details { char name[40]; char addr1[80]; char addr2[80]; struct date_of_birth dob; }; main() { struct personal_details person1; printf(nEnter name: ); scanf(%[^n], person1.name); fflush(stdin); printf(nEnter first line of address: ); scanf(%[^n], person1.addr1); fflush(stdin); printf(nEnter second line of address: ); scanf(%[^n], person1.addr2); fflush(stdin); printf(nEnter date of birth: dd mm yyyy: ); scanf(%d %d %d, person1.dob.dd, person1.dob.mm, person1.dob.yy); printf(nName = %s, person1.name); printf(nFirst line of address = %s, person1.addr1);](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-132-2048.jpg)
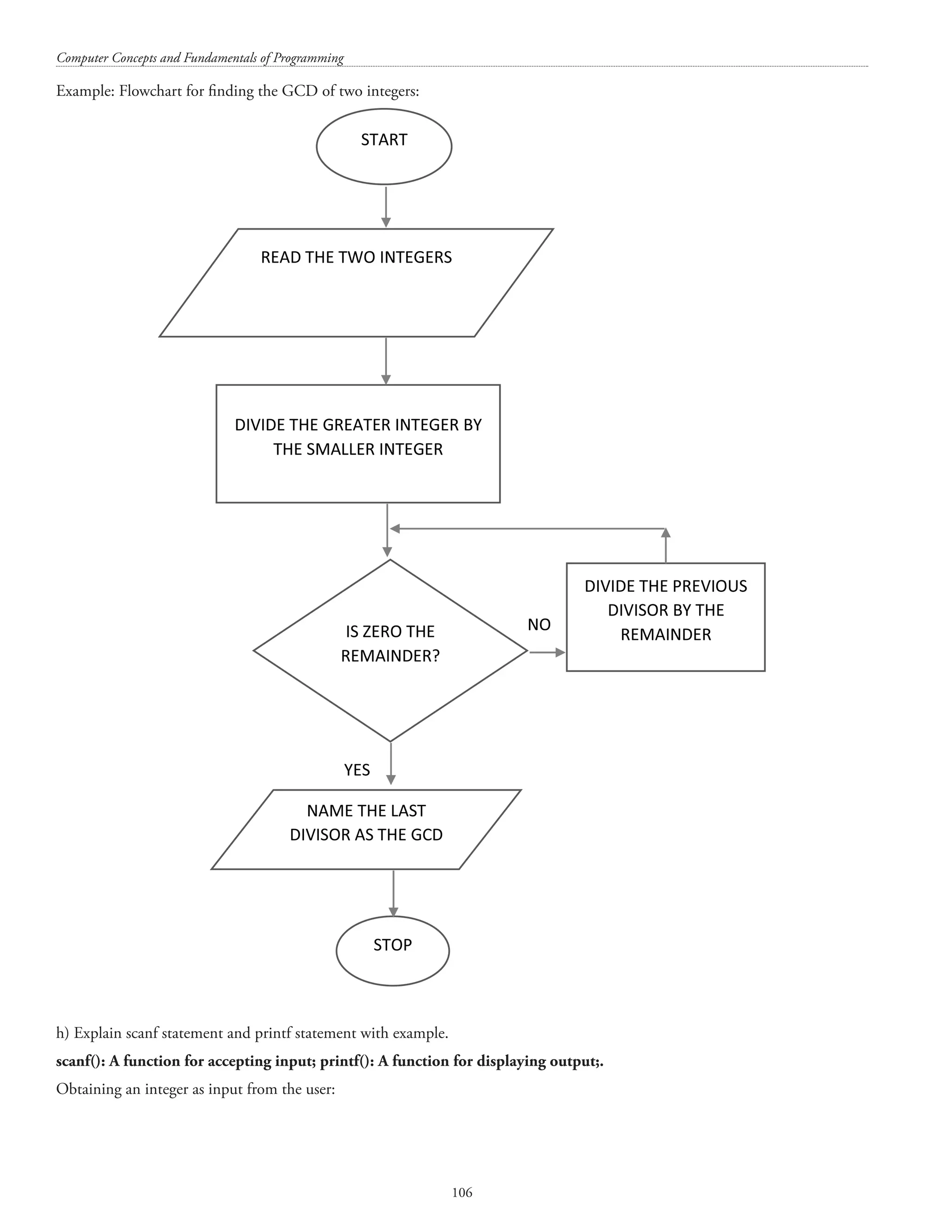
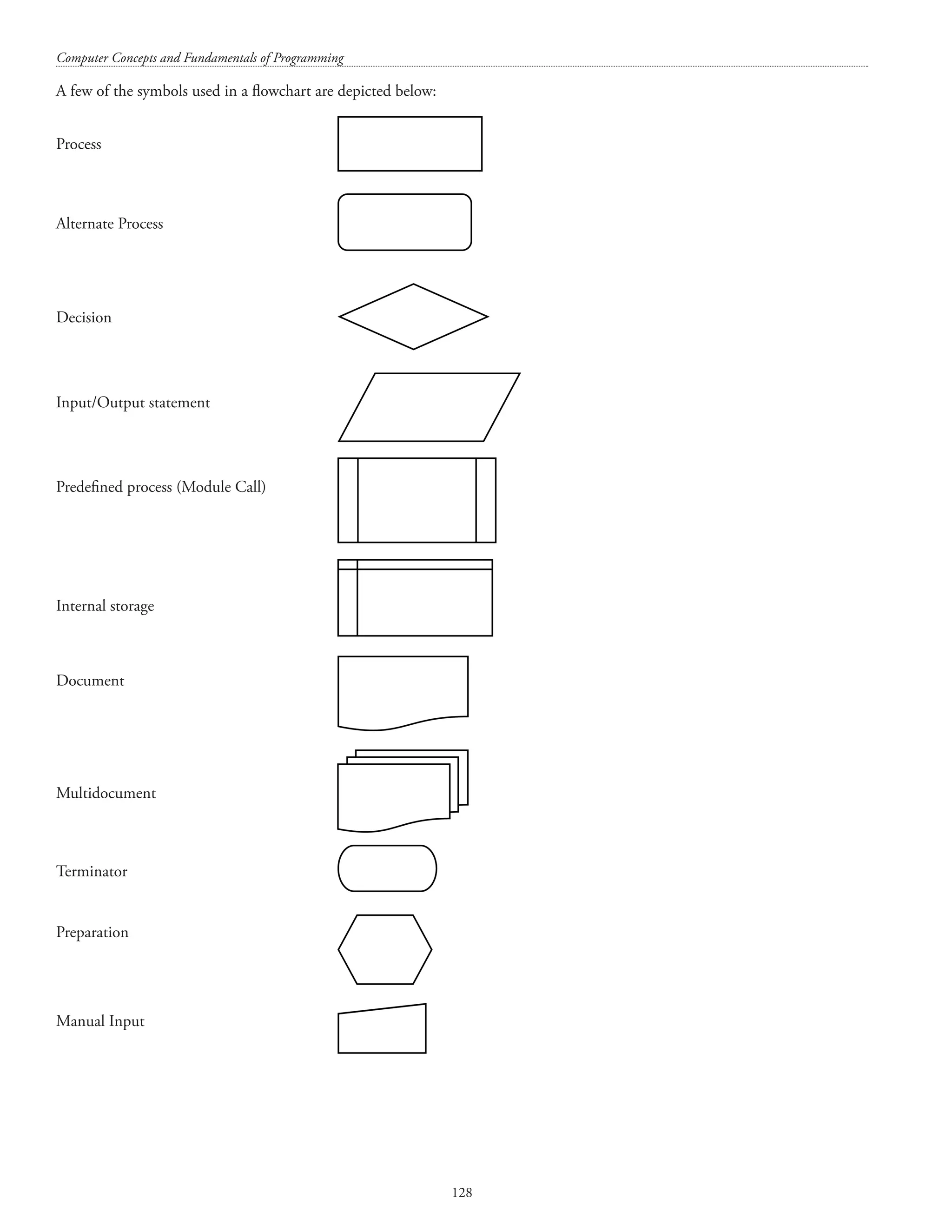
![Structures and unions 127 printf(nSecond line of address = %s, person1.addr2); printf(nDate of birth = %d/%d/%d, person1.dob.dd, person1.dob.mm, person1.dob.yy); return 0; } (ii) How many bits does a char type data has? Answer. Most of the personal computers use 1 byte to store the char datatype. A byte has 8 bits. [The unit symbol for byte is B and the unit symbol for bit is b. The term byte was coined by Werner Buchholz. The term “qubit” was coined by Benjamin Schumacher. 1 Kilobyte = 1024 bytes 1 Megabyte = 1024 Kilobytes 1 Gigabyte = 1024 Megabytes 1 Terabyte = 1024 Gigabytes 1 Petabyte = 1024 Terabytes 1 Exabyte = 1024 Petabytes 1 Zettabyte = 1024 Exabytes 1 Yottabyte = 1024 Zettabytes] h) Describe the similarities and dissimilarities between algorithm and flowchart. Answer. An algorithm is a logical step-by-step method for solving a problem. An algorithm details the procedure for solving a problem. Algorithm includes calculations, reasoning, and data processing. A flowchart is a pictorial depiction (using different shapes) of the logic used in solving a problem. A flowchart depicts the logic flow of a program. In other words, a flowchart depicts the design of an algorithm. A flowchart helps in pictorial thinking and visualization. A flowchart shows the order and sequence of the actions to be performed for solving a problem.](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-133-2048.jpg)
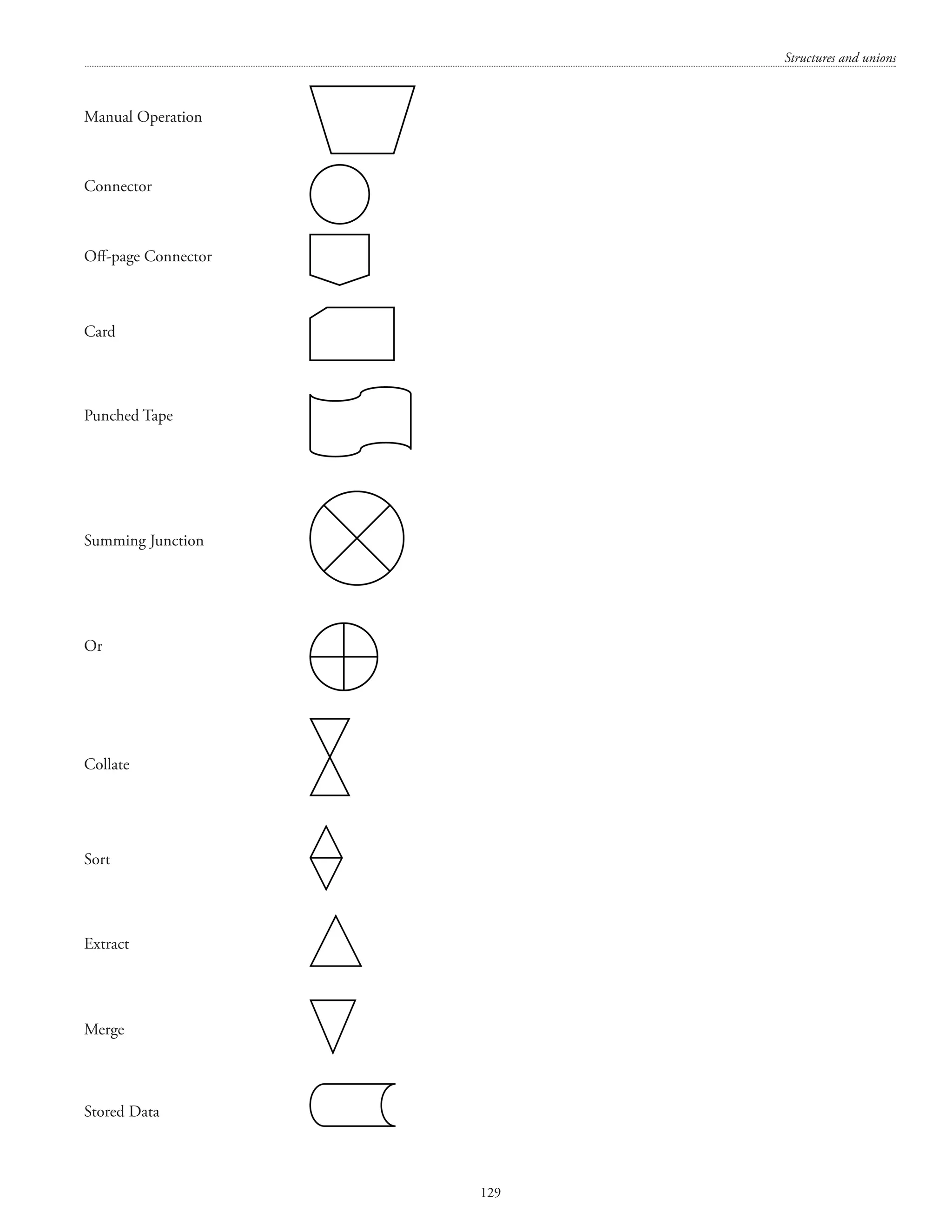
![Computer Concepts and Fundamentals of Programming 130 Delay Sequential Access Storage Magnetic Disk Direct Access Storage Display Flow Line An algorithm is a finite set of instructions that, if followed, accomplishes a particular task. In addition, all algorithms must satisfy the following criteria: 1. Input. Zero or more quantities are externally supplied. 2. Output. At least one quantity is produced. 3. Definiteness. Each instruction is clear and unambiguous. 4. Finiteness. If we trace out the instructions of an algorithm, then for all cases, the algorithm terminates after a finite number of steps. 5. Effectiveness. Every instruction must be very basic so that it can be carried out, in principle, by a person using only pencil and paper. It is not enough that each operation be definite as in criterion 3; it also must be feasible. (Source for definition of algorithm: Ellis Horowitz, Sartaj Sahni, Sanguthevar Rajasekaran) [N.B.: Algorithmics is a term coined by Brassard and Bratley. Algorithmics is the systematic study of the fundamental techniques used to design and analyse efficient algorithms.] i) List out the various application of computer? Answer. Computers are used in Engineering Design, Defence, Health care, Education, Businesses, Weather forecasting, simulation, etc. j) List the advantage of Pseudo-code? Answer. Pseudocode depicts the logic of solving a problem in simple English and mathematics. It is a stepwise description of the logic used for solving a problem. A pseudocode uses structural conventions of a normal computer programming language. A pseudocode is normally to be read and understood by human beings rather than machines. The word pseudo means false and code means programs.](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-136-2048.jpg)

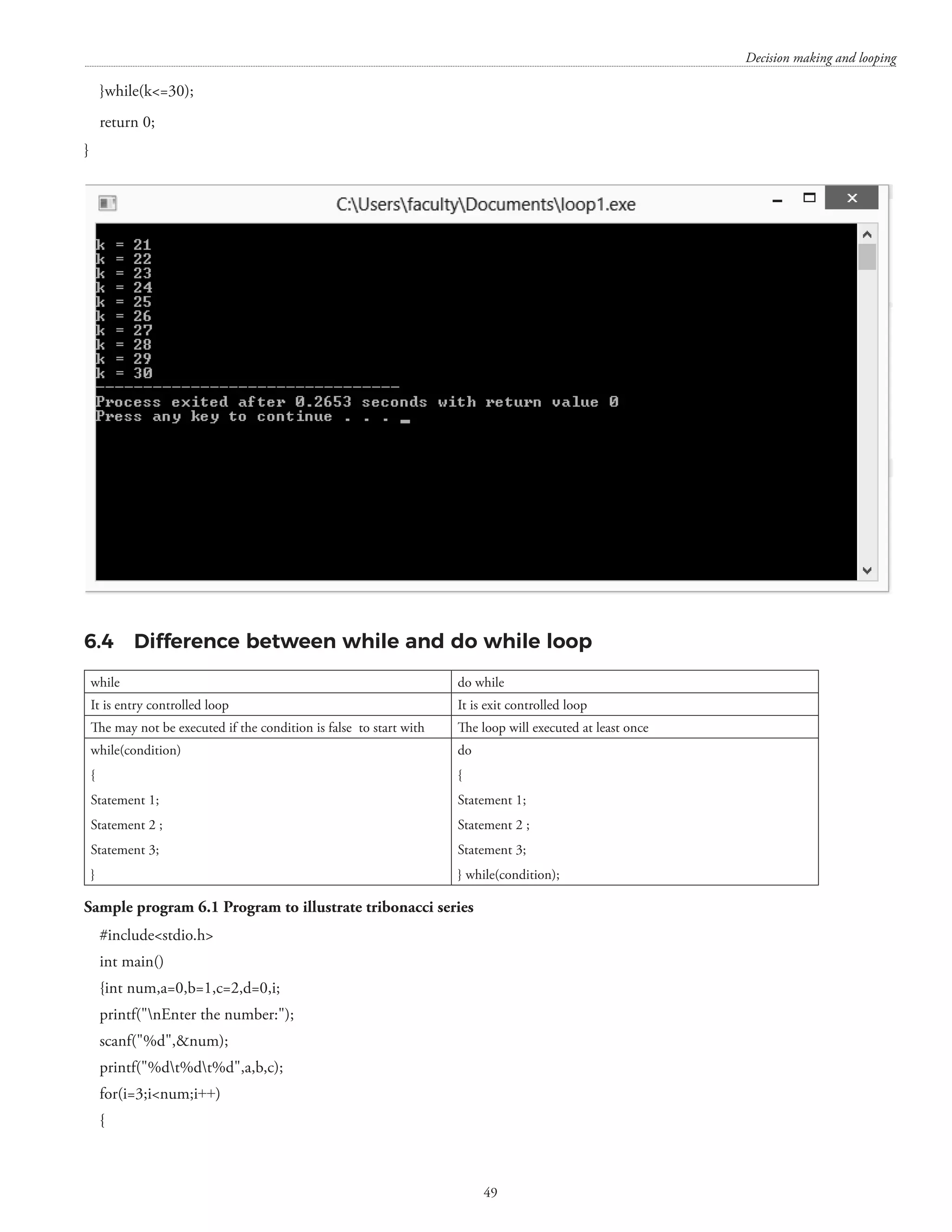
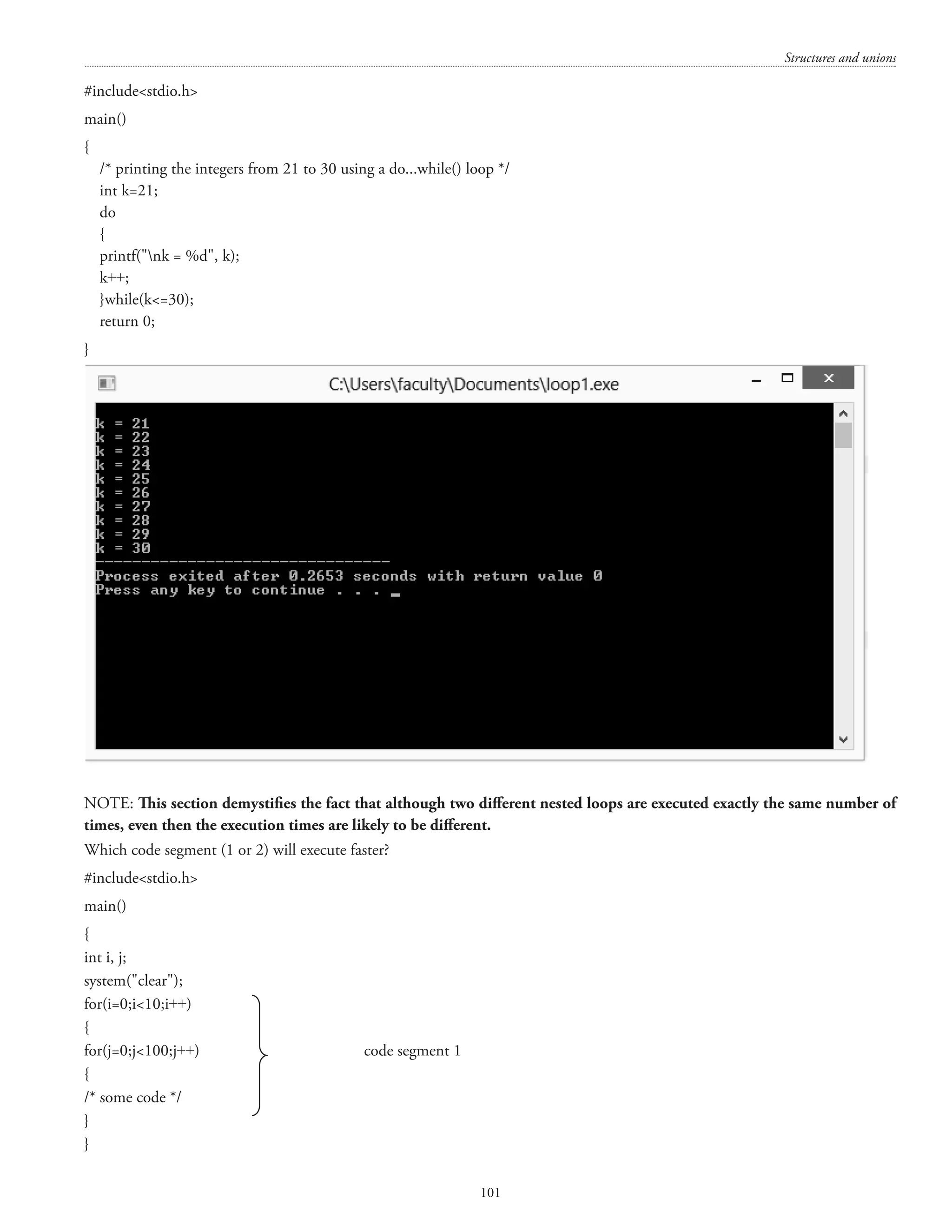
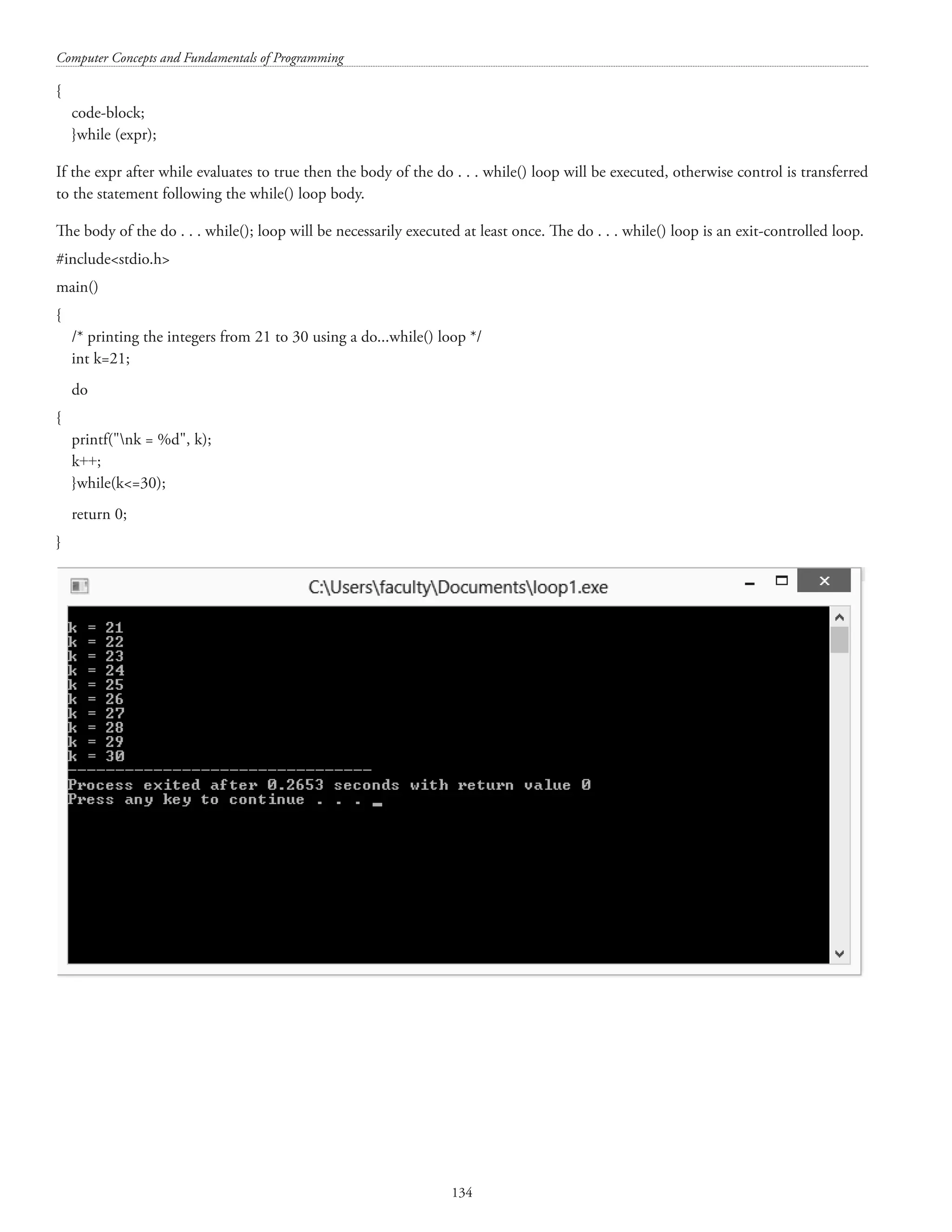
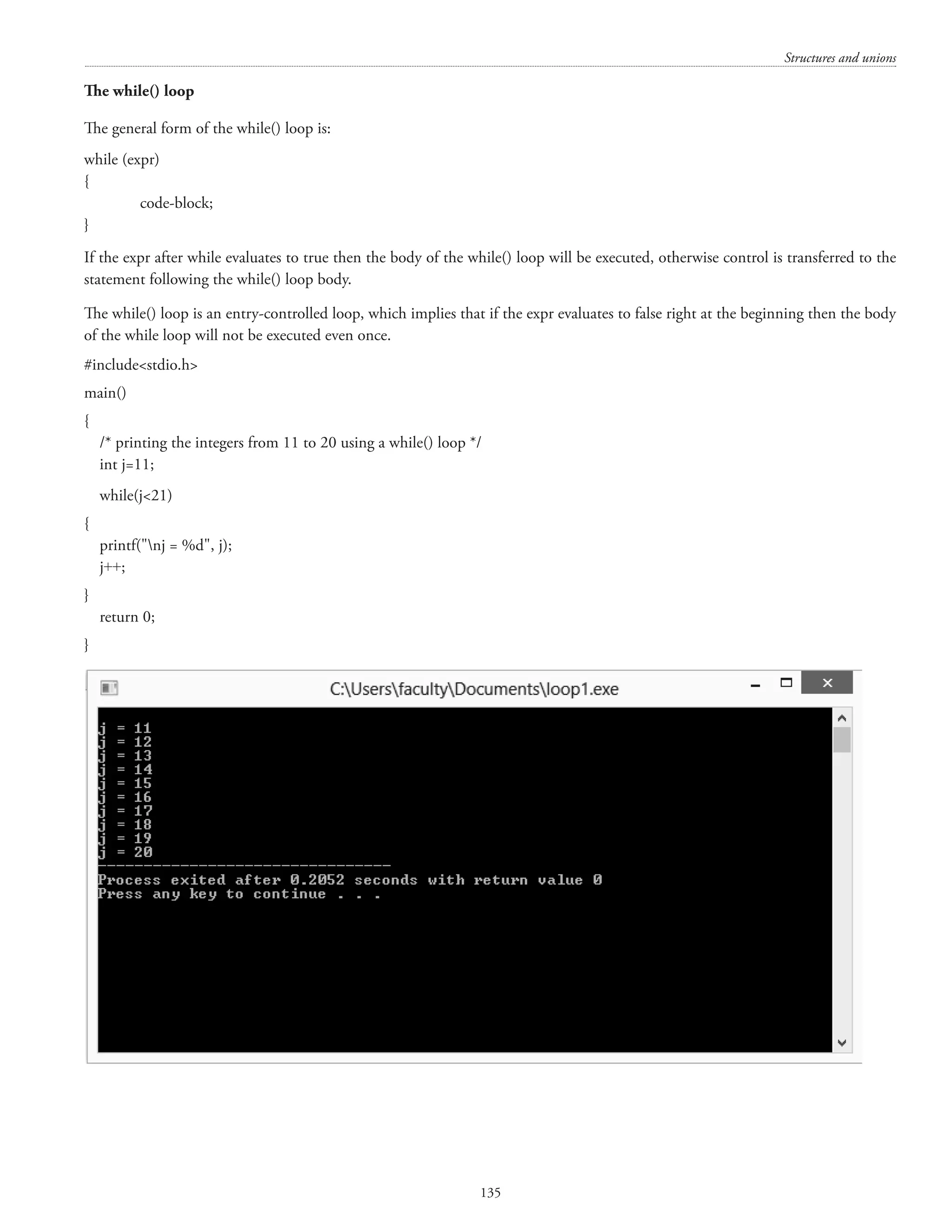
![Structures and unions 133 [407 is divisible by 1, 11, 37, and 407] c) Differentiate between do-while and while loop with a suitable example. (7+4+3) Answer. The do . . . while() loop The general form of the while() loop is: do](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-139-2048.jpg)
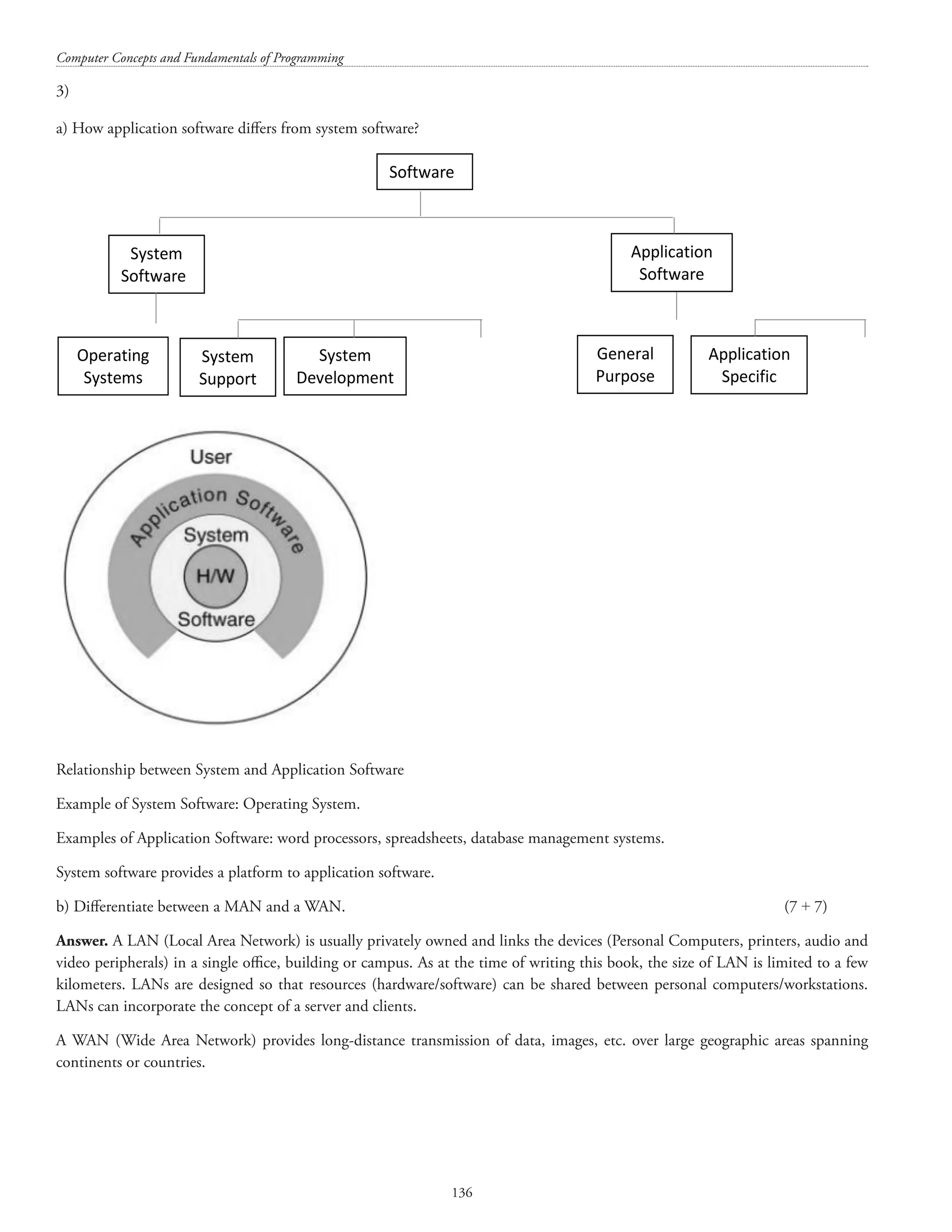
![Structures and unions 137 A MAN (Metropolitan Area Network) is a network with a size between a LAN and a WAN. Basis of comparison LAN MAN WAN Expansion Local Area Network Metropolitan Area Network Wide Area Network Geographical Area Small. For example School, College, Hospital, Office Larger region such as a city or a town Countries or even continents Ownership of network Usually private Private or public Private or public Devices used WiFi, Ethernet cables, Hub, Switch, Router Modem and Wire cable Optic fibres, Microwave, Satellites [Note: VLAN is for Virtual Local Area Network] 4) a) Define an algorithm. How is it useful in the context of software development? Answer. An algorithm is a finite set of instructions that, if followed, accomplishes a particular task. In addition, all algorithms must satisfy the following criteria: 1. Input. Zero or more quantities are externally supplied. 2. Output. At least one quantity is produced. 3. Definiteness. Each instruction is clear and unambiguous. 4. Finiteness. If we trace out the instructions of an algorithm, then for all cases, the algorithm terminates after a finite number of steps. 5. Effectiveness. Every instruction must be very basic so that it can be carried out, in principle, by a person using only pencil and paper. It is not enough that each operation be definite as in criterion 3; it also must be feasible. (Ellis Horowitz, Sartaj Sahni, Sanguthevar Rajasekaran) Program: A program is the expression of an algorithm in a programming language. Algorithms help in developing code. b) Write a pseudo-code to count number of vowels in a text. (7 + 7) Answer. Obtain text as input from the user and assign it to a string variable Set up a counter for counting vowels and initialize it with 0 (zero) find the length of the string and store it in a variable (string_length, for instance) read the entire string from the first character to the last character (string_length) (using a loop) { read a character if the character read is a vowel (a, e, i, o, u, A, E, I, O, U), then increment counter by 1 } print the value of counter [Note: The examinee is required to write only the pseudocode but for the benefit of the reader a program in ‘C’ for counting the number of vowels in a string is produced below:](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-143-2048.jpg)
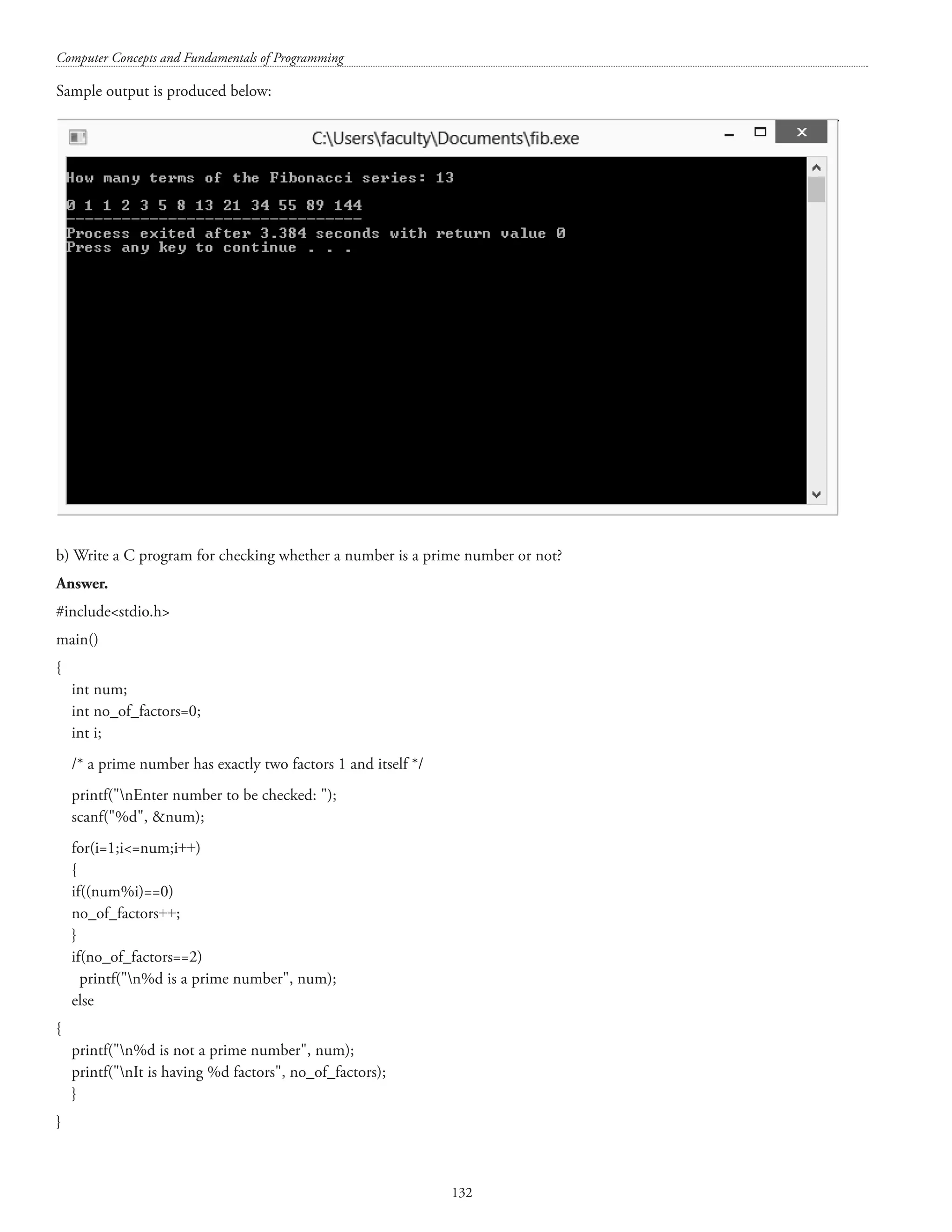
![Computer Concepts and Fundamentals of Programming 138 #includestdio.h #includestring.h main() { char str[80]; char c; int i, len, ctr=0; printf(nEnter any string: ); scanf(%[^n], str); len=strlen(str); for(i=0;ilen;i++) { c=str[i]; if((c=='a') || (c=='A')) ctr++; else if((c=='e') || (c=='E')) ctr++; else if((c=='i') || (c=='I')) ctr++; else if((c=='o') || (c=='O')) ctr++; else if((c=='u') || (c=='U')) ctr++; } printf(nstr = %s, str); printf(nNumber of vowels = %d, ctr); return 0; } A sample output is shown below: Enter any string: Computer Science str = Computer Science Number of vowels = 6 The program for counting the number of vowels in a string can also be written as follows: #includestdio.h #includestring.h main() { char str[80]; char c; int i, len, ctr=0; printf(nEnter any string: ); scanf(%[^n], str); len=strlen(str);](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-144-2048.jpg)
![Structures and unions 139 for(i=0;ilen;i++) { c=str[i]; switch(c) { case 'a': case 'A': case 'e': case 'E': case 'i': case 'I': case 'o': case 'O': case 'u': case 'U': ctr++; } } printf(nstr = %s, str); printf(nNumber of vowels = %d, ctr); return 0; } A sample interaction with the program is shown below: Enter any string: Mouse was invented by D. Engelbart str = Mouse was invented by D. Engelbart Number of vowels = 10 ] 5) a) Write a program using pointers to insert a value in an array. Answer. #includestdio.h #define SIZE 10 void func(int *arrptr, int n, int loc); main() { int arr[SIZE]; int i; int num; int location; printf(nNow obtaining %d integers for the array: n, SIZE); for(i=0;iSIZE;i++) { printf(nEnter %dth integer: , i); scanf(%d, arr[i]); } printf(nEnter integer to be inserted: ); scanf(%d, num);](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-145-2048.jpg)
![Computer Concepts and Fundamentals of Programming 140 printf(nEnter location at which integer is to be inserted: ); scanf(%d, location); printf(nThe original array elements:); for(i=0;iSIZE;i++) printf(narr[%d] = %d, i, arr[i]); func(arr, num, location); printf(nThe array elements after inserting %d at %d:, num, location); for(i=0;iSIZE;i++) printf(narr[%d] = %d, i, arr[i]); return 0; } void func(int *arrptr, int n, int loc) { if((loc0) || (loc =SIZE)) printf(nThe array subscripts are numbered from 0 to %d, SIZE-1); else arrptr[loc] = n; } A sample interaction with the program is produced below: Now obtaining 10 integers for the array: Enter 0th integer: 0 Enter 1th integer: 1 Enter 2th integer: 2 Enter 3th integer: 3 Enter 4th integer: 4 Enter 5th integer: 5 Enter 6th integer: 6 Enter 7th integer: 7 Enter 8th integer: 8 Enter 9th integer: 9 Enter integer to be inserted: -4521 Enter location at which integer is to be inserted: 3 The original array elements: arr[0] = 0 arr[1] = 1 arr[2] = 2 arr[3] = 3 arr[4] = 4 arr[5] = 5](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-146-2048.jpg)
![Structures and unions 141 arr[6] = 6 arr[7] = 7 arr[8] = 8 arr[9] = 9 The array elements after inserting -4521 at 3: arr[0] = 0 arr[1] = 1 arr[2] = 2 arr[3] = -4521 arr[4] = 4 arr[5] = 5 arr[6] = 6 arr[7] = 7 arr[8] = 8 arr[9] = 9 b) What is a null pointer? Give one example. (10 + 4) Answer. A null pointer is a pointer of any type that is assigned the constant NULL (stdio.h). Examples: char *pChar = NULL; /* NULL pointer of type char */ int *pInt = NULL; /* NULL pointer of type int */ float *pFloat = NULL; /* NULL pointer of type float */ double *pDouble = NULL; /* NULL pointer of type double */ If a pointer variable is declared within the main() function or any other function and it has not been initialised or assigned a value, then it contains a garbage value as demonstrated below: #includestdio.h main() { int *iptr; float *fptr = NULL; printf(niptr = %u, iptr); /*iptr will contain a junk value since it is not initialized */ printf(nfptr = %u, fptr); return 0; } Sample output: iptr = 3 fptr = 0](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-147-2048.jpg)

![Computer Concepts and Fundamentals of Programming 146 printf(nAfter invoking swap()); printf(nvar1 = %d, var2 = %d, var1, var2); return 0; } void swap(int *a, int *b) { int temp; temp = *a; *a = *b; *b = temp; } OUTPUT: In pass by value, the main program [or function like main()] and the subprogram (or the called function) create two different variables or objects. Communication between the main program (or the calling function) and the subprogram (or the called function) is only one-way, i.e. from the main program to the subprogram. The variables or objects created in the main program belong to the main program and the variables or objects created in the sub-program belong to the sub-program. In pass by reference any change in values in the called function will also be reflected in the calling function. [Important Note: There is no pass by reference in ‘C’. is also known as referencing operator in C++.] b) What is the difference between gets() and scanf() function? Write the differences between structures and arrays. (7 + 7) Answer. gets() is used to obtain a string value from the user. scanf() can be used to obtain a character, int, float, or double type value from the user.](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-152-2048.jpg)
![Structures and unions 147 Conversion specifications are to be used with scanf()such as %c for character, %d or %i for integer, %f for float. For accepting a string containing spaces ^[n] is used in scanf(). The gets() function accepts a line terminated by the newline character and converts the newline character to ‘0’. A structure is a collection of related elements, possibly of different or same subtypes, identified by a single name. Each element in the structure is called a field. The difference between an array and a structure is that all elements in an array must be of the same type, while the elements in a structure can be of the same or different types. But an array of structures can be created and array(s) can be part of a structure. The fields (or structure elements) should all be related to one object (as a matter of good programming practice). For example: struct book { char book_name[80]; char author1[80]; char author2[80]; char author3[80]; char publisher[80]; char edition[80]; int no_of_pages; char isbn[14]; }; [The student is advised to read the chapters on arrays and structures carefully in order to gain an understanding for answering this question.] *****](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-153-2048.jpg)






![Appendix Opening a web browser via a ‘C’ program Is it possible to open a web page in a browser using a ‘C’ program? The program below provides an answer to the aforementioned question: Program listing one #includestdio.h main() { char url[25] = “www.mail.yahoo.com”; char launch[255]; system(“clear”); sprintf(launch, “gnome-open %s”, url); system(launch); return 0; } [NOTE: 1. The above code should be compiled on a Linux system. 2. Parallel methods for opening a web-browser are available for Windows/Mac OSs. For instance, on a Mac OS, system(“open http://url”); might be used.] An alternative method of opening a web page is given below: Program listing two #includestdio.h main() { char url[25] = “www.iiml.ac.in”; char launch[255]; system(“clear”); sprintf(launch, “firefox %s”, url); system(launch); return 0; }](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-165-2048.jpg)
![Computer Concepts and Fundamentals of Programming 160 [Note: The code in Program listing two assumes that firefox is installed on the workstation and the appropriate PATH has been set.] The program below provides an illustration of another method of opening a web-browser via a ‘C’ program: Program listing three #includestdio.h #includeunistd.h main() { execl(“/usr/bin/firefox”, (char *)0); printf(“execl() could not open the web-page”); /* this line will be executed only if execl() above is not able to launch firefox*/ return 0; } The reader may interpret execl()as execute and leave. The execl() function replaces the current process by running the program specified as an argument to the execl()function. The process identifier (PID) of the new process will be the same as the PID of the old process (old process refers to the program in program listing three which is being compiled and executed and new process refers to firefox). The prototype of the execl()function is: int execl(const char *path, const char *arg1,...); execl() is a variadic function and the list of arguments to execl() should be terminated by a NULL pointer, therefore (char *)0 has been used to indicate the end of arguments to execl().](https://image.slidesharecdn.com/finalcomputerconceptsandfundamentalsofprogramming22-08-2018-200418115322/75/COMPUTER-CONCEPTS-AND-FUNDAMENTALS-OF-PROGRAMMING-166-2048.jpg)







