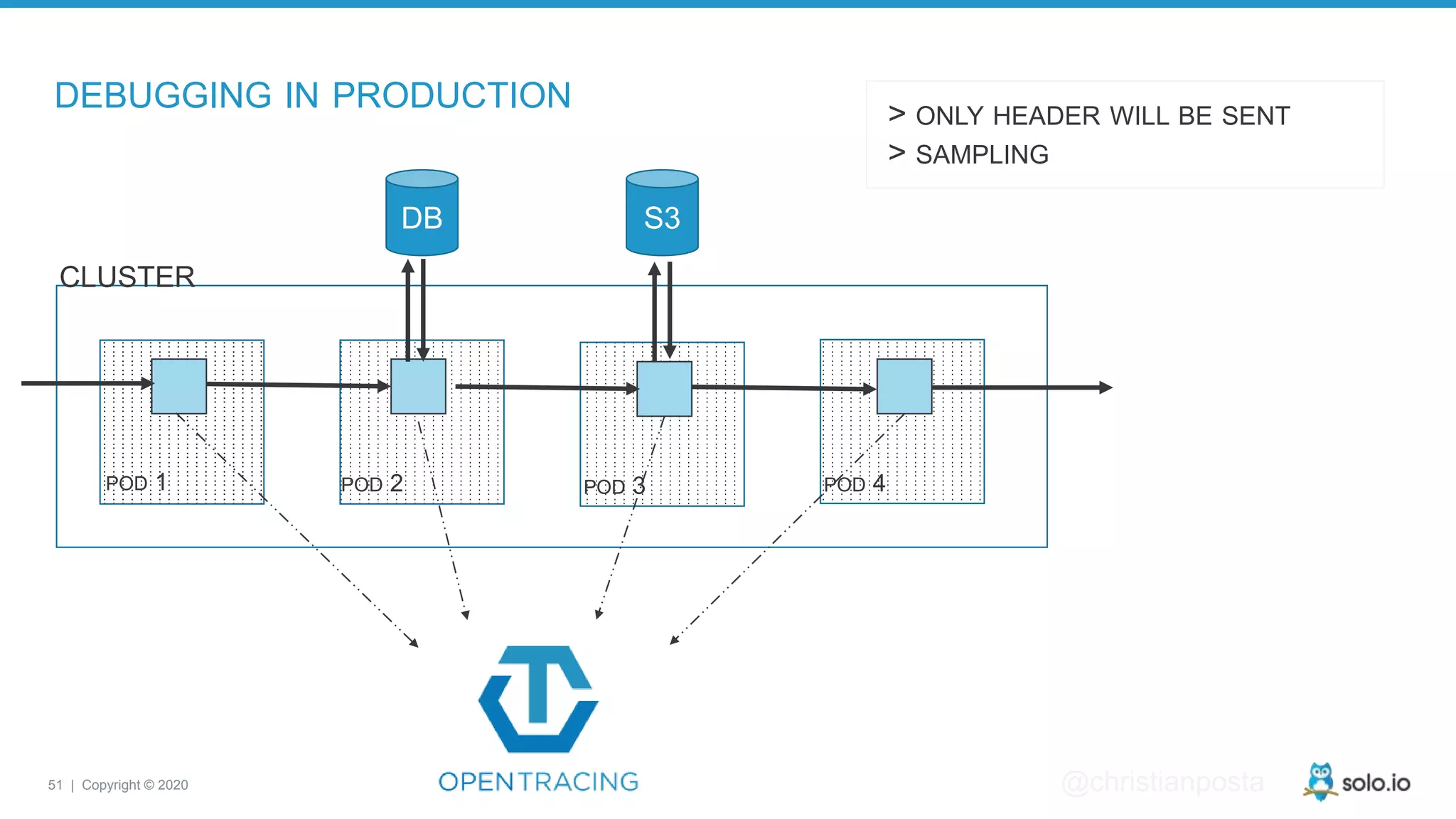
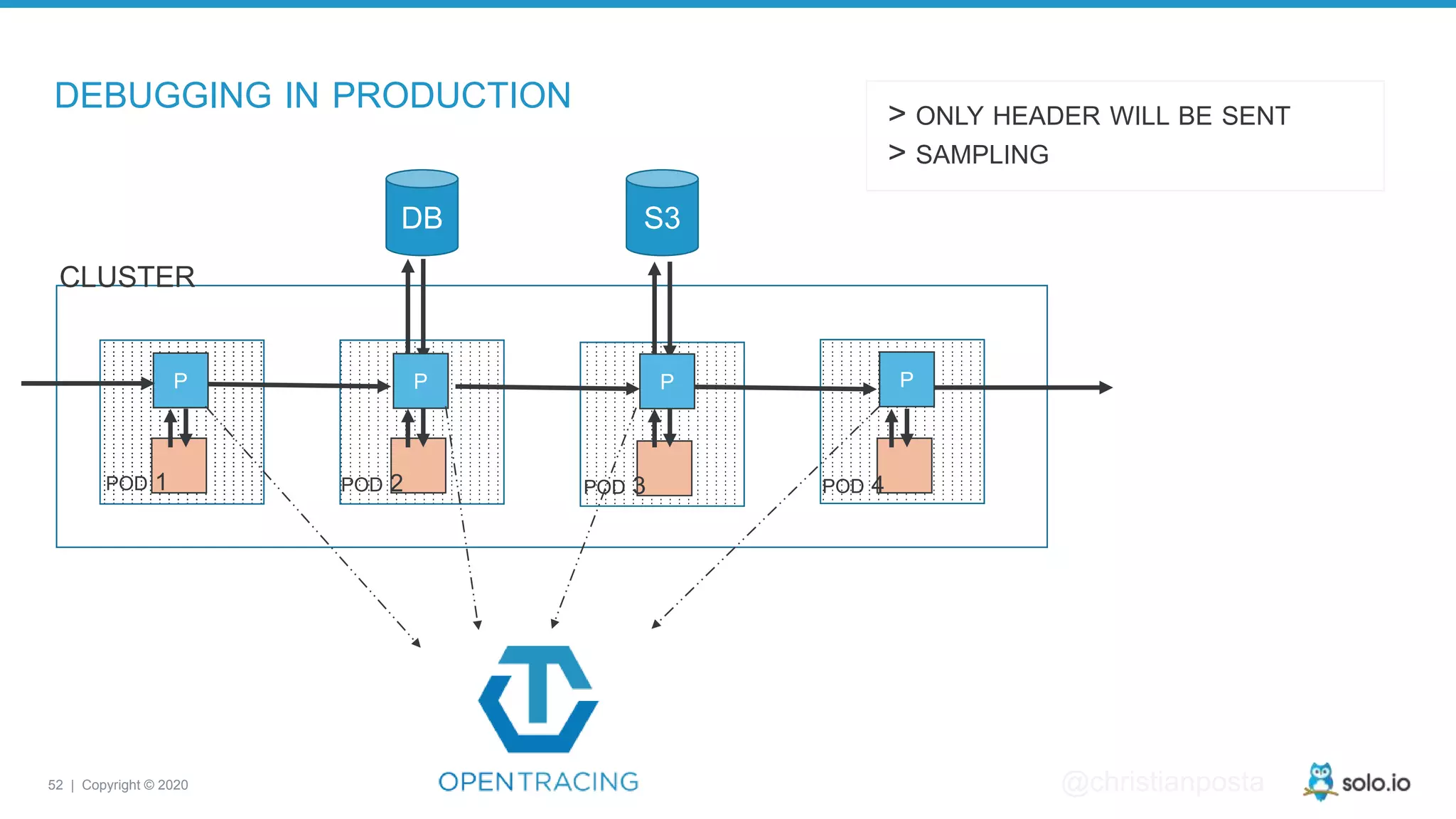
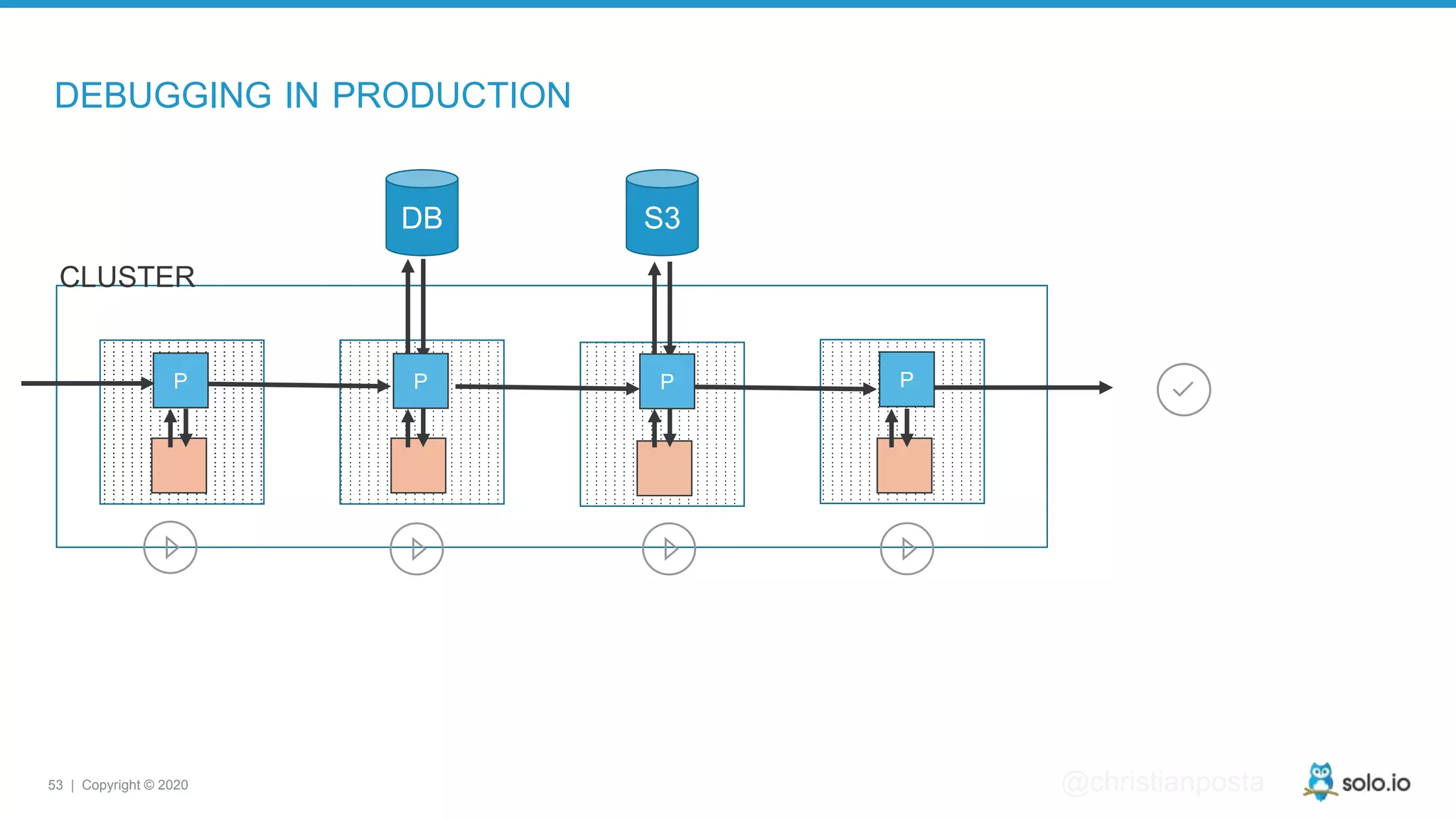
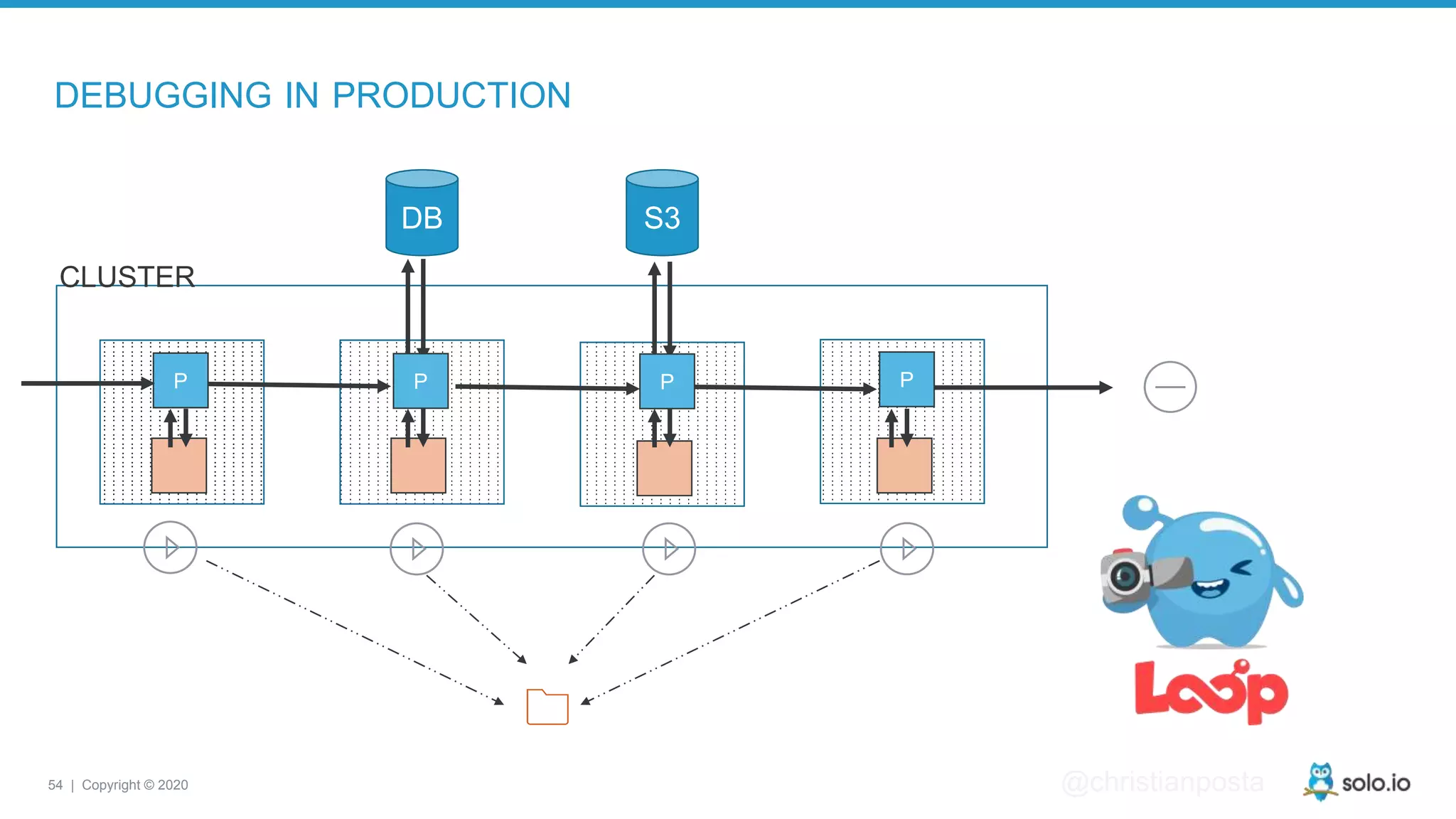
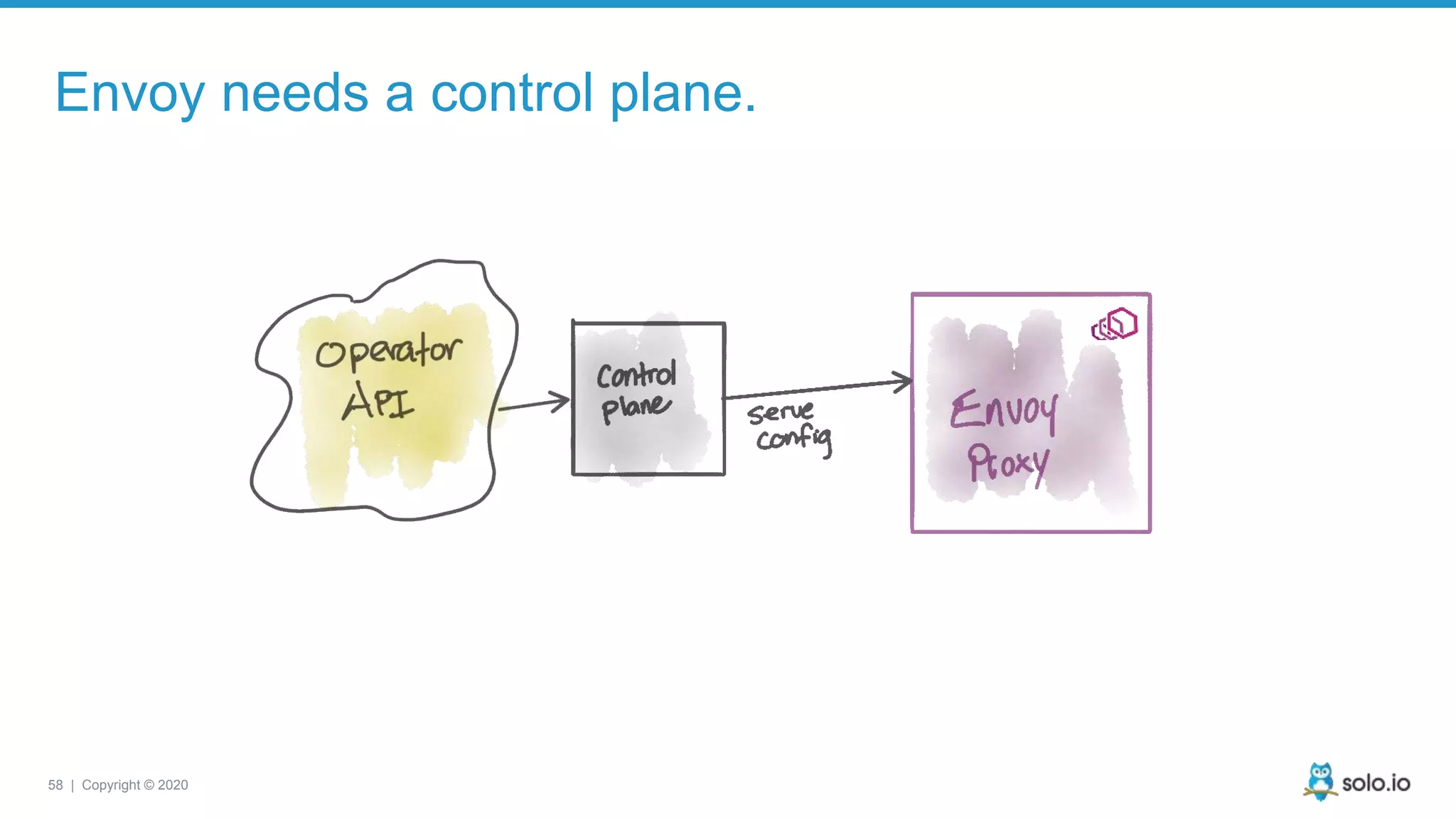
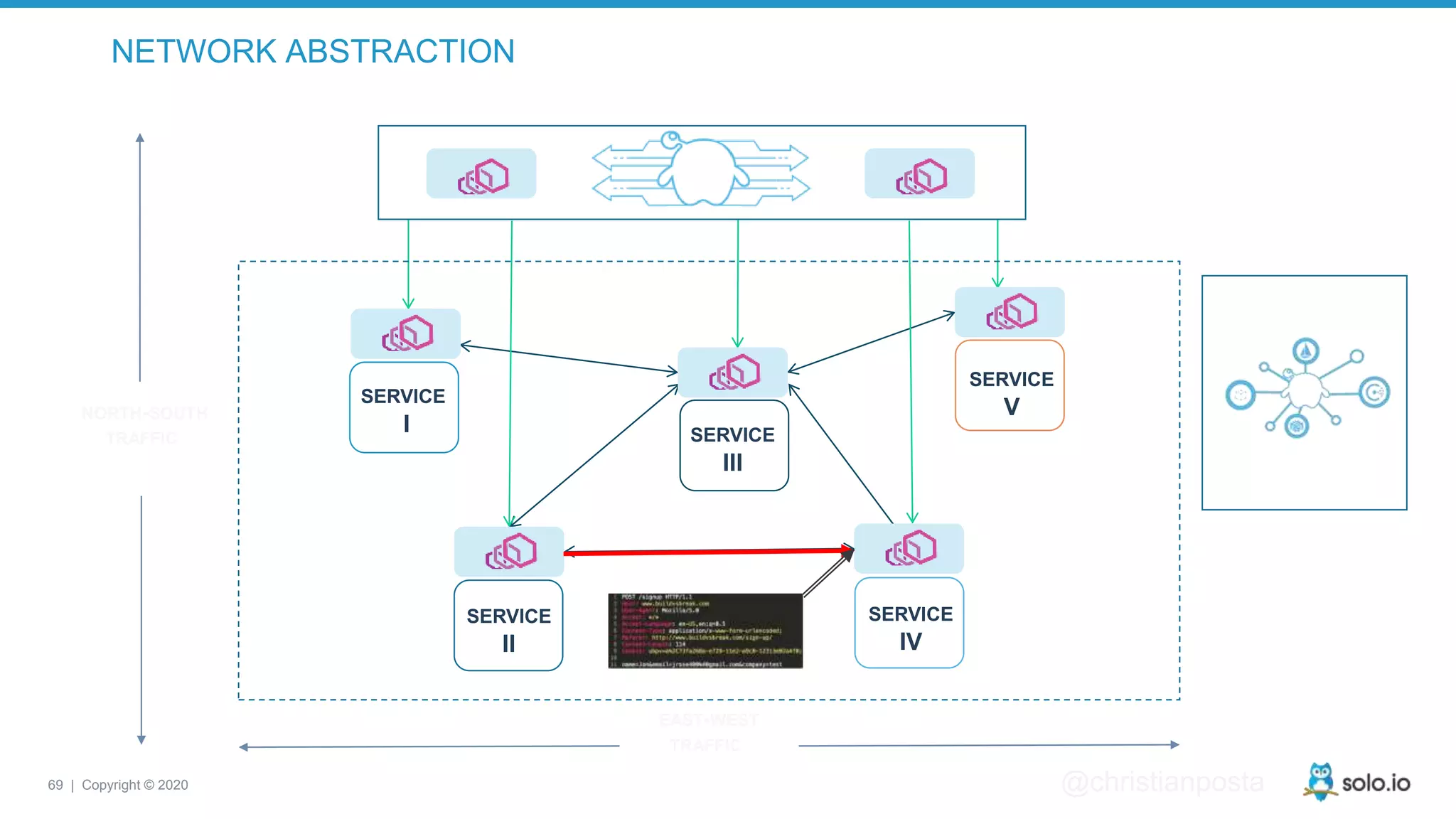
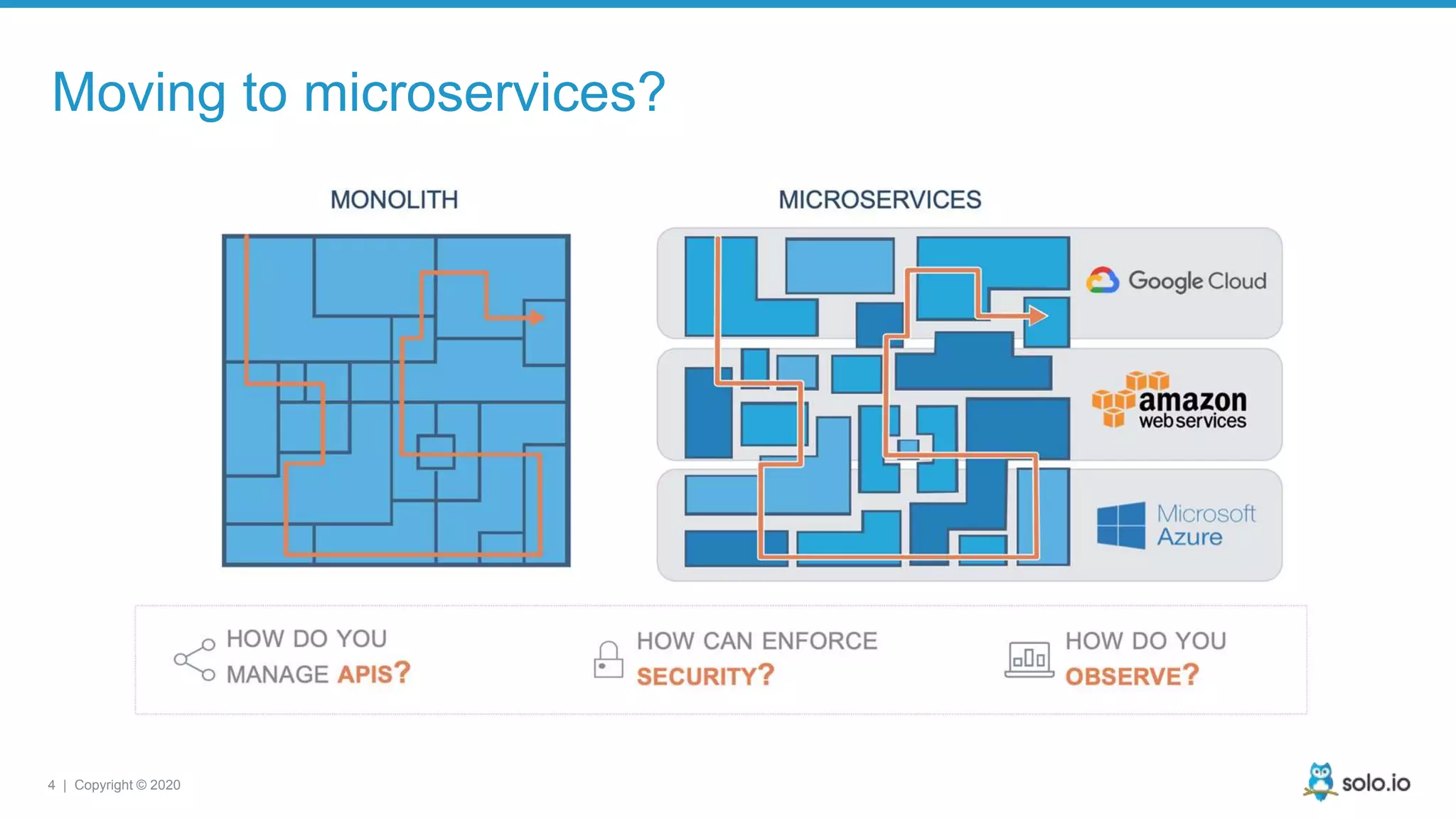
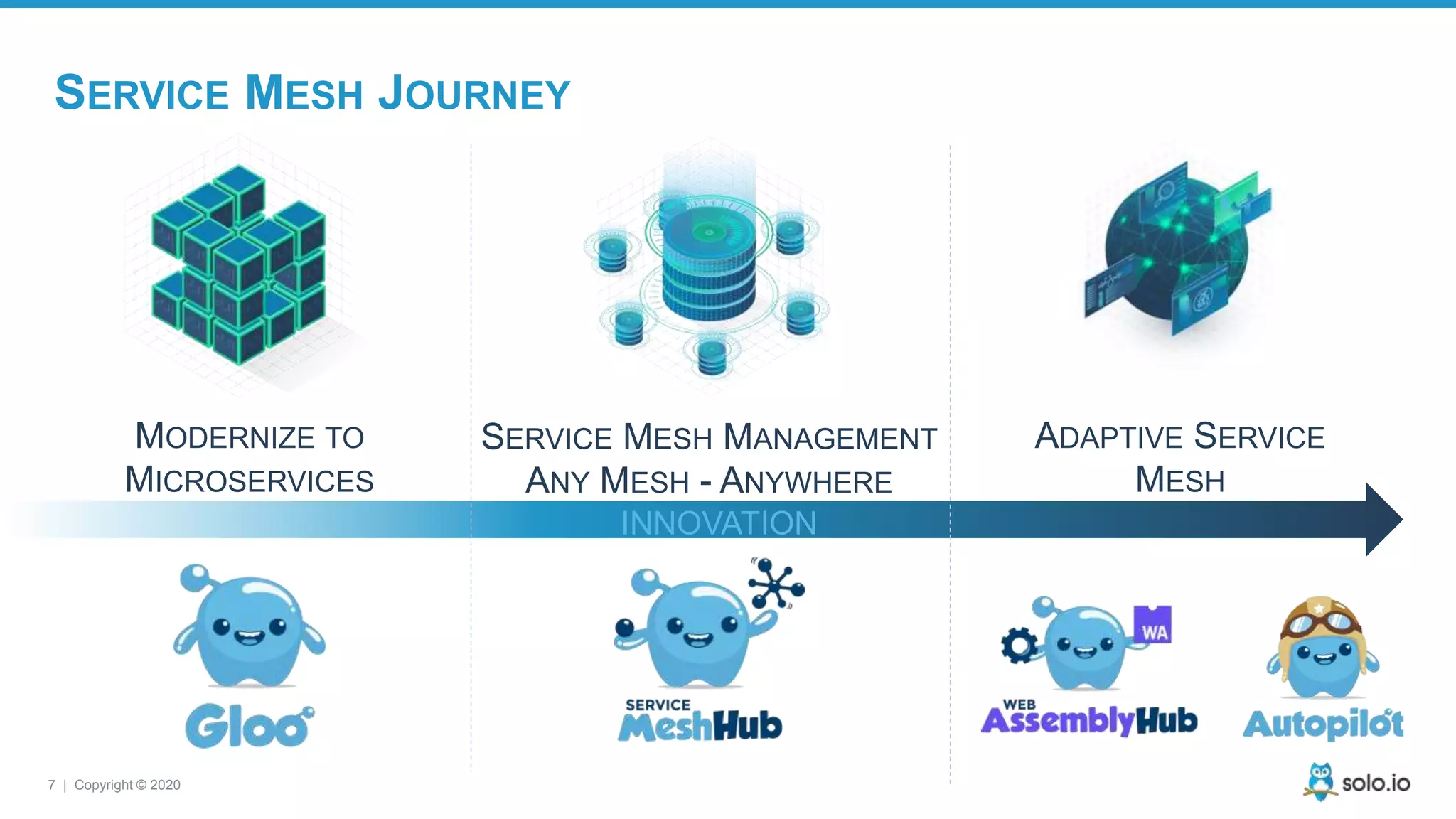
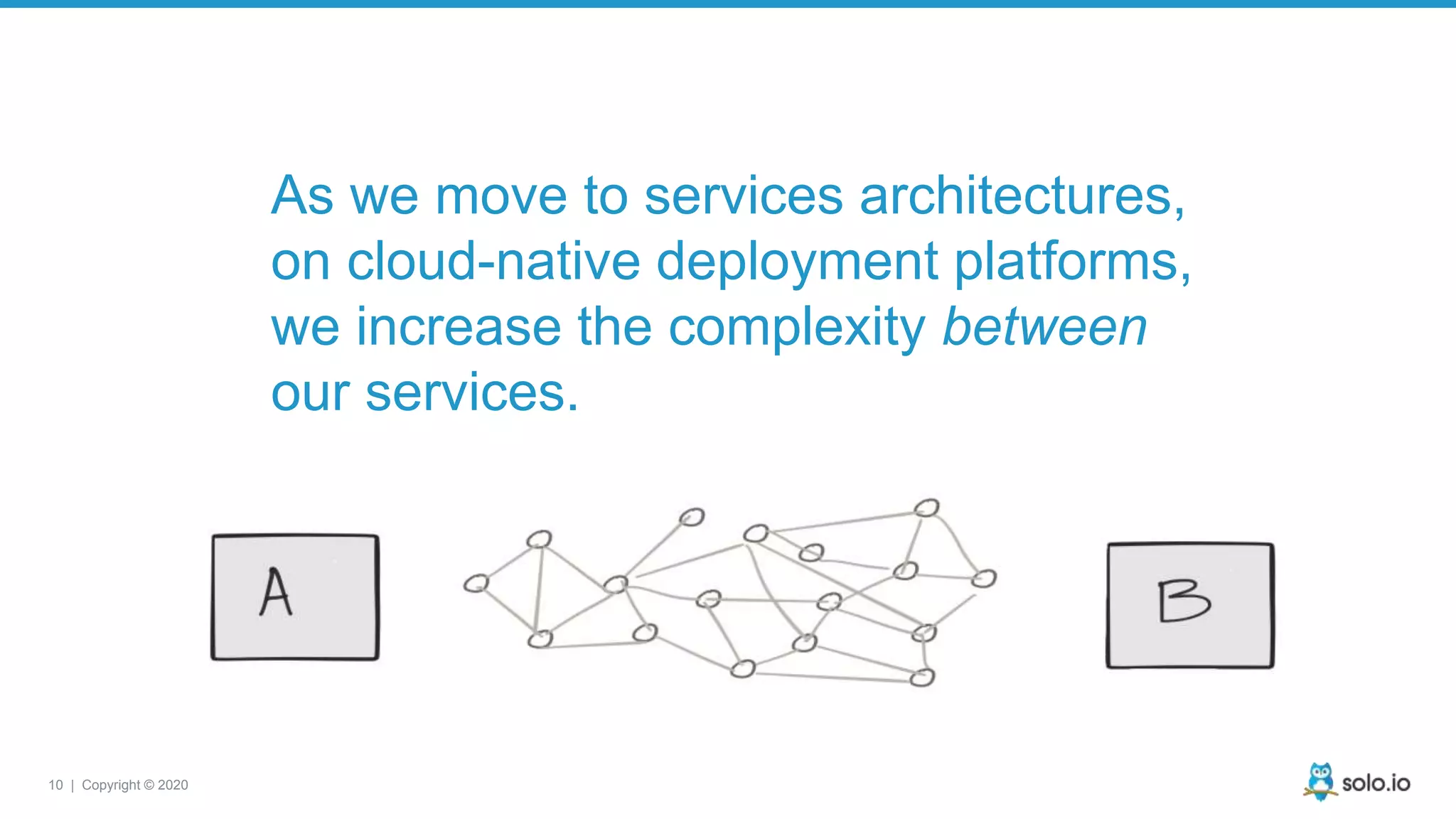
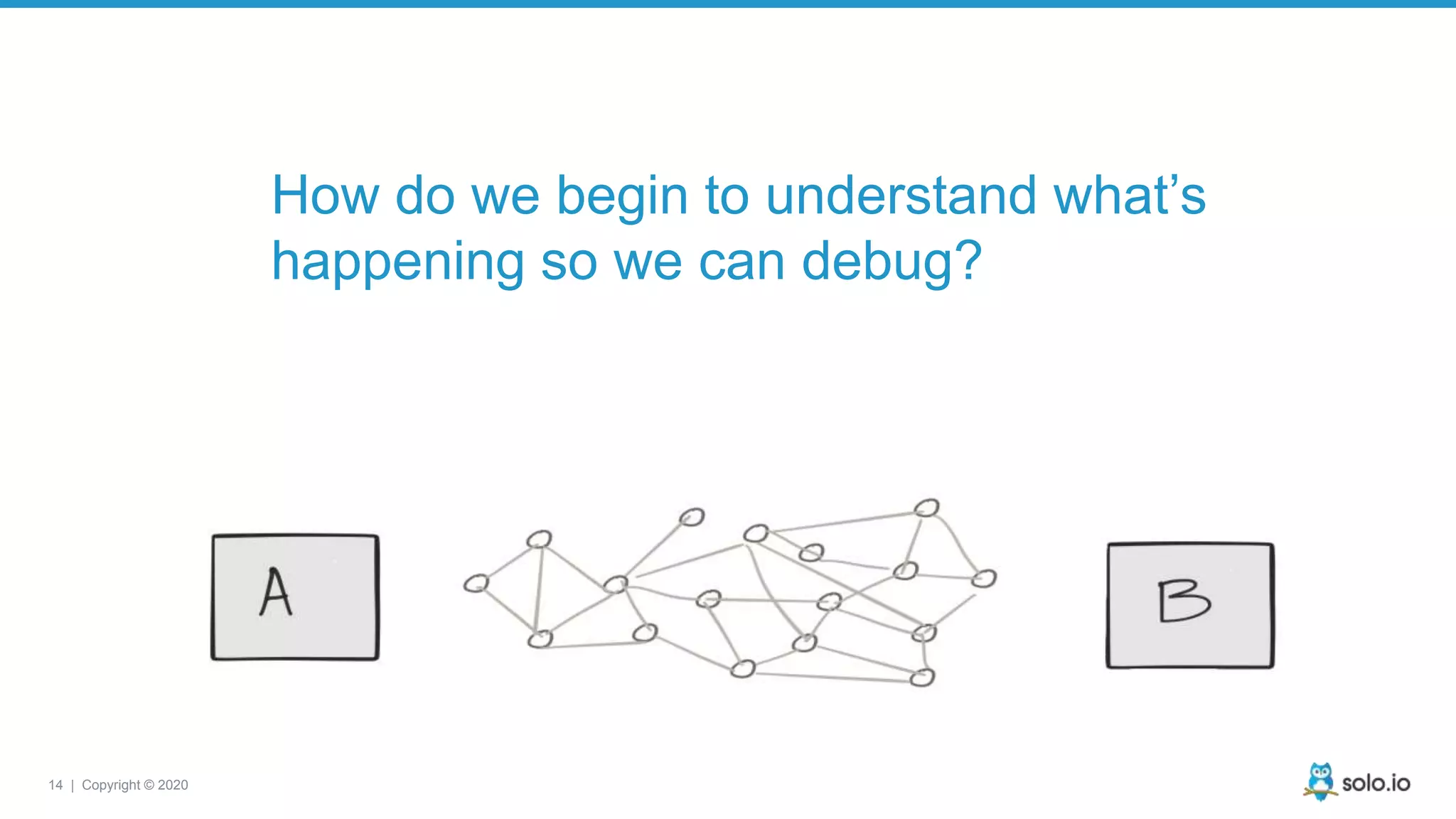
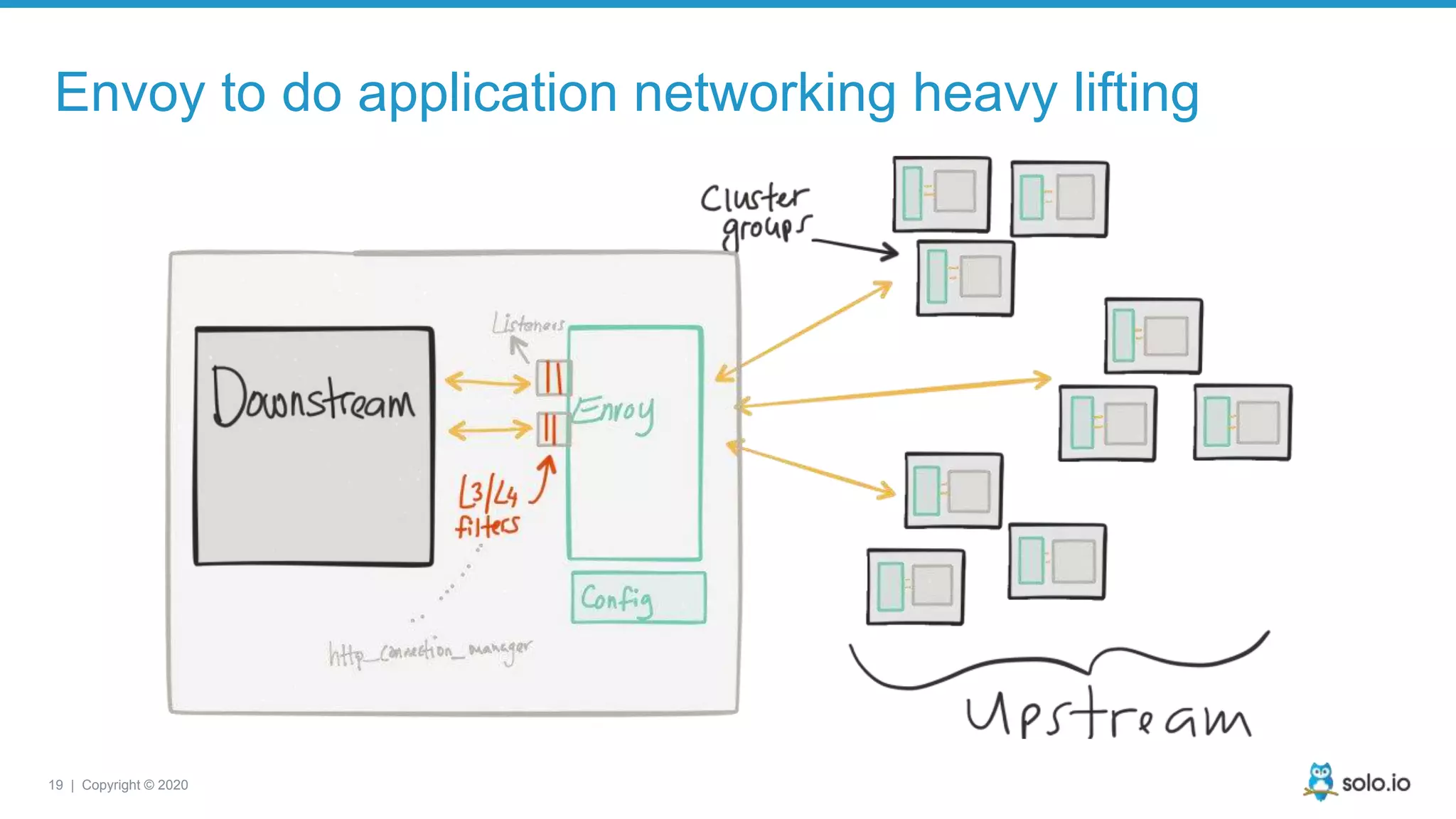
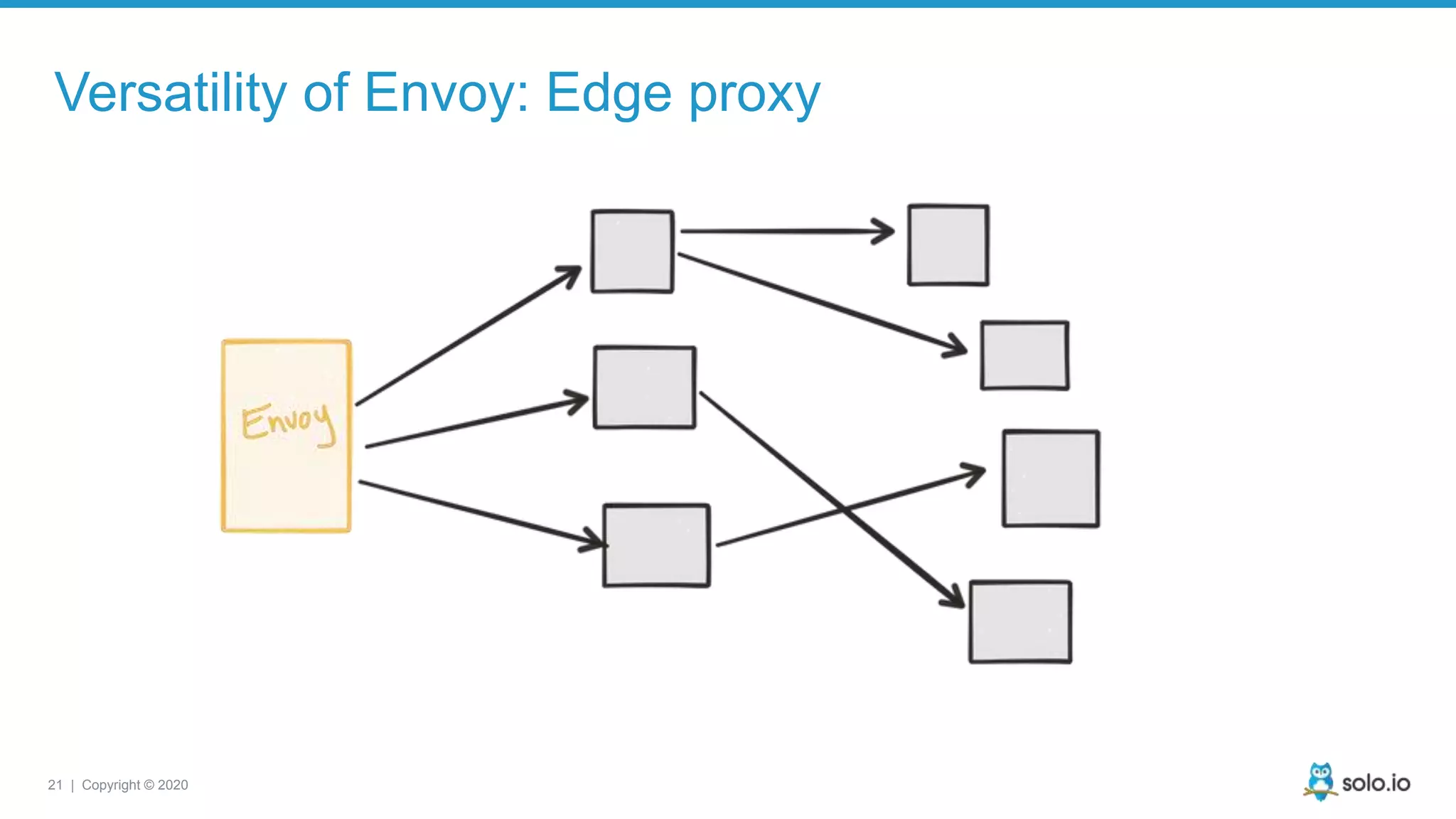
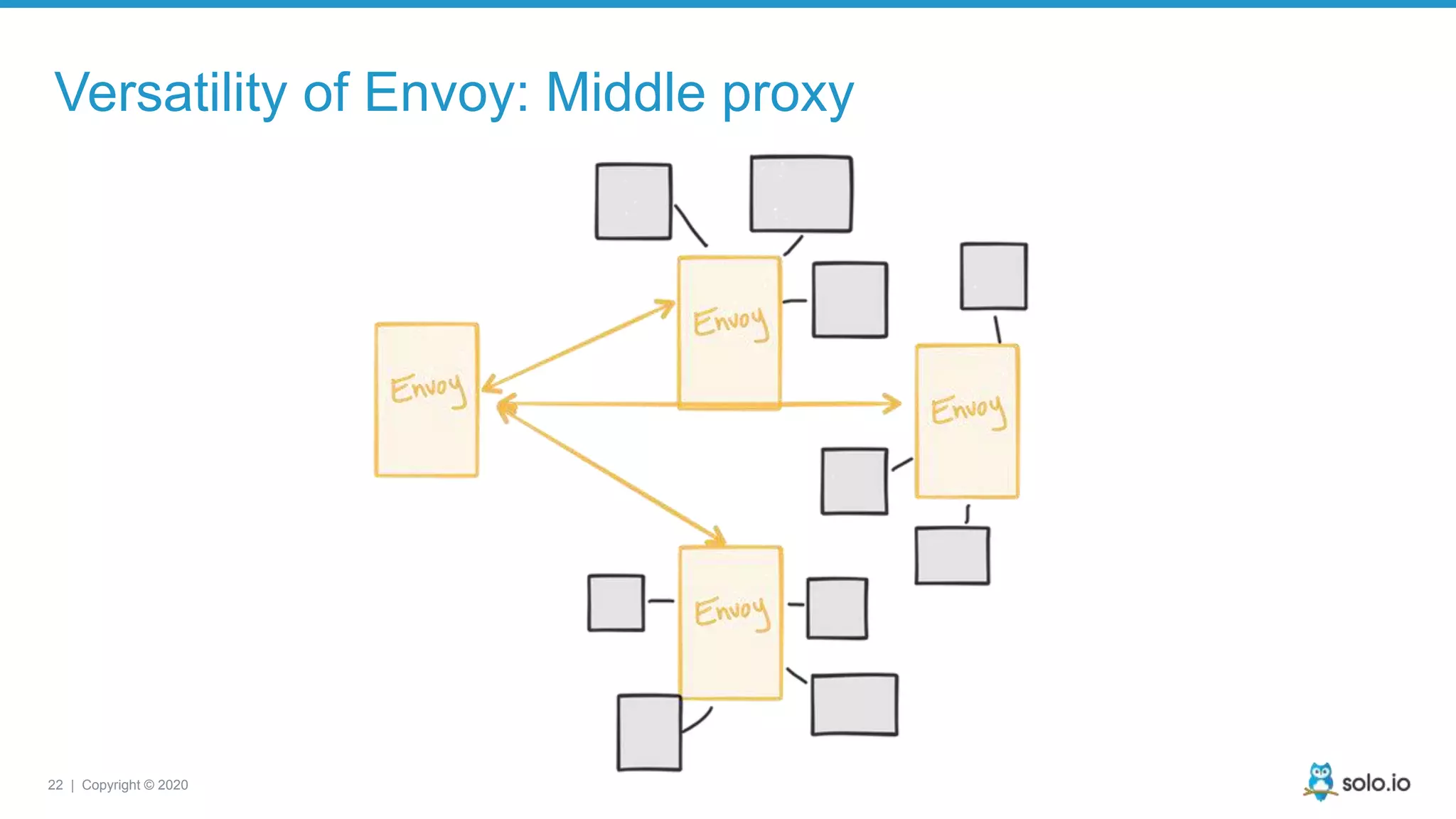
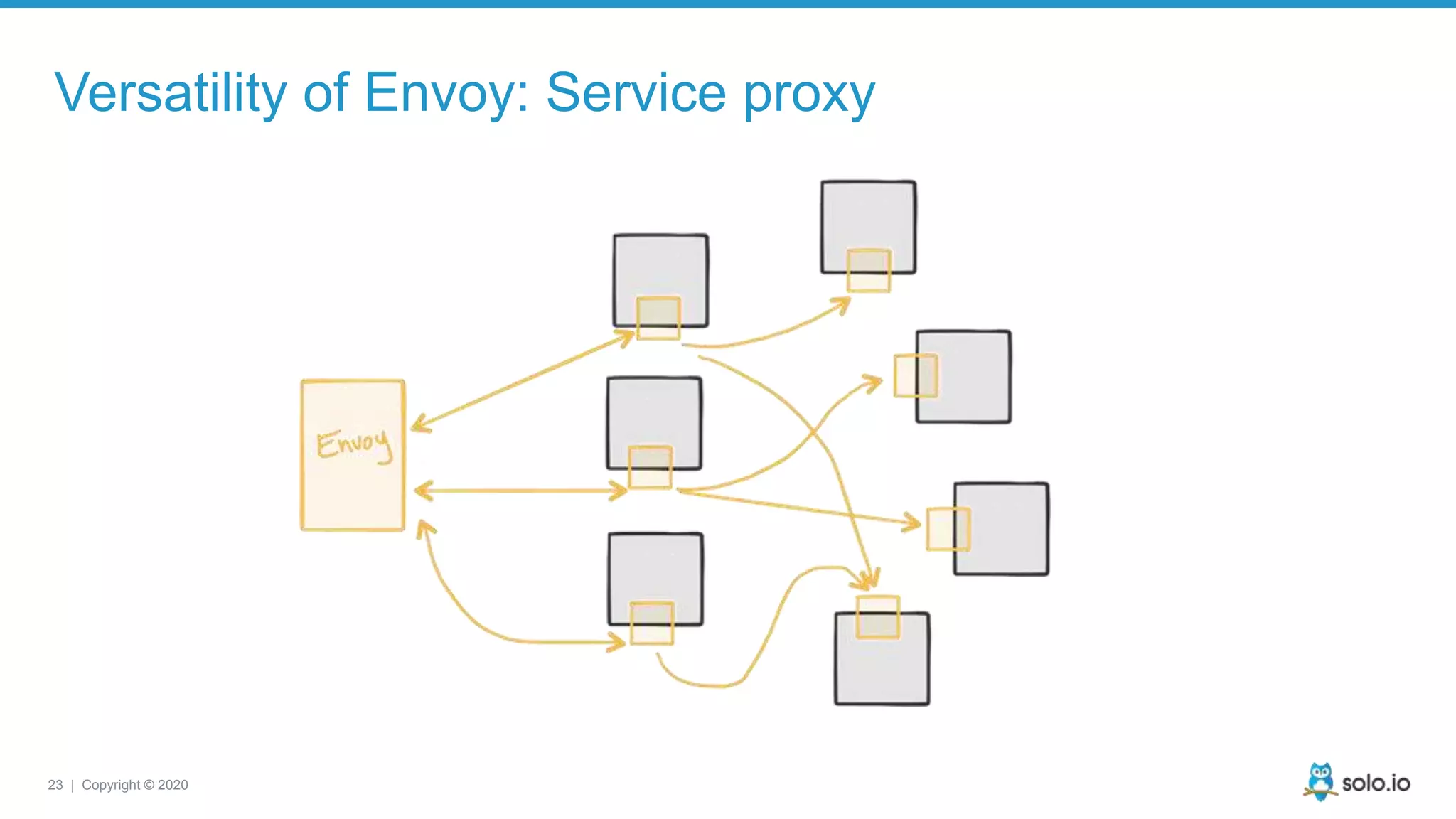
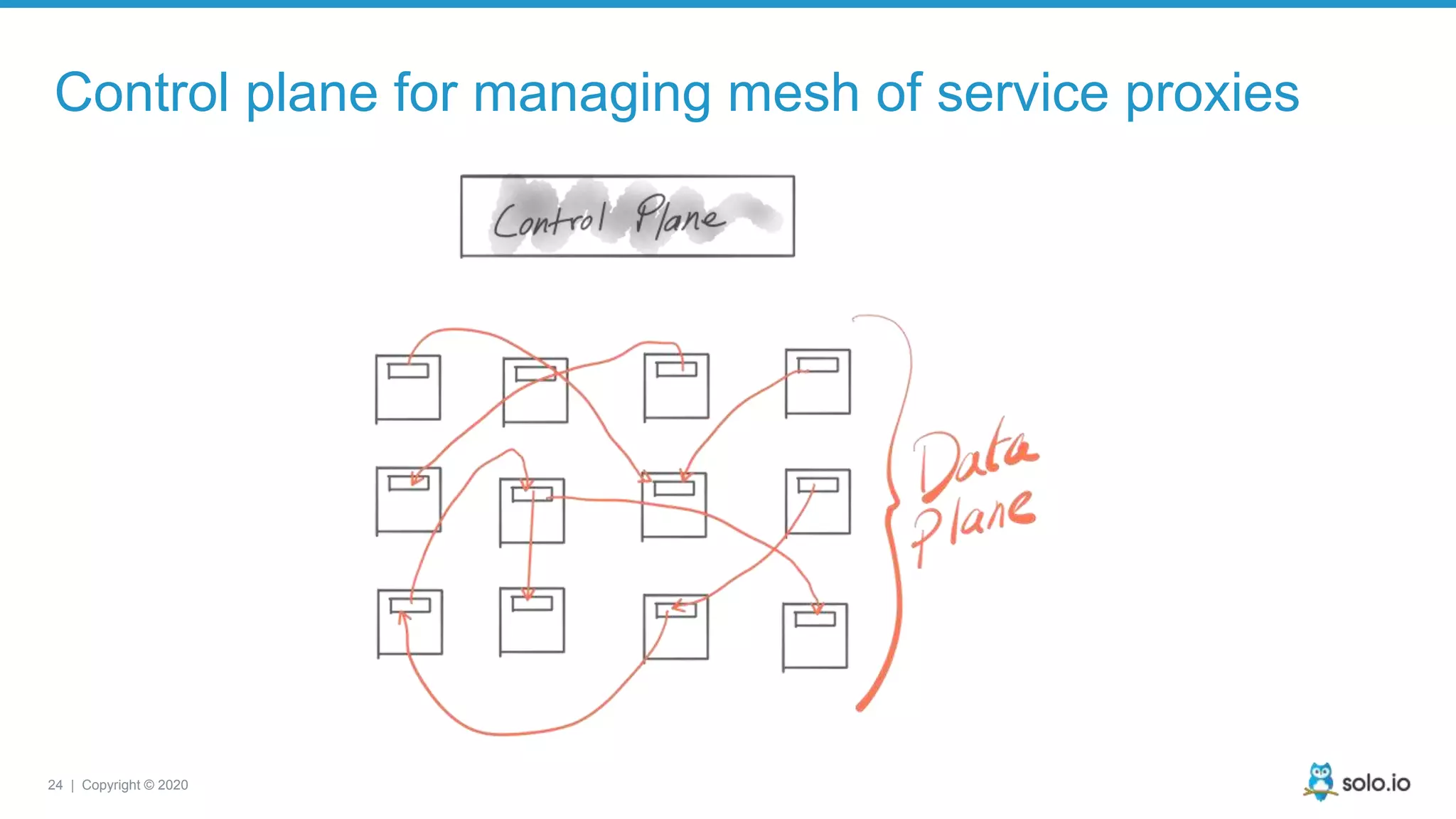
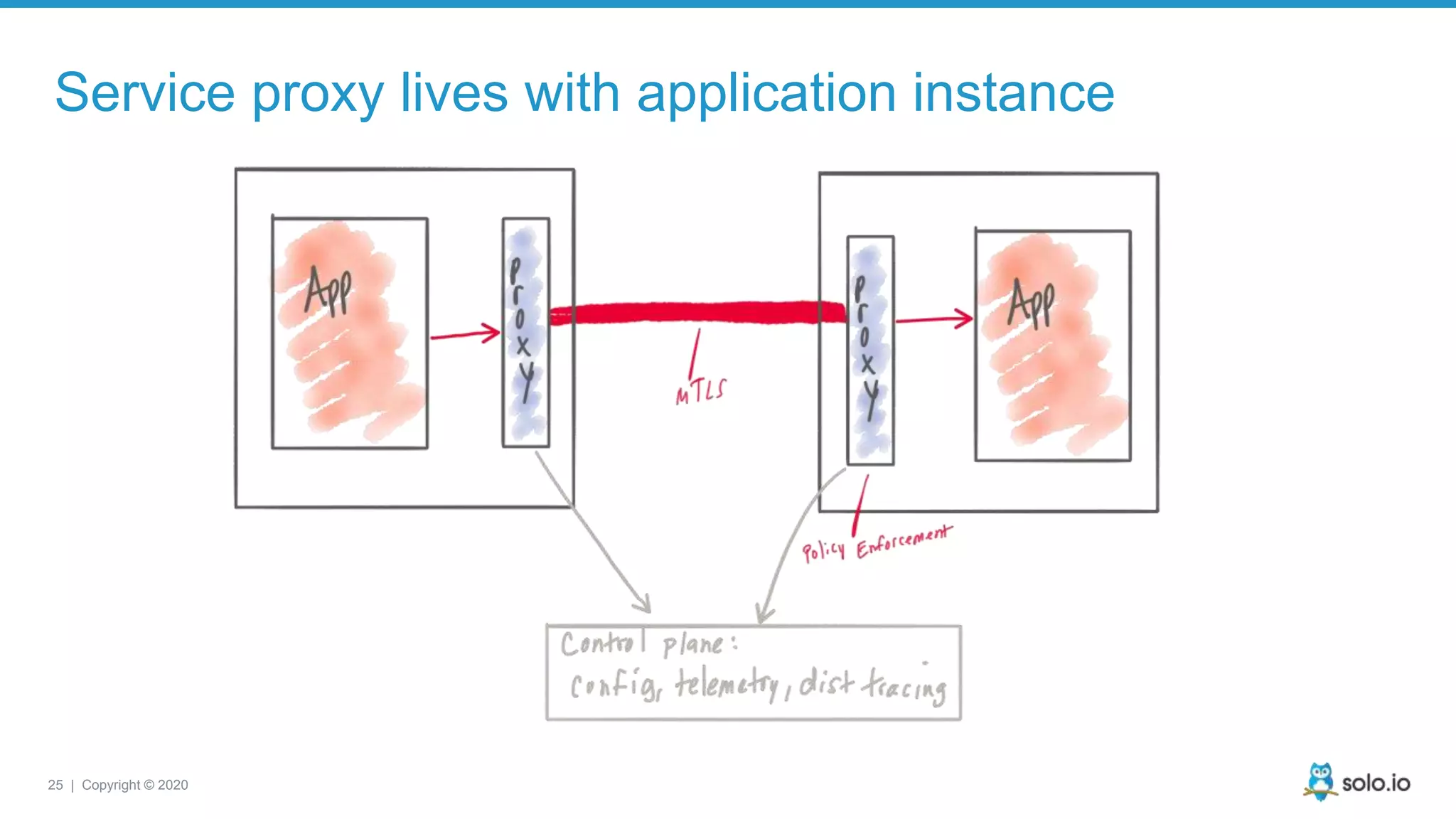
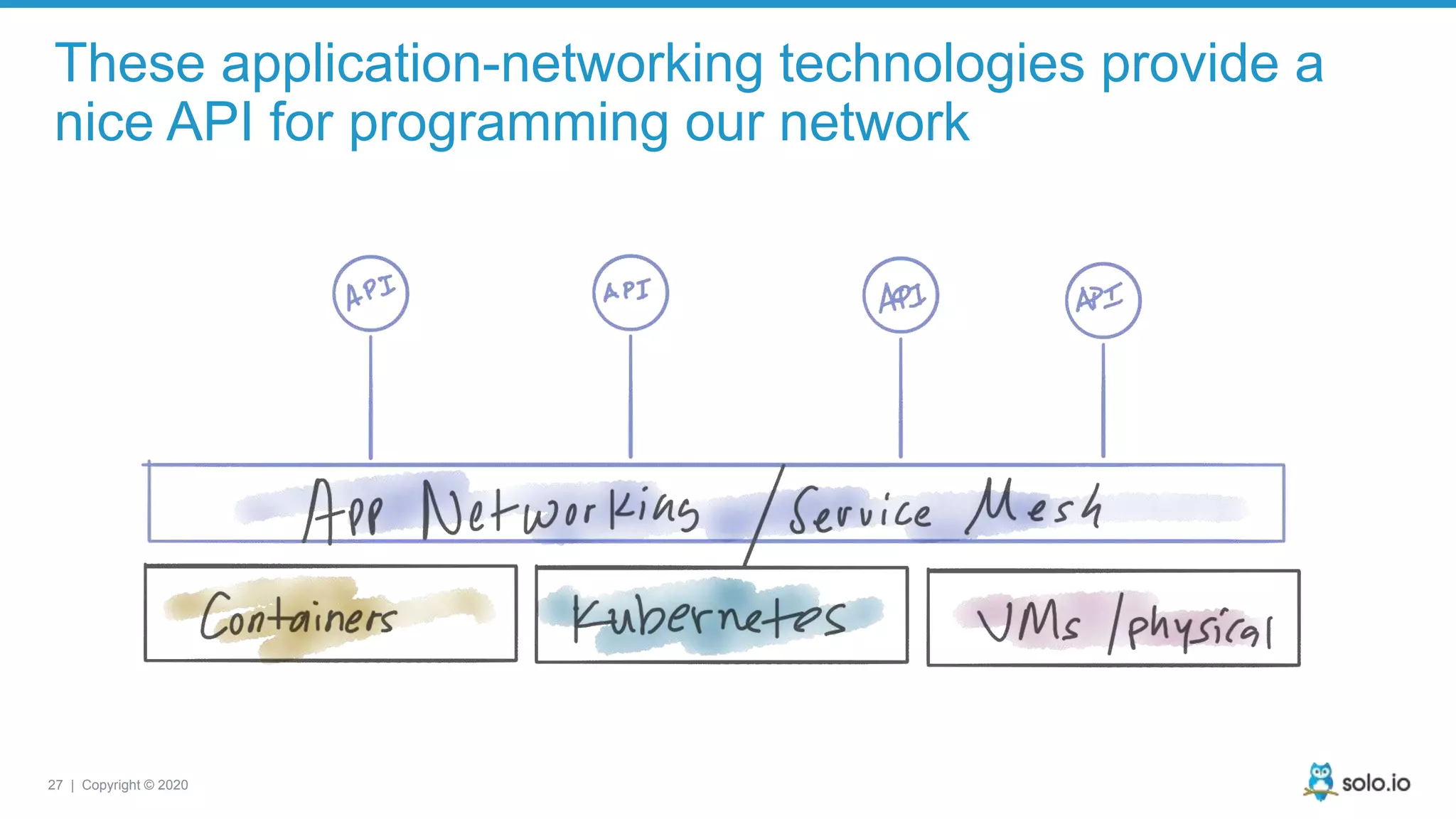
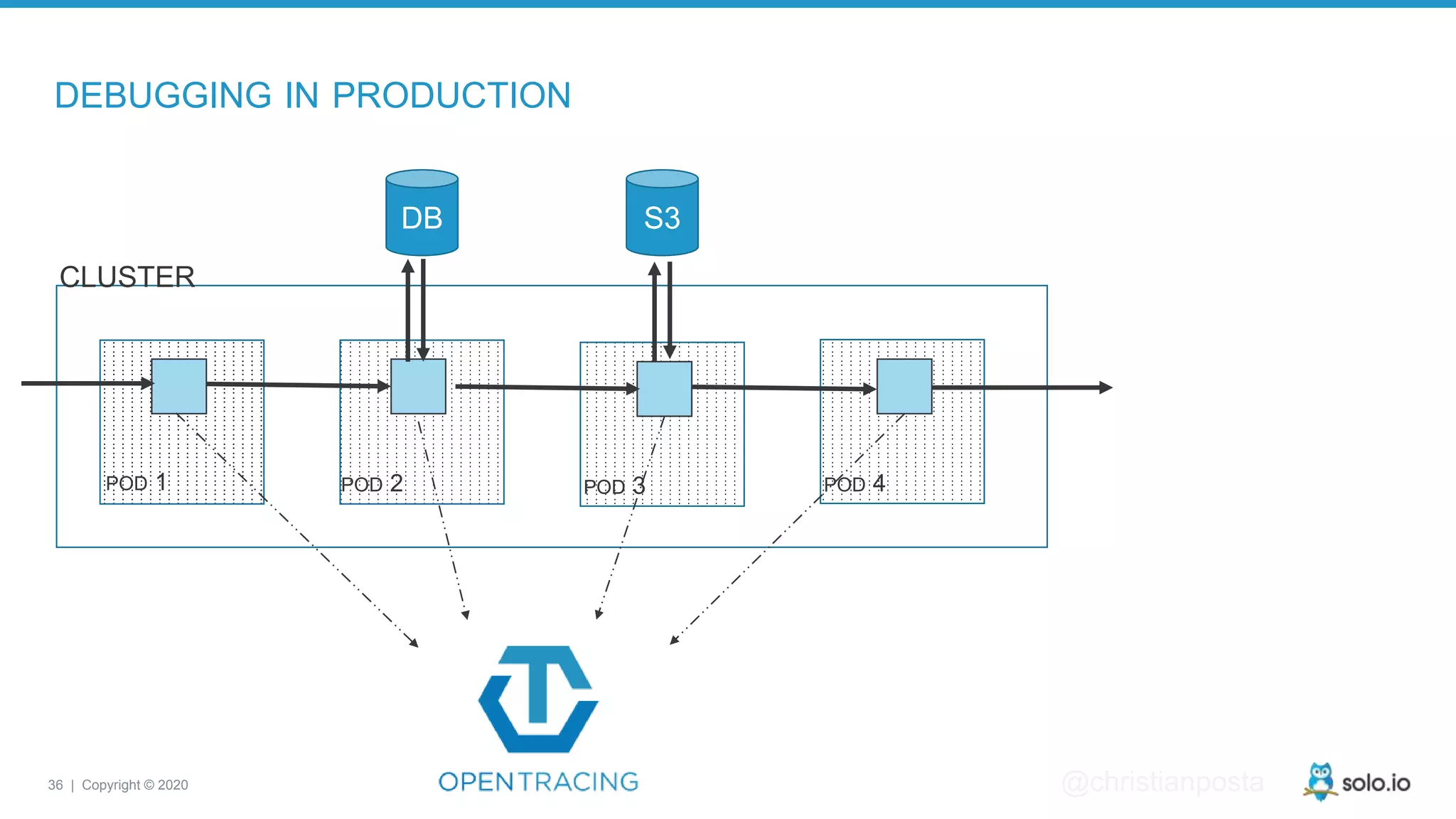
The document discusses cloud-native application debugging using Envoy and service mesh technologies, emphasizing the complexities introduced by microservices architectures. It explores challenges in debugging and observability, and highlights Envoy's capabilities in application networking, load balancing, and proactive debugging methods such as chaos engineering. Additionally, the document outlines tools and techniques for setting up lab environments for effective microservices debugging and testing.











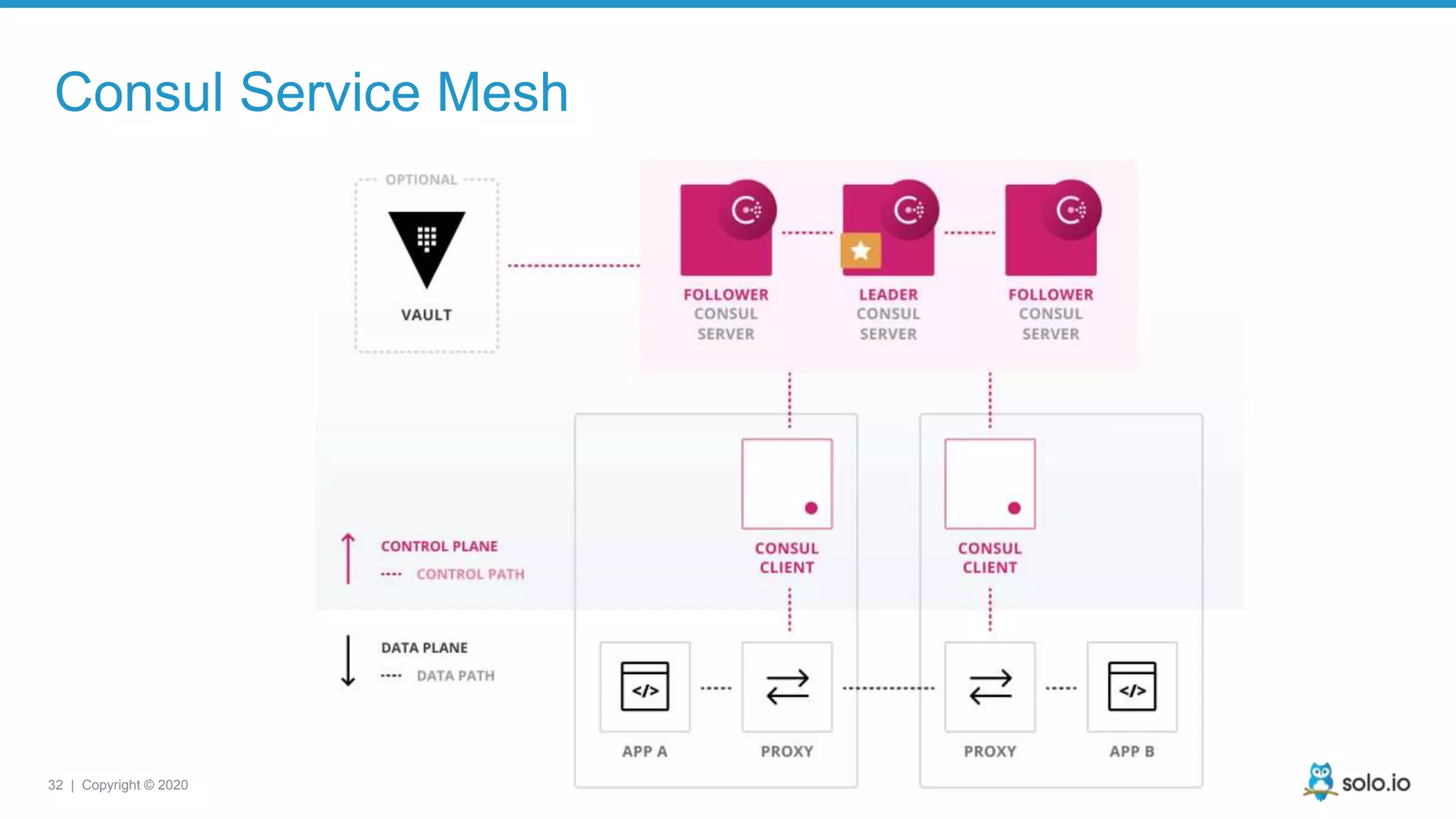
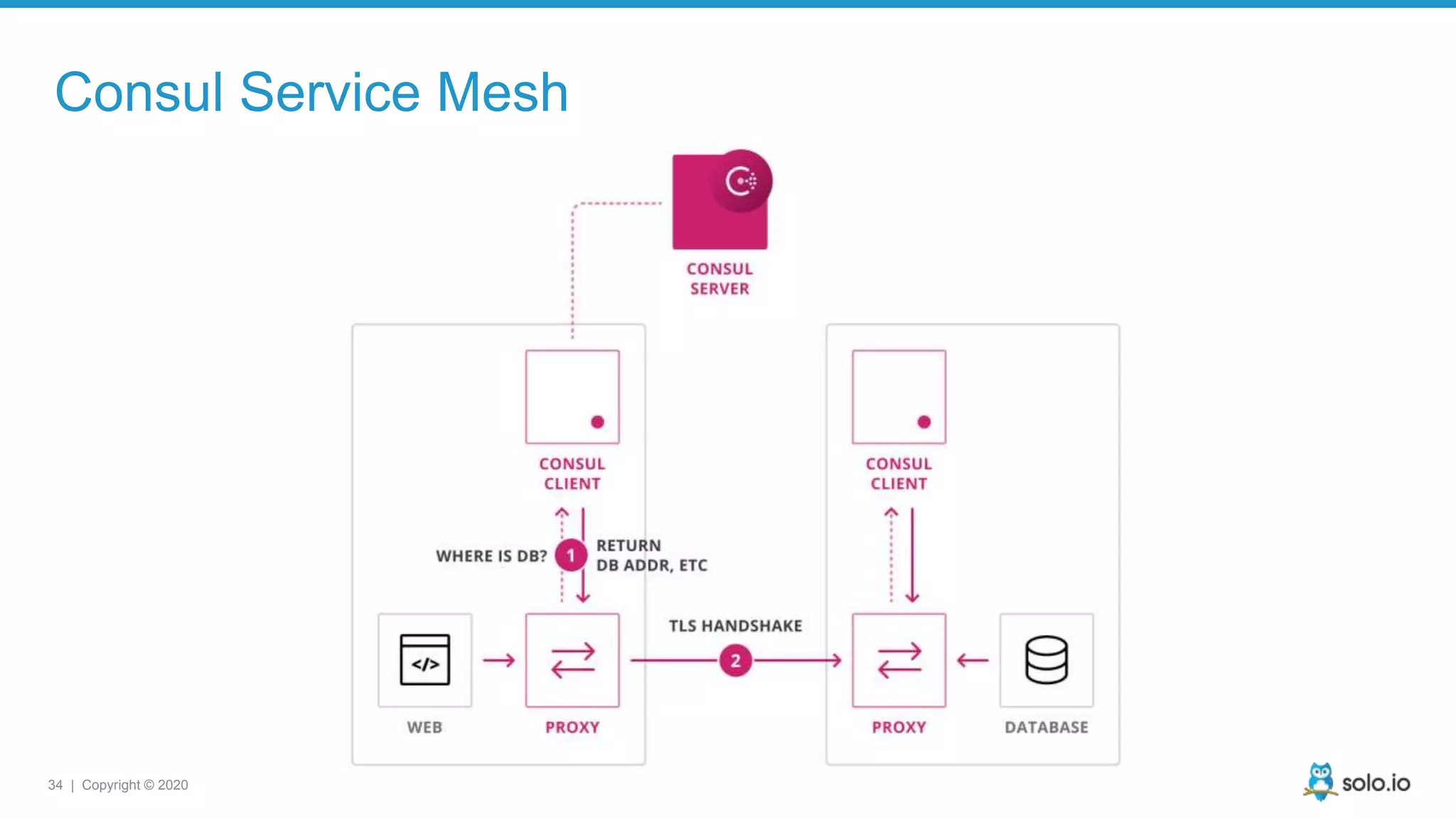
![33 | Copyright © 2020 Consul Service Mesh connect = { proxy = { config = { upstreams = [ { destination_name = "mysql", local_bind_port = 8001 } ] } } }](https://image.slidesharecdn.com/sacon-ny-2020-debug-microservices-200225143145/75/Cloud-Native-Application-Debugging-with-Envoy-and-Service-Mesh-33-2048.jpg)

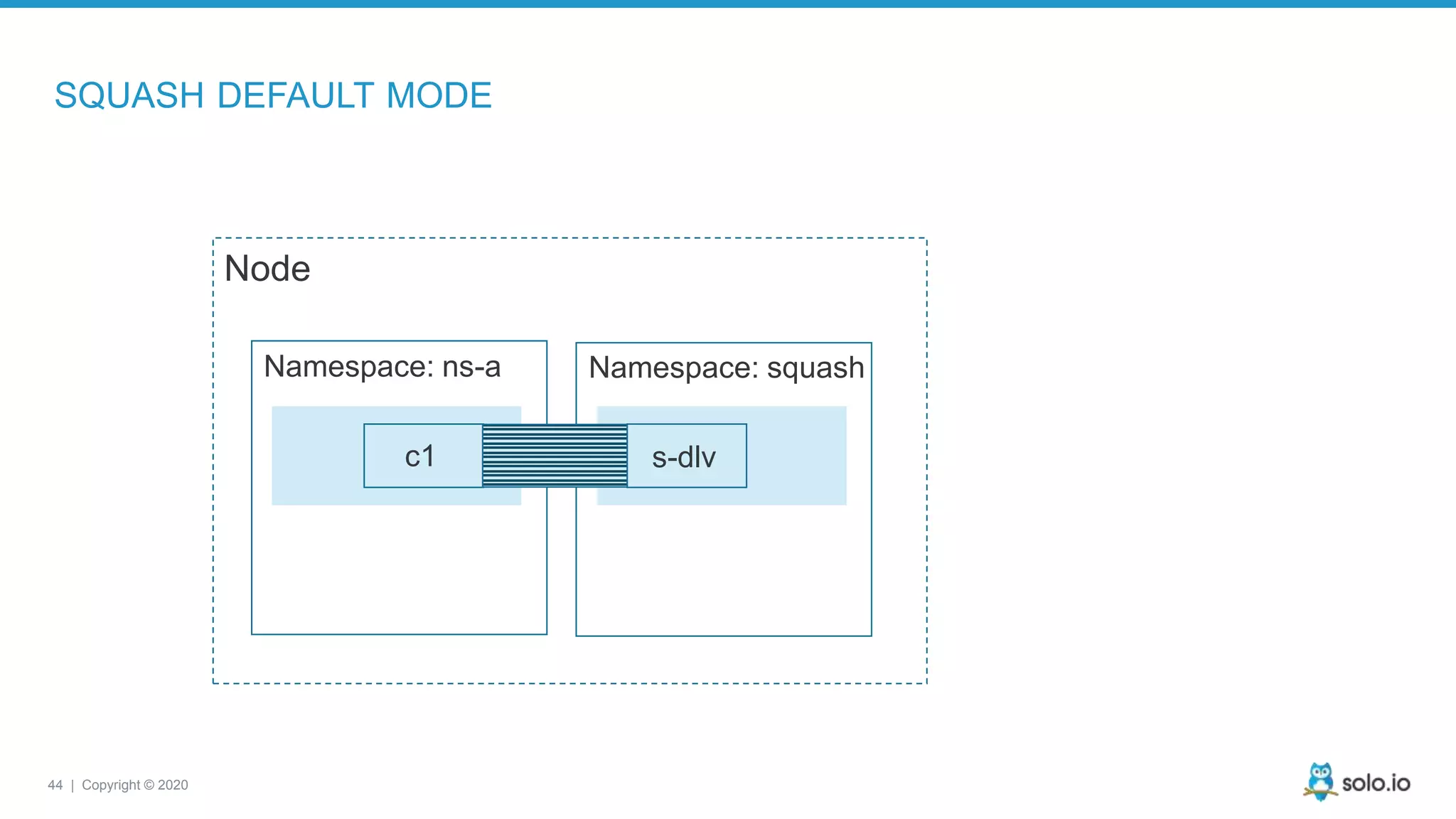
![45 | Copyright © 2020 -> ls -l /proc/self/ns total 0 lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 cgroup -> cgroup:[4026531835] lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 ipc -> ipc:[4026531839] lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 mnt -> mnt:[4026531840] lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 net -> net:[4026532009] lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 pid -> pid:[4026531836] lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 pid_for_children -> pid:[4026531836] lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 user -> user:[4026531837] lrwxrwxrwx 1 idit idit 0 Dec 7 01:14 uts -> uts:[4026531838] -> inod of mnt namespace (unique identifier to the container namespace) via CRI api call ExecSyncRequest Node Namespace: ns-a s-dlv CRI c1 We need to translate the pid of the process (application that run in the container) to the host pid namespace to allow debugger to attach. Namespace: Squash](https://image.slidesharecdn.com/sacon-ny-2020-debug-microservices-200225143145/75/Cloud-Native-Application-Debugging-with-Envoy-and-Service-Mesh-45-2048.jpg)