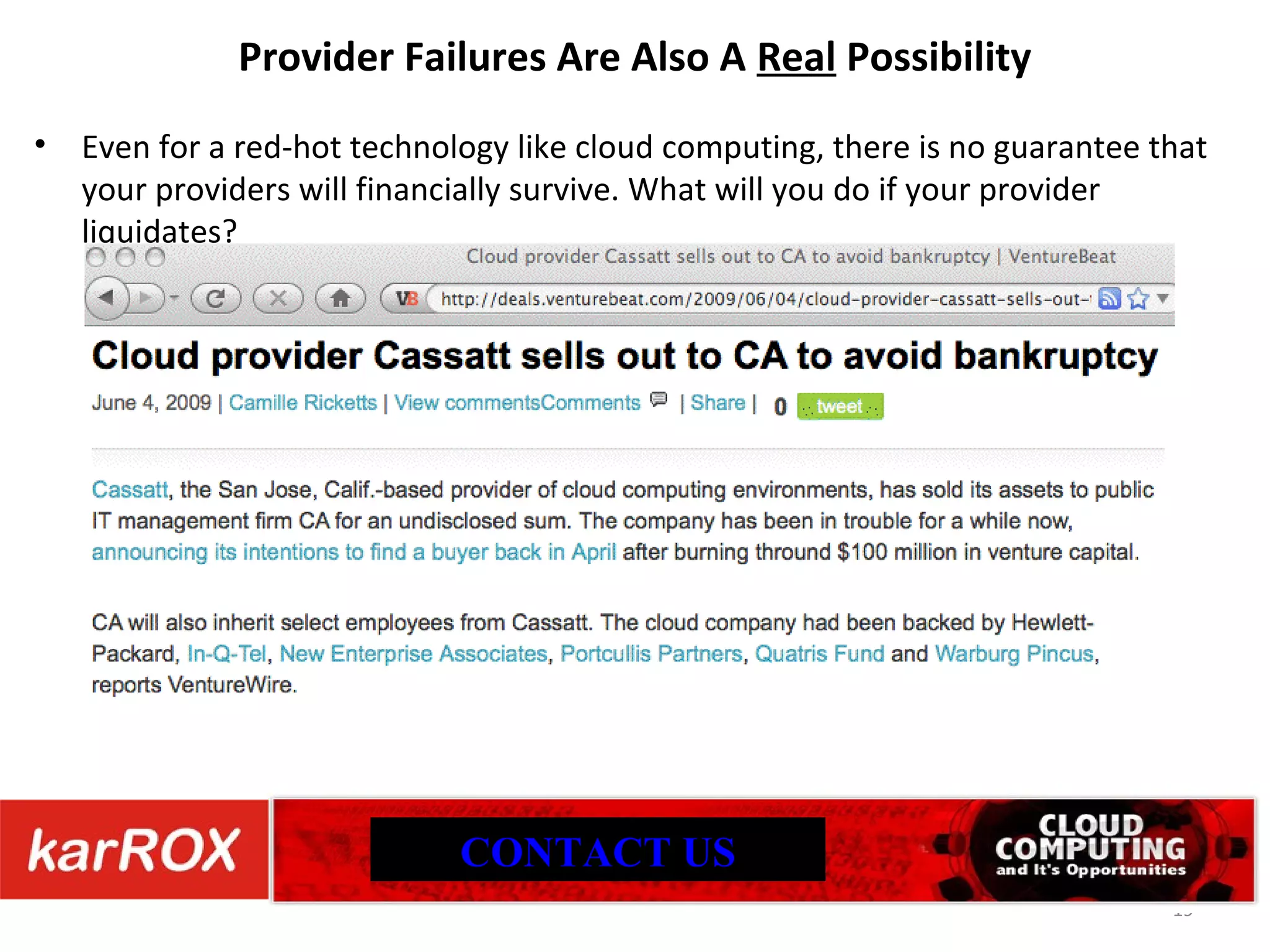
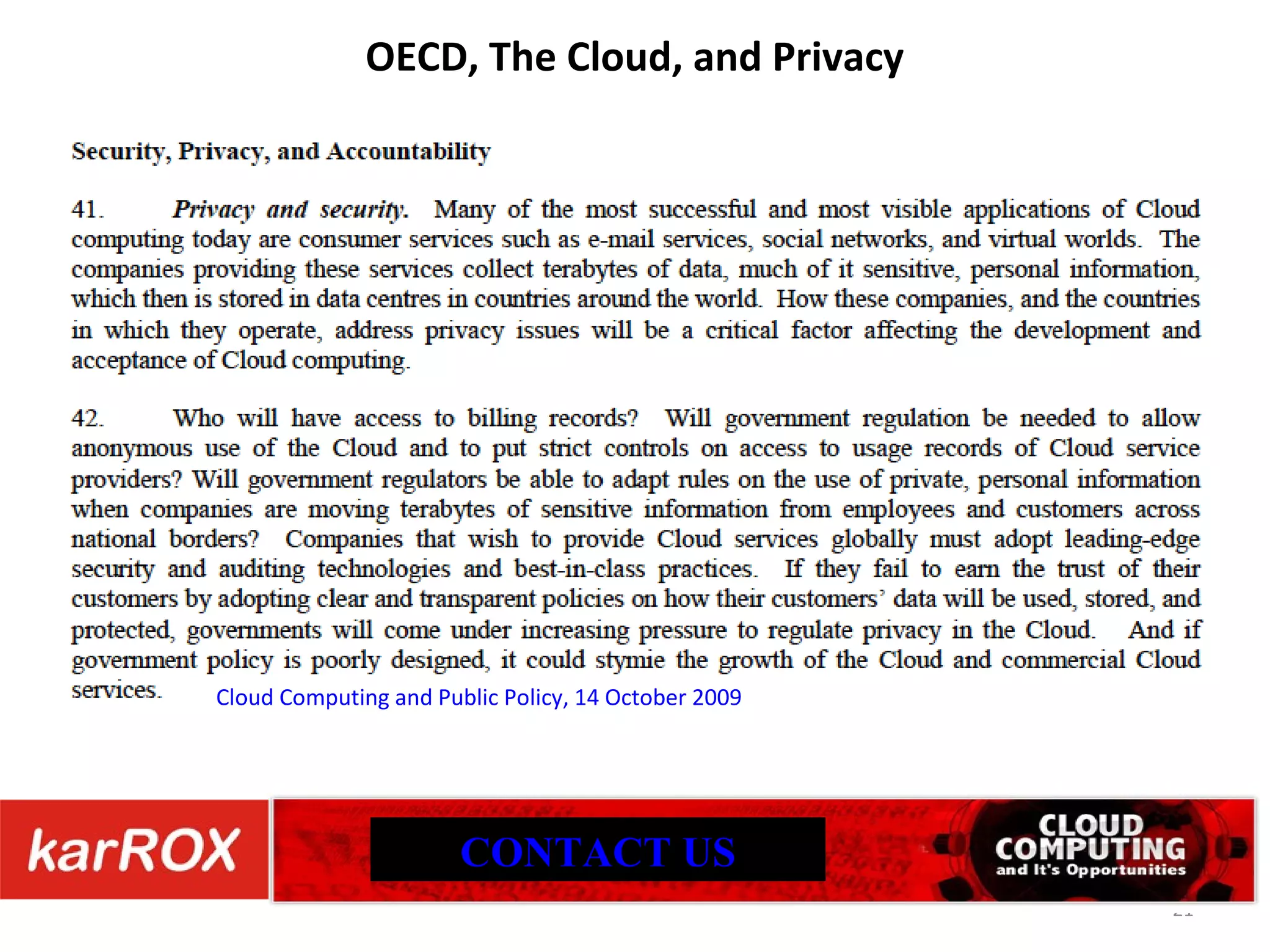
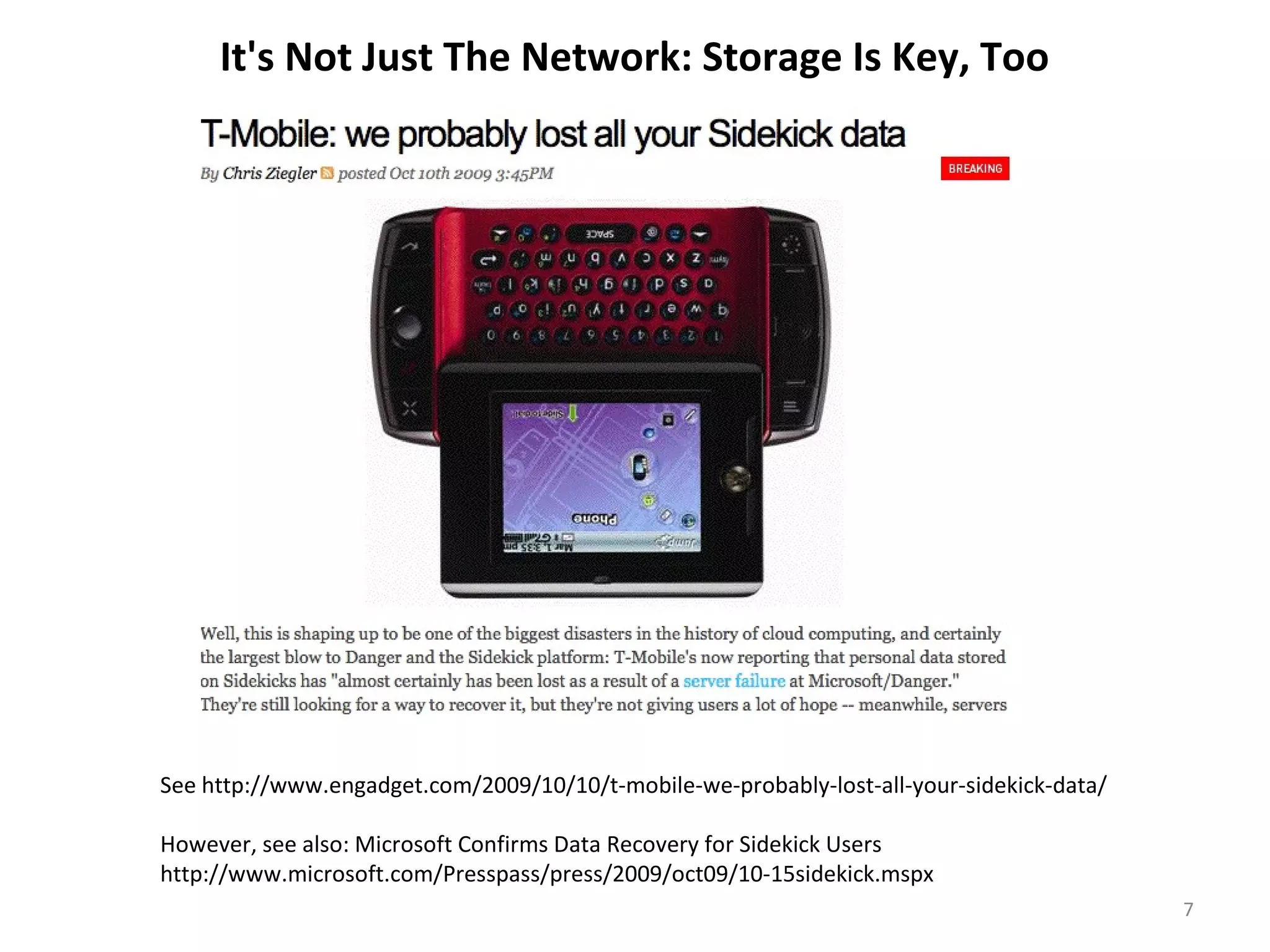
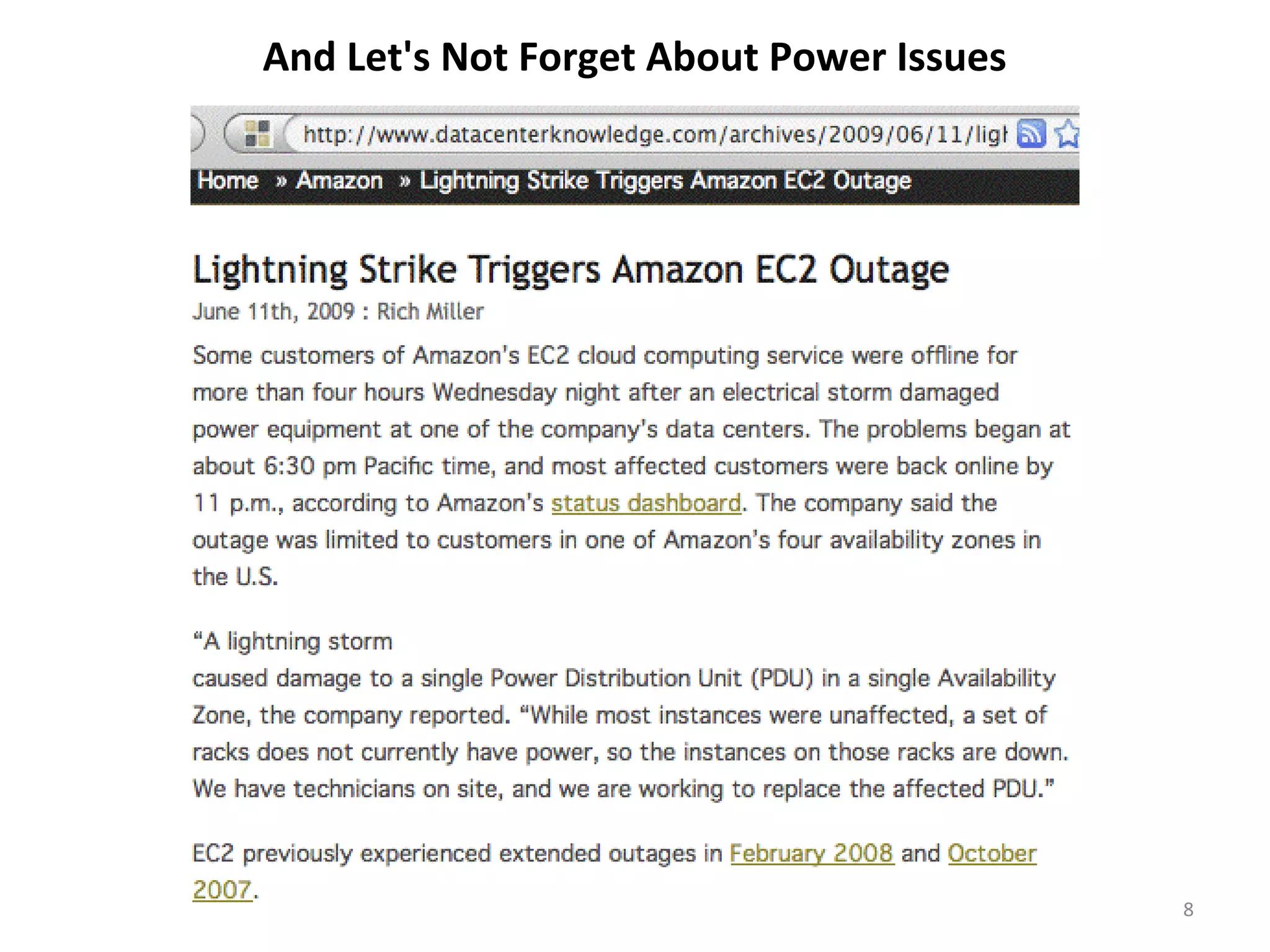
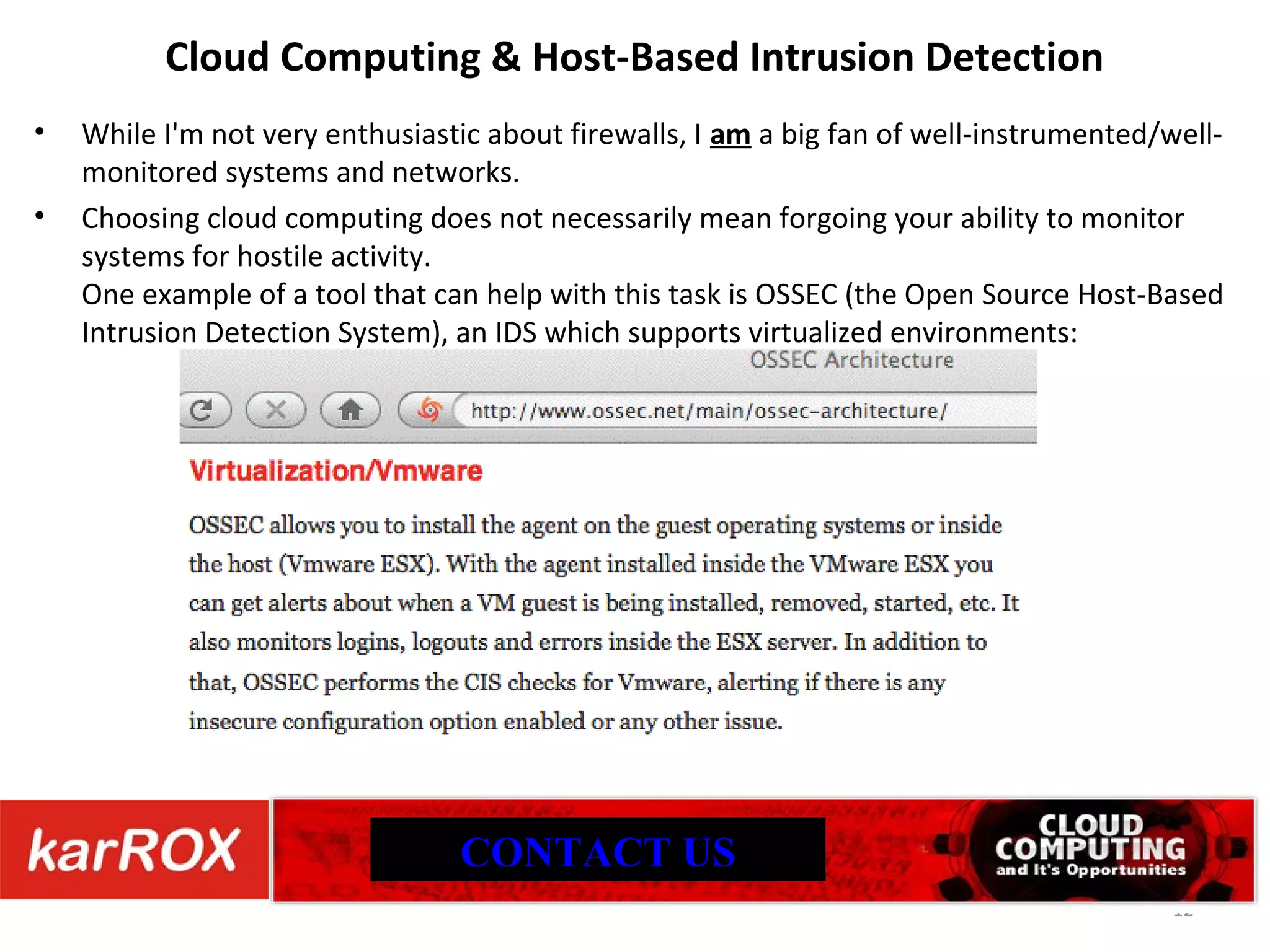
The document discusses cloud computing security, highlighting that common web vulnerabilities like SQL injection and physical security concerns are equally relevant for cloud environments as for traditional hosting. It emphasizes the importance of availability, risk management, compliance, and the trustworthiness of cloud providers, including their practices regarding employee vetting and transparency. Unique issues such as data loss, provider location, and incident management are also addressed, underscoring the need for thorough due diligence in cloud service partnerships.





![Cloud Computing Also Relies on the Security of Virtualization Because cloud computing is built on top of virtualization, if there are security issues with virtualization, then there will also security issues with cloud computing. For example, could someone escape from a guest virtual machine instance to the host OS? While the community has traditionally been somewhat skeptical of this possibility, that changed with Blackhat USA 2009, where Kostya Kortchinsky of Immunity Inc. presented "Cloudburst: A VMware Guest to Host Escape Story", see here Kostya opined: "VMware isn't an additional security layer, it's just another layer to find bugs in" [put another way, running a virtualization product increases the attack surface] CONTACT US](https://image.slidesharecdn.com/cloudcomputingsecurityissues-101026021742-phpapp01/75/Cloud-Computing-Security-Issues-13-2048.jpg)


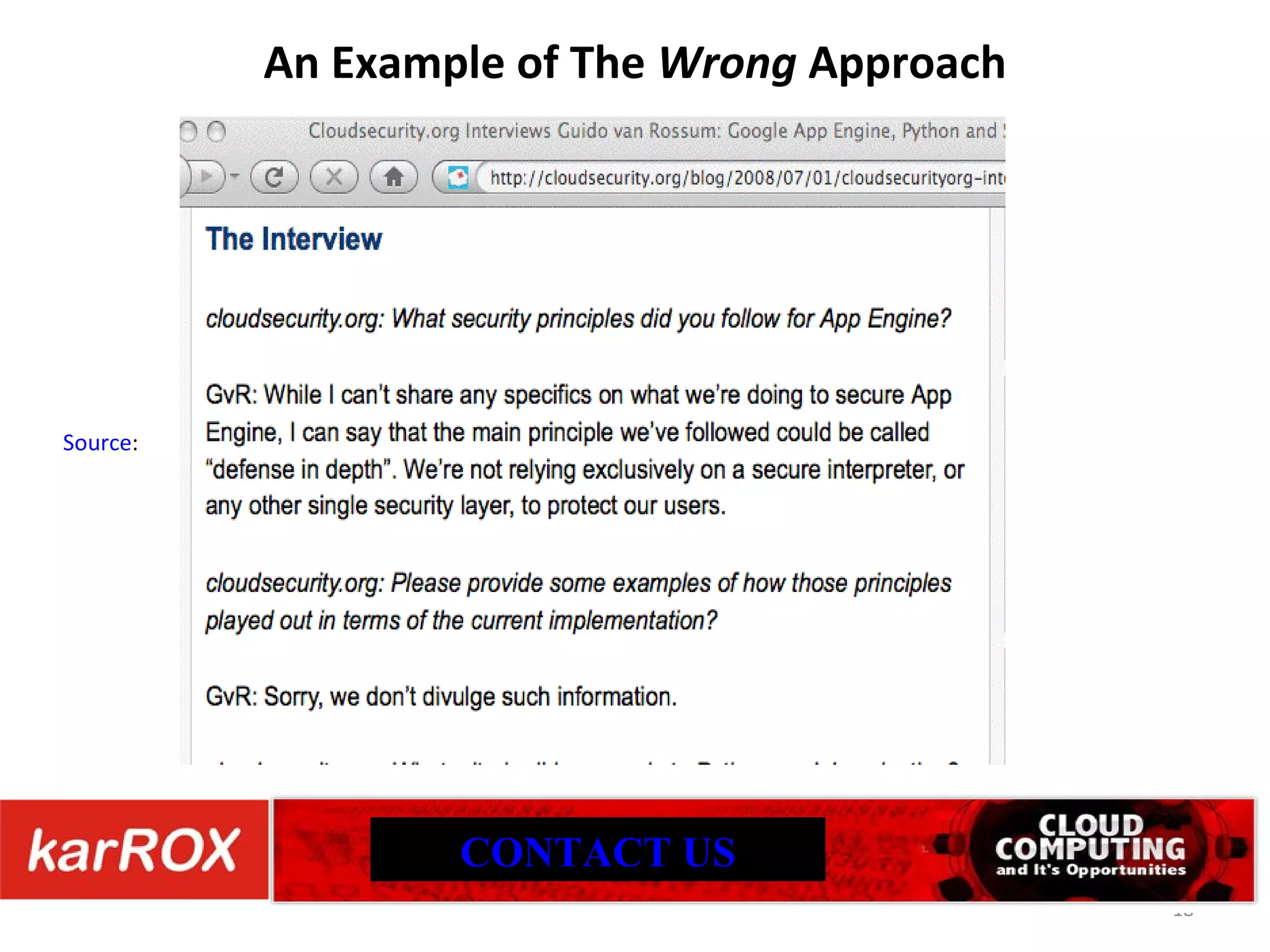
![Cloud Provider Transparency You will only be able to assess the sufficiency of cloud provider security practices if the cloud provider is willing to disclose its security practices to you. If your provider treats security practices as a confidential or business proprietary thing, and won't disclose their security practices to you, you'll have a hard time assessing the sufficiency of their security practices. Unfortunately, you may need to consider using a different provider. Remember: "Trust, but verify." [A proverb frequently quoted by President Reagan during arms control negotiations] I'm not known for being a big Microsoft cheerleader, but Microsoft deserves recognition for promoting both their Cloud Computing Advancement Act and pressing cloud vendors to police themselves when it comes to transparency. See here CONTACT US](https://image.slidesharecdn.com/cloudcomputingsecurityissues-101026021742-phpapp01/75/Cloud-Computing-Security-Issues-17-2048.jpg)