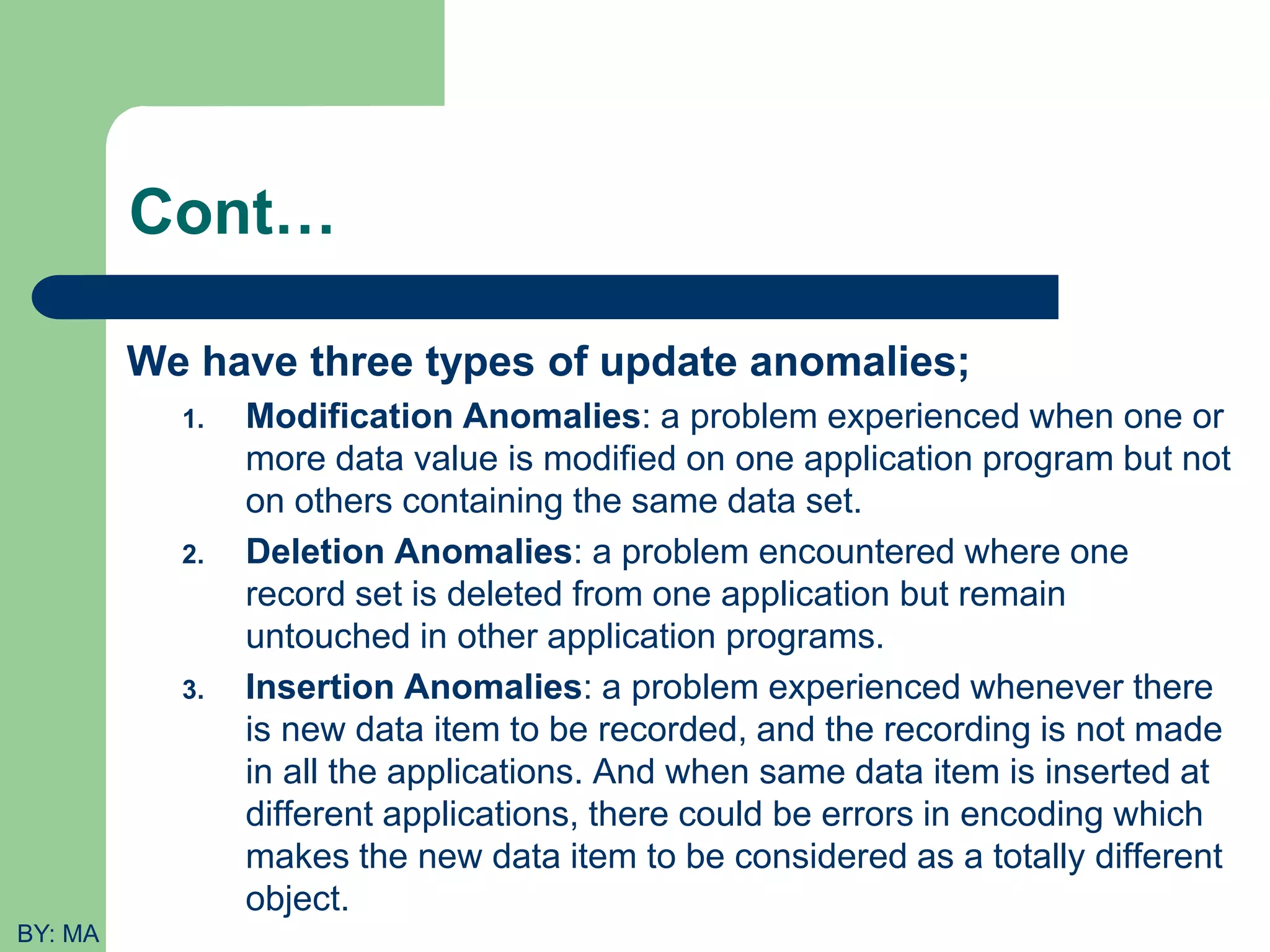
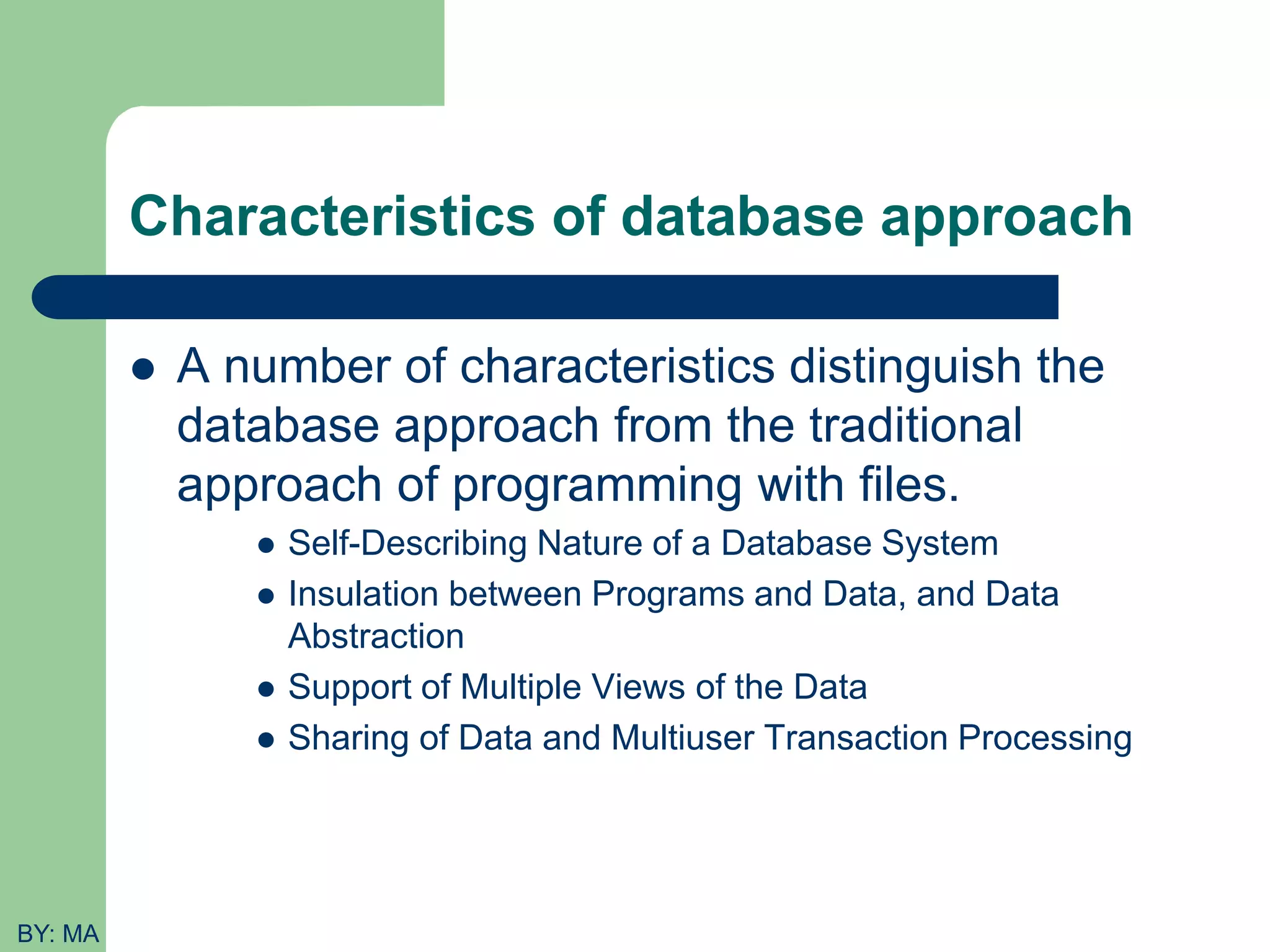
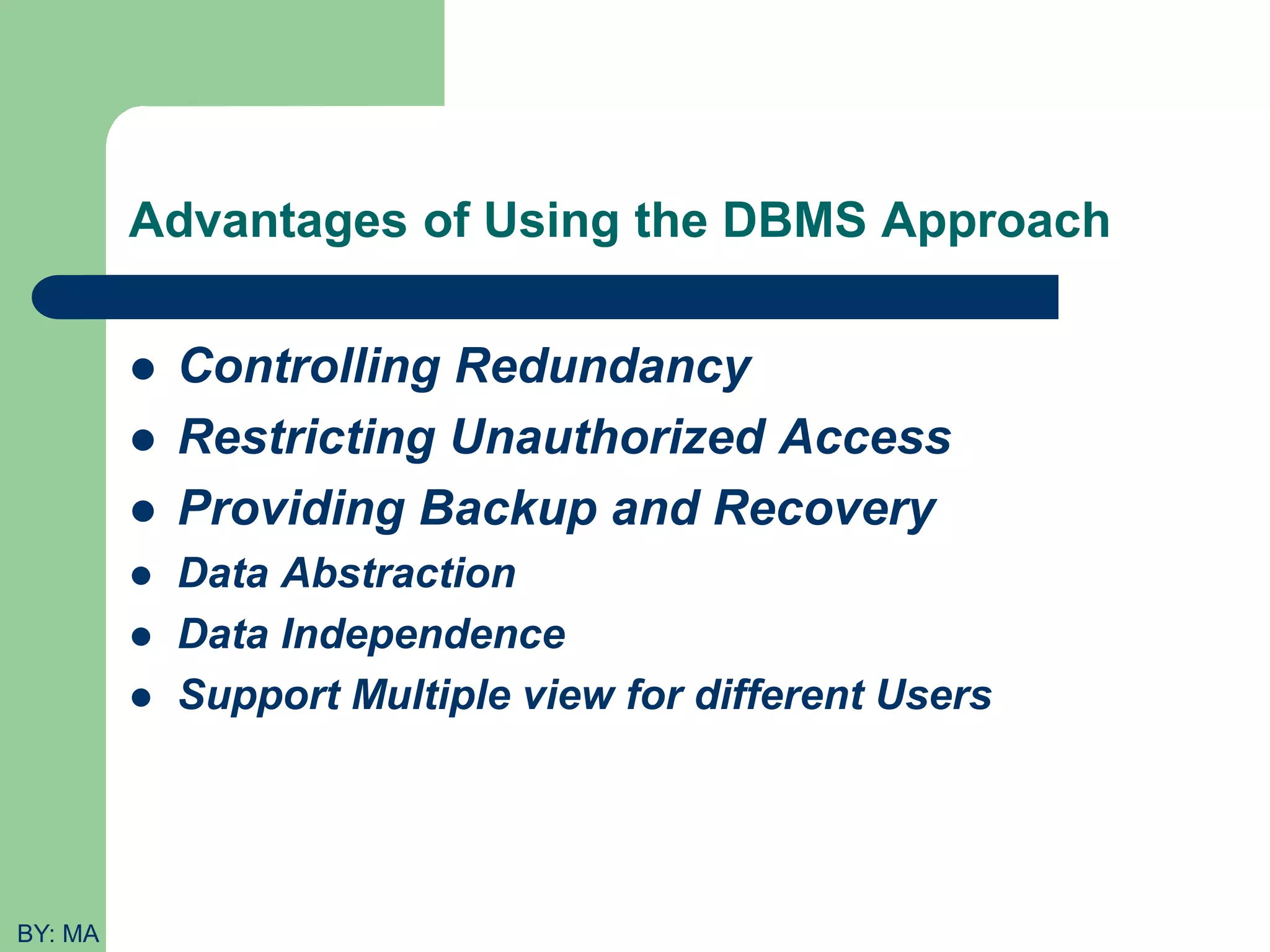
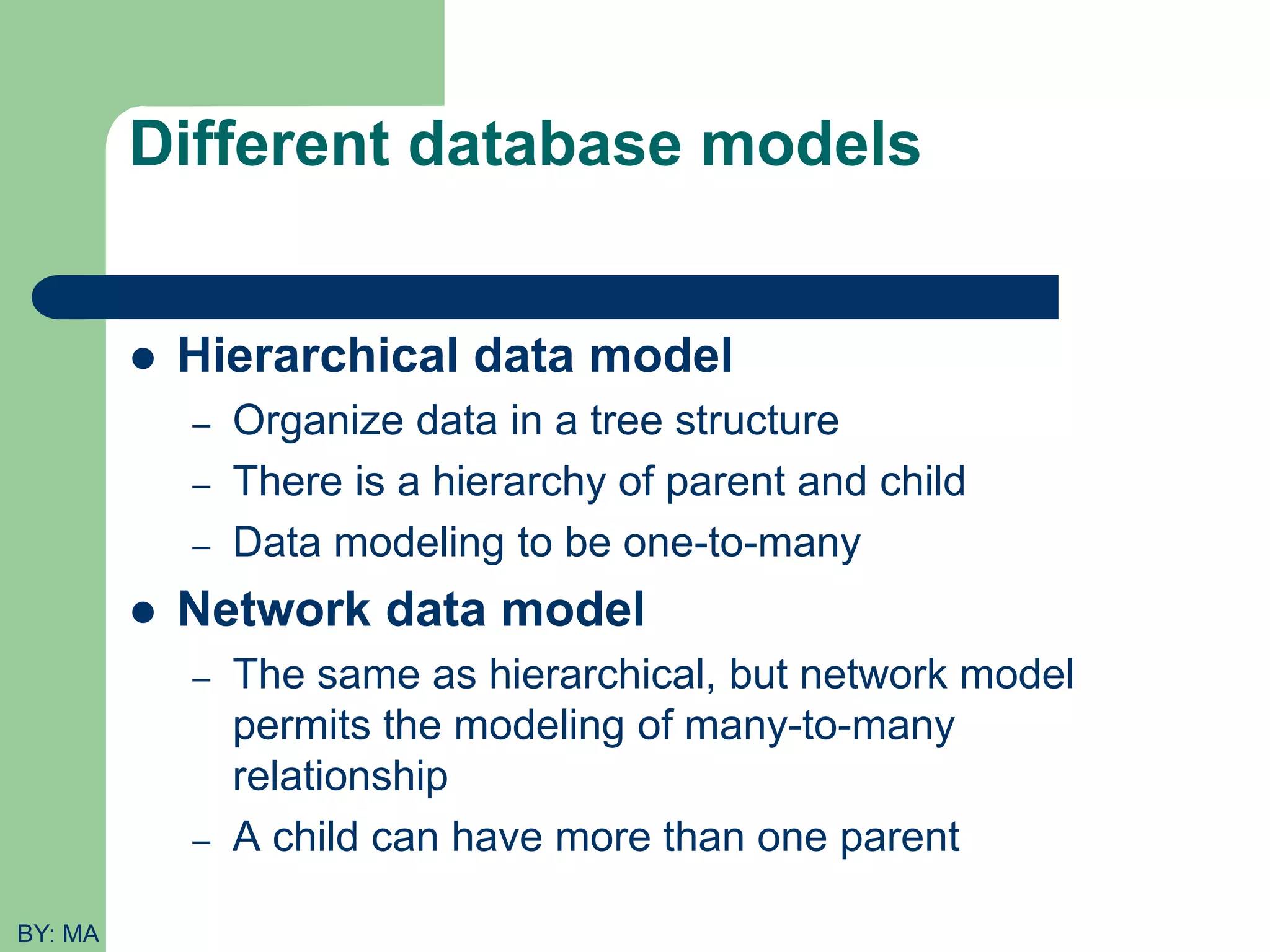
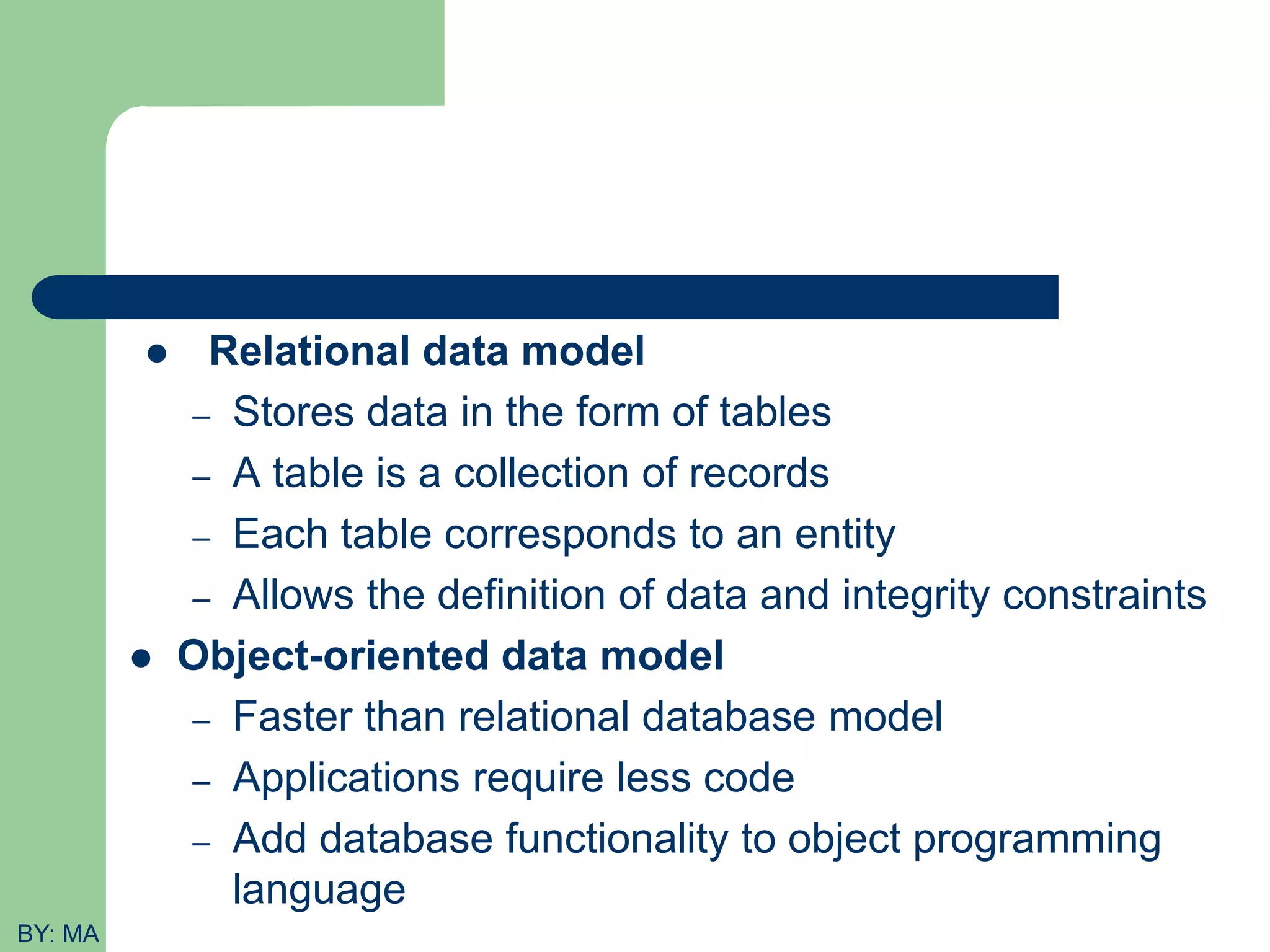
This document provides an introduction to database systems. It defines key concepts like data, databases, database management systems (DBMS), and file systems. It describes the evolution from manual data handling to file-based systems to modern database approaches. The database approach provides benefits like reducing data redundancy, improving data sharing and security. Actors involved with databases like database administrators, designers, and end users are also outlined. Basic database terminology is defined, including entities, attributes, records, files and different database models.