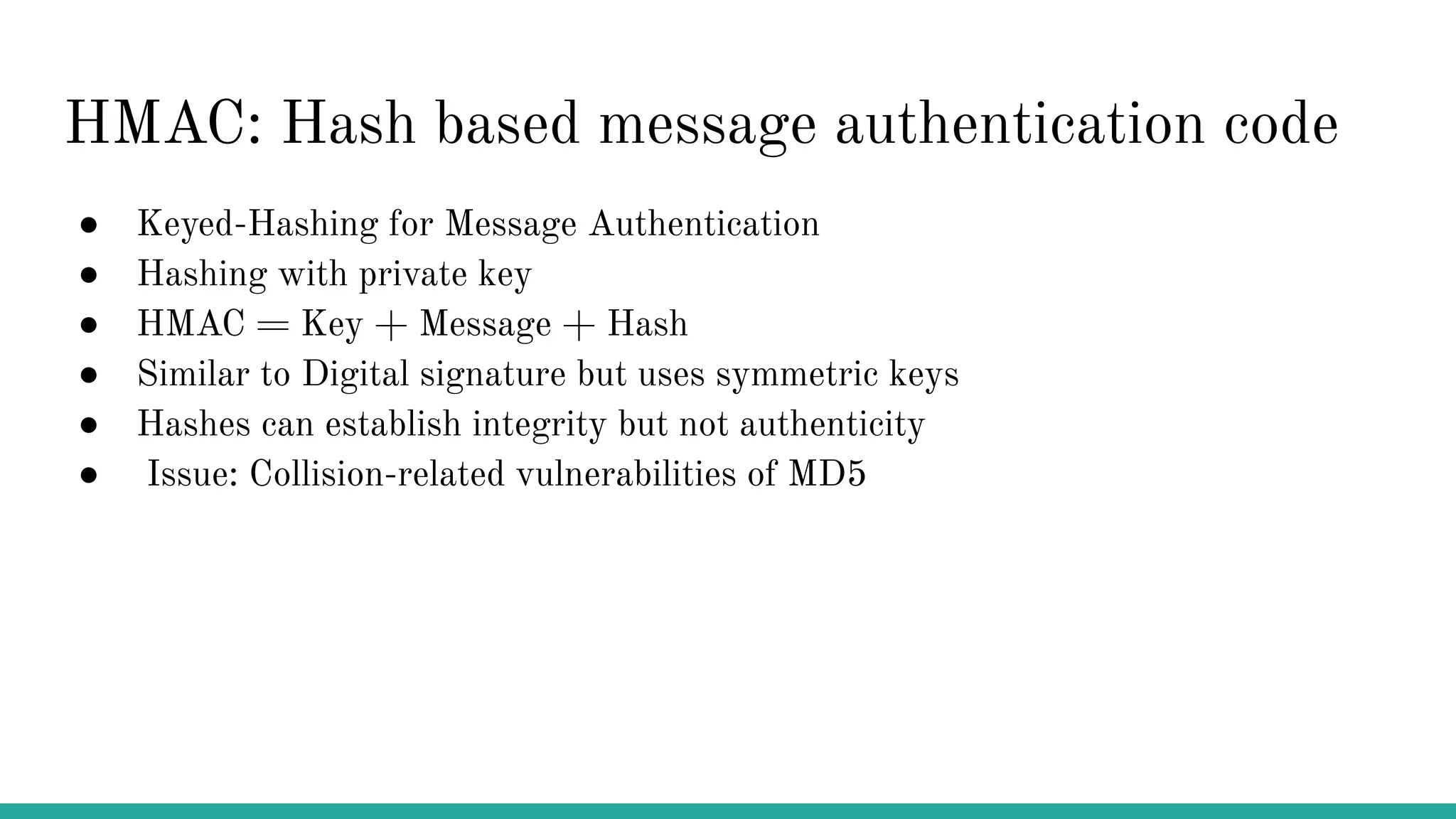
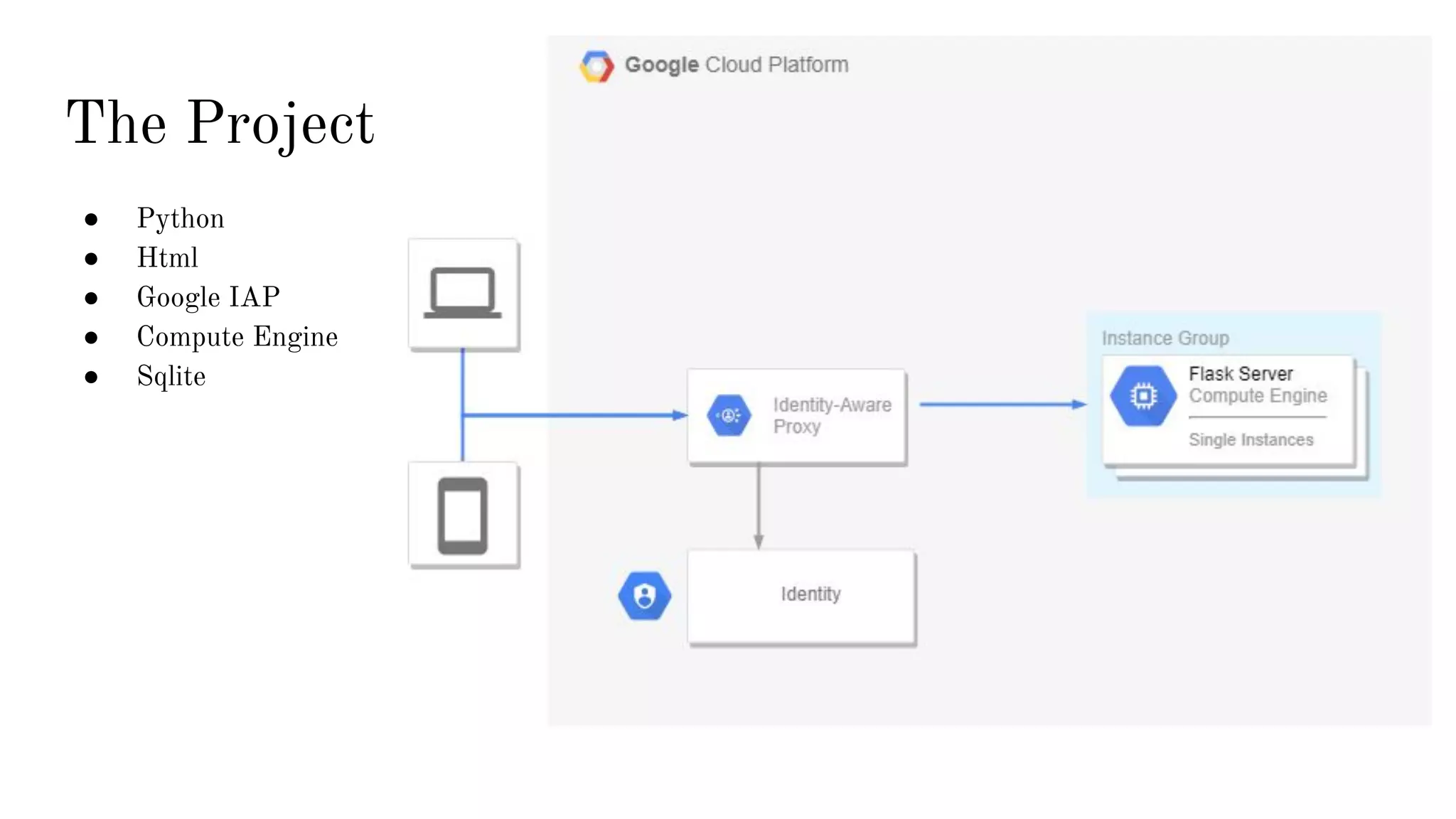
This document discusses building your own web-based time-based one-time password (TOTP) authenticator using Python, HTML, Google Identity-Aware Proxy (IAP), Compute Engine, and SQLite. It provides background on multi-factor authentication (MFA) and the cryptographic techniques HMAC and TOTP. The project aims to create an easy way to generate one's own TOTP codes as an alternative to proprietary authenticator apps, while future work could involve using HMAC to generate random URLs.