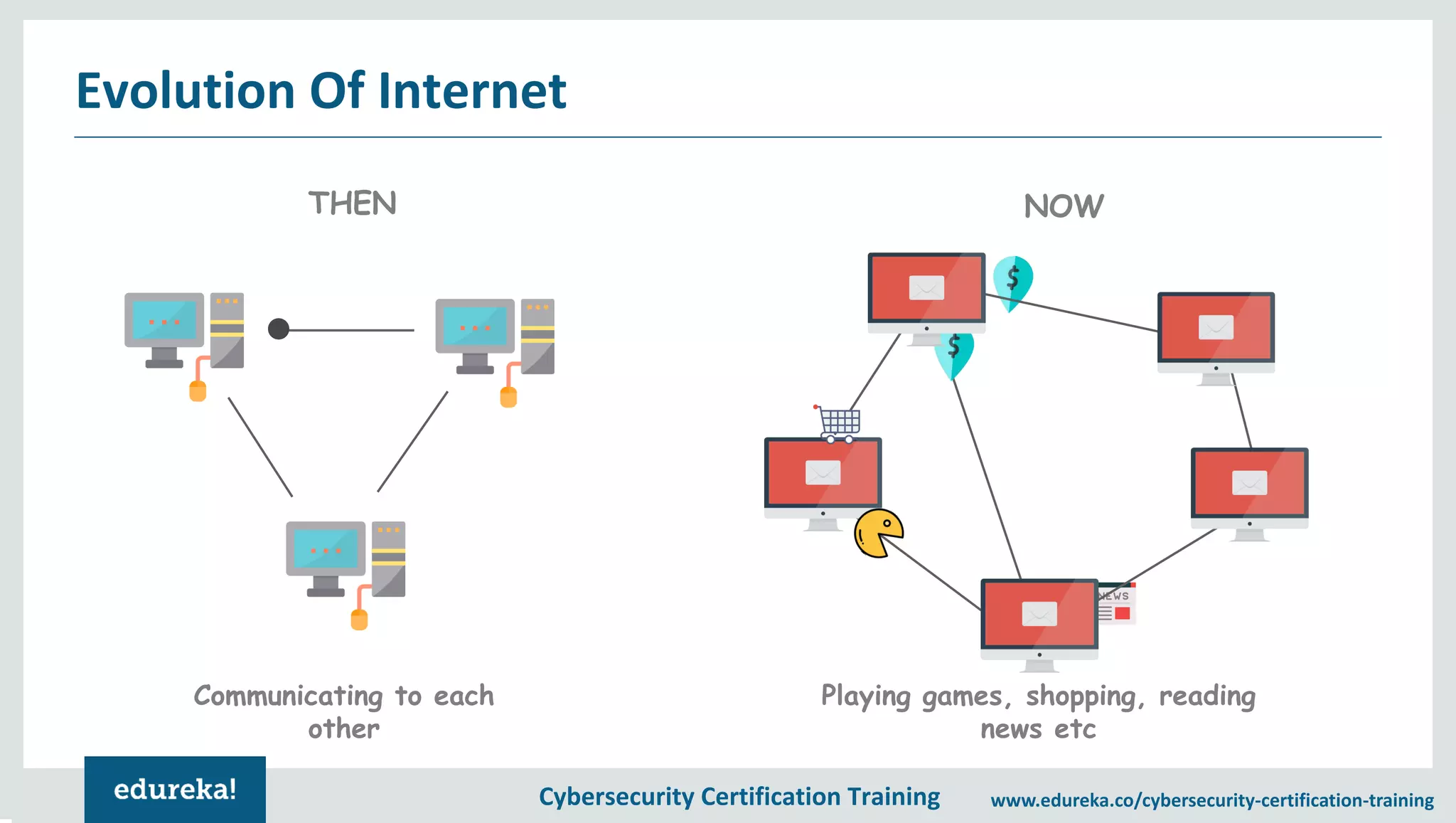
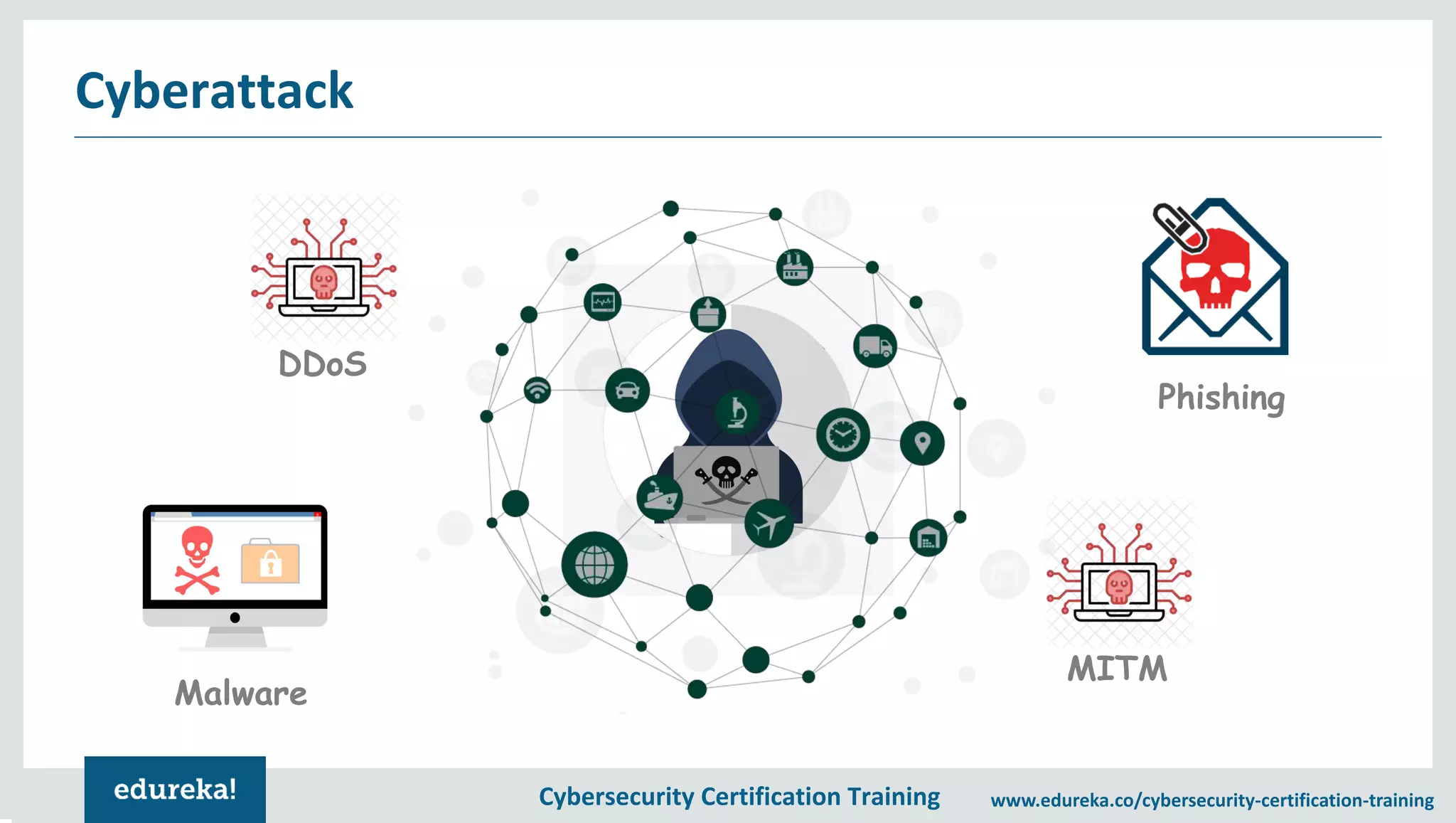
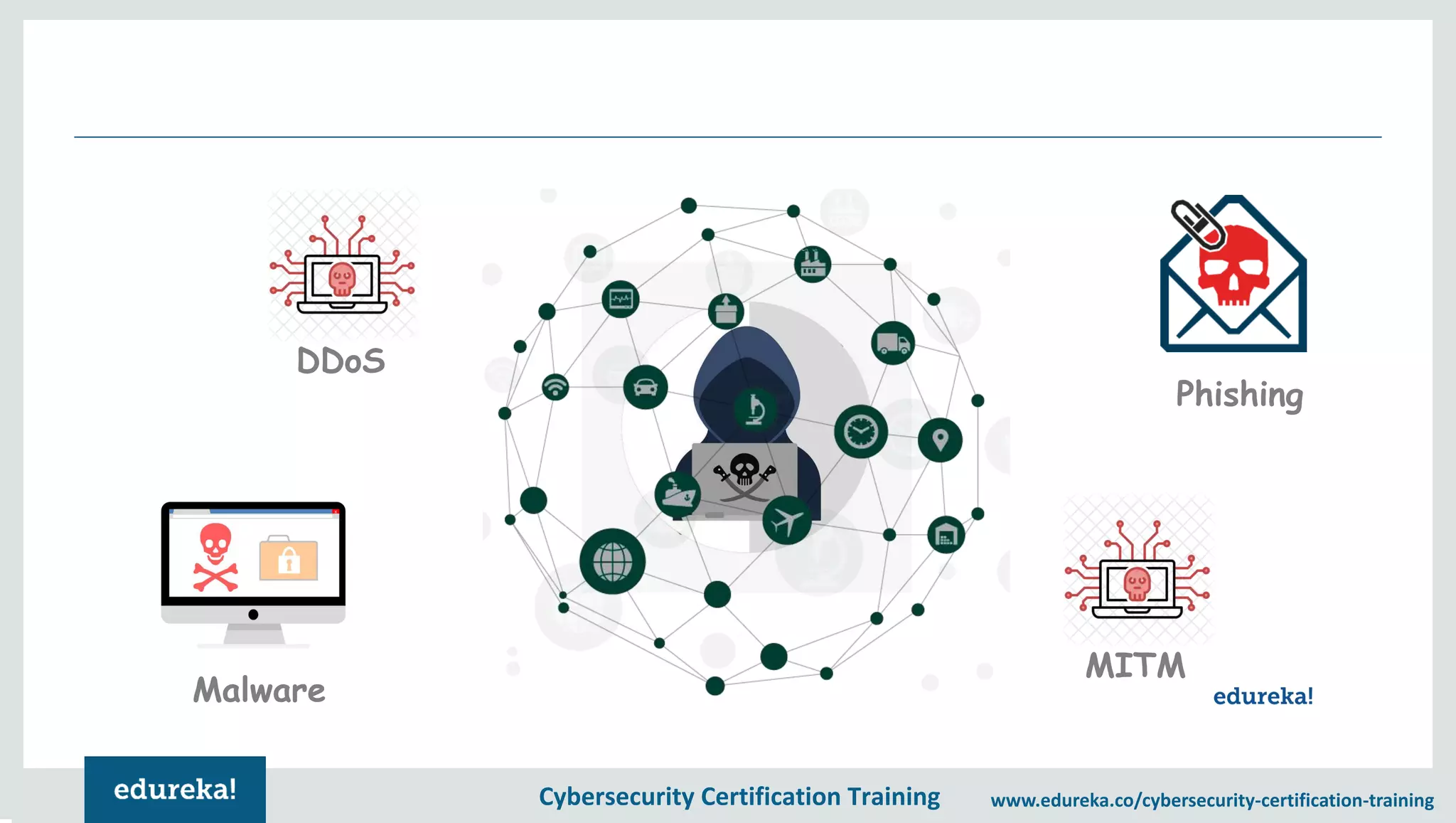
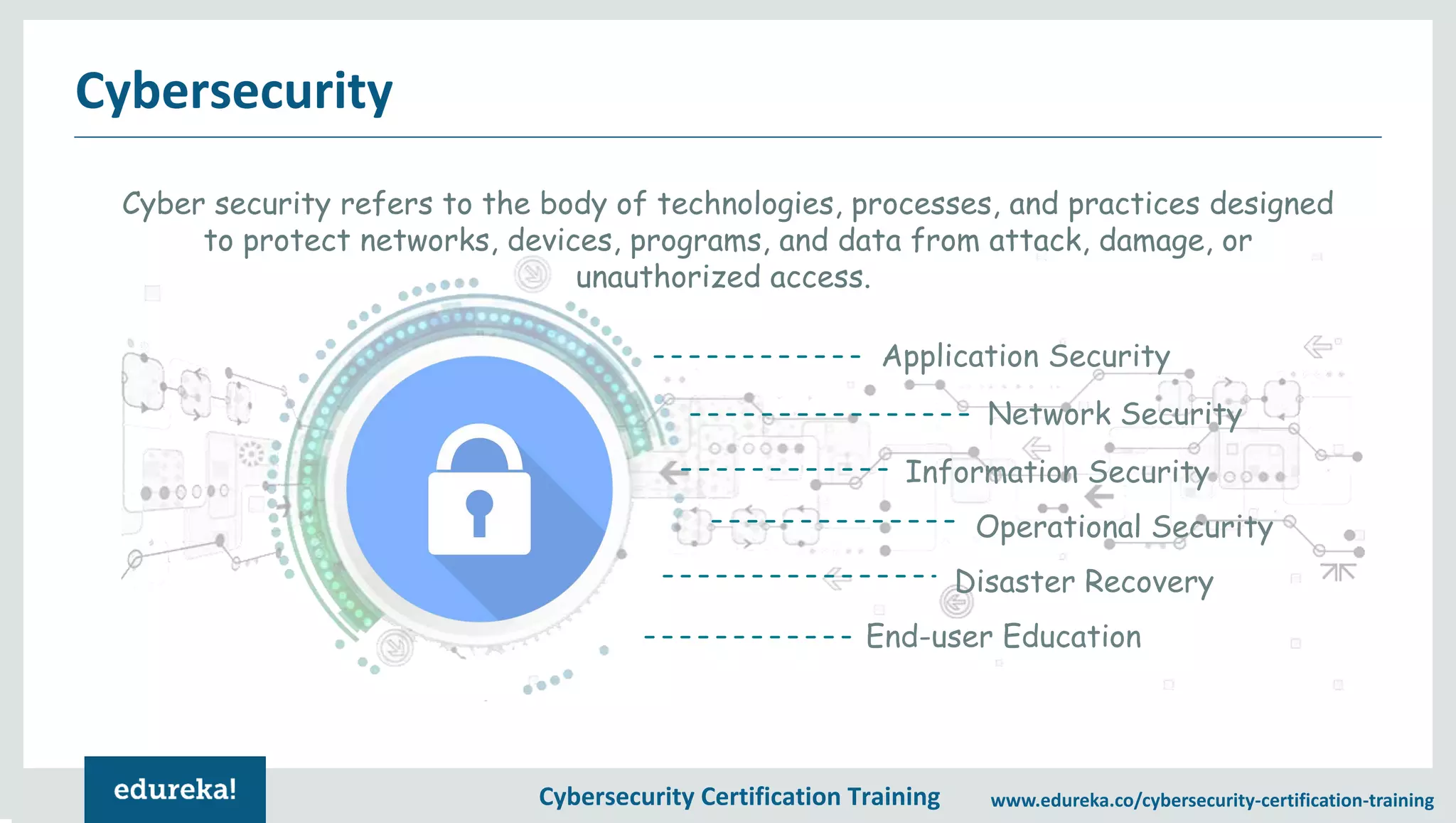
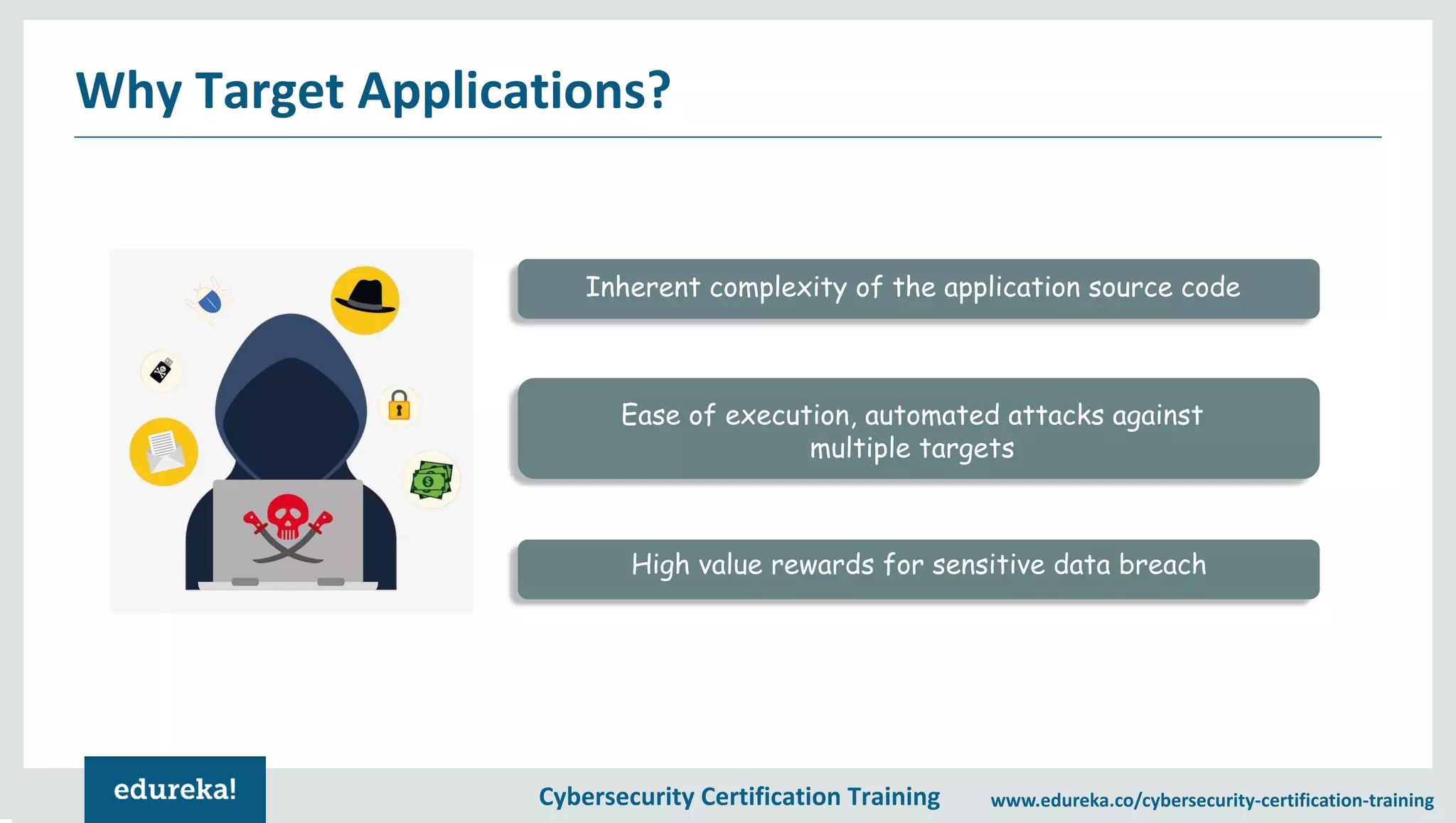
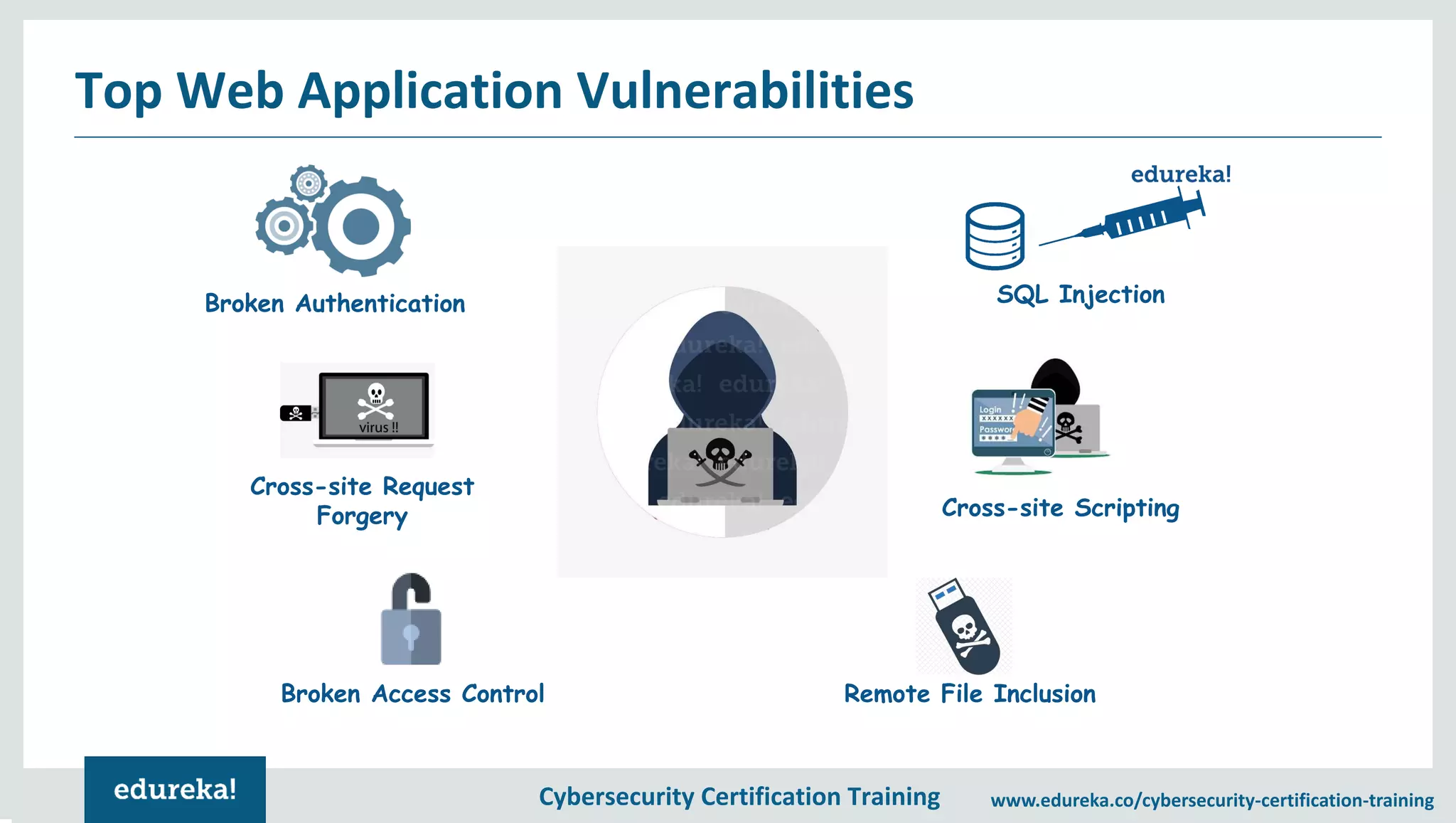
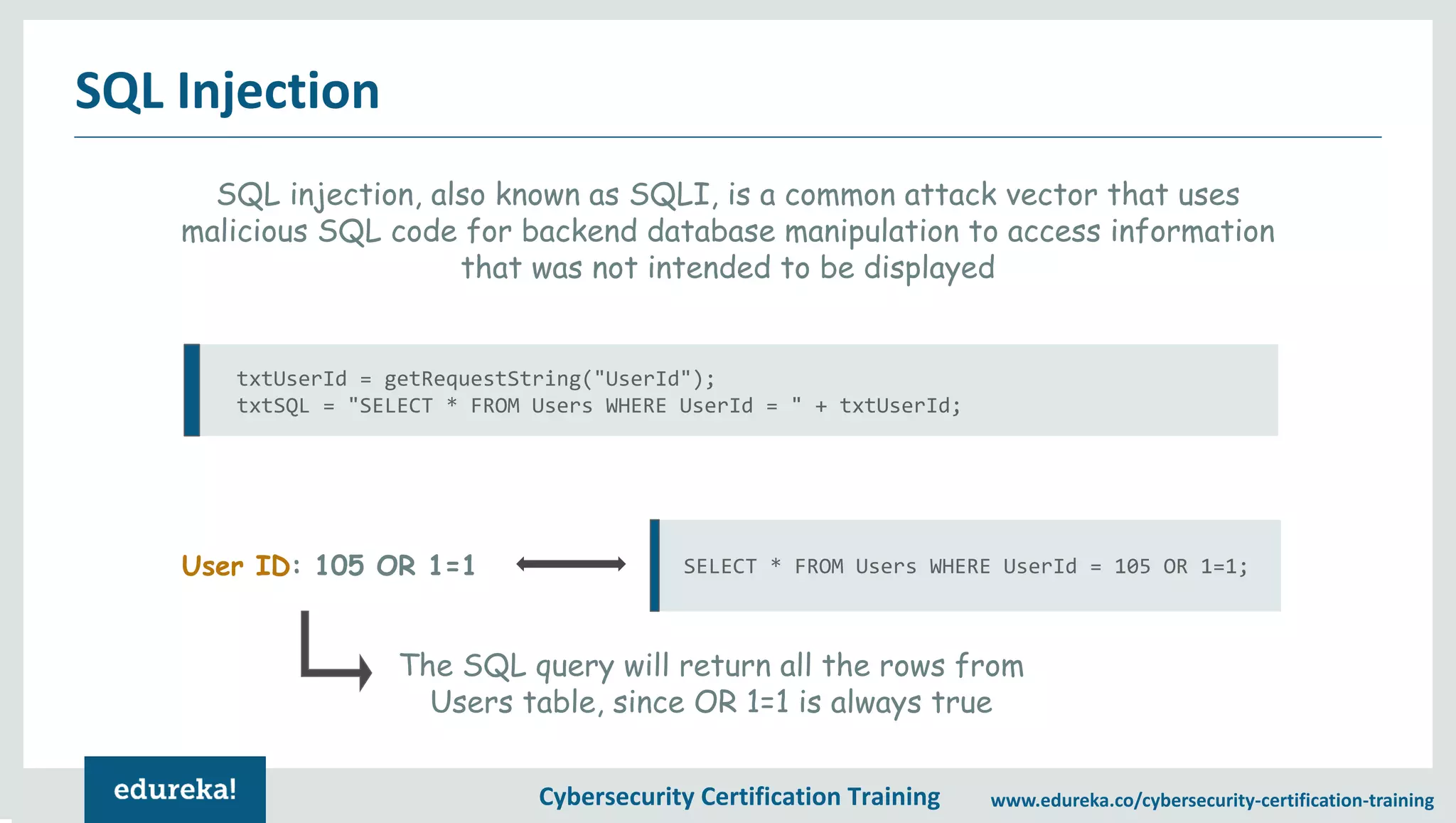
The document provides an overview of a cybersecurity certification training course, covering topics such as application security, SQL injection attacks, and the importance of protecting networks and data from various cyber threats. It outlines key vulnerabilities in web applications and emphasizes the need for practices like end-user education and disaster recovery. The course aims to equip individuals with knowledge on securing applications against external threats and common attack vectors.