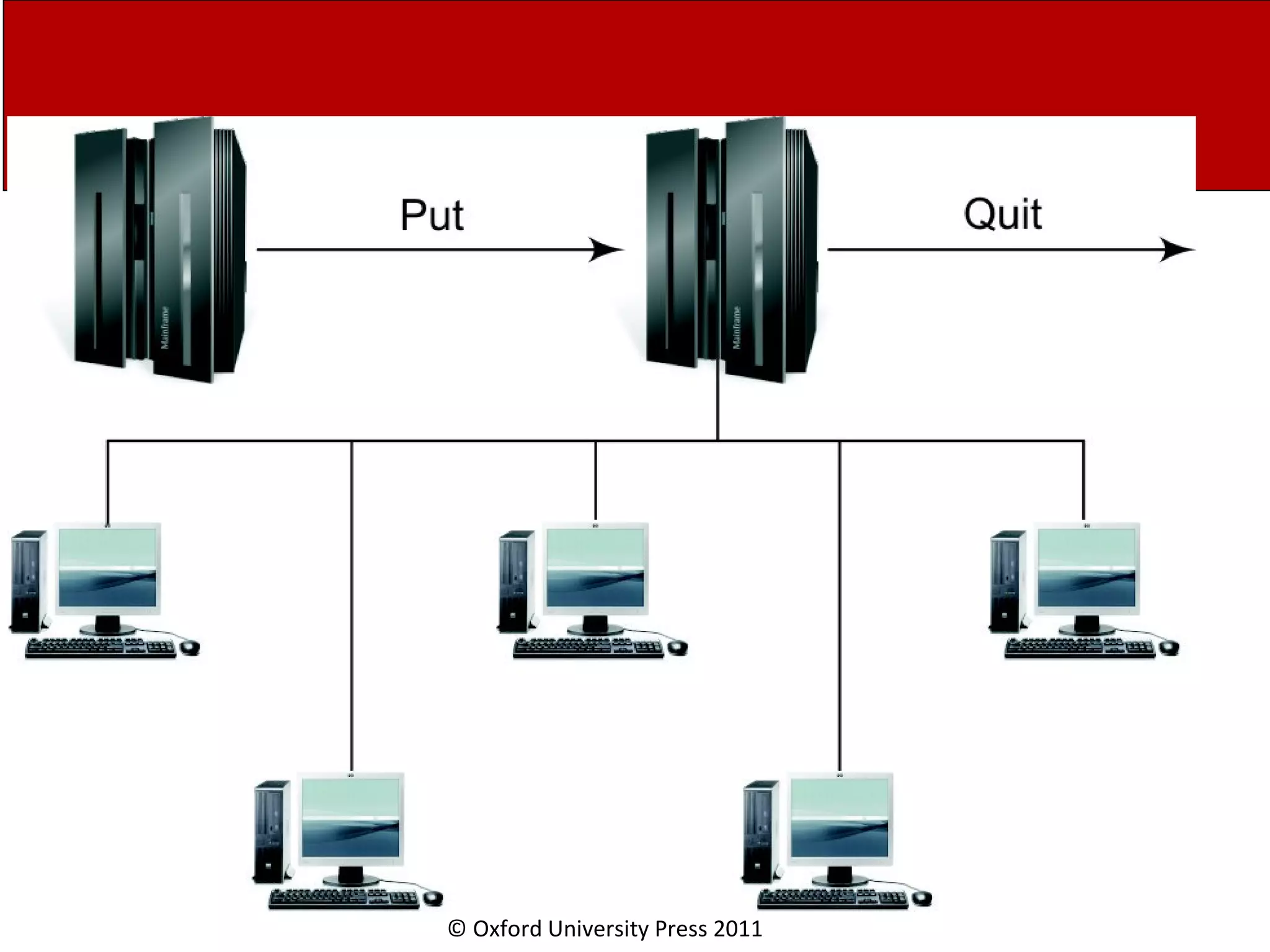
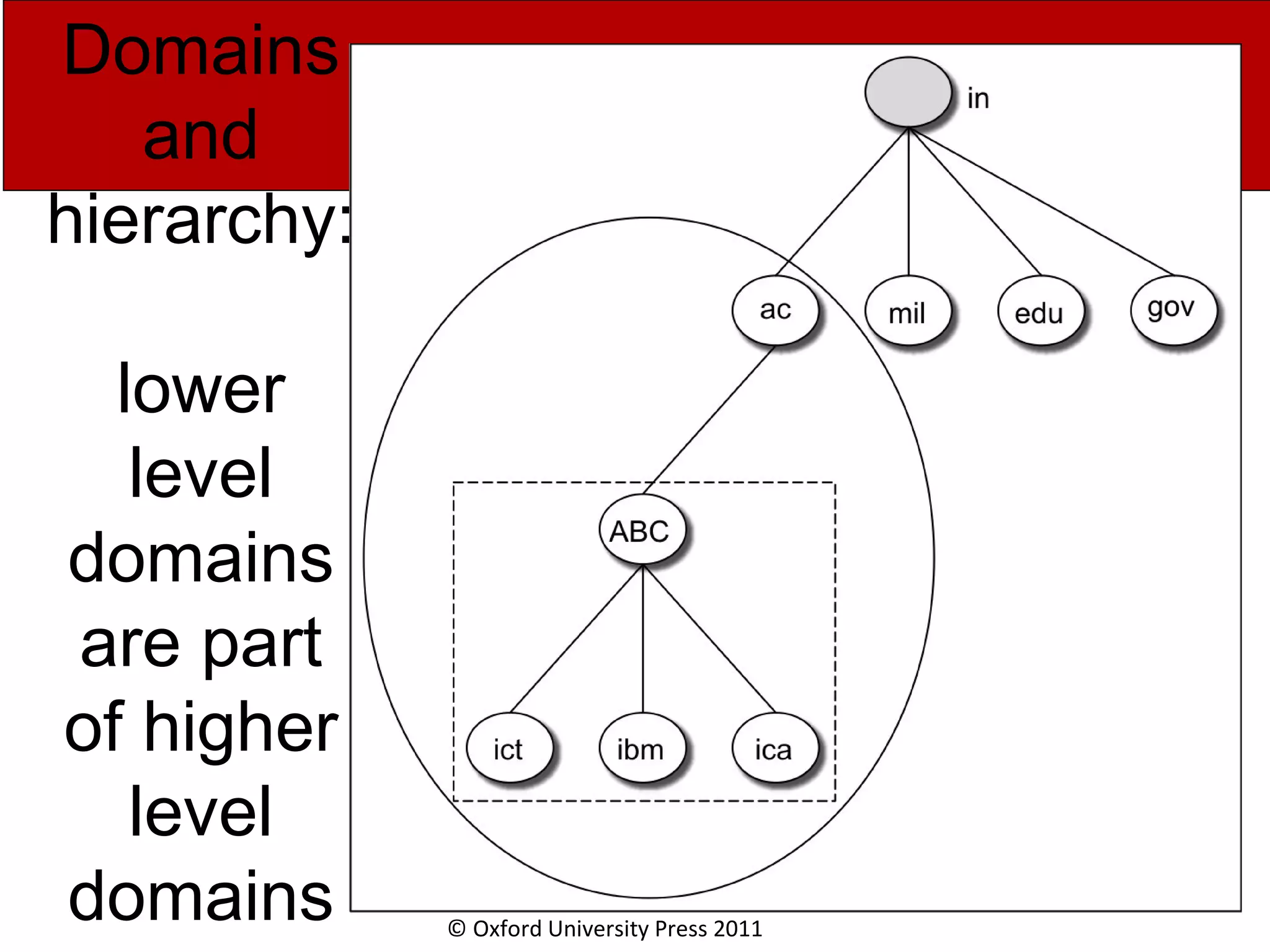
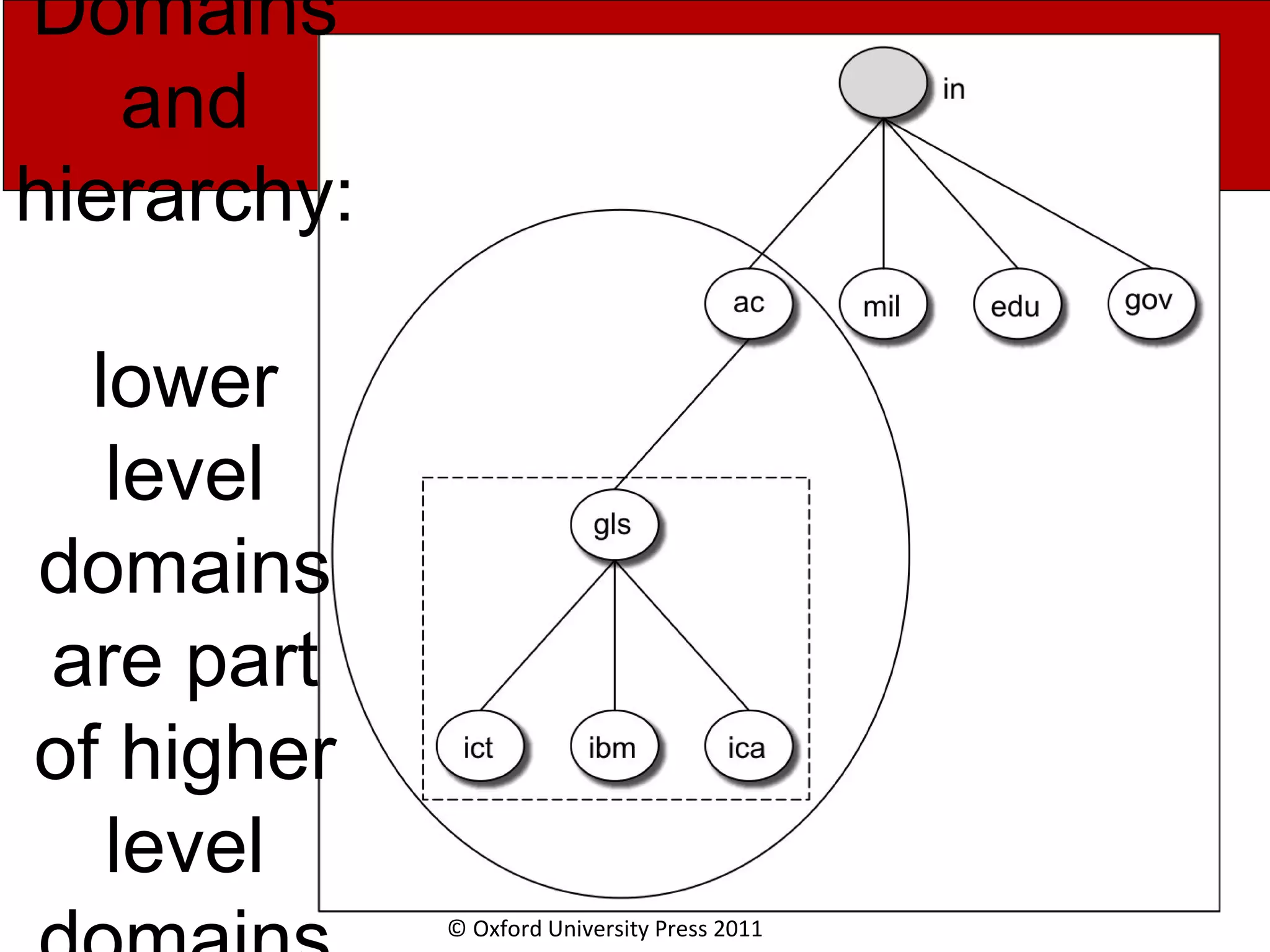
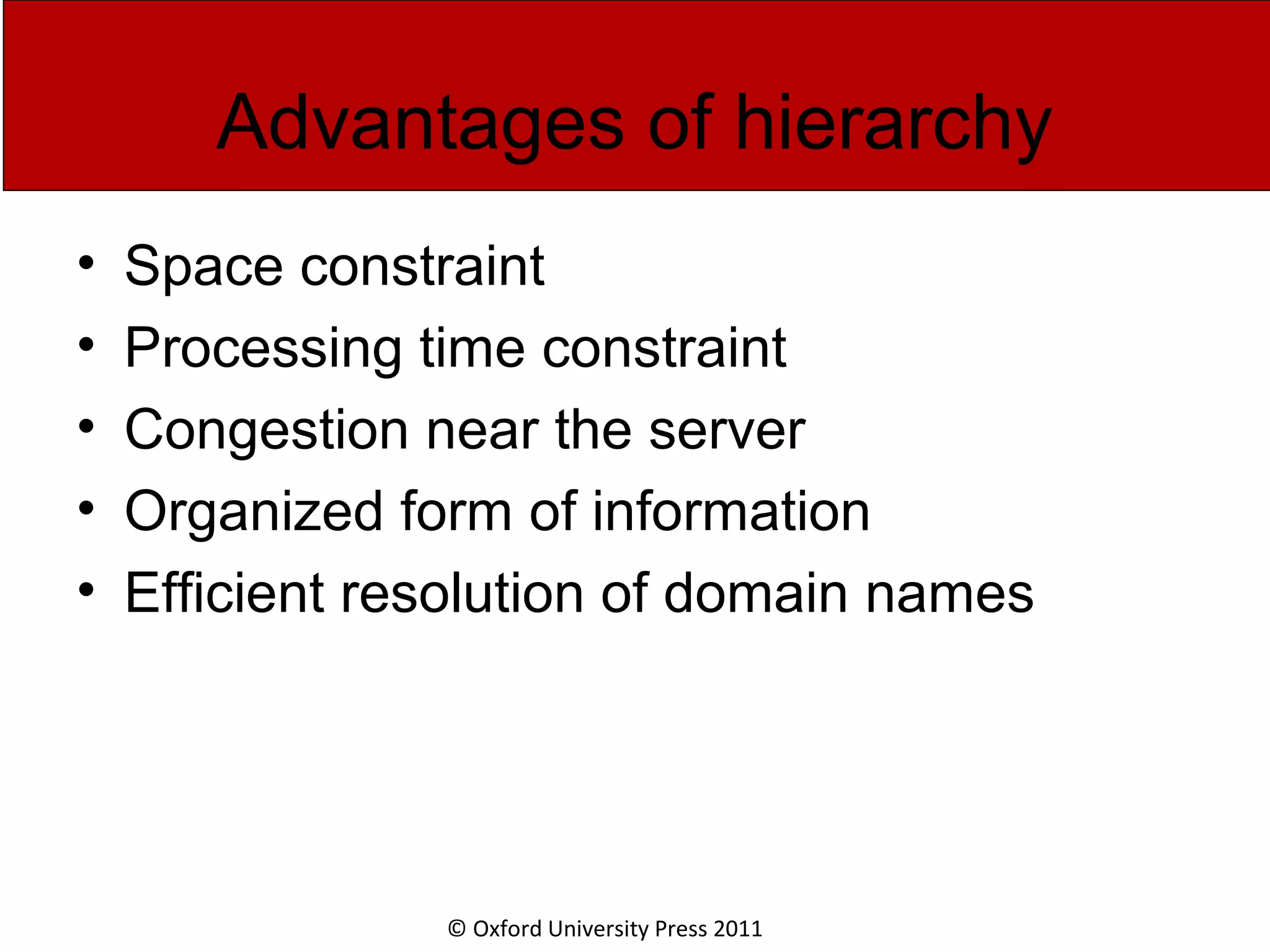
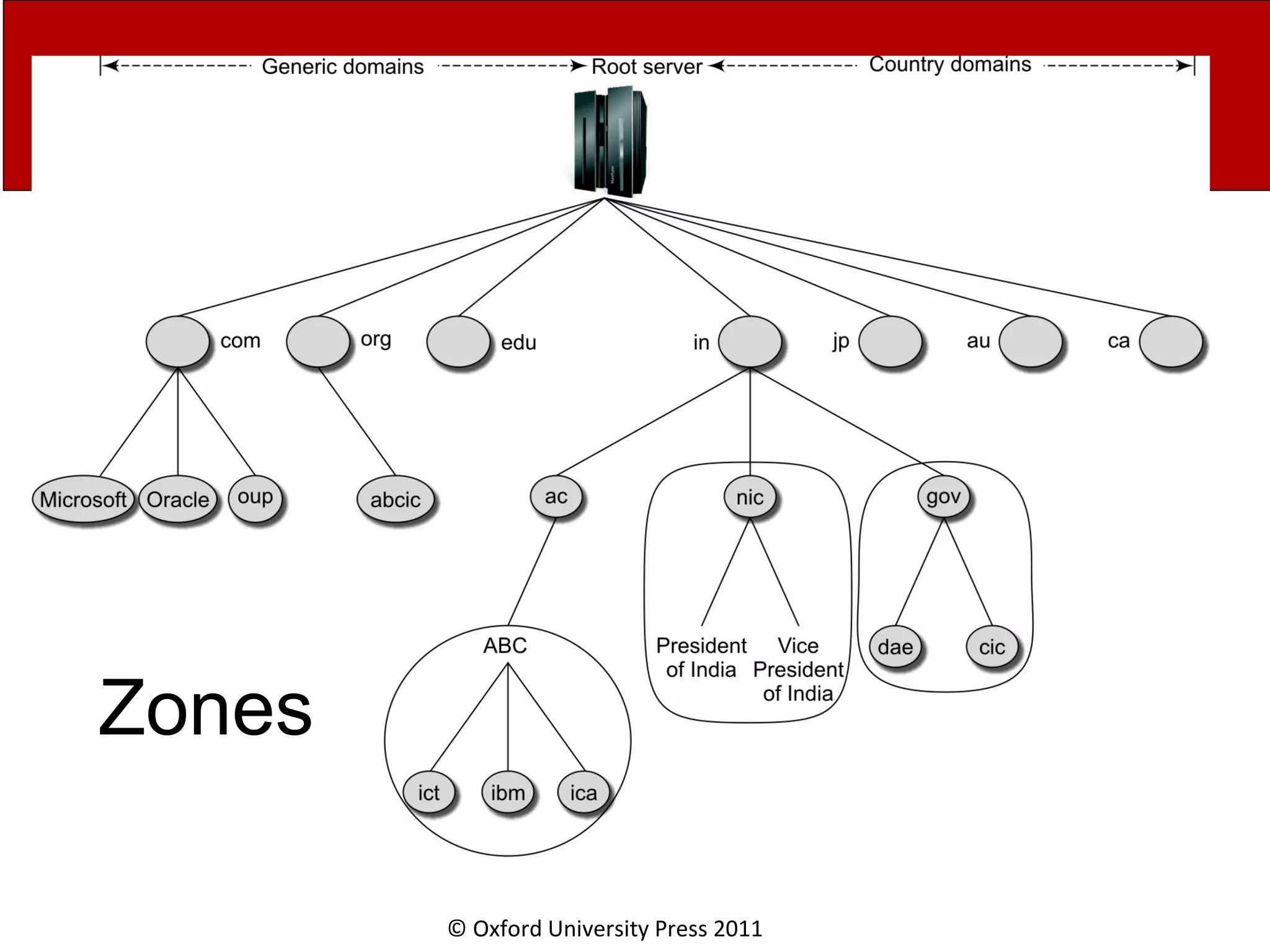
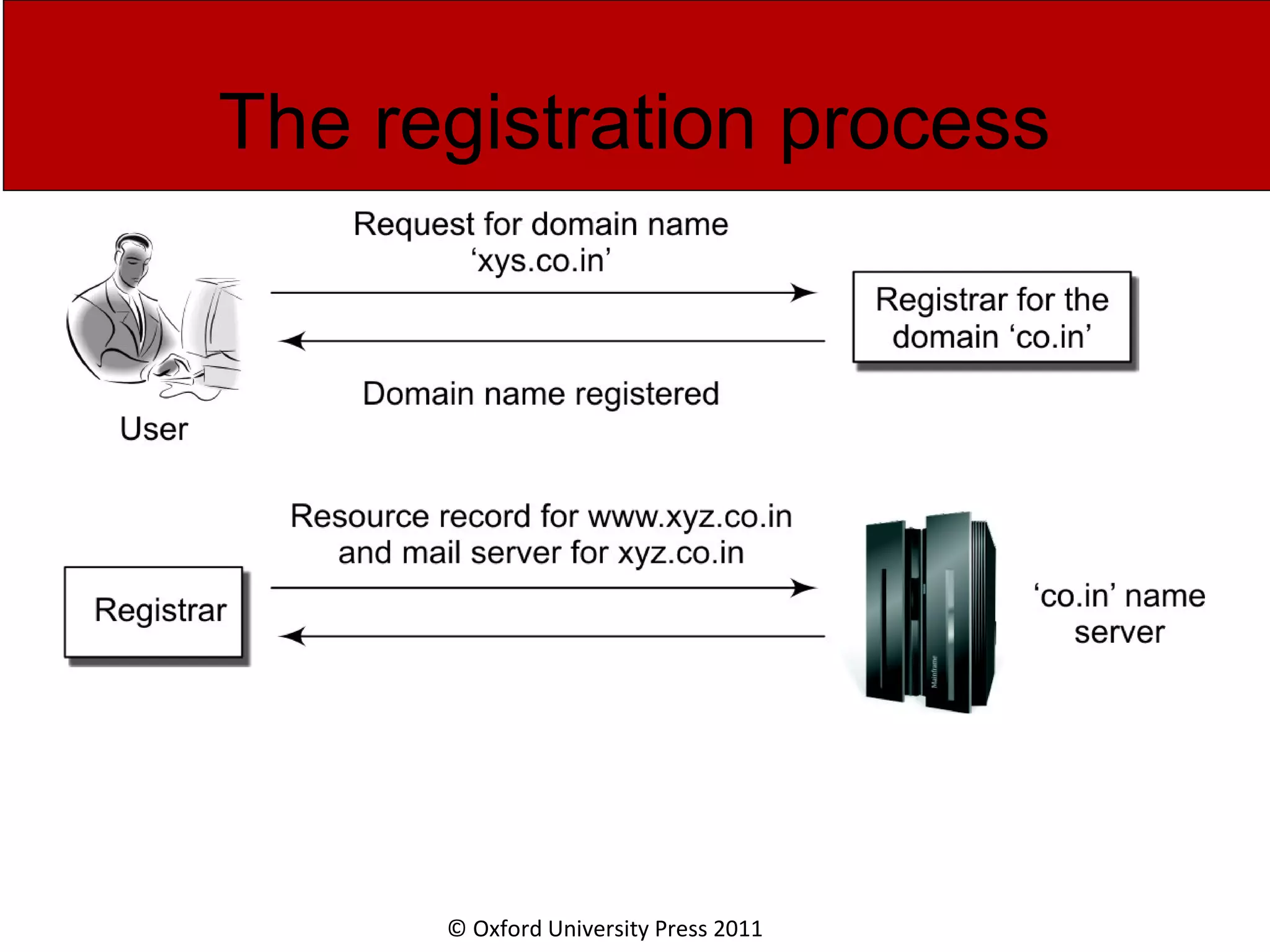
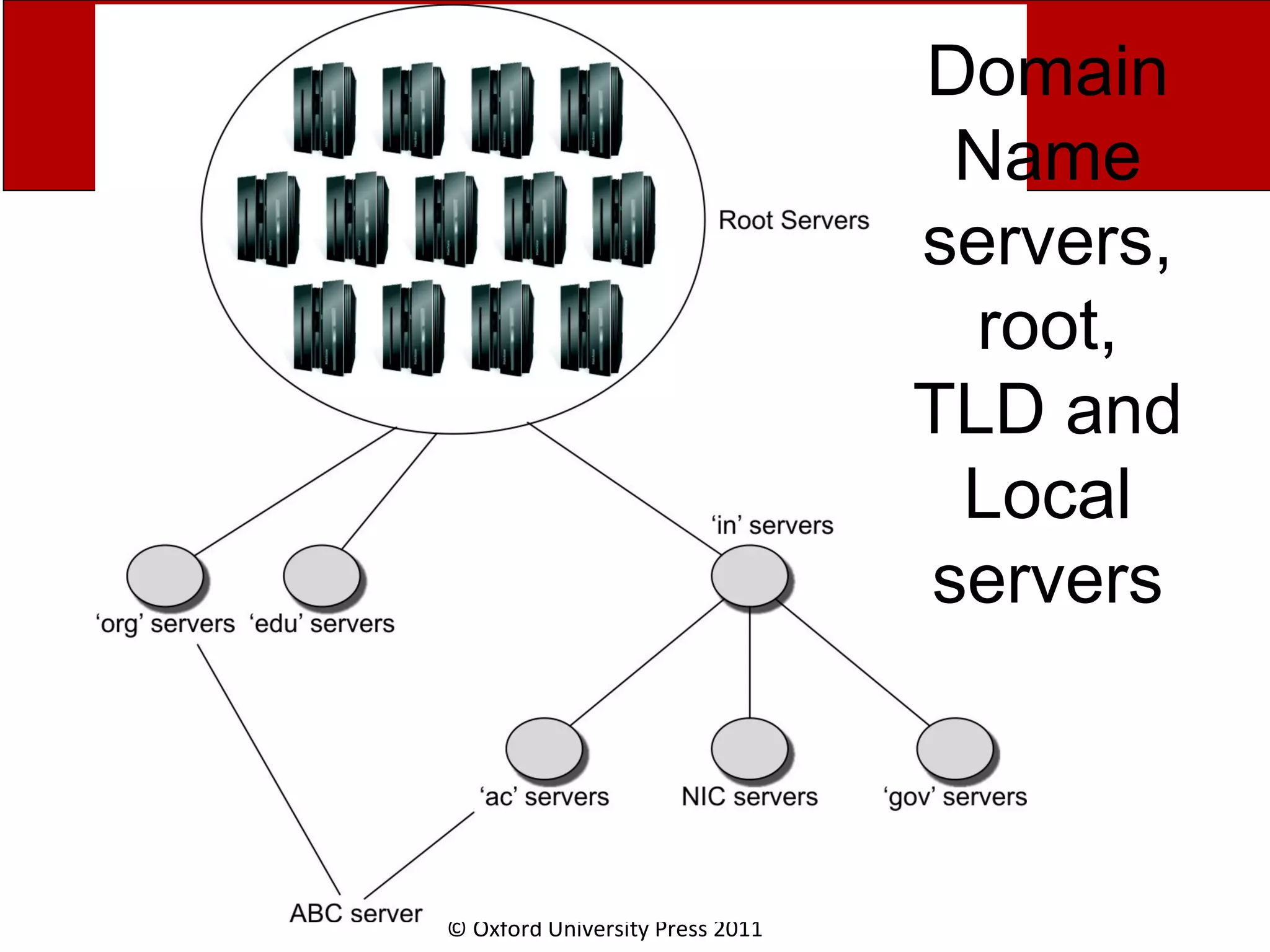
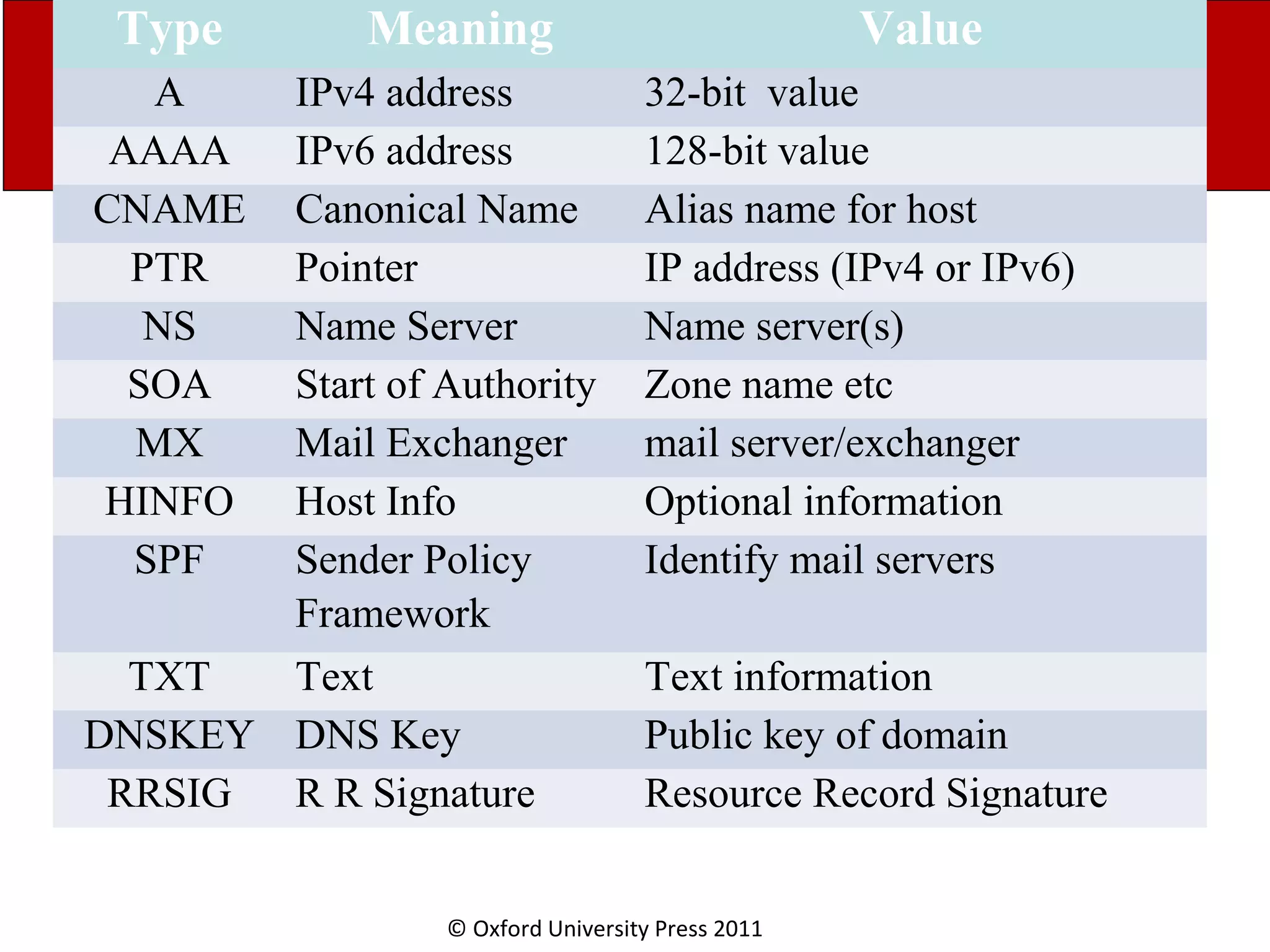
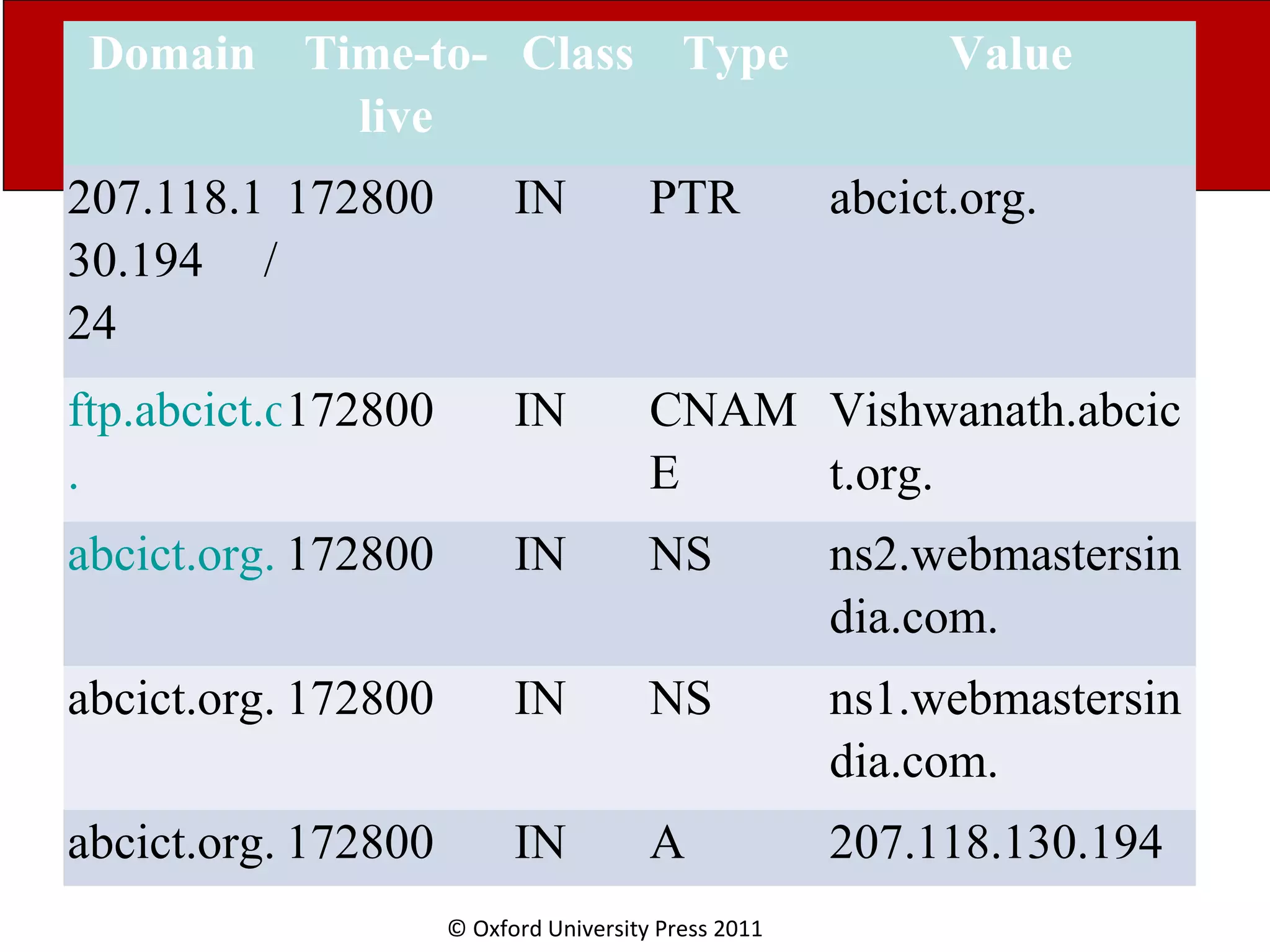
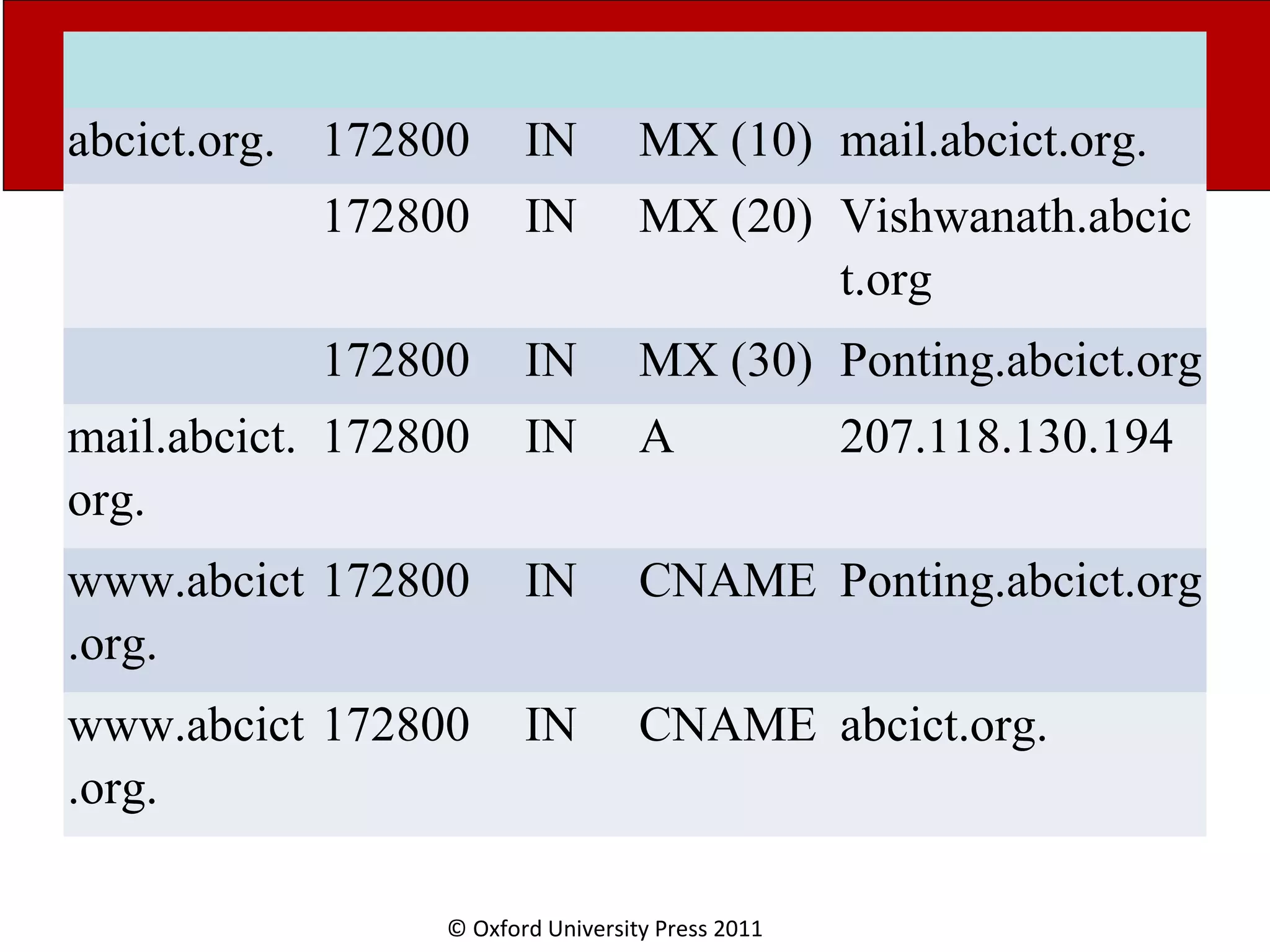
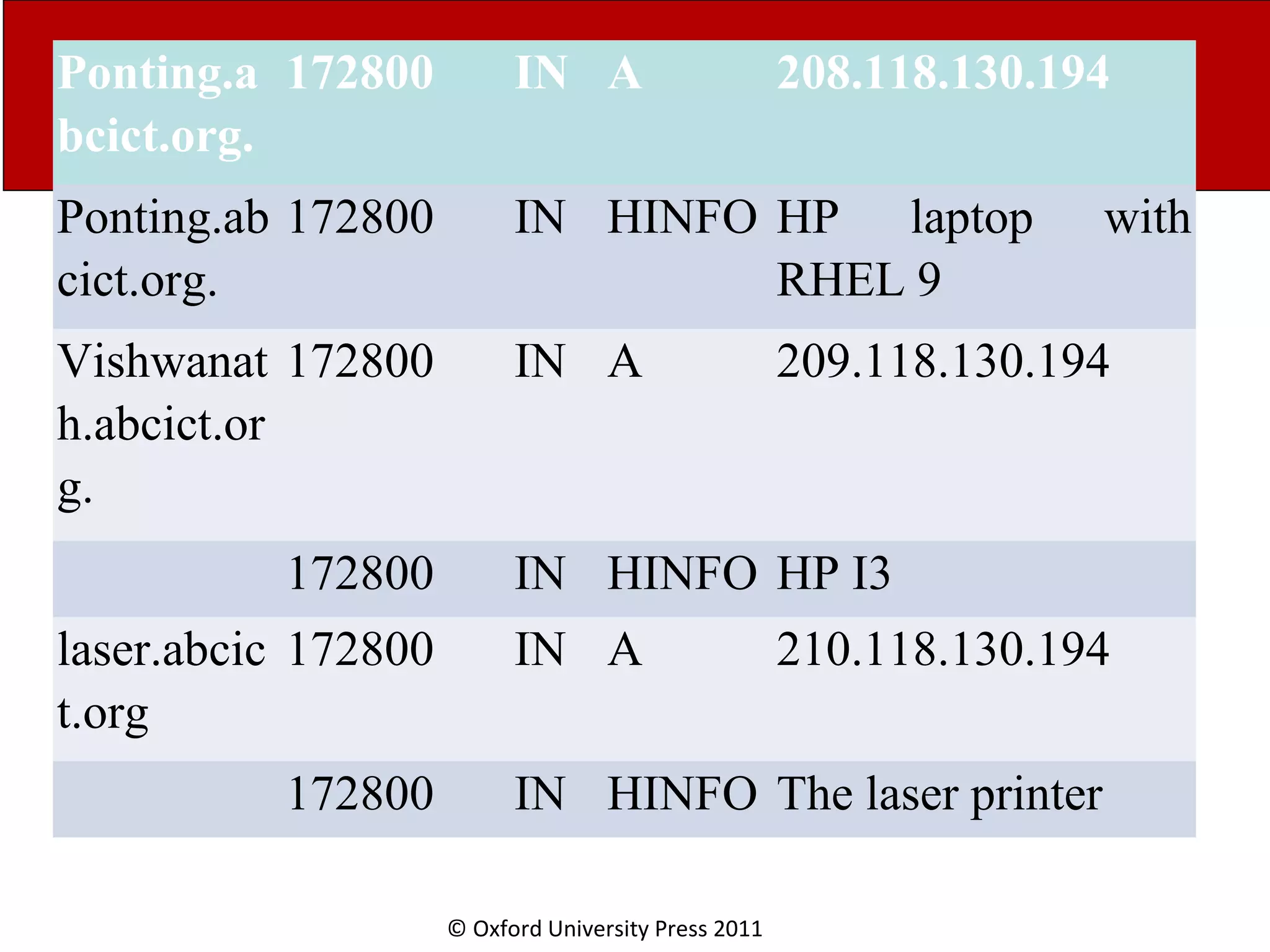
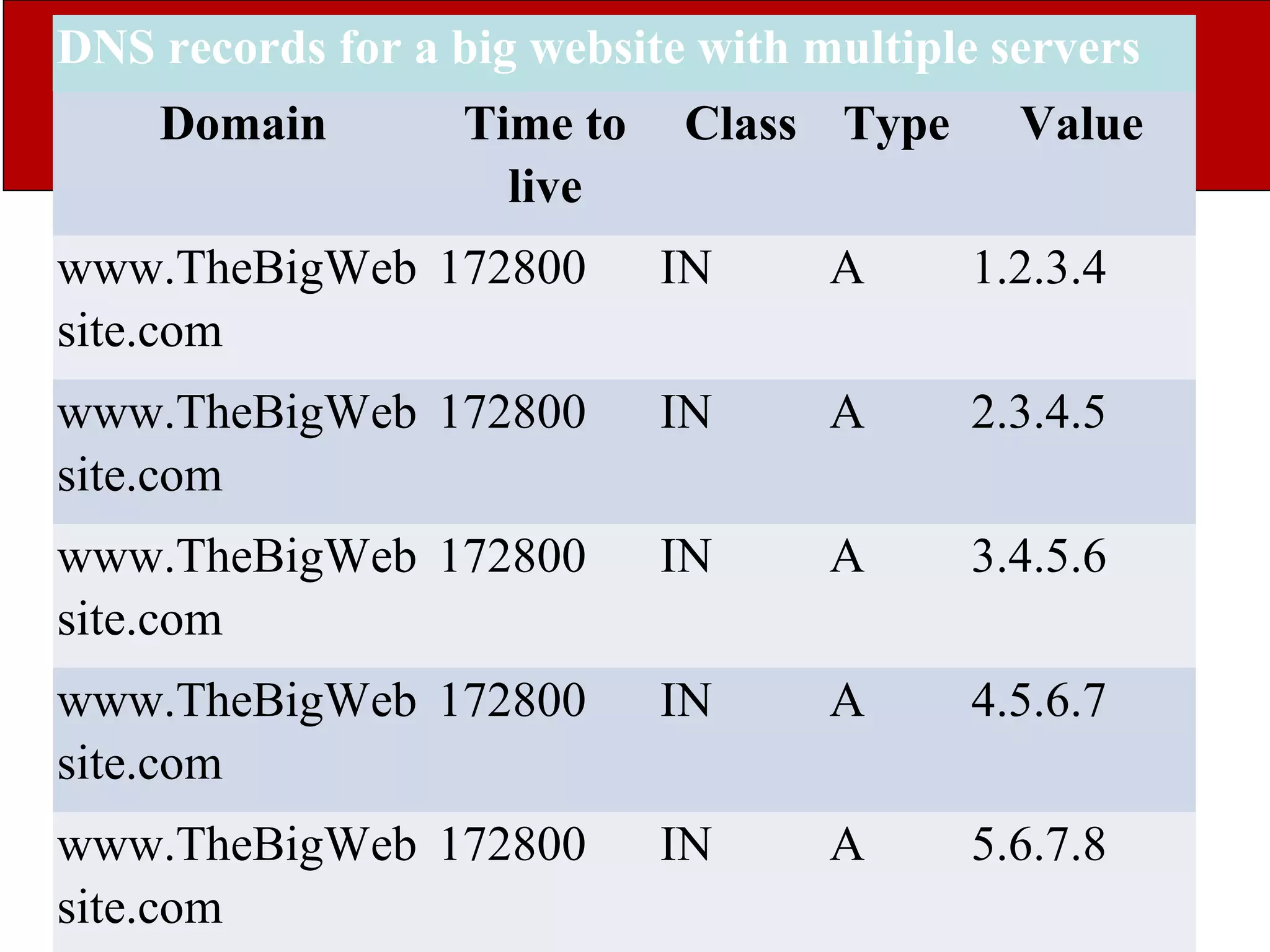
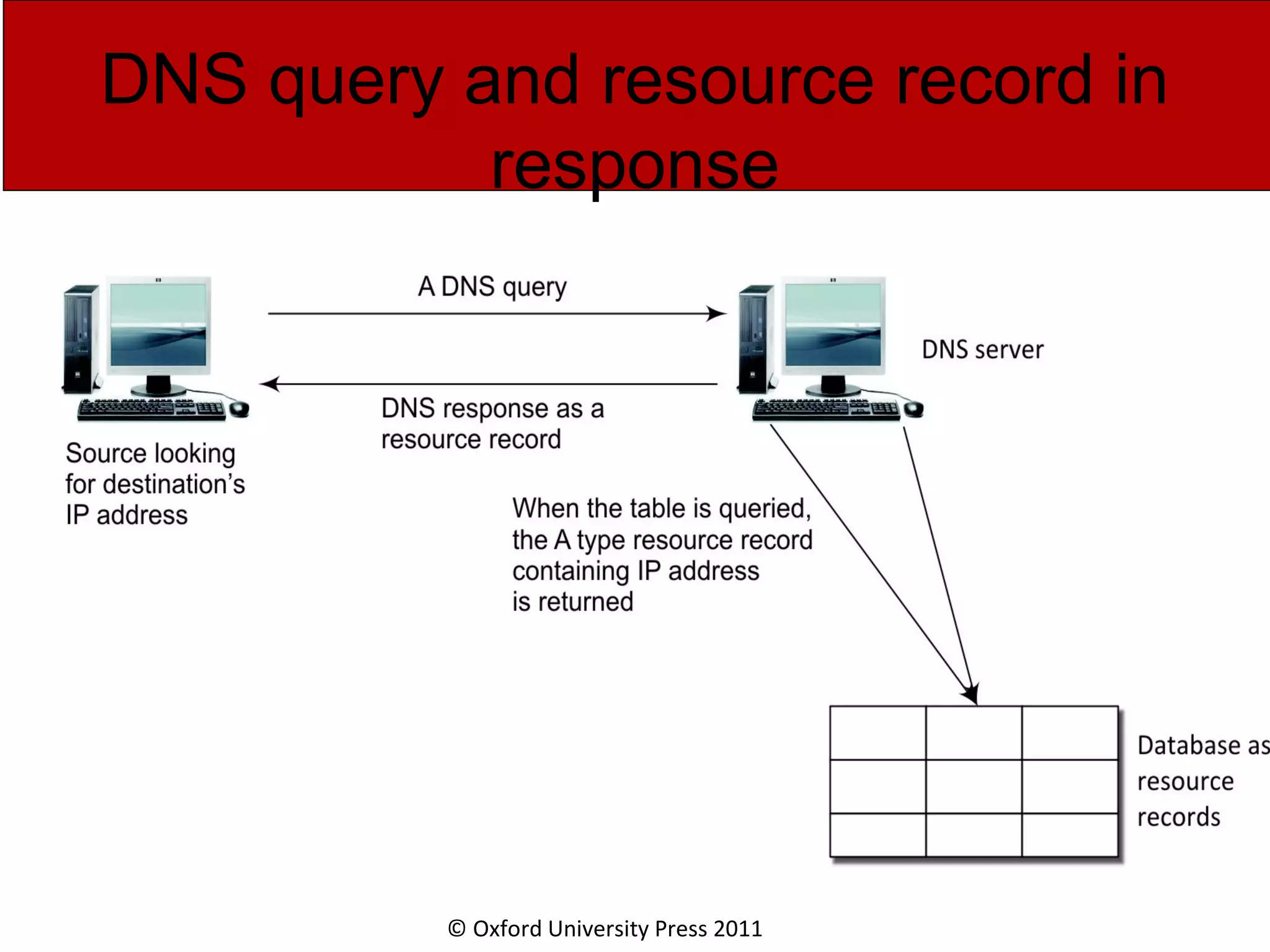
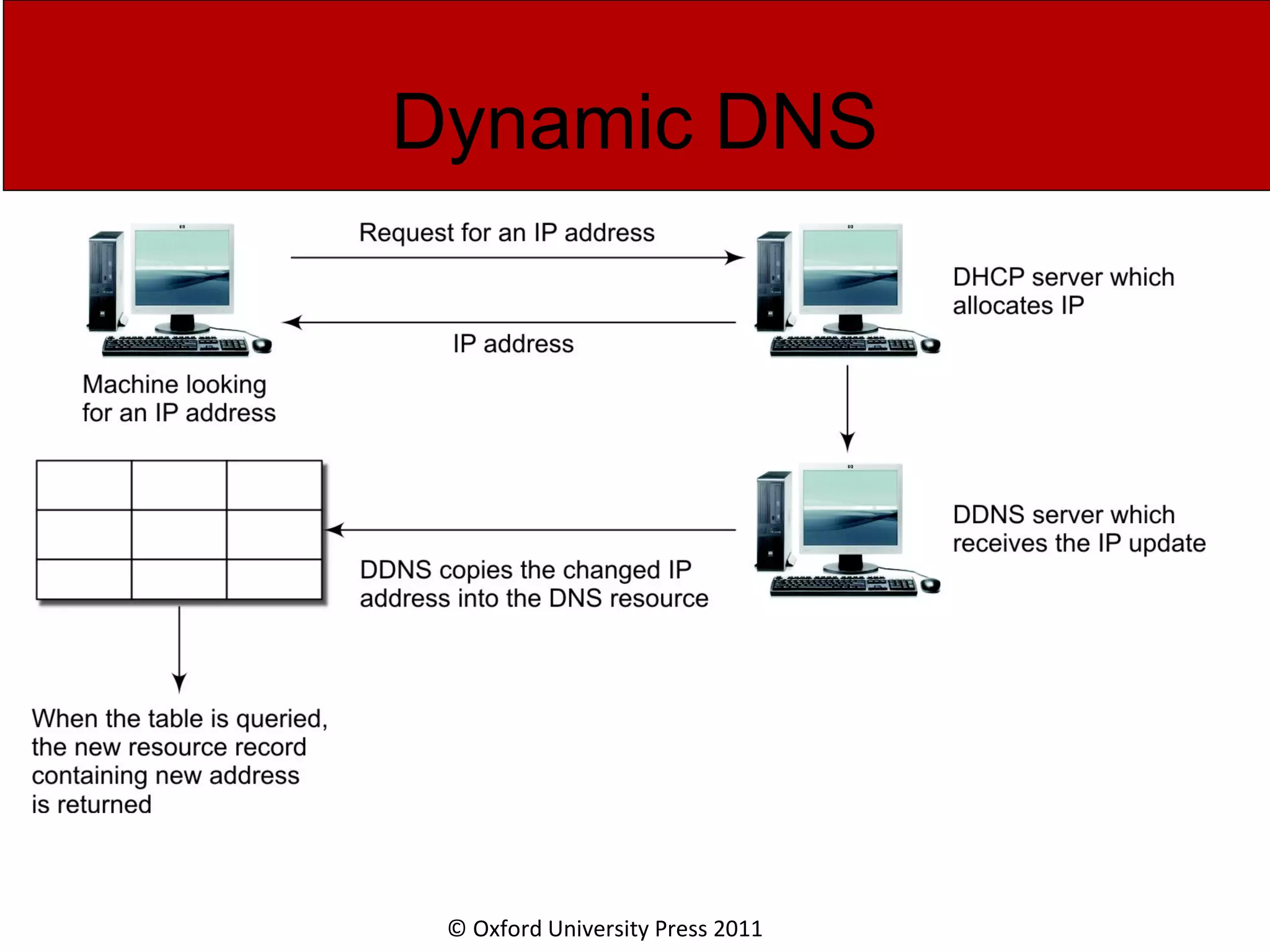
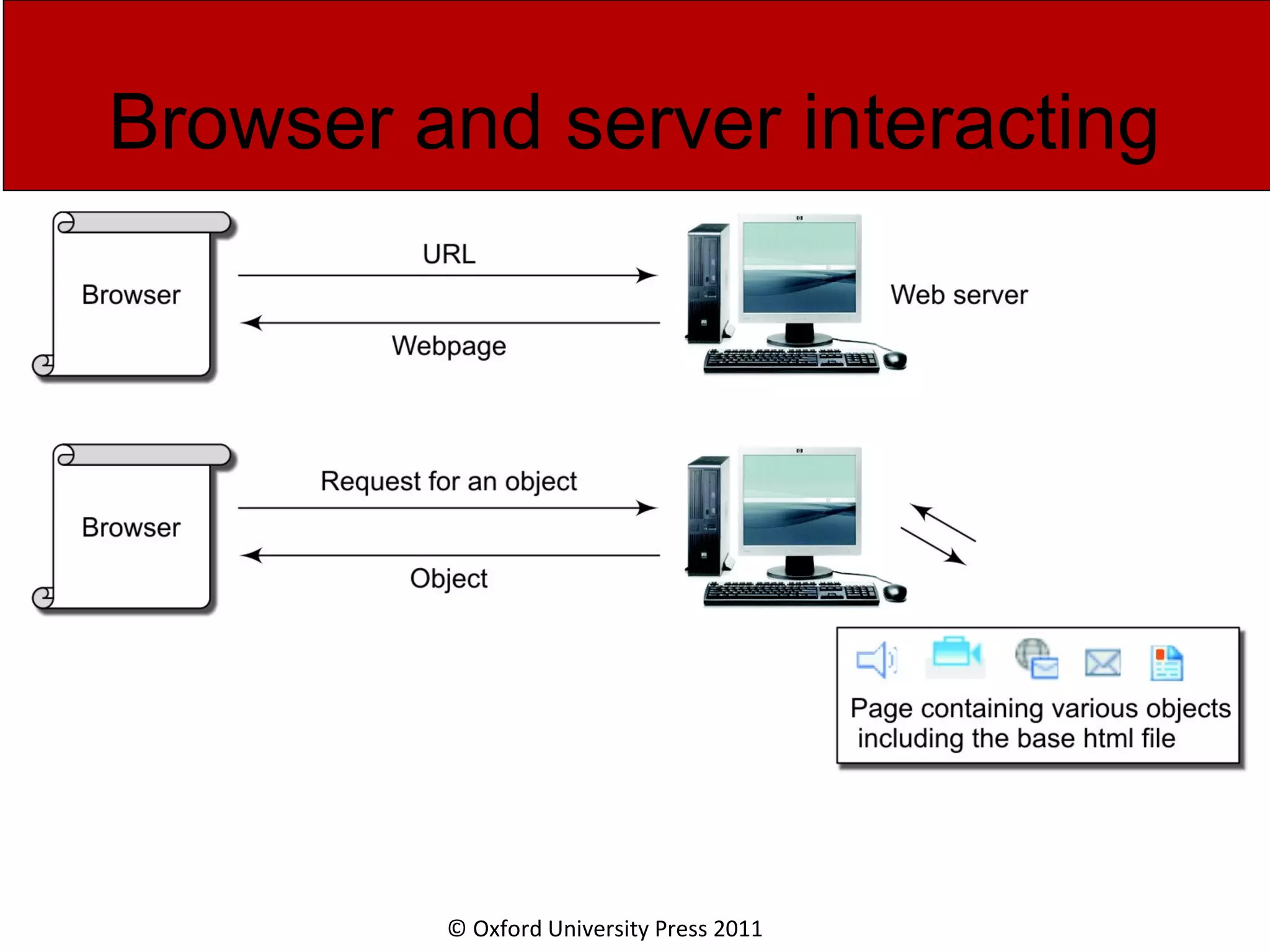
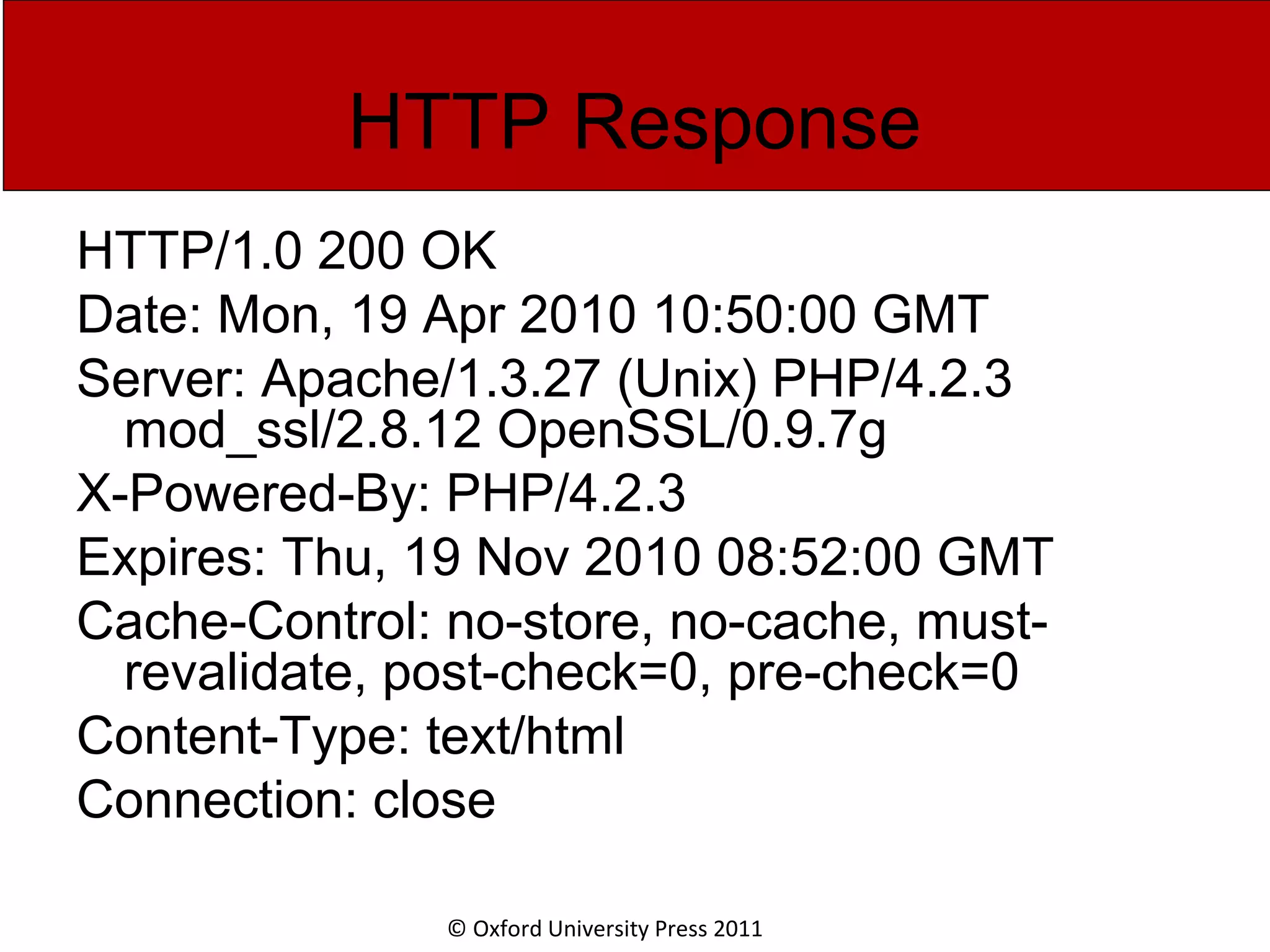
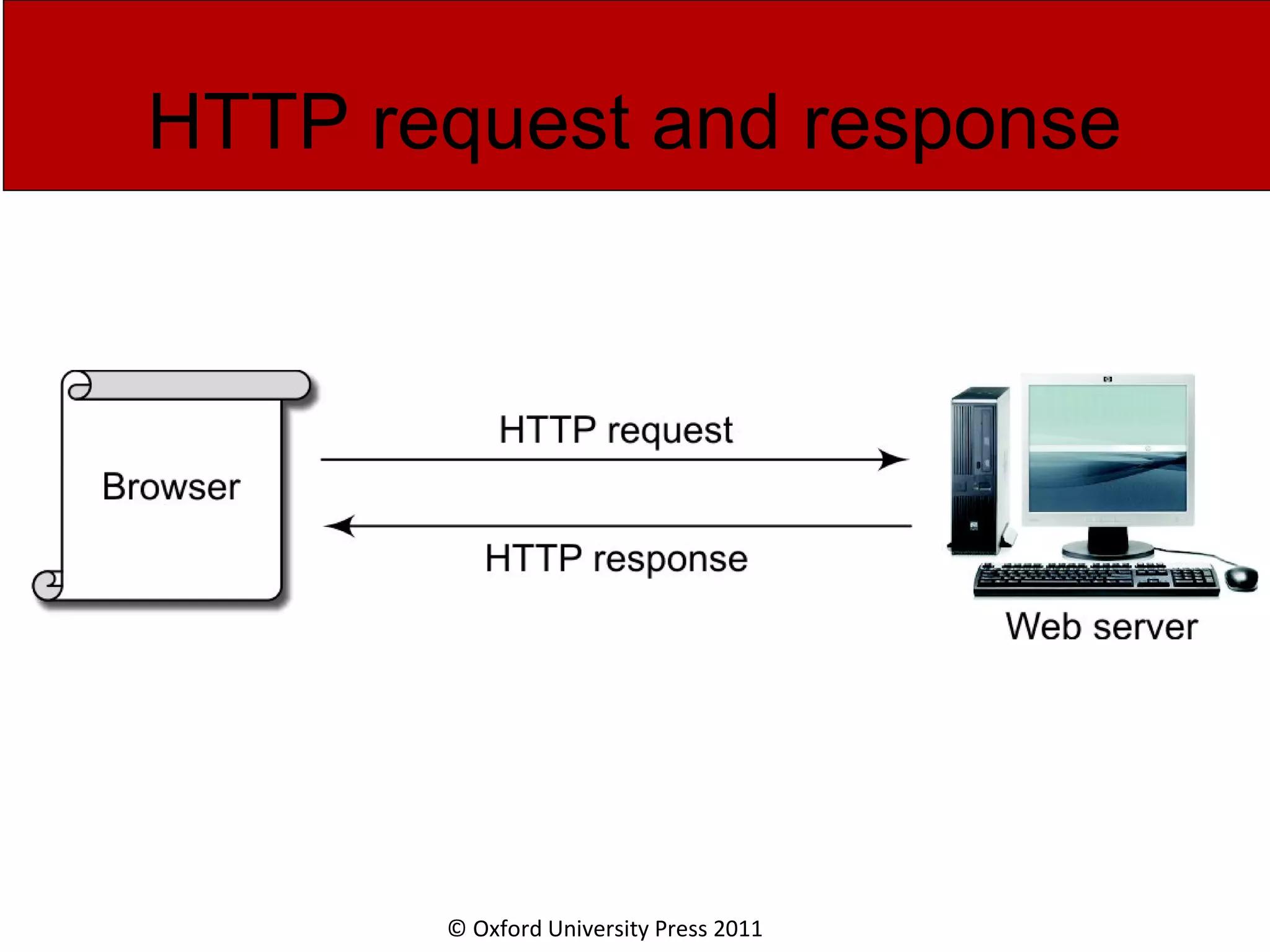
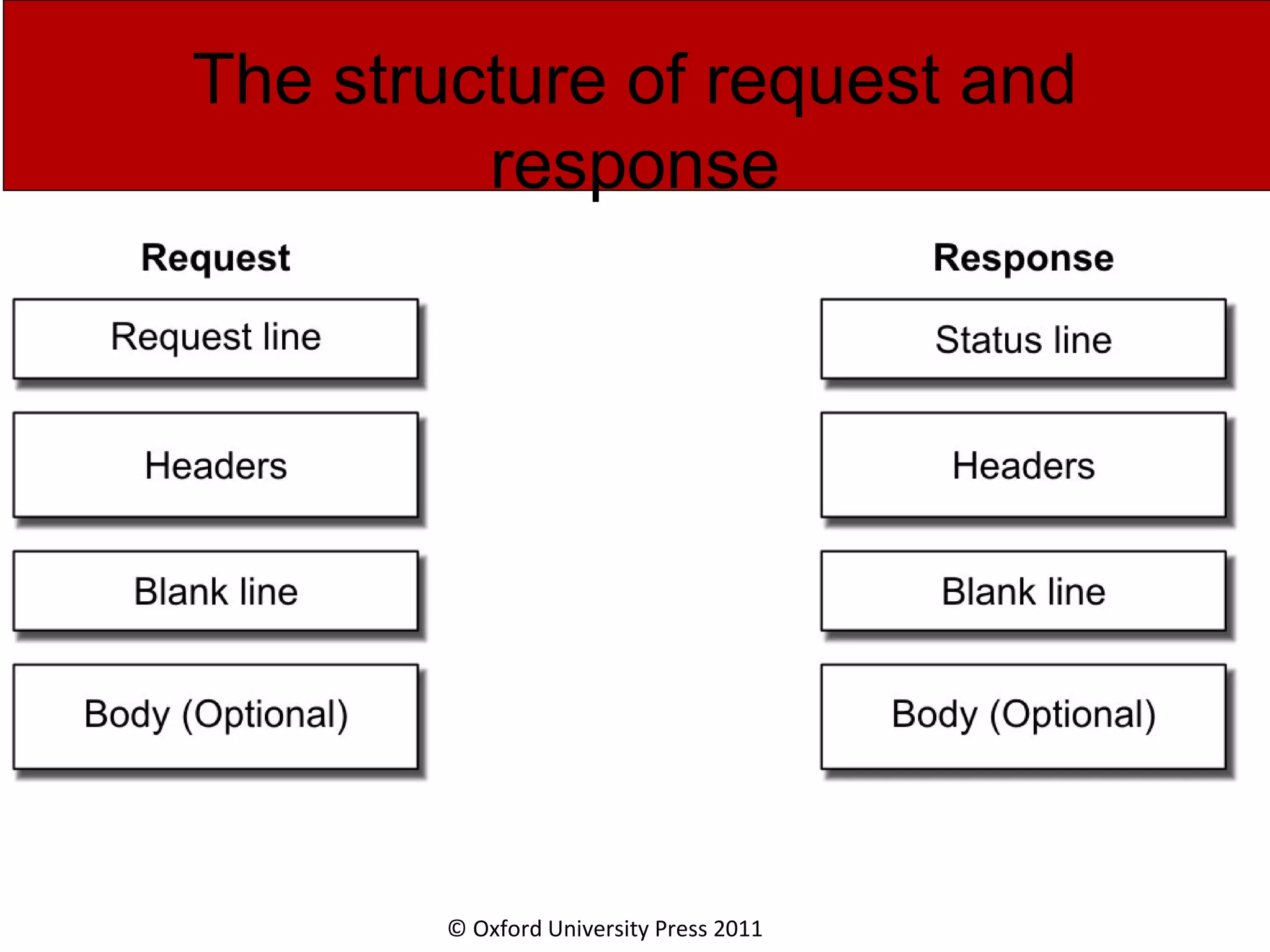
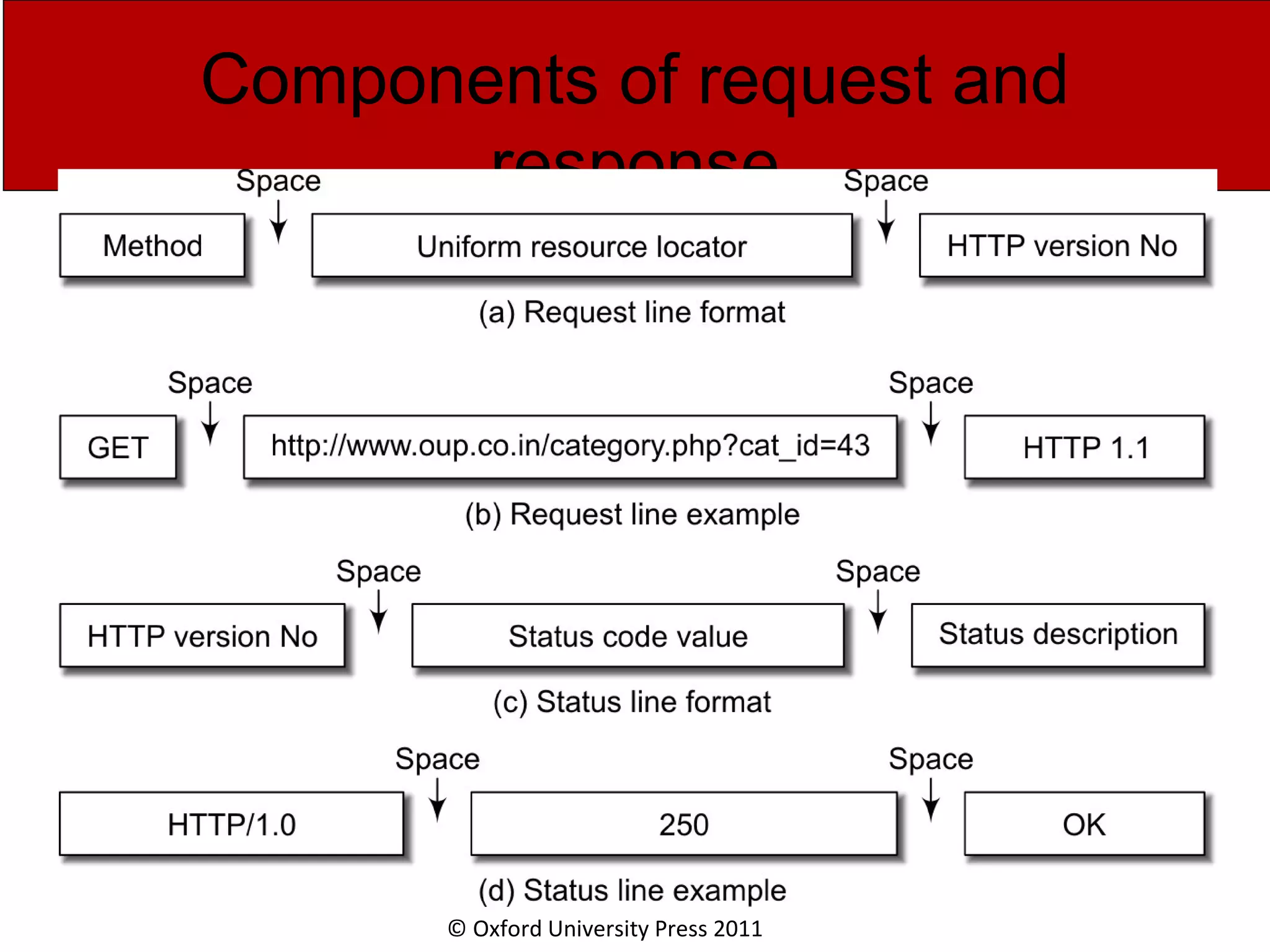
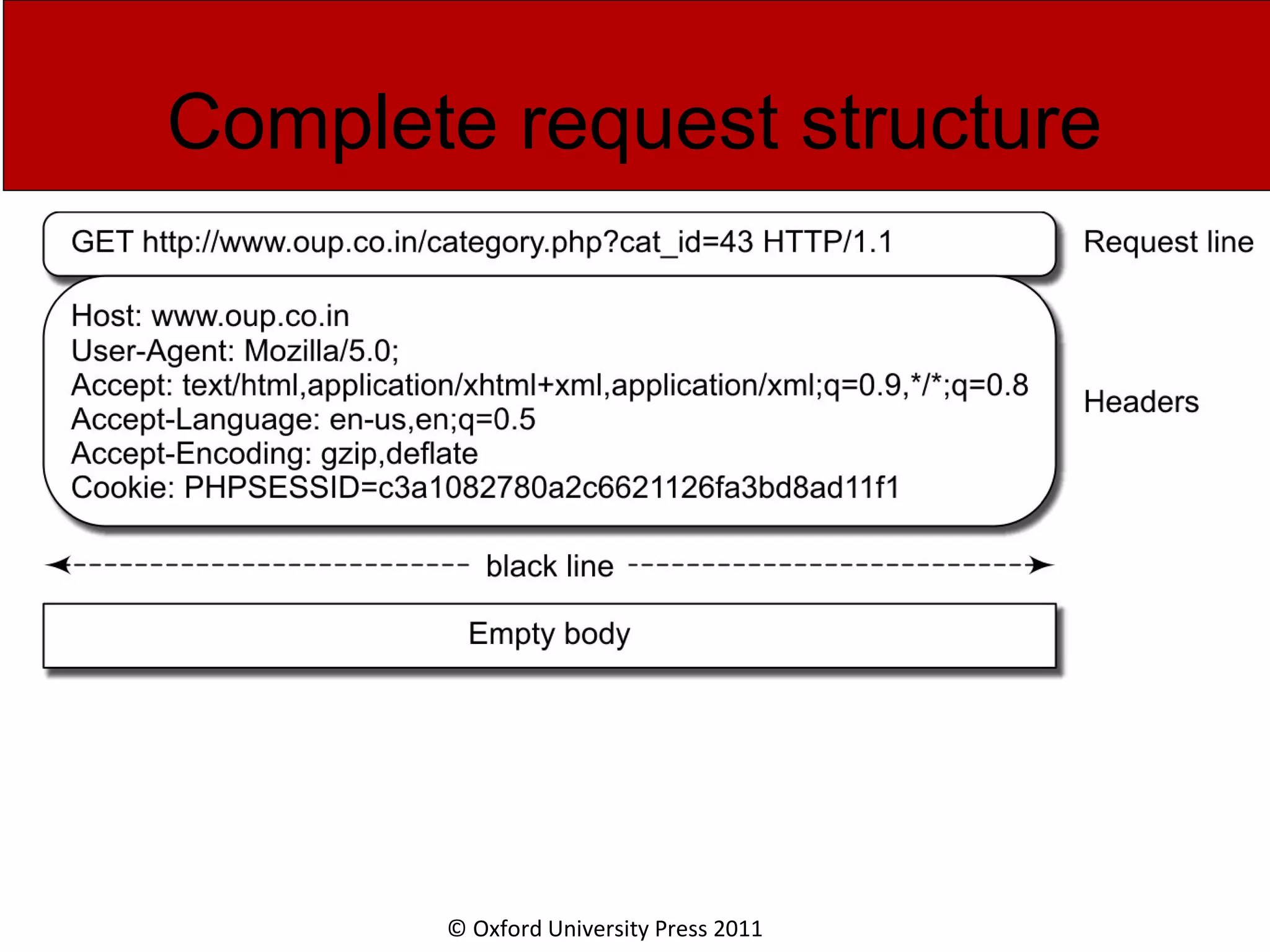
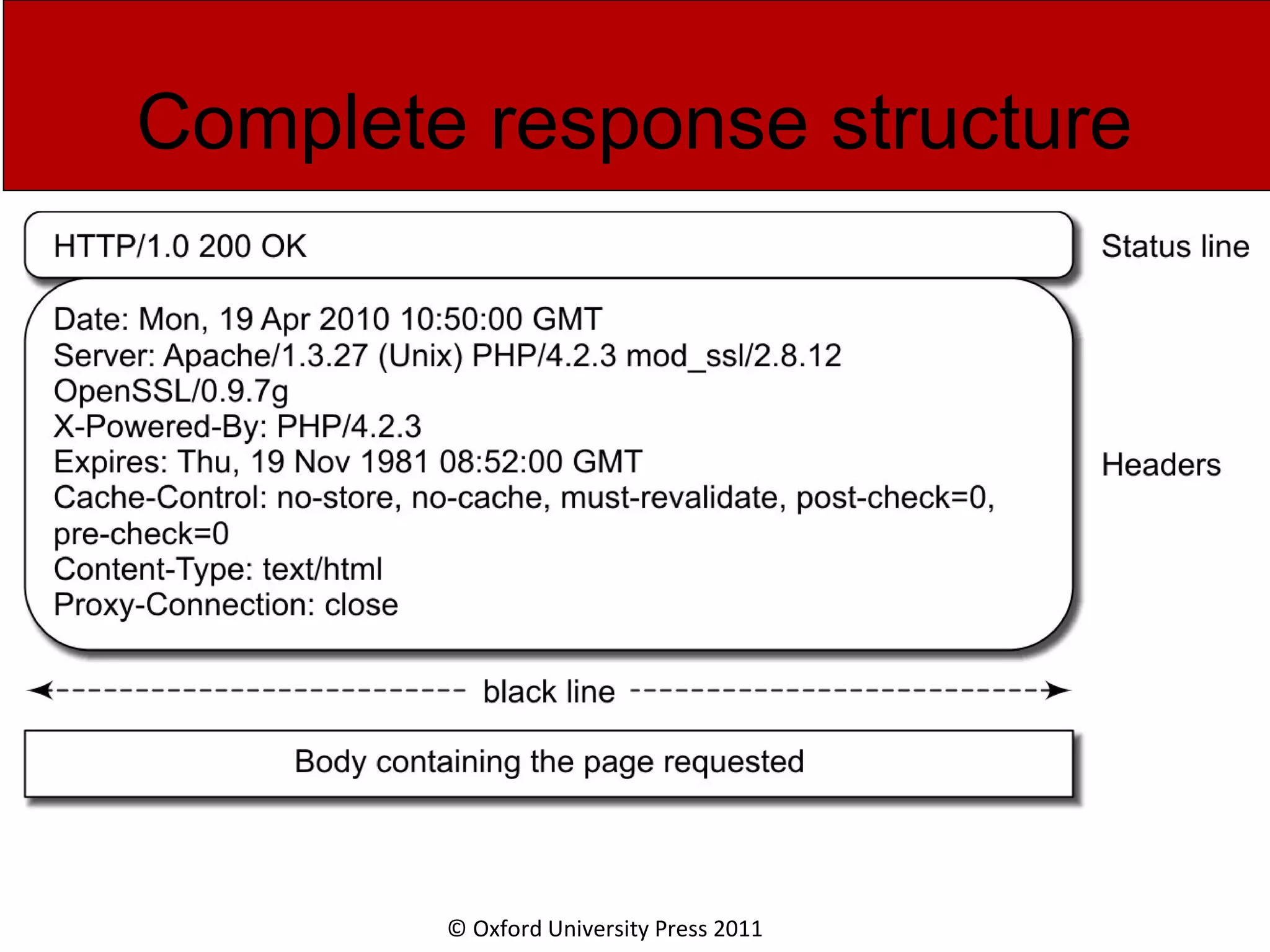
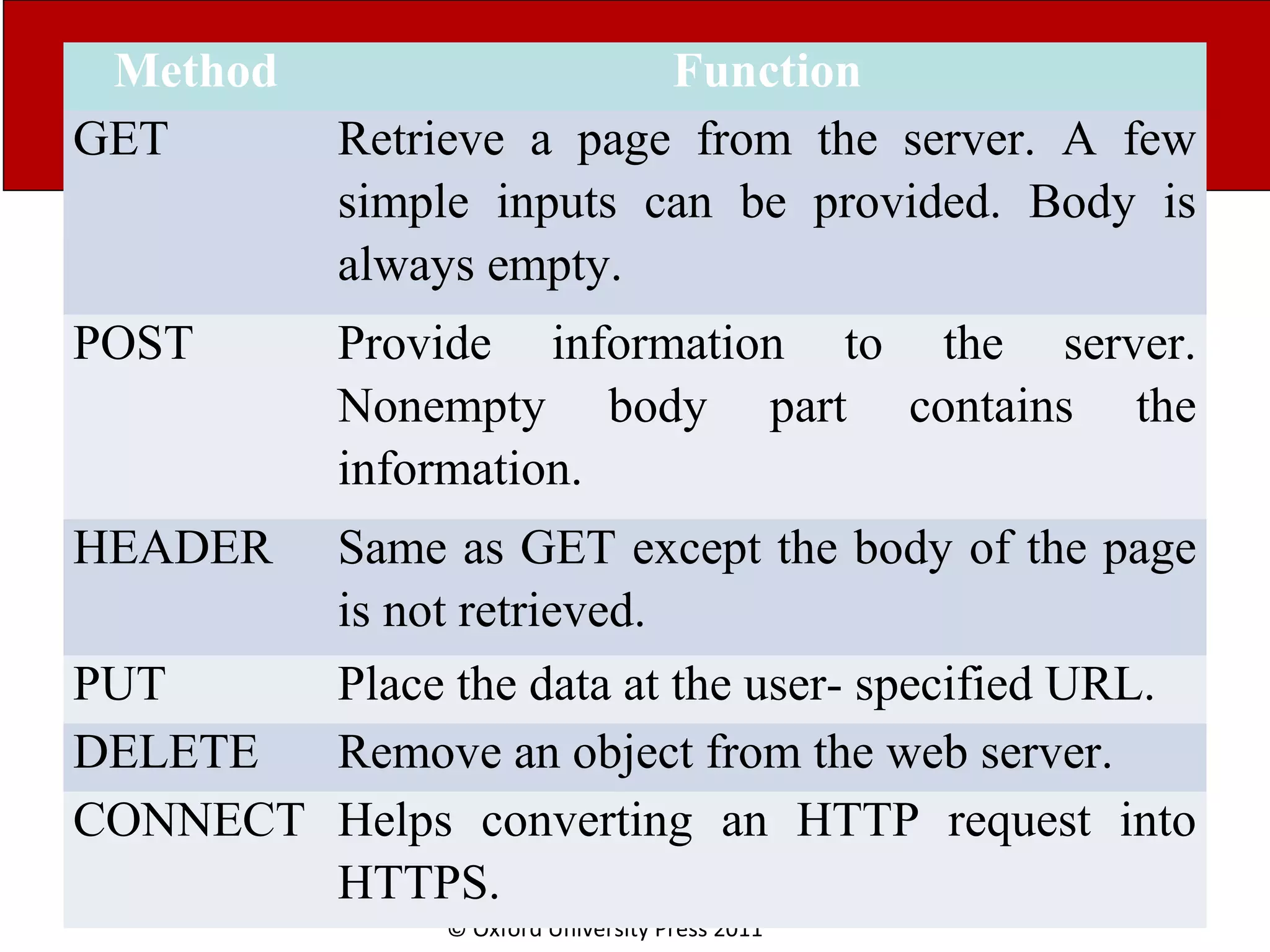
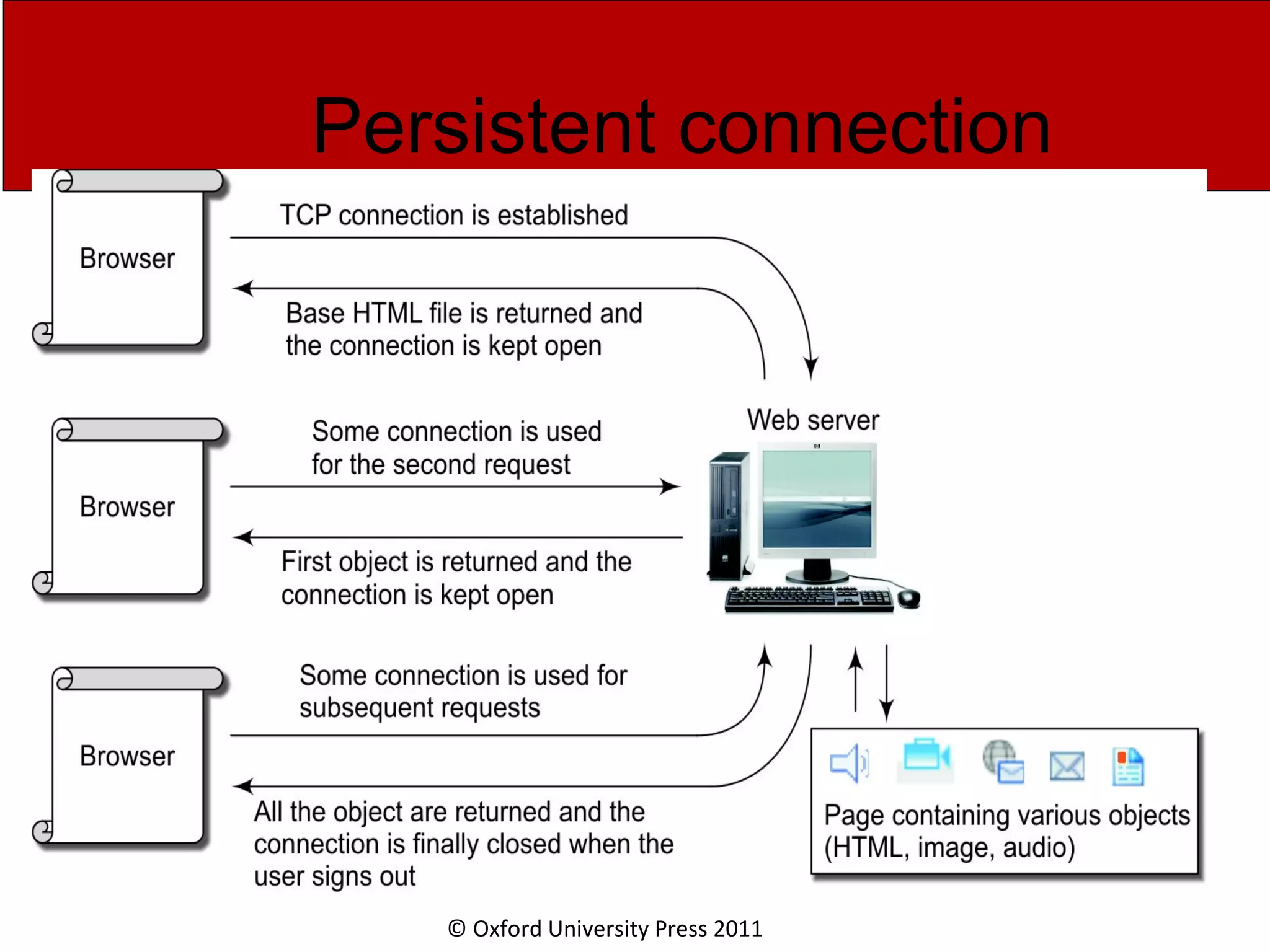
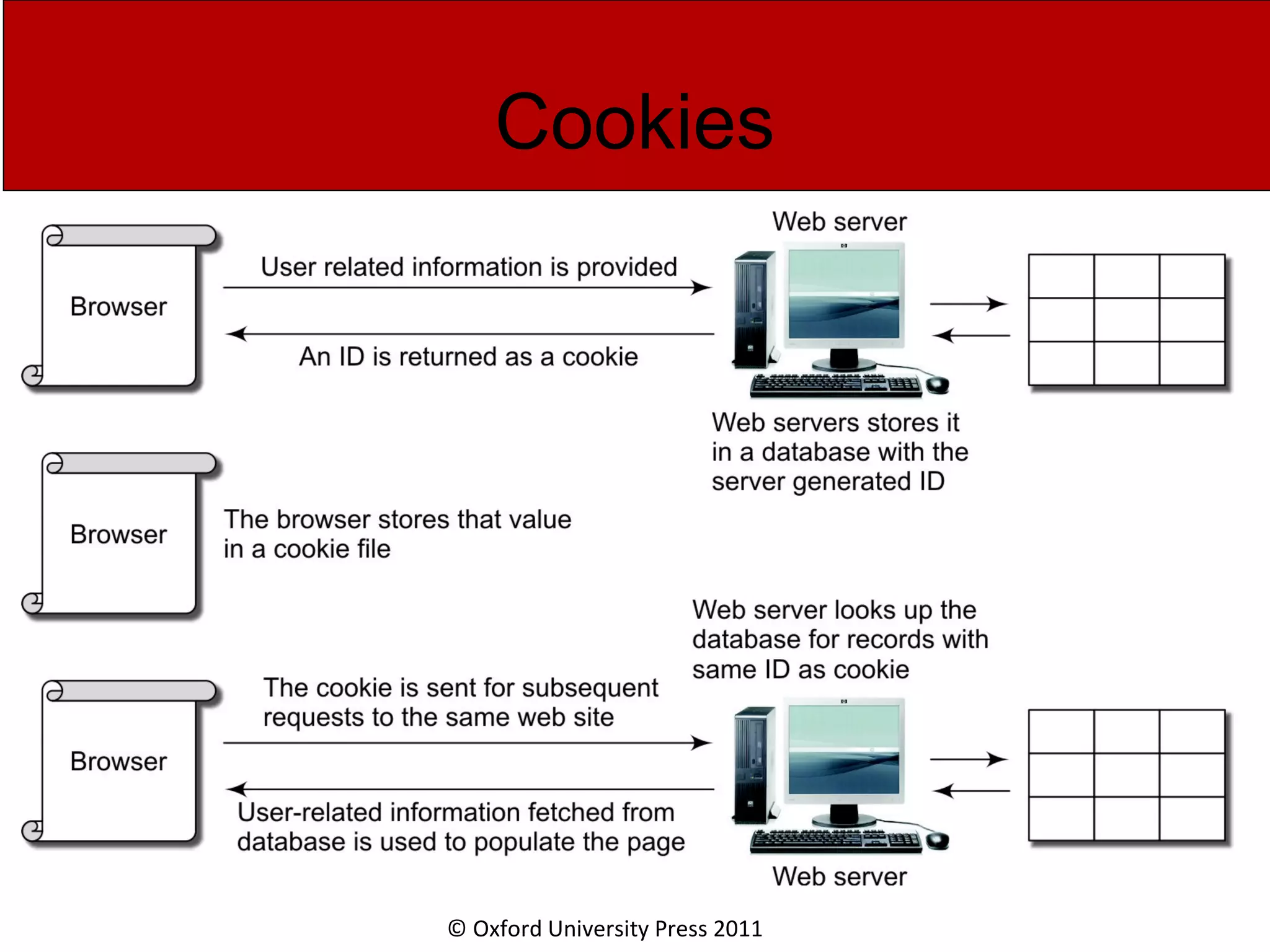
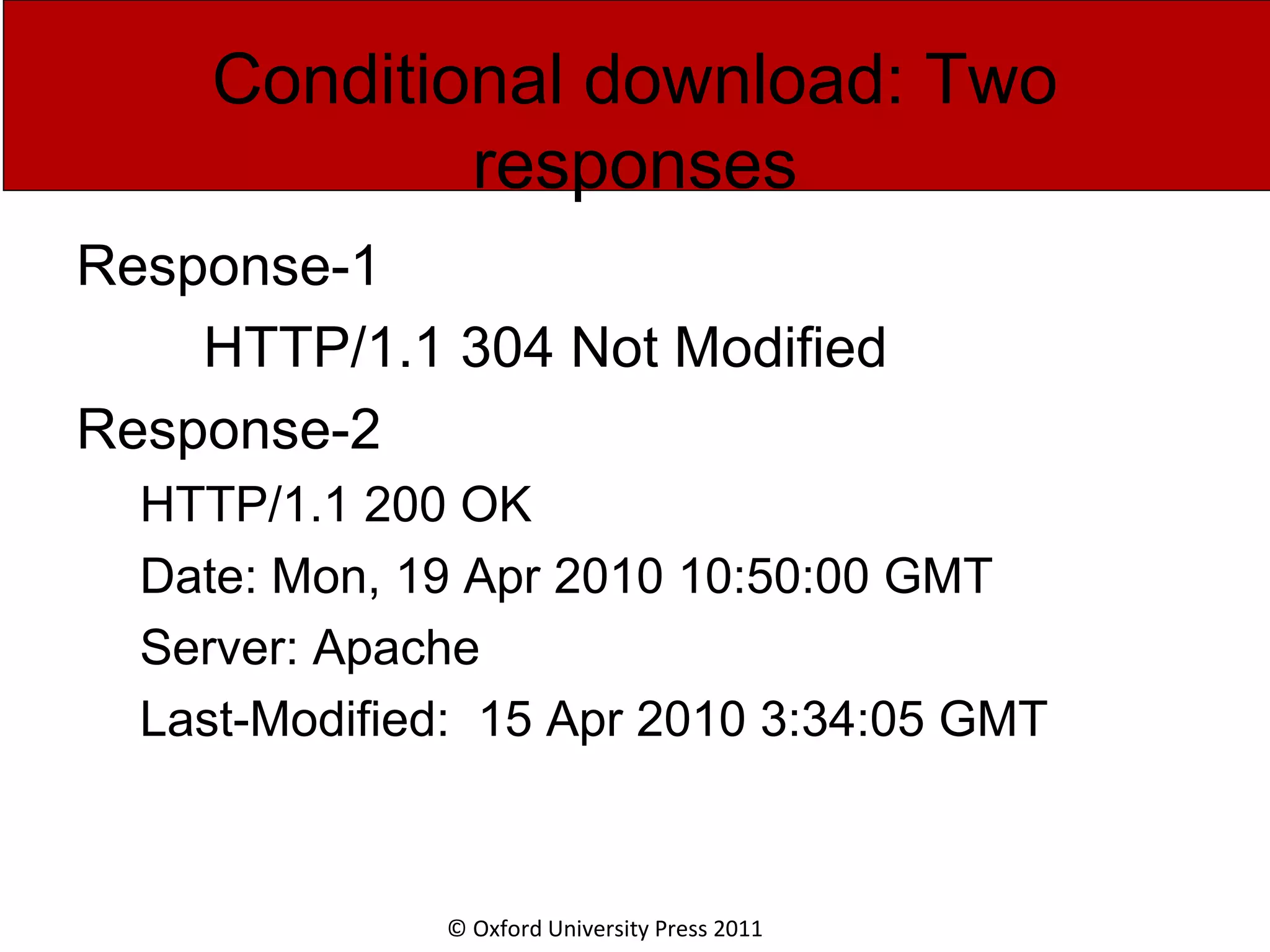
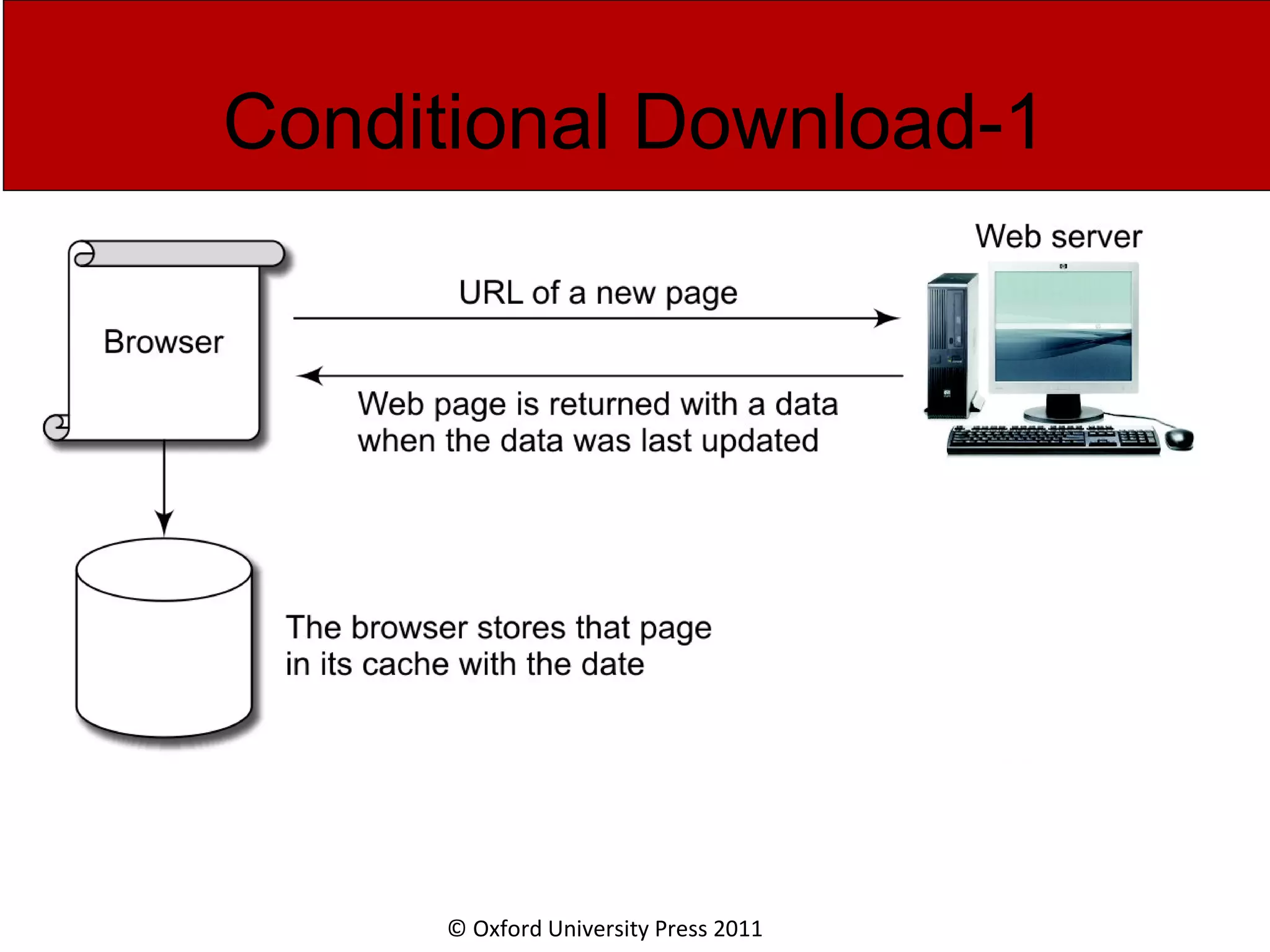
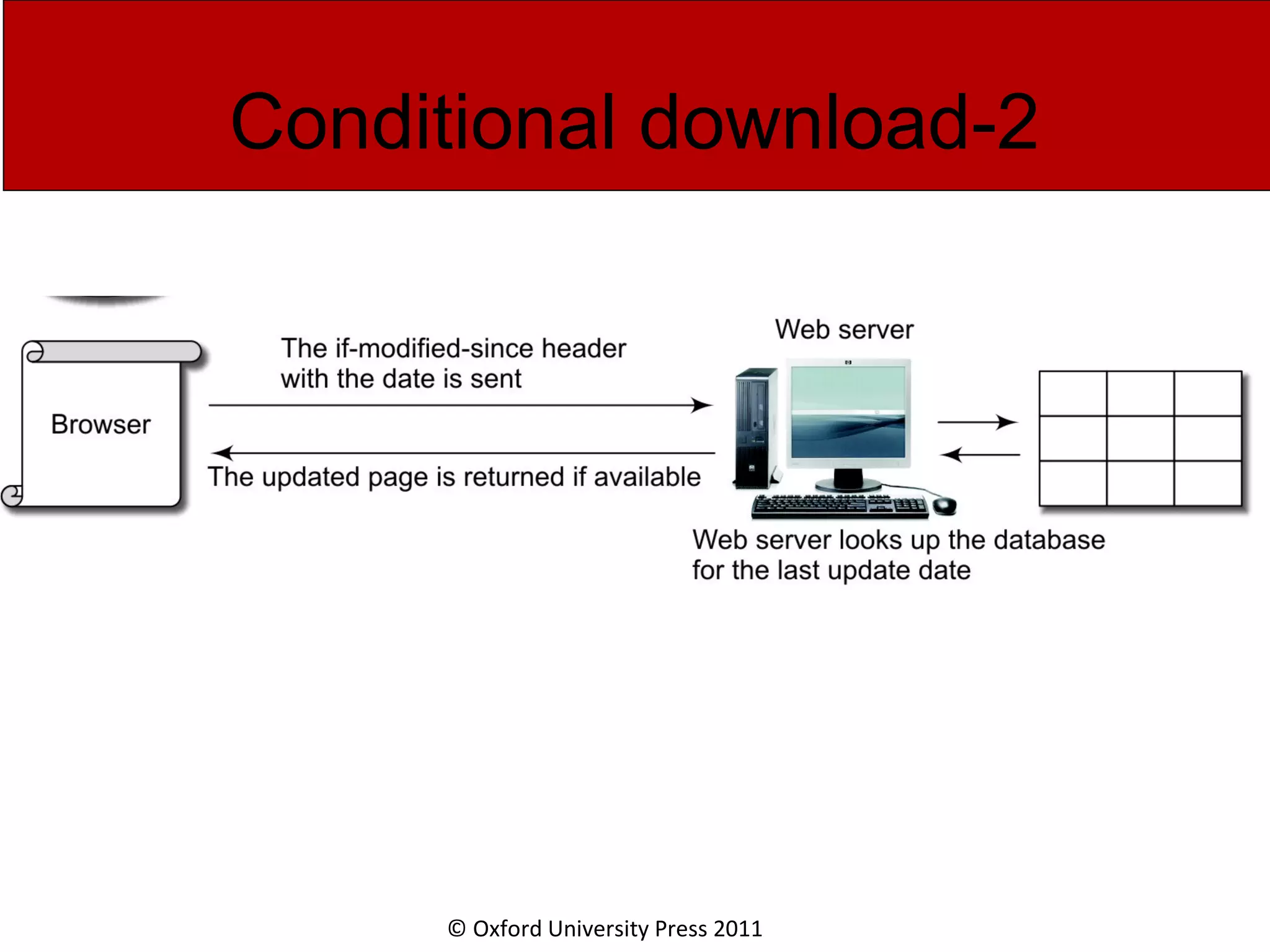
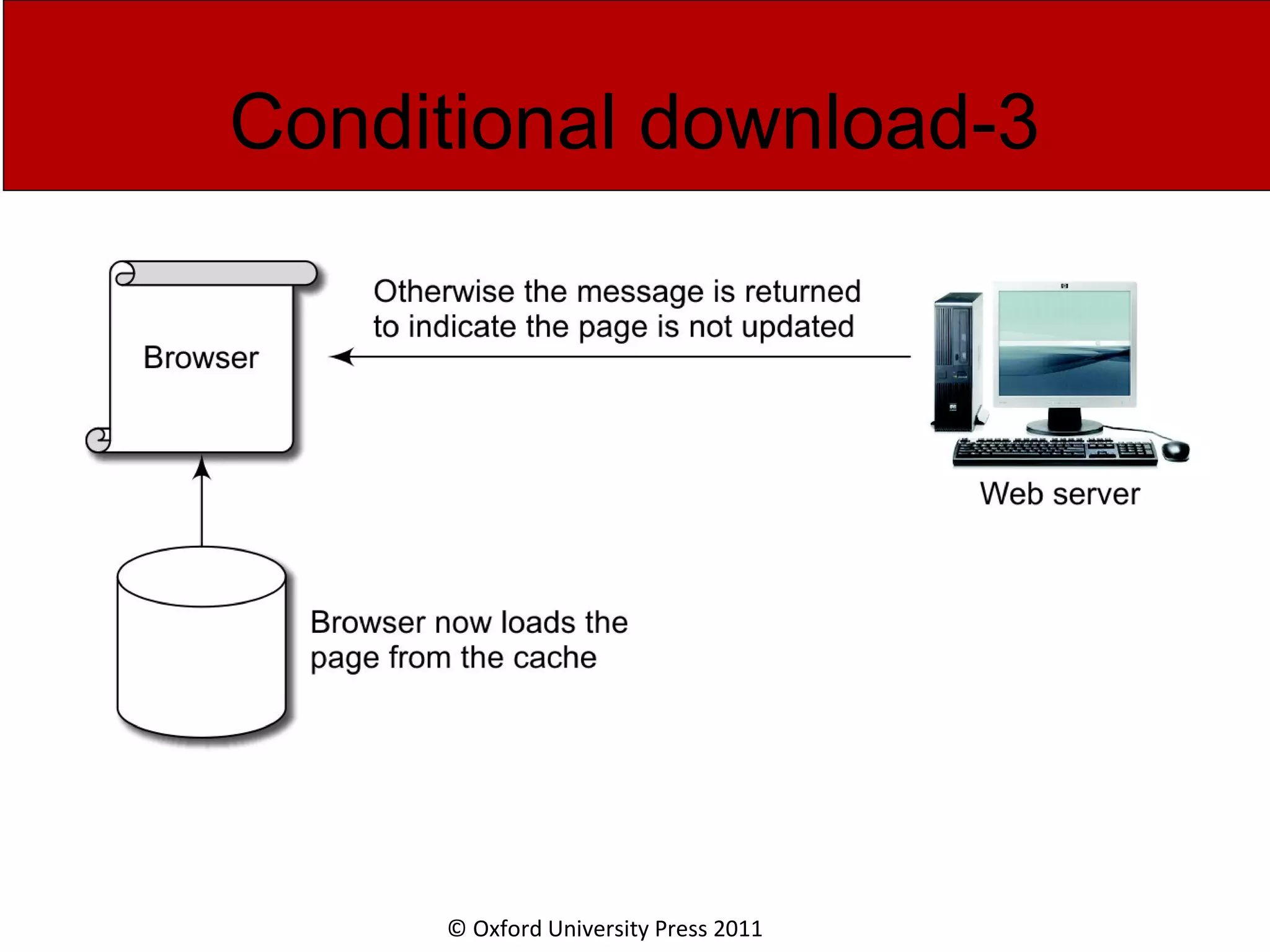
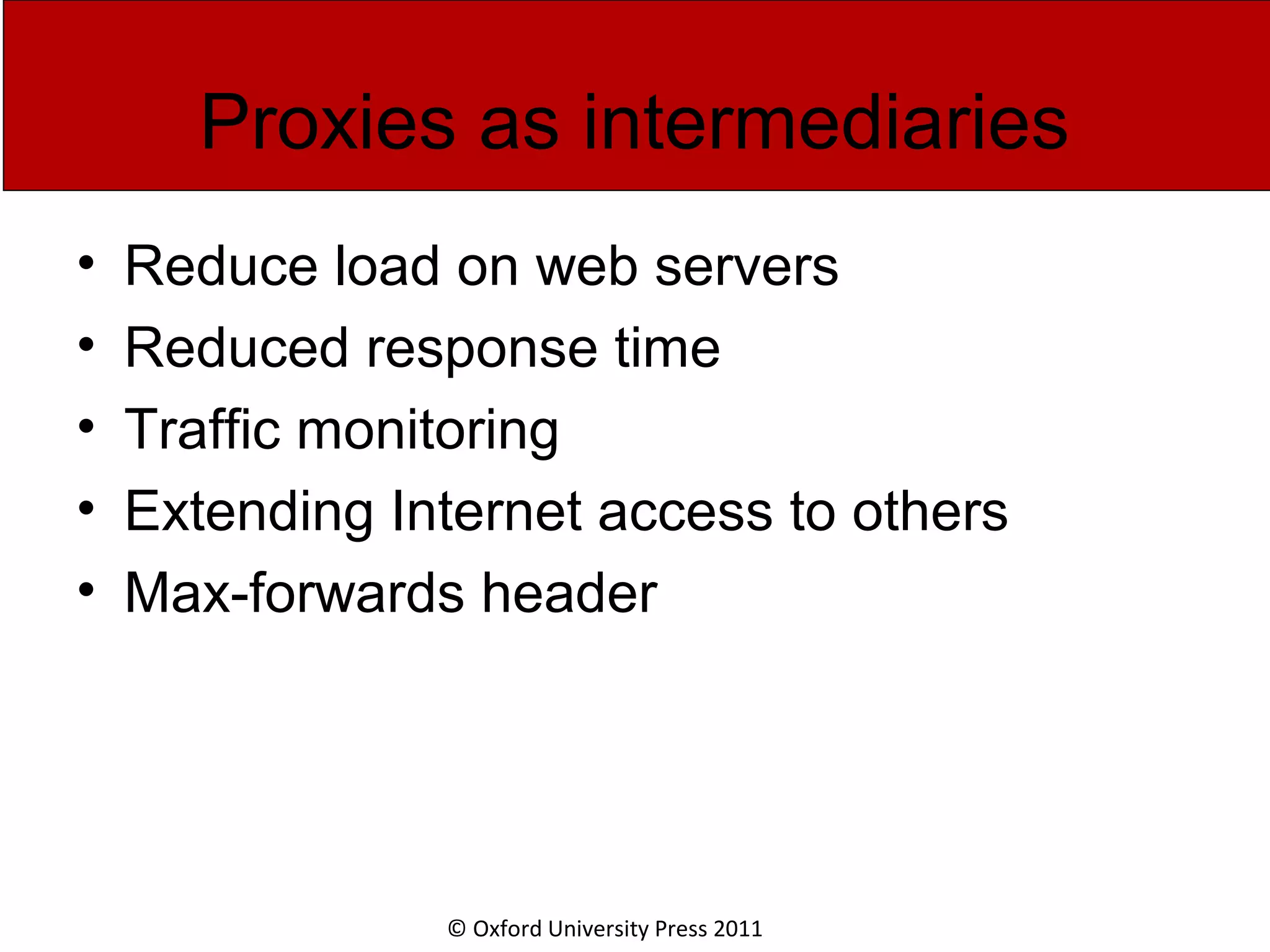
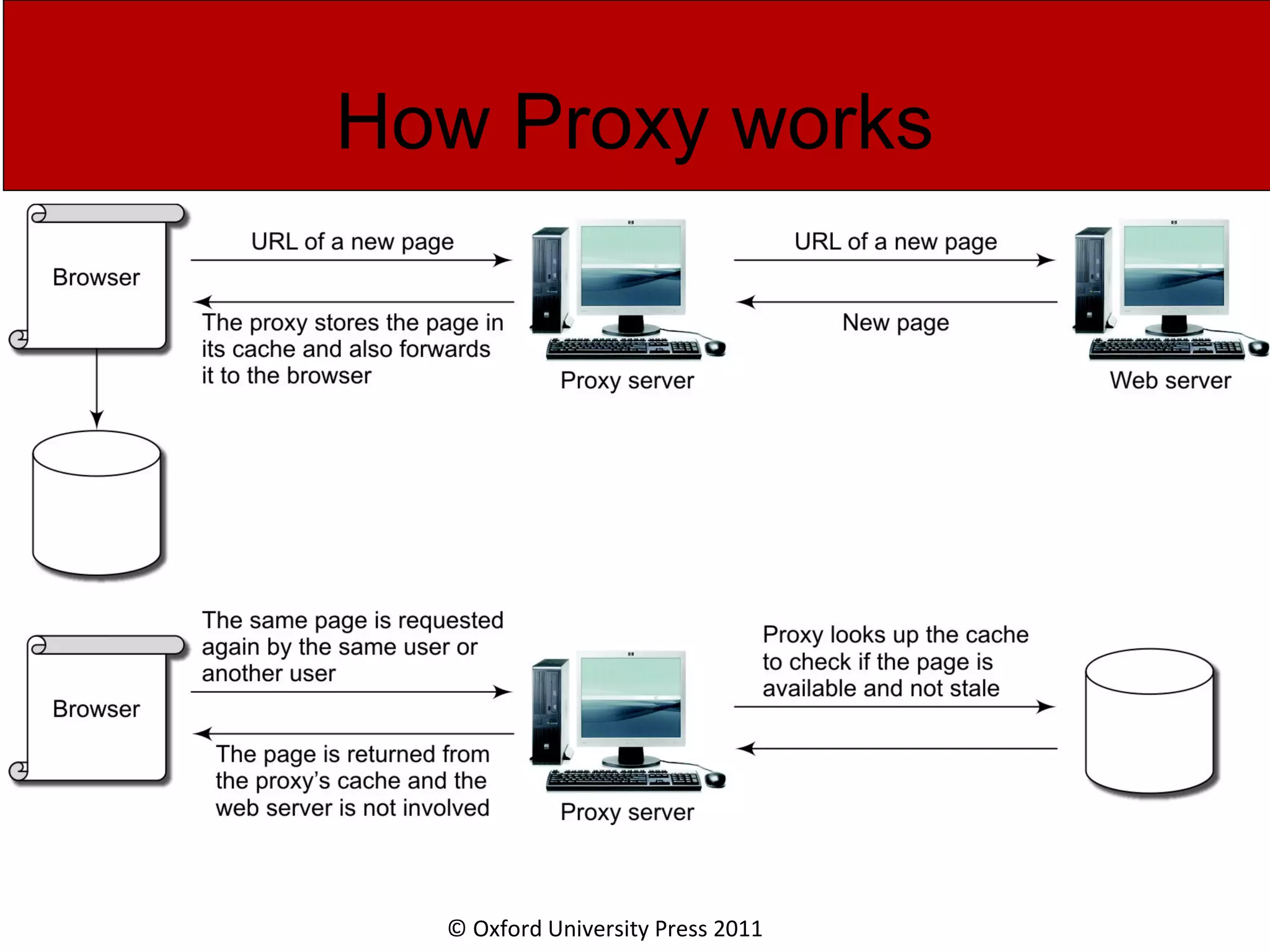
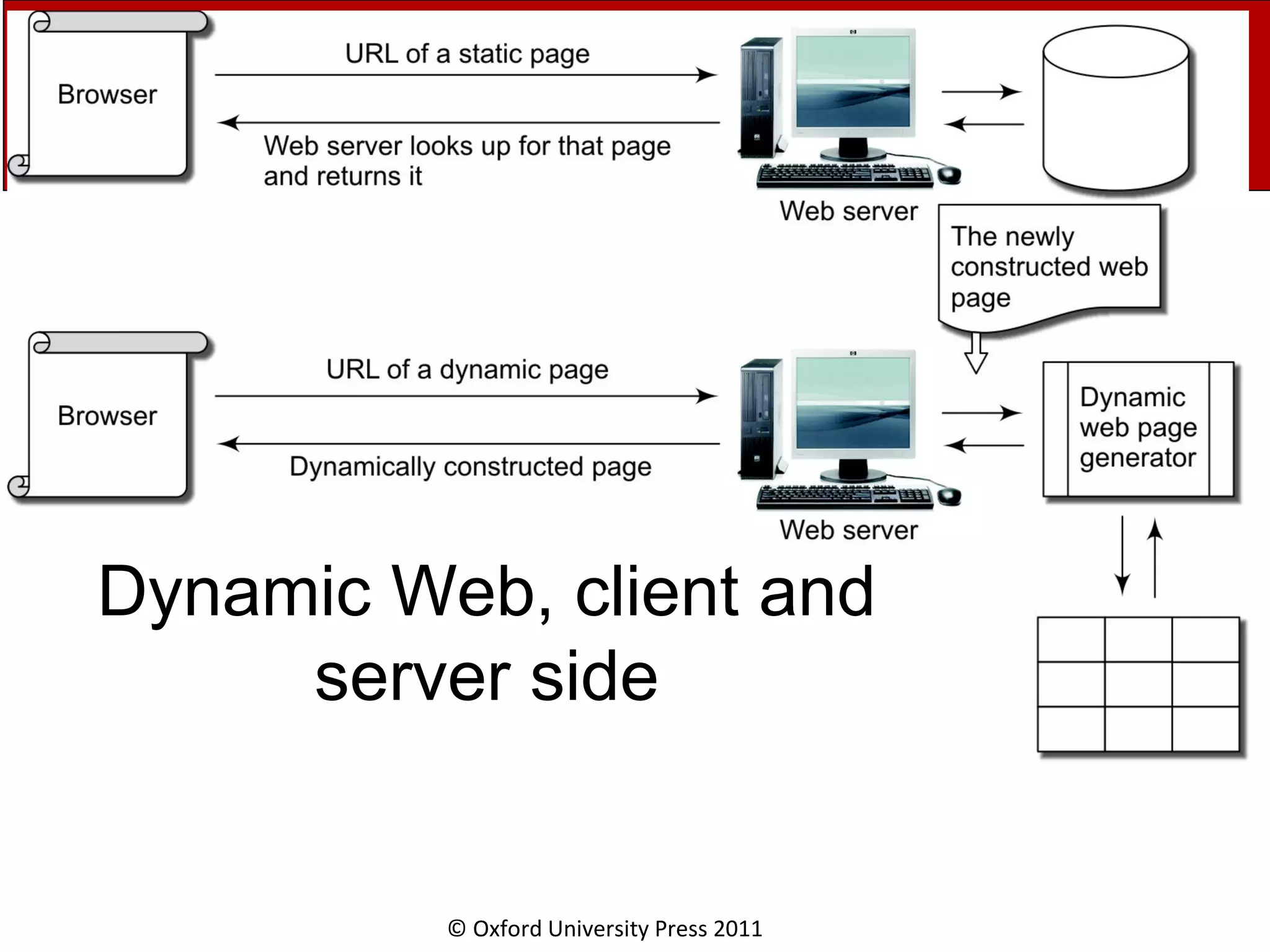
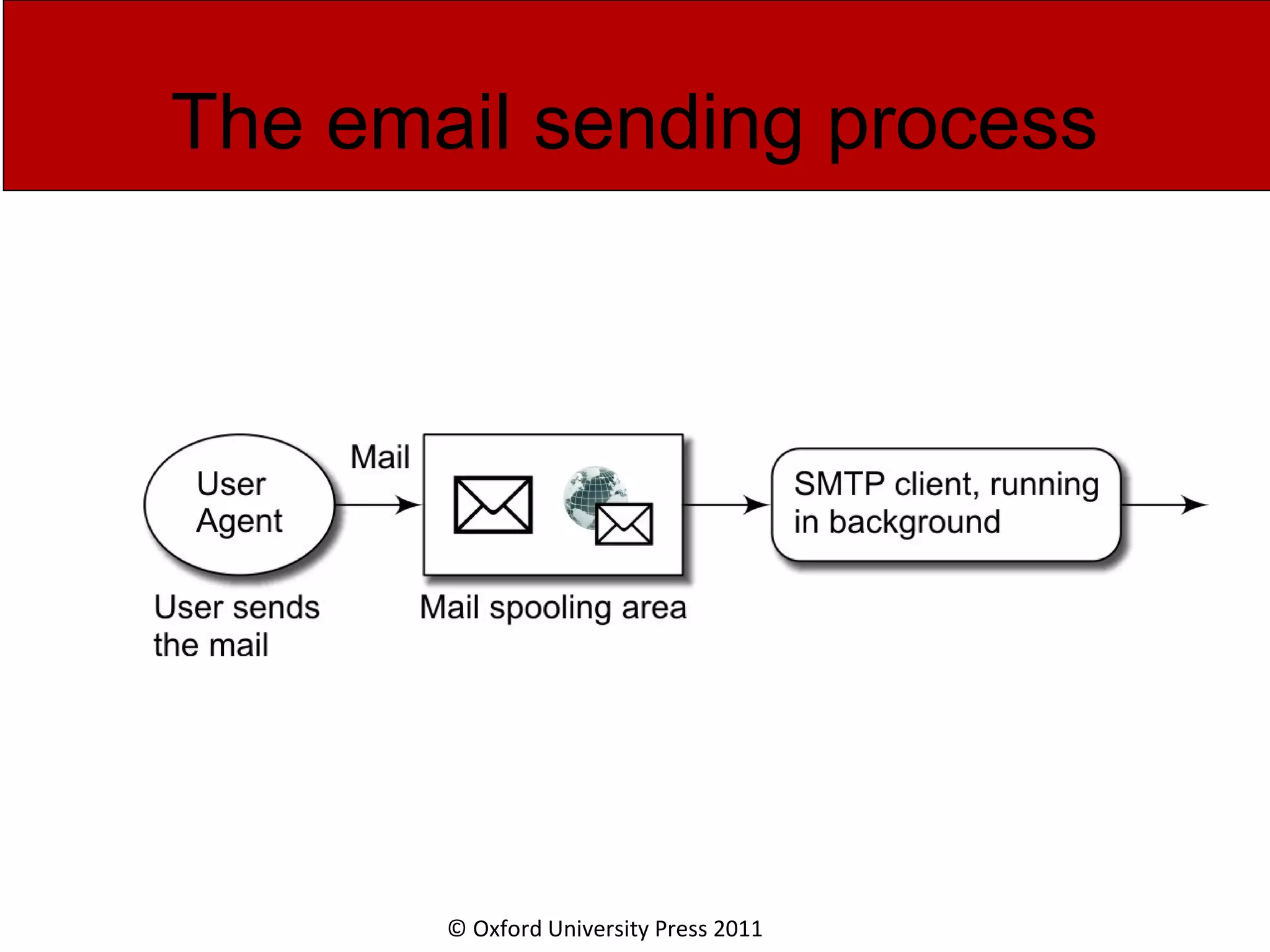
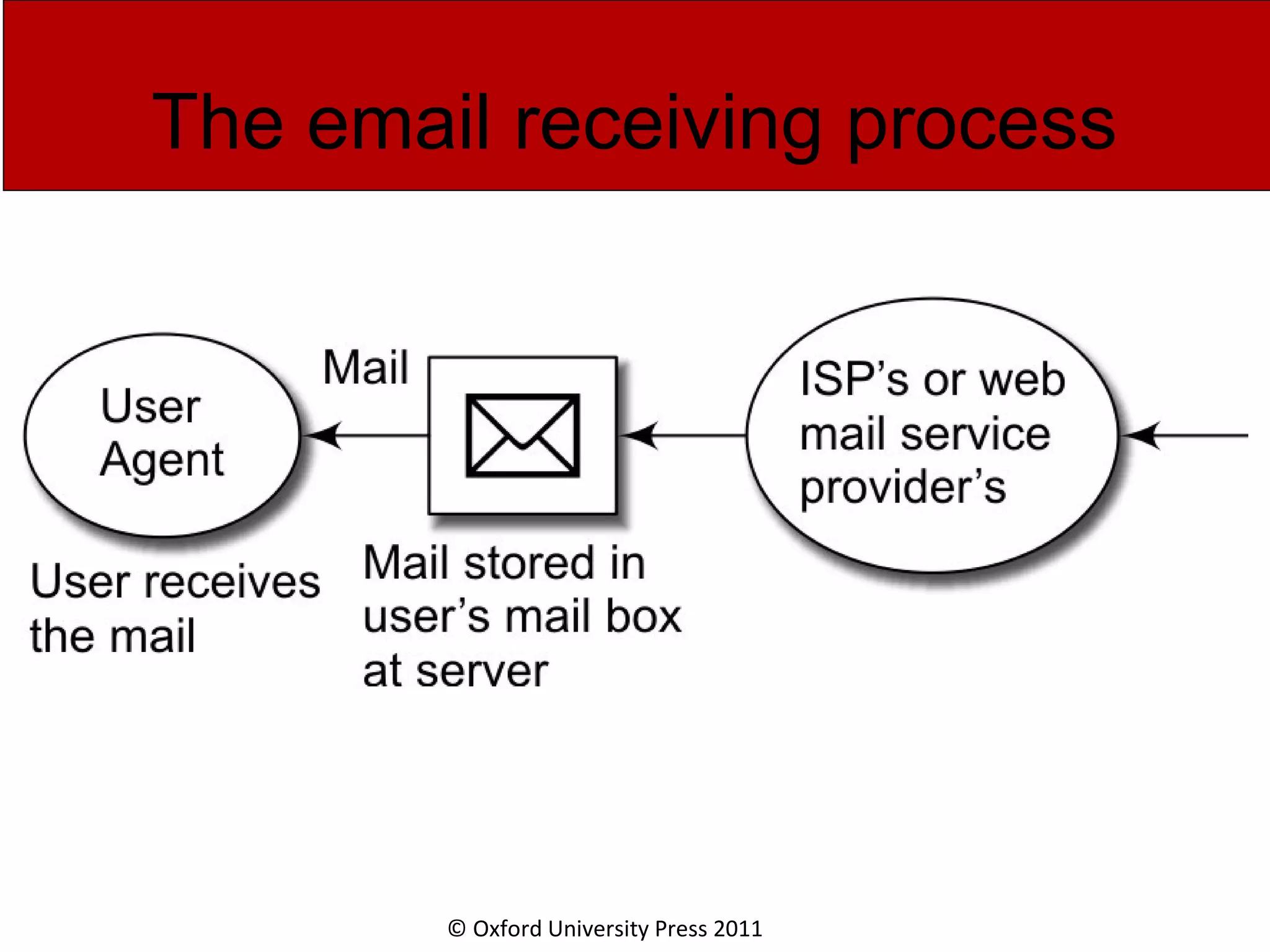
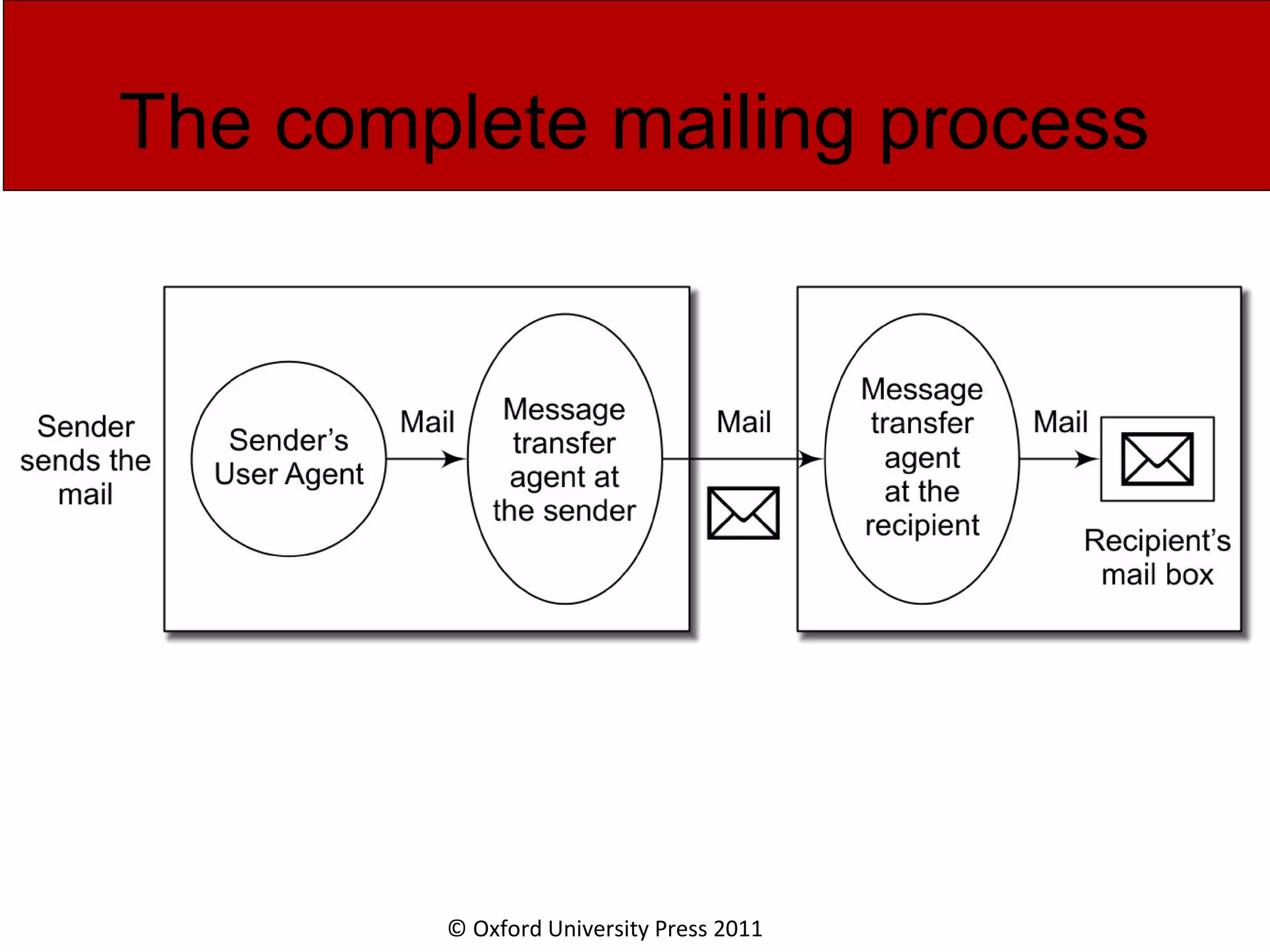
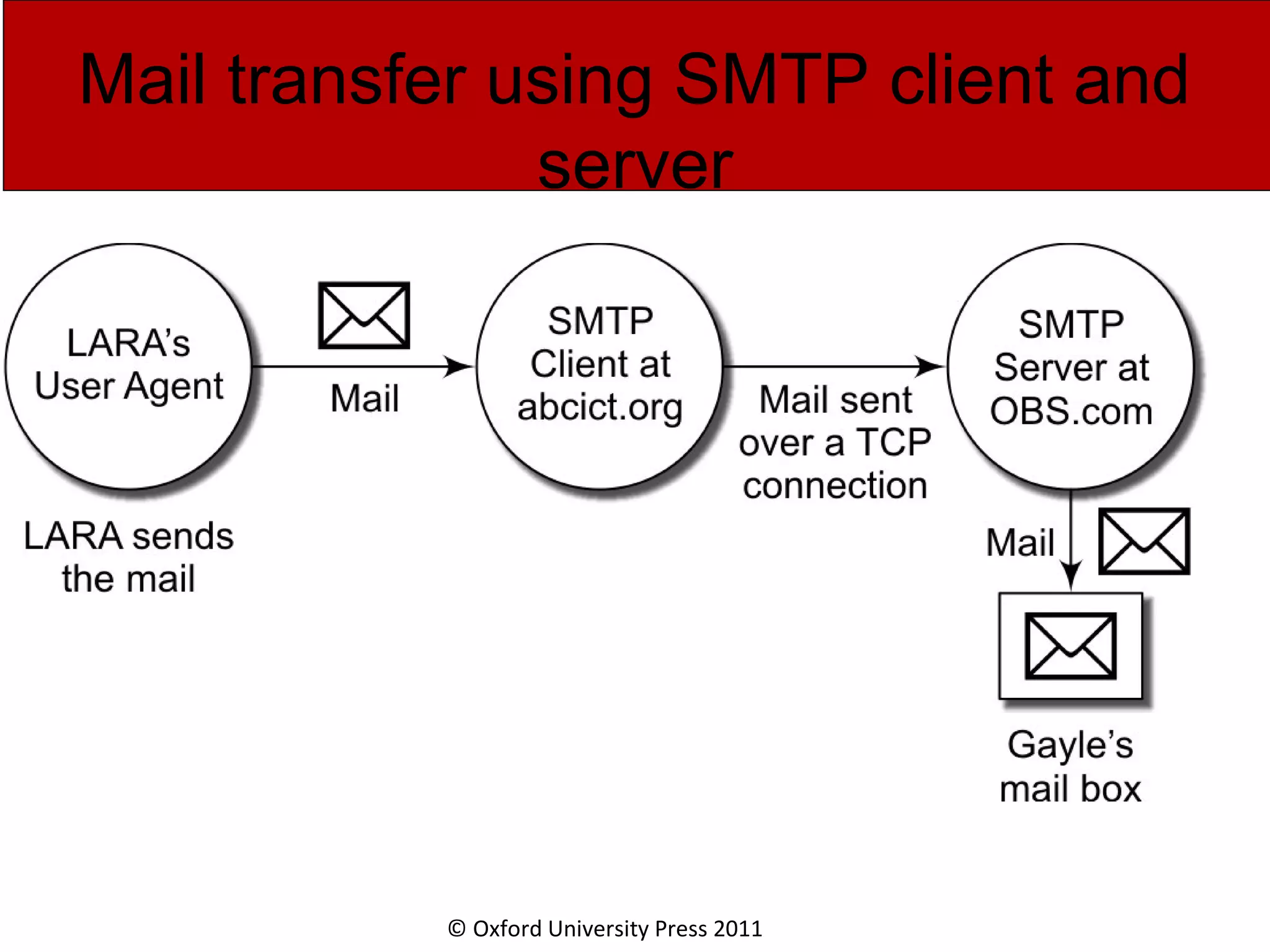
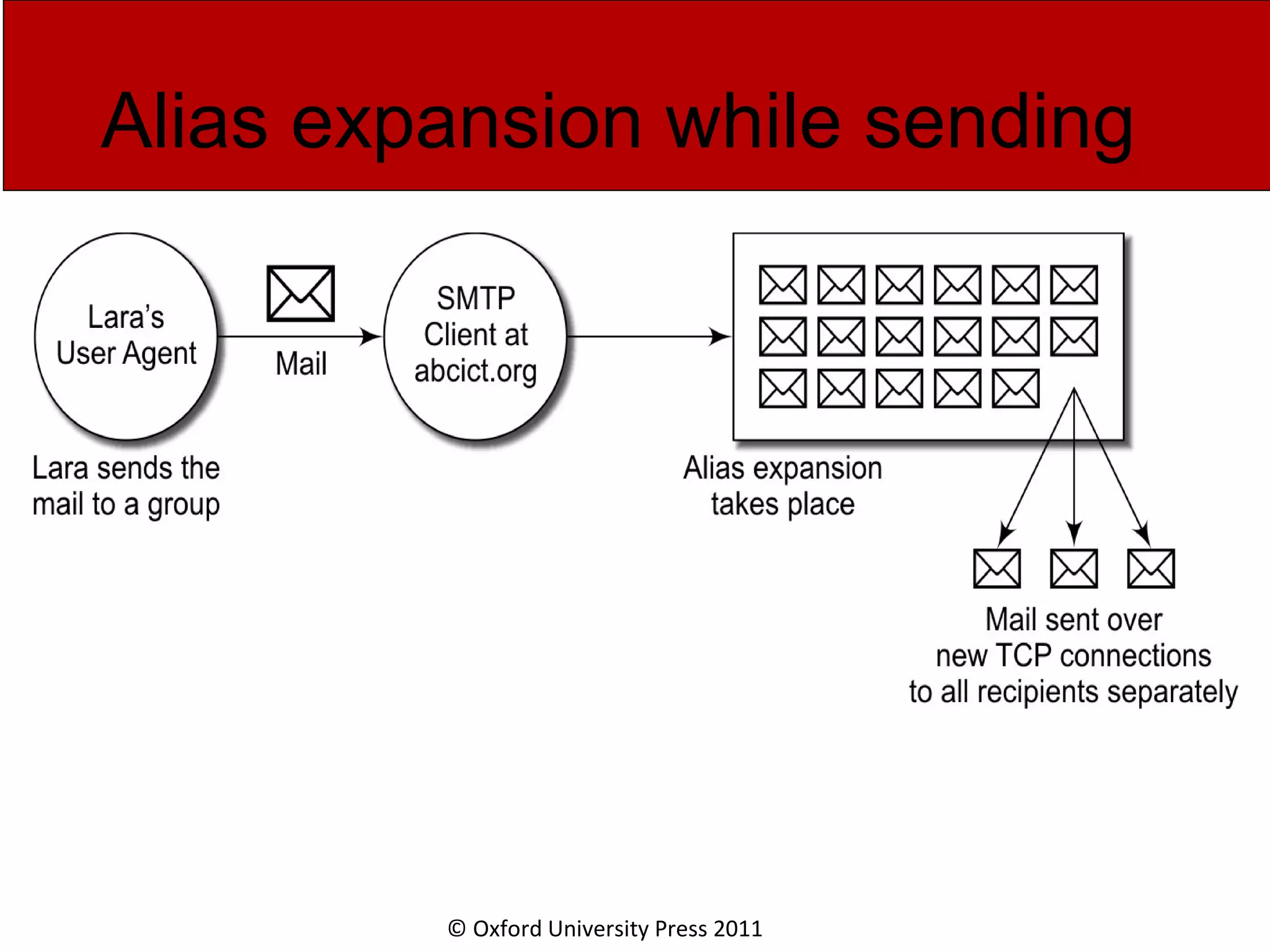
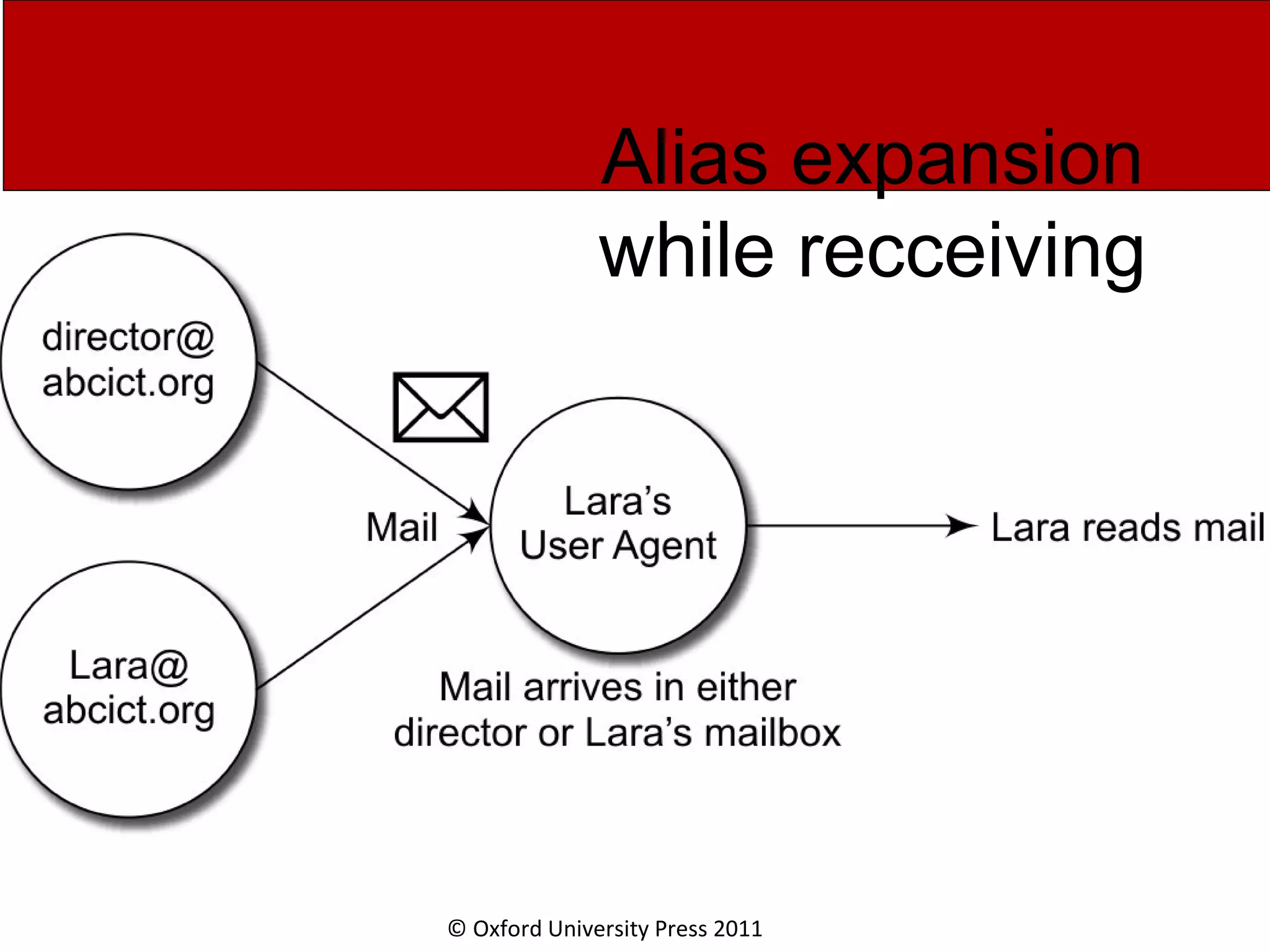
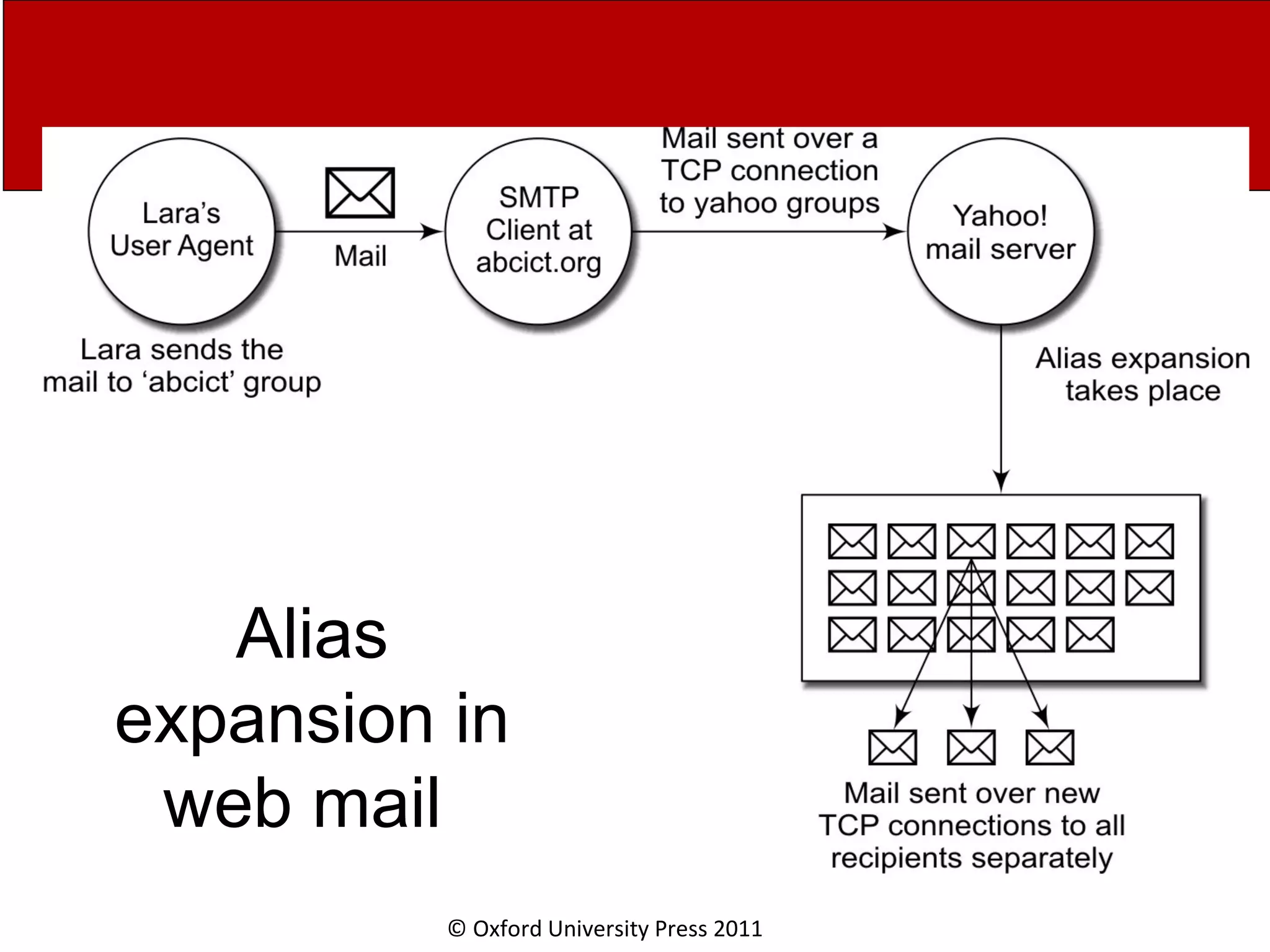
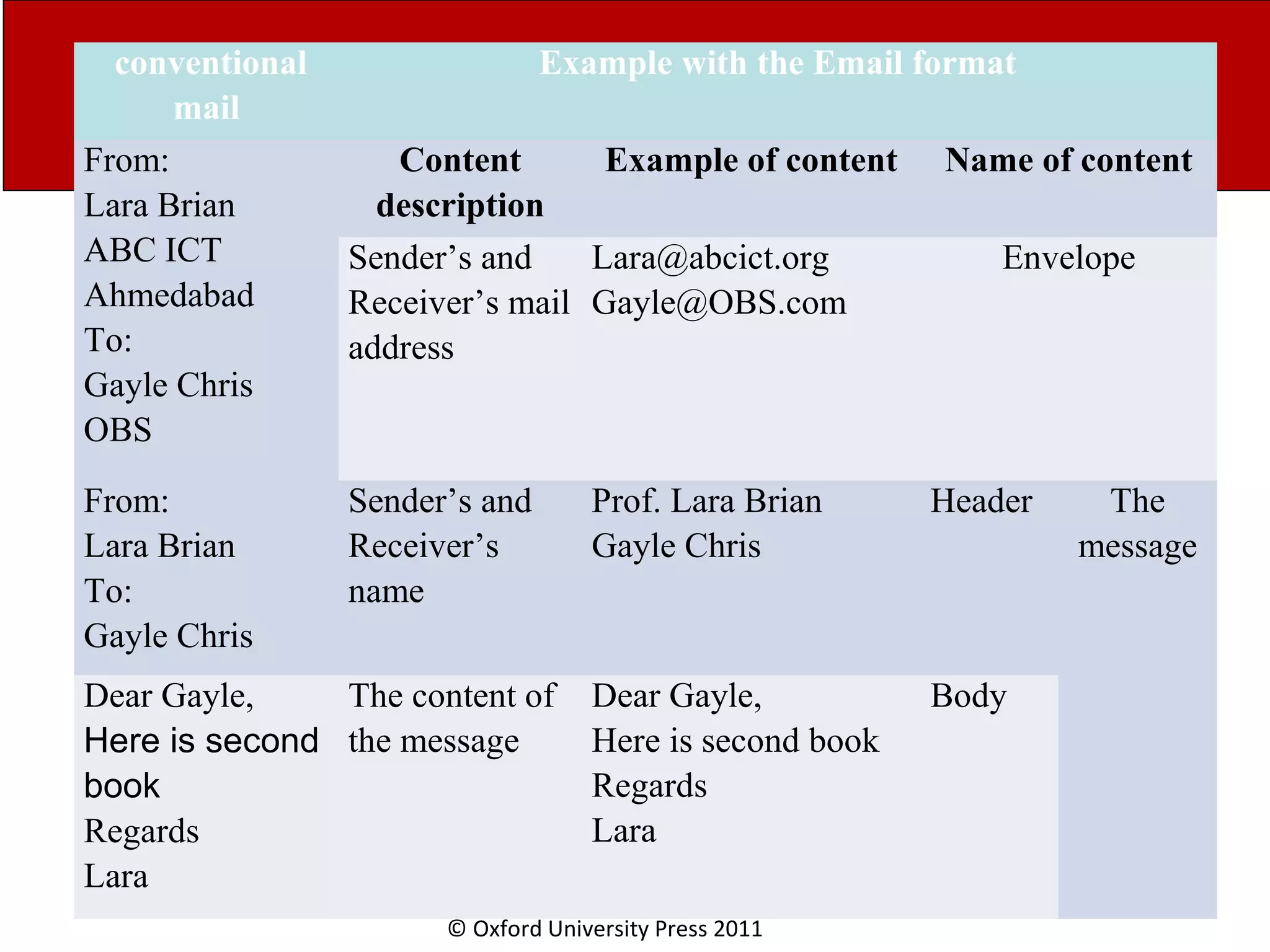
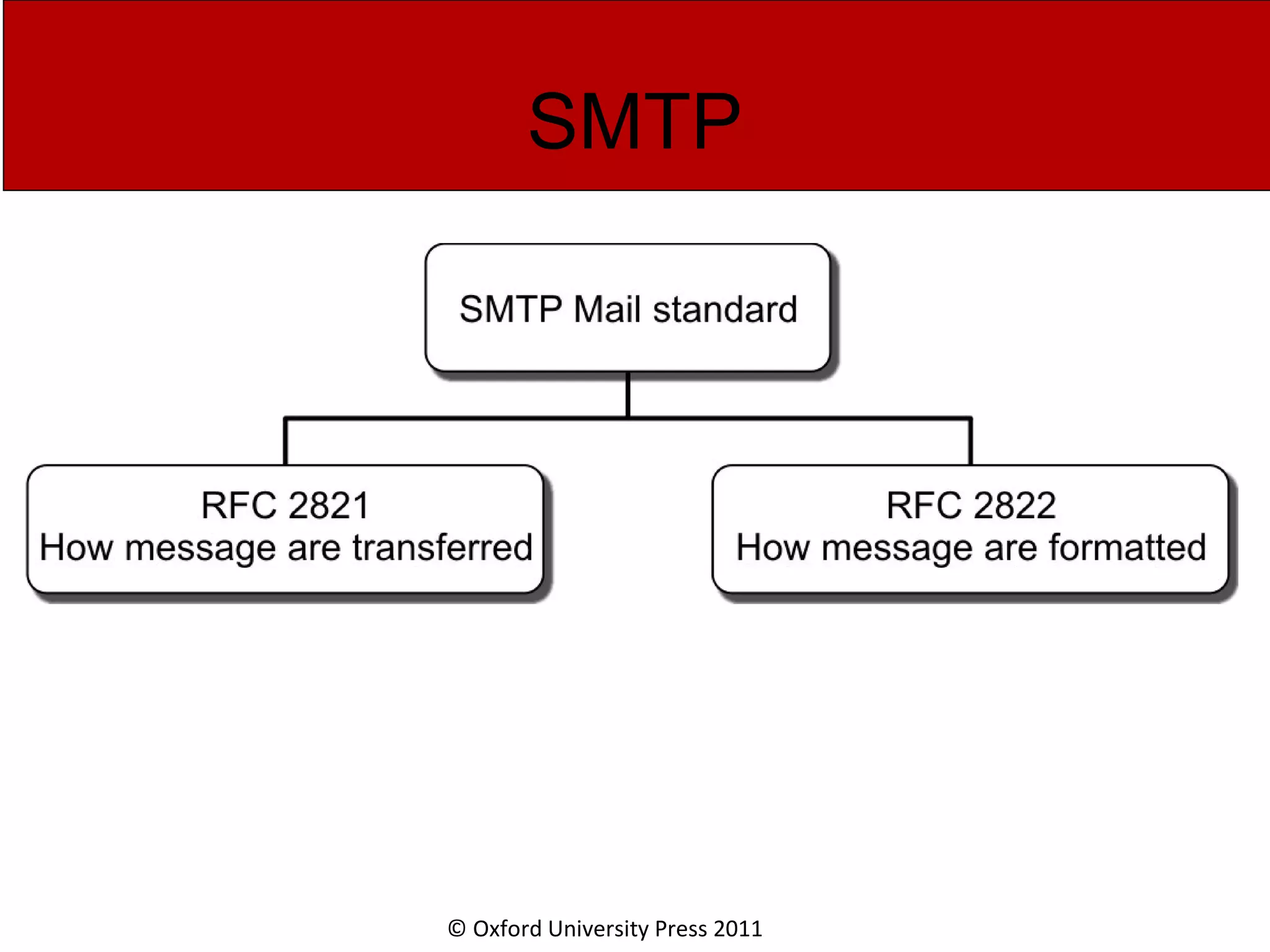
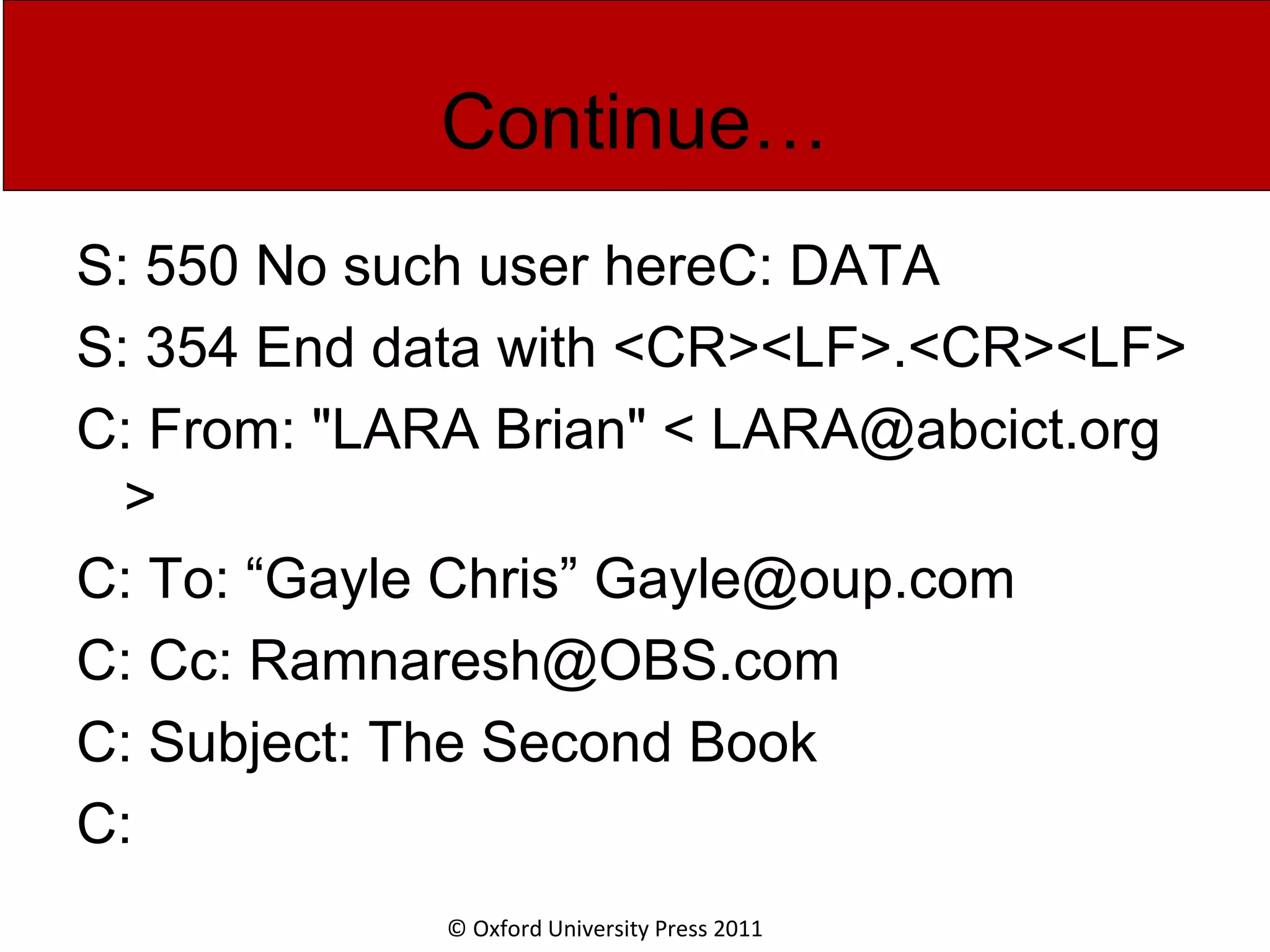
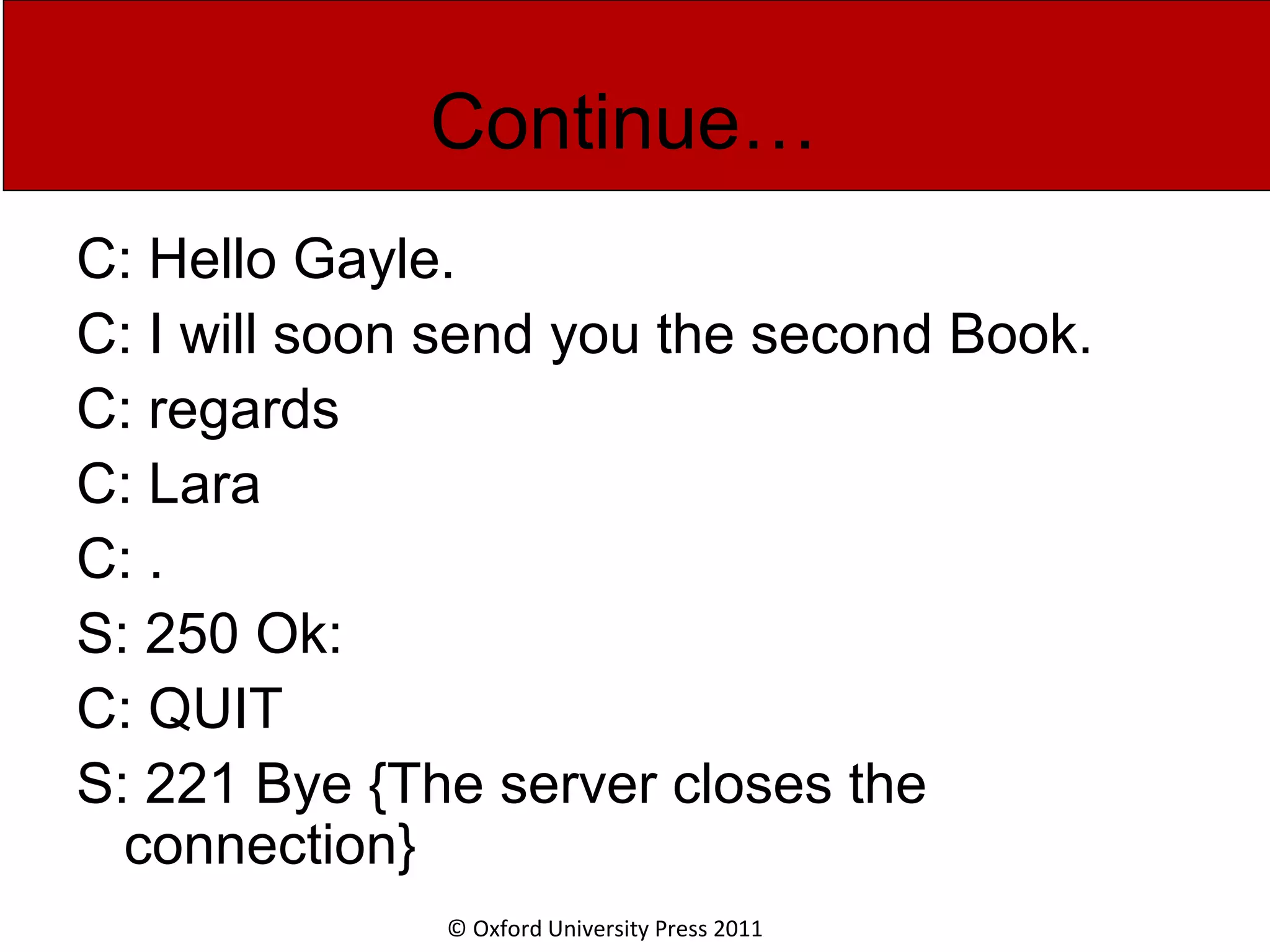
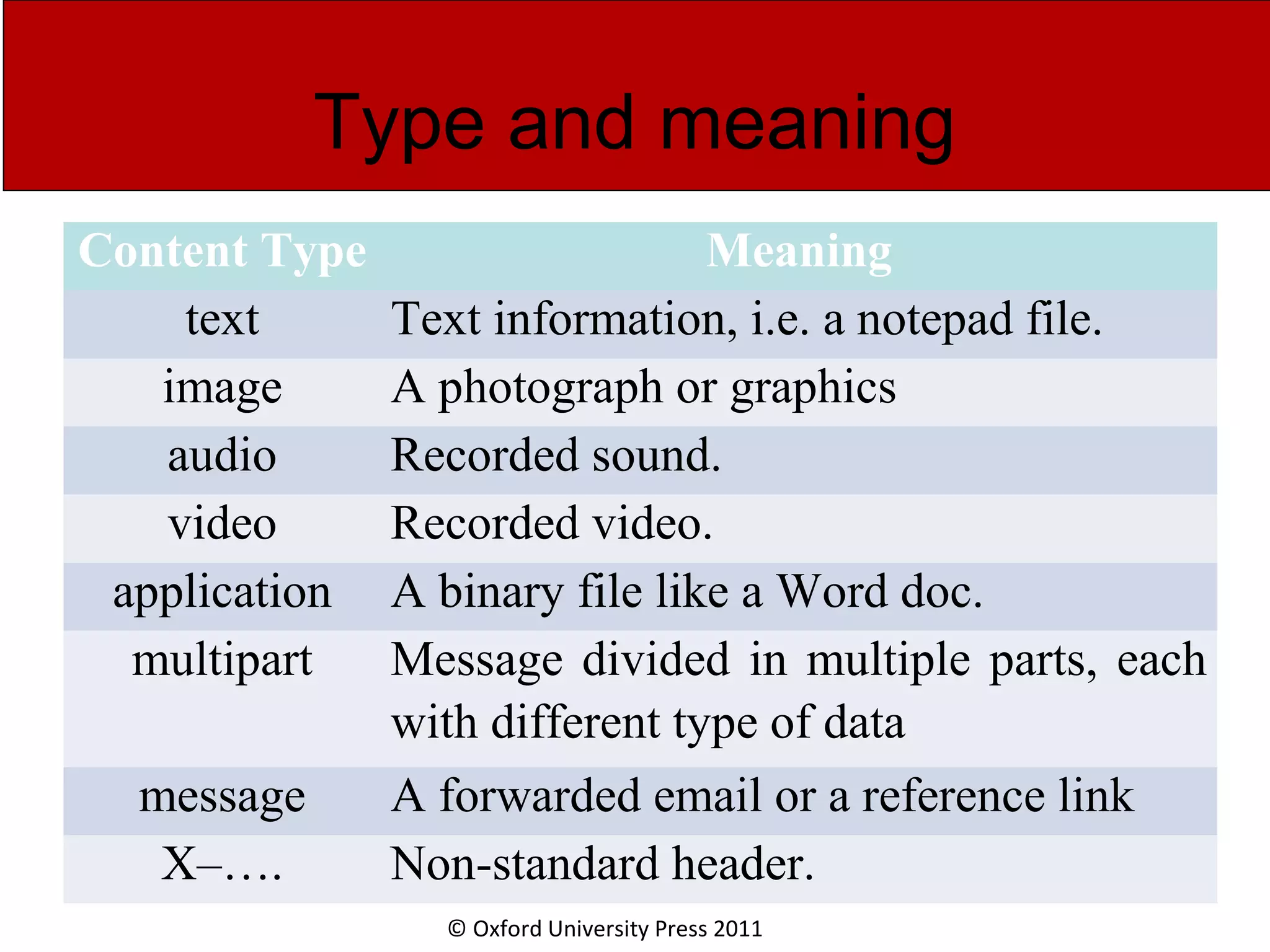
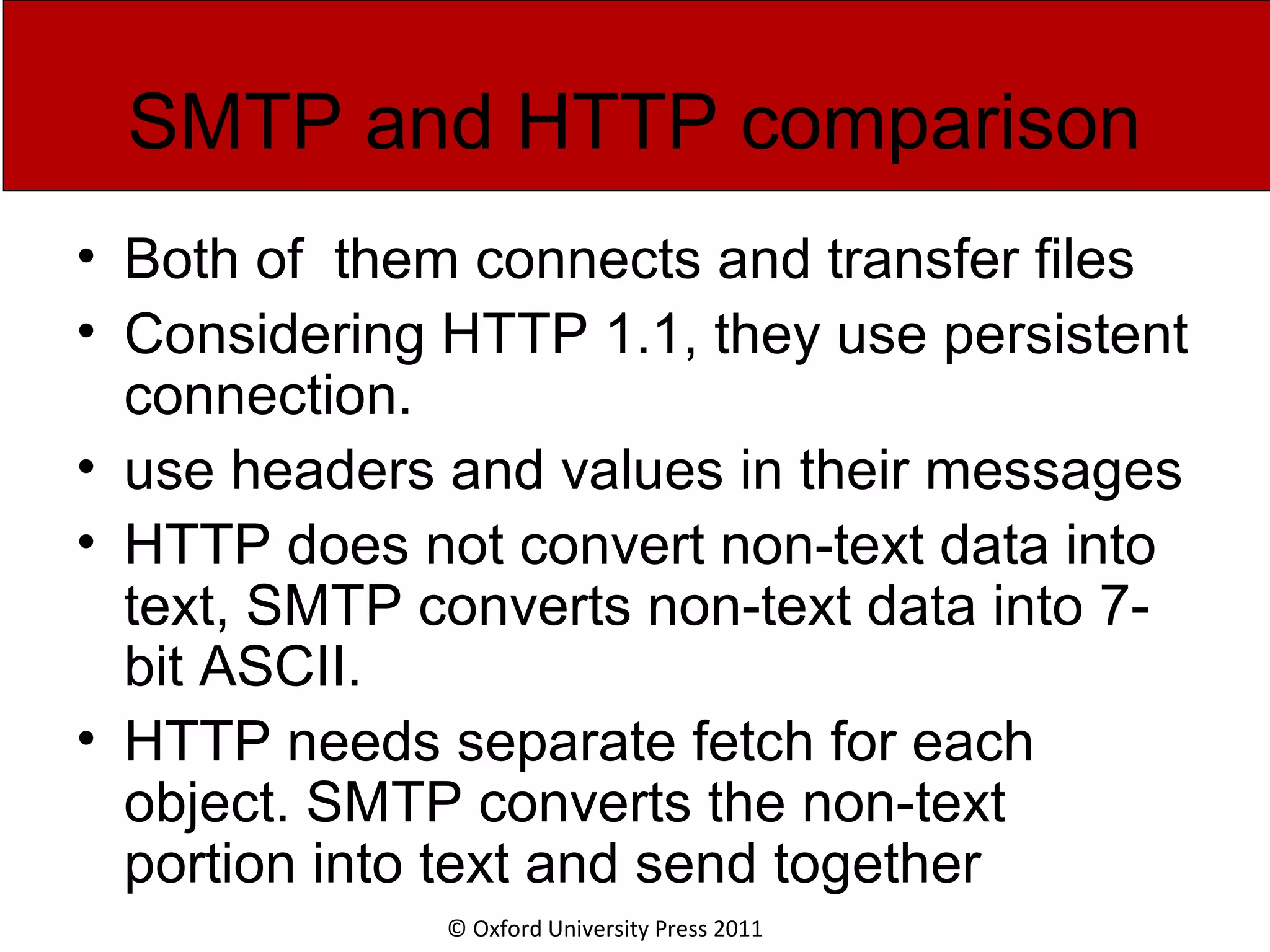
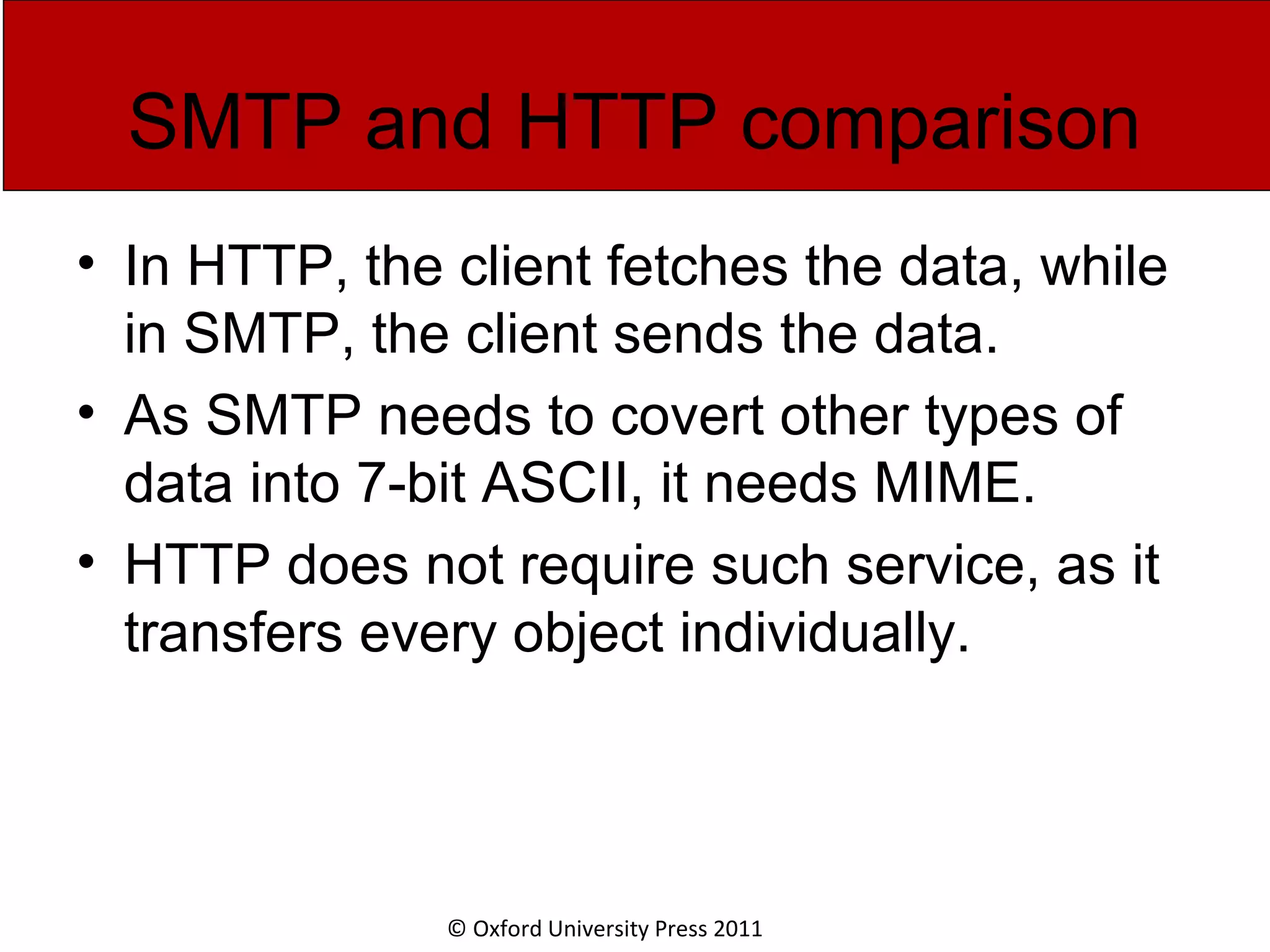
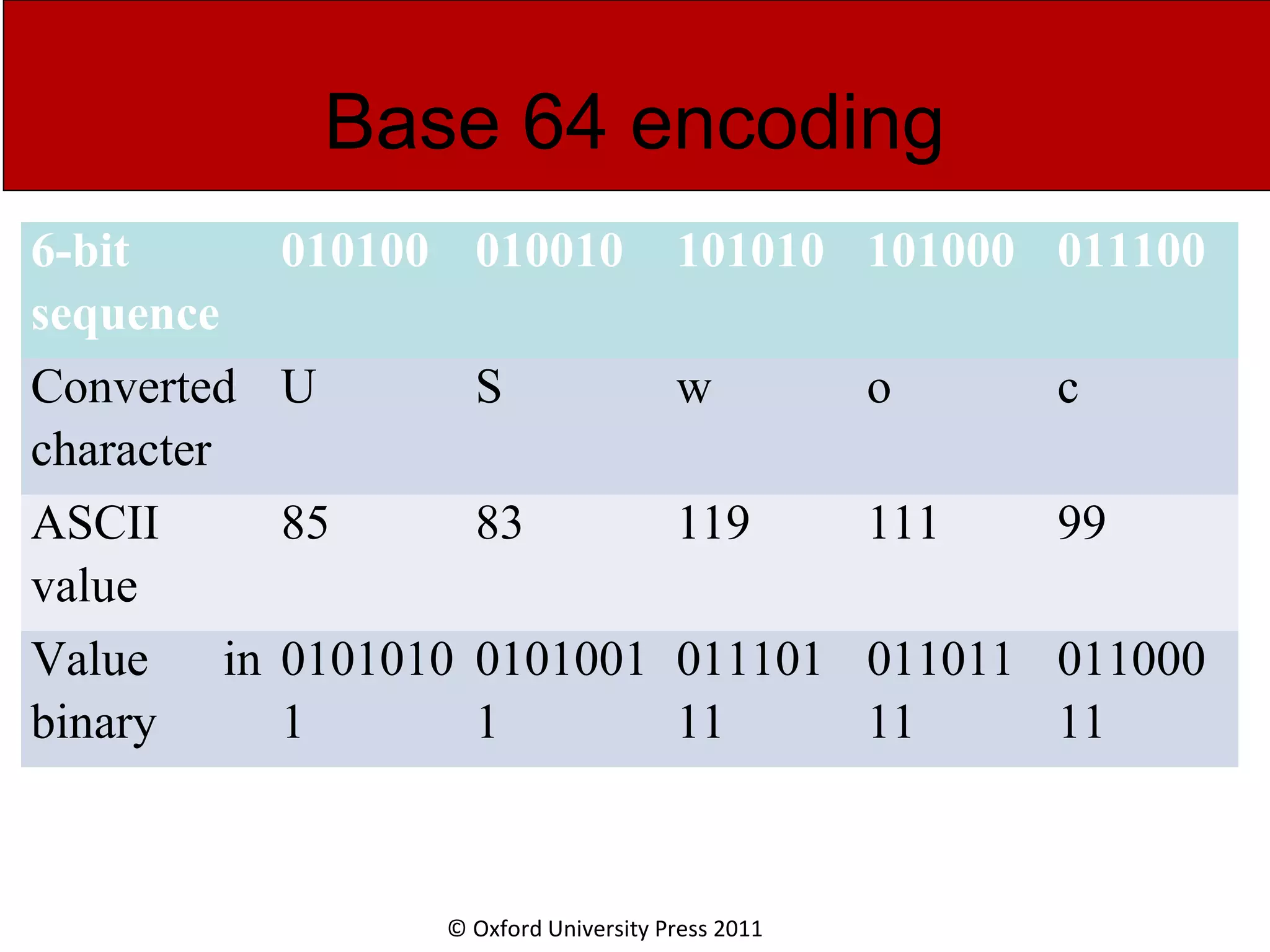
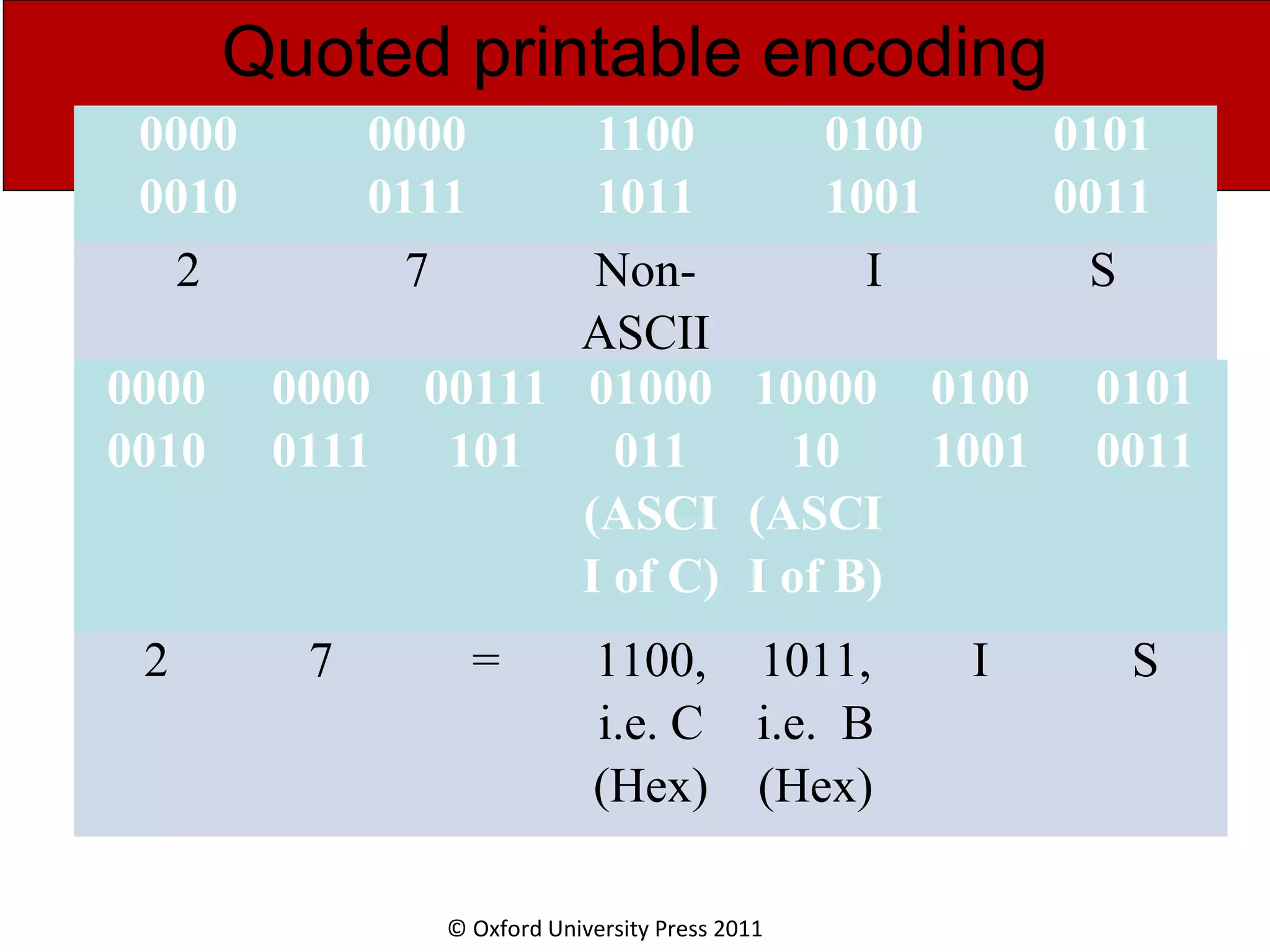
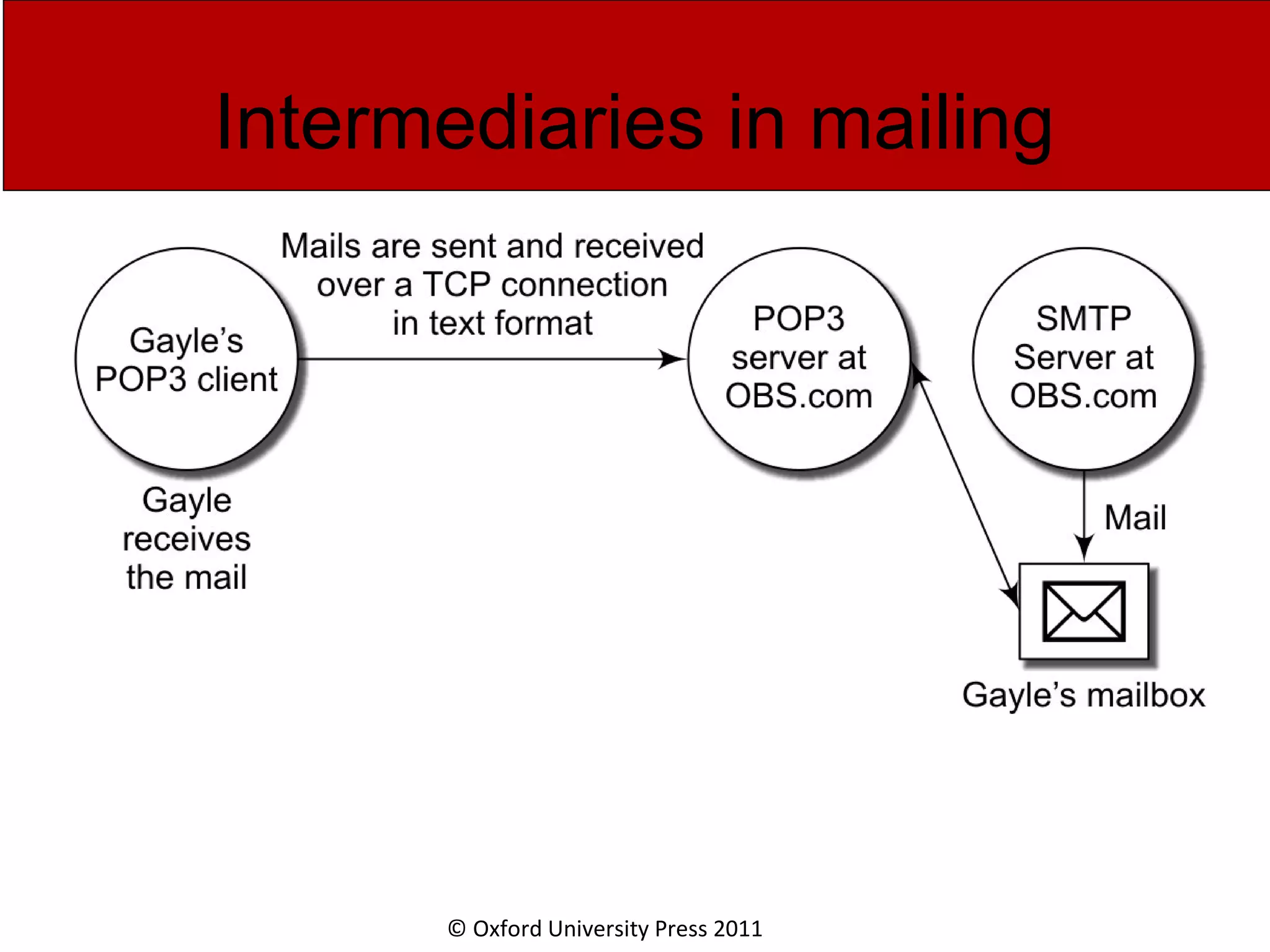
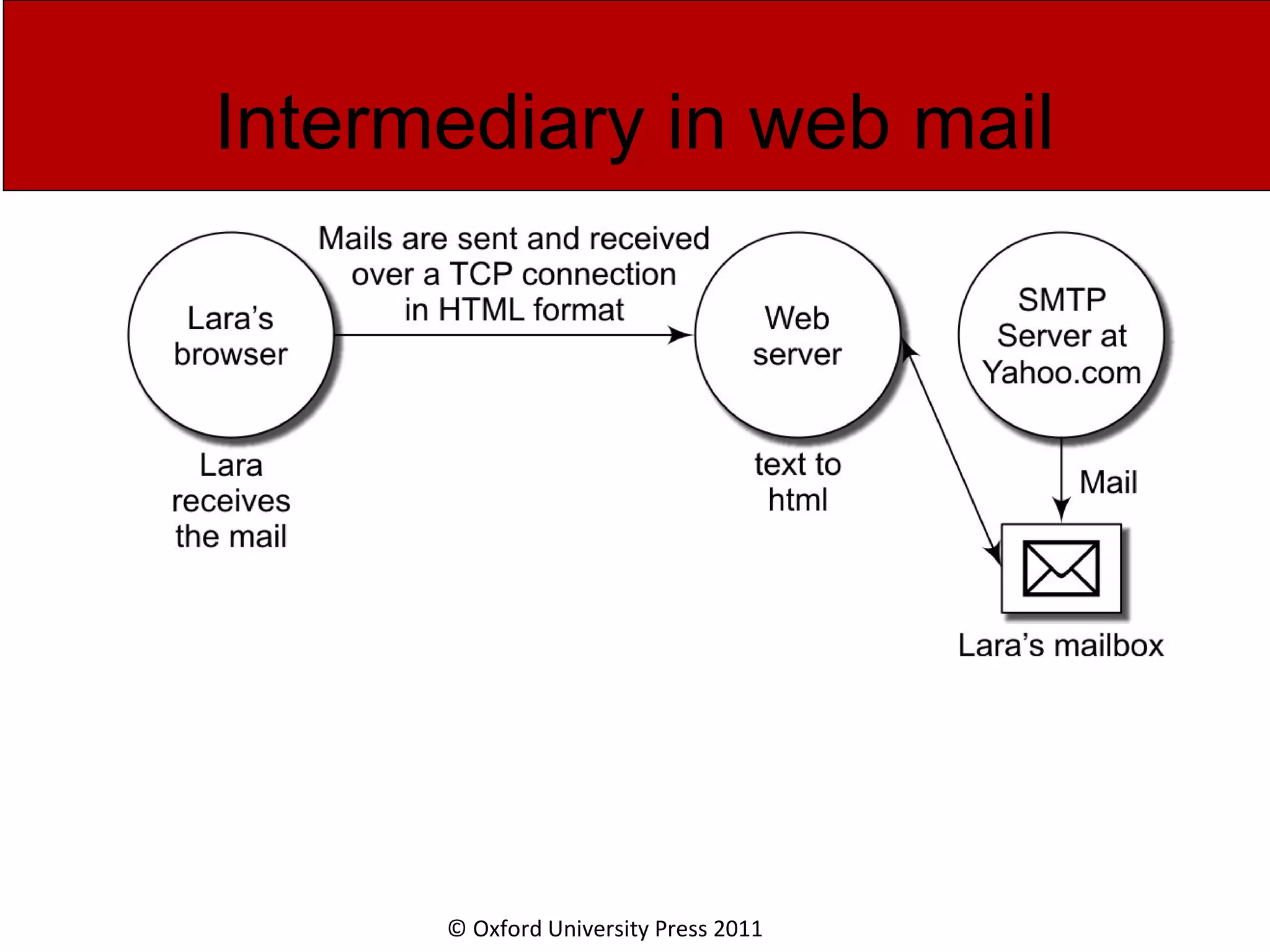
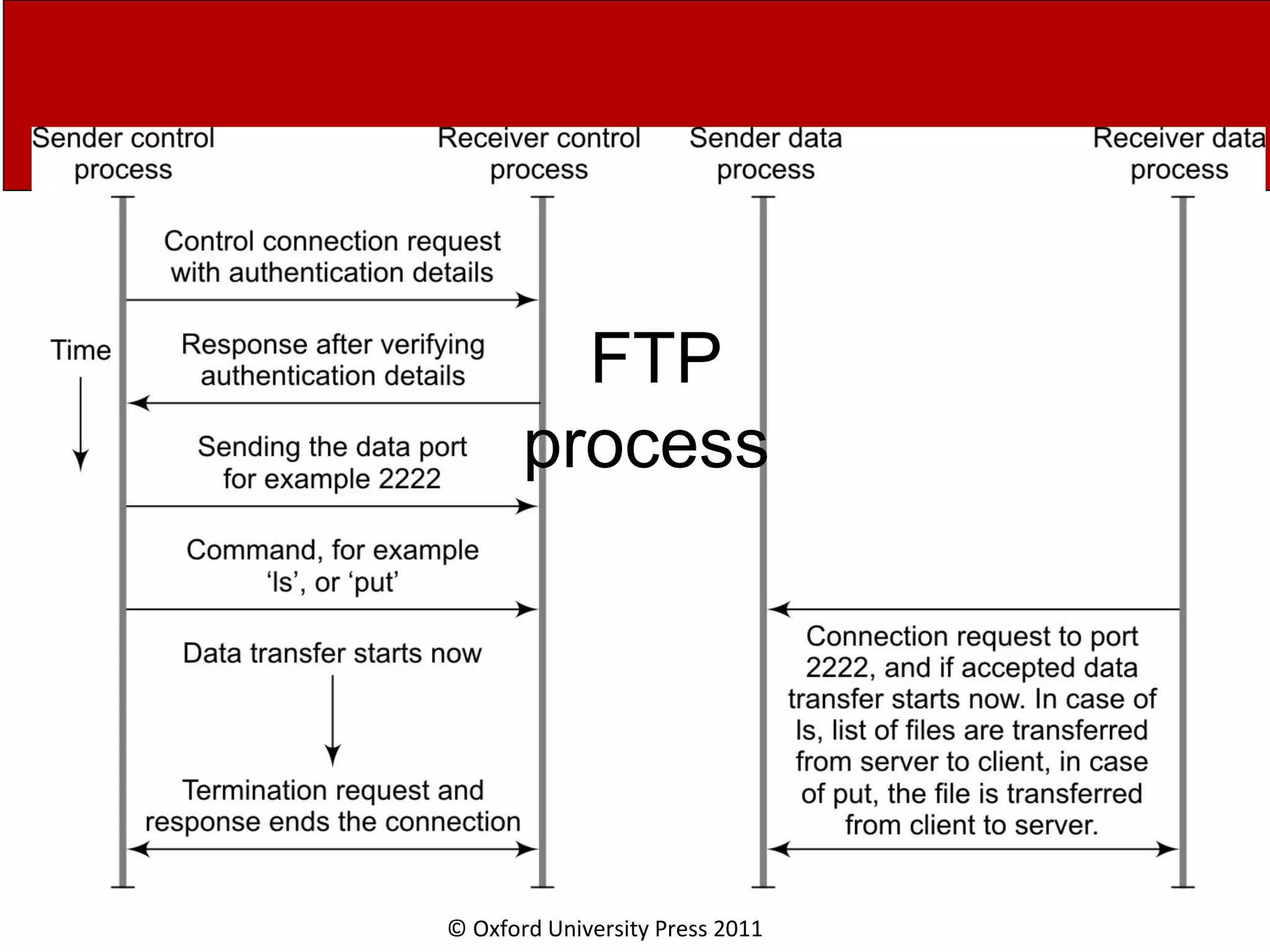
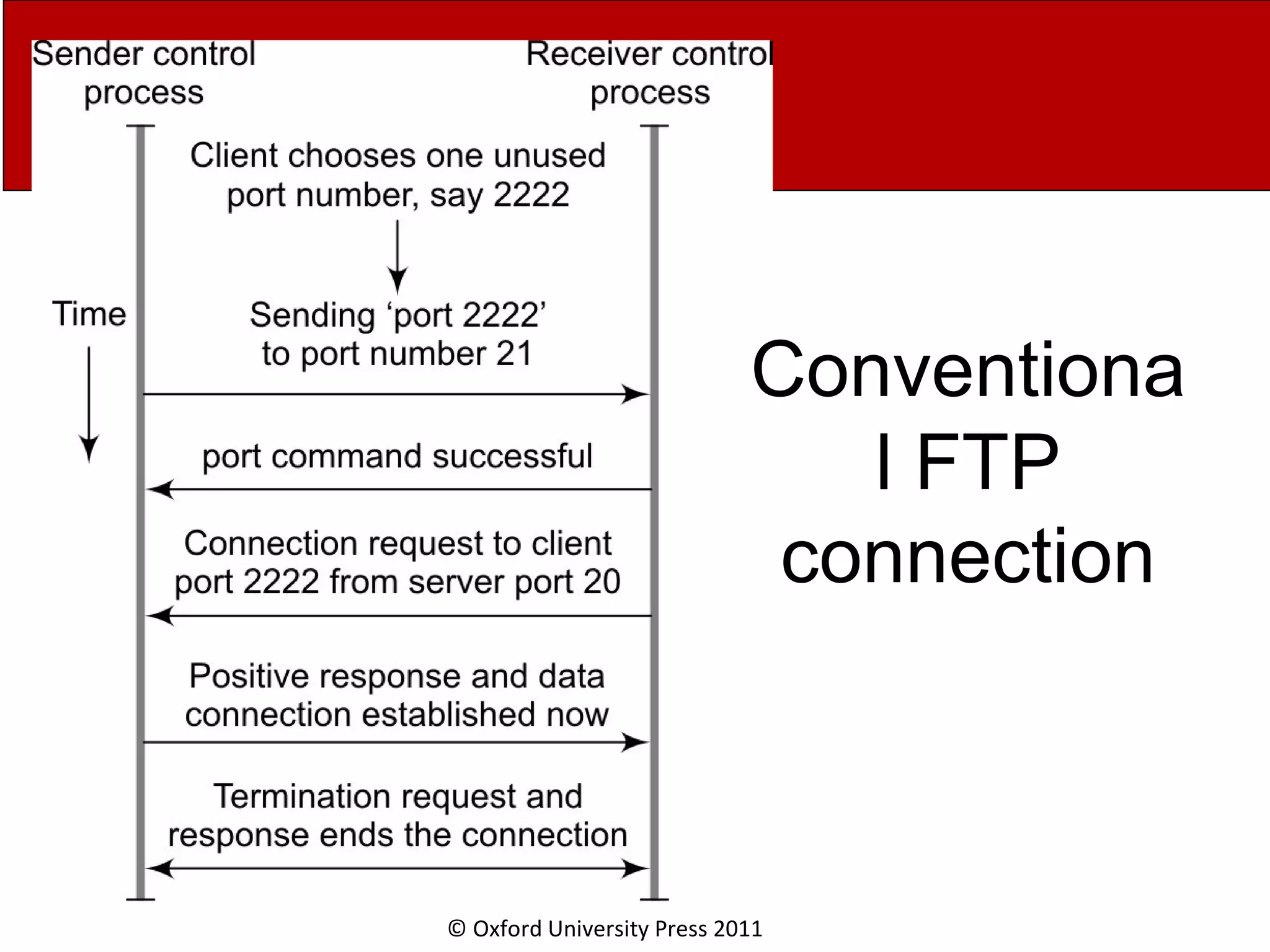
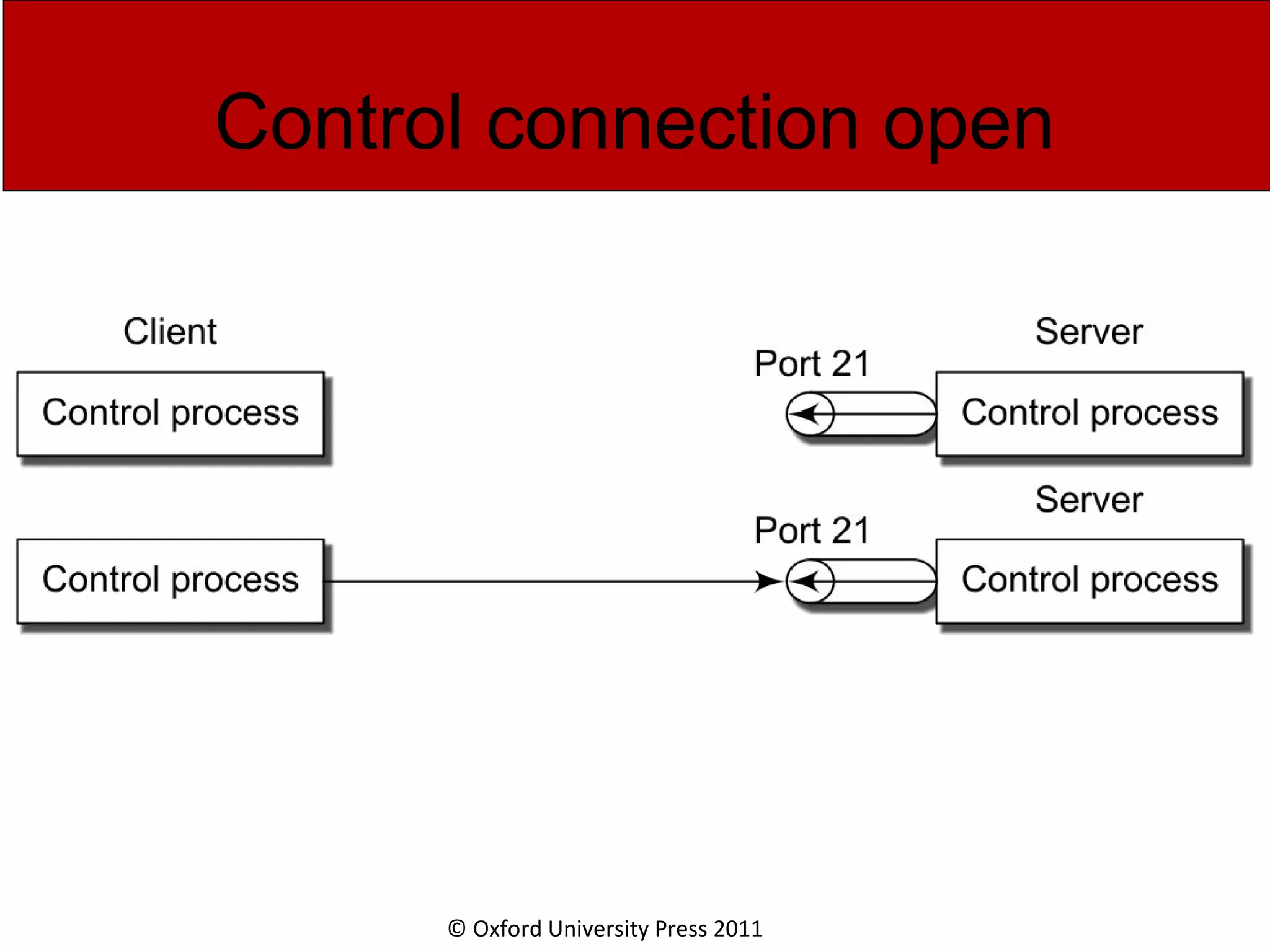
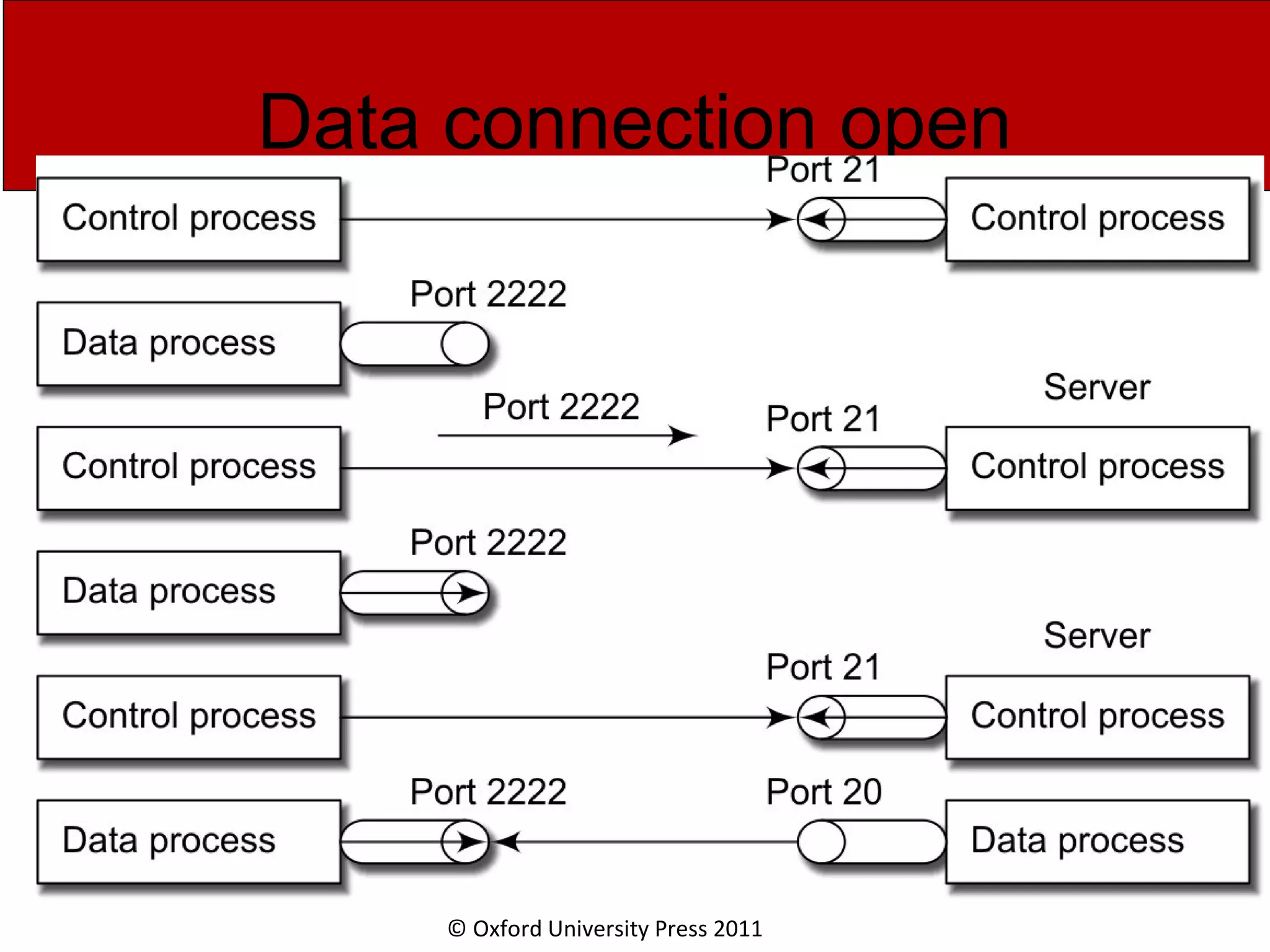
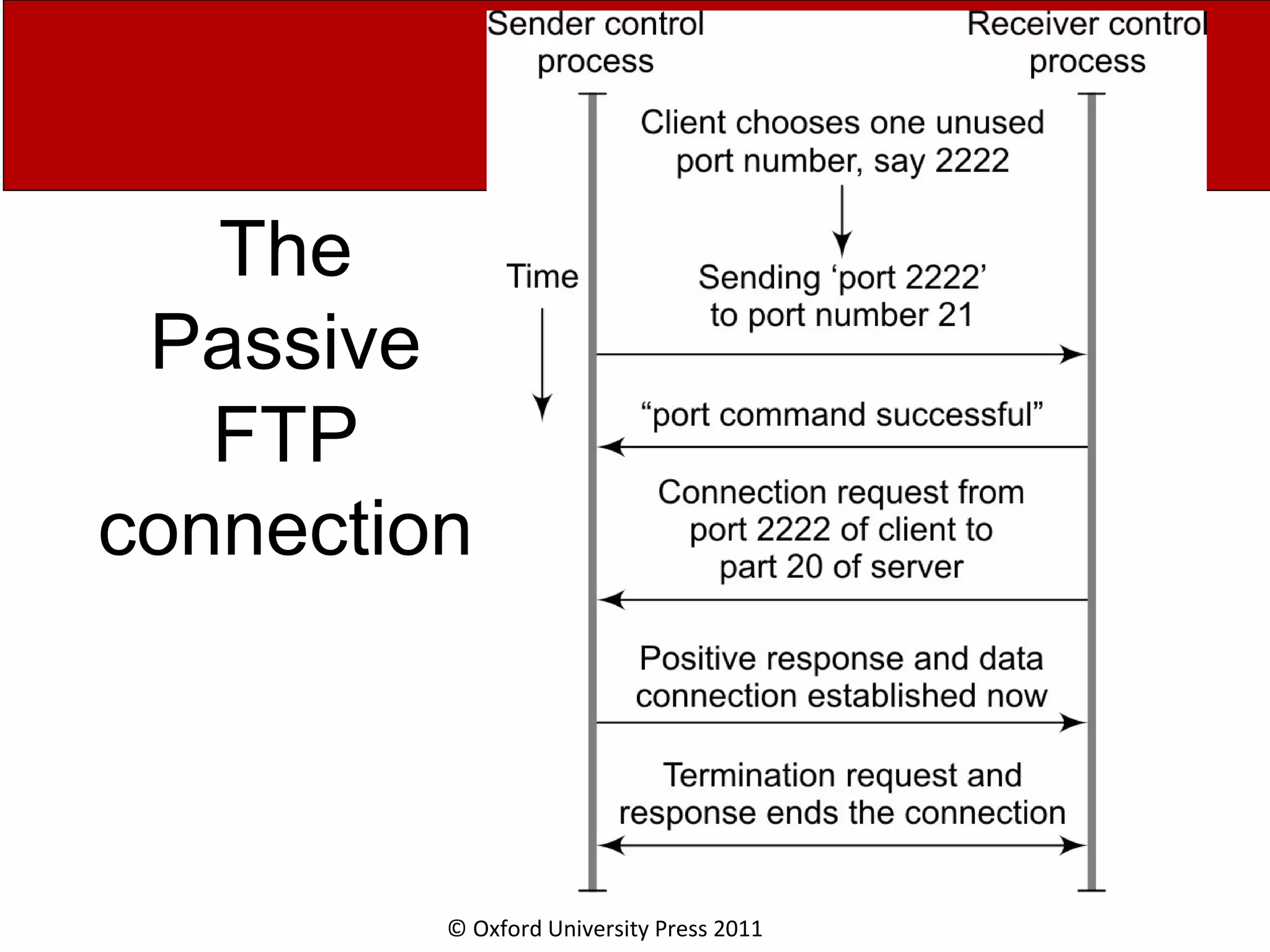
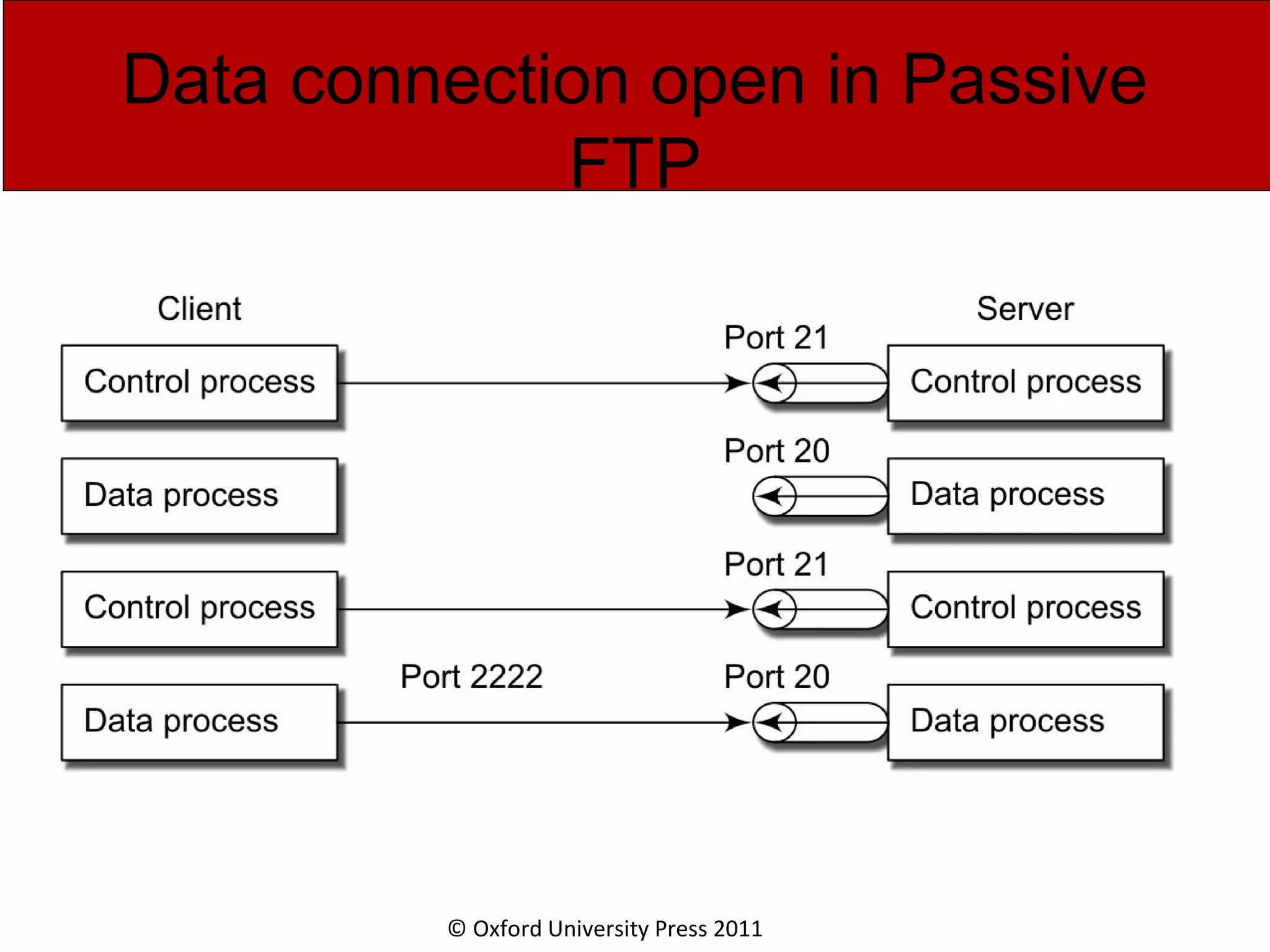
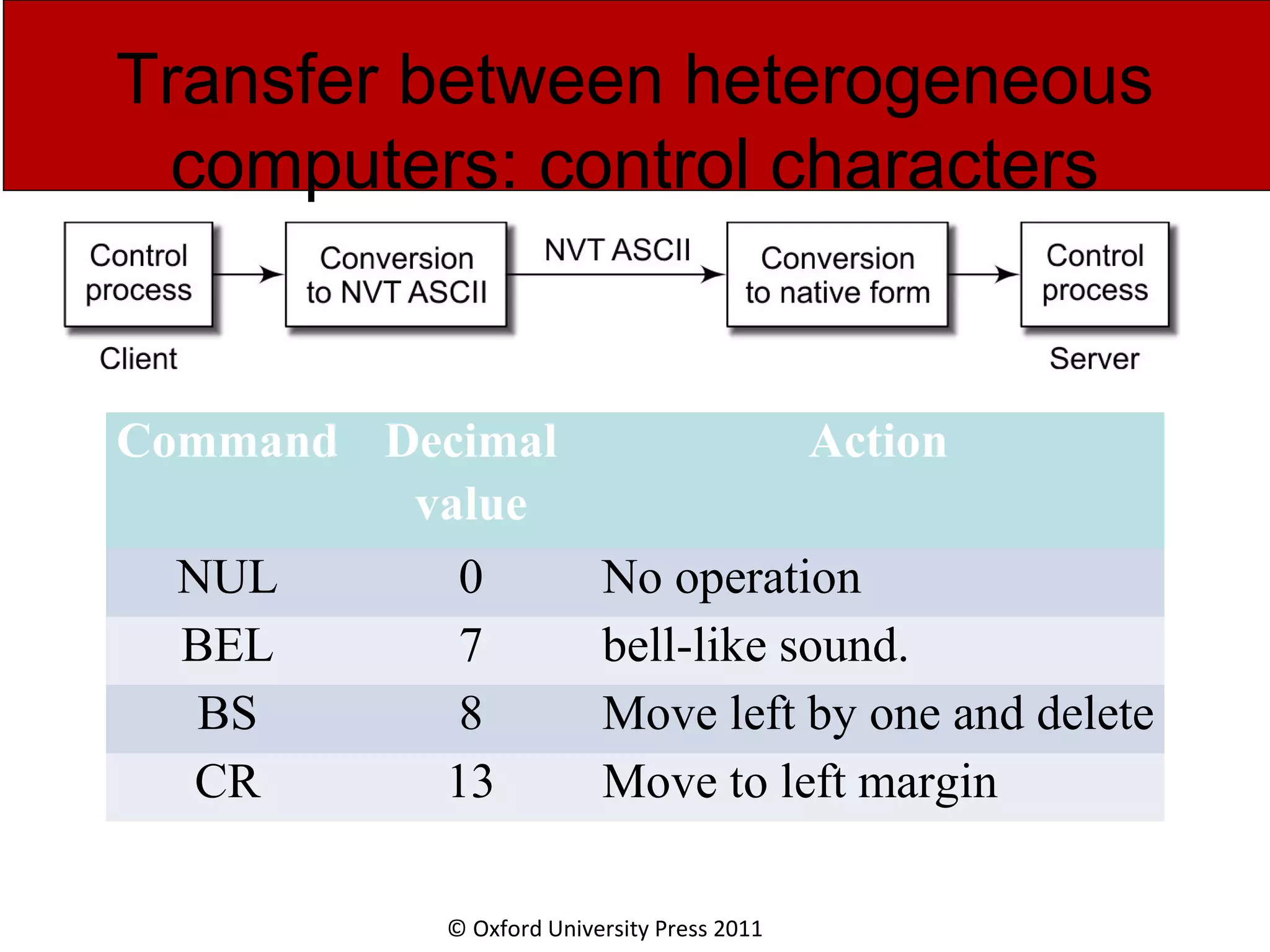
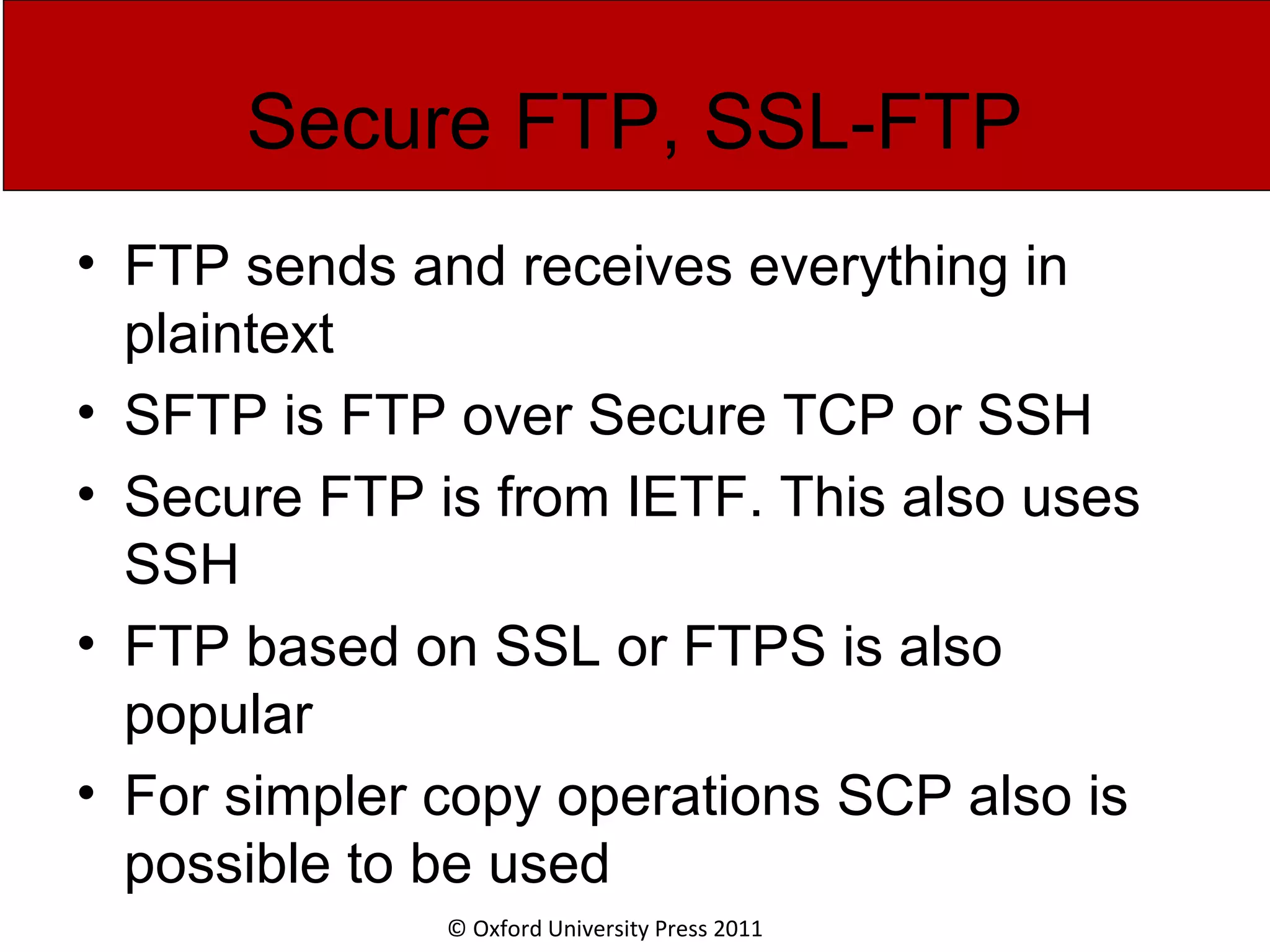
The document discusses the application layer in computer networks and describes how it interacts with users through applications and uses TCP or UDP to transmit data, covering topics like the domain name system, HTTP requests and responses, email sending and receiving processes, and how proxies and cookies work. It also explains concepts like persistent connections, conditional downloads, and dynamic web pages using client-side and server-side processing.