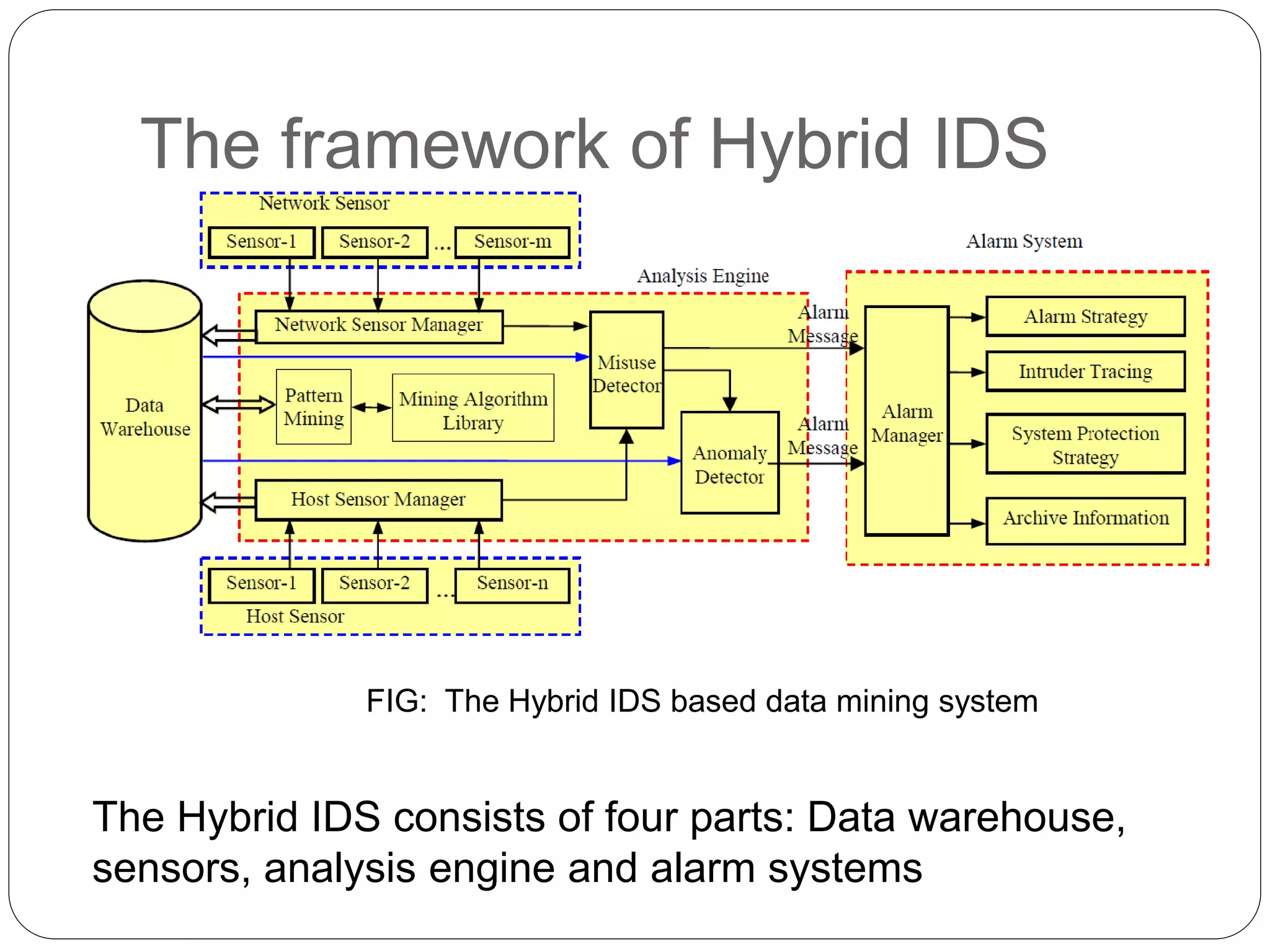
This document discusses using data mining techniques to improve intrusion detection systems (IDS). It begins by introducing computer network risks and limitations of existing IDS approaches. It then discusses using data mining algorithms like ID3, k-means clustering, and Apriori pattern mining within a hybrid IDS framework. The framework includes sensors to collect host and network data, a data warehouse for storage, and an analysis engine using misuse detection, anomaly detection and data mining algorithms to detect intrusions. It concludes that data mining allows IDS to detect both known and unknown attacks more efficiently.







![References [1] Wenke Lee, S. J. Stolfo, “A data mining Framework for Building Intrusion detection models” IEEE 1999. [2] He Min, Luo Laijun “Search of network real-time intrusion detection system base on data mining” in proceedings of the 2011 IEEE Internatioanl conference of uncertainty reasoning and knowledge engineering. [3] Sanjay Kumar Sharma, Pankaj Pandey, Susheel Kumar Tiwari & Mahendra singh Sisodia, “An improved network intrusion detection technology based on k-means clustering via Naiive bayes classifiaction” in proceedings of IEEE-International Conference On Advances In Engineering, Science And Management (ICAESM -2012) March 30, 31, 2012 [4] Mrutyunjaya Panda, Manas Ranjan Patra, “A comparative study of data mining algorithms for network intrusion detection” in proceedings of First International Conference on Emerging Trends in Engineering and Technology 2008 IEEE [5] Yan Yu “A Novel intrusion detection approaches based on data mining” IEEE 2010 [6] Dyuanyang Zhao, Zhilin Feng, Qingxiang Xu, “Analysis and design for Intrusion detection system based on data mining” in proceedings of 2010 IEEE second international workshop on education technology and computer science [7] Ming Xue, Changjun Zhu “Applied research on data mining algorithm in network intrusion detection” in proceedings of 2009 IEEE international joint conference on artificial intellengence [8] LIU Dihua, WANG Hongzhi , WANG Xiumei “Data mining for intrusion detection” IEEE 2001](https://image.slidesharecdn.com/analysisanddesignforintrusiondetectionsystemon-151002065916-lva1-app6892/75/Analysis-and-Design-for-Intrusion-Detection-System-Based-on-Data-Mining-11-2048.jpg)
