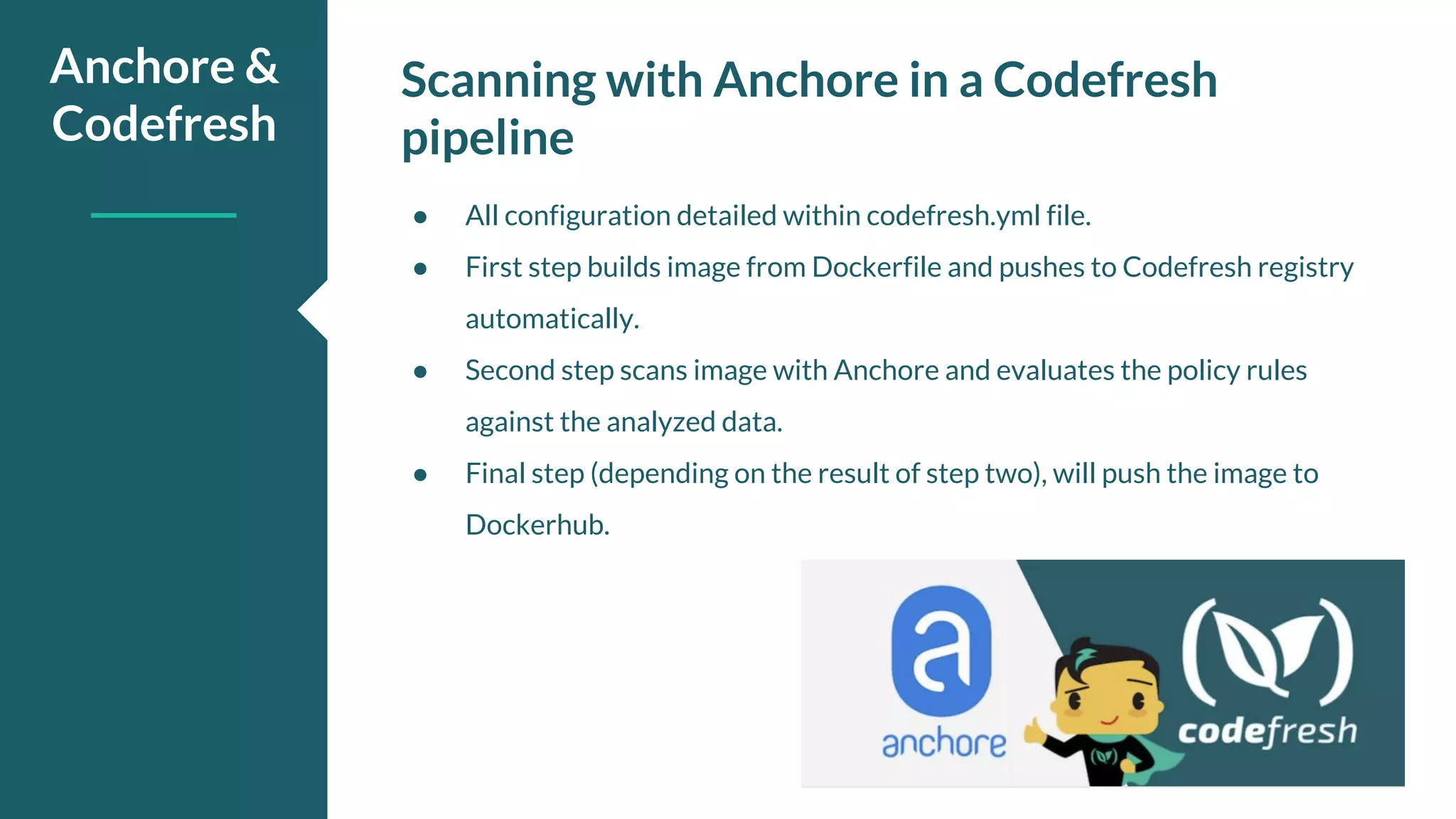
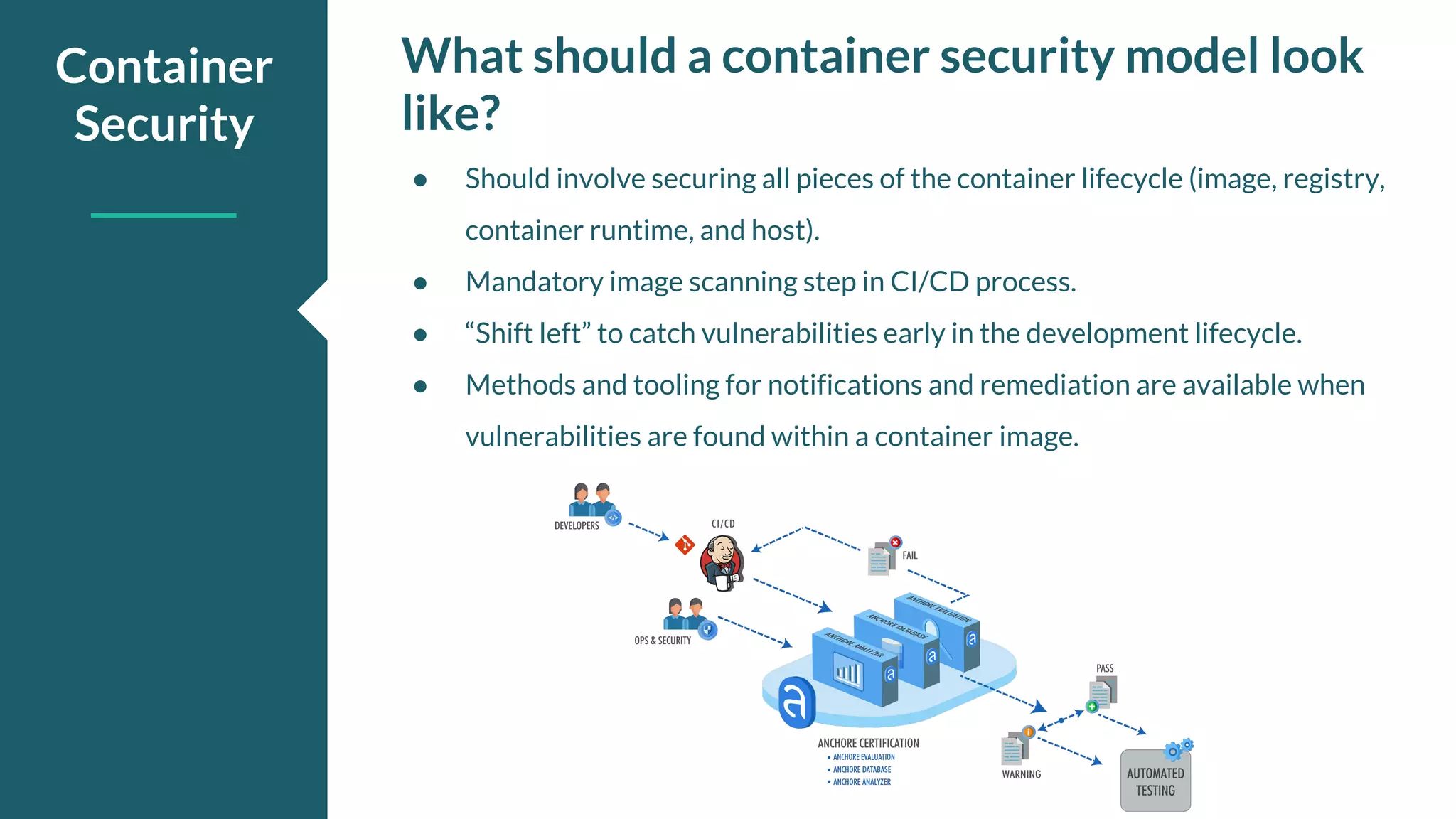
The document discusses the importance of scanning container images within CI/CD pipelines to enhance security by identifying vulnerabilities and configuration issues early in the development lifecycle. It outlines how Anchore tools analyze container images, generate manifests, and enforce user-defined policies through integration with Codefresh. Key takeaways include the necessity of mandatory image scanning, the creation of policies to govern image security, and the utilization of Anchore's capabilities in CI/CD processes.


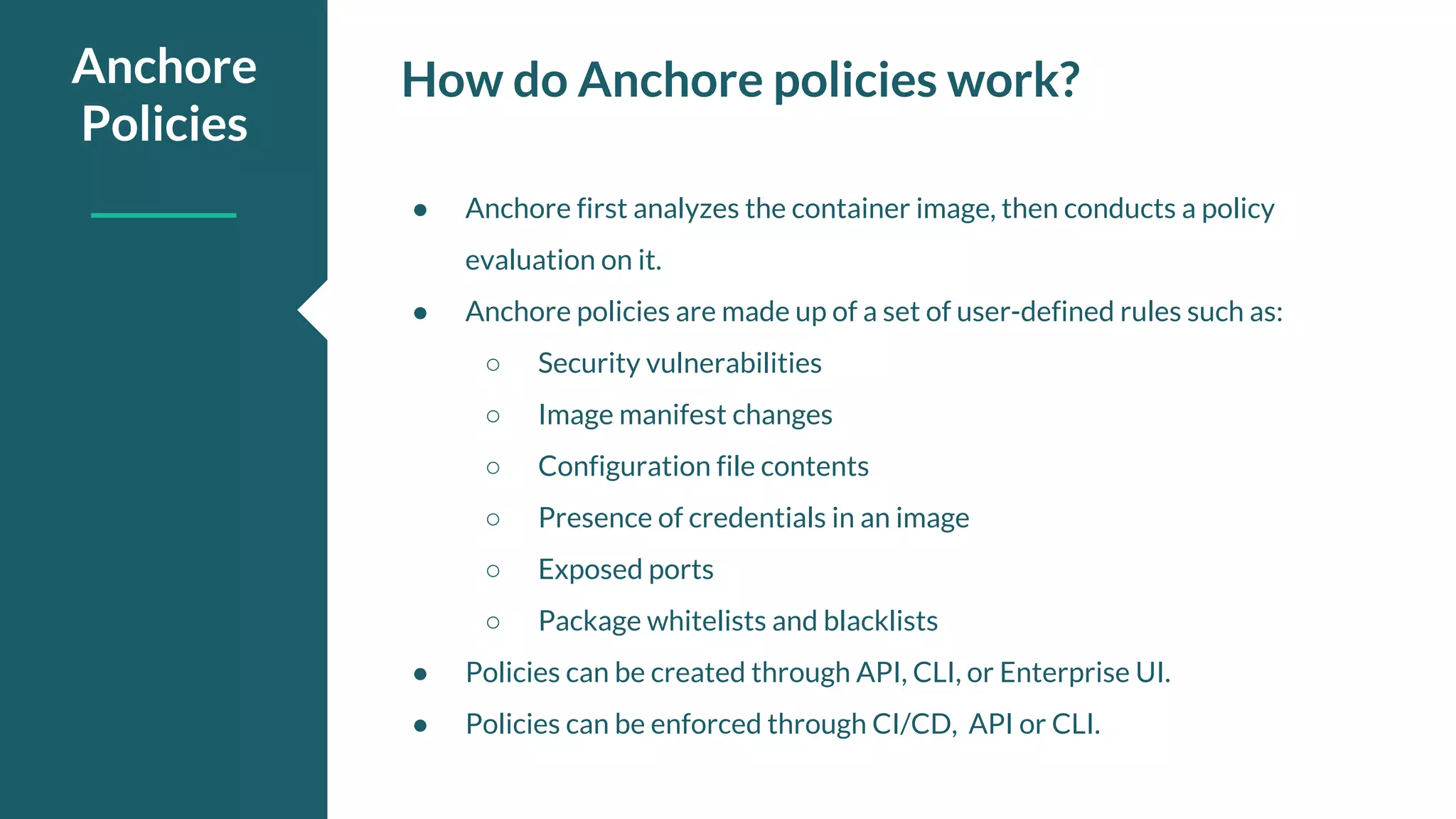
![{ “id”: “48e6f7d6-1765-11e8-b5f9-8b6f228548b6”, “name”: “Example Policy”, “rules”: [ { “action”: “STOP”, “gate”: “dockerfile”, “id”:“ce7b8000-829b-4c27-8122-69cd59018400”, “params”: [ { “name”: “ports”, “value”: “22” } ] } ] Example Policy](https://image.slidesharecdn.com/anchore-codefreshwebinar-181221202607/75/Adding-Container-Image-Scanning-to-Your-Codefresh-Pipelines-with-Anchore-8-2048.jpg)