The document discusses a proposed hybrid intrusion detection system (IDS) that combines the min-min algorithm and neural networks to enhance network security. It outlines two types of intrusion detection—misuse-based and anomaly-based—and emphasizes the need for efficient resource utilization while improving security. The research also includes a comparative analysis between signature-based and anomaly-based IDS technologies, highlighting the novel algorithm developed for better detection of network attacks.
![A Hybrid Intrusion Detection System For Network Security: A New Proposed Min – Min Algorithm Parveen Sadotra Research Scholar, Department of Computer Science Career Point University, Kota, Rajasthan, India Dr. Chandrakant Sharma Professor, Department of Computer Science Career Point University, Kota, Rajasthan, India Abstract— When talk about intrusion, then it is pre- assume that the intrusion is happened or it is stopped by the intrusion detection system. This is all done through the process of collection of network traffic information at certain point of networks in the digital system. In this way the IDS perform their job to secure the network. There are two types of Intrusion Detection: First is Misuse based detection and second one is Anomaly based detection. The detection which uses data set of known predefined set of attacks is called Misuse - Based IDSs and Anomaly based IDSs are capable of detecting new attacks which are not known to previous data set of attacks and is based on some new heuristic methods. In our hybrid IDS for computer network security we use Min-Min algorithm with neural network in hybrid method for improving performance of higher level of IDS in network. Data releasing is the problem for privacy point of view, so we first evaluate training for error from neural network regression state, after that we can get outer sniffer by using Min length from source, so that we hybridized as with Min – Min in neural network in hybrid system which we proposed in our research paper Keywords— intrusion detection, network security, anomaly, Min-Min algorithm, Neural network. I. INTRODUCTION An Intrusion Detection System (IDS) is a dynamic monitoring system used to identify, examine and observe violated activities. It discovers breach and illegal access to confidentiality, unavailability, authorization, authentication, integrity and network resources [4]. The related works shows that there exist a trade-off between better security mechanism and efficient resource utilization of sensor networks. If we increase network security we have to compromise on efficient resource consumption and vice versa. As a result, better security mechanisms is required that uses network resources efficiently. In order to tackle with this issue, we have proposed a Mobile Agent Based Hierarchical Intrusion Detection System (MABHIDS). Our proposed scheme uses minimum network resources by providing enhanced level of security. Energy Prediction Approach alone is not suitable for the WSN, so H-HIDS, which is suitable for large and sustainable WSN is combined, the two approaches along with the Min- Min with neural network to make it suitable for a large WSN. Therefore, the new proposed IDS will offer a wide range of flexibility for its application in any type of network security. This paper proposes an anomaly based IDS (Intrusion Detection System) AIDS. AIDS provides detection of un- trusted users; false requests that may lead to spoofing, XSS or DOS attack and many such possible attacks. Aids can be helpful in detecting such attacks and maintaining the QoS of network security. We also perform the various parameters to check its reliability, throughput, failure probability and wait time. This paper also analyses the problem of intrusion detection in a Uniform, and unified distributed network security by characterizing the detection probability with respect to the application requirements and the network parameters under both single sensing detection and multiple sensing detection model. II. BACKGROUND OF THE RESEARCH The intrusion detection market began to gain in popularity and truly generate revenues around 1997. In that year, the security market leader, ISS, developed a network intrusion detection system called “Real Secure”. A year later, Cisco recognized the importance of network intrusion detection and purchased the Wheel Group, attaining a security solution they could provide to their customers. Similarly, the first visible host- based intrusion detection company, Centrax Corporation, emerged because of a merger of the development staff from Haystack Labs and the departure of the CMDS team from SAIC. From there, the commercial IDS world expanded its market-base and a roller coaster ride of start-up companies, mergers, and acquisitions ensued. Martin Roesch, in the year 1998 launched a lightweight open source Network IDS named “SNORT” [3], which has since then gained much popularity. In year, 1999 Okena Systems worked out the first Intrusion Prevention System (IPS) under the name “Storm Watch”. IPS is the systems, which not only detect the intrusions but also are able to react on alarming situation. These systems can co- operate with firewall without any intermediary applications. Signature/pattern based Detection International Journal of Computer Science and Information Security (IJCSIS), Vol. 15, No. 9, September 2017 135 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/16paper31081736ijcsiscamerareadypp-180206144423/75/A-Hybrid-Intrusion-Detection-System-for-Network-Security-A-New-Proposed-Min-Min-Algorithm-1-2048.jpg)
![In this technique, the sensors, which are, placed in different LAN segments filter and analysis network packets in real time and compares them against a database of known attack signatures. Attack signatures are known methods that intruders have employed in the past to penetrate a network. If the packet contents match an attack signature, the IDS can take appropriate countermeasure steps as enabled by the network security administrator. These countermeasures can take the form of a wide range of responses. They can include notifications through simple network management protocol (SNMP) traps or issuance of alerts to an administrator’s email or phone, shutting down the connection or shutting down the system under threat etc. An advantage of misuse detection IDS is that it is not only useful to detect intrusions, but it will also detect intrusion attempts; a partial signature may indicate an intrusion attempt. Furthermore, the misuse detection IDS could detect port scans and other events that possibly precede an intrusion. Unauthorized Access based Detection In unauthorized access detection, the IDS detect attempts of any access violations. It maintains an access control list (ACL) where access control policies for different users based on IP addresses are stored. User requests are verified against the ACL to check any violations. Behavioral Anomaly (Heuristic based) Detection: In behavioral anomaly detection method, the IDS are trained to learn the normal behavioral pattern of traffic flow in the network over an appropriate period. Then it sets a baseline or normal state of the network’s traffic, protocols used and typical packet sizes and other relevant parameters of network traffic. The anomaly detector monitors different network segments to compare their state to the normal baselines and look for significant deviations. Protocol Anomaly Detection: With this technique, anomaly detector alerts administrator of traffic that does not conform to known protocol standards. As the protocol anomaly, detection analyzes network traffic for deviation from standards rather than searching for known exploits there is a potential for protocol anomaly to serve as an early detector for undocumented exploits. Mining Techniques In Network Security To Enhance Intrusion Detection Systems The mining techniques in network security to enhancements in this research concentrate on two main phases of IDS, which are feature selection and normalization. Feature selection enhancement (or the first enhancement) is enhanced by an improved method that filters the most valuable features for IDS. On the other hand, the normalization of nominal features (or the second enhancement) solved the problem of different feature types, data dominance, and impact on classification. The latter is modified to be hybrid approach. These enhancements boost significantly the classifier performance. Statistical Anomaly Based Intrusion Detection System (SABIDS) Statistical modelling is among the earliest methods used for detecting intrusions in electronic information systems. Statistical based anomaly detection techniques use statistical properties and statistical tests to determine whether “Observed behavior” deviate significantly from the “expected behavior” [7]. Statistical based anomaly detection techniques use statistical properties (e.g., mean and variance) of normal activities to build a statistical based normal profile and employ statistical tests to determine whether observed activities deviate significantly from the normal profile. The IDS goes on assigning a score to an anomalous activity. As soon as this score becomes greater certain threshold, it will generate an alarm. SABIDS is a two-step process: first, it establishes behaviour profiles for the normal activities and current activities. Then these profiles are matched based on various techniques to detect any kind of deviation from the normal behavior. SABIDS can further be classified into following categories a. Operational Model or Threshold Metric b. Markov Process Model or Marker Model c. Statistical Moments or Mean and Standard Deviation Model d. Multivariate Model e. Time Series Model Knowledge Based Detection Technique Knowledge based detection Technique can be used for both signature based IDS as well as anomaly based IDS. It accumulates the knowledge about specific attacks and system vulnerabilities. It uses this knowledge to exploit the attacks and vulnerabilities to generate the alarm. Any other event that is not recognized as an attack is accepted. Therefore, the accuracy of knowledge based intrusion detection systems is considered good. However, their completeness requires that their knowledge of attacks be updated regularly [29]. Machine Learning Based Detection Technique Machine learning can be defined as the ability of a program and/or a system to learn and improve their performance on a certain task or group of tasks over time. Machine learning techniques focus on building a system that improves its performance based on previous results i.e. machine learning techniques have the ability to change their execution strategy based on newly acquired information [5]. This feature could make it desirable to use in all situations, but the major drawback is their resource expensive nature. In many cases, International Journal of Computer Science and Information Security (IJCSIS), Vol. 15, No. 9, September 2017 136 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/16paper31081736ijcsiscamerareadypp-180206144423/75/A-Hybrid-Intrusion-Detection-System-for-Network-Security-A-New-Proposed-Min-Min-Algorithm-2-2048.jpg)

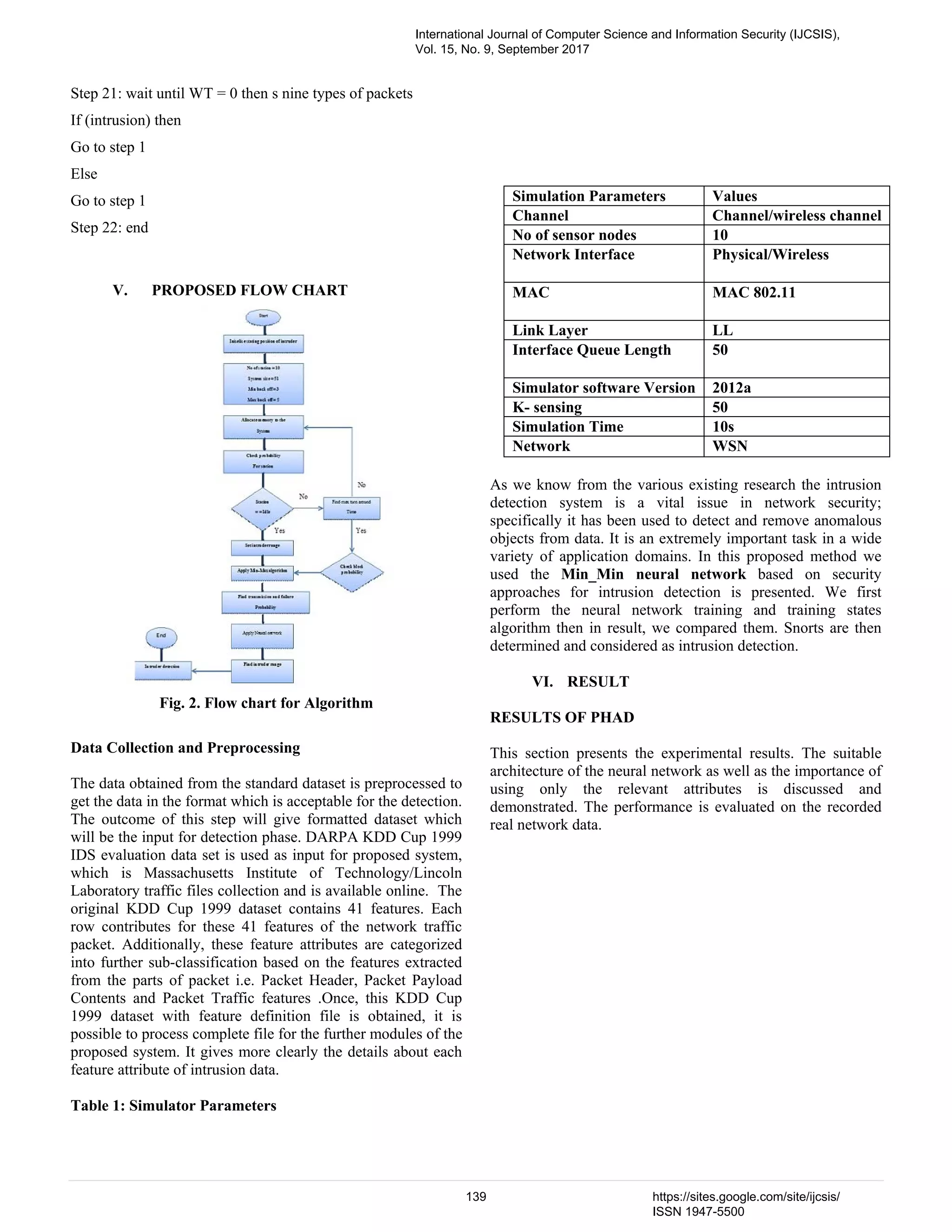
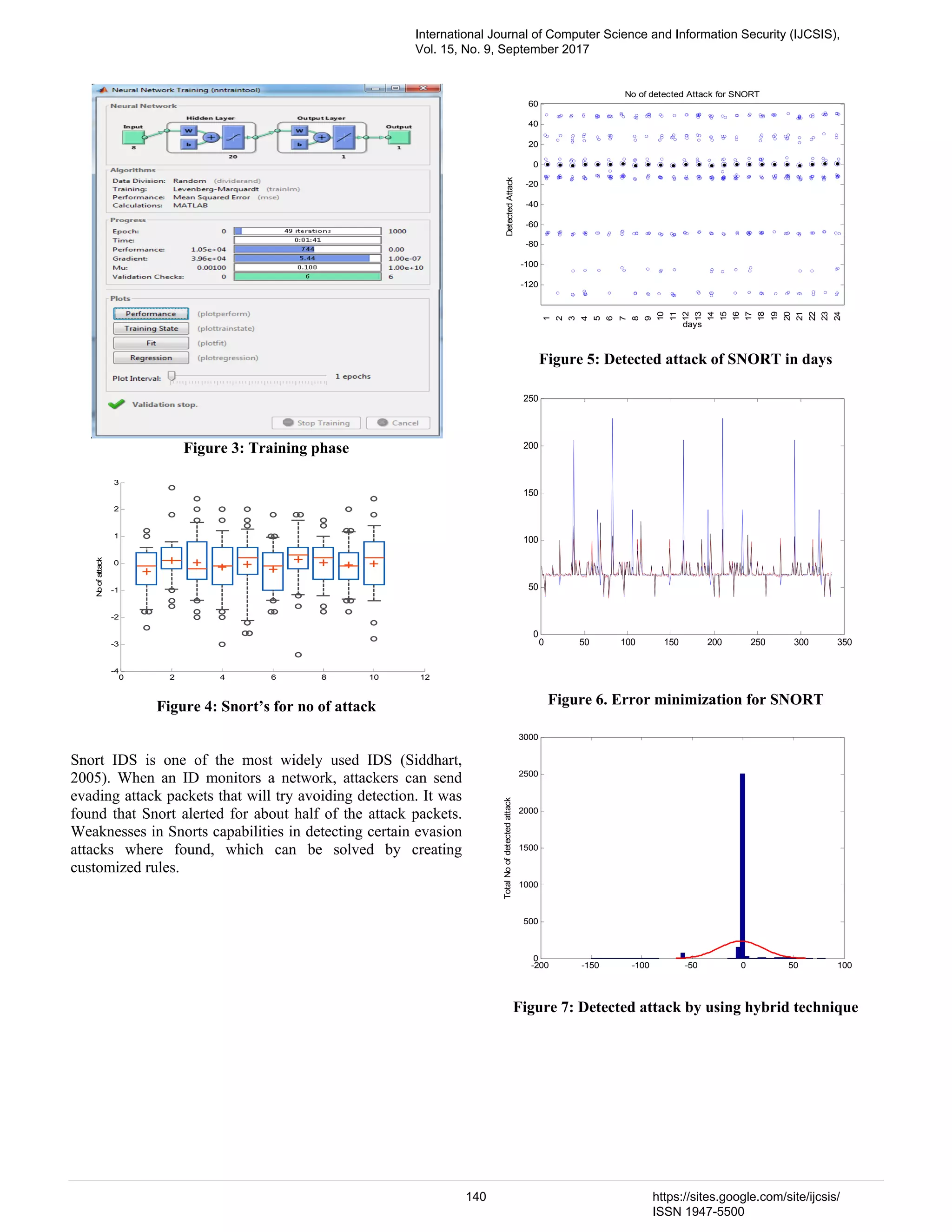
![PHAD [1] is a simple time-based protocol anomaly detector for network packets. To apply time-based modeling to anomaly detection with explicit training and test periods, an anomaly score= tn/r is calculated, where n is the number of times a packet field is observed during the training period and r is the number of distinct values of a particular packet field observed during training period, and where t is the time since the last anomaly [2]. SIGNATURE BASED IDS Signature based IDS matches the signatures of already known attacks that are stored into the database to detect the attacks in the computer system. Results of Signature based IDS that is evaluated is Snort. B. SNORT IDS Snort [3] is a small, lightweight open source IDS written by Martin Roesch which has become the most widely used IDS. Snort is an open source Intrusion Detection System that may also be configured as an Intrusion Prevention system for monitoring and prevention of security attacks on networks C. EVALUATION OF PHAD AND SNORT 3.4 Design Architecture The proposed research design architecture can be divided into three phases of development namely, data collection and pre- processing; Known and unknown attack detection; and Prevention as shown in Fig. 1 Fig. 1: Intrusion Detection Phase of System Architecture IV. PROPOSED NOVEL ALGORITHM MIN-MIN NN (MIN_MIN NEURAL NETWORK) MIN-MIN ALGORITHM STEPS OF PROPOSED WORK Input: Training set, testing set, h (theta), service, src_byte, wrong_fragment, flag, num_failed_logins Output: Min-Min neural network Process: Step 1. Start Step 2. Load the dataset Step 3. Specify the initial parameters h, service, src_byte, wrong_fragment, flag, num_failed_logins Step 4. If the input pattern is the first input pattern in the learning process, then assign the value of vij and wij. Step 5: For all tasks i t in Step 6:For all machines m j Step 7: CTij j = ET ij+ r Step 8: Do until all risk in MT are mapped Step 9: For each task i t in MT (meta task for intruder) Step 10: Find minimum CTij and resource that obtains it. Step 11: Find the intruderkt with the minimum CTij . Step 12: assign kt to resource and take hidden valuel m that Step 13: Delete kt from MT. Step 14: Update l r. Step 15: Update using feed forward CTil for all i. Step 16: when node wants to send data to next protocol version Step 17: If it is free then PHAD for anomaly detection. Step 18: if (ACK == yes) then the first phase is the filtering of incoming client sessions to distinguish beginning of Step 19: if (ACK == no) means acknowledgment not received then new Min-Min back-off is called to calculate the waiting slot time. Step 20: if (n=number of attack detect< no of intruder )Only the traffic data, which evidence of attacks are included in, is passed to the modeling phase Else WT = Min-Min (n) End if International Journal of Computer Science and Information Security (IJCSIS), Vol. 15, No. 9, September 2017 138 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/16paper31081736ijcsiscamerareadypp-180206144423/75/A-Hybrid-Intrusion-Detection-System-for-Network-Security-A-New-Proposed-Min-Min-Algorithm-4-2048.jpg)
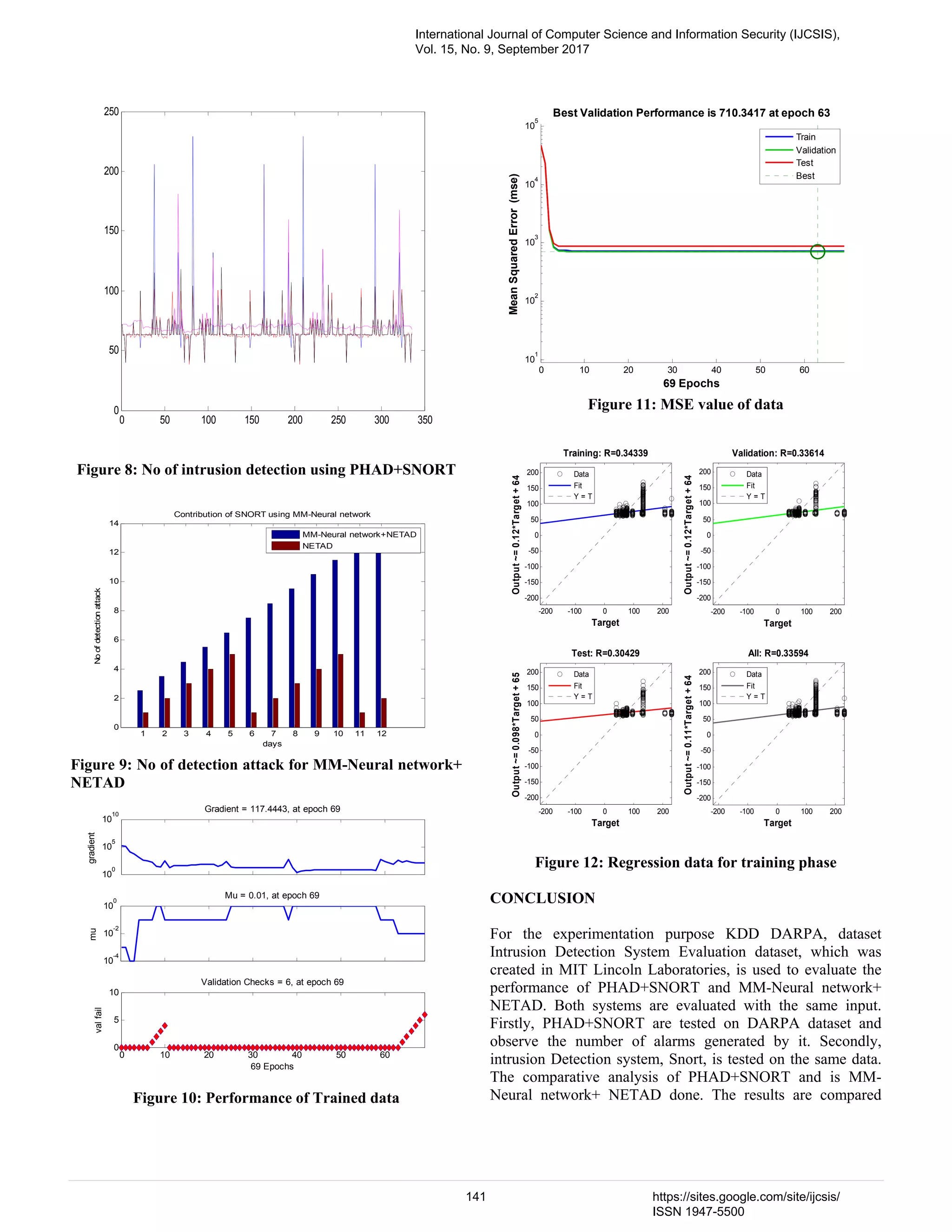
![because of MSE generated per day, MSE generated protocol wise and detection rate. It has been found and concluded that MM-Neural network+ NETAD is better in performance than PHAD+SNORT. REFERENCES [1]. I. F. Akyildiz et al., “Wireless Sensor Networks: A Survey, “Elsevier Comp. Networks, vol. 3, no. 2, 2002,pp. 393–422 [2]. G.Li, J.He, Y. Fu. “Group-based intrusion detection system in wireless sensor networks” Computer Communications, Volume 31, Issue 18 (December 2008) [3]. Michael Brownfield, “Wireless Sensor Network Denial of Sleep Attack”, Proceedings of the 2005 IEEE Workshop on Information Assurance and Security United States Military Academy, West Point, NY. [4]. FarooqAnjum, DhanantSubhadrabandhu, SaswatiSarkar *, Rahul Shetty, “On Optimal Placement of Intrusion Detection Modules in Sensor Networks”, Proceedings of the First International Conference on Broadband Networks (BROADNETS04) [5]. Parveen Sadotra et al, A REVIEW ON INTEGRATED INTRUSION DETECTION SYSTEM IN CYBER SECURITY International Journal of Computer Science and Mobile Computing, Vol.5 Issue.9, September- 2016, pg. 23-28 [6]. Y. Zhang and W. Lee.Intrusion Detection in Wireless Ad-Hoc Networks. In Proc. ACM MobiCom, pages 275-283, 2000 [7]. Qi Wang, Shu Wang, “Applying an Intrusion detection algorithm to wireless sensor networks”, Second international workshop on Knowledge Discovery and Data Mining, 2009. [8]. Xi Peng, Wuhan Zheng Wu, Debao Xiao, Yang Yu," Study on Security Management Architecture for Sensor Network Based on Intrusion Detection '" IEEE, Volume: 2,25-26 April 2009. [9]. Demirkol, F. Alagoz, H. Delic, and C. Ersoy, ― Wireless sensor networks for intrusion detection: packet traffic modelingǁ, 10(1):22–24, January 2006. [10]. W. B. Heinzelman, A. P. Chandrakasan, and H. Balakrishnan, - An application-specific protocol architecture for wireless micro sensor networks,ǁ IEEE Transactions on Wireless Communications, vol. 1, no. 4, pp. 660–670, 2002. [11]. K. Akkayaand M. Younis, ―A Survey of Routing Protocols in Wireless Sensor Networks, ǁ in the Elsevier Ad Hoc Network Journal, Vol. 3/3 pp. 325-349, 2005 [12]. Parveen Sadotra and Chandrakant Sharma. A Survey: Intelligent Intrusion Detection System in Computer Security. International Journal of Computer Applications 151(3):18-22, October 2016 [13]. R. A. F. Mini, B. Nath, and A. A. F. Loureiro,-A probabilistic approach to predict the energy consumption in wireless sensor network,ǁ In IV Workshop ,ǁ In IV Workshop on Wireless Communication and Mobile Computing, Seo Paulo, Brazil, October 23-25 2002. [14]. E. Blaß, M. Conrad and M. Zitterbart, “A Tree Based Approach for Secure Key Distribution in Wireless Sensor Networks.”, 2006. [15]. R. Roman, J. Zhou and J. Lopez, “Applying Intrusion Detection Systems to Wireless Sensor Networks”, Communications Society publication in the IEEE CCNC 2006. [16]. J. G. Tront and R. C. Marchany, “Internet Security Intrusion Detection & Prevention”, IEEE Proceedings ofthe 37th Hawaii International Conference on System Sciences, 2004. [17]. F.L. Lewis, “Wireless Sensor Networks” Smart Environments: Technologies, Protocols, and Applications Conference, New York, 2004. [18]. L. Besson, P. Leleu, “A distributed intrusion detection system for ad-hoc wireless sensor networks”, The 16th IEEE International Conference on Systems, Signals and Image Processing, Vol. 1, pp. 1-3, June 2009. [19]. A. Abduvaliyev, S. Lee, Y.K Lee, “Energy Efficient Hybrid Intrusion Detection System for Wireless Sensor Networks”, IEEE International Conference on Electronics and Information Engineering, Vol.2, pp. 25-29, August 2010. [20]. I. Krontiris, Z. Benenson, T. Giannetsos, F. Freiling, T. Dimitriou, “Cooperative Intrusion Detection in Wireless Sensor Networks”, Lecture Notes in Computer Science, Vol. 5432, pp. 263-278, February 2009. [21]. A. Araujo, J. Blesa, E. Romero, D. Villanueva, “Security in cognitive wireless sensor networks. Challenges and open problems”, EURASIP Journal on Wireless Communications and Networking, February 2012. [22]. Parveen Sadotra(CEH) and Dr. Chandrakant Sharma, “Transformation in Building More Intelligent Intrusion System: A review” presented in ICEECSIT- 17 at New Delhi, India, PP. 1 – 5 [23]. A. Becher, Z. Benenson, and M. Dorsey, Tampering with motes: Real-world physical attacks on wireless sensor networks." in SPC (J. A. Clark, R. F. Paige, F. Polack, and P. J. Brooke, eds.), vol. 3934 of Lecture Notes in Computer Science, pp. 104{118, Springer, 2006. [24]. I. Krontiris and T. Dimitriou, A practical authentication scheme for in-network programming in wireless sensor networks," in ACM Workshop on Real-World Wireless Sensor Networks, 2006 [25]. I. Krontiris, T. Giannetsos, and T. Dimitriou, LIDeA: a distributed lightweight intrusion detection architecture for sensor networks," in Secure Comma '08: Proceedings of the 4th international conference on Security and privacy in communication networks, (New York, NY,USA), pp. 1{10, ACM, 2008 [26]. W. Xu, K. Ma, W. Trappe, and Y. Zhang. Jamming sensor networks: attack and defines strategies. IEEE Network Magazine, 20(3):41–47, 2006. [27]. G. Li, J. He and Y. Fu.A group-based intrusion detection scheme in wireless sensor networks. In GPC-WORKSHOPS ’08: Proceedings of the International Conference on Grid and Pervasive Computing - Workshops, pages 286–291, Washington, DC, USA, 2008. IEEE Computer Society [28]. I. Krontiris, T. Dimitriou, T. Giannetsos, and M. Mpasoukos. Intrusion detection of sinkhole attacks in wireless sensor networks. In ALGOSENSORS ’07: Proceedings of the International Workshop on Algorithmic Aspects of Wireless Sensor Networks, pages 150–161, Germany, 2007. Springer-Verlag. [29]. M. Wen, H. Li, Y. Zheng, and K. Chen.Tdoa-based Sybil attack detection scheme for wireless sensor networks.Journal of Shanghai University (English Edition), 12:66–70,2008. [30]. Chong Eik Loo,Mun Yong Ng, Christopher Leckie, and MarimuthuPalaniswami.(2006) “Intrusion detection for routing attacks in sensor networks,” International Journal of Distributed Sensor Networks, Vol 2, pp. 313–332. [31]. Wei-Tsung Su, Ko-Ming Chang, and Yau-Hwang Kuo.Ehip, (2007) “An energy-efficient hybrid intrusion prohibition system for cluster-based wireless sensor networks,” Computer Networks, Vol 51, pp. 1151–1168. [32]. Sadotra P, Sharma C. A New Distributed Intrusion Detection System in Computer Network: An Approach to Detect Malicious Intrusion Threats at Initial Stage. Orient.J. Comp. Sci. and Technol;10(2) [33]. Fang Liu, Xiuzhen Cheng, and Dechang Chen, (2007) “Insider attacker detection in wireless sensor networks,” In INFOCOM 2007.26th IEEE International Conference on Computer Communications. IEEE, pp. 1937–1945. [34]. SADOTRA, Parveen; SHARMA, Dr. Chandrakant. Intrusion Detection in Networks Security: A New Proposed Min-Min Algorithm. International Journal of Advanced Research in Computer Science, [S.l.], v. 8, n. 3, apr. 2017. ISSN 0976-5697 [35]. Tran Hoang Hai, Eui-Nam Huh, and Minho Jo.(2010) “A lightweight intrusion detection framework for wireless sensor networks,” Wirel.Commun.Mob.Comput., 10(4), pp. 559–572. [36]. TassosDimitriou and AthanassiosGiannetsos.Wormholes no more, (2010) “localized wormhole detection and prevention in wireless networks,” In Distributed Computing in Sensor Systems, pp. 334– 347. Springer Berlin/Heidelberg. [37]. Yun Wang, Wei huang Fu, and Dharma P. Agrawal, Life Fellow, IEEE IEEE Transactions on parallel and distributed systems, vol. 24, no. 2, february 2013 [38]. T. Wimalajeewa and S.K. Jayaweera, “Impact of Mobile Node Density on Detection Performance Measures in a Hybrid Sensor International Journal of Computer Science and Information Security (IJCSIS), Vol. 15, No. 9, September 2017 142 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/16paper31081736ijcsiscamerareadypp-180206144423/75/A-Hybrid-Intrusion-Detection-System-for-Network-Security-A-New-Proposed-Min-Min-Algorithm-8-2048.jpg)
![Network,” IEEE Trans. Wireless Comm., vol. 9, no. 5, pp. 1760- 1769, May 2010. [39]. H. Kung and D. Vlah, “Efficient Location Tracking Using Sensor Networks,” Proc. IEEE Wireless Comm. and Networking Conf., vol. 3,pp. 1954-1961, Mar. 2003 [40]. C.-Y.Lin, W.-C.Peng, and Y.-C. Tseng, “Efficient In-Network Moving Object Tracking in Wireless Sensor Networks,” IEEE Trans. Mobile Computing, vol. 5, no. 8, pp. 1044-1056, Aug. 2006. [41]. Chao, S. Ren, Q. Li, H. Wang, X. Chen, and X. Zhang, “Design and Analysis of Sensing Scheduling Algorithms under Partial Coverage for Object Detection in Sensor Networks,” IEEE Trans. Parallel and Distributed Systems, vol. 18, no. 3, pp. 334-350, Mar. 2007. [42]. SADOTRA, Parveen; SHARMA, Dr. Chandrakant. SQL Injection Impact on Web Server and Their Risk Mitigation Policy Implementation Techniques: An Ultimate solution to Prevent Computer Network from Illegal Intrusion. International Journal of Advanced Research in Computer Science, [S.l.], v. 8, n. 3, apr. 2017. ISSN 0976-5697. [43]. S. Ren, Q. Li, H. Wang, X. Chen, and X. Zhang, “Design and Analysis of Sensing Scheduling Algorithms under Partial Coverage for Object Detection in Sensor Networks,” IEEE Trans. Parallel and Distributed Systems, vol. 18, no. 3, pp. 334-350,Mar. 2007 [44]. B. Liu, P. Brass, O. Dousse, P. Nain, and D. Towsley, “Mobility Improves Coverage of Sensor Networks,” Proc. Sixth ACM Int’lSymp. Mobile Ad Hoc Networking and Computing (MobiHoc ’05),pp. 300-308, 2005. [45]. M. Guerriero, L. Svensson, and P. Willett, “Bayesian Data Fusion for Distributed Target Detection in Sensor Networks,” IEEE Trans. Signal Processing, vol. 58, no. 6, pp. 3417-3421, June 2010. [46]. M. Zhu, S. Ding, Q. Wu, R. Brooks, N. Rao, and S. Iyengar,“Fusion of Threshold Rules for Target Detection in Wireless Sensor Networks,” ACM Trans. Sensor Networks, vol. 6, no. 2,article 18, 2010. [47]. Sasikumar, P. ; Sch. of Electron. Eng., VIT Univ., Vellore, India ;Khara, S. K-Means Clustering in Wireless Sensor Networks” Computational Intelligence and Communication Networks (CICN), 2012 [48]. I.F. Akyildiz, W. Su, Y. Sankarasubramaniam, and E. Cayirci, “A Survey on Wireless Sensor Networks,” IEEE Comm. Magazine, vol. 40, no. 8, pp. 102-114, Aug. 2002. [49]. S. Tilak, N.B. Abu-Ghazaleh, and W. Heinzelman, “A Taxonomy of Wireless Micro-Sensor Network Models,” ACM Mobile Computing and Comm. Rev., vol. 6, no. 2, pp. 28-36, Apr. 2002. [50]. A. Agah, S. Das, K. Basu, and M. Asadi, “Intrusion Detection in Sensor Networks: A Non-Cooperative Game Approach,”Proc. Third IEEE Int’l Symp. Network Computing and Applications (NCA ’04), pp. 343-346, 2004. [51]. Parveen Sadotra (Ceh) ,Chandrakant Sharma , (2017 ) " Transformation in Building More Intelligent Intrusion Detection System: A Review " , International Journal of Management and Applied Science (IJMAS) , pp. 29-33, Volume-5, Issue-3 [52]. S. Kumar, T.H. Lai, and J. Balogh, “On K-Coverage in a Mostly Sleeping Sensor Network,” Proc. 10th Ann. Int’l Conf. Mobile Computing and Networking (MobiCom ’04), pp. 144-158, 2004. [53]. V. Giruka, M. Singhal, J. Royalty, and S. Varanasi, “Security in Wireless Sensor Networks,” Wireless Comm. and Mobile Computing, vol. 8, no. 1, pp. 1-24, 2008. [54]. H. Kung and D. Vlah, “Efficient Location Tracking Using Sensor Networks,” Proc. IEEE Wireless Comm. and Networking Conf., vol. 3,pp. 1954-1961, Mar. 2003. [55]. M. Ali Aydın *, A. HalimZaim, K. GokhanCeylan “A hybrid intrusion detection system design for computer network security” Computers and Electrical Engineering 35 (2009) 517–526. International Journal of Computer Science and Information Security (IJCSIS), Vol. 15, No. 9, September 2017 143 https://sites.google.com/site/ijcsis/ ISSN 1947-5500](https://image.slidesharecdn.com/16paper31081736ijcsiscamerareadypp-180206144423/75/A-Hybrid-Intrusion-Detection-System-for-Network-Security-A-New-Proposed-Min-Min-Algorithm-9-2048.jpg)