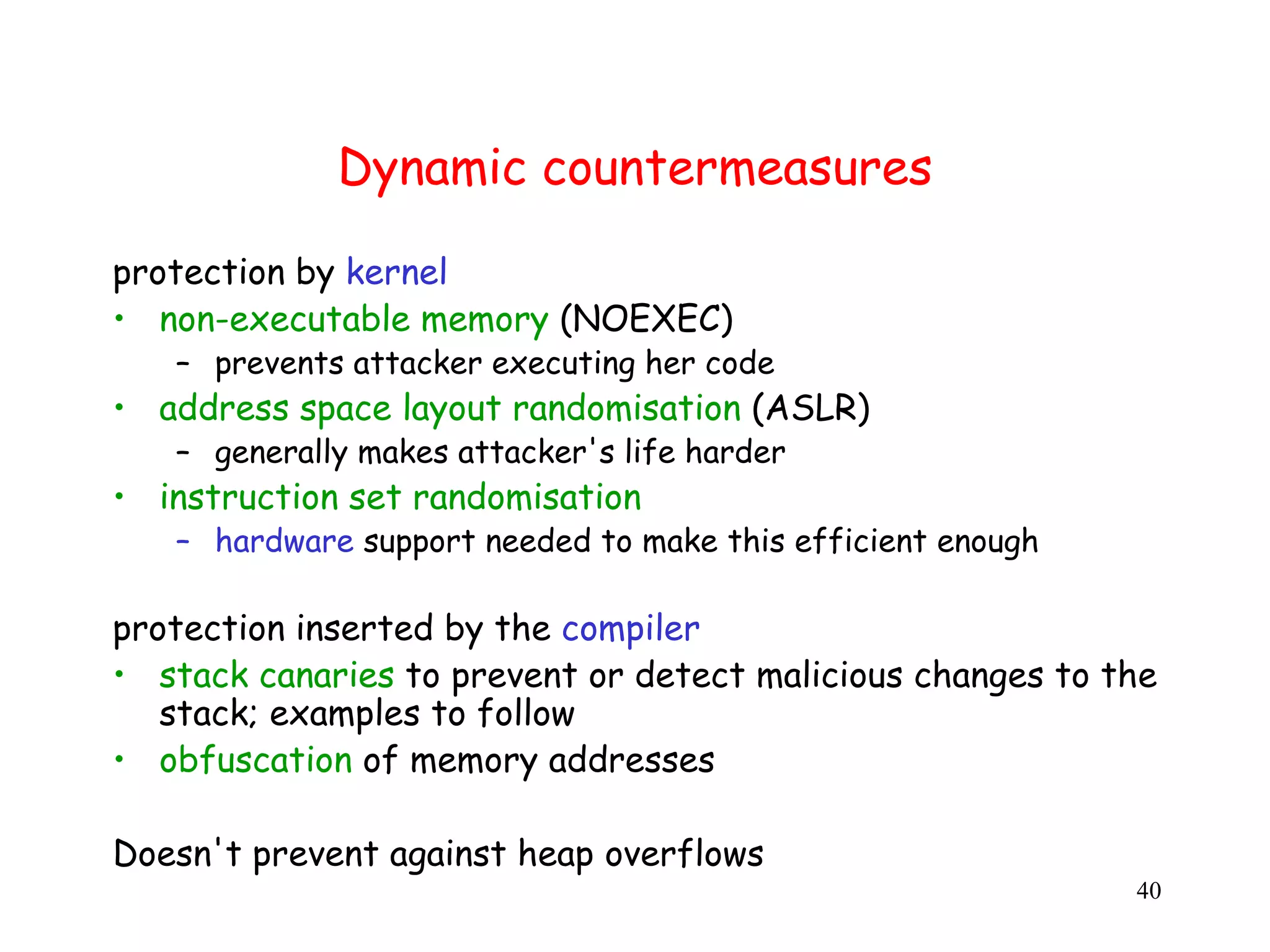
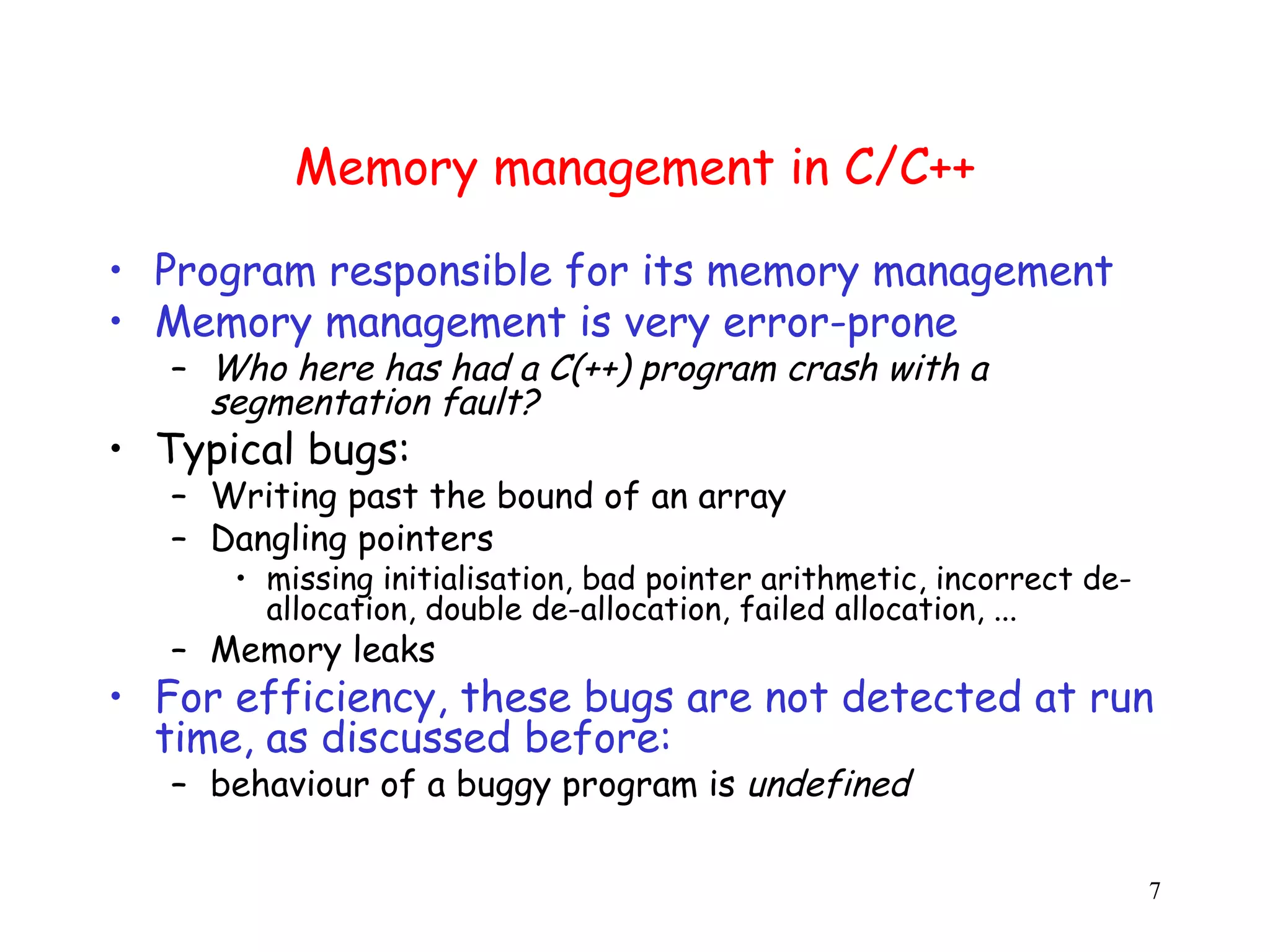
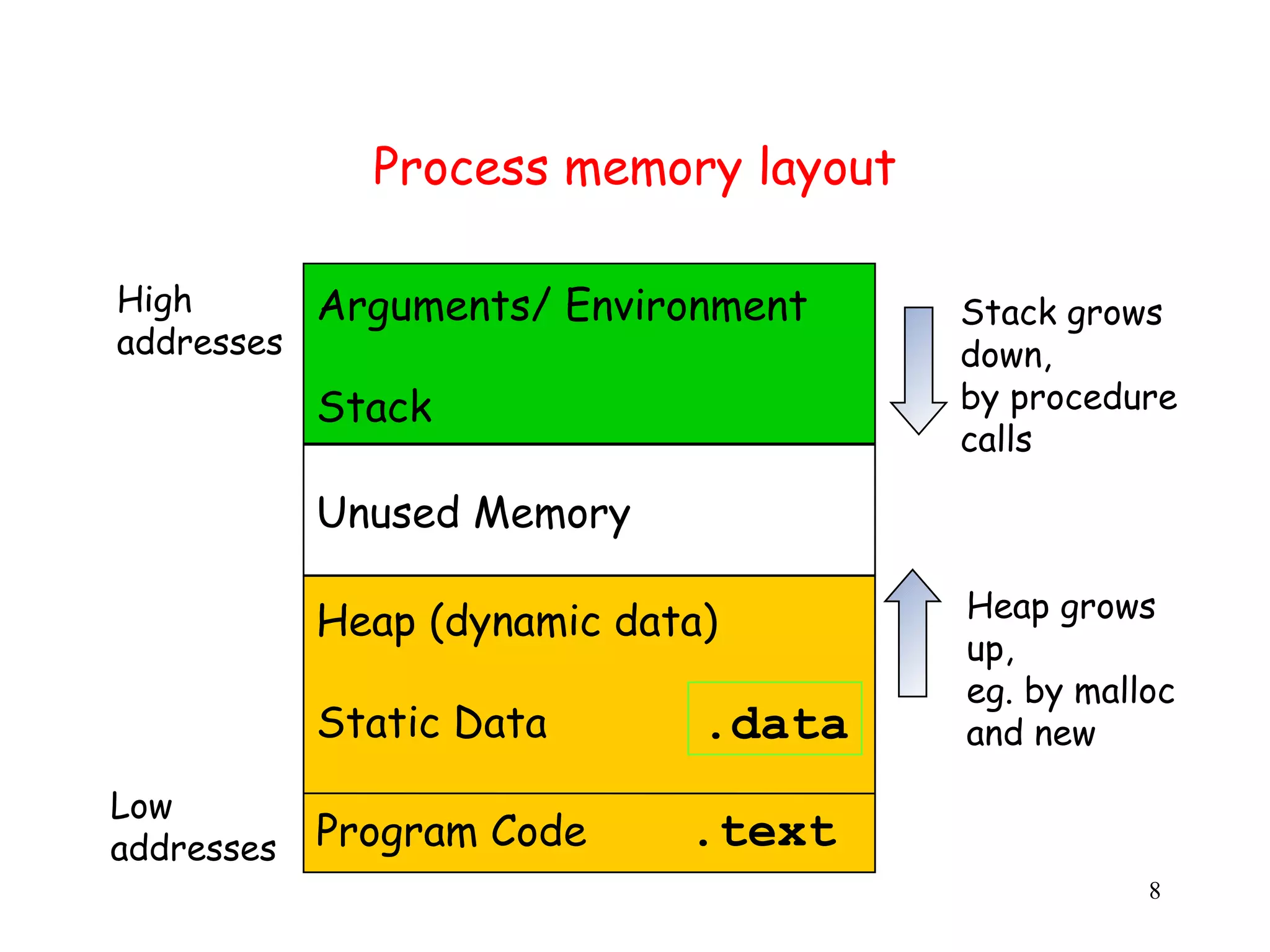
This document discusses buffer overflows as a major software security problem. It begins by explaining how a buffer overflow occurs when a program writes past the end of an allocated buffer through errors like failing to check array bounds. This can allow attackers to execute arbitrary code by overwriting return addresses on the stack. The document covers various dynamic countermeasures implemented by compilers like stack canaries to help detect and prevent buffer overflow attacks. However, it notes these don't prevent all overflows like those on the heap.

![Essence of the problem Suppose in a C program we have an array of length 4 char buffer[4]; What happens if we execute the statement below ? buffer[4] = ‘a’; Anything can happen ! If the data written (ie. the “a”) is user input that can be controlled by an attacker, this vulnerability can be exploited: anything that the attacker wants can happen. 2](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-2-2048.jpg)




![Stack overflow The stack consists of Activation Records: x AR main() m return address AR f() f buf[4..7] buf[0..3] Stack grows void f(int x) { Buffer grows downwards char[8] buf; upwards gets(buf); } void main() { f(…); … } void format_hard_disk(){…} 9](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-9-2048.jpg)
![Stack overflow What if gets() reads more than 8 bytes ? x AR main() m return address AR f() f buf[4..7] buf[0..3] void f(int x) { Buffer grows char[8] buf; upwards gets(buf); } void main() { f(…); … } void format_hard_disk(){…} 10](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-10-2048.jpg)
![Stack overflow What if gets() reads more than 8 bytes ? x AR main() m return address AR f() f buf[4..7] buf[0..3] Stack grows void f(int x) { Buffer grows downwards char[8] buf; upwards gets(buf); } never use void main() { f(…); … gets()! } void format_hard_disk(){…} 11](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-11-2048.jpg)



![Example: gets char buf[20]; gets(buf); // read user input until // first EoL or EoF character • Never use gets • Use fgets(buf, size, stdin) instead 15](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-15-2048.jpg)
![Example: strcpy char dest[20]; strcpy(dest, src); // copies string src to dest • strcpy assumes dest is long enough , and assumes src is null-terminated • Use strncpy(dest, src, size) instead 16](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-16-2048.jpg)
![S Spot the defect! (1) char buf[20]; char prefix[] = ”http://”; ... strcpy(buf, prefix); // copies the string prefix to buf strncat(buf, path, sizeof(buf)); // concatenates path to the string buf 17](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-17-2048.jpg)
![S Spot the defect! (1) char buf[20]; char prefix[] = ”http://”; ... strcpy(buf, prefix); // copies the string prefix to buf strncat(buf, path, sizeof(buf)); // concatenates path to the string buf strncat’s 3rd parameter is number of chars to copy, not the buffer size Another common mistake is giving sizeof(path) as 3rd argument... 18](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-18-2048.jpg)
![S Spot the defect! (2) char src[9]; char dest[9]; char base_url = ”www.ru.nl”; strncpy(src, base_url, 9); // copies base_url to src strcpy(dest, src); // copies src to dest 19](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-19-2048.jpg)
![S Spot the defect! (2) base_url is 10 chars long, incl. its char src[9]; null terminator, so src won’t be char dest[9]; not null-terminated char base_url = ”www.ru.nl/”; strncpy(src, base_url, 9); // copies base_url to src strcpy(dest, src); // copies src to dest 20](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-20-2048.jpg)
![Spot the defect! (2) base_url is 10 chars long, incl. its char src[9]; null terminator, so src won’t be char dest[9]; not null-terminated char base_url = ”www.ru.nl/”; strncpy(src, base_url, 9); // copies base_url to src strcpy(dest, src); // copies src to dest so strcpy will overrun the buffer dest 21](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-21-2048.jpg)
![Example: strcpy and strncpy • Don’t replace s strcpy(dest, src) by s strncpy(dest, src, sizeof(dest)) but by s strncpy(dest, src, sizeof(dest)-1) dst[sizeof(dest-1)] = `0`; if dest should be null-terminated! • Btw: a strongly typed programming language could of course enforce that strings are always null-terminated... 22](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-22-2048.jpg)


![S Spot the defect! (3) char *buf; May result in integer overflow; int i, len; we should check that len+1 is positive read(fd, &len, sizeof(len)); i if (len < 0) {error ("negative length"); return; } buf = malloc(len+1); read(fd,buf,len); buf[len] = '0'; // null terminate buf 25](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-25-2048.jpg)
![S Spot the defect! (4) #ifdef UNICODE #define _sntprintf _snwprintf #define TCHAR wchar_t #else #define _sntprintf _snprintf #define TCHAR char #endif TCHAR buff[MAX_SIZE]; _sntprintf(buff, sizeof(buff), ”%sn”, input); [slide from presentation by Jon Pincus] 26](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-26-2048.jpg)
![Spot the defect! (4) #ifdef UNICODE #define _sntprintf _snwprintf #define TCHAR wchar_t #else #define _sntprintf _snprintf #define TCHAR char #endif _snwprintf’s 2nd param is # of chars in buffer, not # of bytes TCHAR buff[MAX_SIZE]; _sntprintf(buff, sizeof(buff), ”%sn”, input); The CodeRed worm exploited such an ANSI/Unicode mismatch [slide from presentation by Jon Pincus] 27](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-27-2048.jpg)
![S Spot the defect! (5) #define MAX_BUF = 256 v void BadCode (char* input) { short len; char buf[MAX_BUF]; len = strlen(input); if (len < MAX_BUF) strcpy(buf,input); } 28](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-28-2048.jpg)
![Spot the defect! (5) #define MAX_BUF = 256 What if input is longer than 32K ? v void BadCode (char* input) { short len; len will be a negative number, char buf[MAX_BUF]; due to integer overflow hence: potential len = strlen(input); buffer overflow if (len < MAX_BUF) strcpy(buf,input); } The integer overflow is the root problem, but the (heap) buffer overflow that this enables make it exploitable 29](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-29-2048.jpg)
![S Spot the defect! (6) b bool CopyStructs(InputFile* f, long count) { structs = new Structs[count]; f for (long i = 0; i < count; i++) { if !(ReadFromFile(f,&structs[i]))) break; } } 30](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-30-2048.jpg)
![S Spot the defect! (6) b bool CopyStructs(InputFile* f, long count) { structs = new Structs[count]; f for (long i = 0; i < count; i++) { if !(ReadFromFile(f,&structs[i]))) break; } } effectively does a malloc(count*sizeof(type)) which may cause integer overflow And this integer overflow can lead to a (heap) buffer overflow. (Microsoft Visual Studio 2005(!) C++ compiler adds check to prevent t this) 31](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-31-2048.jpg)
![Spot the defect! (7) char buff1[MAX_SIZE], buff2[MAX_SIZE]; // make sure url a valid URL and fits in buff1 and buff2: if (! isValid(url)) return; if (strlen(url) > MAX_SIZE – 1) return; // copy url up to first separator, ie. first ’/’, to buff1 out = buff1; do { // skip spaces if (*url != ’ ’) *out++ = *url; } while (*url++ != ’/’); strcpy(buff2, buff1); ... [slide from presentation by Jon Pincus] 32](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-32-2048.jpg)
![Spot the defect! (7) Loop termination (exploited by Blaster) ( char buff1[MAX_SIZE], buff2[MAX_SIZE]; // make sure url a valid URL and fits in buff1 and buff2: if (! isValid(url)) return; if (strlen(url) > MAX_SIZE – 1) return; // copy url up to first separator, ie. first ’/’, to buff1 out = buff1; do { length up to the first null // skip spaces if (*url != ’ ’) *out++ = *url; } while (*url++ != ’/’); strcpy(buff2, buff1); ... what if there is no ‘/’ in the URL? [slide from presentation by Jon Pincus] 33](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-33-2048.jpg)
![Spot the defect! (7) char buff1[MAX_SIZE], buff2[MAX_SIZE]; // make sure url a valid URL and fits in buff1 and buff2: if (! isValid(url)) return; if (strlen(url) > MAX_SIZE – 1) return; // copy url up to first separator, ie. first ’/’, to buff1 out = buff1; do { // skip spaces if (*url != ’ ’) *out++ = *url; } while (*url++ != ’/’) && (*url != 0); strcpy(buff2, buff1); ... [slide from presentation by Jon Pincus] 34](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-34-2048.jpg)
![Spot the defect! (7) char buff1[MAX_SIZE], buff2[MAX_SIZE]; // make sure url a valid URL and fits in buff1 and buff2: if (! isValid(url)) return; if (strlen(url) > MAX_SIZE – 1) return; // copy url up to first separator, ie. first ’/’, to buff1 out = buff1; do { // skip spaces if (*url != ’ ’) *out++ = *url; } while (*url++ != ’/’) && (*url != 0); strcpy(buff2, buff1); ... Order of tests is wrong (note the first test includes ++) What about 0-length URLs? [slide from presentation by Jon Pincus] Is buff1 always null-terminated? 35](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-35-2048.jpg)
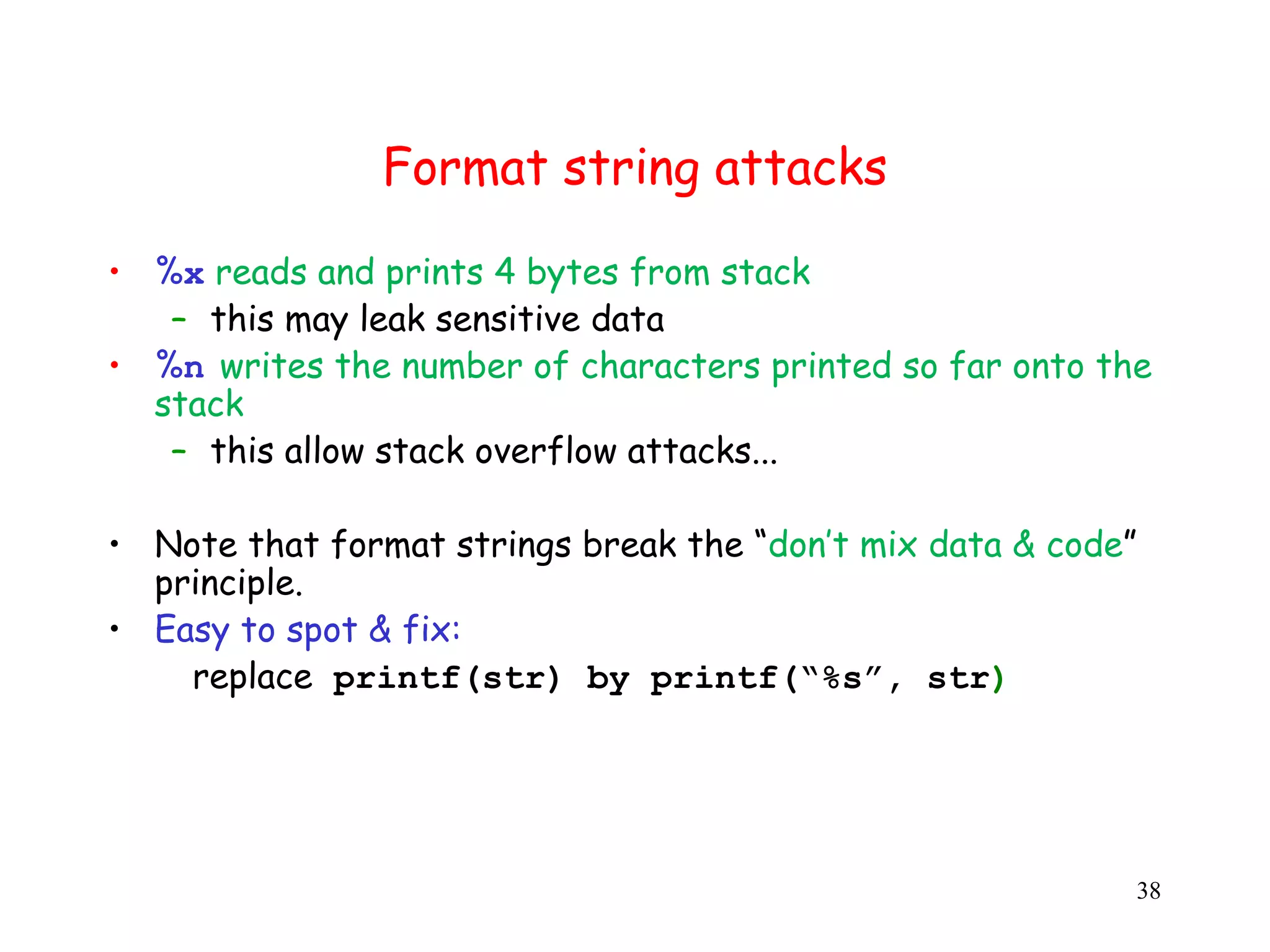
![Spot the defect! (8) #include <stdio.h> int main(int argc, char* argv[]) { if (argc > 1) printf(argv[1]); return 0; } This program is vulnerable to format string attacks, where calling the program with strings containing special characters can result in a buffer overflow attack. 36](https://image.slidesharecdn.com/2bufferoverflows-110821191852-phpapp02/75/2-buffer-overflows-36-2048.jpg)