You can use prefix lists to manage frequently used IP address ranges. You can then reference these prefix lists in security group rules and route entries within your account or other accounts. When you modify a prefix list, all configurations that reference the prefix list are automatically updated.
Prefix lists are useful in the following scenarios:
Centralized management of company egress IP addresses: A company needs to access multiple ECS instances from the Internet. The traditional approach is to add the company's egress IP addresses to the security group rules for each ECS instance. However, if these egress IP addresses change frequently, manually updating the security group rules for all ECS instances is cumbersome and error-prone. If you use prefix lists to centrally manage egress IP addresses, you only need to update the prefix list. All security group rules that reference the prefix list are automatically updated. This significantly improves configuration efficiency and management.
Centralized maintenance of partner IP ranges: If your business needs to communicate with partner IP ranges, you typically need to add the same routes to different route tables. You can use prefix lists to centrally manage partner IP ranges and avoid duplicate configurations. When partner IP ranges change, you only need to edit the prefix list. All route tables that reference the prefix list are automatically updated, which simplifies scaling and maintenance.

Limits
Gateway route tables and Basic Edition transit routers cannot reference prefix lists.
A prefix list is a region-specific resource that can be used only within the region where it is created. It cannot be referenced or shared across regions.
A prefix list cannot contain both IPv4 and IPv6 CIDR blocks.
You must specify the maximum number of entries when you create a prefix list.
When a prefix list is referenced, it consumes the quota of the resource that references it. VPC route tables and ECS security groups consume quota based on the maximum number of entries in the prefix list. Enterprise Edition transit router (TR) route tables consume quota based on the actual number of entries in the prefix list. For example, you create a prefix list with a maximum of 50 entries but it contains only 20 entries. When referenced by a VPC route table or security group, the prefix list consumes the quota for 50 routes or 50 security group rules. However, when referenced by a TR route table, it consumes the quota for only 20 routes.
When you create a gateway endpoint for a specific Alibaba Cloud service in a region for the first time, the system automatically creates a system prefix list containing the IP address ranges for that service. The system then adds a route to the VPC route table that references this prefix list and sets the gateway endpoint as the next hop, which allows the VPC to access the service. You cannot reference, modify, delete, or share this system prefix list. In the console, the Owner of the prefix list is ALIYUN/System Account.
Manage prefix lists
Console
Create a prefix list
Go to the VPC Prefix Lists page in the VPC console. In the top-left corner, select a Region and then click Create VPC Prefix List.
In the Create VPC Prefix List panel:
Select the IP Version (IPv4 or IPv6).
Set Maximum Number Of Entries: This value counts against the quotas for VPC route tables and security groups, and can be modified after creation.
For example, if a prefix list contains only 20 entries but the maximum number of entries is set to 50, the prefix list still consumes the quota for 50 routes or 50 security group rules when referenced by a VPC route table or security group.
For more information about quotas, see the following topics: By default, a VPC route table supports up to 200 custom route entries. By default, a security group supports up to 200 rules.
Configure Prefix List Entries. You can select Enter One By One, Enter In Batches, or Clone From Another Prefix List. Cloning is supported across regions, but not for shared or system prefix lists.
Add or delete entries
On the Entries tab of the target prefix list's details page:
To add an entry, click Create VPC Prefix List Entry.
To delete entries, click Delete in the Actions column for a single entry, or select multiple entries and click Batch Delete.
View resources that reference a prefix list
On the details page of the prefix list, click the Associations tab.
Delete a prefix list
Click Delete in the Actions column for the target prefix list or on its details page.
Before you delete a prefix list, make sure that it is not referenced by other resources or shared.
API
Call CreateVpcPrefixList to create a prefix list.
Call ModifyVpcPrefixList to add or delete entries.
Call GetVpcPrefixListAssociations to view resources that reference a prefix list.
Call DeleteVpcPrefixList to delete a prefix list.
Before you delete a prefix list, make sure that it is not referenced by other resources or shared.
Terraform
Resource: alicloud_vpc_prefix_list
# Specify the region provider "alicloud" { region = "cn-hangzhou" } # Create a prefix list resource "alicloud_vpc_prefix_list" "example_pl" { prefix_list_name = "example_pl_name" ip_version = "IPV4" # IP version max_entries = 50 # Maximum number of entries entrys { cidr = "10.0.1.0/24" # Entry 1 } entrys { cidr = "10.0.2.0/24" # Entry 2 } }Reference a prefix list
You can reference prefix lists in VPC route tables, Enterprise Edition transit router (TR) route tables, and ECS security groups. After you modify a prefix list, the resources that reference it are automatically updated. This helps improve configuration efficiency.
VPC route table references
When you add custom route entries to a VPC route table, you can reference a prefix list. Take note of the following items:
The prefix list cannot conflict with existing route entries in the VPC. Otherwise, the reference fails. If a conflict occurs after the prefix list is referenced, see Handle entry conflicts after referencing.
The maximum number of entries in the prefix list, not the actual number of entries, consumes the quota for custom route entries in the VPC route table. To reduce the risk of exceeding the quota, you can decrease the maximum number of entries, merge adjacent IP ranges, or clear unused entries.
Console
Go to the details page of the route table. On the tab, click Add Route Entry and configure the following parameters:
Destination CIDR Block: Select VPC Prefix List from the drop-down list on the left and select the prefix list on the right.
Next Hop Type: Select the type and instance.
API
Call CreateRouteEntry and specify the instance ID of the prefix list for the DestinationCidrBlock parameter.
Terraform
Resources: alicloud_route_entry
# Specify the region provider "alicloud" { region = "cn-hangzhou" } # Add a VPC route entry with a prefix list as the destination CIDR block resource "alicloud_route_entry" "example" { route_table_id = "vtb-bp1pa1mwgfd6rqxfxxxxx" # VPC route table ID destination_cidrblock = "pl-bp1fnjzxkk2m6qrwxxxxx" # Destination CIDR block. Enter the prefix list ID. nexthop_type = "Ecr" # Next hop type nexthop_id = "ecr-assoc-stwhaft9a371nxxxxx" # Next hop instance ID }TR route table references
You can reference prefix lists in Enterprise Edition transit router route tables. After a prefix list is referenced, the system automatically adds routes for all CIDR blocks in the prefix list to the Enterprise Edition transit router route table. Take note of the following items:
If route synchronization is enabled for the transit router, the system automatically propagates the route entries from the prefix list to other network instances after the prefix list is referenced.
The route entries from the prefix list cannot conflict with existing route entries in the transit router route table. For more information, see Route compatibility to determine whether route conflicts will occur. Incompatibility indicates a conflict. If conflicts exist, the reference fails. If conflicts occur after the prefix list is referenced, see Handle entry conflicts after referencing.
The actual number of entries in the prefix list consumes the quota for route entries in the transit router route table. We recommend that you merge adjacent IP ranges and clear unused entries to reduce the risk of exceeding the quota.
Console
Associate a prefix
Go to the details page of the transit router route table, click the Route Prefixes tab, and then click Associate Route Prefix:
Route Prefix ID: Select the prefix list that you want to reference.
Is Blackhole Route:
Yes: The system discards traffic that matches the prefix list.
No: The system directs traffic that matches the prefix list to the Next Hop Connection.
Filter route entries corresponding to a prefix list
Go to the details page of the transit router route table, click the Route Entries tab, and filter by Route Prefix ID to view the route entries that are added from the prefix list.
Disassociate a prefix
After you disassociate a prefix list, the system automatically revokes all related route entries that have been added to the Enterprise Edition transit router route table. Before you disassociate the prefix list, make sure that you have migrated the service traffic. Otherwise, network interruptions may occur.
Go to the Basic Information page of the transit router route table, click the Route Prefixes tab, and then click Delete in the Actions column of the prefix list.
API
Associate a prefix list: Call CreateTransitRouterPrefixListAssociation to reference a prefix list in an Enterprise Edition transit router route table.
Filter route entries that correspond to a prefix list: Call ListTransitRouterPrefixListAssociation and filter the route entries added from the prefix list by
PrefixListIdin the returned results.Delete a prefix list: Call DeleteTransitRouterPrefixListAssociation to delete a referenced prefix list from an Enterprise Edition transit router route table.
Terraform
Resources: alicloud_cen_transit_router_prefix_list_association
# Specify the region provider "alicloud" { region = "cn-hangzhou" } # Reference a prefix list in a Cloud Enterprise Network transit router resource "alicloud_cen_transit_router_prefix_list_association" "example" { prefix_list_id = "pl-bp1fnjzxkk2m6qrwxxxxx" # Prefix list ID transit_router_id = "tr-bp1czv20pflygguoxxxxx" # Transit router ID transit_router_table_id = "vtb-bp1v7079o4dwrkgpxxxxx" # Transit router route table ID next_hop_type = "BlackHole" # Next hop type next_hop = "BlackHole" # Next hop instance ID }ECS security group references
You can reference prefix lists when you configure inbound or outbound security group rules.
Console
The following steps describe how to add an inbound security group rule. Go to the details page of the security group in the ECS console. On the Access Rules page, click the Inbound tab, and then click Add Rule.
Source: Select Prefix List from the drop-down list on the left and select the prefix list on the right.
Configure other parameters as required.
API
When you call AuthorizeSecurityGroup to add an inbound security group rule, specify the prefix list ID for the
SourcePrefixListIdparameter.When you call AuthorizeSecurityGroupEgress to add an outbound security group rule, specify the prefix list ID for the
DestPrefixListIdparameter.
Terraform
Resources: alicloud_security_group, alicloud_security_group_rule
# Specify the region provider "alicloud" { region = "cn-hangzhou" } # Specify the security group resource "alicloud_security_group" "sg_example" { security_group_name = "sg_example_name" vpc_id = "vpc-bp1d00iurwfx3pcxxxxx" # VPC ID } # Reference a prefix list when you create a security group rule resource "alicloud_security_group_rule" "sg_rule_pl_example" { security_group_id = alicloud_security_group.sg_example.id type = "ingress" ip_protocol = "tcp" policy = "accept" port_range = "8080/8080" prefix_list_id = "pl-bp1fnjzxkk2m6qrxxxxxx" # VPC prefix list ID }Handle entry conflicts after referencing
After you reference a prefix list in a VPC route table or transit router route table, if changes to the prefix list conflict with existing entries in the route table, the latest changes do not take effect.
You can view conflict details on the Associations tab of the prefix list details page. The Status of the reference that has conflicts is Not Associated With Latest Version. You can move the pointer over the Status to view the ErrorMessage for specific conflicting entries.
You can use one of the following methods to resolve conflicts:
Before you perform the operations, make sure that modifying the route entries does not affect your services.
Modify the prefix list: Delete the conflicting entries from the prefix list. After you delete the entries, the system automatically redeploys the prefix list to all associated resources.
Modify the route table: Delete the conflicting route entries from the route table. Then, manually redeploy the prefix list until the status changes from Not Associated With Latest Version to Deployment Successful.
The following steps describe how to manually redeploy a prefix list.
Console
Go to the VPC Prefix Lists page in the VPC console. In the upper-left corner of the top menu bar, select the region and then click the Instance ID of the prefix list.
Click the Associations tab, find the reference, and click Retry in the Actions column.
API
Call RetryVpcPrefixListAssociation to redeploy the prefix list.
Terraform
Terraform does not support redeploying a prefix list without modifying its entries.
Share prefix lists
By sharing prefix lists, different accounts can reference the same prefix list to configure security groups or routes. This enables unified management of specific IP address ranges and avoids duplicate maintenance of the same IP ranges. This improves maintenance efficiency and reduces configuration errors.
The following example describes how Account A shares a prefix list with Account B. In this scenario, Account A is the prefix list owner and Account B is the prefix list principal.
An owner can share their prefix lists with any Alibaba Cloud account or only with accounts within a resource directory.
Console
Enable sharing
This section describes how to share a prefix list with any account. For information about how to share a prefix list within a resource directory, see Share resources only within a resource directory.
Log on to the account of the prefix list owner and go to the Resource Sharing - My Shares page in the Resource Management console. In the upper-left corner of the top menu bar, select the region where the shared resource is located. Then, click Create Resource Share. On the page that appears, perform the following steps:
Step 1: Enter a Resource Share Name. In the Resources panel, select VPC Prefix List from the drop-down list, and then select the prefix list to share.
Step 2: The system automatically selects the AliyunRSDefaultPermissionPrefixList permission.
Step 3: For Principal Scope, select Share Resources With Any Account. For Add Method, select Manual. Enter the Alibaba Cloud account ID of the prefix list principal in the Principal ID field, and click Add.
Step 4: After verification, click OK at the bottom of the page.
Log on to the account of the prefix list principal and accept the sharing invitation:
Go to the Resource Sharing - Shared with Me page in the Resource Management console.
In the upper-left corner of the top menu bar, select the region where the shared resource is located, and then click Accept in the Status column of the resource share.
After the invitation is accepted, the principal can access the shared prefix list. Any additional shared resources that are added to this resource share are automatically accepted.
Go to the VPC Prefix Lists page in the VPC console. After you select the region where the shared prefix list is located in the top menu bar, you can view the received prefix list. The prefix list is marked as Shared in the Owner column.
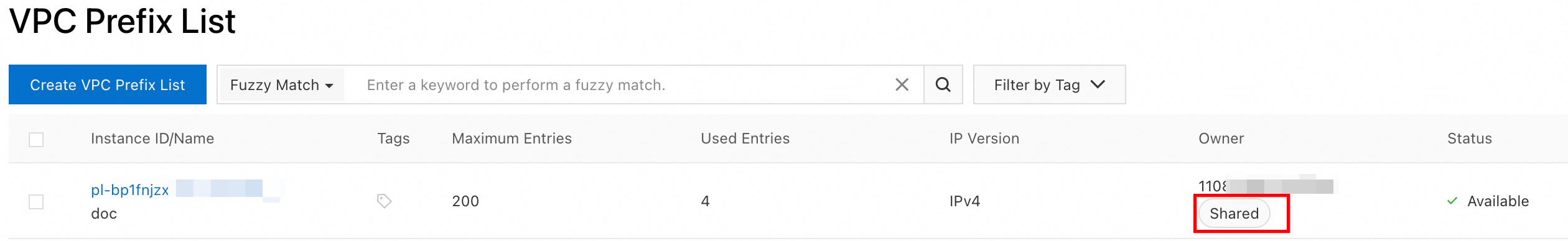
You can now reference the prefix list in VPC route tables, Enterprise Edition transit router route tables, and ECS security groups. For more information, see Reference a prefix list.
Manage shared prefix lists and principals
The prefix list owner can perform the following steps to view, add, or delete shared prefix lists and their principals.
Log on to the account of the prefix list owner and go to the Resource Sharing - My Shares page in the Resource Management console. In the upper-left corner of the top menu bar, select the region where the shared prefix list is located.
On the My Shares page, you can perform the following operations:
View shared prefix lists: Click the Shared Resources tab.
View principals of shared prefix lists: Click the Principals tab.
Click the Resource Shares tab, find the resource share, and click the resource share ID.
You can click the Resources or Principals tabs to view the shared prefix lists and principals in this resource share.
If the Sharing Status on the Resources and Principals tabs is Associated, the shared resources and principals are successfully added:
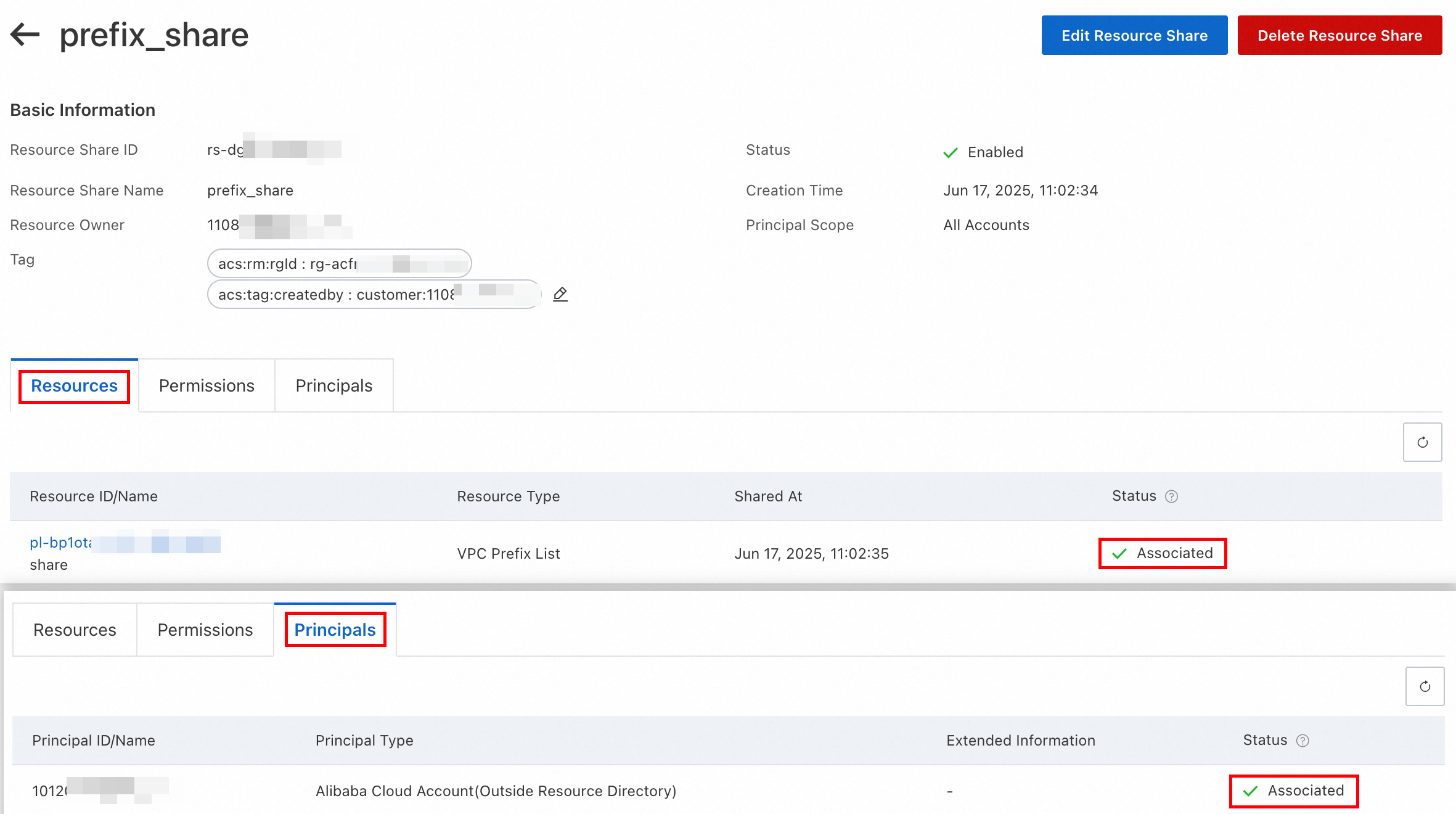
On the page of the resource share, click Edit Resource Share in the upper-right corner. Within this resource share, you can perform the following operations:
Add or delete shared prefix lists: In Step 1, select or deselect prefix lists.
Add or delete principals of shared prefix lists: In Step 3, add or delete account UIDs.
After verification, in Step 4 of the Edit Resource Share page, click OK.
API
Enable sharing
Method 1: Share with any account
Use the identity credentials of the prefix list owner to call CreateResourceShare to create a resource share. Make sure that you set the
AllowExternalTargetsparameter toTrue.Use the identity credentials of the prefix list principal to first call ListResourceShareInvitations to query received resource invitations, and then call AcceptResourceShareInvitation to accept a sharing invitation.
Method 2: Share only within a resource directory
Before you perform the operations, make sure that the prefix list owner and principal have joined the same resource directory.
Use the identity credentials of the management account of the resource directory to call EnableSharingWithResourceDirectory to enable resource sharing within the resource directory.
Use the identity credentials of the prefix list owner to call CreateResourceShare to create a resource share. Make sure that you set the
AllowExternalTargetsparameter toFalse.
Manage shared prefix lists and principals
The prefix list owner can view the shared prefix lists and principals.
Call ListSharedResources to view shared prefix lists.
Call ListSharedTargets to view the list of principals of shared prefix lists.
The prefix list owner can manage shared prefix lists and principals within a resource share:
Call ListResourceShareAssociations to view prefix lists or principals within the resource share.
Call AssociateResourceShare to add shared prefix lists or principals within the resource share.
Call DisassociateResourceShare to delete shared prefix lists or principals within the resource share.
Terraform
Terraform does not support sharing prefix lists with any account. It supports sharing only within a resource directory. Before you perform the operations, make sure that the management account of the resource directory has enabled resource sharing within the resource directory.
Resources: alicloud_resource_manager_resource_share, alicloud_resource_manager_shared_resource, alicloud_resource_manager_shared_target
Use the identity credentials of the prefix list owner to enable sharing:
# Specify the region provider "alicloud" { region = "cn-hangzhou" } # Specify the resource share name resource "alicloud_resource_manager_resource_share" "example_unit" { resource_share_name = "example_unit_name" } # Specify the shared prefix list resource "alicloud_resource_manager_shared_resource" "example_vsw" { resource_share_id = alicloud_resource_manager_resource_share.example_unit.id resource_id = "pl-bp18t4lsc3e4yd6xxxxx" # The ID of the prefix list to be shared resource_type = "PrefixList" # The resource type is PrefixList } # Specify the user of the shared prefix list resource "alicloud_resource_manager_shared_target" "example_target" { resource_share_id = alicloud_resource_manager_resource_share.example_unit.id target_id = "101xxxxxxxxxxxxxxx" # The UID of the prefix list principal }More information
Billing
The prefix list feature is free of charge.
Supported regions
Area | Regions |
Asia Pacific - China | China (Hangzhou), China (Shanghai), China (Nanjing - Local Region), China (Qingdao), China (Beijing), China (Zhangjiakou), China (Hohhot), China (Ulanqab), China (Shenzhen), China (Heyuan), China (Guangzhou), China (Chengdu), China (Hong Kong), China (Wuhan - Local Region), and China (Fuzhou - Local Region) |
Asia Pacific - Others | Japan (Tokyo), South Korea (Seoul), Singapore, Malaysia (Kuala Lumpur), Indonesia (Jakarta), Philippines (Manila), and Thailand (Bangkok) |
Europe & Americas | Germany (Frankfurt), UK (London), US (Silicon Valley), US (Virginia), and Mexico |
Middle East | UAE (Dubai) and SAU (Riyadh - Partner Region) Important The SAU (Riyadh - Partner Region) region is operated by a partner. |
Quotas
Quota name | Description | Default limit | Increase quota |
vpc_quota_prefixlist_num | The number of prefix lists that can be created by an Alibaba Cloud account. | 10 | Go to the Quota Management page or Quota Center to request a quota increase. |
vpc_quota_prefixlist_cidr_num_per_prefixlist | The number of CIDR entries supported by a prefix list. | 50 | |
vpc_quota_prefixlist_accept_shared_prefixlist_num | The number of shared prefix lists that a principal can accept. | 100 | |
vpc_quota_prefixlist_share_user_num_per_prefixlist | The number of principals to which a prefix list can be shared. | 10 |
For more information about resource sharing quotas, see Limits on resource sharing.