By default, new RDS SQL Server instances cannot be connected from external devices. To ensure security, you must configure IP address whitelists for an RDS instance to allow only trusted IP addresses to access the RDS instance. After you create an RDS instance, we recommend that you immediately configure an IP address whitelist and regularly maintain the whitelist to improve access security. When you configure an IP address whitelist for your RDS instance, the RDS instance continues to run as expected.
To configure whitelists for other engines, see the following:
Scenarios
You must configure an IP address whitelist in the following scenarios:
After you create an RDS instance, you need to add external IP addresses to the whitelist to allow external devices to access the instance.
An RDS instance cannot be connected. You must check whether the IP address whitelists of the RDS instance are correctly configured.
The following table provides the IP address whitelist configurations in various connection scenarios.
Connection type | Network type | IP address whitelist setting |
Connect an Elastic Compute Service (ECS) instance to an RDS instance | The ECS instance and the RDS instance reside in the same virtual private cloud (VPC). This is the recommended connection scenario. | Add the private IP address of the ECS instance to an IP address whitelist of the RDS instance. |
The ECS instance and the RDS instance reside in different VPCs. | Instances in different VPCs cannot communicate with each other over internal networks. In this case, make sure that the ECS instance and the RDS instance reside in the same VPC and add the private IP address of the ECS instance to an IP address whitelist of the RDS instance. | |
Connect containers in an ACK cluster to an RDS instance | The ACK cluster and the RDS instance reside in the same virtual private cloud (VPC). This is the recommended connection scenario. |
You can view the Pod IP address and node IP address on the pod page of the target ACK cluster. |
The ACK cluster and the RDS instance reside in different VPCs. | Instances in different VPCs cannot communicate with each other over internal networks. In this case, make sure that the ACK cluster and the RDS instance reside in the same VPC and add the IP address of the ACK cluster where the application is located to an IP address whitelist of the RDS instance.
| |
Connect a self-managed host outside the cloud to an RDS instance | N/A | Add the public IP address of the self-managed host outside the cloud to an IP address whitelist of the RDS instance. Note The applications that run on the self-managed host connect to the public endpoint of your RDS instance. |
Usage notes
A maximum of 50 IP address whitelists can be configured for each RDS instance.
You can delete the entries in the IP address whitelist that is labeled default but you cannot delete the whitelist. The IP address whitelist that is labeled default contains only the IP address 127.0.0.1. This indicates that no IP addresses can access the RDS instance.
Do not modify or delete the IP address whitelists that are automatically generated for other Alibaba Cloud services. If you delete the IP address whitelist that is automatically generated for an Alibaba Cloud service, the Alibaba Cloud service cannot connect to the RDS instance. For example, the IP address whitelist labeled ali_dms_group is generated for Data Management (DMS), and the IP address whitelist labeled hdm_security_ips is generated for DAS.
ImportantIf an RDS instance is created after December 2020, the IP address whitelist that is labeled hdm_security_ips is invisible to users. This prevents the IP address whitelist from being unintentionally modified or deleted.
Procedure
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
In the navigation pane on the left, click Whitelist and SecGroup.
On the Whitelist Settings tab, you can view the mode of the IP address whitelist.
NoteExisting RDS instances may run in enhanced whitelist mode. All new RDS instances run in standard whitelist mode.
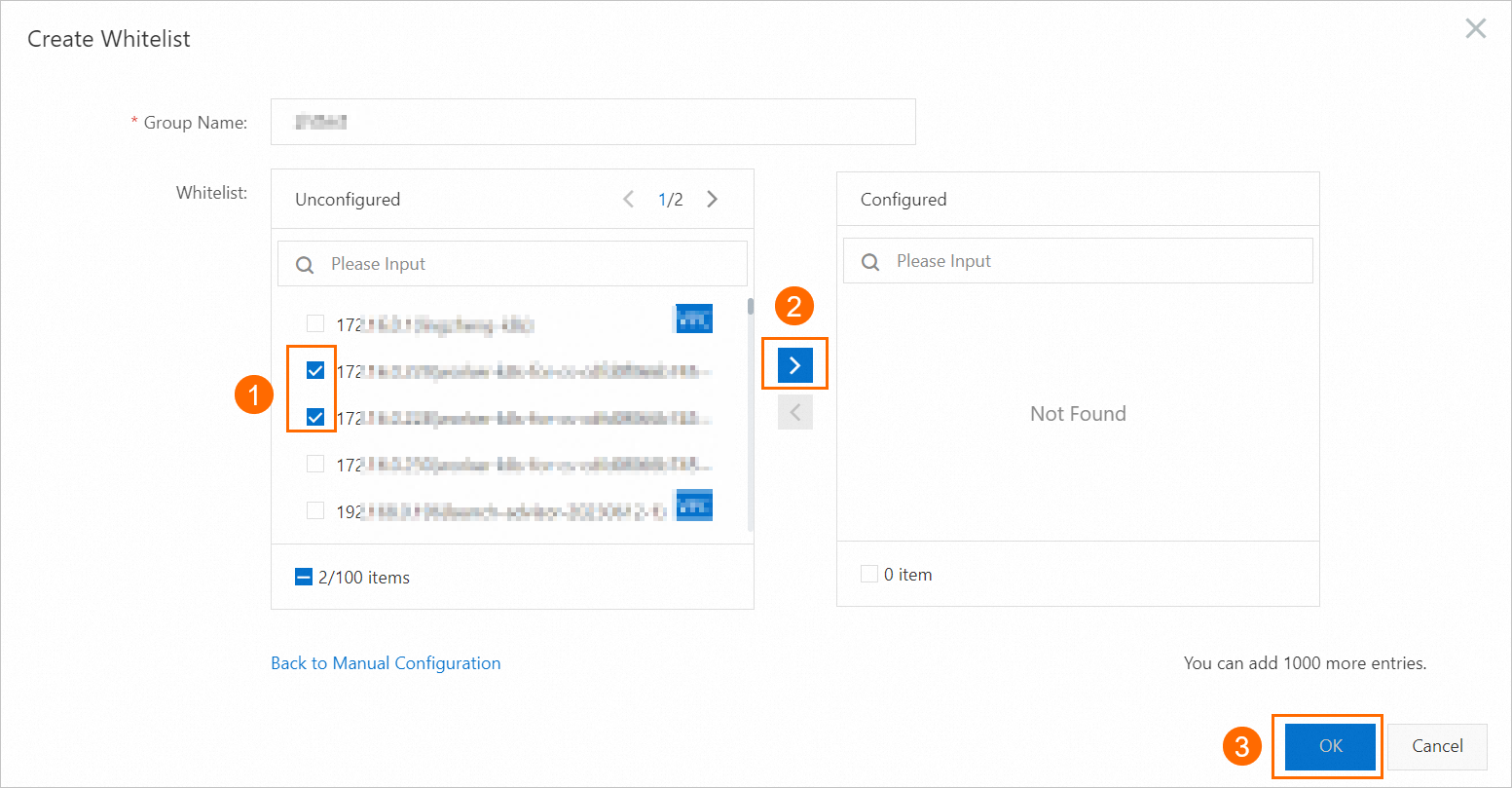
Click Create Whitelist. In the dialog box that appears, configure the Whitelist Name parameter, add the IP address of the application server to the whitelist, and then click OK.
NoteYou can also click Modify to the right of the default group to change the whitelist within the group.
You must separate multiple IP addresses and CIDR blocks with commas (,). Do not add spaces before and after each comma. Example:
192.XXX.XXX.1,172.XXX.XXX.9.A maximum of 1,000 IP addresses and CIDR blocks can be configured for each RDS instance. If you want to add many IP addresses, we recommend that you merge the IP addresses into CIDR blocks, such as 10.10.10.0/24.
If the RDS instance runs in standard whitelist mode, you do not need to take note of special considerations when you configure IP address whitelists for the RDS instance. If the RDS instance runs in enhanced whitelist mode, you must take note of the following considerations when you configure IP address whitelists for the RDS instance:
Add the public IP addresses of ECS instances or the private IP addresses of classic network-type ECS instances to the IP address whitelists of the classic network type.
Add the private IP addresses of VPC-type ECS instances to the IP address whitelists of the VPC network type.
Optional. In the Create Whitelist dialog box, click Add Internal IP Address of ECS Instance. In the dialog box that appears, view the IP addresses of all the ECS instances that are created within your Alibaba Cloud account. Then, add the required IP addresses to the IP address whitelist that you want to configure.
What to do next
Appendix: Obtain the IP address of the application server
You must obtain the correct IP address based on your business scenario and add the IP address to the IP address whitelist. The following table describes IP addresses that are required in various scenarios.
Scenario | IP address to be obtained | How to obtain |
Requirements for internal network access | Corresponding IP address of the container in the ACK cluster |
You can view the Pod IP address and node IP address on the pod page of the target ACK cluster. |
Private IP address of the ECS instance |
| |
You want to connect to the RDS instance from an ECS instance that is inaccessible over an internal network. | Public IP address of the ECS instance | |
You want to connect to the RDS instance from an on-premises device. | Public IP address of the on-premises device | On the on-premises device, use a search engine such as Google to search for IP. Note The IP address that is obtained using this method may be inaccurate. You can use other methods to obtain the IP address. |
