AWS IAM Users Complete Guide
1. What is an IAM User?
An IAM User is an identity within AWS that represents a single person, system, or application requiring access to AWS resources.
Unlike IAM Roles, which provide temporary credentials, IAM Users have long-term credentials (passwords for console access or access keys for programmatic access).
IAM Users are scoped to one AWS account and are fundamental to managing identity and access in AWS.
2. Core Characteristics of IAM Users
-
Authentication methods
- Console access → username + password
- Programmatic access → access key ID + secret access key
Permissions → Defined through policies (direct or via groups)
Long-term identity → Permanent until explicitly deleted
Tags → Can be tagged for cost allocation, auditing, or automation
Security support → MFA, password policies, key rotation
Management → Users can belong to multiple groups and have multiple policies
3. Common Problems With IAM Users
🔴 Problem 1: Directly attached policies
Attaching policies to each user separately, inconsistent permissions, management overhead.
🔴 Problem 2: Access key leakage
Developers embedding keys in code repositories → critical security risk.
🔴 Problem 3: Over-privileged accounts
Users being given AdministratorAccess for convenience → violates least privilege principle.
🔴 Problem 4: Inactive users
Employees leaving the company but accounts not removed → insider threat.
🔴 Problem 5: Scalability limits
In large organizations, creating an IAM user for every employee doesn’t scale.
4. Solutions and Best Practices
✅ Policy Management
- Assign users to groups and attach policies to groups, not individuals.
- Enforce least privilege principle: grant only the permissions required.
- Use IAM Access Analyzer to identify unused or overly broad permissions.
✅ Security Hardening
- Enable MFA for all IAM users, especially privileged accounts.
- Rotate passwords and access keys regularly.
- Prohibit hard-coded access keys in applications → use IAM Roles or AWS Secrets Manager instead.
✅ Lifecycle Management
- Run IAM Credential Reports regularly to detect inactive users and outdated keys.
- Automate user provisioning/de-provisioning with federated identity providers (e.g., AWS SSO, Active Directory).
- Maintain auditability with CloudTrail logs to monitor IAM user activity.
✅ Industry Practice
- Limit IAM Users to a small number of admin/break-glass accounts.
- For workforce authentication, integrate with SSO or Identity Federation.
5. Industry Examples
-
Startup:
- A small dev team creates IAM Users for each developer.
- Users are added to groups like Developers with managed policies (e.g.,
AmazonS3ReadOnlyAccess).
-
Enterprise:
- 10,000+ employees → IAM Users become unmanageable.
- Instead, the company uses federation with SAML/Active Directory. Only a few IAM Users exist for special purposes (e.g., automation, break-glass admin).
-
Financial Sector:
- Strict compliance requires tagging IAM Users by department and cost center.
- All IAM Users are required to use MFA.
- Access keys rotated every 90 days.
-
DevOps Automation:
- A pipeline that previously used IAM User access keys was migrated to IAM Roles attached to EC2/CodeBuild.
- Result: eliminated secret sprawl and reduced risk.
6. Interview Questions on IAM Users
Basic Level
- What is an IAM User?
- How does an IAM User authenticate with AWS?
- What’s the difference between an IAM User and an IAM Role?
Intermediate Level
- How do you enforce least privilege with IAM Users?
- What is the best way to manage permissions for a large group of IAM Users?
- How would you secure IAM User access keys used by applications?
Advanced Level
- What problems arise from using IAM Users at scale in enterprises?
- How do IAM Users fit into an AWS Organization with multiple accounts?
- How do you design a secure strategy for IAM User lifecycle management?
Pre-checks (before you start)
- You must be signed in as an IAM user with
iam:CreateUseror as an admin. - Decide: console access? programmatic access? both? Which groups/policies? Tags? MFA requirement?
Console Steps
- Sign in to the AWS Management Console (use an account that has IAM rights).
Open the IAM console: Services → Security, Identity, & Compliance → IAM.

In the left navigation choose Users → Add users.
Enter username (e.g.,
dev-alice).-
Select AWS access type:
- Programmatic access → creates access key ID + secret access key.
- Console access → enable password (auto-generated or custom).

- Click Next: Permissions → choose group, clone from user, or attach policies directly.
Click Next: Tags → add metadata like
Team=Platform.
.
- Post-creation → Enable MFA and assign correct groups.
CLI Examples
Create the user
aws iam create-user --user-name dev-user1 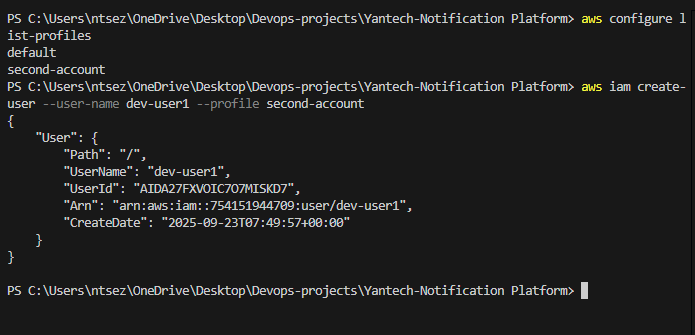 ### Create console password (login profile)
bash
aws iam create-login-profile \
--user-name dev-user1 \
--password 'ComplexTempP@ssw0rd!' \
--password-reset-required \
--profile second-account
Create a group and attach a managed policy
aws iam create-group --group-name Developers aws iam attach-group-policy \ --group-name Developers \ --policy-arn arn:aws:iam::aws:policy/AmazonS3ReadOnlyAccess 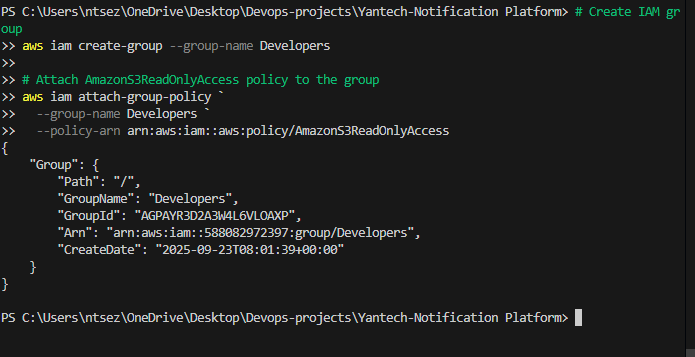 ### Add user to group
bash
aws iam add-user-to-group --user-name dev-user1 --group-name Developers
Create programmatic access keys
aws iam create-access-key --user-name dev-user1 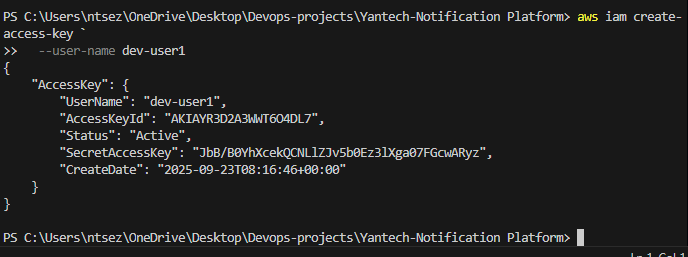 ### Disable an access key
bash
aws iam update-access-key \
--user-name dev-user1 \
--access-key-id AKIA... \
--status Inactive
Delete user (cleanup order)
aws iam delete-access-key --user-name dev-user1 --access-key-id AKIA... aws iam delete-login-profile --user-name dev-user1 aws iam remove-user-from-group --user-name dev-user1 --group-name Developers aws iam detach-user-policy --user-name dev-user1 --policy-arn <policy-arn> aws iam delete-user --user-name dev-user1 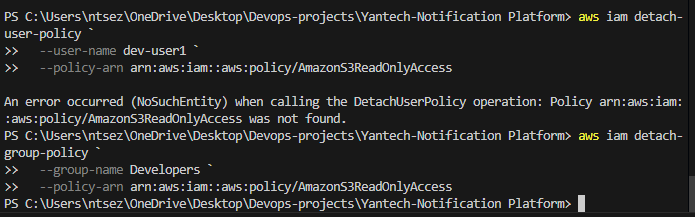 ### Automation & Reporting Generate Credential Report
bash
aws iam generate-credential-report
aws iam get-credential-report --query "Content" --output text | base64 --decode > credential-report.csv
🙏 Thanks for reading! If you found this helpful, drop a ❤️, leave a comment, or follow me here on Dev.to for more deep dives into AWS and DevOps. Your support means a lot and keeps me motivated to share more. 🚀
✨ Wrapping Up
IAM Users are powerful but must be managed carefully. By applying least privilege, enabling MFA, and automating lifecycle management, you can build a stronger security posture for your AWS environment.
📌 I wrote this because many new cloud engineers (and even experienced teams) often overlook IAM fundamentals. Mastering these basics early saves a lot of headaches down the road.
🙏 Thanks for reading! If this guide helped you, don’t forget to:
❤️ Leave a reaction and follow for more AWS/DevOps guides.
💬 Drop your questions or experiences in the comments — I’d love to hear how you manage IAM in your projects.
📢 Share this post with your team, co-workers, or community so we can all grow together.
🚀 Stay tuned for the next part in the AWS IAM Deep Dive series!










Top comments (0)