1. rancher、kubernetes-dashboard等应用需要通过https方式访问,所以此次部署将开启traefik对https的支持。
2. 基于之前的rancher HA是部署在cattle-system命名空间下的,所以此次同样将traefik部署在cattle-system命名空间下,并且使用同样的tls证书。
RBAC清单文件traefik-rbac.yaml如下:
--- apiVersion: v1 kind: ServiceAccount metadata: name: traefik-ingress-controller namespace: cattle-system --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-ingress-controller rules: - apiGroups: - "" resources: - services - endpoints - secrets verbs: - get - list - watch - apiGroups: - extensions resources: - ingresses verbs: - get - list - watch --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: traefik-ingress-controller roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: traefik-ingress-controller subjects: - kind: ServiceAccount name: traefik-ingress-controller namespace: cattle-system
应用清单文件
[root@k8s-master03 traefik]# kubectl apply -f traefik-rbac.yaml serviceaccount/traefik-ingress-controller created clusterrole.rbac.authorization.k8s.io/traefik-ingress-controller created clusterrolebinding.rbac.authorization.k8s.io/traefik-ingress-controller created
damonset清单文件traefik-ds.yaml如下:
--- kind: ConfigMap apiVersion: v1 metadata: name: traefik-conf namespace: cattle-system data: traefik.toml: | insecureSkipVerify = true defaultEntryPoints = ["http","https"] [entryPoints] [entryPoints.http] address = ":80" [entryPoints.https] address = ":443" [entryPoints.https.tls] [[entryPoints.https.tls.certificates]] CertFile = "/ssl/tls.crt" KeyFile = "/ssl/tls.key" --- kind: DaemonSet apiVersion: extensions/v1beta1 metadata: name: traefik-ingress-controller namespace: cattle-system labels: k8s-app: traefik-ingress-lb spec: template: metadata: labels: k8s-app: traefik-ingress-lb name: traefik-ingress-lb spec: serviceAccountName: traefik-ingress-controller terminationGracePeriodSeconds: 60 hostNetwork: true volumes: - name: ssl secret: secretName: tls-rancher-ingress - name: config configMap: name: traefik-conf containers: - image: traefik name: traefik-ingress-lb ports: - name: http containerPort: 80 hostPort: 80 - name: admin containerPort: 8080 securityContext: privileged: true args: - --configfile=/config/traefik.toml - -d - --web - --kubernetes volumeMounts: - mountPath: "/ssl" name: "ssl" - mountPath: "/config" name: "config" --- kind: Service apiVersion: v1 metadata: name: traefik-ingress-service namespace: cattle-system spec: selector: k8s-app: traefik-ingress-lb ports: - protocol: TCP port: 80 name: web - protocol: TCP port: 8080 name: admin - protocol: TCP port: 443 name: https #type: NodePort
应用清单文件
[root@k8s-master03 traefik]# kubectl apply -f traefik-ds.yaml configmap/traefik-conf created daemonset.extensions/traefik-ingress-controller created service/traefik-ingress-service created
ingress清单文件traefik-ui.yaml如下:
apiVersion: v1 kind: Service metadata: name: traefik-web-ui namespace: cattle-system spec: selector: k8s-app: traefik-ingress-lb ports: - name: web port: 80 targetPort: 8080 --- apiVersion: extensions/v1beta1 kind: Ingress metadata: name: traefik-web-ui namespace: cattle-system spec: rules: - host: traefik-ui.sumapay.com http: paths: - path: / backend: serviceName: traefik-web-ui servicePort: web
应用清单文件
[root@k8s-master03 traefik]# kubectl apply -f traefik-ui.yaml service/traefik-web-ui created ingress.extensions/traefik-web-ui created
[root@k8s-master01 ~]# kubectl get pods -n cattle-system NAME READY STATUS RESTARTS AGE cattle-cluster-agent-594b8f79bb-pgmdt 1/1 Running 5 11d cattle-node-agent-lg44f 1/1 Running 0 11d cattle-node-agent-zgdms 1/1 Running 5 11d rancher2-9774897c-622sc 1/1 Running 0 9d rancher2-9774897c-czxxx 1/1 Running 0 9d rancher2-9774897c-sm2n5 1/1 Running 1 9d traefik-ingress-controller-hj9nc 1/1 Running 0 142m traefik-ingress-controller-vxcgt 1/1 Running 0 142m [root@k8s-master01 ~]# kubectl get svc -n cattle-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE rancher2 ClusterIP 10.111.16.80 <none> 80/TCP 9d traefik-ingress-service ClusterIP 10.111.121.27 <none> 80/TCP,8080/TCP,443/TCP 143m traefik-web-ui ClusterIP 10.103.112.22 <none> 80/TCP 136m [root@k8s-master01 ~]# kubectl get ingress -n cattle-system NAME HOSTS ADDRESS PORTS AGE rancher2 rancher.sumapay.com 80, 443 9d traefik-web-ui traefik-ui.sumapay.com 80 137m
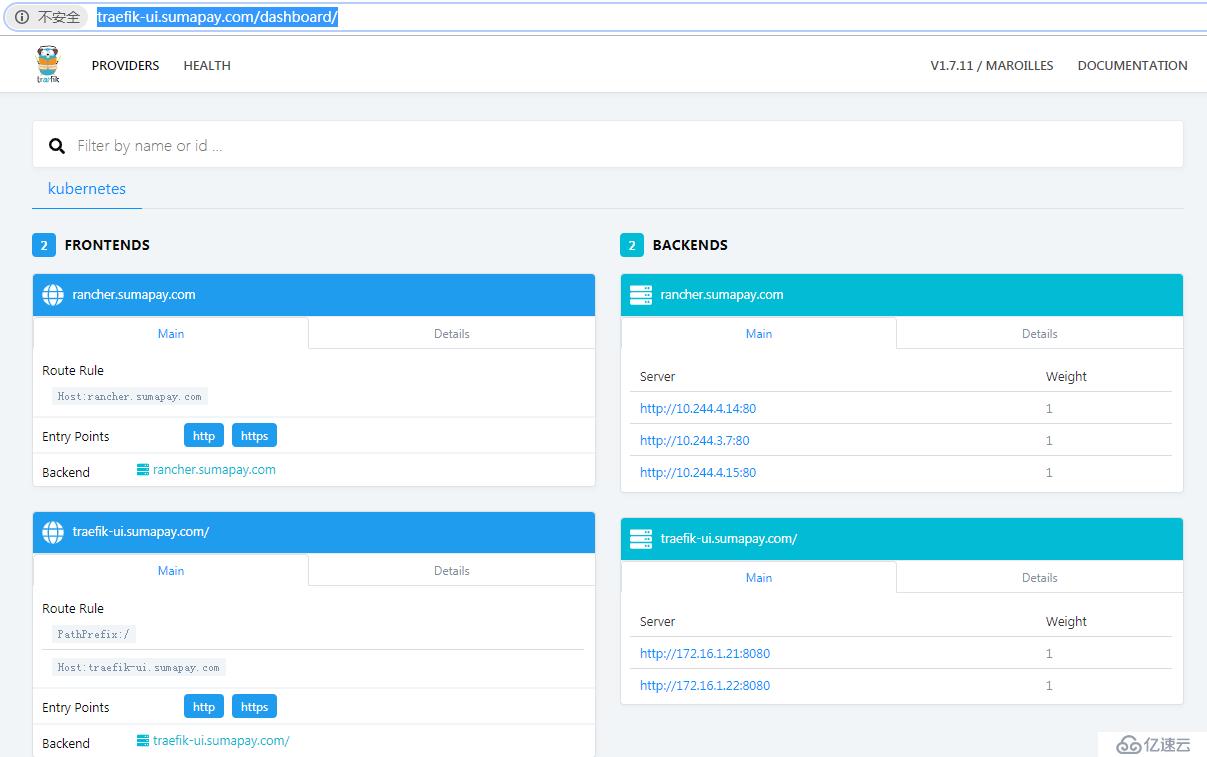
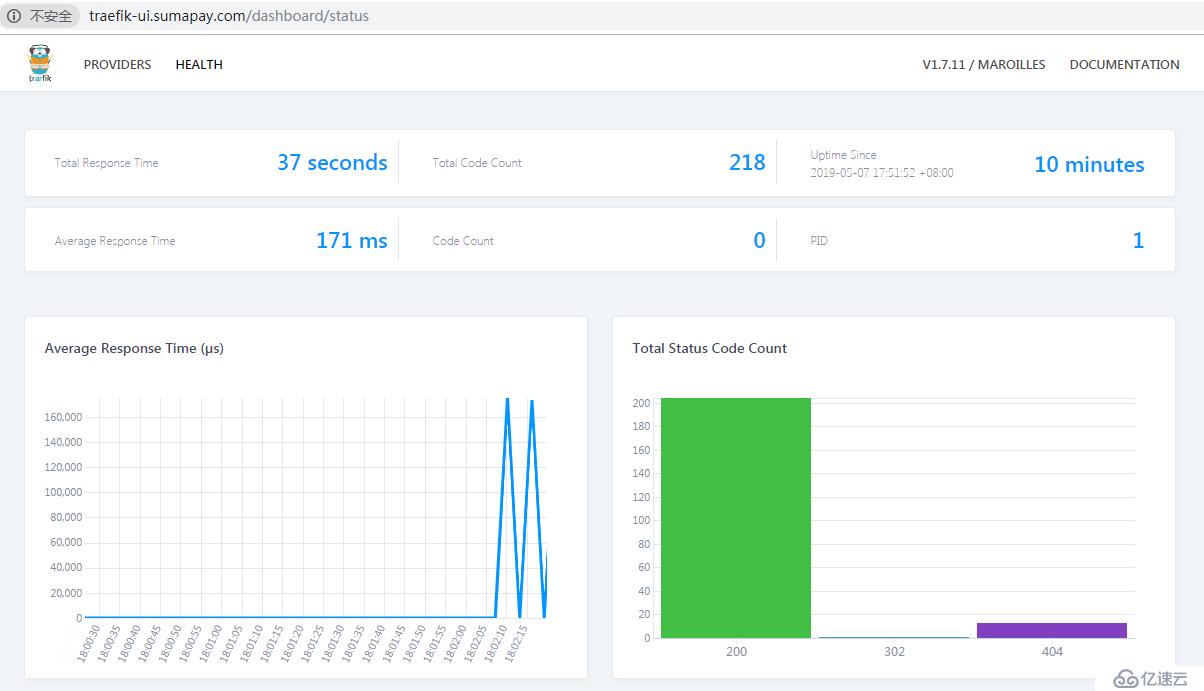
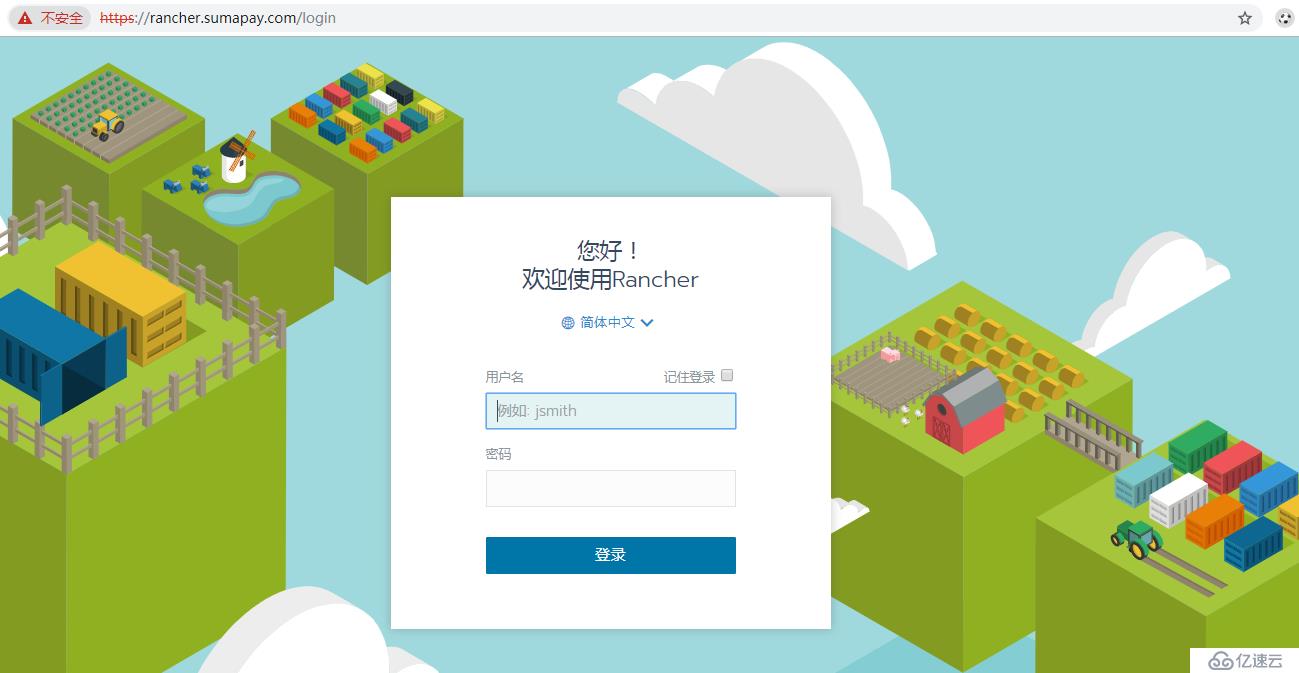
将域名映射到外部负载均衡IP后,就可以通过域名访问traefik UI和rancher HA服务了。
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。