This document discusses a solution for wireless communication within sensor networks that eliminates the need for pre-shared secrets, addressing the circular dependency problem (CDP) using the Advanced Encryption Standard (AES) algorithm. The proposed system improves communication efficiency, security, and eliminates data loss, making it suitable for environments where nodes frequently change. Simulation results demonstrated that AES offers better performance in terms of energy consumption, end-to-end delay, and overall reliability compared to existing methods.

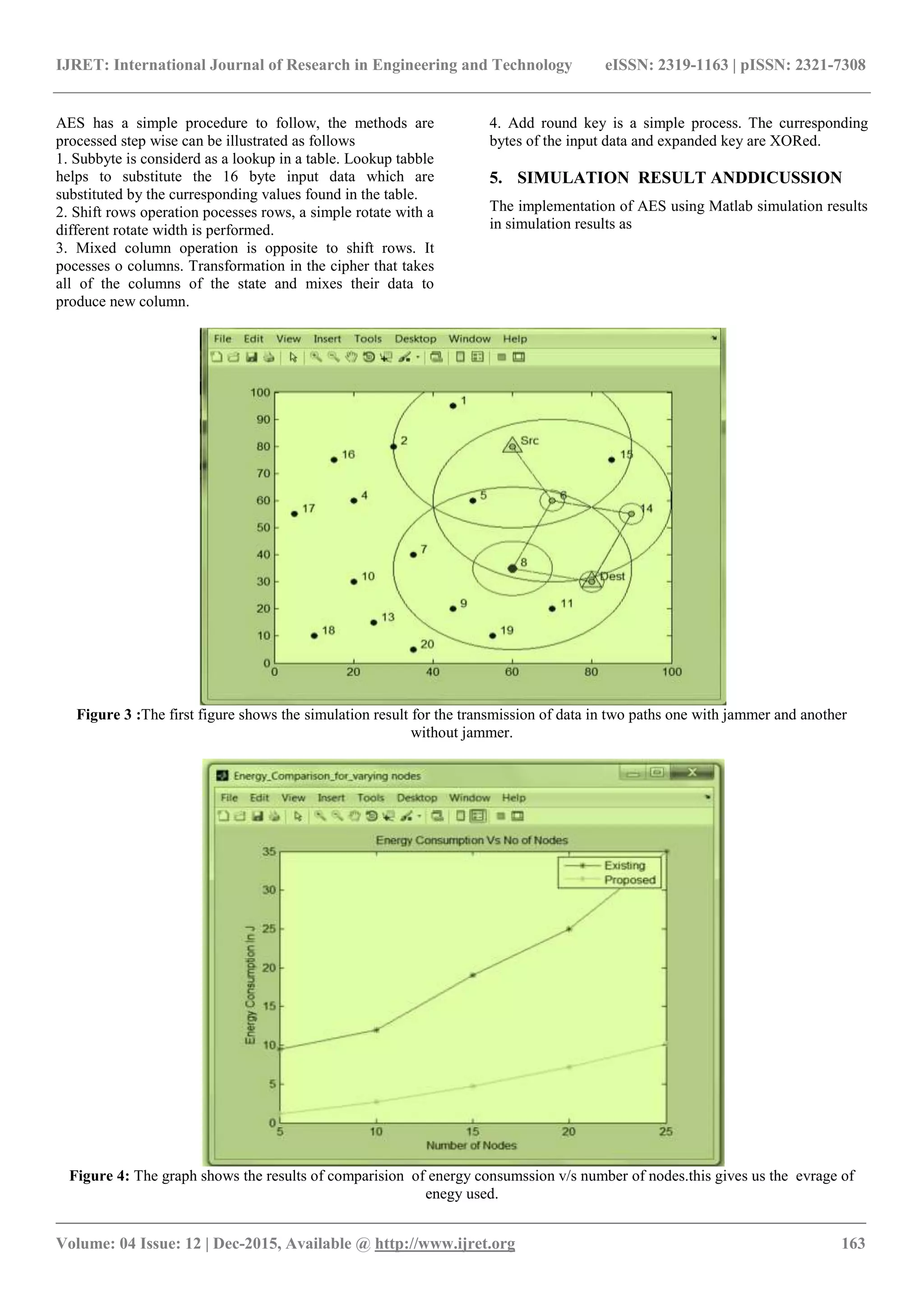
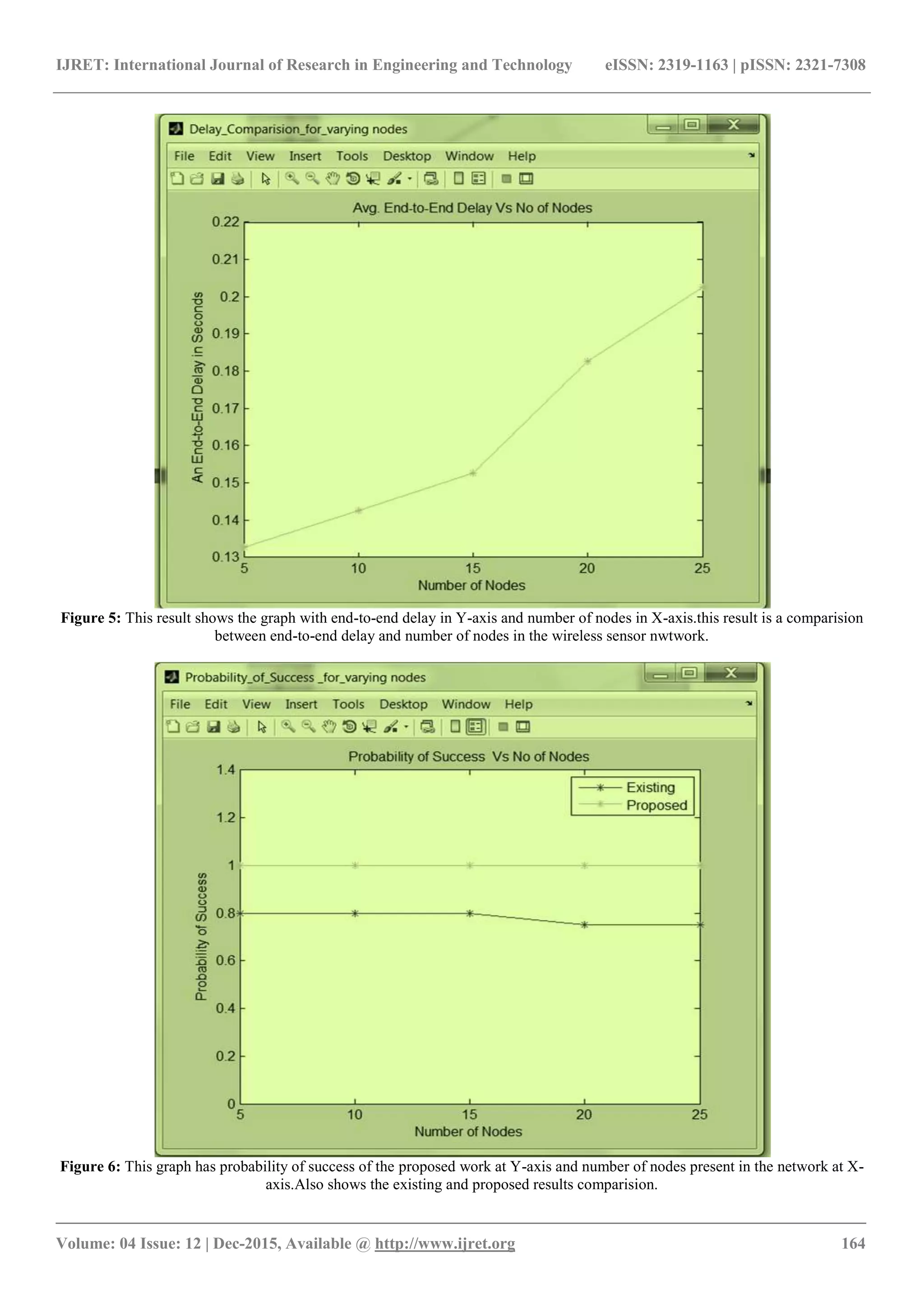
![IJRET: International Journal of Research in Engineering and Technology eISSN: 2319-1163 | pISSN: 2321-7308 _______________________________________________________________________________________ Volume: 04 Issue: 12 | Dec-2015, Available @ http://www.ijret.org 165 All these simulation results displays the performance of proposed work interms of energy,time and security. Thse results also compares the existing and proposed work result which makes the user to know which is more efficient method to use. Analyzation of these simulation results conclude dat AES (Advanced Encryption Standard) is a better algorithm than any other existig method in tems of efficiency including security. 6. CONCLUSION The propsed work lasts with accuracy ,efficiency and security. Use of AES algorithm gives the wireless communication with less complexity and high security data transmission in a wireless sensor network. We gain a transimmion with no data loss. The above simulation results have been analyzed in MATLAB envirnment. REFERENCES [1]G.Lin and G. Noubir, “On Link Layer Denial of Service Data Wireless LANs”, Wireless comm.. Mobile Computing, Vol 5, no.3, pp 273-284, 2005. [2]Wenyuan Xu, Wade Trappe, Yanyong Zhang, “Jamming Sensor Networks: Attack and DfenceStrategis”, IEEE Network, vol.20,no.3, pp. 41-47, 2006. [3]William Stallings, “Cryptography and network security principles and practices”, pp 134-165. 2007. [4]Radhapoovendra,Minggyan Li, Koutsopouls,” Optimal jamming attacks &network defense policies in wireless sensor network”,Proc.IEEE INFOCOM, 2007. [5]MarioStrasser, Christina popper, Srdjancapkun, Mario Cagalji, “Jamming-resistance Key Establishment using Uncoordinating Frequency Hopping”, Proc.IEEESymp.Security and Privacy (ISSP) 2008. [6]A.Cassola, T.Jin, G.Noubir, and B>Thapa, “Spread Spectrum Communication without Any pre-Shared Secrets,” technical report, http://www.ccs.neu.edu/home/bthapa/techreport/trek.pdf, 2013 [7]Ettus Research, “Universal Software Radio Peripheral,” http://www.ettus.com, 2013.](https://image.slidesharecdn.com/wirelesscommunicationwithoutpre-sharedsecretsusingspreadspectrumtechnique-160919102947/75/Wireless-communication-without-pre-shared-secrets-using-spread-spectrum-technique-5-2048.jpg)