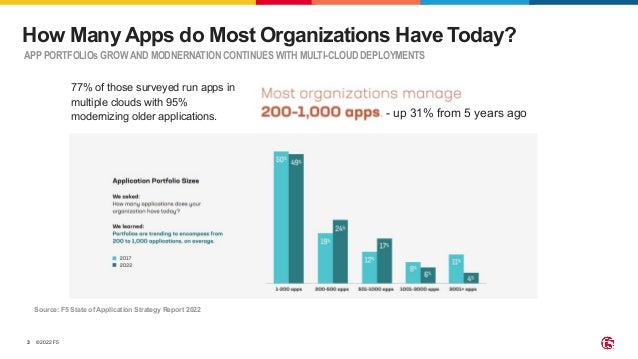
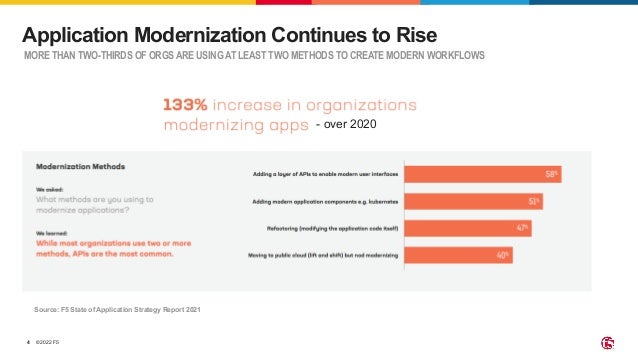
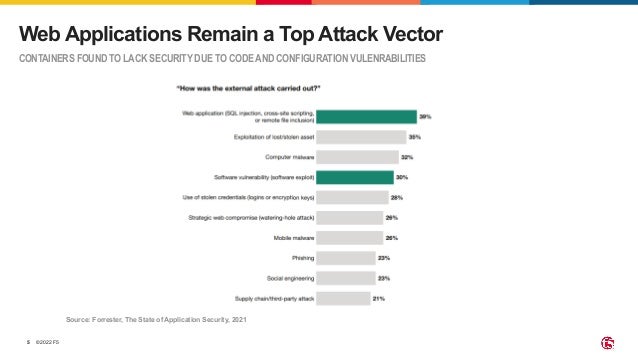
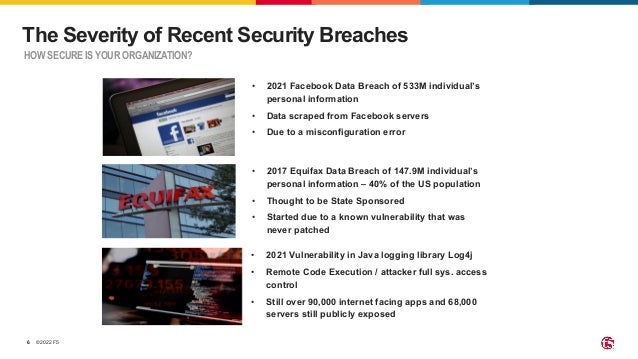
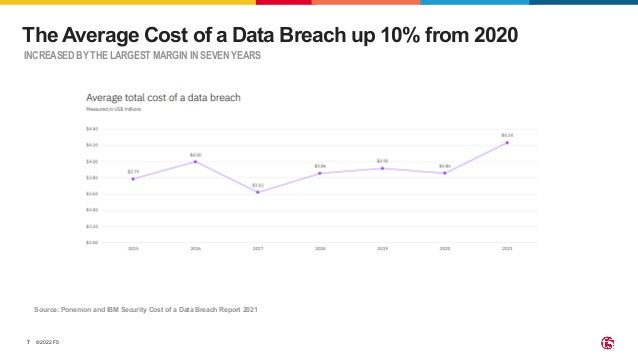
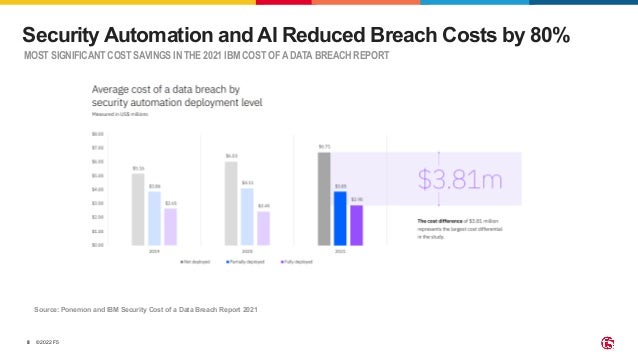
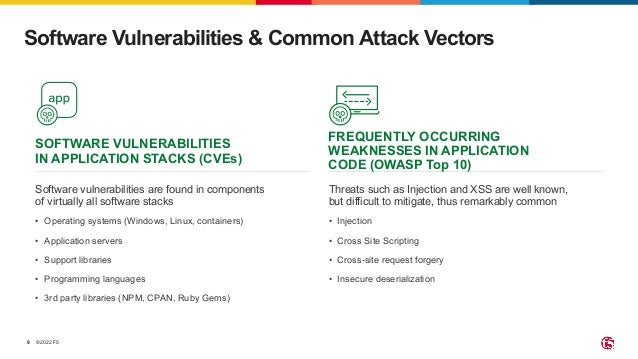
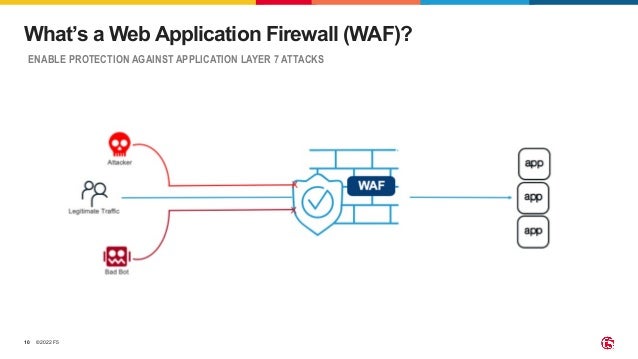
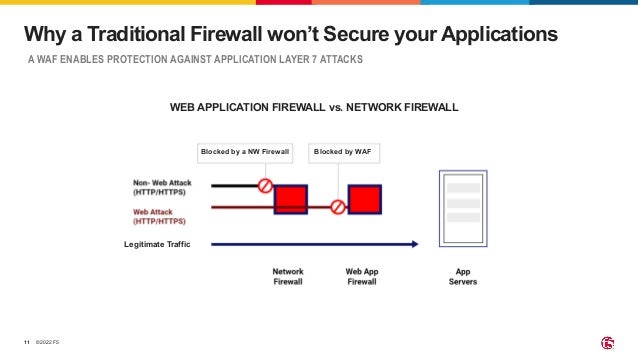
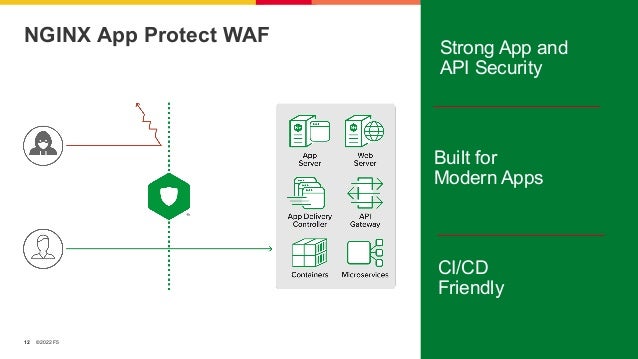
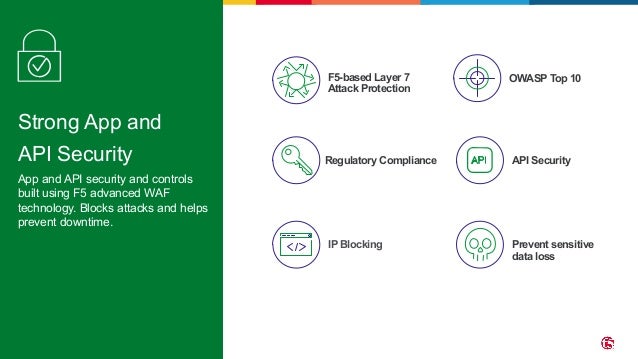
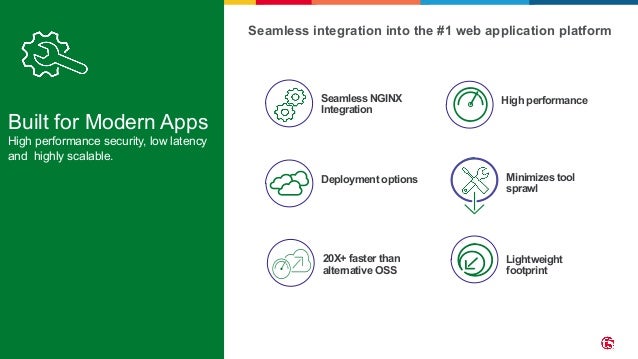
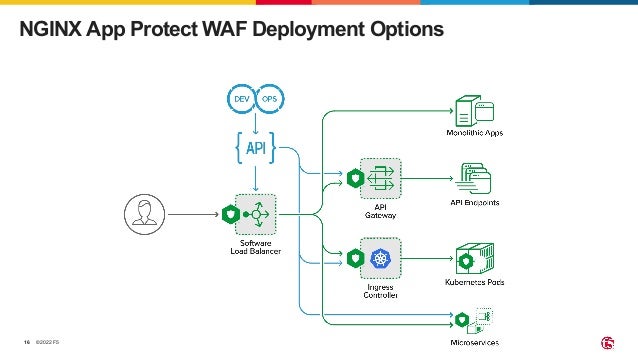
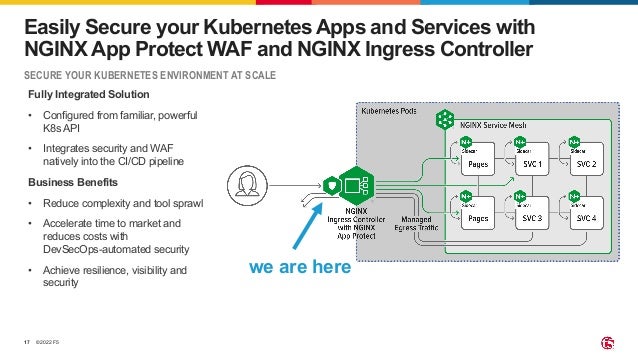
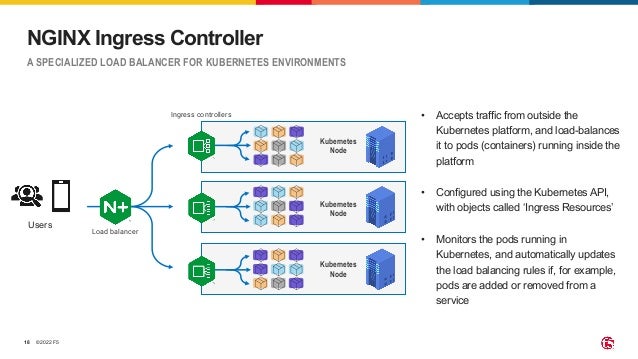
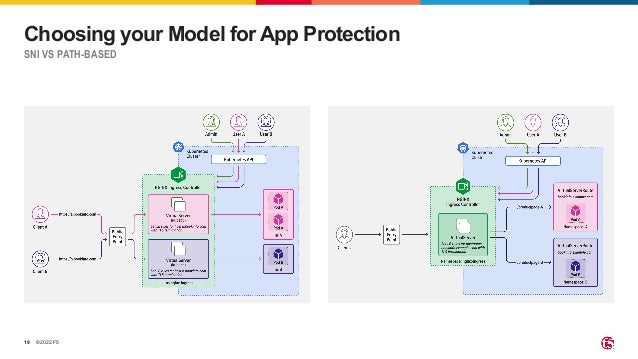
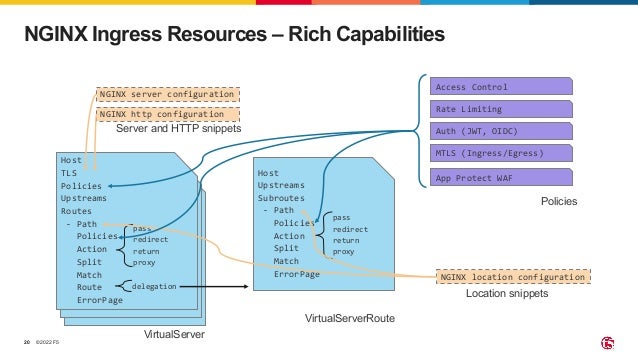
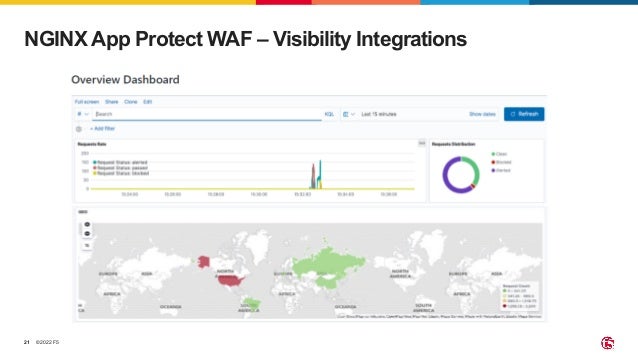
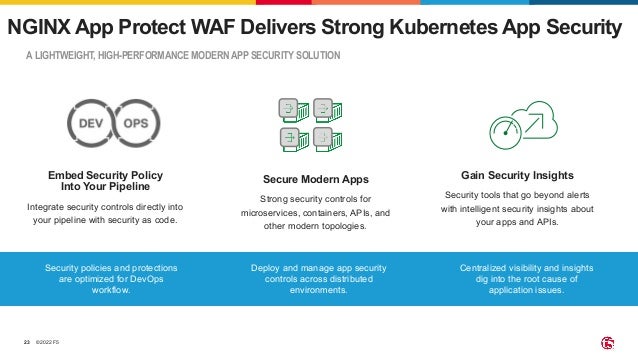
The document outlines the necessity of securing Kubernetes applications using NGINX App Protect WAF and Ingress Controller to mitigate vulnerabilities and prevent breaches. It discusses the rise in application usage across multiple clouds, highlights the increasing cost of data breaches, and emphasizes the importance of web application firewalls for modern application security. The document also details the integration of security into CI/CD pipelines to enhance DevOps initiatives and improve overall application security without sacrificing performance.