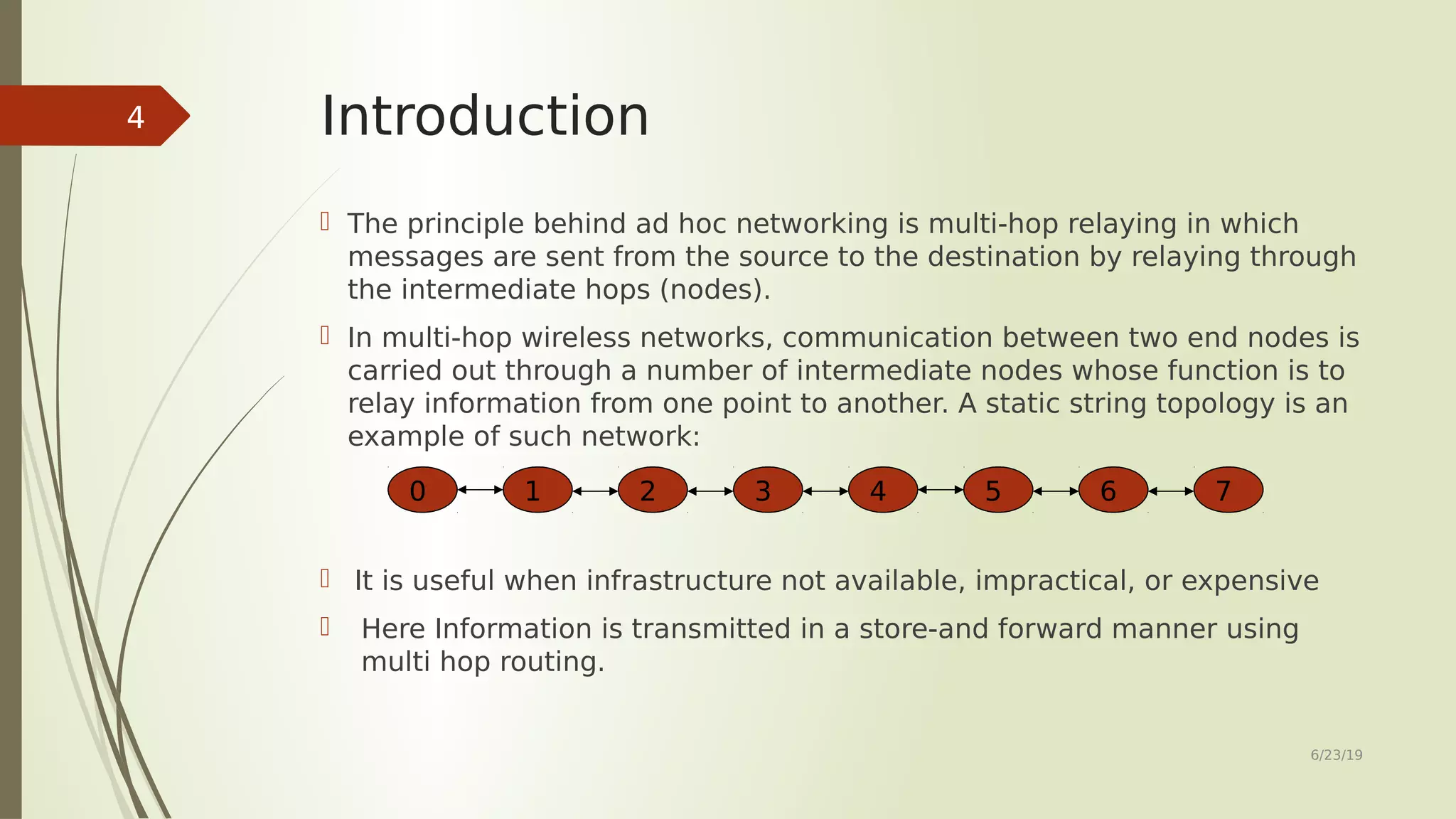
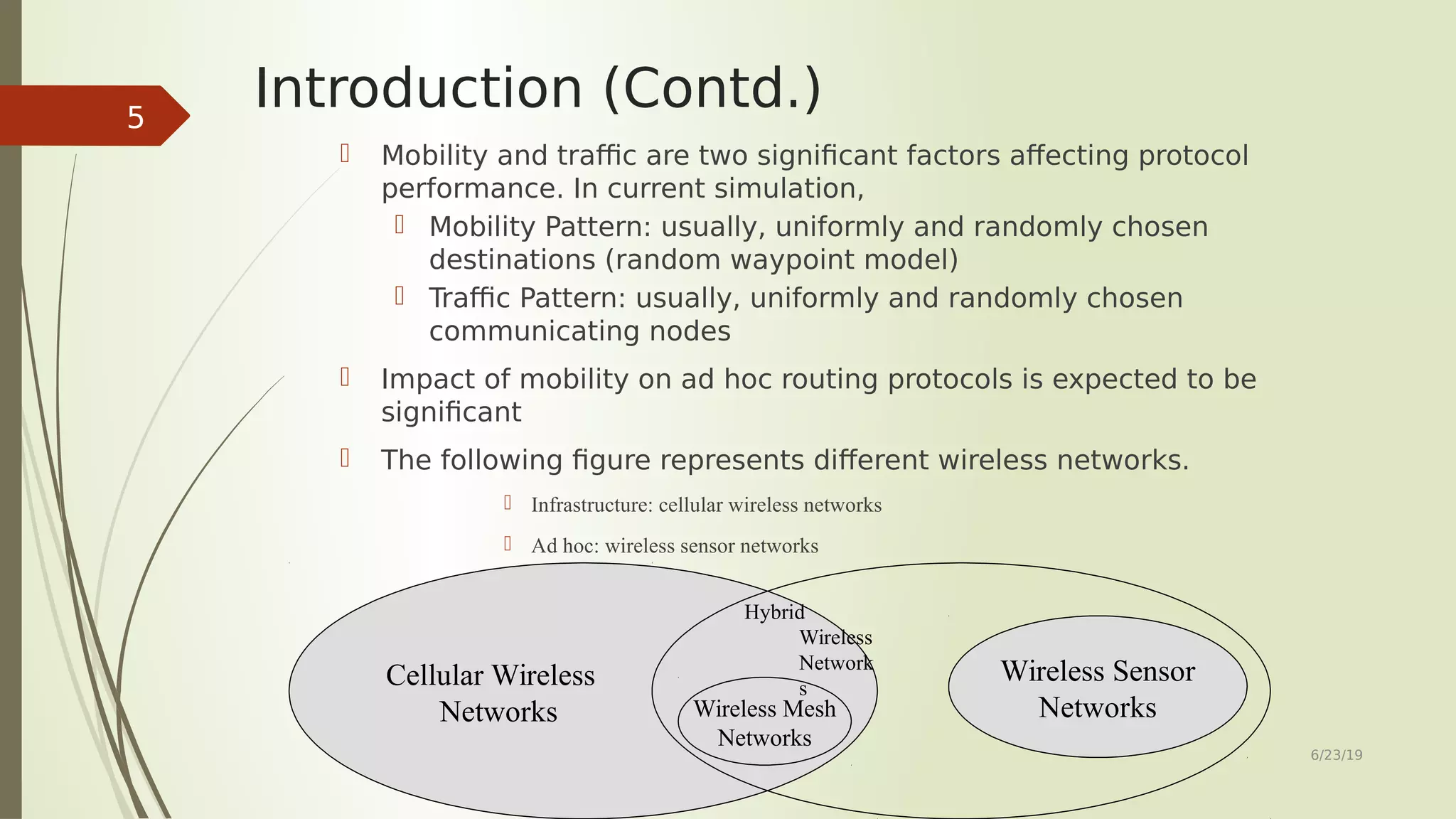
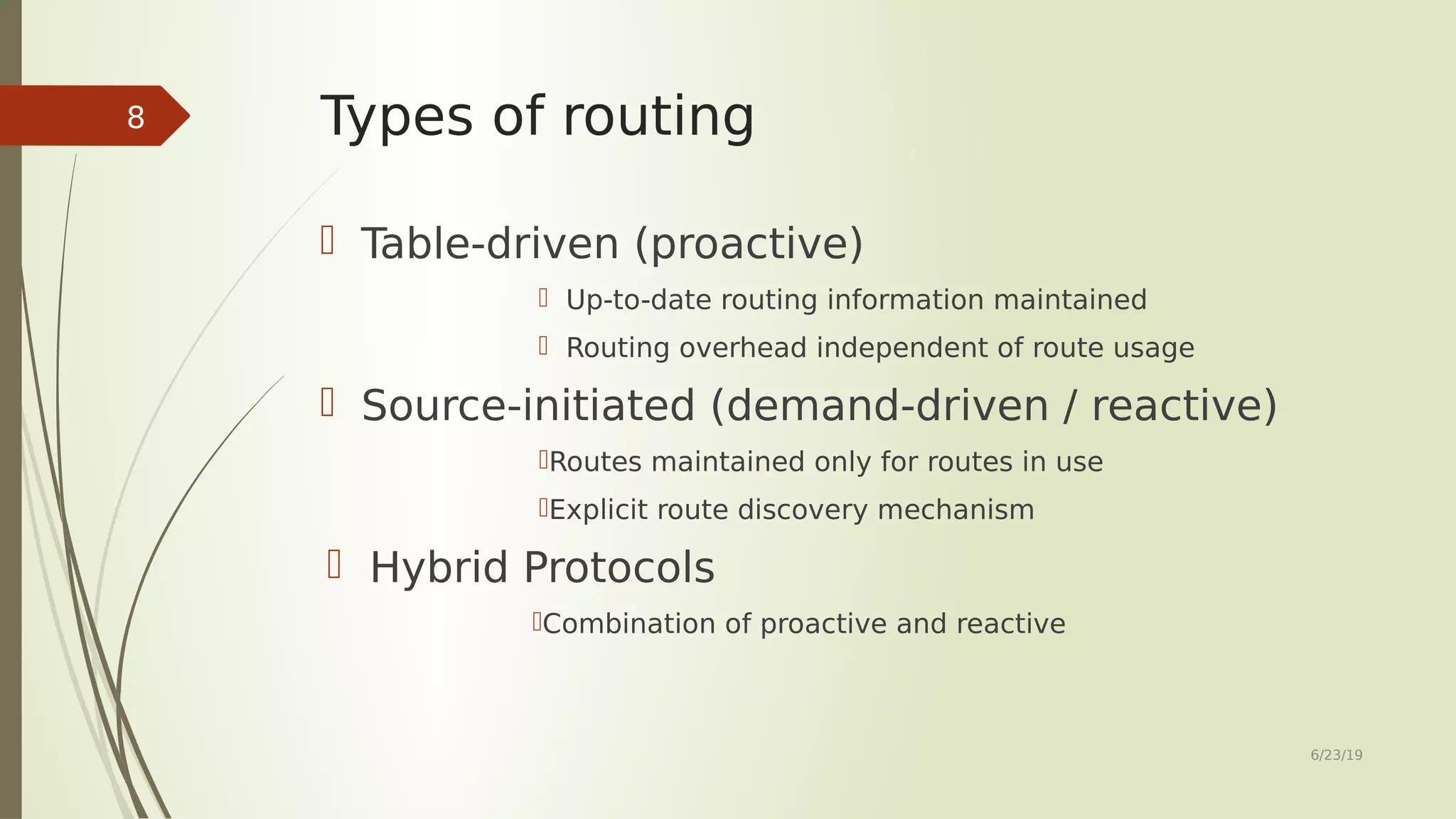
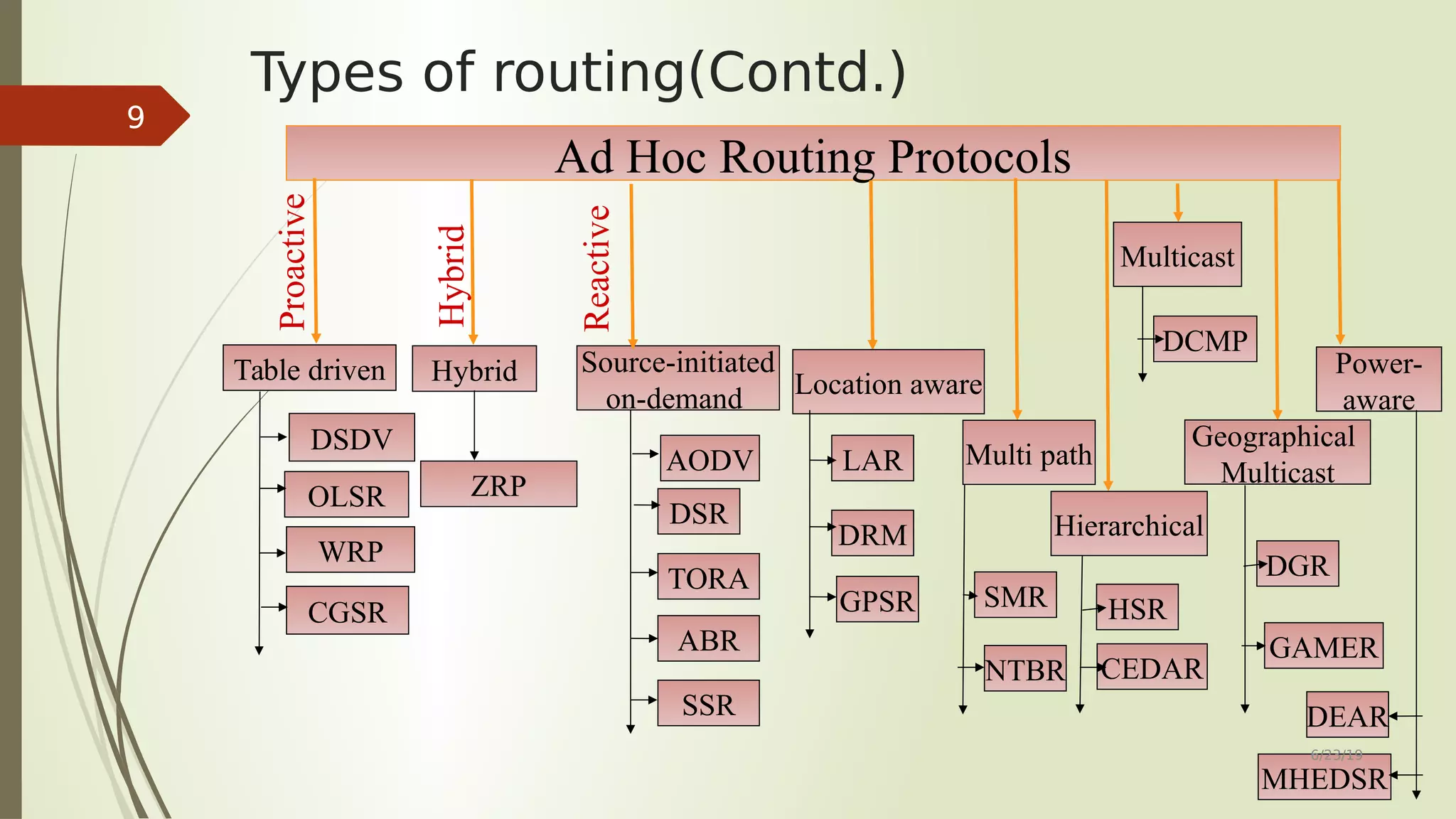
This document provides an overview of routing protocols in ad hoc networks. It begins with an abstract describing the objectives of surveying and comparing different classes of ad hoc routing protocols. The document then outlines the topics to be covered, including the characteristics, applications, and types of ad hoc routing protocols. Several representative routing protocols are described in detail, including table-driven, hybrid, source-initiated, location-aware, multipath, hierarchical, multicast, and power-aware protocols. The document concludes by discussing future work related to improving reusability and security of ad hoc routing protocols.








![References [1] J.-D. Abdulai, M. Ould-Khaoua, L. Mackenzie, Adjusted probabilistic route discovery in mobile ad hoc networks, Computers and Electrical Engineering 35 (1) (2009) 168–182. [2] P. Papadimitratos and Z.J. Haas, “Secure Link State Routing for Mobile Ad Hoc Networks,” Proc. IEEE Workshop on Security and Assurance in Ad Hoc Networks, IEEE Press, 2003, pp. 27–31. [3] D.B. Johnson, “Routing in Ad Hoc Networks of Mobile Hosts,” Proc. IEEE Workshop on Mobile Computing Systems and Applications (WMCSA’94), IEEE Press, 1994, pp. 158–163. [4] Suraj Sharma, Deepak Puthal, Sabah Tazeen, Mukesh Prasad, Albert Y. Zomaya, "MSGR: A Mode-Switched Grid-Based Sustainable Routing Protocol for Wireless Sensor Networks", Access IEEE, vol. 5, pp. 19864-19875, 2017. [5] Sobinder Singh, Abhishek Swaroop, Ajay Kumar, Anamika, "A survey on techniques to achive energy efficiency in cloud computing", Computing Communication and Automation (ICCCA) 2016 International Conference on, pp. 1281-1285, 2016. 6/23/19 21](https://image.slidesharecdn.com/routingprotocolsinad-hocnetwork-190623055559/75/Routing-protocols-in-ad-hoc-network-21-2048.jpg)