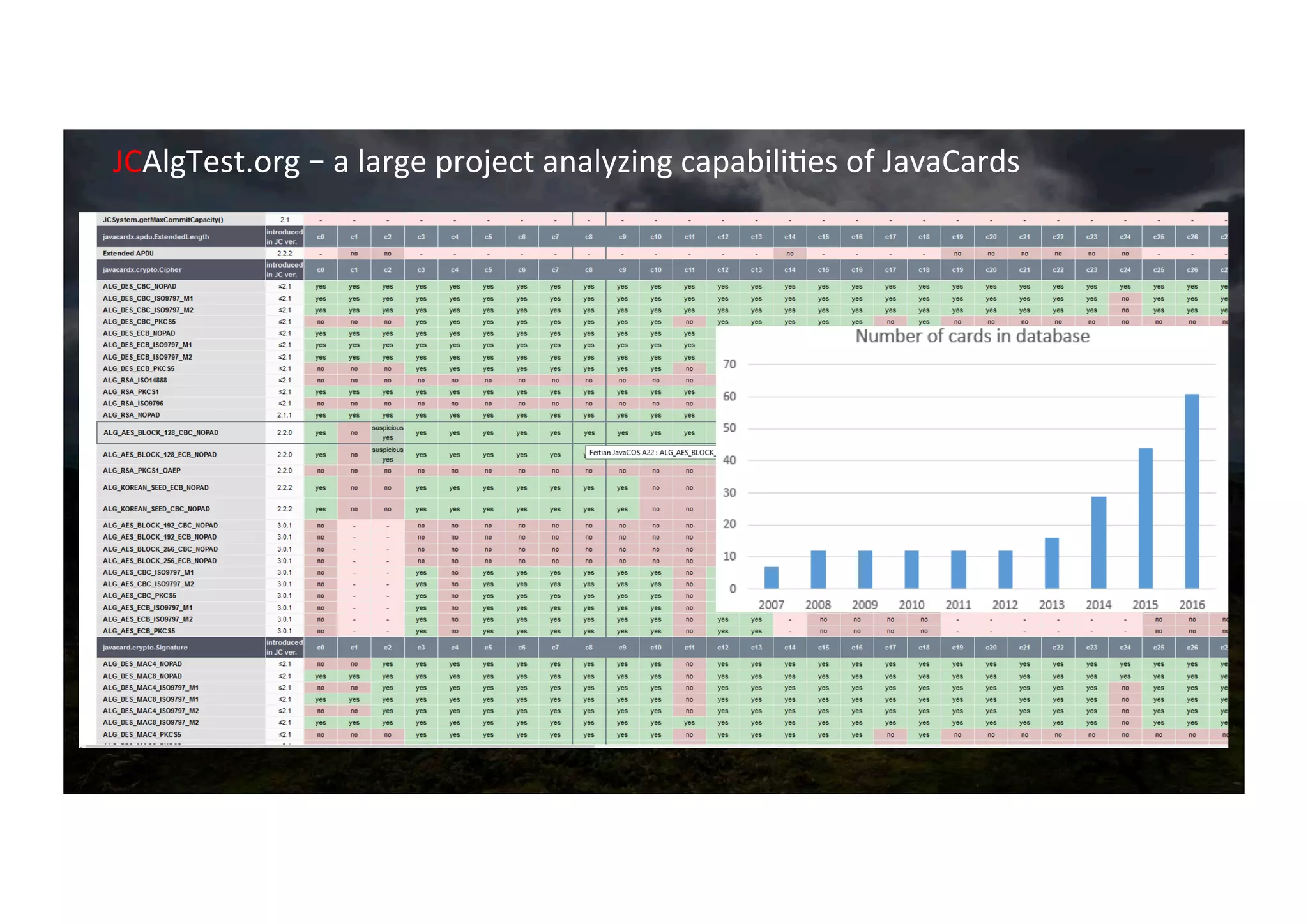
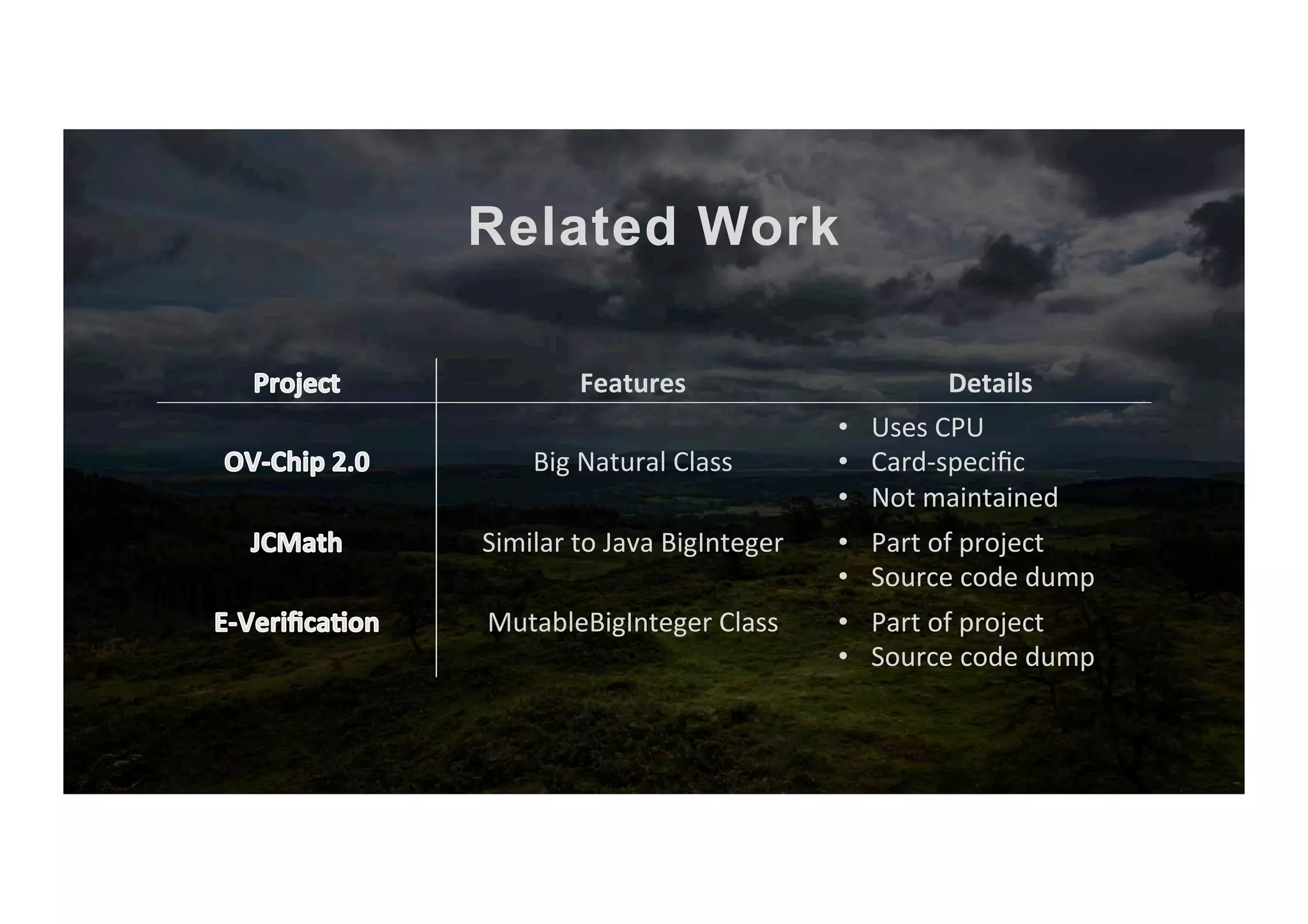
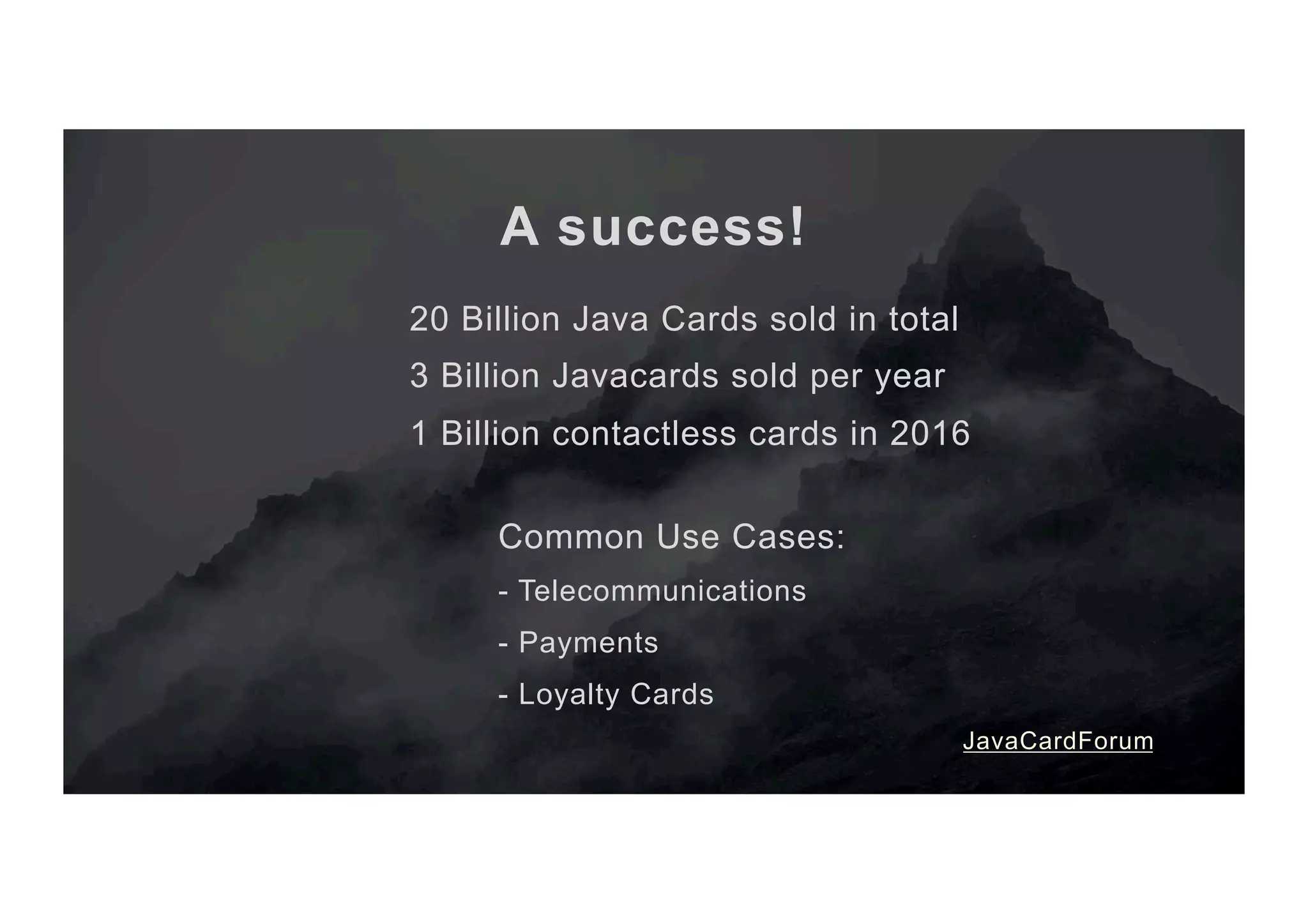
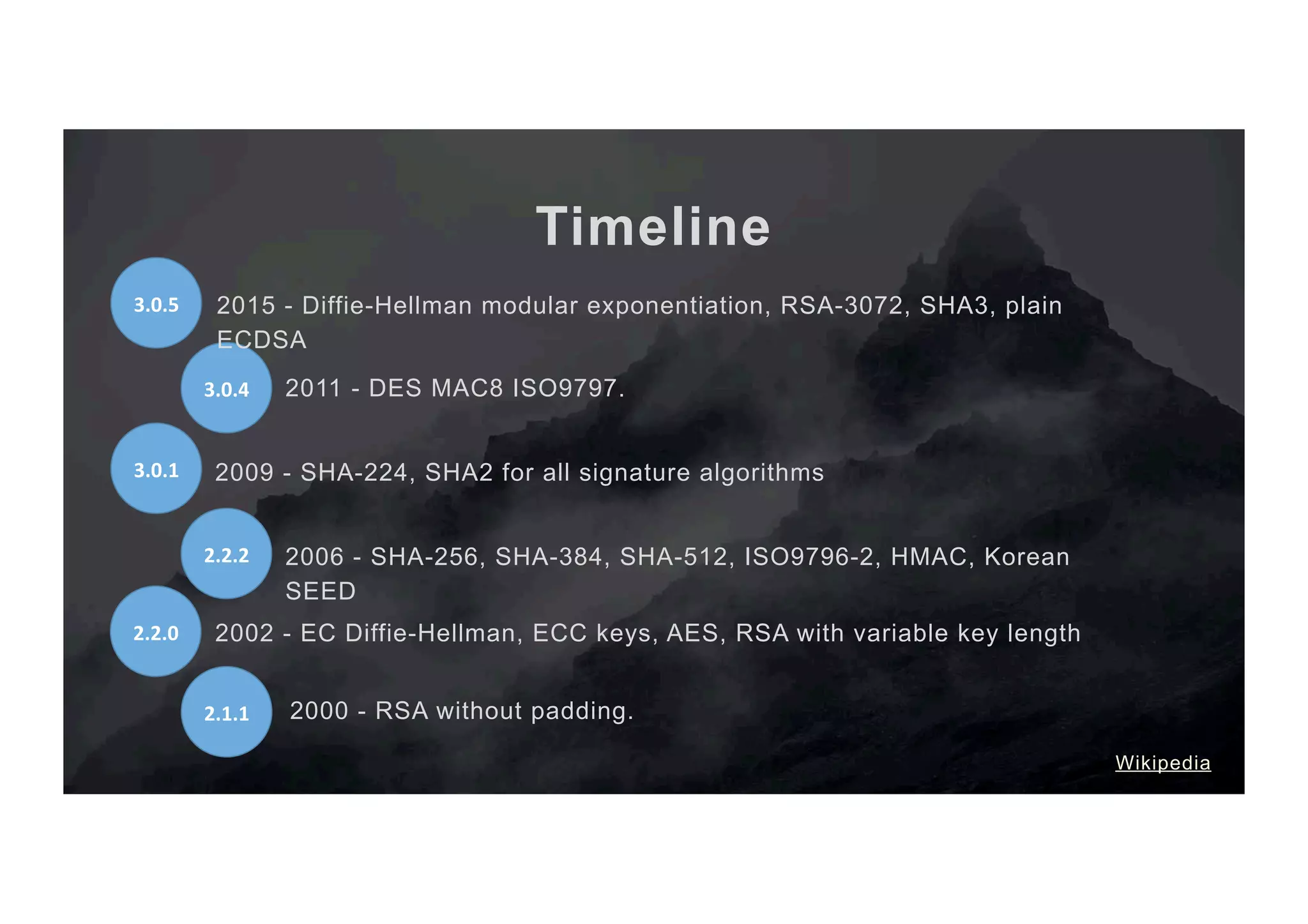
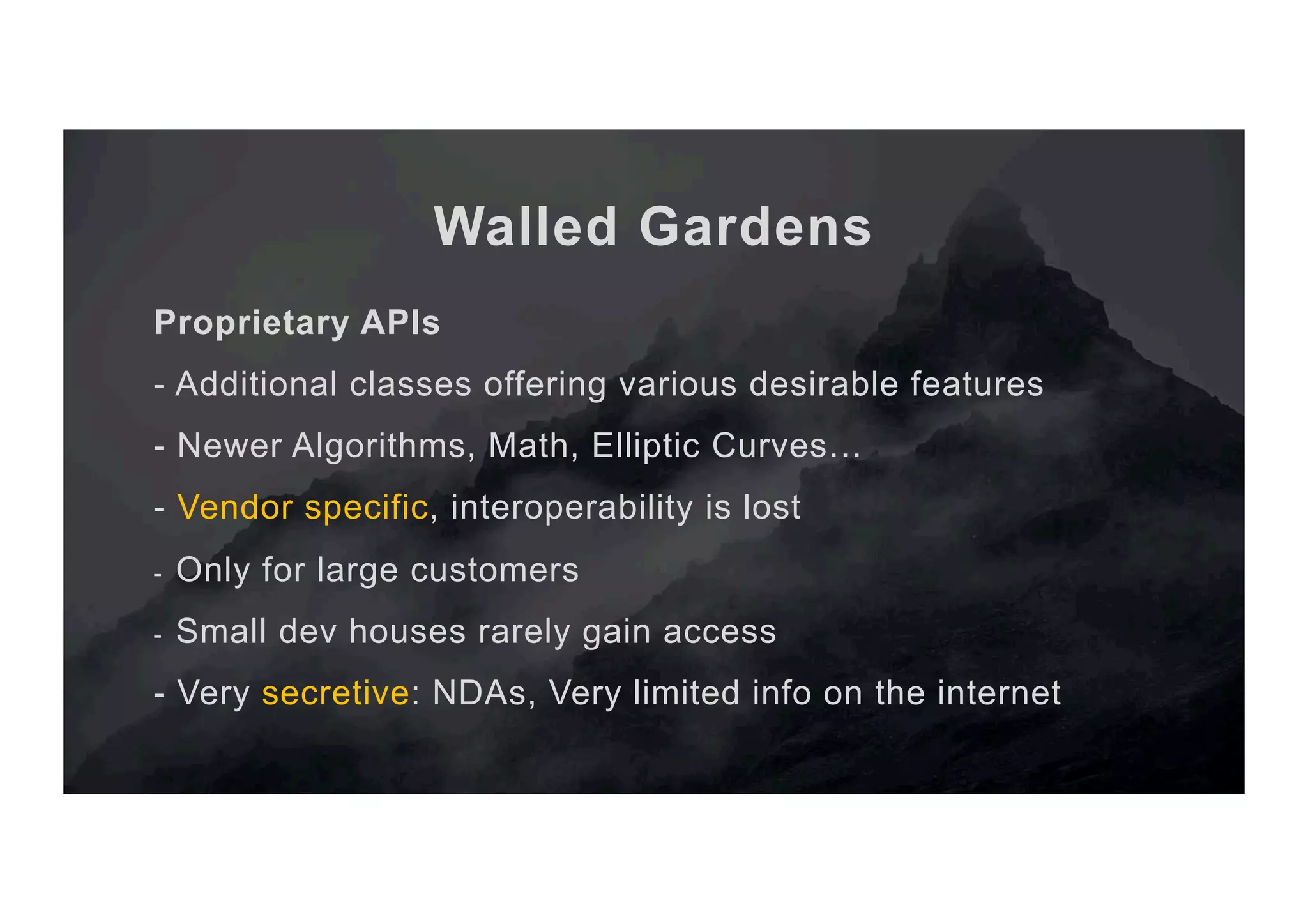
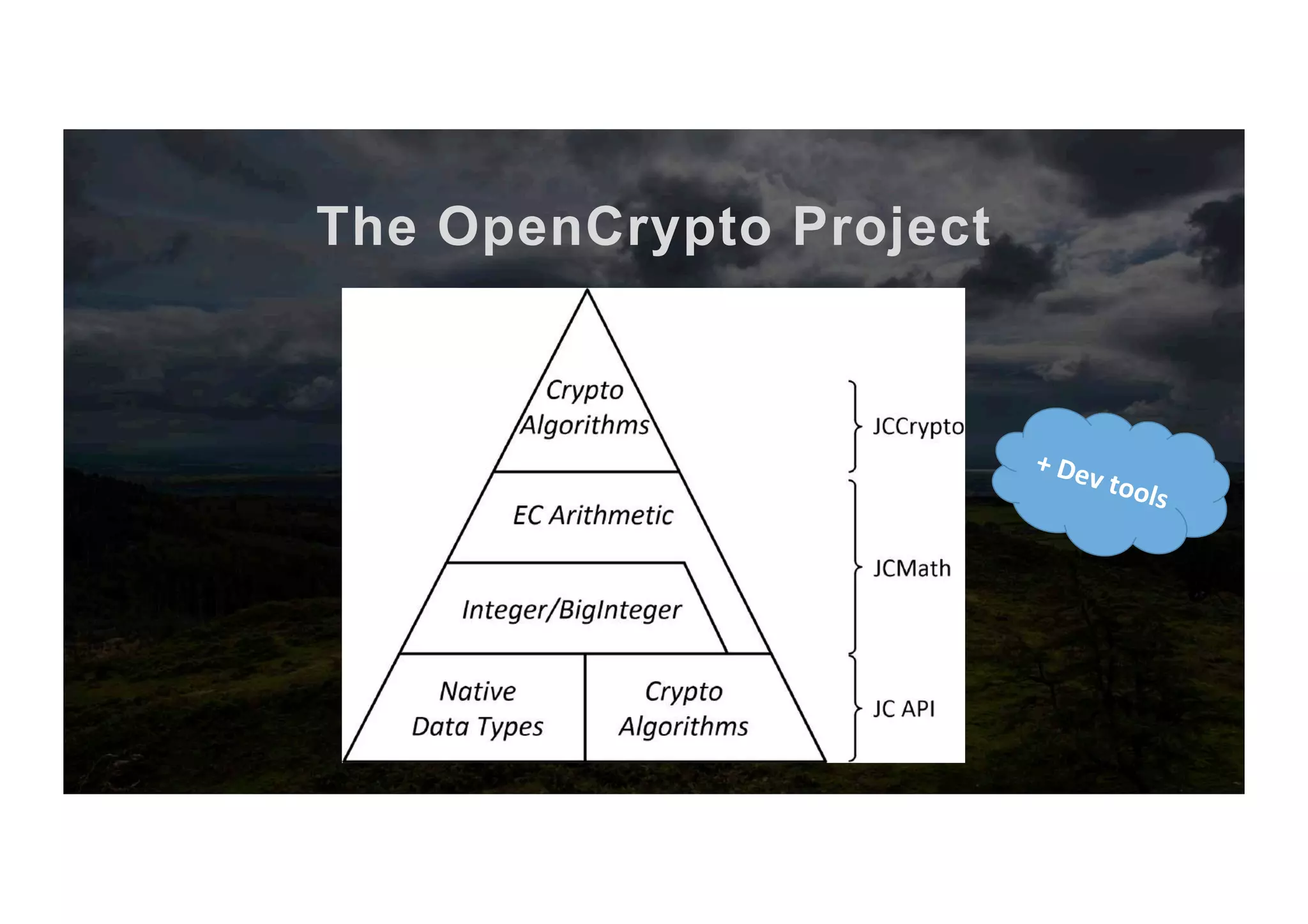
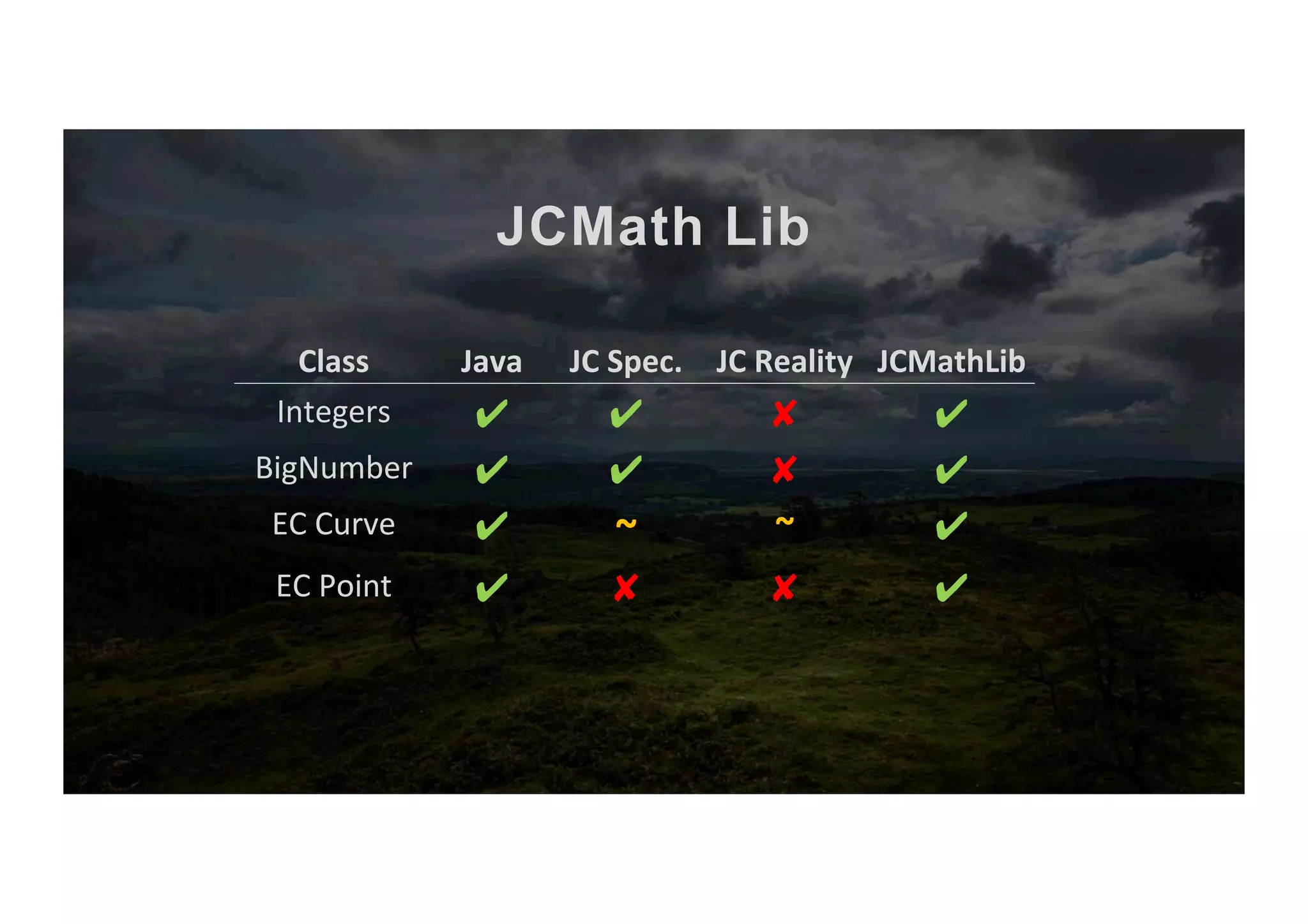
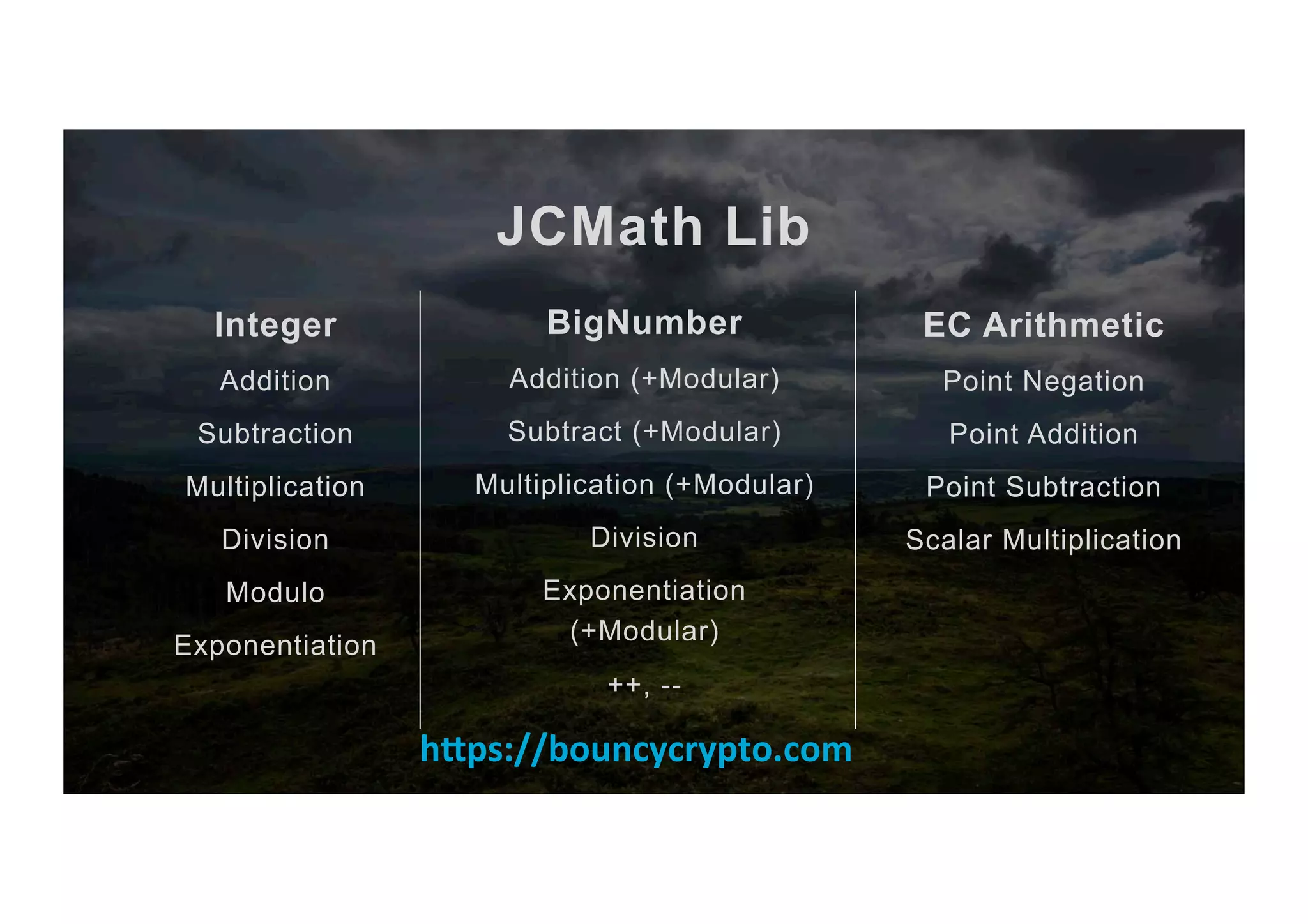
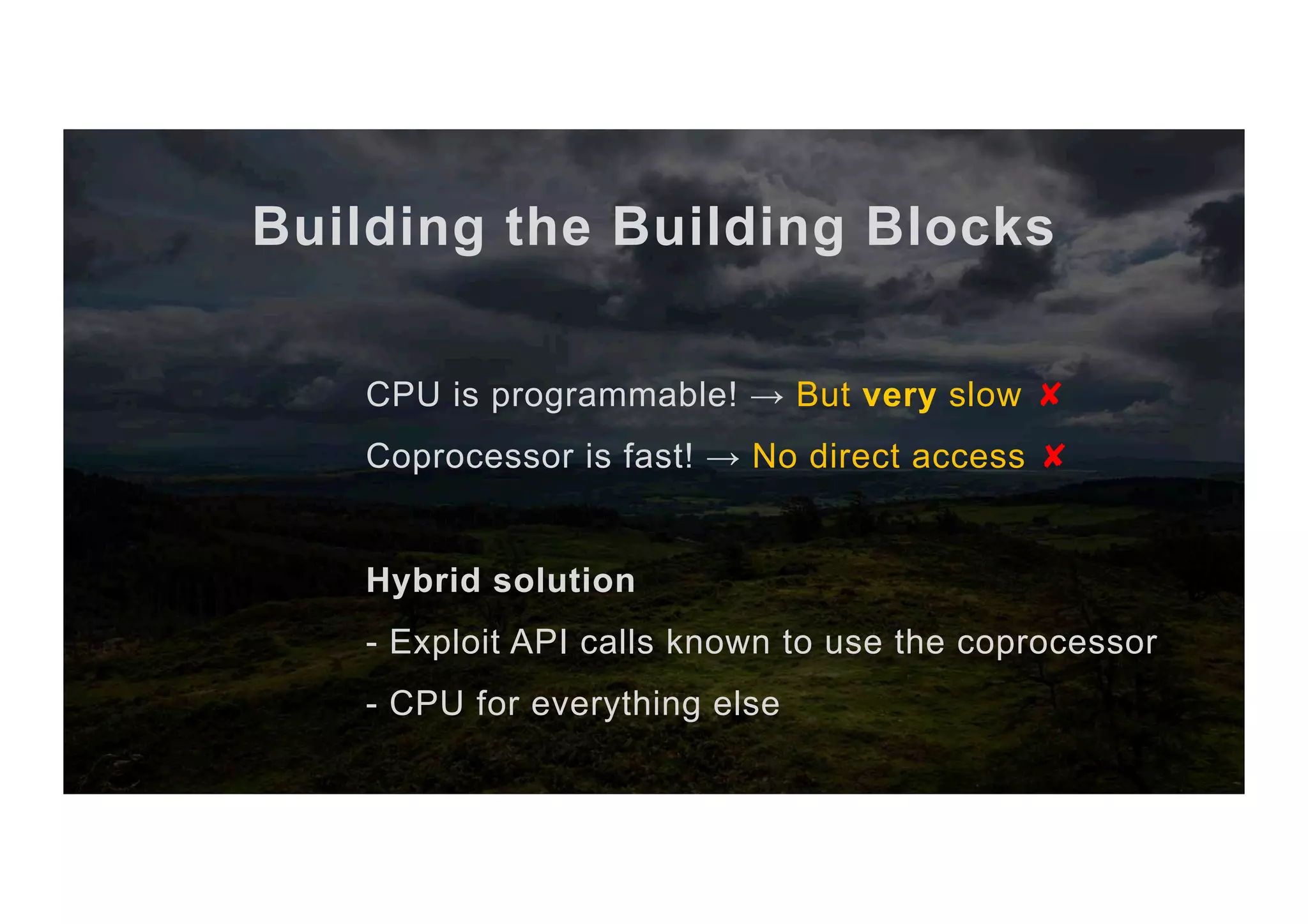
The document outlines the evolution and current state of the JavaCard ecosystem, emphasizing the importance of smart cards for secure transactions and authentication. It discusses the challenges of interoperability among cards and the need for open-source tools to enhance developer access to modern cryptographic algorithms. The OpenCrypto project aims to address these issues by providing a library and framework for easier development on JavaCard platforms.













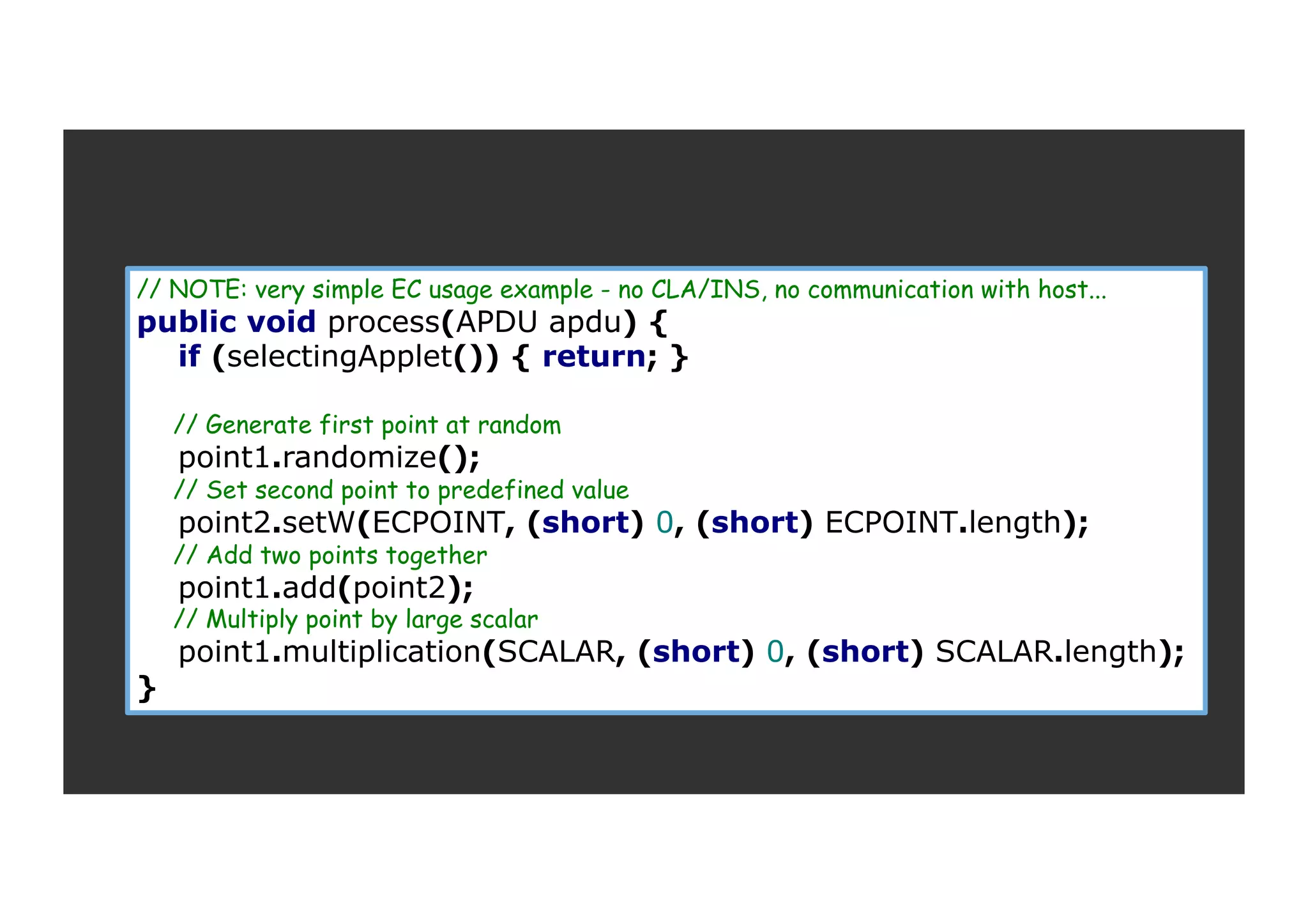
![package opencrypto.jcmathlib; public class ECExample extends javacard.framework.Applet { final static byte[] ECPOINT = {(byte)0x04, (byte) 0x3B… }; final static byte[] SCALAR = {(byte) 0xE8, (byte) 0x05… }; MLConfig mlc; ECCurve curve; ECPoint point1, point2; public ECExample() { // Pre-allocate all helper structures mlc = new MLConfig((short) 256); // Pre-allocate standard SecP256r1 curve and two EC points on this curve curve = new ECCurve(false, SecP256r1.p, SecP256r1.a, SecP256r1.b, SecP256r1.G, SecP256r1.r, mlc); point1 = new ECPoint(curve, mlc); point2 = new ECPoint(curve, mlc); } …](https://image.slidesharecdn.com/jcmathlibbouncycryptoblackhatusa2017-171003201021/75/One-library-for-all-Java-encryption-24-2048.jpg)
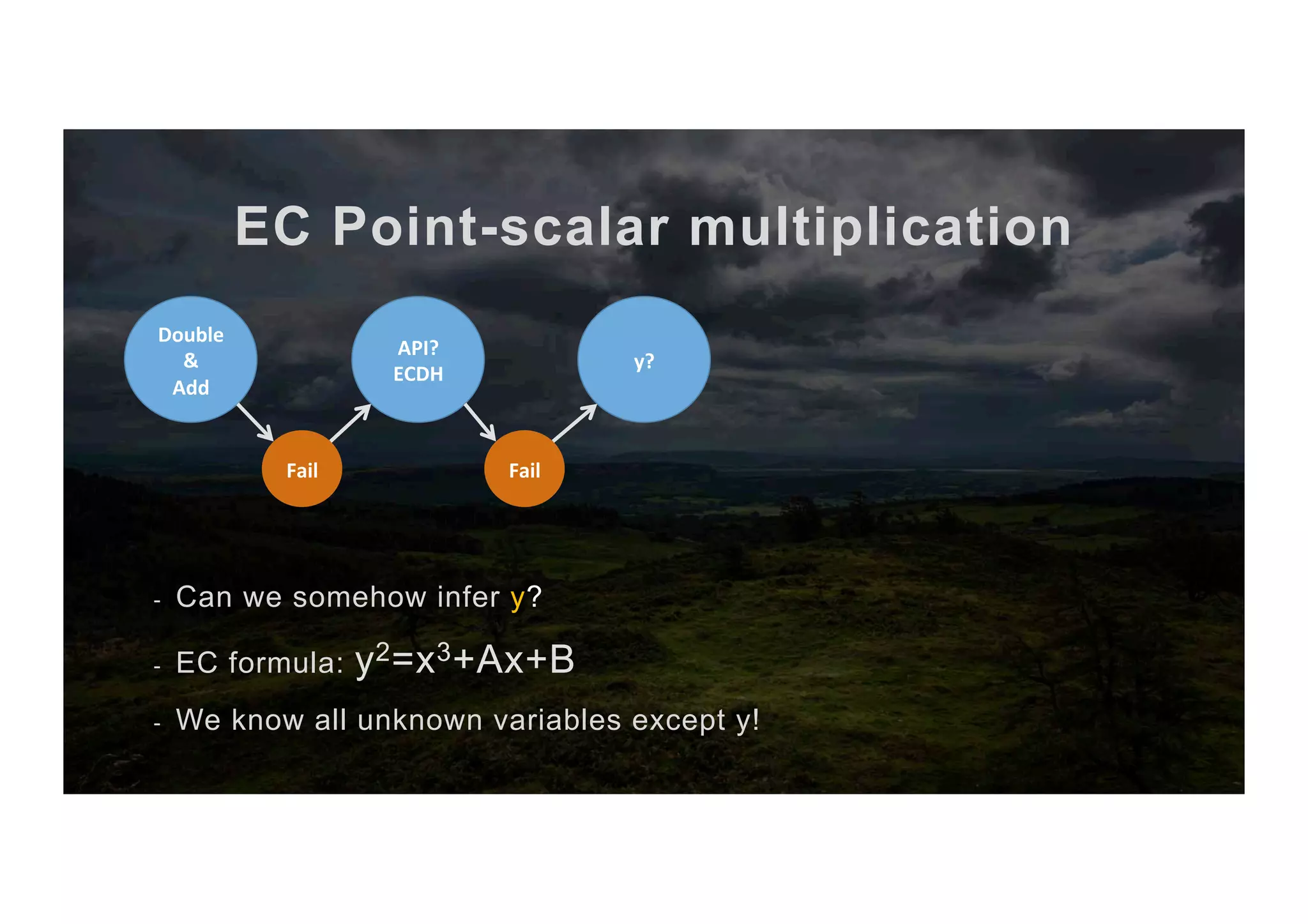
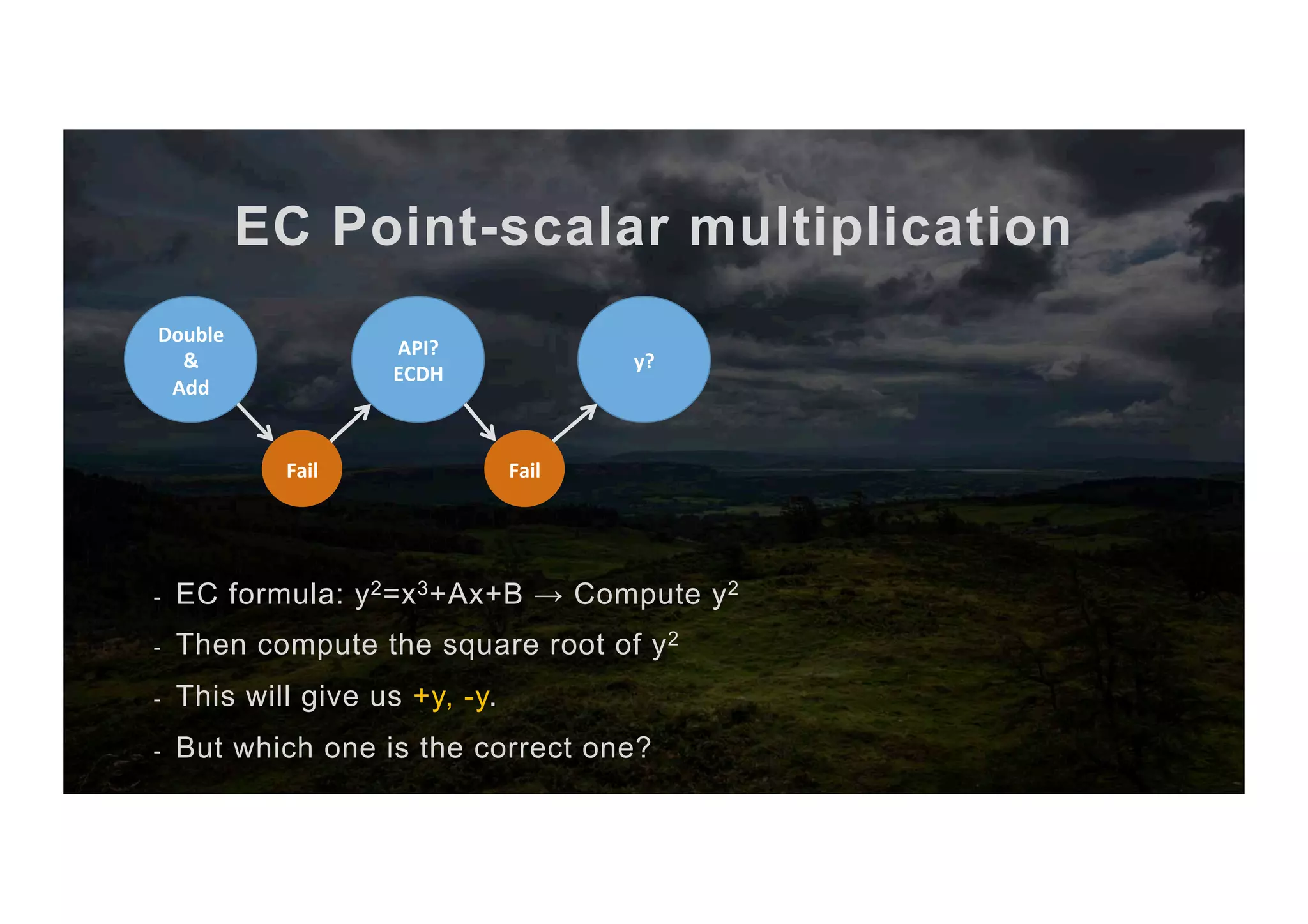
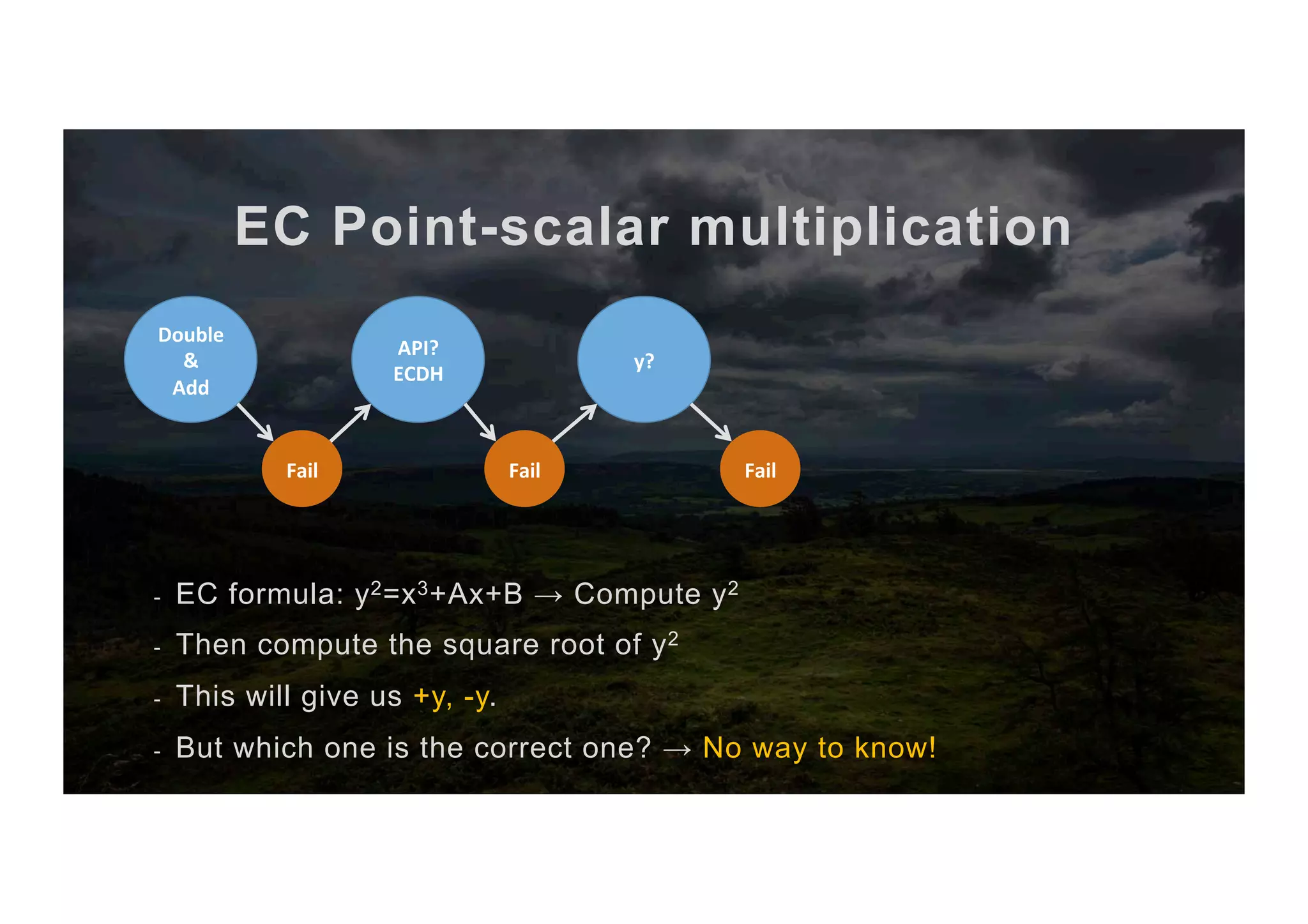
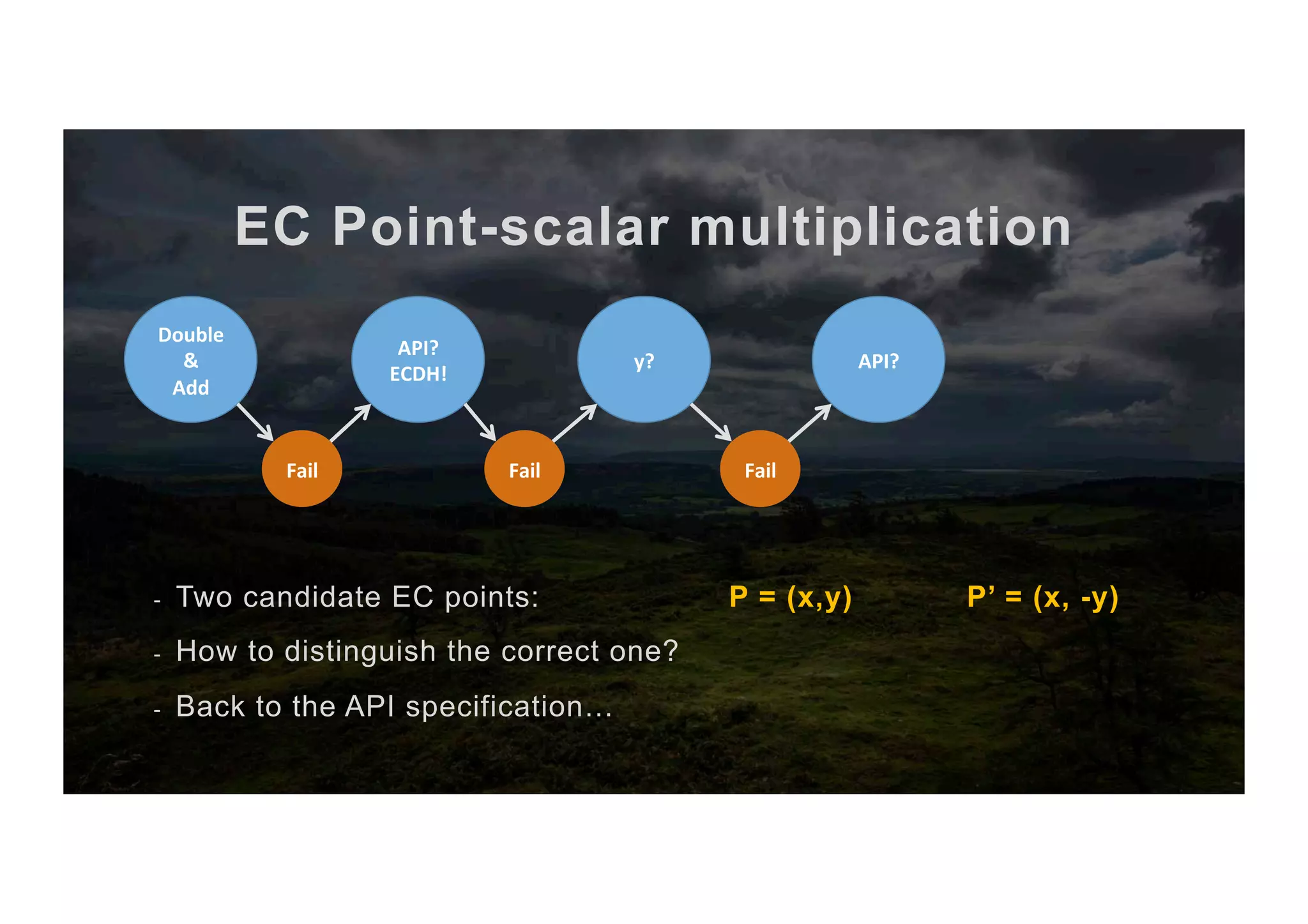
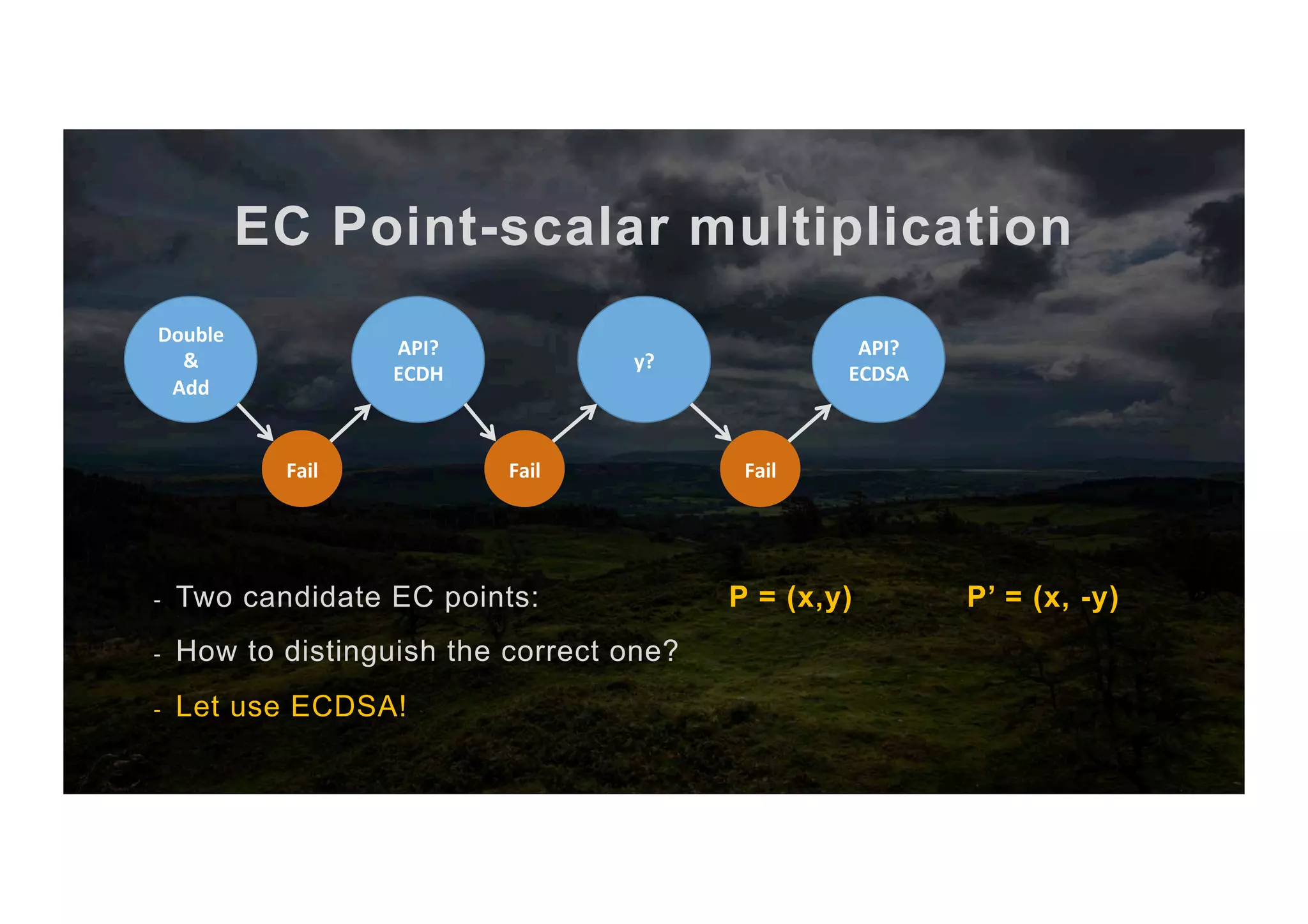
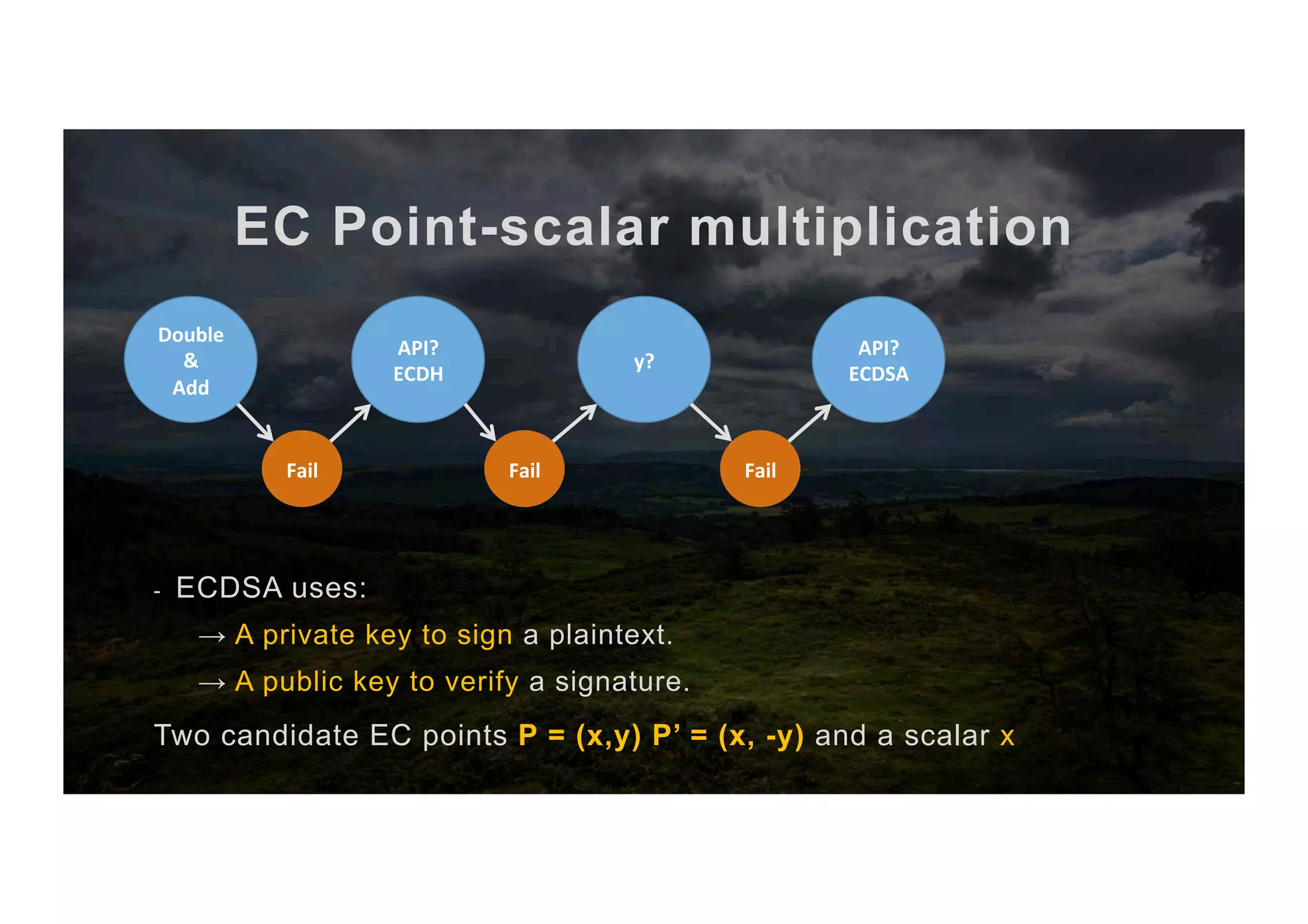
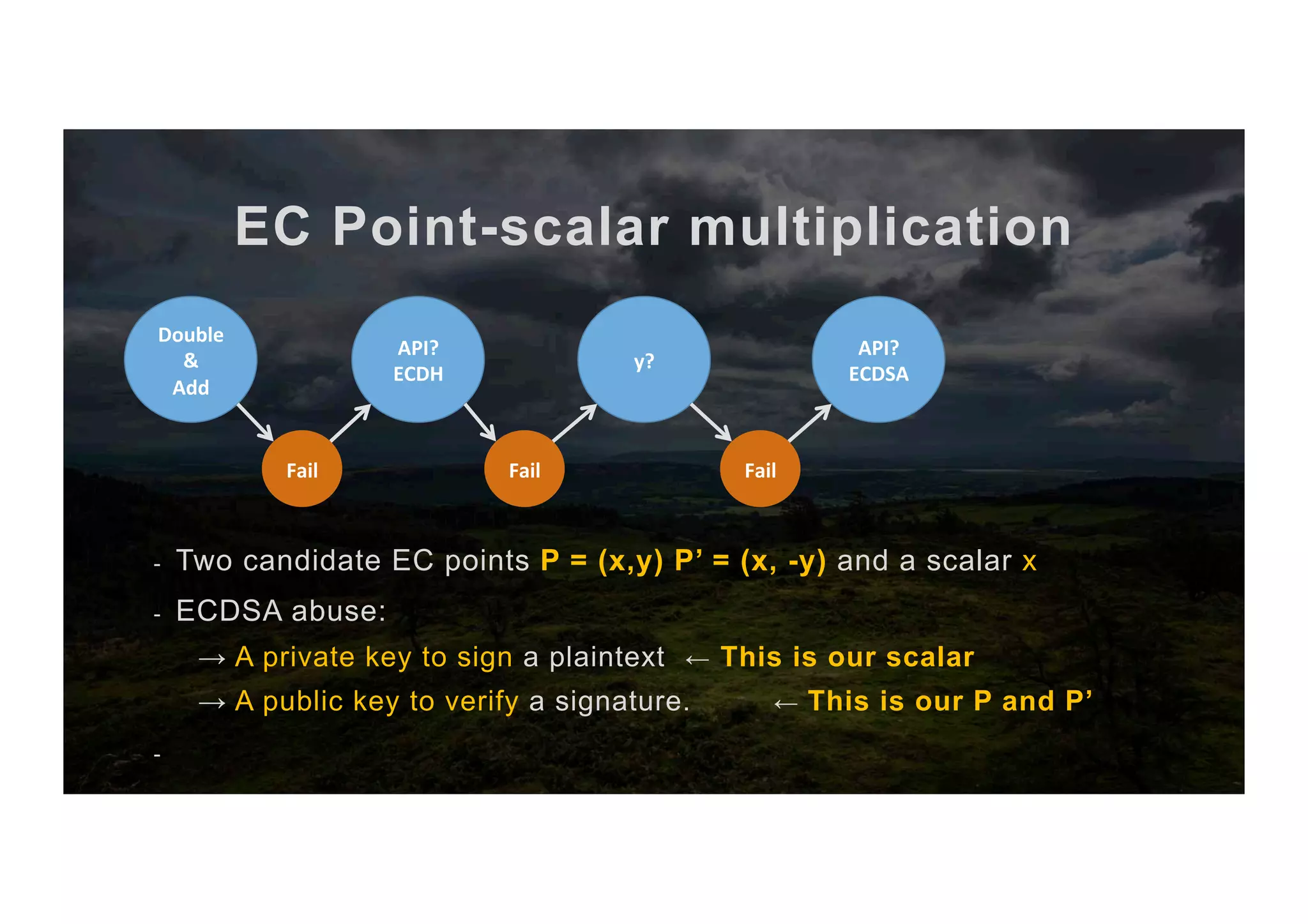
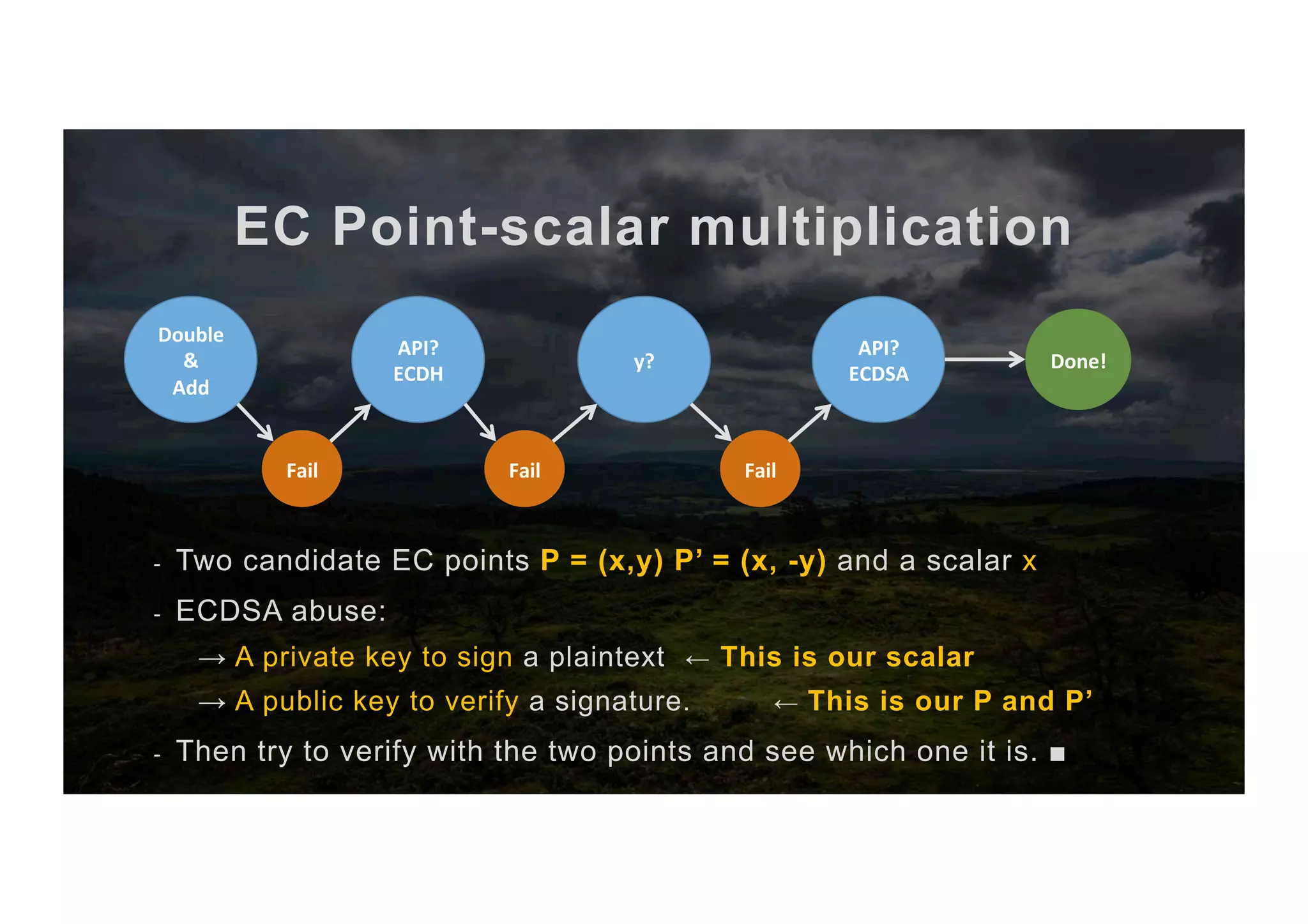
![EC Point-scalar multiplication The full algorithm 1. Input scalar x and point P 2. Abuse ECDH key exchange to get [x,+y,-y] 3. Compute the two candidate points P, P’ 4. Sign with scalar x as priv key 5. Try to verify with P as pub key 6. If it works → It’s P else → It’s P’ 7. return P or P’ (co-processor) (CPU) (co-processor) (co-processor)](https://image.slidesharecdn.com/jcmathlibbouncycryptoblackhatusa2017-171003201021/75/One-library-for-all-Java-encryption-42-2048.jpg)
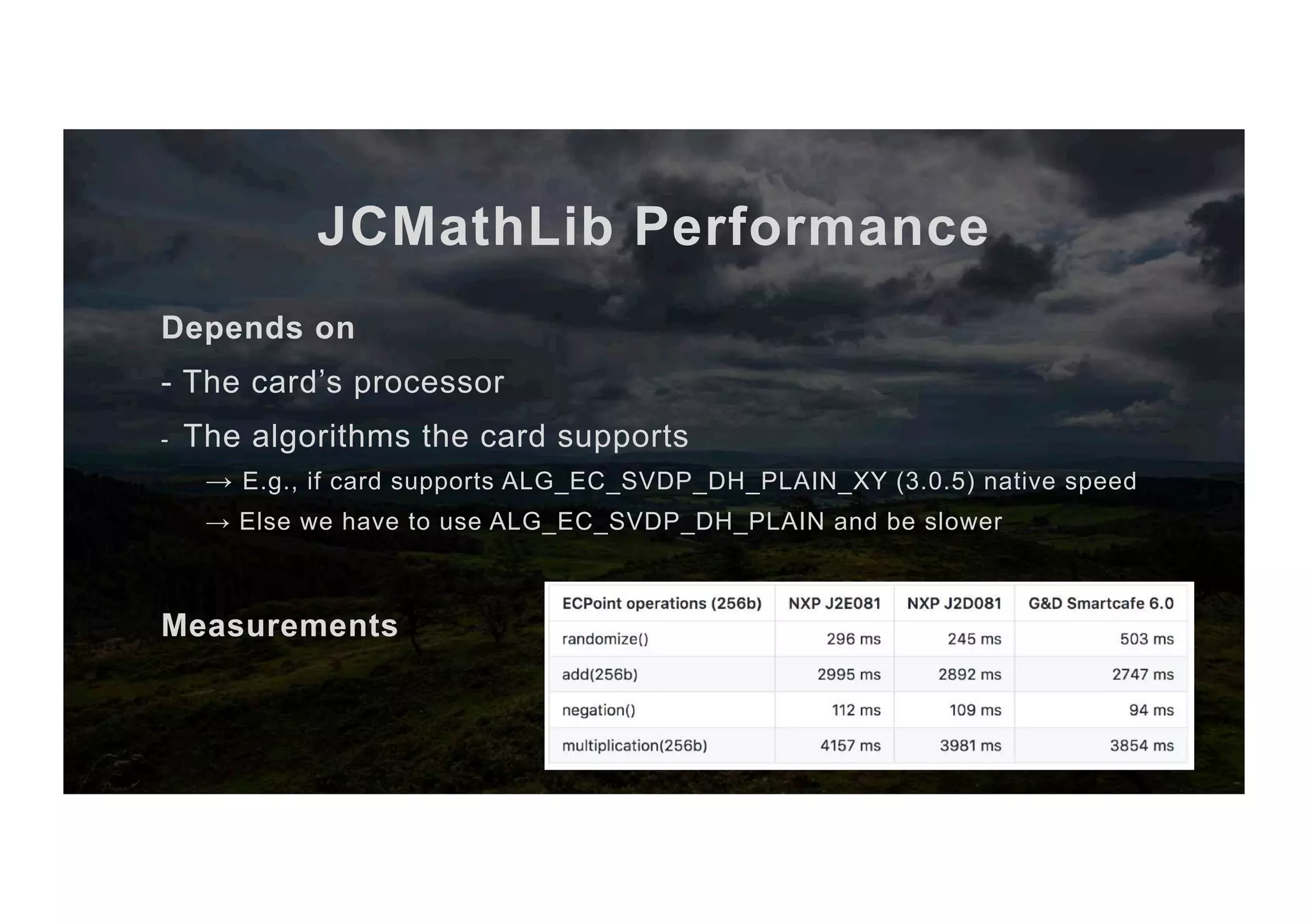
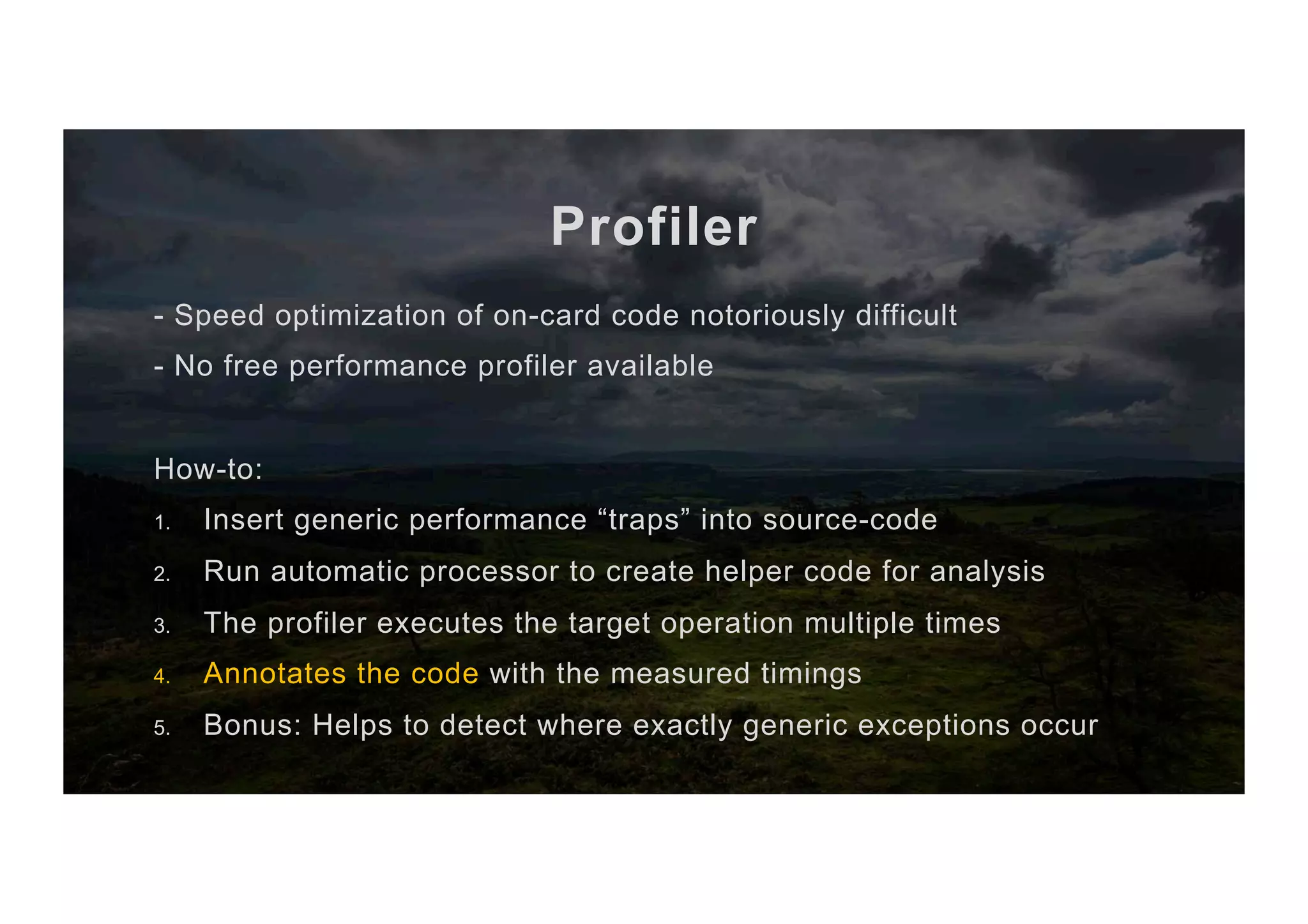
![Performance profiler private short multiplication_x_KA(Bignat scalar, byte[] outBuffer, short outBufferOffset) { priv.setS(scalar.as_byte_array(), (short) 0, scalar.length()); keyAgreement.init(priv); short len = this.getW(point_arr1, (short) 0); len = keyAgreement.generateSecret(point_arr1, (short) 0, len, outBuffer, outBufferOffset); return COORD_SIZE; } private short multiplication_x_KA(Bignat scalar, byte[] outBuffer, short outBufferOffset) { PM.check(PM.TRAP_ECPOINT_MULT_X_0); priv.setS(scalar.as_byte_array(), (short) 0, scalar.length()); PM.check(PM.TRAP_ECPOINT_MULT_X_0); keyAgreement.init(priv); PM.check(PM.TRAP_ECPOINT_MULT_X_0); short len = this.getW(point_arr1, (short) 0); PM.check(PM.TRAP_ECPOINT_MULT_X_0); len = keyAgreement.generateSecret(point_arr1, (short) 0, len, outBuffer, outBufferOffset); PM.check(PM.TRAP_ECPOINT_MULT_X_0); return COORD_SIZE; } private short multiplication_x_KA(Bignat scalar, byte[] outBuffer, short outBufferOffset) { PM.check(PM.TRAP_ECPOINT_MULT_X_1); priv.setS(scalar.as_byte_array(), (short) 0, scalar.length()); PM.check(PM.TRAP_ECPOINT_MULT_X_2); keyAgreement.init(priv); PM.check(PM.TRAP_ECPOINT_MULT_X_3); short len = this.getW(point_arr1, (short) 0); PM.check(PM.TRAP_ECPOINT_MULT_X_4); len = keyAgreement.generateSecret(point_arr1, (short) 0, len, outBuffer, outBufferOffset); PM.check(PM.TRAP_ECPOINT_MULT_X_5); return COORD_SIZE; } Client-side tesQng code private short multiplication_x_KA(Bignat scalar, byte[] outBuffer, short outBufferOffset) { PM.check(PM.TRAP_ECPOINT_MULT_X_1); // 40 ms (gd60,1500968219581) priv.setS(scalar.as_byte_array(), (short) 0, scalar.length()); PM.check(PM.TRAP_ECPOINT_MULT_X_2); // 12 ms (gd60,1500968219581) keyAgreement.init(priv); PM.check(PM.TRAP_ECPOINT_MULT_X_3); // 120 ms (gd60,1500968219581) short len = this.getW(point_arr1, (short) 0); PM.check(PM.TRAP_ECPOINT_MULT_X_4); // 9 ms (gd60,1500968219581) len = keyAgreement.generateSecret(point_arr1, (short) 0, len, outBuffer, outBufferOffset); PM.check(PM.TRAP_ECPOINT_MULT_X_5); // 186 ms (gd60,1500968219581) return COORD_SIZE; }](https://image.slidesharecdn.com/jcmathlibbouncycryptoblackhatusa2017-171003201021/75/One-library-for-all-Java-encryption-47-2048.jpg)