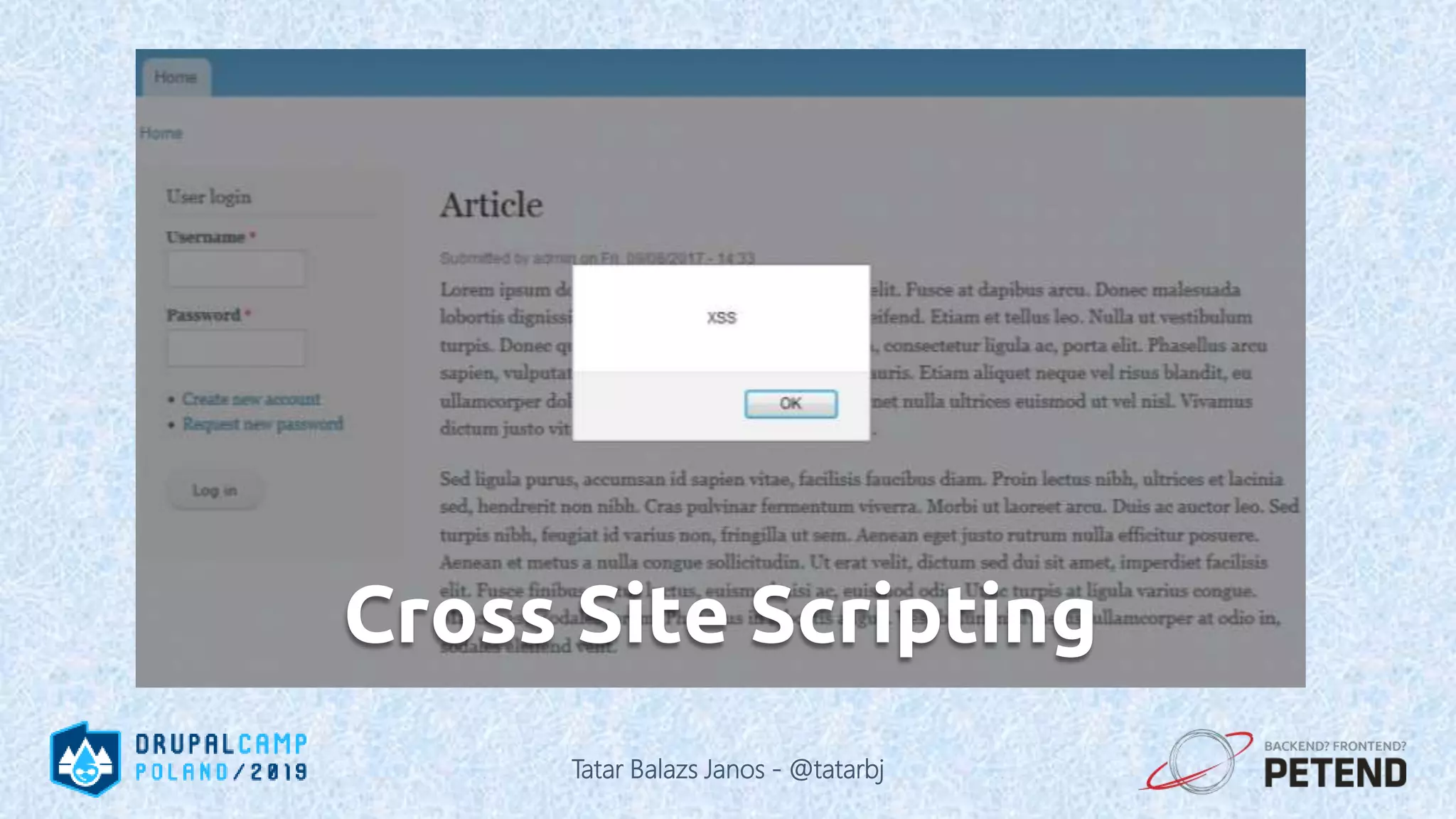
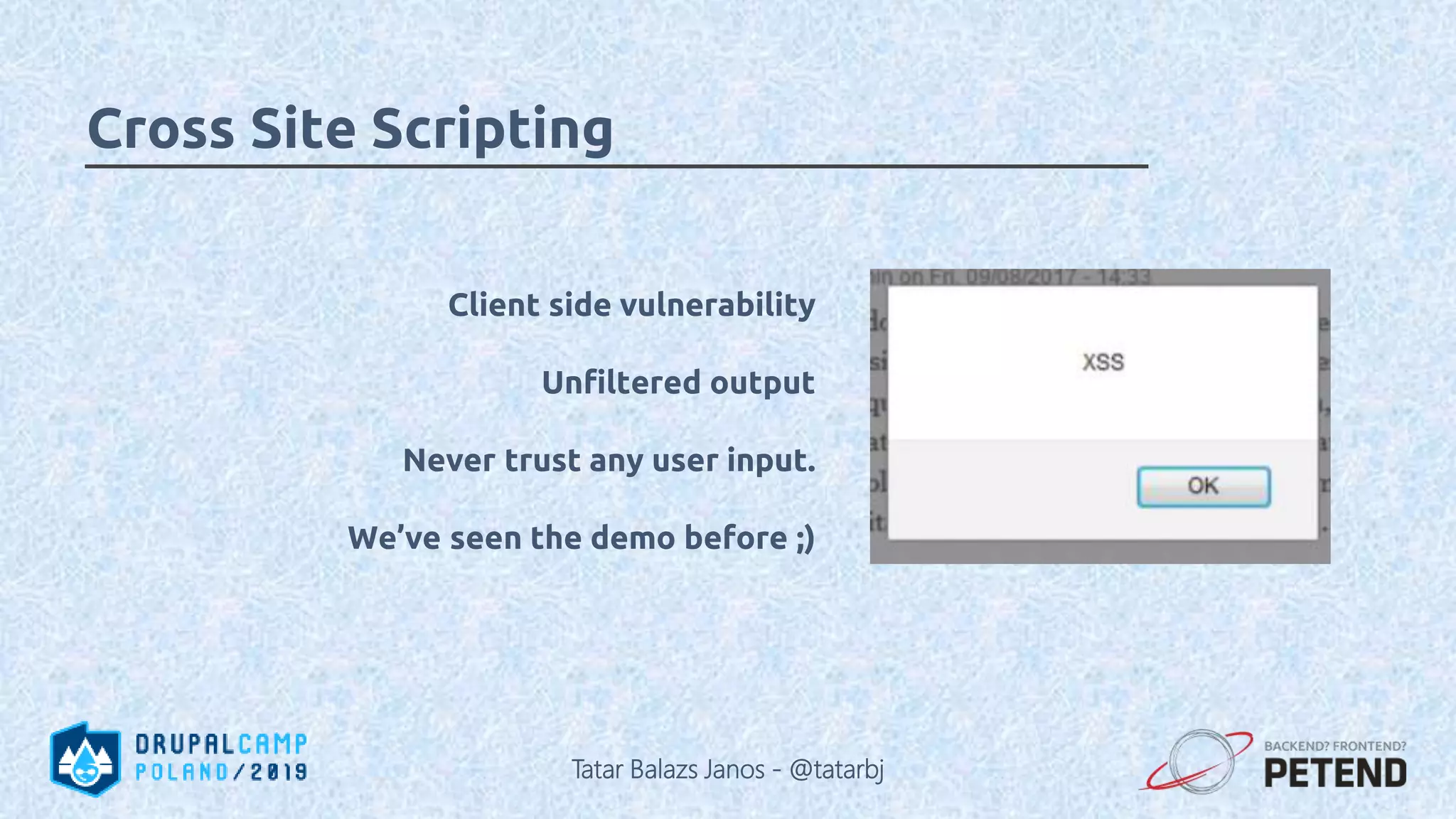
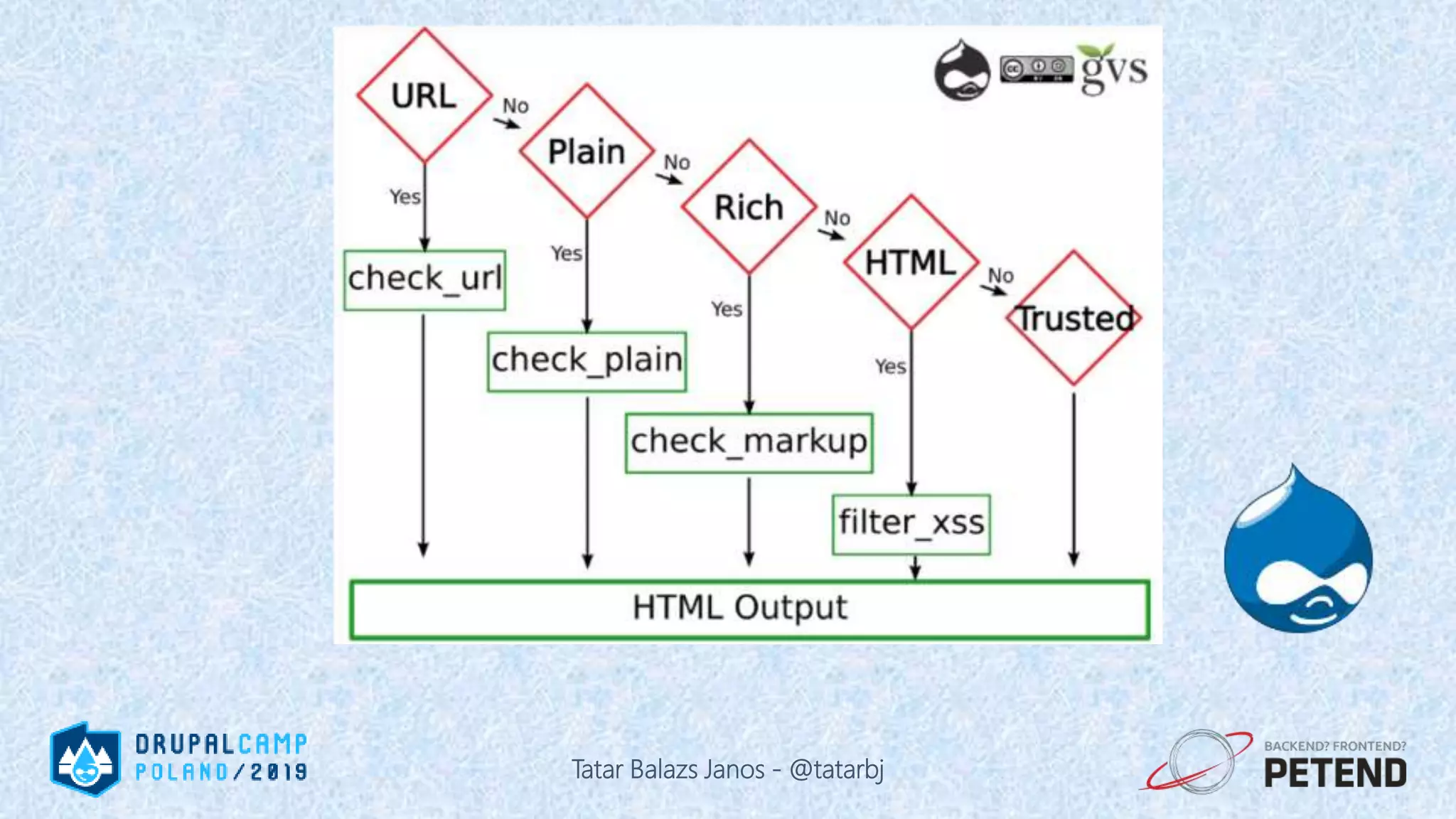
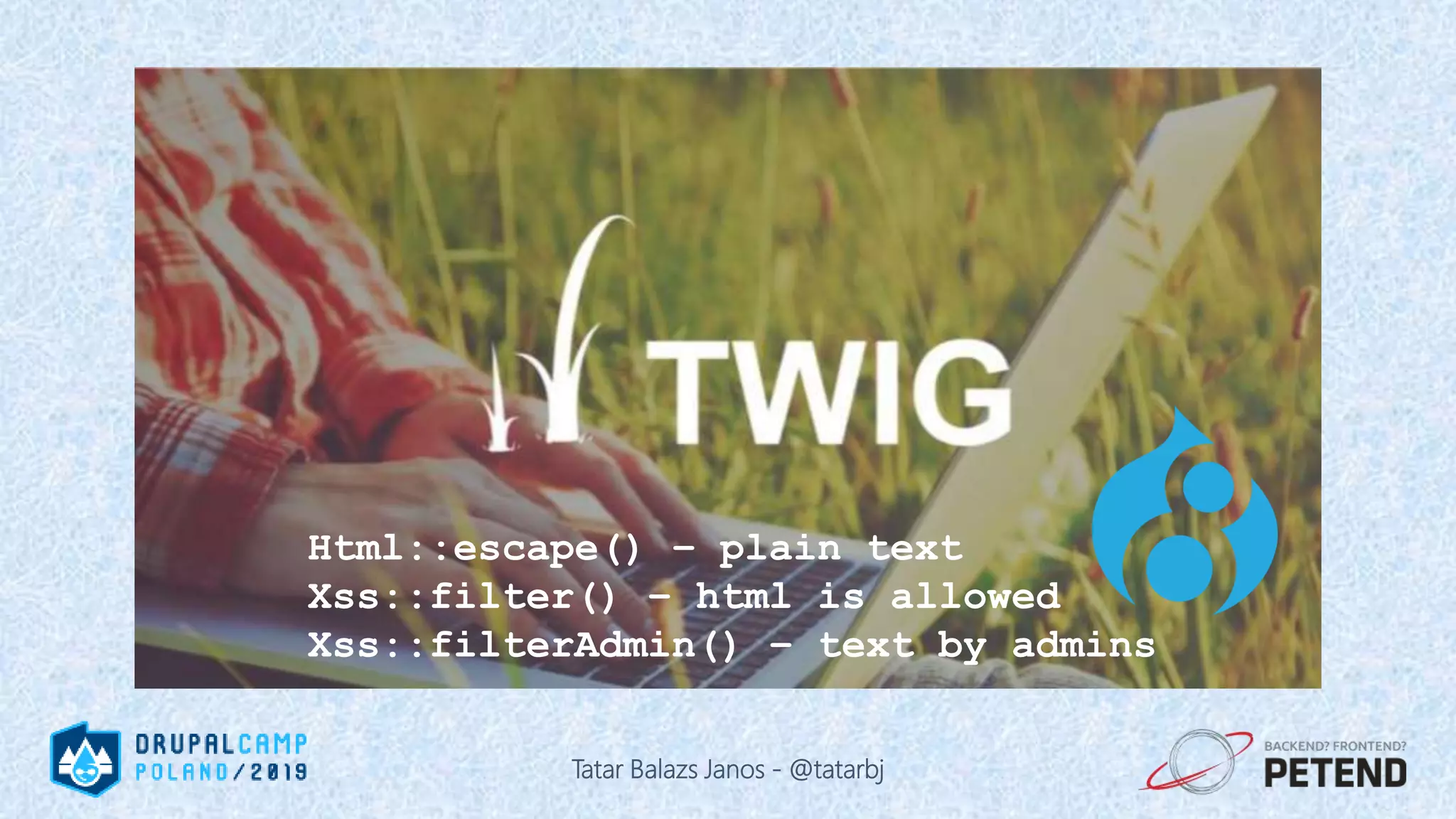
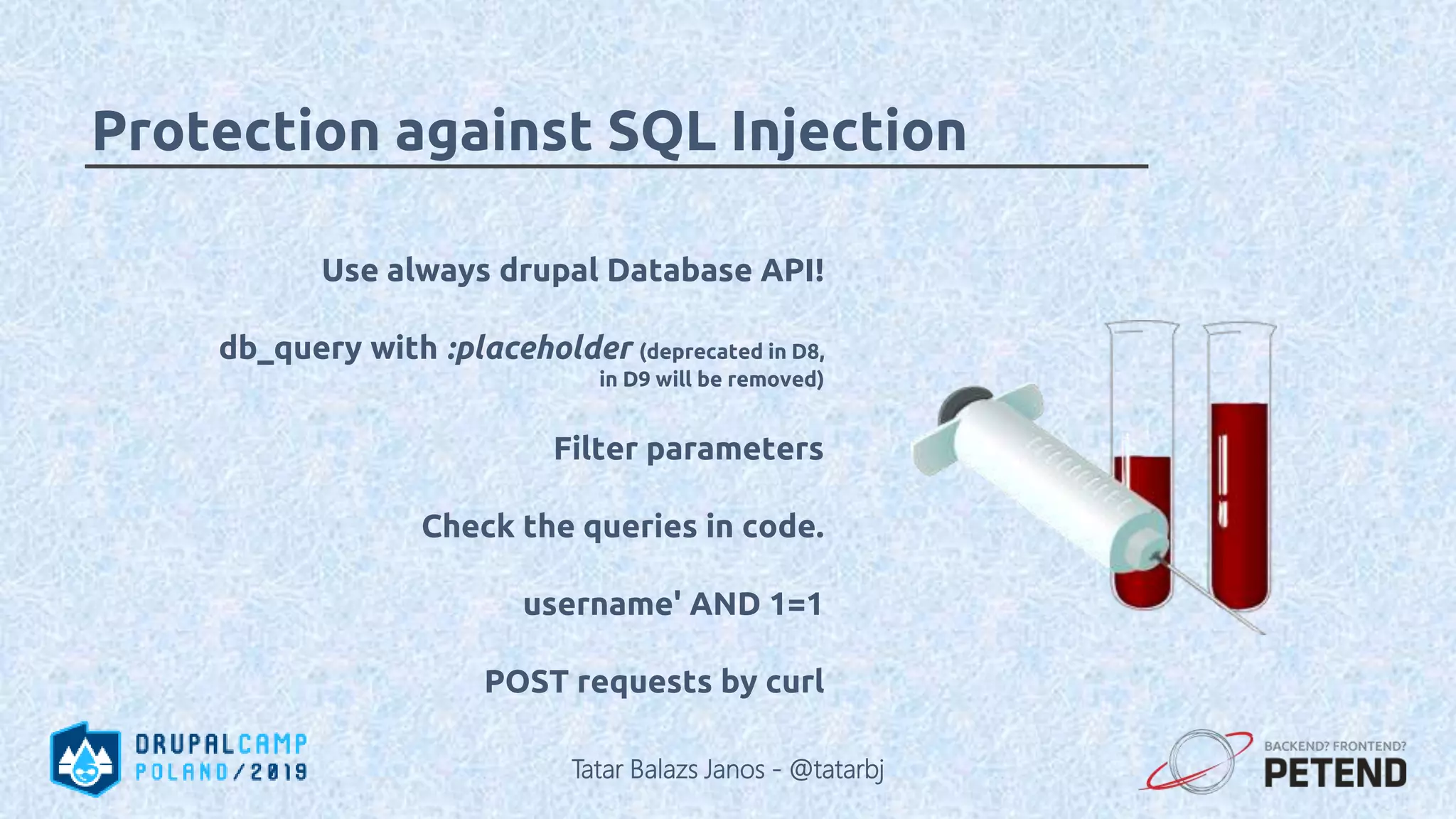
The document is a presentation by Tatar Balazs Janos on writing secure Drupal code. It provides an overview of the presenter's background and experience with Drupal security. The presentation covers trends in security, types of vulnerabilities like cross-site scripting and SQL injection, and techniques for protecting against vulnerabilities such as input filtering, automated testing, and access control. It includes code examples and opportunities for audience participation through a bingo game.










![function custom_field_formatter_view(...) { foreach ($items as $key => $value) { //... $element[$key] = array( '#type' => 'markup', '#markup' => t('<img src="!src" alt="@alt" />', array('!src' => $value['src'], ‚$alt’ => $value['alt'])), ); //... } return $element; } Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-23-2048.jpg)
![function custom_field_formatter_view(...) { foreach ($items as $key => $value) { //... $element[$key] = array( '#type' => 'markup', '#markup' => t('<img src="!src" alt="@alt" />', array('!src' => $value['src'], ‚$alt’ => $value['alt'])), ); //... } return $element; } Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-24-2048.jpg)
![function custom_field_formatter_view(...) { foreach ($items as $key => $value) { //... $element[$key] = array( '#type' => 'markup', '#markup' => t('<img src="@src" alt="@alt" />', array('@src' => $value['src'], ‚$alt’ => $value['alt'])), ); //... } return $element; } Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-25-2048.jpg)
![foreach ($items as $delta => $item) { $id = $item->getValue()['target_id']; $content = Drupal::entityTypeManager() ->getStorage($entity_type_id) ->load($id); $body = $content->get('body_field')->getValue()[0]['value']; } $elements[$delta] = array( '#theme' => 'something_custom', '#body' => $body, ); return $elements; Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-27-2048.jpg)
![foreach ($items as $delta => $item) { $id = $item->getValue()['target_id']; $content = Drupal::entityTypeManager() ->getStorage($entity_type_id) ->load($id); $body = $content->get('body_field')->getValue()[0]['value']; } $elements[$delta] = array( '#theme' => 'something_custom', '#body' => $body, ); return $elements; Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-28-2048.jpg)
![foreach ($items as $delta => $item) { $id = $item->getValue()['target_id']; $content = Drupal::entityTypeManager() ->getStorage($entity_type_id) ->load($id); $body = [ '#type' => 'processed_text', '#text' => $content->get('body_field')->getValue()[0]['value'], '#format' => $content->get('body_field')->getValue()[0]['format'], ]; } $elements[$delta] = array( '#theme' => 'something_custom', '#body' => $body, ); return $elements; Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-29-2048.jpg)








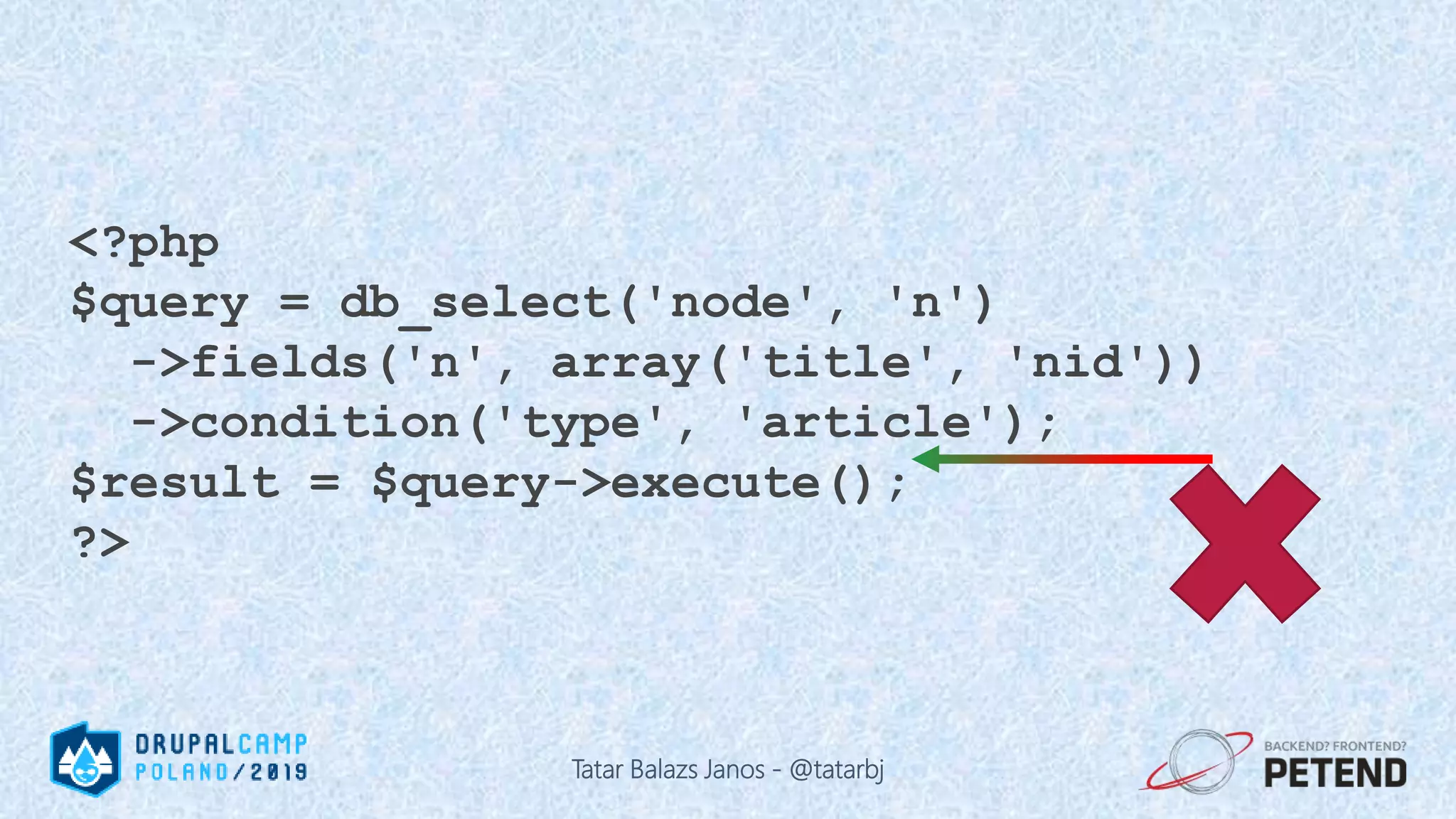
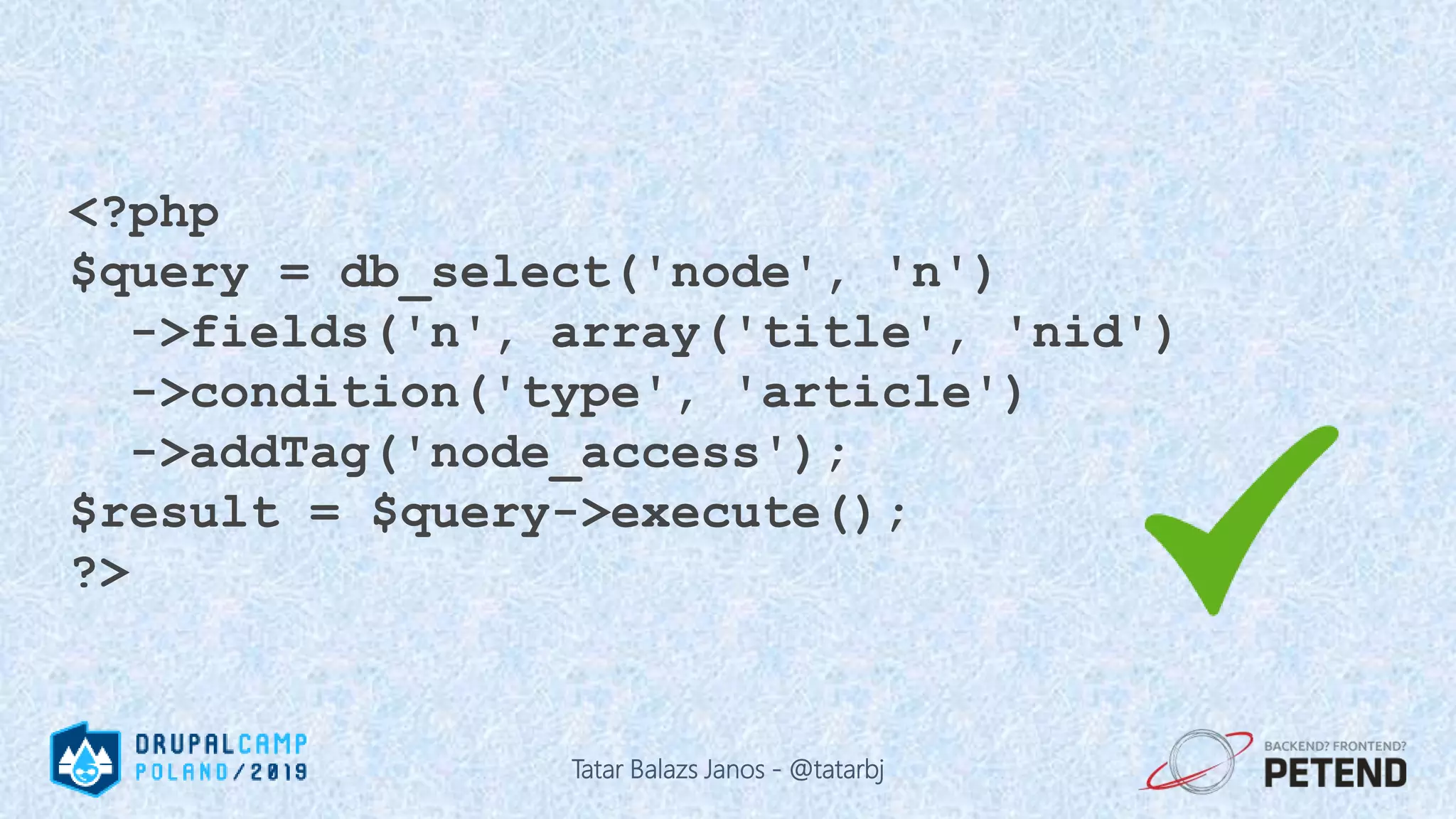
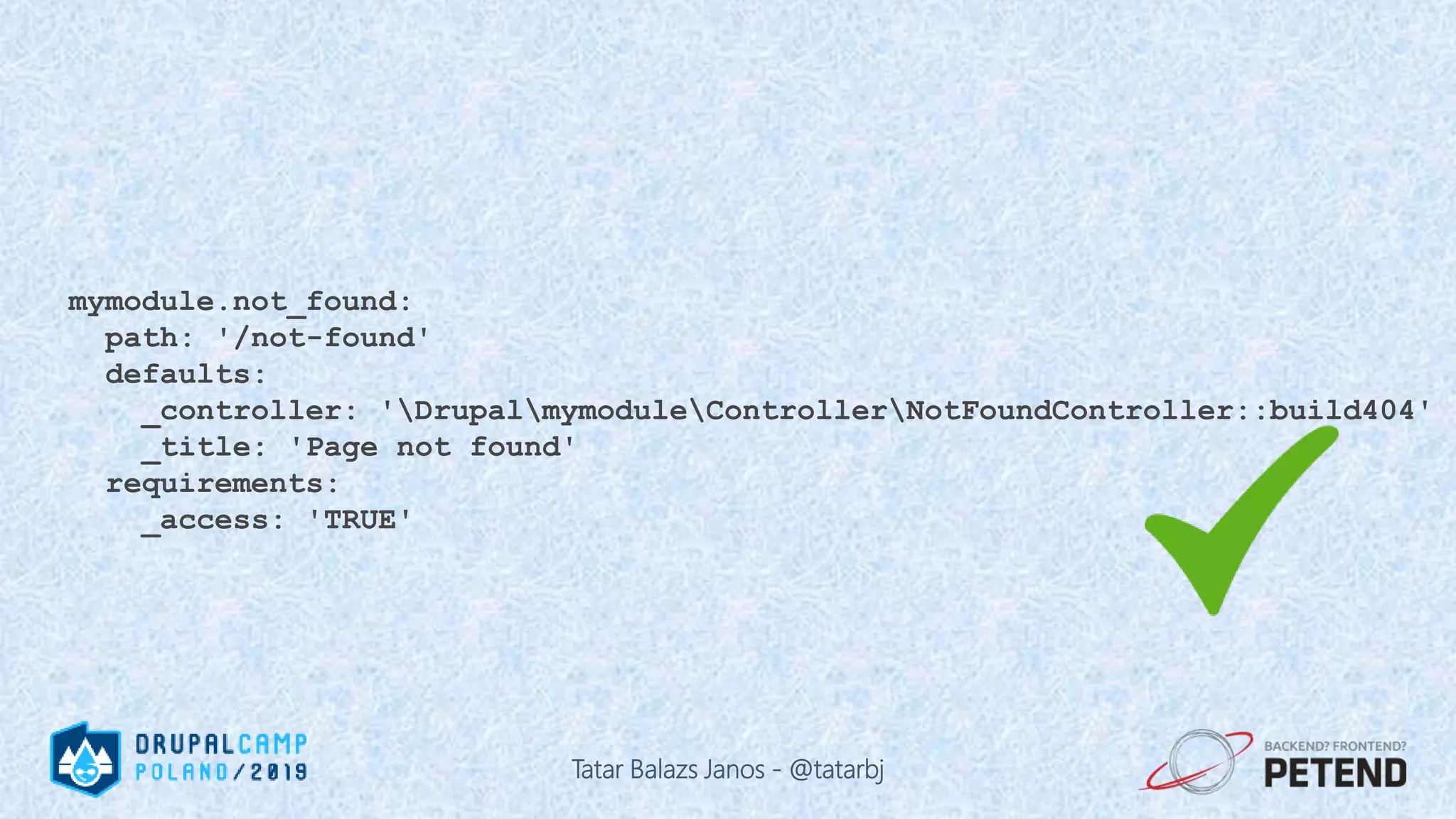
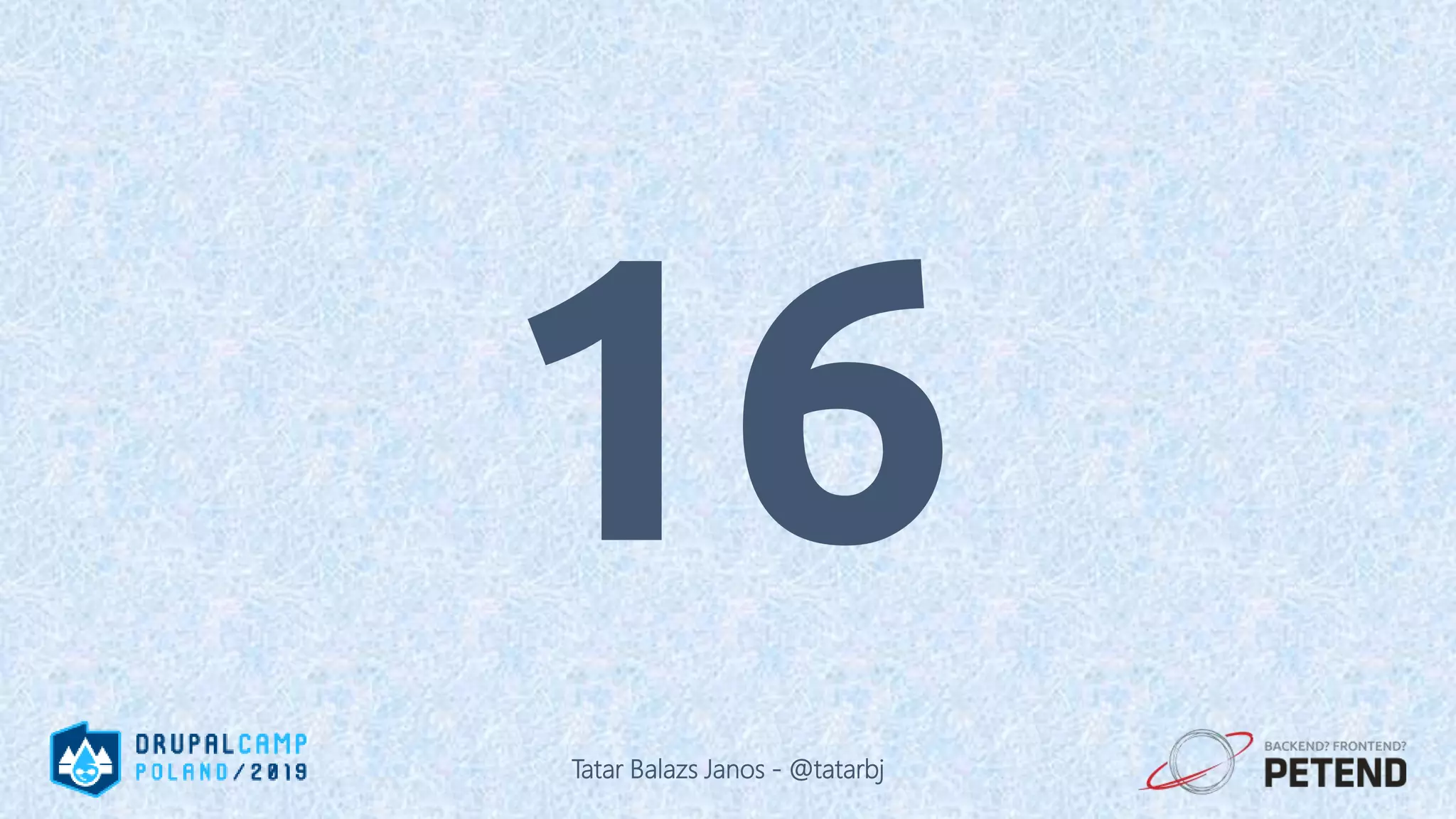



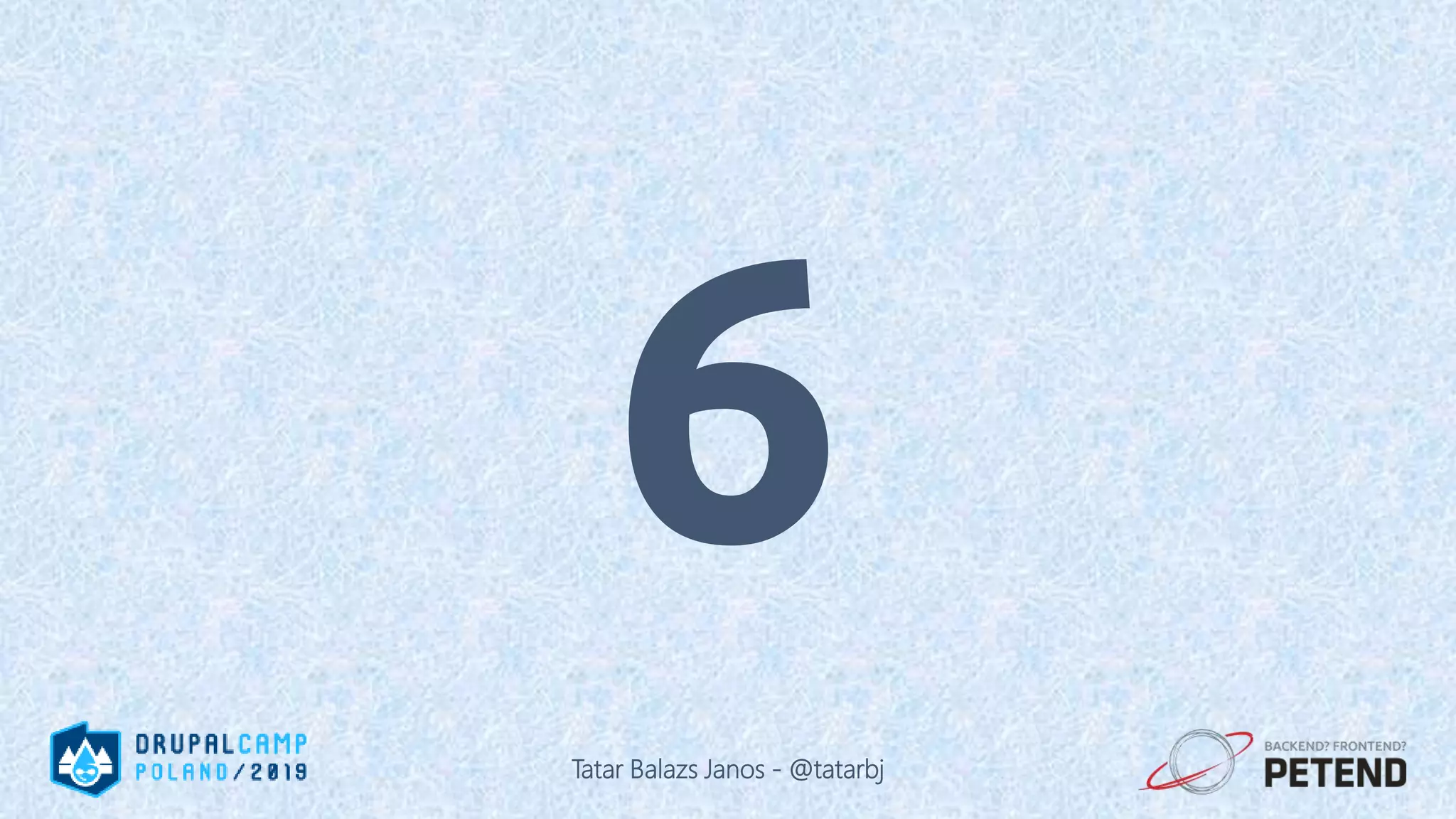
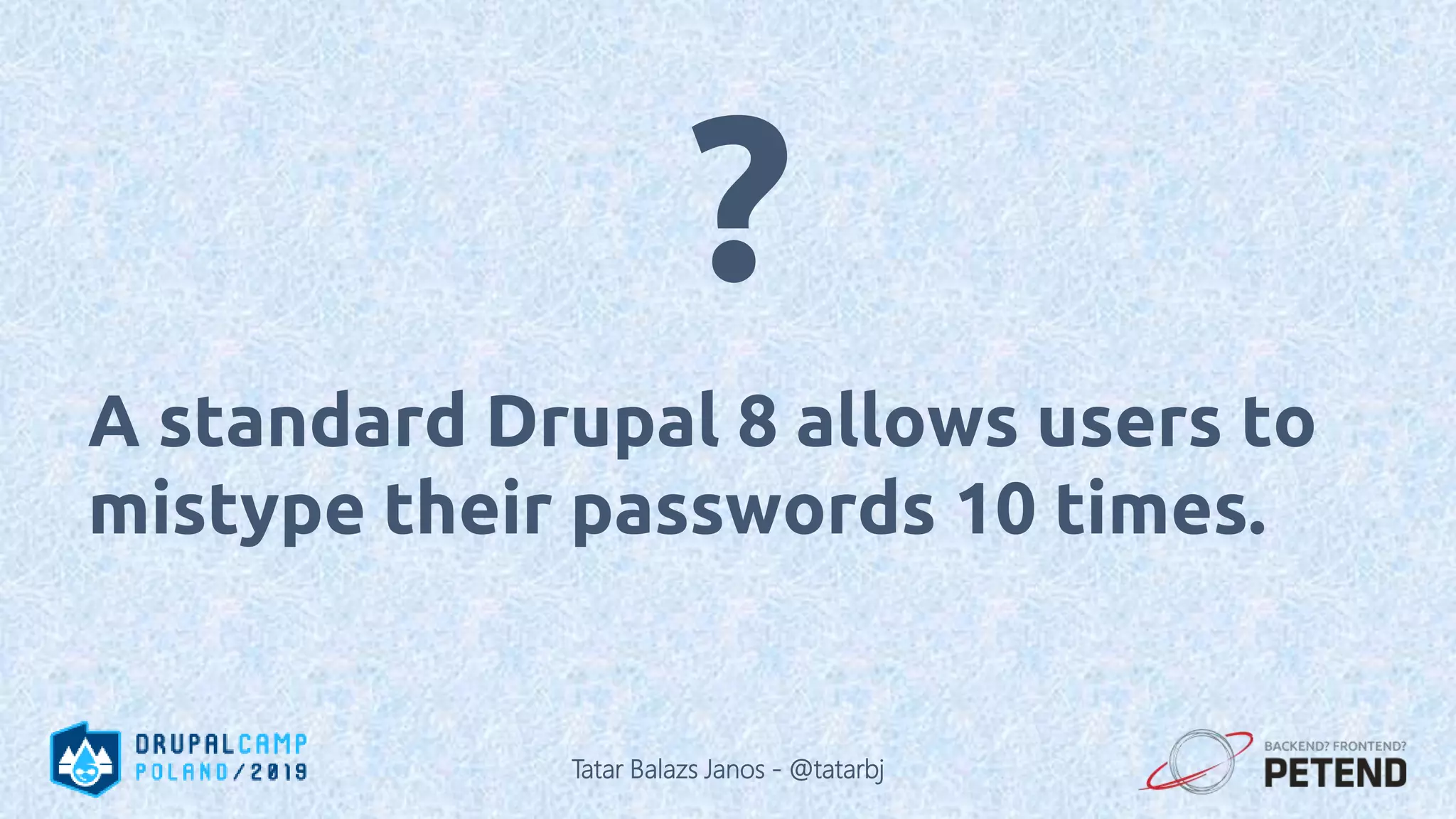

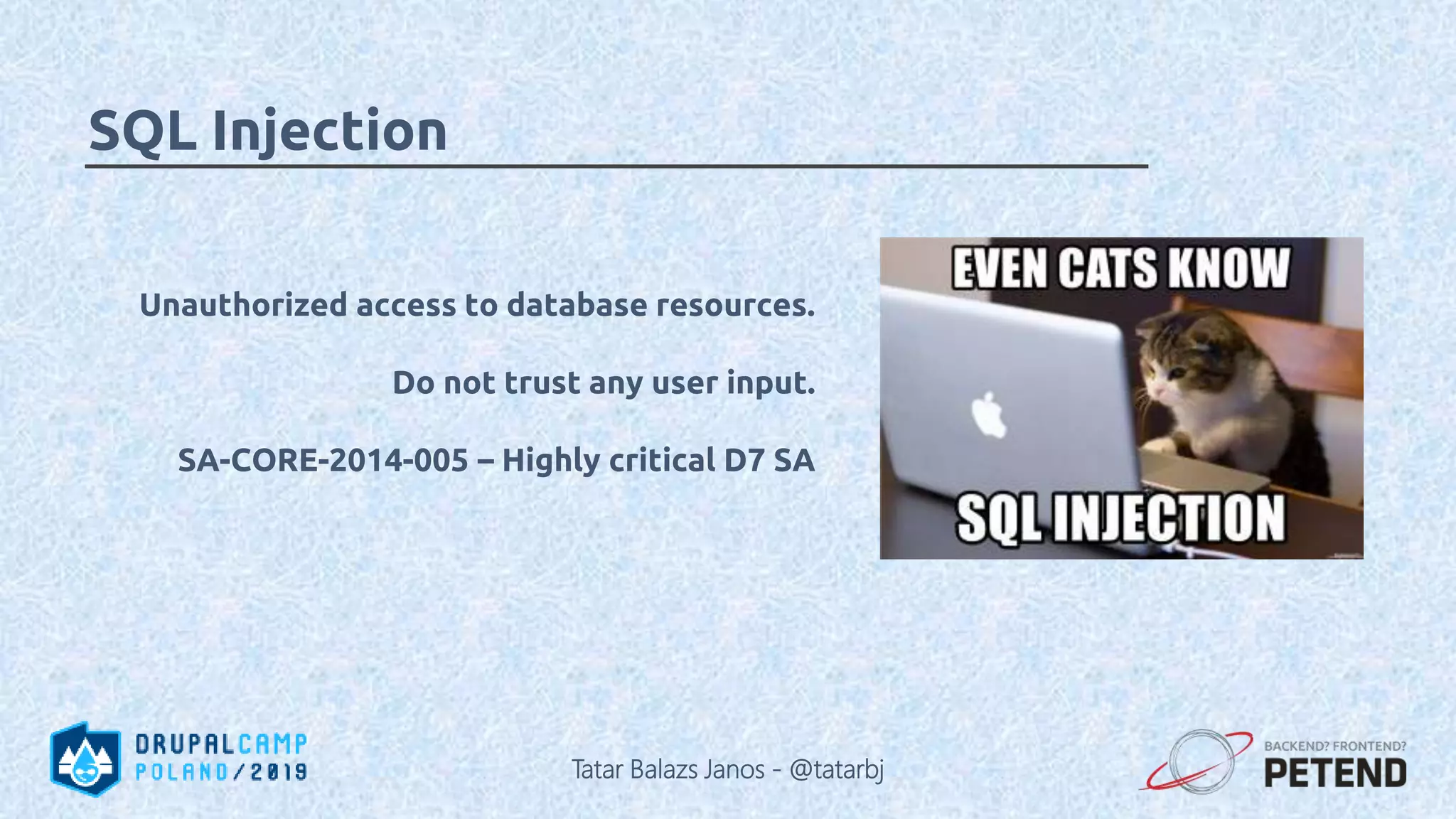

![<?php $result = Drupal::database() ->delete('people') ->condition('name', '%_' . $_GET['param'], 'LIKE'); ->execute(); ?> Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-63-2048.jpg)
![<?php $result = Drupal::database() ->delete('people') ->condition('name', '%_' . $_GET['param'], 'LIKE'); ->execute(); ?> Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-64-2048.jpg)
![<?php $database = Drupal::database(); $result = $database ->delete('people') ->condition('name', $database->escapeLike($_GET['param']), 'LIKE'); ->execute(); ?> Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-65-2048.jpg)
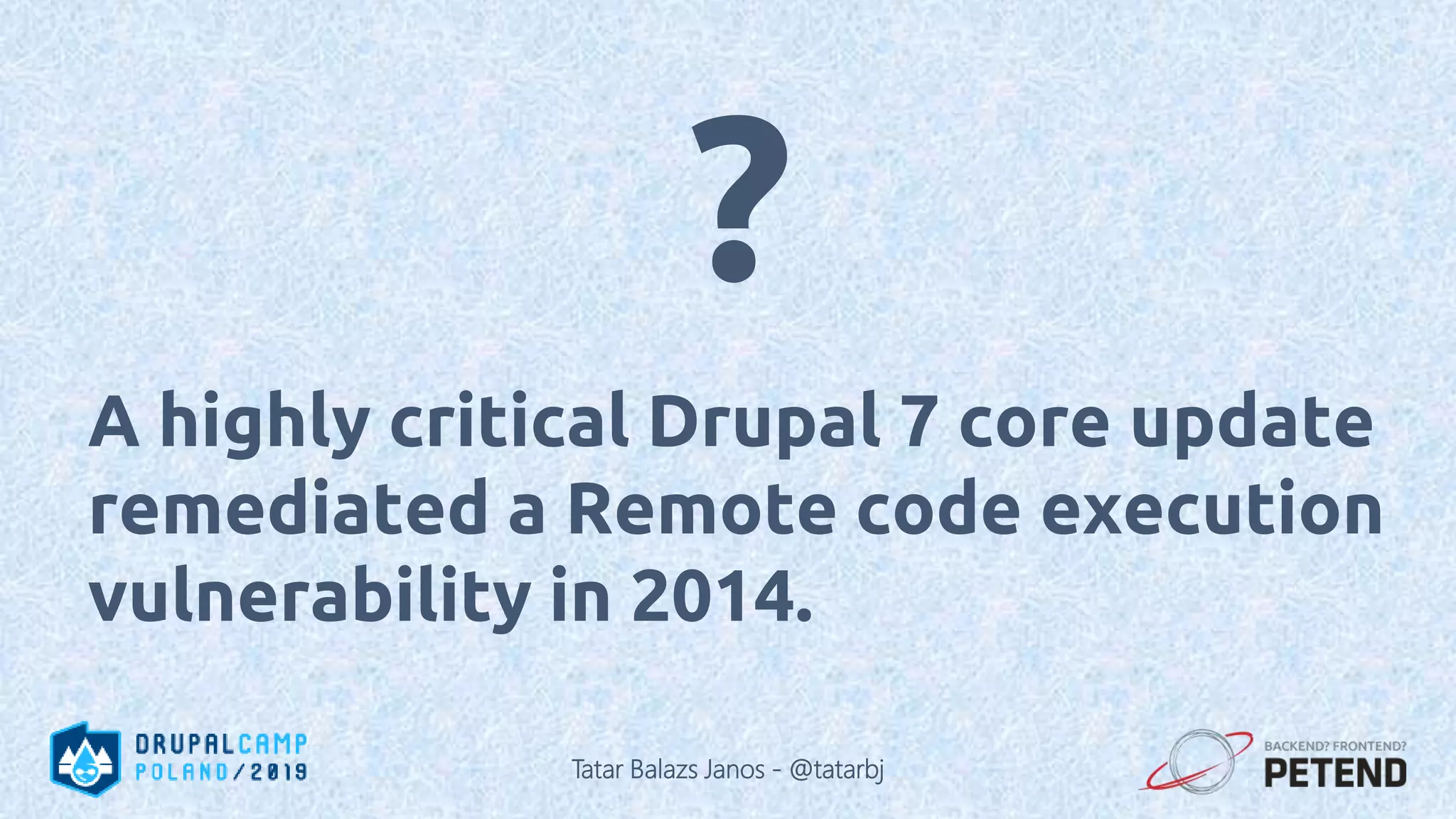
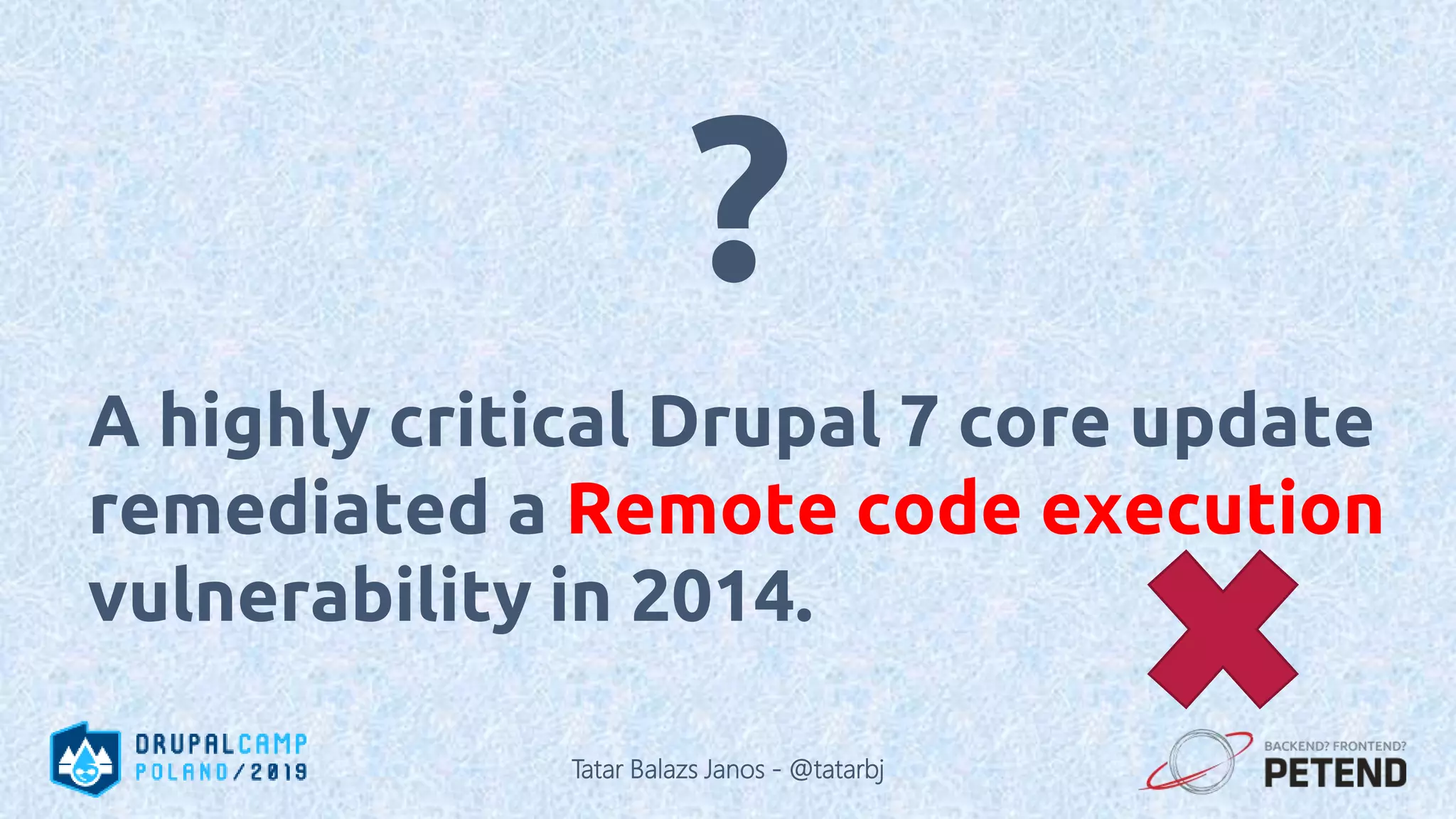
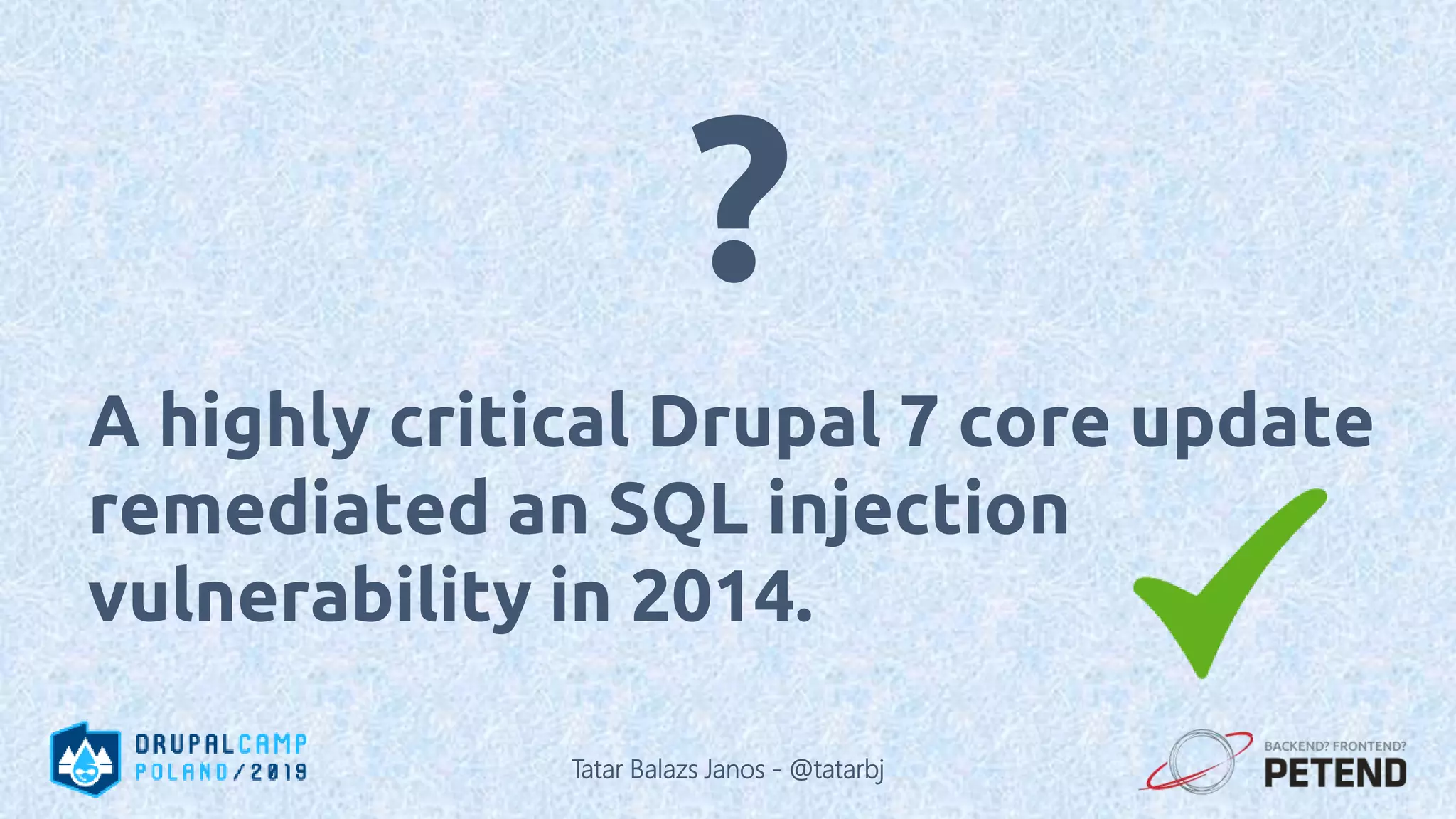
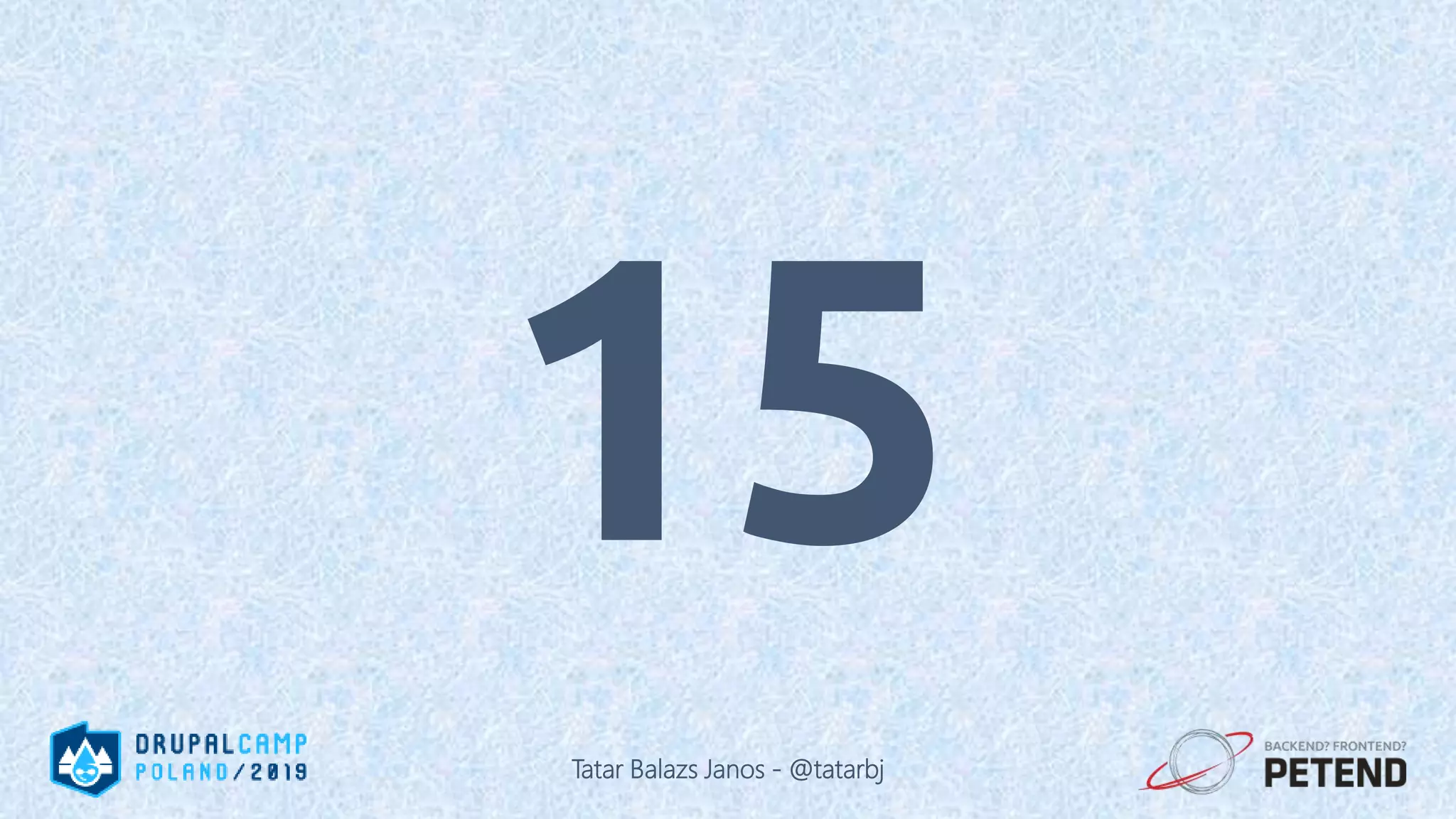

![<?php function _generate_password($length = 8) { $pass = ’’; for ($i = 0; $i < $length; $i++) { // Each iteration, pick a random character from the // allowable string and append it to the password: $pass .= $allowable_characters[mt_rand(0, $len)]; } } ?> Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-74-2048.jpg)
![<?php function _generate_password($length = 8) { $pass = ’’; for ($i = 0; $i < $length; $i++) { // Each iteration, pick a random character from the // allowable string and append it to the password: $pass .= $allowable_characters[mt_rand(0, $len)]; } } ?> Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-75-2048.jpg)
![<?php function _generate_password($length = 8) { $pass = ’’; for ($i = 0; $i < $length; $i++) { do { // Find a secure random number within the range needed. $index = ord(drupal_random_bytes(1)); } while ($index > $len); $pass .= $allowable_characters[$index]; } } ?> Tatar Balazs Janos - @tatarbj](https://image.slidesharecdn.com/letswritesecuredrupalcodepoland2019-190601152636/75/Let-s-write-secure-Drupal-code-Drupal-Camp-Poland-2019-76-2048.jpg)